#Password management
Text
FabSec05 - Security Posture
Tempo fa avevo pubblicato un paio di post legati all’utilizzo delle password e all’uso che ne facciamo. Il primo era questo, mentre il secondo lo trovate qui
L'altro giorno mi sono imbattuto in un articolo di Daniel Miessler, un esperto di sicurezza informatica che seguo con interesse. L’articolo contiene una sorta di classificazione della sicurezza e gestione delle nostre password, riassunta da questo diagramma:

Il diagramma mostra quanto debole o robusto possa essere il modo in cui utilizziamo le password tutti i giorni. Si parte da
1 = password condivise = male, molto male!
e si arriva a
8 = utilizzo di un token fisico, tipo Yubico o Thetis = well done!
Sul lato destro è anche presente una lista di attacchi associati a ciascuna “security posture”, attacchi che sono obbligati a diventare sempre più sofisticati man mano che si sale.
Il diagramma è un buono strumento per incentivare le persone a migliorare la propria sicurezza (chi non vuole scalare una classifica?! :), perciò ho pensato fosse un ottimo complemento a quella discussione.
Per chi fosse interessato all’articolo completo, eccolo qui
#infosec#infomation security#fabsec#password#password management#sicurezza#sicurezza informatica#cyber#cybersecurity
4 notes
·
View notes
Text
Cybersecurity Report: Protecting DHS Employees from Scams Targeting Personal Devices
🔒 DHS Cybersecurity Alert! 🔒 Scammers targeting personal devices threaten national security. Our new report reveals these risks & offers robust solutions - MFA, security software, cybersecurity training & more. Safeguard yourself & critical operations!
Introduction
The digital age has ushered in an era of unprecedented connectivity and technological advancements, but it has also given rise to a new breed of threats that transcend traditional boundaries. Cybercriminals are constantly evolving their tactics, exploiting vulnerabilities in both organizational systems and personal devices to gain unauthorized access, steal sensitive data, and…

View On WordPress
#access controls#antivirus#awareness campaigns#best practices#collaboration#cyber resilience#cybersecurity#cybersecurity training#data backup#data protection#DHS#firewall#government#impersonation#incident response#insider threats#malware#multi-factor authentication#national security#password management#personal device security#phishing#physical security#public outreach#risk assessment#scams#social engineering#software updates#threat intelligence#VPN
1 note
·
View note
Text
Unlock Fort Knox for Your Laptop: The Definitive Guide to Bulletproof Security

What steps can I take to enhance my laptop's security?
Dive into my latest Blog post and discover the ultimate secrets to fortifying your laptop's defenses! Transform your device into a digital fortress and safeguard your data like never before.
From foolproof password strategies to state-of-the-art encryption techniques, explore a treasure trove of tips and tricks to keep hackers at bay. Say goodbye to cyber worries and hello to peace of mind!
Ready to take control of your laptop's security? Arm yourself with knowledge now!
Read the full post and become the guardian of your digital domain. #LaptopFortress #SecureYourData #ReadMore
#LaptopSecurity#DataProtection#CybersecurityTips#Laptop security#Data protection#Cybersecurity tips#Digital privacy#Encryption#Password management#Cyber threats#Data security measures#Online safety#Tech security#Information security#Secure computing#IT security#Protecting sensitive data#Internet safety
1 note
·
View note
Text
Importance Of Using Password Manager
A password manager stores all your passwords in a single account. The master password to your safe is the only the password you'll ever need to remember.

