#black hat hacker
Text

This Is What The Black Hat Hacker Look Like In Terrain Of Magical Expertise:
(Seriously, He Resembled The Watchdogs From Manhunt 2 Because Of The Designs Also, They Do Have The Sharp Teeth and Long Tongue Than The White Hat Hacker's Teeth and Tongue, which he look like the tumblr sexyman)
#Terrain Of Magical Expertise#tome rpg#black hat hacker#white hat hacker#i swear that he look like the tumblr sexyman#but what about the gray hat hacker
1 note
·
View note
Video
#WHAT IS ETHICAL HACKING? |Part 3 |#intro beginner |[HINDI] #एथिकल हैकर ...
#youtube#type of hacker#what is ethical hacking#hacker#white hat hacker#black hat hacker#gray hat hacker#what is hacking#what is cyber#intro hack
0 notes
Text
In today’s modern technology, we are using the internet extensively to meet our online needs. We indulge our sensitive data in our regular online resources such as banking information, mobile number, e-mail, and Aadhaar details to have a hassle-free browsing experience.
#hacking#ethicalhacking#ethicalhackers#type of hacking#internet security#grey hat hacker#white hat hacker#black hat hacker#cyber security#cyberattack#cybercrime#infosectrain#learntorise
0 notes
Text
👺
I'D RATHER GET KILLED
THAN LET YOU INVADE
MY PRIVATE SPACE,
NOT BEING ABLE TO KICK YOU OUT,
OR SEE YOUR TRUE FACE!
©
S. Y.
#hackers#hacking#hacking is a crime#hacking is attacking#cybercrime#mental abuse#trauma#my poetry#my poem#black hat hacker#narc abuse#narcissism#narcissist#hacker#hacker narcissist#psycho#anonymous#abuse#abuse of power#poem#poets on tumblr#poetry#reality#notes during the first world cyber war#stalkers#cyberstalking#gaslighting#hackers abuse their power
1 note
·
View note
Text
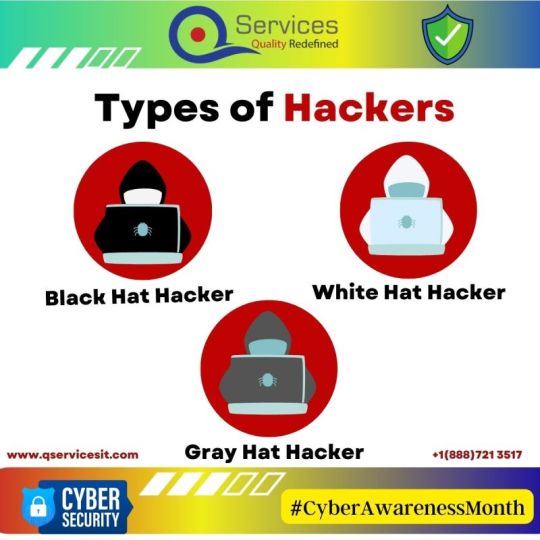
𝗧𝘆𝗽𝗲𝘀 𝗼𝗳 𝗛𝗮𝗰𝗸𝗲𝗿𝘀:
When a Black Hat Hacker discovers a software bug, they attempt to exploit it, frequently by planting malware such as a virus.
White Hat Hackers are moral security intruders who find and patch holes.
Grey Hat Hackers reveal bugs in exchange for payment rather than fully exploiting them, including zero-day bugs.
To read more click here: qservicesit.com
#QServices#typesofhackers#cybersecurity#cybersecurityawareness#cyberattack#hackertypes#white hat hacker#black hat hacker#grey hat hacker
1 note
·
View note
Text
3 Types of Hackers You Don't Know
3 Types of Hackers You Don’t Know
Hacking is the effort to gain access to a computer’s internal private network or system. To put it simply, it is the unauthorized use of computer network security systems or the control over them for illegal purposes. We have different types of hackers and each one of them has a goal.
# 1 White Hat Hackers
White hat hackers use their capabilities to uncover security failings to help safeguard…

