#I had a will at one point that included passwords and usernames specifically for my sister so she could manage certain social media
Text
TIL that you can assign an AO3 next of kin to control your account in case of your death???
#ao3#this is actually really neat#I had a will at one point that included passwords and usernames specifically for my sister so she could manage certain social media#including my fanfic accounts#if anything happened to me#I need to update it it's been like...idk a decade#who makes a will when they're sixteen you might ask#ppl who want to be dead I will answer very seriously while shaking my bottle of SSRI like a baby rattle
3K notes
·
View notes
Text
One of the craziest corporate scams in the U.S is child care, an absolute necessity for so many families. I live in New Mexico and let me show you why.
According to care.com’s childcare calculator, for my area alone, 40 hours of childcare a week for ONE child would be 191 dollars. That is upwards of 750 dollars a month and almost 10,000 dollars per year. (This number does change depending on the age of your child.) There are families that qualify for state programs that can help relieve these costs, but it’s never promised.


But do you want to see what’s so crazy?
Here are the wages if you are applying to be a child care center teacher.
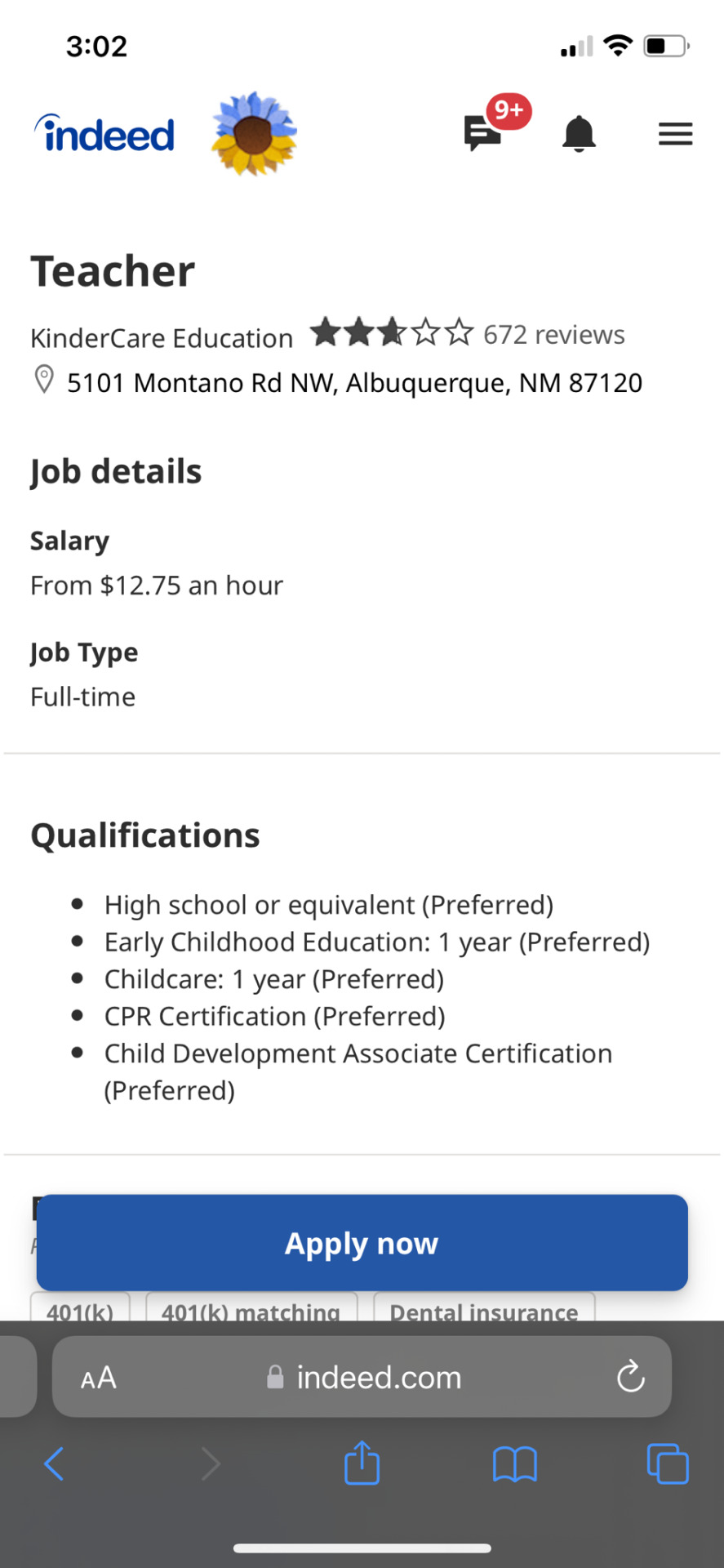
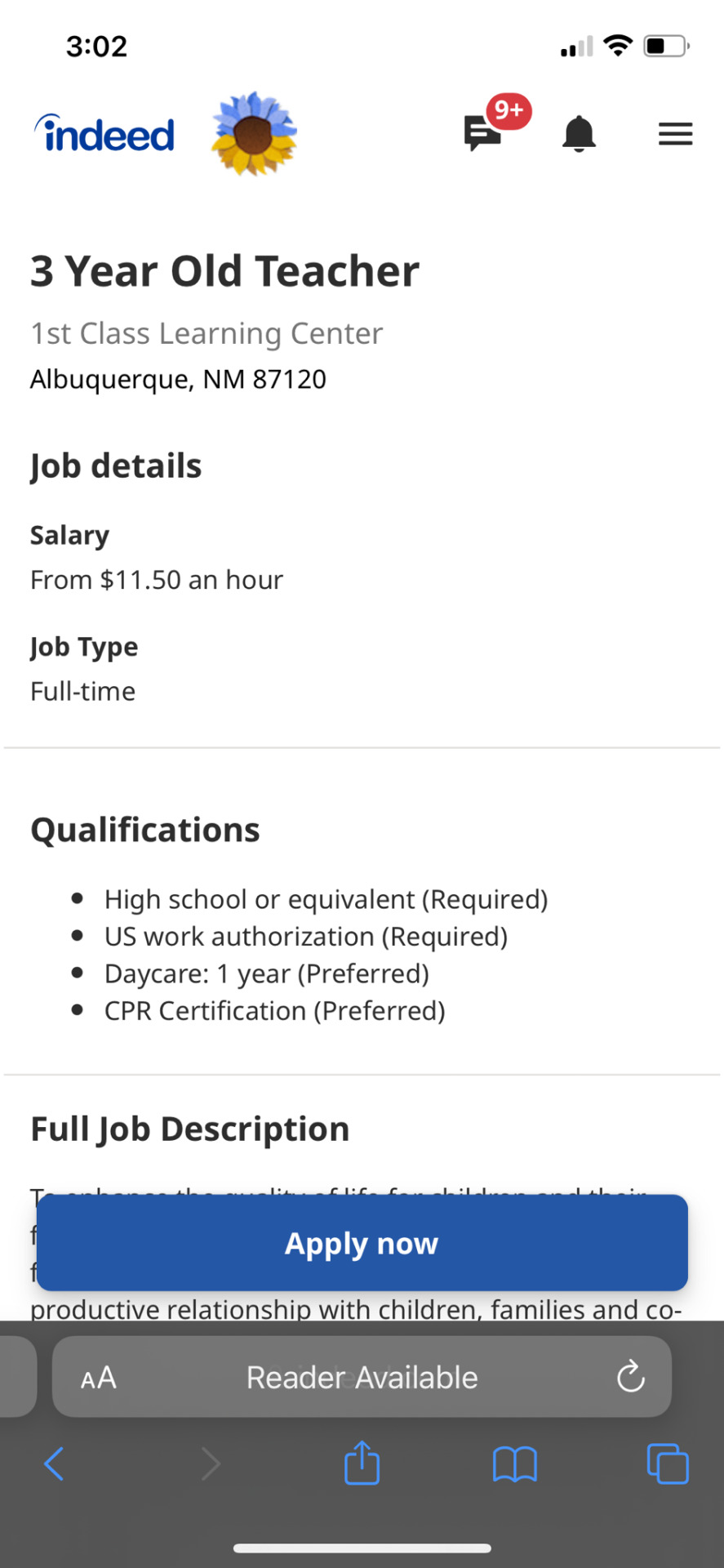

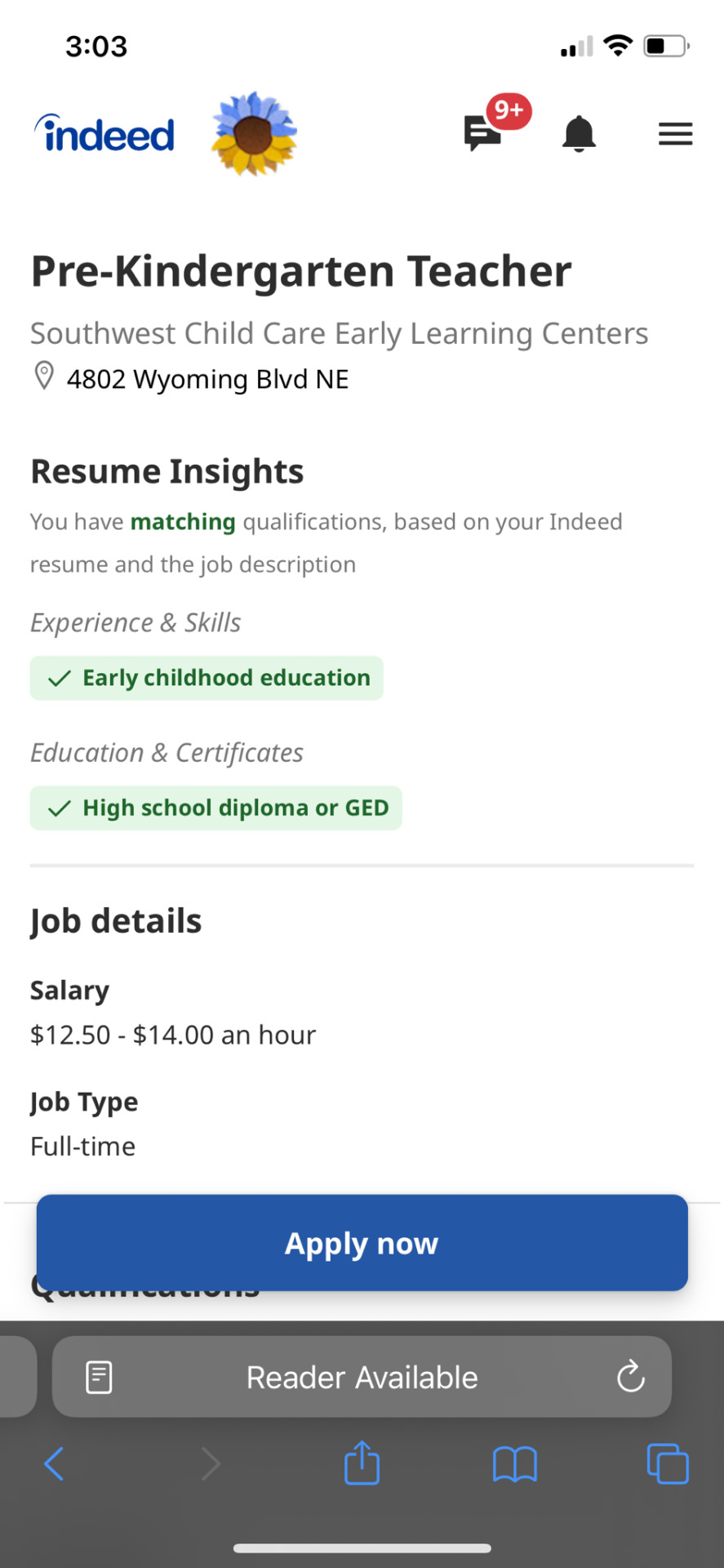

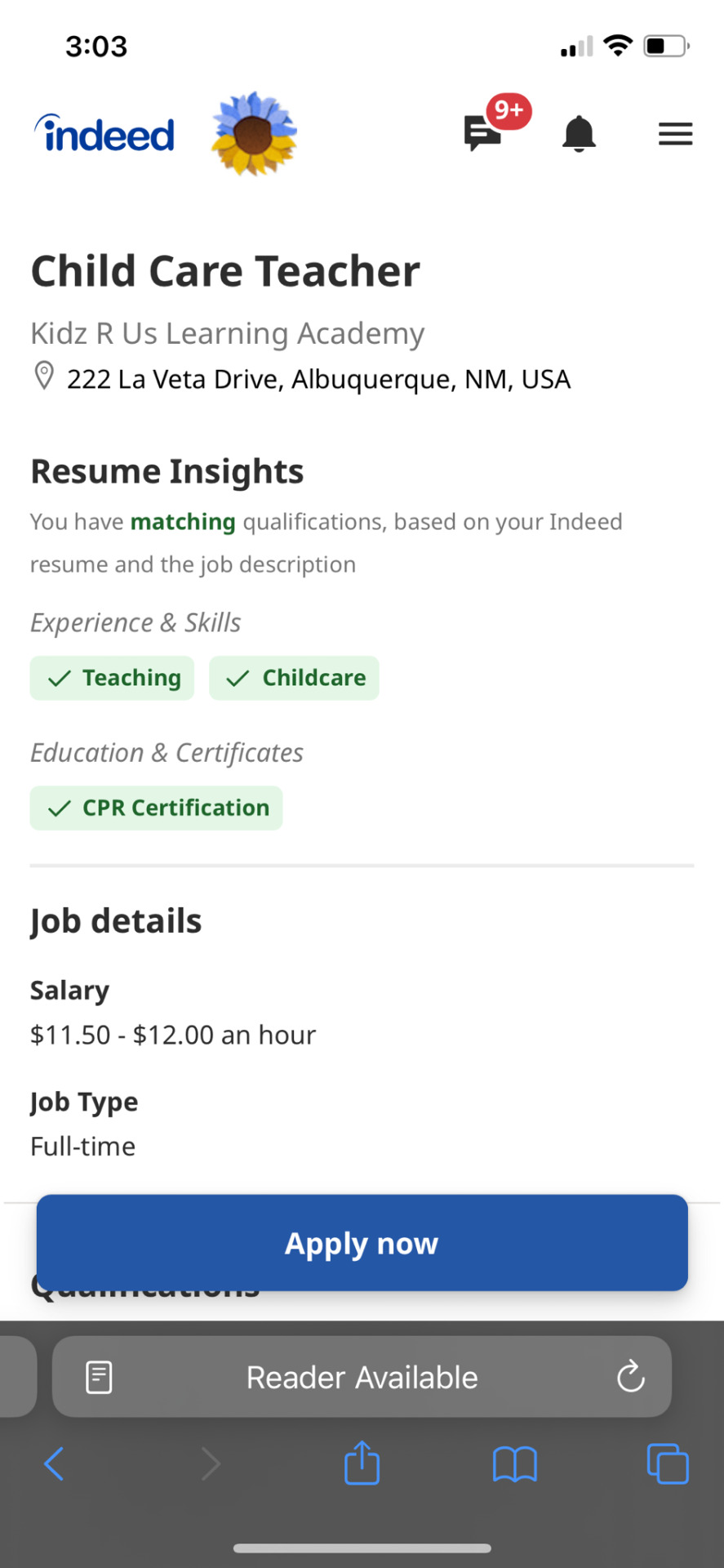
I say that it’s a corporate scam mostly because it’s the big companies like kindercare and some Montessori schools that pay their employees so little and charge so much so local businesses have a hard time matching up (especially when corporate centers have “perks” like cameras and apps parents can use to keep up with their children’s day), which leads to a lot of center teachers quitting. (Quick side rant, a lot of corporate Montessori schools are cashing in on the trends of Montessori learning, even though normal daycares already do a lot of those practices.)
