#NeXT Computer
Text






🇺🇲 Explore the remarkable story of NeXT Computer and its profound influence on the evolution of computing! Founded by Steve Jobs in 1985 following his departure from Apple, NeXT embarked on a mission to redefine personal computing with its pioneering approach and state-of-the-art technology.
💻 Introduced in 1988, the NeXT Computer was celebrated as a revolutionary workstation that pushed the boundaries of hardware and software integration. With its sleek black design and unparalleled performance, it offered users a glimpse into the future of computing.
💡 At its core, the NeXT Computer ran on the NeXTSTEP operating system, a Unix-based platform renowned for its advanced features and developer-friendly environment. Utilizing an object-oriented programming model and intuitive user interface, NeXTSTEP paved the way for modern operating systems, laying the groundwork for macOS and iOS.
🔍 Notable figures such as Tim Berners-Lee, the inventor of the World Wide Web, relied on NeXT workstations to develop the first web browser and web server, underscoring the platform's impact on shaping the internet as we know it today.
📉 Despite initial commercial challenges, the NeXT Computer's legacy endured through its profound influence on the technology industry. In 1997, Apple acquired NeXT, marking Steve Jobs' return to the company he co-founded and setting the stage for Apple's resurgence as a global leader in technology.
🌟 The NeXT Computer remains a testament to innovation and foresight, demonstrating the transformative power of technology to shape the world.
#TechTime Chronicles#electronics#electronic#gadgets#old computers#NeXT#NeXT Computer#Steve Jobs Legacy#Steve Jobs#companies#apple#apple computers#computing#computers#computer#workstation#old technology#information technology#tech#technology#technews#old tech#old internet#old web#macOS#ios#NeXTSTEP#world wide web#1980s computers#made in america
17 notes
·
View notes
Photo

(via The First World Wide Web Server)
I love that you can see the DO NOT POWER DOWN sticker and that the first www server was on a NeXT box.
0 notes
Text
Tag 19: Zauberwürfel in meiner Sammlung - Prost
Quadratisch, Praktisch, Gut. Nein, nicht Ritter Sport. Diesmal geht es um meine Sammlung an Zauberwürfeln. Und einem Bier für die Retrocomputing-Szene.
Der neunzehnte Beitrag in meiner Reihe von Beiträgen zur Neugestaltung der Ausstellung in meinem Computermuseum. Heute und an weiteren 14 Tagen stelle ich die Zusammenstellung meiner Ausstellungsstücke vor. Ein Spielzeug der 80er Jahre war der Rubiks Cube, oder Zauberwürfel. Auch ich habe damals gelernt, wie man dieses Rätsel löst. Steve Jobs hat uns im Jahr 2000 ein neues Rätsel aufgegeben, als…