View On WordPress
1 note
·
View note
Text

been trying to make a rab design 💥 im going with the bottom one/s (2 different doodles but its the same design) Anyway do we fw my rab
ends of ears (+ maybe part of the hood idk havent decided yet) are black to represent black hat hacking ^_^ which if u dk just refers to hacking used in malicious criminal activity so like ggy ykyk
#i may have done this mostly to implement the black hat hacking thing tbhhh.........#ive had all this information about the different types of hackers since i was a kid and i finally have smth to use it for 🙏🏼🙏🏼#cam.art#fnaf#dr rabbit#dr. rabbit#ggy#probz gonna tweak the design a little but i really like it :3
19 notes
·
View notes
Text
Thinkinmg...of a TOME au
My friend kept quoting the "Yas queen, slay! Slay! SLAY YOUR ENEMIES" video while in call and it just made me think of Nylocke but like.. evil
So TOME swap au where the evil are good and the good are evil
We get an entire protag group of just BADDIES
And I wanna draw that so bad
#i need to sleep#not nylocke though#sorry nye but i'd rather lose my arm than draw armor#he'd have a cool black armor though bc THINK ABOUT IT#THE DANDY ALLIANCE JUST BEING ALL BLACK HAT HACKERS#EDGELORDS <3#tome rpg#terrain of magical expertise
18 notes
·
View notes
Text
"Hacking Unveiled" – An Exploration into the Dark World of Cybercrime
Dive into the heart-pounding realm of hacking and cybercrime with “Hacking Unveiled.” This thrilling journey uncovers the mysterious world of hackers and their techniques, guiding you through the preventative measures you can take to safeguard yourself.
Discover the diverse types of hackers and their motivations, from ethical hackers to cyber criminals. Unveil the intricacies between “white hat” and “black hat” hackers, and learn how to become an ethical hacker yourself.
Enter into the infamous world of the “famous hackers and their stories” and the notorious “anonymous group and their attacks.” Get an inside look into the “hacking techniques used by cybercriminals” and the profound impact these actions have on businesses.
Get a sneak peek into the latest “hacking tools and software” used by both ethical hackers and cybercriminals, and delve into the subjects of “penetration testing” and “protecting against social engineering attacks.” Stay ahead of the game with the latest “hacking news and updates” and uncover the captivating “career opportunities in ethical hacking and cybersecurity.”
Be aware of the ever-evolving future of hacking and cyber threats. Let “Hacking Unveiled” guide you through the unknown, demystifying the complexities of cybercrime.
White Hat Hackers
Black Hat Hackers
Anonymous
Gray Hat Hackers
State-sponsored Hackers
Hardware Hackers
Crackers
The Spectrum of Cybercrime: Understanding the Different Types of Hackers
White Hat Hackers
White hat hackers, or “ethical hackers,” use their skills for good. They work alongside organizations, acting as “cybersecurity experts,” to identify and fix system vulnerabilities, protecting individuals and companies from cyber attacks.
Black Hat Hackers
In contrast, white and “black hat hackers” engage in illegal or malicious activities, such as stealing personal information, disrupting services, and spreading malware.
Anonymous
The loosely organized international group of hackers, “anonymous,” is known for participating in high-profile cyberattacks and spreading political messages.
Gray Hat Hackers
Sitting between white and black hat hackers, “gray hat hackers” may use their skills to identify vulnerabilities but exploit them for personal gain or to draw attention to the issue.
State-sponsored Hackers
The ominous “state-sponsored hackers” work on behalf of governments, using their skills for espionage or political sabotage, potentially significantly impacting national security and international relations.
Hardware Hackers
In addition to software hacking, there are also “hardware hackers,” who specialize in manipulating physical devices, such as breaking into intelligent homes or hacking into cars.
Crackers
A synonym for black hat hackers, “crackers” use their skills to crack into systems, software, or networks, gaining unauthorized access.
Cybercrime: Understanding Standard Techniques
To safeguard against malicious cyber attacks, knowing the most frequently employed tactics, including phishing scams, password attacks, and exploiting software vulnerabilities, is crucial. This post delves into the most prevalent hacking methods, from social engineering and phishing to malware and advanced persistent threats (APTs). Stay alert and ensure your software and security systems are always up-to-date to minimize the risk of falling victim to cybercrime.
Social Engineering: The Deceptive Tactic
Cybercriminals often resort to social engineering to manipulate individuals into divulging sensitive information or performing actions they wouldn’t otherwise. This tactic can take various forms, including phishing scams, pretexting, baiting, and more. To guard against these attacks, it is critical to be suspicious of unsolicited requests for personal data, be cautious when clicking on links or downloading attachments from unknown sources, and keep your software and security programs up-to-date.
Phishing: The Tricky Scam
Phishing is a form of social engineering that seeks to deceive individuals into surrendering confidential information, such as login credentials, financial details, or sensitive personal data. These scams often come in email or text messages, posing as credible sources. To avoid falling prey to phishing attempts, it is recommended to look out for suspicious messages, particularly those asking for personal information, verify the authenticity of links before clicking on them, and be wary of downloading attachments or clicking links from unknown sources.
Malware: The Harmful Threat
Malware, including viruses, trojans, and ransomware, is specifically designed to cause harm to computer systems. Installing and updating a reputable antivirus program is essential to protect your computer.
Additionally, be mindful of the files you download and links you click, especially if they are from unknown sources, as they may contain malware.
APTs: The Persistent Threat
Advanced persistent threats (APTs) are cyber attacks by state-sponsored hackers or highly-skilled cybercriminals. These attacks are known for their persistence as the attackers often go undetected for an extended period. To detect and fend off APTs, it is crucial to have an up-to-date antivirus program installed on your computer and to be cautious of unsolicited emails or text messages, especially those asking for personal information.
Defending Against Cyber Threats: Strategies for Keeping Your Data Safe
Essential Tactics to Outwit Hackers and Stay Secure
Essential tactics to protect against cyberattacks include using robust passwords, safeguarding personal information, regularly updating software, and securing devices. These may sound simple, but neglecting to do so can have severe consequences.
The Importance of Strong Passwords and Up-to-Date Software Keeping software current helps to avoid vulnerabilities that older versions may have. Strong, unique passwords for each account can provide an easy yet effective layer of security.
Tips to Protect Personal Information and Devices Being mindful of phishing scams, using privacy settings on social media, and being prudent about what personal information is shared online are critical in securing personal information. Ensure devices are protected with a passcode or fingerprint and backup important files regularly.