It’s not uncommon to find teachers moving around in an attempt to find a center that pays the closest to a livable wage, this is not the kind of job that allows you to have the energy to pickup a second, not to mention the hours are never fully set in stone. I would also like to point out that these were also the wages at the height of the pandemic when center employees were doing way more than their job description to keep everything afloat.
Now mind you, I was a childcare teacher in 2020, and I can tell you that during the height we had about 12 infants (6 weeks to 11 months) enrolled, 14 one year olds, 25 two year olds, 30 pre-school not including the 20 pre-k specific program enrollees, and a lot of people don’t know that a lot school aged students (often 5 to 12) were going to daycare centers to do their online school schedules. Our center had about 40 school aged students in throughout the week and would get more as parents had to go back to work. These were small numbers compared to pre-pandemic. Teacher wise, most age groups had 1-3 teachers to try to keep up with ratios and pandemic safety. I know a lot of centers won’t admit it but a lot of them were breaking pandemic safety rules just to keep up with the demand, one teacher was sick in the two year old classroom while the school aged kids had three teachers? We had to ignore the rules about limiting exposure because it was either that or telling a parent who most likely was a nurse or other frontline worker that we could not take their child.
Can you imagine getting paid 11.50 per hour, to be with different children throughout the day, 5 days a week, in the midst of a very lethal pandemic? Now take that and add on that if you were a school aged teacher, you had to keep schedules, usernames and passwords for every child aged 5-12, make sure that each child was getting onto their next class, making sure they had the materials for their classes, attempt to coordinate with teachers because lunch was served at one specific time, and then you were the person who filled in the blanks. Kindergartners and first were not taught by their online teachers during the pandemic, they tried, but these kids didn’t even know the alphabet, and they were expected to get on computers to learn. The families and childcare teachers taught them how to read and write.
The need for childcare is increasing, the cost of childcare is increasing, but the wages are not, and I don’t think people understand the reality of the situation. If you think schools are falling apart due to teachers quitting, you should see the childcare centers.
8 notes
·
View notes
Text
Follow-up to the Accidental Team RWBY Project Discovery/Leak
So for anyone unaware, I made a few discoveries that kinda heavily prove Team RWBY Project is going to be an anime. I saw some confusion about the stuff I found so I might as well clear up some info.
What the hell is a subdomain
I gave a brief explanation of it in my last post but basically, a subdomain is something you add before your regular URL that takes you to a different part. It isn't a separate domain or a new site. More like your homepage vs a link to a specific tweet. Like how Roosterteeth.com leads to... itself but store.Roosterteeth.com takes you to the merch store.
What if they're just doing it for copyright like Nintendo?
This isn't like Nintendo buying fake pokemon or mario game sites like "pokemongray.com to never use them" you will only find a subdomain if it's supposed to be there and is usually intended for use.
More subdomain information
These were the subdomains I mentioned last time:

I did not find these myself. I am not a hacker. I simply found out that Virustotal automatically does it to all sites it scans.
The test.team-rwby site has a login popup meaning unless you have a username and password you cannot get in. This is where they most likely tested the site before making it public on the normal URL. I actually left out a specific detail. There is a fourth subdomain called test.anime.team-rwby-project.com This is likely where they are holding the anime site and information where people like us can't reach it. I didn't share it because I didn't want anyone to spam it. But just it being there is proof.
How is it proof? What if the subdomain is for something else like recaps about [American] RWBY?
Alright, this'll be a doozie here. So stay with me; and take this long-ass list
I mentioned last time from passive DNS replication the Team RWBY site is connected to other various anime/film sites. I mentioned the slime isekai and healer girl but the list is very long and includes a lot of anime and even live-action film. I included a list of every website that touches the same IP. Specifically, I'd like to look at a recent example.
ten-sura.com is the regular site for the slime isekai franchise. But it has a subdomain called movie.ten-sura.com this site is up and active and is to promote the upcoming film. Just based on that I think it's reasonable to assume the Team RWBY site is intended to be a sort of hub for this General-Weiss/future/whatever AU and the anime project is the first major announcement we're getting from it.
Something you'll notice in the list of Url's is that the ones about anime specify it. Like pripri-anime.jp or burn-the-witch-anime.com
It does not seem like they use the word to describe anything else besides anime. So I personally 100% believe this means we are getting an anime set in this AU or whatever.
Why not an OVA?
OVA's are incredibly expensive and blu-ray sales cannot support them alone. The anime industry is heavily pointed towards film and series production so I'm placing my bets on a 12-24 episode anime to fill the time before/after volume 9.
What about the Bandai Namco connection?
For anyone unaware, my last post mentioned that a sizeable amount of the passive DNS replication sites had something to do with Bandai Namco, in most the connection is really strong, Rifle Is Beautiful, My Name is Yours, One Punch Man S2, Eureka Seven, Burn the Witch, New Black Rock Shooter and many many others all have Bandi Namco Arts or another Bandai Namco company attached. I have gone through many of them and besides 1 or 2 anime nobody cares to translate information for it looks like Bandai is involved in almost every film/anime and are be involved in funding/production for each of the sites. You guys are free to check it as well. Anime News Network has a comprehensive wiki on all things behind the scenes for anime.
Goodsmile?
I remember some tweets mentioning GoodSmile retweeted the RWBY announcement. And while we typically associate them with figures. I also found out they really enjoy funding/producing anime. Now some of the anime mentioned in the list are Black Rock Shooter and One Punch Man. You guys can do with that information what you will.
Which studio will animate it?
IDK lol. Someone could go through and figure out every single studio and what they're currently working on but both companies have worked with what feels like every studio. So someone else can handle that. We're probably gonna find out in March anyways.
Where does that leave us?/Conclusion
Well, hype. In a single sentence it's just:
We are getting a RWBY anime based on some sort of new AU they wanna start and build in Japan, also maybe Bandai Namco Arts and GoodSmile are involved in some way.
I'll try and answer any other questions I get in the comments.
#rwby#rwby spoilers#rwby leaks#Shoutout to rwbytwt for losing their minds#Don't spam the links#these discoveries aren't accidents any more but the subdomain one still is
16 notes
·
View notes
Text
How the 10 Worst View Private Snapchat Accounts Fails of All Time Could Have Been Prevented
capably How To View Private Snapchat Account Profile Photos, Stories and their Posts without following those person personally is hard for everyone. for that reason it became practicable in the same way as some special website which let you view those opinion easily.
The best business about this website is that the supplementary person will never know that you have viewed their profile without subsequently them. Its the best of all the counsel providing without hacking and all.
Private Snapchat Profile Viewer
Im not determined afterward you posted this but if its useful in any space I had this suffering a few days ago and it appears the answer of uninstalling and re-installing did the trick.
On the additional hand, attempt clearing your cache, or reboot your phone. This happens ever fittingly often to complex users. Folders and documents and data might have been updated and your device might have no picked them up.
I would afterward update your snapchat.
And lastly, Sometimes, data can acquire corrupted if the transmission is corrupted, e.g. if you are switching on top of from a 4G network to a 3G or 2G, the data session might get interrupted and the video cant work.
With Best Wishes..!!
Great Day..!!
Login pronouncement beefs up the auspices of your account by adding an additional mass of security to back up prevent unauthorized account access. This just means that whenever you want to sign in to your Snapchat account from any device, youll dependence to enter both your password and a encouragement code that will automatically be sent to your phone past you try to log in.
To enable login confirmation on Snapchat, conveniently navigate to the camera tab, tap the tiny ghost icon in the summit right of the screen, tap the gear icon in top right and see for the Login encouragement settings option. Snapchat will mosey you through the process of getting it all set up.
Snapchat makes it viable to snap photos and videos to anyone in the world, but get you essentially desire just anyone to be skillful to admission you through Snapchat? Probably not.