0 notes
Text
The global password management market is experiencing growth due to several factors, including a rise in the adoption of remote work culture, an increase in demand for convenient authentication methods, and cybersecurity concerns among consumers
#password management market#password management#password market#password management market growth#password management market trends
0 notes
Text
youtube
What are Session and Federation Management Techniques
Session and federation management are critical aspects of identity and access management (IAM) in modern web applications and systems. They deal with how user authentication and authorization are handled across different services and applications.
#session and federation management techniques#session management#federation management#single sign-on#federation in cyber security#identity and access management#cyber security authentication#token-based authentication#cyber security tokens#cross-site request forgery#state management#security assertion markup language#service providers#identity federation protocols#security protocols#multi-factor authentication#password management#role-based access control#Youtube
0 notes
Text
TIL that you can assign an AO3 next of kin to control your account in case of your death???
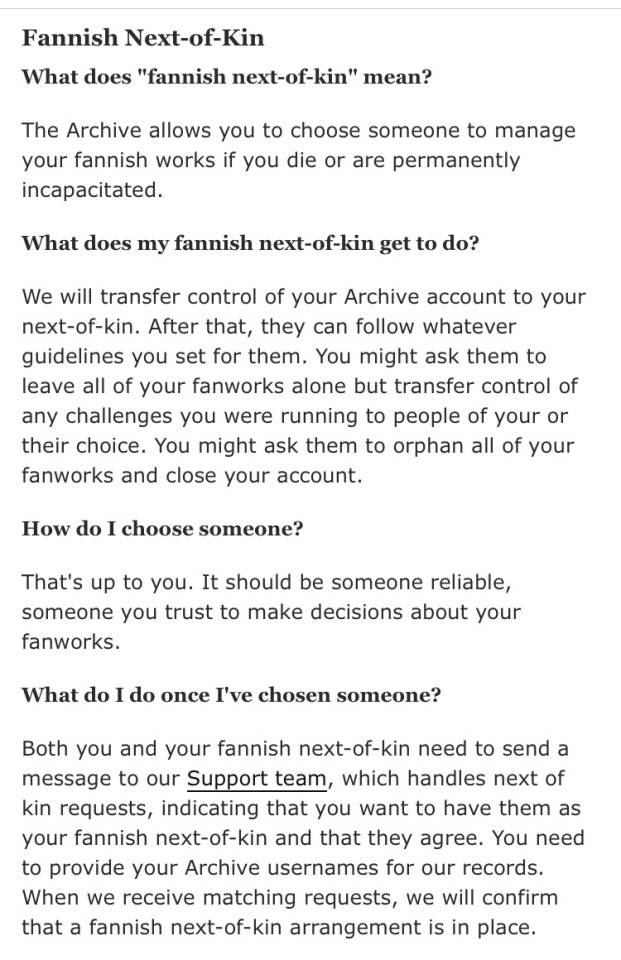
#ao3#this is actually really neat#I had a will at one point that included passwords and usernames specifically for my sister so she could manage certain social media#including my fanfic accounts#if anything happened to me#I need to update it it's been like...idk a decade#who makes a will when they're sixteen you might ask#ppl who want to be dead I will answer very seriously while shaking my bottle of SSRI like a baby rattle
3K notes
·
View notes
Text
youtube
What are Session and Federation Management Techniques
Federation is a very common method used by most organizations to maintain user identity. There are many techniques and frameworks available to manage the federation. In this episode, we will learn about the basics of session management as well as user federation workflow. Join our Facebook page: https://www.facebook.com/InfoSecForStarters
#session and federation management techniques#session management#federation management#single sign-on#federation in cyber security#identity and access management#cyber security authentication#token-based authentication#cyber security tokens#cross-site request forgery#state management#security assertion markup language#service providers#identity federation protocols#security protocols#multi-factor authentication#password management#role-based access control#Youtube
0 notes
Text
Online Security in the Age of AI: Protecting Your Data and Privacy
In the age of artificial intelligence (AI), cybersecurity concerns have grown exponentially. As AI continues to advance, so do the capabilities of cybercriminals who use sophisticated tools and techniques to exploit vulnerabilities in the digital world. In this article, we’ll explore the challenges and risks associated with online security in the AI era, and provide practical tips for protecting…