The Mysterious World of the Dark Web
The dark web may sound like a concept from a hacker movie, but it’s real and can be a bit frightening. It’s crucial to understand what it is, how it differs from the regular web, and the type of activity. This article will shed some light on the enigmatic side of the internet.
Accessing the dark web requires special software and is invisible to the general internet user. It’s often linked to illegal activities, such as buying and selling illicit items, hacking services, and trafficking personal information. Exercise caution when accessing the dark web and take steps to protect personal information.
The dark web is a collection of websites that can only be accessed using specialized software, such as the Tor browser. Despite being often linked to illegal activities, not all its use is illicit.
However, accessing the dark web carries risks and can threaten personal information and security. Be cautious and take measures to protect personal data when accessing the dark web.
Why Access the Dark Web
Accessing the dark web can be dangerous and threaten personal information and security. Exercise caution and take necessary measures to protect personal data when accessing the dark web.
How to Enter the Dark Web
The most popular way to access the dark web is by using the Tor browser. It’s a free, open-source browser that routes traffic through multiple layers of encryption, making it challenging to trace activity. However, accessing the dark web comes with risks and requires using a VPN, never sharing personal information, and avoiding using real names.
Now that you have a better understanding of the dark web, the choice is to delve into the mysterious side of the internet.
Don’t Fall Victim: How to Protect Yourself from Identity Theft
Be Alert! Identity Theft Lurks, Stalking Unsuspecting Victims
It’s a modern-day nightmare – cybercriminals prowling the internet, seeking out unsuspecting individuals and businesses to victimize through identity theft. From phishing scams to data breaches, the tactics used by these criminals are sophisticated and ever-evolving. The consequences of falling prey to such a crime can be devastating, leaving financial losses and a tarnished reputation in its wake.
Beware! Know Your Enemy.
Cybercriminals use various methods to obtain personal information, including phishing scams, data breaches, dumpster diving, and even purchasing it on the dark web. Stay informed and take proactive measures to protect yourself and your information.
The Aftermath – A Life Turned Upside Down
The impact of identity theft is far-reaching, affecting victims’ finances and reputation and often causing emotional stress as they work to regain control of their personal information.
Don’t Be a Statistic – Defend Yourself!
Fortunately, you can take steps to safeguard yourself against identity theft. Regularly updating software, using strong and unique passwords, being cautious about sharing personal information, and remaining vigilant for unsolicited phone calls or emails are just a few examples.
Protect Your Information and Devices
In addition to these basic measures, take extra steps to secure your personal information and devices. Keeping personal information offline, using anti-virus software and firewalls, encrypting sensitive data, and ensuring your devices with locks and PINs are crucial for maximum protection.
If Disaster Strikes – Have a Plan
If you suspect you have fallen victim to identity theft, acting quickly is essential. Notify your bank, credit card companies, and credit reporting agencies to place a fraud alert on your accounts. Turn to resources such as the Federal Trade Commission’s IdentityTheft.gov and the Identity Theft Resource Center for guidance on reporting and recovering from the crime.
Stay Protected – Stay Vigilant
Identity theft is a constant threat that requires ongoing attention and preventative measures. By staying informed, protecting yourself and your information, and knowing where to turn in the event of a breach, you can reduce your risk of falling victim to this malicious crime.
Stay Ahead of the Game – Subscribe to Our Blog!
Remember to subscribe to our blog for more informative and helpful articles on cybersecurity and protecting yourself. Stay ahead of the game in the fight against identity theft!
This article is originally posted at https://nikolin.eu/tech/hacking-unveiled-a-fascinating-dive-into-the-world-of-cybercrime-and-its-prevention/
#hacking#hackers#black hat hackers#white hat hackers#gray hat hackers#cybercrime#cybersecurity#dark web
10 notes
·
View notes
Text
Flipper Zero Hacking Device On Track To Earn $80 Million In Sales
#superglitterstranger#flipper zero#hacker life#hollywood#hacker news#gadgets#technology#hackingtools#black hat#red hat#hellboundhackers#techcrunch
4 notes
·
View notes
Text