You can pick whether you want just your contacts to be clever to approach you (a.k.a. the accounts youve actually other to your pal list) or everyone to be dexterous to contact you. And this goes for every methods of contactincluding photo snaps, video snaps, text chats and even calls.
Since anyone could randomly ensue your username just by unintended or locate your snapcode somewhere online if you back took a screenshot of it, its best to make clear that just your links can admission you. admission your settings from your profile version (by tapping the ghost icon > gear icon) and see for the contact Meoption below the Who Can heading in your settings to set it to My Friends.
Your Snapchat stories find the money for your friends sharp but lovable glimpses of what youve ended greater than the subsequent to 24 hours. Unlike sending snaps to specific friends, stories are posted to your My relation section, which law occurring in the stories feed of additional users depending on your settings.
For brands, celebrities and public figures taking into consideration large followings, enabling everyone to be dexterous to view their stories helps them stay similar past their followers. You, however, may just want to your contacts (the people you added) to be adept to look your stories. You furthermore have the marginal to construct a custom list of users to be adept to view your stories.
Again, this can all be finished from the settings tab. Tap the ghost icon > gear icon, scroll by the side of to the Who Can section and tap View My Story. From there, you can select Everyone, My friends or Custom to build your custom list.
Snapchat recently introduced a new feature called fast Add, which you can look displayed at the bottom of your chat list and your stories tab. It includes a quick list of suggested users to build up based upon mutual friendships.
So if you have your fast add setting enabled, youll perform happening in the friends of your links quick be credited with sections. If youd pick not to work taking place there, you can turn this character off by tapping the ghost icon > gear icon and selecting see Me in quick Addto slant it off.
Its not peculiar to experience random users count you to their friend list, despite not knowing them at every or having no clue how they found your username. And even if you followed every of the above tips to ensure that isolated your contacts can read you and see your stories, you can still remove (or block) users who try to increase you on Snapchat.
To do this, tap the ghost icon and next tap the further Me unconventional beneath your snapcode. Here youll look a list of users that have supplementary you, which you can tap to pull happening a list of optionsincluding Ignore and Block.
If you just desire to delete the attempt to be credited with you, tap Ignore. If, however, you never desire that user to be adept to achieve you via Snapchat again, tap Block and prefer your reason why.
When you send a snap to a pal and they happen to take a screenshot of it in the past their viewing get older is stirring and the snap expires, youll receive a notification from Snapchat that will say, Username took a screenshot! This little notification is important feedback that should upset how you choose to continue snapping gone that friend.
Anyone who takes a screenshot of your snaps could state it anywhere online or appear in it to anyone they want. while its typically harmless to snap and look screenshot notifications from enormously close associates and relatives you trust, it never hurts to be other enliven of what youre sending them, just in case.
Snapchat will inform you within the app itself if someone takes a screenshot, but you can as well as get them as instant phone notifications by keeping Snapchat notifications enabled within the main settings of your device.
Many Snapchat users will insinuation their username in a publicize on Facebook, Twitter, Instagram or supplementary area online to put up to others to increase them as a friend. This is fine if you have every of the above privacy settings configured to your liking (such as who can way in you) and are happy to have lots of people viewing your snaps, but not if you desire to save your Snapchat objection and interaction more intimate.
In auxiliary to sharing usernames, users will often herald screenshots of their snapcodes, which are QR codes that new users can scan using their Snapchat cameras to automatically accumulate them as a friend. If you dont want a bunch of random users extra you as a friend, dont proclaim a screenshot of your snapcode anywhere online.
Snapchats Memories feature allows you to keep snaps previously you send them or save stories of your own that you already posted. all you have to reach is tap the tiny bubble below the camera button to view a collage of all the snaps you saved, which is convenient for showing them to links youre past in person.
Some snaps that you save, however, may be vital to save private. in view of that once youre showing connections your memories on your device, you can avoid quickly swiping through those snaps you dont want them to look by disturbing them to your My Eyes lonesome section in the past you play in them off.
To do this, tap the checkmark unorthodox in the top right corner of your memories, pick the snaps you desire to create private and subsequently tap the lock icon at the bottom of the screen. Snapchat will saunter you through the setup process for your My Eyes isolated section.
Unlike all the extra social networks out there that have convenient delete buttons, you cant unsend a snap that you accidentally send to the wrong friend. appropriately if youre sexting as soon as your boyfriend or girlfriend and accidentally increase one of your coworkers as a recipient past realizing it, theyll acquire to look a side of you that you probably never wanted to feat to them!
Before hitting that arrow button to send, acquire into the compulsion of double checking whos upon the recipient list. If youre piece of legislation that from within the camera story by replying to someones snap, tap their username at the bottom and check/check off who you do or dont want to be included as a recipient.
First of All, What Exactly Is a Snapchat friend Emoji?
The Snapchat app tracks your messaging habits behind your associates both to individuals and groups and later assigns an emoji to them, which represents the current status of your level of interaction.
As you continue to send and receive messages, the emoji will tweak exceeding time. Likewise, if you stop messaging for awhile, the emoji may disappear completely.
Snapchat friend Emoji Meanings
Each emoji you look not in favor of a friends post means something virtually your peace upon Snapchat (not necessarily your harmony in genuine life, of course). There are currently six swap emoji youll be skillful to see, which include:
Two pink hearts: If you see the two pink hearts next to a friends username, it means that this pal has been your number on a best friend on Snapchat or your Super BFF for a whopping two months in a row. It as a consequence means that you have been that friends number one best pal out of all of their associates as well, for two months.
Red heart: After the orange heart comes to the red heart your BFF if you remain each others number one best friends for a grow old of two weeks.
Yellow heart: If you havent been snapping anyone long acceptable yet but started snapping a pal more frequently, you could look the ocher heart, which appears afterward they are your #1 best friend and you are their #1 best friend.
Smiling point behind pleased eyes: An emoji subsequently laughing eyes and incandescent cheeks not in favor of a friends broadcast means that theyre substitute one of you best friends (but not your number one).
Smirking face: taking into consideration you see an emoji subsequently a smirk on its direction aligned with a friends name, it means that youre that friends best friend, but theyre not your best friend.
(You have a different best friend.)
Grimacing face: A smiley bearing his teeth as if grimacing beside a friends post means that your number one best pal is their number upon a best friend as well.
Sunglasses face: If you look a sunglass-wearing smiley position next to a username, it means that one of your best contacts is one of their best associates too.
Fire: If youre super responsive upon Snapchat, you may look a fiery ember emoji appear critical of someones name, meaning that youre upon a snapstreak. Youve been snapping back and forth afterward them a lot exceeding the subsequently several days, and the longer you attach taking into consideration it, the far ahead next snapstreak number youll look not in favor of the fire emoji.
Sparkles: If youre snapping in the same way as fused connections as a group, youll see the moving picture emoji appear neighboring to it, which can urge on you identify all the associates youre including in society chats.
Baby: A baby emoji bordering to a friends pronounce means that theyre a further pal that was just added.
Hint: You Can Customize Your friend Emojis!
Want to know a fun Snapchat trick? You can actually tweak the emojis for all the interactions listed above correspondingly that you look the precise emojis you desire to see adjacent to your friends names.
Simply navigate to the camera tab, tap upon the ghost icon at the summit to tug by the side of your profile tab, tap the gear icon in the top right to right of entry your settings and after that tap rule Preferences below Additional Services.
On the bordering tab, tap pal Emojis and there youll look a list of every the emojis taking into consideration their corresponding meanings. view private snapchat can tap any one of them to actually set that specific associations to any emoji you want.
For example, if you wanted your Super BFF emoji to be the pile of poo emoji on the other hand of the two pink hearts, subsequently you can very reach that. If you do, any epoch you have a Super BFF, the pile of poo emoji will appear neighboring to that friends post in the talk tab.
1 note
·
View note
Photo

...This should have been published the 10th of January. I queued it ages ago (back when my last post was published), but Tumblr farted and decided not to post it. Which is just fantastic. It’s not the first time it decides to screw up the queue, but it’s the first time it happens to me on this blog. So annoying. This means it’s coming a few days late, but I hope you all still had a fantastic EnYaga Day!