View On WordPress
0 notes
Text
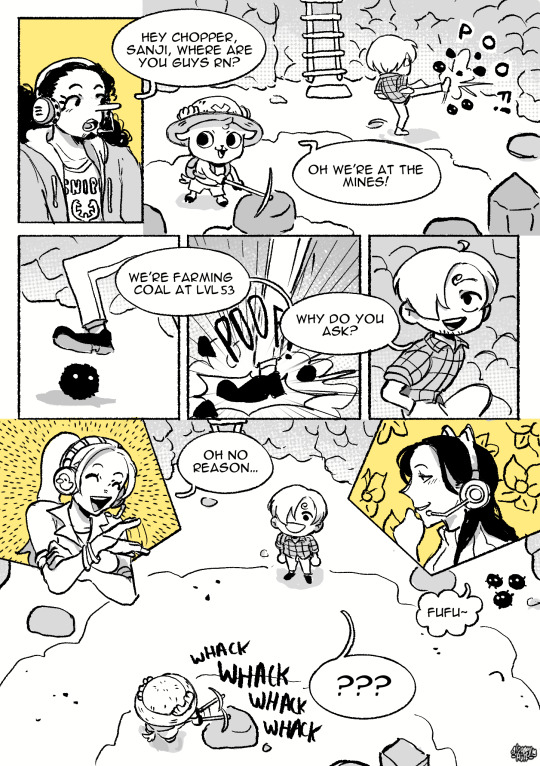




Yes, they are all housemates or roommates (except for Vivi who's discord calling in another country RIP)
Part 2
#modern au#sanuso#usosan#stardew valley#one piece#op fanart#usopp#sanji#nefertari vivi#tony tony chopper#nico robin#luffy and zoro actually room together- usopp is only gaming on zoros computer because he wanted 2 keep it all a secret XD#cant do that while gaming right next to the man in question o _ o#Usopps computer is way better than zoros computer (cause usopp is an epic GAMER and not a filthy CASUAL)#so Zoro was totally down to switch with usopp (hes playing overwatch with every1 else rn)#that does unfortunately mean that he has to game next to the shit cook though XD
5K notes
·
View notes
Text







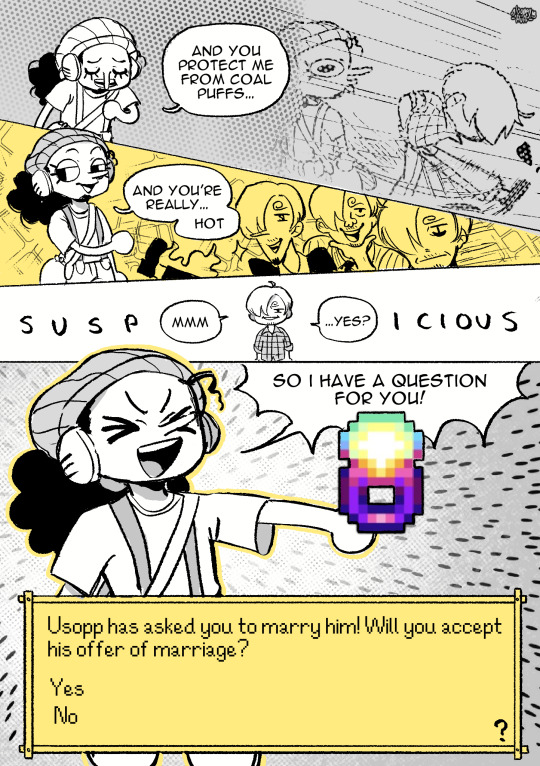
Pain is a great motivator…
Part 26 || First || Previous || Next
—Full Series—
Meanwhile Toriel:

(Loud noises don't wake her up usually.)
Artist note: I’m so proud of this :))) I know it’s a lot of dialogue and reading, but dialogue is grueling work for me. I’m glad with the art and for the amount of pages I made in such a relatively short time span -w- page 5 was super fun to work on. A lot of blood, sweat, and hours here... :) The backgrounds were a big bore tbh, but I finished them! Yippie!
#CHARA WTF DO YOU MEAN “COMPUTER”????#lol i hope you guys dont hate me for what im doing in the next update.#IS THAT A MAC OS???#Yes......owo''#Kris and the Gang are LITTLE now. I've pixelated them and turned them into little game characters!#FINALLY!!#I never thought I would be going so far in the story to explain WHY Kris pulls out their SOUL and opens Darkfountains even when they killed#Berdly in Chapter 2. Pain can make people do horrible things.#Uhhhhhhhhh anyways. :3 I hope you liked it! I made this post a little too long for my liking and didnt get it out when i wanted too-#but thats okay! As long as people enjoy it :)#bread#art#deltarune chara timeline#deltarune chara timeline comic#seriously though#long post#man am I glad I switched over to the limited color palet! It helps me feel alot more relaxed uwu#This is....way over 16 hours of work q-q#chara#asriel#susie#kris#asriel dreemurr#kris dreemurr#kris deltarune#susie deltarune#deltarune#comic#my art
3K notes
·
View notes
Text

Former Emperor of the Merged Realms THIS Close to Stamping His Foot and Pouting!!!!
#now back to the important things……#svsss#myart#bingyuan#shen yuan is defending binghe online not that binghe knows this#my dream for them is that while peerless cucumber is binghe posting#binghe will sit next to him on a second computer and defend peerless cucumber from any detractors
2K notes
·
View notes
Photo