Rent a Black Hat Hacker for Ethical Cyber Defense Collaboration
Explore the brighter side of cyber security with Aurorahackersgroup as you rent a black hat hacker. Together, we fortify your digital defenses, address vulnerabilities, and boost overall cyber security responsibly. Choose wisely to safeguard your digital assets through ethical collaboration
Visit us:- https://aurorahackersgroup.co/rent-black-hat-hacker/
0 notes
Text
Scammers Suck!!!Thats Why I Love Reporting Their Asses When They Try Following or Interacting with Me When I Notice Links on Their Blogs that I Think May Contain Malware or Lead to Malicious Sites!!!

1 note
·
View note
Text
#white hat hacker#black hat hacker#different#hacking#cybersecurity#hacking techniques#security#hacking help#hack#data security#data privacy#hacking news
0 notes
Text
El hacker César Cerrudo aconseja cómo protegerse ante las amenazas digitales

View On WordPress
#1Password#amenazas digitales#Argentina#Black Hat#blockchain#César Cerrudo#Dashlane#Ekobooks#Ekoparty#Estados Unidos#fishing#Guía de seguridad de un hacker#hacker#IBM#Internet#Internet de las cosas#IoT#LastPass#Microsoft#new york times#Oracle#phishing#Scam#SMS#The Guardian#TIC#Time#Twitter#Whatsapp
1 note
·
View note
Text
I GOT DELETED.
A little argument over whether or not Genshin Impact shamelessly copies off Breath of the Wild and Tears of the Kingdom I guess was the final breaking point. I think the deletion/block? off Discord only really serves as a reminder that my friendship isn't really a net positive to people. I can't say this is the first time it's happened and as someone who once cried over being called a bad person, you would think I have some urge to prove otherwise.
I can't honestly tell you what drives me, and if I were brave enough to propose a nihilistic theory as to what, I would probably say hedonism and selfishness, but the truth is I can't really discuss this with anyone without any sort of negative feedback. And that isn't even a good theory because those traits just seem like symptoms to a much deeper problem. I think even admitting that to anyone would put them on alert as to how I could potentially hurt them.
Maybe I just use people as outlets for my own thoughts and entertainment and I don't care about them at all. In retrospect, it seems like a no-brainer from the outside looking in, but messing around with his girlfriend is not something you do to someone you consider your childhood best friend. And even though he forgave me quickly then, I can't help but ask if I even deserve it and if things like that make it easier to just forget about me.
I worry about the people I talk to now. Or maybe, I just worry about losing them and confirming what I already think about myself - that I deserve to be alone. Whether I bother them too much, weigh them down with too much negativity, burden them with my problems and rants. What are they getting out of talking to me really and is it truly worth it for them? I worry that people are better off and happier without me. If we're being honest, I 100% believe they are. Sometimes it feels like my thoughts and words just cast a shadow over their otherwise relatively unproblematic existence.
Do I deserve to be with anyone? I wonder if I'm hurting my girlfriend's one shot at a fulfilling life by being with me. Because I know I'm not personally fulfilled so much so that I have the urge to write a blog post to nobody about everything going on in my head. Does she deserve someone who isn't constantly questioning who they are and what their value is? Sometimes I wonder if I'm better off alone so I can't hurt anyone. Sometimes I think if this were to fall through, I probably wouldn't start a relationship with anyone again. I think life might just be easier when you leave your self-destructive tendencies to yourself. At least then, there is no one there to hammer the point home.
I wonder what I would have written about today if I hadn't found out he unadded me an hour ago.
#baby come back#baby back ribs#chilis#biden administration#toy story#woody harrelson#jennifer lawrence#dinosaurs#michael jackson#black hat#hacker#binary code#80s computers#retro#robots
1 note
·
View note
Text
u ever start loving a character and then realize. Ughh of course this mf is your favorite u predictable little freak!!!!!!
#hmmm i wonder why i became hyperfixated on gregory + ggy. Surely its not my lifelong interest in hacking and characters who r hackers#that reminds me i should make a rab design that references black hat hacking*#i could make his ears have like black tips or be fully black... Mwahahhaaaa. hacking is so interesting#*black hat hacker refers to a hacker that uses their abilities for illegal purposes / activities. which ggy would be considered#other types of hackers include white hat. grey hat. script kiddies. blue hat. green hat. red hat etc. lots of hats. LIKE WIZARDS IN A WAY#cuz wizards wear those pointy little hats yk....... ggy reference Question mark 🧐🧐 (idk wtf im talking ab anymore ignore this part)#cam.txt
1 note
·
View note