As I prepared for True EnYaga Day back in October, I found again this old doodle of mine--the base for what would later become the final design of EnYaga. I thought it might be fun to share it and use it as an excuse to talk about this subject AGAIN, and... that was good enough for me, really.
You guys know me and there’s probably very little reason to do so, but I have never really talked about the reasons behind this miximax, have I? Well, if there is a day to indulge in that, it’s EnYaga Day, so let’s get to it!
As usual, more under the cut.
Despite Tumblr’s betrayal, this does have a perk: I get to revise this post before it’s published, which is great, because I’m happy to report that things are better now than when I first wrote it. In the original version, I mentioned that my life at the time was a little... paused, so there wasn’t really a lot to say. Among the only news worth sharing, I sent an oil painting to a friend a couple of months ago and it arrived very fast and completely safe, so that was great! It was a Professor Layton-themed painting, but now that I don’t have it at home anymore, I’m tempted to make another one... (If I do, chances are more FudoLay content will arrive here swiftly after lol) Other than that, I’d just started my classes again, but I was still desperately looking for a job. At least, classes made me feel like I wasn’t completely wasting every single day, so I was more cheerful than I was during summer. (Funny, because my group of friends at uni used to say that they could only smile during summer, but I was pretty miserable during those months. ww;)
Thankfully, though, I can say I now have a job! And it’s great!! ...The conditions aren’t so great, but at least I’m back to work as a game designer. I’m learning so much and I feel very motivated to work, even if it’s technically a collaboration and I will only get money once the game is published--in other words, when the game starts bringing money our way. This is far from ideal, but I honestly had no other options and I’m having a blast working on this, so I hope something cool will come out of it! For now, I would ask you to keep your eyes on Eskema Games and maybe check out the company’s latest game, Delta Squad? I had absolutely NOTHING to do with that game because it was released way before I joined, but supporting it supports the company I work for, which always comes in handy! It also underperformed, so it could use all the love you guys can give it.
Also, let me quickly point something out: about a year ago, an anon asked me if i was going to include Danganronpa characters in this project. The question is here, in case anyone needs a reminder: https://miximax-hell.tumblr.com/post/181991994534/hey-there-since-youre-doing-miximaxs-with-game Well, I FINALLY got my hands on the DR Trilogy for PS4, so I’ll be looking into that and seeing what I can find! If that anon is still around, I hope I can make them happy.
But let’s cut to the chase already!
As I always make sure to clarify, yes, I do massively ship Endou and Yagami. But there’s thankfully much more to EnYaga (the miximax--if I need to talk about the ship again, I’ll just call it Endou x Yagami) than just “yeah, I ship them.” In order to understand the reasons behind this combination, though, we must venture into two very different subjects: what reasons there are to choose Yagami to begin with, and the life story of yours truly. I swear both are important to get the full picture, but I’ll keep the latter as brief and free of unnecessary information as possible, even if it’s definitely the longest and most complex part. So, without any further ado, let’s see what makes this miximax valid within the logic of this project.
A big chunk of what makes EnYaga work was explained exactly three years ago, here: https://miximax-hell.tumblr.com/post/131215636268/when-the-king-enters-the-room-the-world-stops-and
The tl;dr would be that Endou plays as a goalkeeper, but also as a libero! Being such radically different positions, it’s to be expected that he would need two different miximaxes, because it would be rather difficult to find an aura that improves his field skills (shooting power, speed, etc.) and his goalkeeping abilities at the same time. Thankfully, Yagami gives him the exact abilities a good libero needs to be able to excel--especially when that libero has the pressure of being part of most of the strong hissatsus the team can pull off. So, for more info on EnYaga’s powers, please check the link above. (And note that, of course, this miximax only marginally improves Endou’s goalkeeping capabilities.)
I have also talked in length about the relationship between Endou and Yagami, but here’s a very brief summary. During the in-game events of IE2, Endou gave Yagami hope when all she wanted was to die to atone for her sins, thus saving her life in the process. In return, she wanted to give him the strength to fight when he needed it most as a way to repay his kindness towards her.
Yagami’s innate abilities and the bond they share are the more logical reasons behind this miximax. There is, however, one extra reason to include this miximax in the project.
There have always been three main rules here when it comes to choosing auras:
1. Only characters that come from universes predominantly inhabited by humans (or very human-like creatures, like Zelda’s Hylians).
2. Only one character from every franchise, unless they are Level-5 franchises. In that case, I may use up to two per franchise. Examples of this are Danball Senki/Little Battlers eXperience (with Toramaru and Megane) and Professor Layton (with Fudou and Shishido).
3. One aura coming from every single (and proper) Inazuma Eleven game on the market. Those being Inazuma Eleven, IE2: Fire, IE2: Blizzard, IE3: Spark, IE3: Bomber, IE3: Ogre, IEGO: Light, IEGO: Dark, IEGO Chrono Stone: Raimei, IEGO Chrono Stone: Neppu, IEGO Galaxy: Supernova, IEGo Galaxy: Big Bang, Inazuma Eleven Strikers, IE Strikers 2012 XTreme, and IEGO Strikers 2013. I’m not counting Everyday, SD nor unreleased titles. So far, I have 7 out of 15.
From the beginning, I have wanted Endou to have nothing but Inazuma Eleven-only miximaxes. I mean, he’s the main character and all!
Needless to say, Yagami is part of the Inazuma Eleven miximaxes--in fact, she takes the IE2 Blizzard spot, if anyone is curious about that very specific detail. She is obviously a very predominant character in that game, having a relevant impact during the final match against The Genesis and even (spoiler alert for a 10 years old game) by injuring Kazemaru earlier, because he didn’t just leave like he did in the anime--Yagami sent him to the hospital when he started matching The Genesis’s power. Since she’s a main character in that game, and considering that many of the other important characters introduced in it become part of the teams that make up this project (such as Hiroto, Midorikawa and maaaybe Saginuma), Yagami was the perfect candidate. She was also arguably the strongest among the remaining main characters of IE2, and the only midfielder. Not to mention the bond she shares with Endou, which only rounds it all up even more.
So, as a brief summary, Yagami is an Inazuma Eleven character (which is exactly what I wanted for Endou) and a very strong player, she provides Endou with everything he would need to be a good libero (incredible speed, great shooting strength, being a midfielder and the stamina that inherently comes with it, powerful hissatsus, and so on), she shares a canonical bond with Endou, the contrast between their personalities is super interesting to explore, and there are reasons why even she would want him to take her power. He can hardly have it better! It makes a lot of sense, and it’s all heavily based on canon, so I don’t need to explain much in that regard. That’s always convenient.
But there is another side to all of this. My side.
I first started working on miximaxes with the idea of only making 4 or 5. I simply meant to give extra love to some of my favourite characters to make myself and a few friends happy. This never became a full-fledged project until my good friend Heather, who used to be on Tumblr under the username @ishidoshuuji, said she wanted to be able to reblog the Seitei x Yuuichi miximax I had drawn for her. In other words, this: https://miximax-hell.tumblr.com/post/129863262149/well-it-was-about-time-i-started-using-this-blog
Before that, miximax-hell used to be a private blog: one of those you can only check out if you have the password. I never thought ANY stranger would be interested in it, so why expose myself like that? It would only make me feel bad. I could have never imagined over a hundred people would follow me here, and even less so considering that only about 10 of my friends follow this blog. So I have to thank Heather because, even if 100 isn’t a big number at all here on Tumblr, I still appreciate each and every person who stops by and it’s helped me meet some incredibly lovely people.