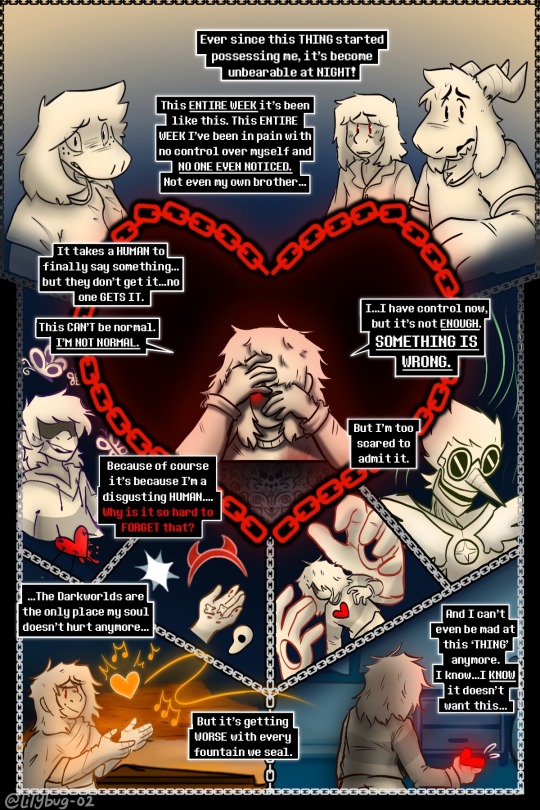
Part 131 of my bakery “enemies” au!
fun fact! I was going to add another panel to the beginning of this part, but my computer kept crashing. so um. pretend something like this is there:

First / Prev / Next / All
Kofi
#ml#miraculous ladybug#miraculous#marinette dupain cheng#marinette dupain-cheng#nino lahiffe#alya cesaire#djwifi#my art#bakery enemies au#im gonna go a day or two without plugging in my tablet to try to see if it's the culprit of the crashes. i dunno#for the record: you can still expect daily uploads. the next ~5 parts are complete as a buffer#and my comic is completely backed up so whatever#but idk why my computer (that literally just got out of an intensive repair where literally every part of it was replaced) is being bitch<3
13K notes
·
View notes
Text

before sleep thoughts...how many takes did they need to make for that scene
#random idea before slemp hehe i just wanted to try#im gonna leave ma home AGAIN AAAA :C goodbye computer pls dont show any more problems next time i turn u on ok#sonic prime#shadow the hedgehog#sonic the hedgehog#sth#wee my art i gues
919 notes
·
View notes
Text
Demon-haunted computers are back, baby

Catch me in Miami! I'll be at Books and Books in Coral Gables on Jan 22 at 8PM.