View On WordPress
#AI-powered attacks#Artificial Intelligence#cyber threats#cybersecurity education#data privacy#deepfakes#device security#network security#online security#password management#two-factor authentication
0 notes
Text
why are so many of you not saving the backup codes they give you when you set up two-factor authentication
#original#i print mine out and also save them in the notes section of my password manager#also you should use an authenticator app and not sms whenever possible bc sms is susceptible to sim spoofing#but people not knowing that is not as mindblowing to me#as the thought of seeing 'here are your backup codes' and not frantically saving it in multiple places
2K notes
·
View notes
Text
andrew’s definitely gotten in trouble with his pr manager for tweeting things along the lines of:
“no mania inducing medication will compare to the euphoria i will feel the day donald trump drops dead”
#pr manager is like: andrew… this is the last time i’m gonna tell you#andrew: whats the point of democracy if i can’t exercise freedom of speech#pr manager: andrew it’s no longer about your image#at this point we are concerned the fbi is going to show up#andrew: neil has connections. i’m fine#they thought marketing andrew on social media would be good#they were sooooo wrong#because now andrew has a place to share every insane thing he’s ever thought#for instance—a tweet that just says ‘an alien googling: human clothes’#he’s on there advocating for lgbtq+ youth you KNOW HE IS#he’s cursing and mildly threatening members of congress for imposing these disgusting bills#one day he tweeted ‘does mitch mcconnell know he’s dead yet’#when mitch mcconnell stepped down from senate andrew tweeted ‘hopefully next he steps down from life’#unsurprisingly: this endears him to some people and makes others fucking hate him#and he’s such a shit. he does not care either way#he’s kind of just like: pr manager. you gave me a twitter and told me to tweet. i’m just doing what you asked me#they’ve threatened to change his password so many times#they actually did once but andrew reported the account so many times for defamation and fraud that it got suspended#and he made a new account out of pure spite#his pr manager is like: andrew nobody is going to want to sign you because of your public image#and andrew is like: ?? ok. they can lose every game then#(he knows he’s the best goalie)#ok i think that’s enough for now. however i will probably be back#andrew minyard#aftg#tfc#trk#tkm#the foxhole court#all for the game
362 notes
·
View notes
Text
Okay, look, they talk to a Google rep in some of the video clips, but I give it a pass because this FREE course is a good baseline for personal internet safety that so many people just do not seem to have anymore. It's done in short video clip and article format (the videos average about a minute and a half). This is some super basic stuff like "What is PII and why you shouldn't put it on your twitter" and "what is a phishing scam?" Or "what is the difference between HTTP and HTTPS and why do you care?"
It's worrying to me how many people I meet or see online who just do not know even these absolute basic things, who are at constant risk of being scammed or hacked and losing everything. People who barely know how to turn their own computers on because corporations have made everything a proprietary app or exclusive hardware option that you must pay constant fees just to use. Especially young, somewhat isolated people who have never known a different world and don't realize they are being conditioned to be metaphorical prey animals in the digital landscape.
Anyway, this isn't the best internet safety course but it's free and easy to access. Gotta start somewhere.
Here's another short, easy, free online course about personal cyber security (GCFGlobal.org Introduction to Internet Safety)
Bonus videos:
youtube
(Jul 13, 2023, runtime 15:29)
"He didn't have anything to hide, he didn't do anything wrong, anything illegal, and yet he was still punished."
youtube
(Apr 20, 2023; runtime 9:24 minutes)
"At least 60% use their name or date of birth as a password, and that's something you should never do."
youtube
(March 4, 2020, runtime 11:18 minutes)
"Crossing the road safely is a basic life skill that every parent teaches their kids. I believe that cyber skills are the 21st century equivalent of road safety in the 20th century."
#you need to protect yourself#internet literacy#computer literacy#internet safety#privacy#online#password managers#security questions#identity theft#Facebook#browser safety#google#tesla#clearwater ai#people get arrested when google makes a mistake#lives are ruined because your Ring is spying on you#they aren't just stealing they are screwing you over#your alexa is not a woman it's a bug#planted by a supervillain who smirks at you#as they sell that info to your manager#oh you have nothing to hide?#then what's your credit card number?#listen I'm in a mood about this right now#Youtube
147 notes
·
View notes
Note
can you actually talk about bitwarden / password managers, or direct me to a post about them? Idk my (completely uneducated) instinct says that trusting one application with all your passwords is about as bad as having the same password for everything, but clearly that isn’t the case.
So it is true that online password managers present a big juicy target, and if you have very stringent security requirements you'd be better off with an offline password manager that is not exposed to attack.
However, for most people the alternative is "reusing the same password/closely related password patterns for everything", the risk that one random site gets compromised is much higher than the risk that a highly security focussed password provider gets compromised.
Which is not to say it can't happen, LastPass gets hacked alarmingly often, but most online password managers do their due diligence. I am more willing to stash my passwords with 1Password or Bitwarden or Dashlane than I am to go through the rigamarole of self-managing an array of unique passwords across multiple devices.
Bitwarden and other password managers try to store only an encrypted copy of your password vault, and they take steps to ensure you never ever send them your decryption key. When you want a password, you ask them for your vault, you decrypt it with your key, and now you have a local decrypted copy without ever sending your key to anyone. If you make changes, you make them locally and send back an encrypted updated vault.
As a result, someone who hacks Bitwarden should in the absolute worst case get a pile of encrypted vaults, but without each individuals' decryption key those vaults are useless. They'd still have to go around decrypting each vault one by one. Combining a good encryption algorithm, robust salting, and a decent key, you can easily get a vault to "taking the full lifetime of the universe" levels on security against modern cryptographic attacks.
Now there can be issues with this. Auto-fill can be attacked if you go onto a malicious website, poorly coded managers can leak information or accidentally include logging of passwords when they shouldn't, and obviously you don't know that 1Password isn't backdoored by the CIA/Mossad/Vatican. If these are concerns then you shouldn't trust online password managers, and you should use something where you remain in control of your vault and only ever manually handle your password.
Bitwarden is open source and fairly regularly audited, so you can be somewhat assured that they're not compromised. If you are worried about that, you can use something like KeePassXC/GNU Pass/Himitsu/ (which all hand you the vault file and it's your job to keep track of it and keep it safe) or use clever cryptographic methods (like instead of storing a password you use a secret key to encrypt and hash a reproducible code and use that as your password, e.g. my netflix password could be hash(crypt("netflixkalium", MySecretKey)), I know a few people who use that method.
Now with any luck because Apple is pushing for passkeys (which is just a nice name for a family of cryptographic verification systems that includes FIDO2/Webauthn) we can slowly move away from the nightmare that is passwords altogether with some kind of user friendly public key based verification, but it'll be a few years before that takes off. Seriously the real issue with a password is that with normal implementations every time you want to use it you have to send your ultra secret password over the internet to the verifying party.
237 notes
·
View notes
Note
Aro culture is the amount of ads i get for dating apps whenever i go anywhere near the internet
.
#Anonymous#aro culture is#aro#aromantic#actually aro#actually aromantic#ask#highly recommend using firefox#and installing: uBlock origin + bitwarden as a password manager + sponsorblock for youtube#it's bliss
68 notes
·
View notes
Text
yesterday i turned 30 so unfortunately i must commit seppuku and delete my blog
#op#just kidding ive been here for a decade now#you'll have to pry it from my cold dead password manager
108 notes
·
View notes