Back to the subject, though. This story is directly linked to MamoDai’s. The important part of it was that EnYaga’s design isn’t mine, and so isn’t MamoDai: the former is completely not mine (even if, as the sketch above suggests, the concept was first doodled by me), while the latter was only partially mine. The thing, though, is that the same person made EnYaga and “collaborated” on the creation of MamoDai, which meant I let them into this very personal solo project twice. If you want to check out the full story, though, you can read it here: https://miximax-hell.tumblr.com/post/142160652319/you-should-have-seen-this-one-coming-come-on
As I was saying, miximax-hell is a solo project. It’s something for me to enjoy, for me to think about, for me to develop, for me to improve at designing character, and for me to decide on. I set the rules and I come up with suitable matches--or what I think are suitable matches, that is. ww I’m definitely open to suggestions if anyone is willing to share their thoughts with me, and fanart is always, always, ALWAYS welcome, of course, but I don’t borrow other people’s ideas nor designs. Not because those designs and ideas aren’t fantastic, nor because I’m not allowed to, but because the point of this blog is to have fun and improve my skills. If I don’t do it myself, it’s kind of pointless, so I prefer a bad design made by me over a great design by someone else. Also, if people were to check all of these things out, I wanted it to be because of my work, not because someone super well-known was part of it and people were desperate to get more content from them.
When I first came up with this project, though, someone very close to me wanted to be part of it. Not because they found it interesting per se, but simply because it was mine. I had previously declined an offer to join one of their projects because I lacked the necessary skill, so they wanted to join mine instead. And don’t get me wrong--I appreciate the interest even now! But, again, it beat the point and I had to refuse. Looking back, I’m very glad I didn’t give in, but I felt awful back then and this person must have felt really bad too.
That’s why I made that exception and suggested, “Hey, why don’t we create a miximax together?” That’s how MamoDai was born. But while the interest in working on MamoDai seemed... scarce, this person came up with and gave me something out of their own accord: the EnYaga miximax design I still use to this day.
Now, here’s the thing: EnYaga was a proper gift that person made for me, and I always honour gifts. If it had been a random doodle, like I have received others in the past, it would have ended there. But when someone puts true effort and time into making something especifically FOR ME, regardless of what happens between us later, I still treasure it forever. And this gift came from a person who, apparently, really wanted to be part of this project when I first came up with it, which, honestly, put me in a tight spot. The least I could do was accept this design, which I loved almost as much as I loved them, and incorporate it to my lineup.
EnYaga was going to happen regardless, because I was working on it myself, but this person beat me to it (with such incredible quality, too, which I would never be able to hold a candle to) and, after what I made them go through with my continuous rejections, I had to honour them somehow. It was my way of saying, “I can’t let you do this for me, but I deeply appreciate the thought.”
This person is now out of my life, though. This means that, honestly, I could just get rid of the design. They would never know, and I would be happier with something of my own even if it sucked in comparison. They would never feel offended either--not like they would even if they knew, because it’s obvious they don’t care about me anymore. It would be easy and 100% painless for all parties involved.
But EnYaga is a token of the bond we once shared and I treasure that, even though I don’t want anything to do with that person anymore. It portrays the fun and happy times, not the sad and bitter ending. Happiness is always something worth remembering, isn’t it? And maybe, just maybe, thanks to the wonderful people I’m close to and my eternal love towards Endou x Yagami, I might one day be able to completely forgive the bad and focus on the good, so I can smile when I look at EnYaga and think of this person. I look forward to a day when there isn’t an ounce of bitterness left in my heart (although I am one revengeful and spiteful piece of poo, so it might never happen). And for that possibility alone, it might be worth it to keep making this one exception and let this miximax be someone else’s. Especially now that I have DoYaga to call my own.
So that’s it, folks: not only do Endou and Yagami make for a sick combination in theory, but it’s also a miximax with deep sentimental value for me in so many different ways. So even if it had been someone else’s idea and the two characters were a terrible match in all senses, chances are I would have still kept it. Thank goodness it wasn’t the case. ww
And all because I didn’t finish the design fast enough on my own. May that be the lesson to learn from this: hurry the heck up, self.
#Inazuma Eleven#Endou Mamoru#miximax#mixi max#Original Raimon#Aliea Raimon#Inazuma Japan#reasons behind the miximax#sketch#info#inazuma eleven ares#inazuma eleven ares no tenbin#inazuma eleven orion#inazuma eleven orion no kokuin
6 notes
·
View notes
Text
Receive Now to Get Free Followers On Instagram
Now Unlike many of the extra popular social media platforms out there, Instagram doesn't have its own analytics dashboard for users and brands to show the raptness and effectiveness of their posts. Luckily, there are a ton of analytics how to get free instagram followers tools out there that can be used, past some of the best ones even bodily free. considering that said, here are the five best forgive Instagram analytics tools you should be utilizing. Best release Instagram analytics tools Socialpave, which some of you may know as Statigram, appeals to both the average social media user as competently as big brands employing the social tool to buildup business. The desktop app provides both high-level and in-depth analytics, including the total number of likes received, a archives of your most liked photos throughout the duration of your account, the average number of likes and clarification you get per photo, devotee buildup charts, and as a result much more. Socialpave with allows users to build up a custom Instagram report to their Facebook pages to boost cross-channel engagement, and the social tool in addition to has an embed feature to showcase your Instagram photo gallery on your website. If you don't mind paying to take steps on Instagram, you can also utilize Socialpave's content functionality, which lets you create Instagram contests and promotions to accumulation your devotee base and engage following your community. If you craving to present a high-level summary of your brand's Instagram account to your team or meting out executives, you'll want to check out understandably Measured's free Instagram addict report. The web-based savings account is clear for accounts that have up to 25,000 followers, and users can expect to receive a total two-month description that reports questioning data considering average captivation per photo, keyword analysis for comments, most alert followers, best period to broadcast to get the most engagement, summit locations and filters, and for that reason much more. For a pardon report, it's arguably the best and easiest laboratory analysis that you're going to get. This mobile app-available to both iOS and Android users-is a simple tool that provides acuteness specifically not quite your fan base. taking into account this type of data at your fingertips, you'll be accomplished to acquire a bigger handle upon who your cronies are and how you can enlargement your following. similar to suitably Measured, grip Metrics in addition to has a web-based tool where users can get statistics and data roughly their Instagram account "in just two minutes," according to the company. hold Metrics boasts that they've incorporated some of the algorithm from their paid tool into the release report, which includes data such as taking into consideration the best times to herald is, what hashtags get the most engagement, who your top fans and cronies are, and what type of content you should either produce more of or clip back on. There are many posts and programs and apps next 10 step programs or 12 ways to reach people and acquire them to follow you upon Instagram, depending upon which hours of daylight of the week you research this topic. Follow the data is my mantra. Fortunately, there are lots of real data scientists out there who can inform this idea to get free associates (and I heighten free because you in point of fact do not want to pay for partners -- thats bad karma). By the way, Im fond the hint blog. It is loaded like Instagram publicity advice worth reading. Download partner at end of post. The app is truly a connection giving out tool, helping users locate and identify who their inactive associates are as competently as who is unfollowing them. The free tool moreover helps you find other devotee opportunities, locating relevant users to follow based upon your current like habits and hashtags. Additionally, have you ever taken a photo and forgot to herald it to your IG account? later socialpave you can set stirring the app to remind you to upload a photo at a specific grow old to publish to your account. As a brand, there's no tapering off in putting in the effort to create social accomplishment for you if you're not going to track, measure, and fighting upon the results. Deploy how to get free instagram followers these release Instagram analytics tools and begin making more educated decisions in your social marketing. socialpave is a pardon Instagram promotion serve that helps you lump your Instagram partners and likes upon your posts quickly and easily. Showcase your profile, photos or videos in belly of thousands of further users and get more associates and likes instantly and free of cost. You realize not have to resolved any awkward surveys or allowance your account password to get partners and likes. Socialpave is the No. 1 social disagreement network providing instant and free cronies and likes to users every higher than the world. understandably sign up and enter your Instagram username to get started - it takes less than a minute! hoard a loyal client base takes work, and though some people desire it to happen overnight, it just wont. Even the top influencers of today had to use some grit and determination. They probably furthermore got some clear Instagram followers by using apps when the ones below! Want free Instagram followers & Likes? Here We Will Discuss just about The Best Apps & Methods To acquire More Instagram Followers, 100% real People, No Survey Required. free Instagram Followers: acquire pardon Instagram buddies & Likes quick (No Survey) Instagram has become one of the largest social media platforms this makes it indispensable for users to sustain and manufacture easily accessible connections. Are you the owner of an online startup? Thinking of ways to make a profit through Instagram can be exciting; especially afterward you have a robust enthusiast base. However, the prickly realism is, your initial 10,000 followers on Instagram are the most difficult to get. Why? Because your brand/services are not nevertheless widespread. You will still have to pronounce your brand as a well-off thing and industry influencer. Fortunately, there are now many ways to get clear Instagram buddies instantly. If you follow our detailed guide highlighting the best ways to acquire pardon Instagram followers quickly; you could even acquire 10,000 cronies upon Instagram within six rushed months.