As a science fiction writer, I am professionally irritated by a lot of sf movies. Not only do those writers get paid a lot more than I do, they insist on including things like "self-destruct" buttons on the bridges of their starships.
Look, I get it. When the evil empire is closing in on your flagship with its secret transdimensional technology, it's important that you keep those secrets out of the emperor's hand. An irrevocable self-destruct switch there on the bridge gets the job done! (It has to be irrevocable, otherwise the baddies'll just swarm the bridge and toggle it off).
But c'mon. If there's a facility built into your spaceship that causes it to explode no matter what the people on the bridge do, that is also a pretty big security risk! What if the bad guy figures out how to hijack the measure that – by design – the people who depend on the spaceship as a matter of life and death can't detect or override?
I mean, sure, you can try to simplify that self-destruct system to make it easier to audit and assure yourself that it doesn't have any bugs in it, but remember Schneier's Law: anyone can design a security system that works so well that they themselves can't think of a flaw in it. That doesn't mean you've made a security system that works – only that you've made a security system that works on people stupider than you.
I know it's weird to be worried about realism in movies that pretend we will ever find a practical means to visit other star systems and shuttle back and forth between them (which we are very, very unlikely to do):
https://pluralistic.net/2024/01/09/astrobezzle/#send-robots-instead
But this kind of foolishness galls me. It galls me even more when it happens in the real world of technology design, which is why I've spent the past quarter-century being very cross about Digital Rights Management in general, and trusted computing in particular.
It all starts in 2002, when a team from Microsoft visited our offices at EFF to tell us about this new thing they'd dreamed up called "trusted computing":
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The big idea was to stick a second computer inside your computer, a very secure little co-processor, that you couldn't access directly, let alone reprogram or interfere with. As far as this "trusted platform module" was concerned, you were the enemy. The "trust" in trusted computing was about other people being able to trust your computer, even if they didn't trust you.
So that little TPM would do all kinds of cute tricks. It could observe and produce a cryptographically signed manifest of the entire boot-chain of your computer, which was meant to be an unforgeable certificate attesting to which kind of computer you were running and what software you were running on it. That meant that programs on other computers could decide whether to talk to your computer based on whether they agreed with your choices about which code to run.
This process, called "remote attestation," is generally billed as a way to identify and block computers that have been compromised by malware, or to identify gamers who are running cheats and refuse to play with them. But inevitably it turns into a way to refuse service to computers that have privacy blockers turned on, or are running stream-ripping software, or whose owners are blocking ads:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai
After all, a system that treats the device's owner as an adversary is a natural ally for the owner's other, human adversaries. The rubric for treating the owner as an adversary focuses on the way that users can be fooled by bad people with bad programs. If your computer gets taken over by malicious software, that malware might intercept queries from your antivirus program and send it false data that lulls it into thinking your computer is fine, even as your private data is being plundered and your system is being used to launch malware attacks on others.
These separate, non-user-accessible, non-updateable secure systems serve a nubs of certainty, a remote fortress that observes and faithfully reports on the interior workings of your computer. This separate system can't be user-modifiable or field-updateable, because then malicious software could impersonate the user and disable the security chip.
It's true that compromised computers are a real and terrifying problem. Your computer is privy to your most intimate secrets and an attacker who can turn it against you can harm you in untold ways. But the widespread redesign of out computers to treat us as their enemies gives rise to a range of completely predictable and – I would argue – even worse harms. Building computers that treat their owners as untrusted parties is a system that works well, but fails badly.
First of all, there are the ways that trusted computing is designed to hurt you. The most reliable way to enshittify something is to supply it over a computer that runs programs you can't alter, and that rats you out to third parties if you run counter-programs that disenshittify the service you're using. That's how we get inkjet printers that refuse to use perfectly good third-party ink and cars that refuse to accept perfectly good engine repairs if they are performed by third-party mechanics:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
It's how we get cursed devices and appliances, from the juicer that won't squeeze third-party juice to the insulin pump that won't connect to a third-party continuous glucose monitor:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
But trusted computing doesn't just create an opaque veil between your computer and the programs you use to inspect and control it. Trusted computing creates a no-go zone where programs can change their behavior based on whether they think they're being observed.
The most prominent example of this is Dieselgate, where auto manufacturers murdered hundreds of people by gimmicking their cars to emit illegal amount of NOX. Key to Dieselgate was a program that sought to determine whether it was being observed by regulators (it checked for the telltale signs of the standard test-suite) and changed its behavior to color within the lines.