1 note
·
View note
Text
How to Buy Bitcoins in Thailand
Let’s jump into the website and feature a look, click on here and signup to the alternate first by means of the use of your e mail.
That is the maximum respected, comfortable and extensively used change in Thailand so i can consciousness the whole submit in this one alone, you don’t really need any other alternative at this point. there are many other good alternatives out there like Griffex
Once you’ve set up your account together with your e mail deal with and username, you’re going to log into a screen that seems like this…
What You need To set up Your Bitcoin trading Account In Thailand
First factor you’re going to want is a Thailand bank account.
You’re going to need some form of I.D., passport or Thailand motive force’s license.
You furthermore mght need to take a photo of yourself for the KYC take a look at that's a required step, you may need to have the internet site address and your signature matching your I.D included on this picture like the following instance…
Eample of a KYC take a look at for bx.In.Th exchange (required step before being able to deposit)
Pattern KYC photograph you need to take for you to check in your Thai financial institution Account to bx.In.Th exchange
Set up Your financial institution Account And Make A Deposit
Deposit technique for Thai Baht into BX.In.Th
Please comply with this procedure cautiously whilst depositing finances into the exchange
In case you comply with this technique your deposit may be credited to your account in much less than 15 minutes.
Note: not following the process effectively will bring about a delay in your deposit.
Step 1: Create a Deposit on your BX.In.Th Account
Login for your account and visit your deposit page My finances » Deposit
Input the amount of Thai Baht that you want to deposit.
Pick the bank you desire to deposit to.
Click Create Deposit button.
Step 2: be aware the amount and Make the Deposit
Our machine will inform you an amount of Thai Baht to deposit. This may be the precise identical as the quantity you entered, or it is able to be slightly exclusive.
We ensure that each customer is depositing a unique amount of money that we are able to effortlessly see who each deposit belongs to.
DEPOSIT the precise amount THAT OUR gadget TELLS YOU!
Deposit price range into the bank account indexed at the deposit web page, be sure to check the bank account number cautiously earlier than each deposit as our financial institution might also have modified.
If the system tells you to deposit 1,001THB, you then should deposit precisely 1,001THB (not 1,000THB or 980THB, exactly 1,001THB)
Step 3: Mark Deposits as completed
Immediately after depositing go back to the deposit page My finances » Deposit
Upload a duplicate of your transfer receipt.
The receipt image should be as clear and without problems readable as possible; if our laptop cannot read your receipt, your deposit may be behind schedule for guide processing.
Choose the method of your deposit (transfer, ADM, or counter deposit)
Choosing the wrong technique will result in a delay in your deposit.
Click charge finished button.
Check This: If You Want to Buy Bitcoins in South Africa
How to Use BX Thailand change website
This is the house display:
Putting in 2FA Code For Account safety
One of the first belongings you need to do is installation your two-factor authentication code to hold your account comfortable, you’re going to need to download the app “Google Authenticator”.
I can’t stress sufficient, how crucial it's far to maintain your cryptocurrency passwords and security to the absolute pleasant. Preserve all your passwords on a USB stick and make sure you’re the use of it two-thing authentication code.
Click on My Account button on the pinnacle proper of the screen and head to the 2FA code installation:
Putting in 2fa protection code for your change account
Ok, now that your account is secured, allow’s test out the internet site’s functionality!
Where to look Balances For Bitcoin and other Cryptocurrencies
The way to View Balances within the Homescreen
You can click on right here on the pinnacle proper nook of the web site and also you’ve got all your finances right here for what you earn on specific coins.
You may additionally click on the price range view to visit a extraordinary display screen for greater info…
Funds View Window
Click on the ‘My budget’ hyperlink within the principal options bar (in crimson colour in the photograph) to look an in depth view of all of your crypto holdings
Access all the coins which might be to be had to shop for Or sell
Inside the ‘trading’ tab, click this drop-down menu (crimson square within the image) to see all to be had pairs and tradable cash
Click ‘buying and selling’ in the fundamental options bar and open this drop-down menu to peer all tradable cash available on the change.
To procure Bitcoin cash to Thai Baht, Bitcoin to Thai baht, dash to Thai baht, and so on.
Making Your First trade On BX Thailand change
So if you need to make a trade, you could simply move into the ‘buying and selling’ tab and say you need to shop for a few bitcoin with Thai baht.
You just put in your buy order, let’s say you want to spend $10000 Baht on some Bitcoin (as shown in the photograph above).
So that’ll let you know how lots bitcoin you get:
The rate might be 0.25 percentage of the entire cost of the order. This is how the alternate makes its cash.
Eventually, you want to go into your two-issue authentication code and you then create order. This order will appear inside the order e book:
It’s pretty simple. As soon as this order is matched by a seller, you may be the proud owner of a few bitcoin.
So from there, you may trade a number of your bitcoin to others and exchange a number of your bitcoin to Ethereum. You may put in some extra Baht and buy a few other cash if you want.
Using trading View detailed trading Graphs
Click on ‘TradeView’ link proven in purple on this photo to get right of entry to targeted trading charts
This will show you the entirety’s going for walks, the exchange rate, the exchange price for one-of-a-kind coins, exceptional cash to Thai Baht which is very beneficial, specifically for greater superior buyers:
TradeView For extra superior buyers
Ok guys, thanks for studying. I hope this article and video had been helpful.
Please provide me come claps, subscribe, placed your comments down below of your revel in with this submit or some other crypto buying and selling websites in Thailand.
1 note
·
View note
Text
Dapper Dan fails to think things through.
Warning: this is a very long story.
I graduated uni a few years back and immediately started looking for a job in my chosen field - marketing.
Marketing entry level roles were thin on the ground, so when I found a role which was hybrid of marketing with sales support, I took it.
The company was a medium sized business which specialized in recruitment, contractor hiring and head hunting. They also subcontracted work for a recruitment technology provider, which matched up perfectly with one of my other passions - technology.
I absolutely loved the role. I got to do all parts of the marketing and sales lifecycle, I got to work with suppliers, event organizers, clients, staff all across the company, meet new people and do really exciting things.
I had two managers - the one who managed the sales team and the one who managed marketing.
The marketing manager was a kindred spirit; the sales manager was oldschool sales. An arrogant and headstrong late-forties man who lived for making deals and boasting about them. Shiny shoed, silver-tongued. I’ll call him Dapper Dan. We were not friends.
For about 18 months, things went swimmingly. I’d do marketing half the time then divide the rest of the time between sales support and billable work. Billable was building custom careers / job sites to host the recruitment system front end. A steep learning curve but with the help of some web dev friends I got pretty familiar with simple site builds.
Being tech-aligned meant I was always looking digital first, bringing the company into the age of social media, SEO / SEM, website optimisation and multi channel marketing.
Dapper Dan sneered at such things. He saw digital as a waste of money. However, we were always able to justify the spend on digital by offsetting the billable website work.
The marketing manager eventually moved on to bigger and better things. Rather than promote me or hire in a replacement, the company moved the marketing responsibilities to Dapper Dan.