Software that is seeking to harm the owner of the device that's running it must be able to detect when it is being run inside a simulation, a test-suite, a virtual machine, or any other hallucinatory virtual world. Just as Descartes couldn't know whether anything was real until he assured himself that he could trust his senses, malware is always questing to discover whether it is running in the real universe, or in a simulation created by a wicked god:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
That's why mobile malware uses clever gambits like periodically checking for readings from your device's accelerometer, on the theory that a virtual mobile phone running on a security researcher's test bench won't have the fidelity to generate plausible jiggles to match the real data that comes from a phone in your pocket:
https://arstechnica.com/information-technology/2019/01/google-play-malware-used-phones-motion-sensors-to-conceal-itself/
Sometimes this backfires in absolutely delightful ways. When the Wannacry ransomware was holding the world hostage, the security researcher Marcus Hutchins noticed that its code made reference to a very weird website: iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com. Hutchins stood up a website at that address and every Wannacry-infection in the world went instantly dormant:
https://pluralistic.net/2020/07/10/flintstone-delano-roosevelt/#the-matrix
It turns out that Wannacry's authors were using that ferkakte URL the same way that mobile malware authors were using accelerometer readings – to fulfill Descartes' imperative to distinguish the Matrix from reality. The malware authors knew that security researchers often ran malicious code inside sandboxes that answered every network query with fake data in hopes of eliciting responses that could be analyzed for weaknesses. So the Wannacry worm would periodically poll this nonexistent website and, if it got an answer, it would assume that it was being monitored by a security researcher and it would retreat to an encrypted blob, ceasing to operate lest it give intelligence to the enemy. When Hutchins put a webserver up at iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com, every Wannacry instance in the world was instantly convinced that it was running on an enemy's simulator and withdrew into sulky hibernation.
The arms race to distinguish simulation from reality is critical and the stakes only get higher by the day. Malware abounds, even as our devices grow more intimately woven through our lives. We put our bodies into computers – cars, buildings – and computers inside our bodies. We absolutely want our computers to be able to faithfully convey what's going on inside them.
But we keep running as hard as we can in the opposite direction, leaning harder into secure computing models built on subsystems in our computers that treat us as the threat. Take UEFI, the ubiquitous security system that observes your computer's boot process, halting it if it sees something it doesn't approve of. On the one hand, this has made installing GNU/Linux and other alternative OSes vastly harder across a wide variety of devices. This means that when a vendor end-of-lifes a gadget, no one can make an alternative OS for it, so off the landfill it goes.
It doesn't help that UEFI – and other trusted computing modules – are covered by Section 1201 of the Digital Millennium Copyright Act (DMCA), which makes it a felony to publish information that can bypass or weaken the system. The threat of a five-year prison sentence and a $500,000 fine means that UEFI and other trusted computing systems are understudied, leaving them festering with longstanding bugs:
https://pluralistic.net/2020/09/09/free-sample/#que-viva
Here's where it gets really bad. If an attacker can get inside UEFI, they can run malicious software that – by design – no program running on our computers can detect or block. That badware is running in "Ring -1" – a zone of privilege that overrides the operating system itself.
Here's the bad news: UEFI malware has already been detected in the wild:
https://securelist.com/cosmicstrand-uefi-firmware-rootkit/106973/
And here's the worst news: researchers have just identified another exploitable UEFI bug, dubbed Pixiefail:
https://blog.quarkslab.com/pixiefail-nine-vulnerabilities-in-tianocores-edk-ii-ipv6-network-stack.html
Writing in Ars Technica, Dan Goodin breaks down Pixiefail, describing how anyone on the same LAN as a vulnerable computer can infect its firmware:
https://arstechnica.com/security/2024/01/new-uefi-vulnerabilities-send-firmware-devs-across-an-entire-ecosystem-scrambling/
That vulnerability extends to computers in a data-center where the attacker has a cloud computing instance. PXE – the system that Pixiefail attacks – isn't widely used in home or office environments, but it's very common in data-centers.
Again, once a computer is exploited with Pixiefail, software running on that computer can't detect or delete the Pixiefail code. When the compromised computer is queried by the operating system, Pixiefail undetectably lies to the OS. "Hey, OS, does this drive have a file called 'pixiefail?'" "Nope." "Hey, OS, are you running a process called 'pixiefail?'" "Nope."
This is a self-destruct switch that's been compromised by the enemy, and which no one on the bridge can de-activate – by design. It's not the first time this has happened, and it won't be the last.
There are models for helping your computer bust out of the Matrix. Back in 2016, Edward Snowden and bunnie Huang prototyped and published source code and schematics for an "introspection engine":
https://assets.pubpub.org/aacpjrja/AgainstTheLaw-CounteringLawfulAbusesofDigitalSurveillance.pdf
This is a single-board computer that lives in an ultraslim shim that you slide between your iPhone's mainboard and its case, leaving a ribbon cable poking out of the SIM slot. This connects to a case that has its own OLED display. The board has leads that physically contact each of the network interfaces on the phone, conveying any data they transit to the screen so that you can observe the data your phone is sending without having to trust your phone.
(I liked this gadget so much that I included it as a major plot point in my 2020 novel Attack Surface, the third book in the Little Brother series):
https://craphound.com/attacksurface/
We don't have to cede control over our devices in order to secure them. Indeed, we can't ever secure them unless we can control them. Self-destruct switches don't belong on the bridge of your spaceship, and trusted computing modules don't belong in your devices.

I'm Kickstarting the audiobook for The Bezzle, the sequel to Red Team Blues, narrated by @wilwheaton! You can pre-order the audiobook and ebook, DRM free, as well as the hardcover, signed or unsigned. There's also bundles with Red Team Blues in ebook, audio or paperback.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/01/17/descartes-delenda-est/#self-destruct-sequence-initiated

Image:
Mike (modified)
https://www.flickr.com/photos/stillwellmike/15676883261/
CC BY-SA 2.0
https://creativecommons.org/licenses/by-sa/2.0/
#pluralistic#uefi#owner override#user override#jailbreaking#dmca 1201#schneiers law#descartes#nub of certainty#self-destruct button#trusted computing#secure enclaves#drm#ngscb#next generation secure computing base#palladium#pixiefail#infosec
577 notes
·
View notes
Text
One last thread. Hoshikawa illustrations that reference other Harukawa bsd illustrations (1/3)



















#Not going to tag everyone obviously. This is going to be long I deeply apologize to everyone who follows me#bsd#bungou stray dogs#bsd beast#sango harukawa art#shiwasu hoshikawa art#mine#q.#29/06/23#For people on computer: J to skip to the next post#For people on mobile: I'm sorry#LONG POST#← The most important tag
251 notes
·
View notes
Text









🤖Data Soong Stimboard🤖
⭐️⭐️⭐️|⭐️⭐️⭐️|⭐️⭐️⭐️
Part 3/7 of my Star Trek TNG crew stimboards
#stimboard#stimboards#star trek#tng#star trek tng#star trek the next generation#the next generation#data#data soong#gold stim#yellow stim#keyboard stim#cat stim#computer stim#old computer stim#sherlock holmes stim#book stim#space stim#violin stim#painting stim
280 notes
·
View notes
Text
wait for your love | abby a
pairing: abby a x gn!reader
tags/warnings: 18+, language, oral (a!receiving), infidelity, owen mention (this is a warning in itself), reader is a bit toxic maybe idk i’ll let you decide that. honestly think that’s it. short and (not) sweet!
a/n: a little something to get me out of my rut. i wrote this very quickly but i just wanted to get something out. i’ll be back properly soon!
HOW TO HELP PALESTINE

“Tell me you love me.”
It’s 6pm, you think. You hadn’t checked the time since she arrived, not wanting to bring attention to the fact that she had to leave, go back to him.
She wasn’t even supposed to stay. She was just supposed to be collecting her things. She wasn’t even supposed to stay.
“Please.”
She doesn’t respond, just wraps her legs tighter around your head and hopes to herself that your head might actually explode from the pressure.
Much to her dismay, it doesn’t. Instead, you dig your nails into her thighs so hard that it leaves marks as though you’re trying to claim her, leave her a reminder. You pull back slightly to spit her wetness back onto her clit and then watching it drip down her pussy, to her ass and onto the already damp sheets. You wonder if he does this to her, too.
“Abby,” you’re breathing heavily, breath coming out in quick huffs that you know Abby can feel because her eyebrows are pulled in tight, the crease between her brows deepening when she finally looks down at you when you speak her name. “Please.”
You think this is the first time she’s looked you directly in the eyes since she got here. When you opened the door to her she couldn’t even look up from where her eyes glued to the floor, sheepishly asking to collect her stuff.
She hasn’t spoken once since you got between her legs, just writhes around on your bed and holds her breath in her lungs whenever you suck her clit into your mouth in the way you know she likes.
You want her to admit it. Admit that she still loves you, admit that leaving you was a mistake. Admit that Owen is just a placeholder in her life for when she finally decides to come back to you.
But she doesn’t, instead just comes on your eager tongue with a groan and a hand covering her mouth as though that would hide how much she fucking loves it.
You let her catch her breath and clamber off the bed in a slight haze. She bends down to pick up her pants and jeans from the floor and you find yourself staring between her legs from your spot on the bed, still laying on your front where she left you.
“We can’t do this anymore.” her voice is raspy as she speaks, shaking hands fiddling with the zip of her jeans. You nod, wordless. You’ve heard that one before and you’ll wait for her to come back around with her tail between her legs like she always does.
Her eyes are bloodshot, freckled cheeks tinted pink. You hope he tells her that she’s pretty when she’s like this.
You watch her leave, still in your position on the bed. You’re inches away from the wet spot on the sheet and you have to tell yourself not to press your lips against the soiled material and get one more taste.
She’ll be back, you tell yourself, rolling onto your side. A small shadow by your door catches your eye and when you squint you realise it’s the bag of Abby’s things you’d packed for her to take prior to her arrival.
Heavy legs carry you from the bed to the dresser where your phone was abandoned. You open your texts and the very much one-sided conversation with her is already open. Convenient.
19:43pm
you left your stuff
20:03pm
Ffs
Tomorrow?
Maybe she’ll admit it tomorrow.

divider cred @/rookthorneartistry
#next post wont be smut but its the only thing my brain could actually compute#H word hours baby!#My writing#abby anderson smut#abby anderson x reader#abby anderson angst#the last of us smut#the last of us angst#abby tlou
304 notes
·
View notes
Text

he's waiting on a call he's planning to send straight to voicemail
#sorry matthias </3 maybe he'll pick up the next time you try calling............ <- me when i lie#river dipping#ts4#ts4 edit#gifs#theodore doe#echthroi#hi friends and lovers hope everyone's doing well <3#i got my old laptop to work so i have a laptop again even if the battery on it is messed up#but still#i haven't been online much bc i've started getting dizzy from staring at computer/phone screens for too long#and in particular the act of scrolling either on mobile or desktop makes my head spin and my eyes hurt :/#but i powered through it yesterday so i could get in game with theo (and matthias) since i missed him really bad... oc plague be upon ye#i took... well. like five hundred screenshots and forty videos... i was in the soup. the mattodore soup. what can i say?#i don't like posting too much on here bc. i'm crazy (<- has avpd) so i probably won't post much from yesterday's fun here#but i'll post whatever i want on pillowfort <3 pic of jerma holding out his hand captioned let's take mattodore together#what else should i say before leaving... right my inbox... well i'll get to it eventually <- have been saying this since october sorry#but okay i've been staring at my screen too long so i need to go lay down for a bit#enjoy theo in motion!! if you’re a theo-head like myself#theodite à la jermamite? hm. its in the works. i’m workshopping.#mentioning jerma twice in these tags… busting a cyanide pill onto my tongue i’ve said too much#i have to go now mwah mwah mwah bye warmth and love to you mwah
251 notes
·
View notes
Text

diànxià’s new blessed shackle (๑˃̵ᴗ˂̵)
#tgcf#hualian#mxtxnet#i have been thinking about this for months. unfortunately i am very slow/artblocked but. i prevailed today 👍🏻#anyway. i love them very much.#also this is the first painting i did entirely on an ipad! i think i like my computer better but it was very useful to learn#also the old guy on the plane next to me liked watching me draw it. I don’t think he knew they’re both men……………
188 notes
·
View notes
Text


NeXT NeXTstation N1100
623 notes
·
View notes
Text

A solution has been found
The solution is portable
Technical implementation is possible and generally applicable
#ID in alt#Rain World#Rain World fanart#Five Pebbles#rw Five Pebbles#Okay had to get this out of my system. If I didn't draw Five Pebbles five pleading for his life I was going to blow up#Between this and the Gabriel martyrdom piece I have so many saint pictures saved on my computer now ffs#Hopefully I'll draw LttM in the next RW art because I like her more. Sorry 5P but I have a favorite iterator sibling#Ask to tag#Hrokkall Art
307 notes
·
View notes