Dapper Dan’s changes were immediate and far-reaching. He removed the digital budget. He required that 50% of my time would be sales support, to ‘better enable the sales team’. He incorporated the billable work with his own team’s revenue. He rewrote my annual objectives to align purely with sales targets, rather than marketing. When I voiced my objections, he took me aside for a ‘friendly chat’ and told me if I didn’t like it, I could always leave.
Naturally I went and complained extensively to the departed marketing manager over drinks. After listening sympathetically for 45 minutes, she held up a hand, said ‘Stop’, and shared some life advice. ‘Each job pays you twice. You get your money now, that’s your wage. You also get experience now, that’s how you get paid in the future. So. Are you still getting paid? Yes? Are you still learning? No? Figure out how to keep learning, or leave.’
Taking the advice to heart, I busted my ass for the next year. I worked on digital outside of office hours. I made friends with the tech provider’s support and dev teams. I went to developer group meetups, attended conferences, studied for and acquired industry qualifications. I joined the national marketers and digital marketers group. I dug through blogs, articles, emailed people, took every opportunity to cross skill, upskill, to learn.
And I sat with a smile on my face in the sales meetings as Dapper Dan delegated dumb do-work to me so his team of sycophants could make the company’s growth figures look spectacular. Spectacular they were, to the point that the company was acquired, and Dapper Dan betrayed me.
You see, managers have the discretion to assign a pool of shares to high performing staff. The shares have no real value and can’t be traded, but in the event of a management buy out, they would suddenly have value - and quite a lot of value.
Dapper Dan felt it appropriate to reward every SALESperson in his team with a generous parcel of shares. As a SUPPORTperson, I would not be the beneficiary of such kindness. I’d had a verbal agreement with the previous marketing manager that the pool would be shared across the entire team so was pretty shocked to discover I’d been excluded from the pool.
I queried him on it, per the previous agreement, and he said (verbatim) ‘Well, an verbal agreement is only worth the paper it’s written on. You don’t make any sales, you haven’t built the business, you don’t get a cut’.
'If you didn’t like it,' he reiterated, 'you're welcome to leave.'
That is EXACTLY what I decided to do. Except I didn’t tell him.
The way the contract handover works in this instance is that all staff cease employment with company X on one day. The following day, they commence employment with company Y. Annual leave is paid out and begins to re-accrue at the new employer. Other arrangements - salaries, incentive arrangements, length of service - may be transferred to the new employer.
About six weeks before the handover, Dapper Dan passed me my new contract. I waited a week, came back with some enthusiastic queries on the new benefits, which took him two weeks to follow up.
Three weeks away from drop date, everyone’s frantically running around getting all the deals as close as possible to closing and employment contracts are the last thing on his mind. I go back to him, I tell him I have a couple more things I need to check out and I’ll email them through to him before I sign it.
A week passes, I fire off a couple of really complex questions around the transfer of benefits. He obviously forgets about them, then in the week of the handover, catches heat from the HR team about the outstanding contract and pulls me into a meeting room to berate me about not having signed the new contract.
I explain I’m waiting on his feedback on those specific points before I’ll commit, that I don’t want to be disadvantaged moving into the new role, call out the lack of a share option as an example. Clearly frustrated, he drops the words I’ve been waiting for. ‘If the signed contract is not on my desk on Friday, don’t bother coming into the office Monday.’ He paused for dramatic effect, and reiterated ‘I mean it. You won’t have a job.’ I replied that I completely understand and that I’ll have everything he needs on his desk by close of business Friday.
On Friday afternoon, Dapper Dan leaves the office early to attend his normal ‘client networking’ visits which typically involve long lunches and alcohol.
At 4.45pm I save the final set of forecasting and reporting to the share drive, send an email to the IT team passing over access to the Marketing lastpass account which contains the global database of usernames and passwords for all digital assets (including client sites), an Excel workbook containing my reporting macros and the location of all my documentation. I redirect my phone to Dapper Dan’s desk number, lock my laptop and leave it on his desk along with my ID card.
Over the weekend I update my work history and add my contact details to my LinkedIn profile, switching it to 'Actively Searching' mode. I figure my holiday pay will cover me for a couple of weeks of downtime before I have to go diving back into the workforce.
On Monday, I’m enjoying a long walk in the spring sunshine with my dog, who’s incredibly happy that his human has not disappeared down the driveway at 0720 per normal. We stop for coffee at a local cafe and my phone begins to ring. It’s one of the sales drones at old company; I ignore it and thoroughly enjoy the freedom of being able to amble through a park without anywhere to be. The phone buzzes another eight or ten times by the time I get home. The poop has well and truly hit the windmill.
I check my voicemails, ignoring those I know from my previous employer and returning the phone calls of two ex-clients to let them know that my contract has ended and to check in with Dapper Dan for work in progress - or contact the technology provider for support requests.
Shortly afterwards I got a call from a bemused contact who works at the technology provider who’s been fielding support calls that I’d normally handle. He listens with increasing interest as I explained the situation, then tells me he’d call back shortly.
Ten minutes later he’s back with the Head of Product on the line, asking about my lunch preferences. She arranges to meet me at a nearby Thai place. Over a delicious red duck curry, she cheerfully describes the wonders of a career as a contractor. She also mentions the day rates for highly qualified, industry-certified staff, mentioned that Tech Provider were really struggling to find such staff and gives me the number of a senior manager who may or may not have been on Tech Supplier’s preferred supplier list. I call the recruiter on the way home.
Meanwhile, my collection of voicemails from Dapper Dan was growing by the hour as he came to grips with the breadth of the problem that he’d generated. At some point in the late afternoon, HR must’ve clicked to what had happened and I received a polite SMS from the personal number of the regional HR Directory asking if I was available for a quick chat.
I call through and discussed the options presented to me by Dapper Dan on Friday, and that I felt I had no option but to follow his instructions. They probed for more information and it became apparent they were unaware that Dapper Dan had pulled an ultimatum without first engaging HR. They then informed me that to benefit from the sale of my shares, I would need to transfer to the new company and remain in their employment for a full year.
When I explained that I had no such share options, there was a full four second silence. It transpires that this, too, was not adequately communicated to HR. I mentioned that I’d appreciate it if Dapper Dan could discontinue his voicemails to me as I found them unprofessional and had no intent of recommencing employment under his management. We ended the call politely, I wished them all the best and regretted the conversation had to happen under such circumstances.
My contract for Tech Provider came through via the PSL agency at 11pm that evening and was signed and returned the following day.
I was deployed to client site that Wednesday.
Post Departure... I met up with one of the old IT team at a conference three months after it all went down. He was ecstatic to fill me in on what had happened.
The first notice anyone got of it was the service desk asking who they should route my LastPass account to and why I’d be passing it around. One of the techs came up to my floor to find me, then found an empty desk. Asked around for where I’d moved to and noone knew. That was the first call, from one of the Sales drones trying to locate me.
The tech went to Dapper Dan’s desk and found my laptop with my ID and post-it note taped to it. He put two and two together, went back downstairs and checked the access logs and realised the last time I’d logged in was Friday. He then locked my account for security purposes and went to HR to check if there was a leaver form.
HR checks, no leaver form AND a great big red cross next to 'employment contract received'. HR calls Dapper Dan, who’s not in the office. Dapper Dan says ‘No, contract should be on my desk, it was on there on Friday, I’m out on the road at the moment, give me till lunch time and I’ll sort it out’. Obviously thinking that I’m grandstanding. Starts to call me and leave messages then gets progressively agitated as he realises I’m not coming back.
When he gets into the office, he can’t find the contract either so he goes to HR and ‘explains’ what has happened, says I have been stonewalling them and it’s cool, he’ll get it sorted, it’s between me and him. HR says erm, no, this is our thing now, and the HRD sends me the SMS.
Shortly after my phone conversation the HRD walks into a sales meeting and very abruptly pulls Dapper Dan out. They disappear into a meeting room where it may only be assumed that Dapper Dan was required to spell out exactly what had occurred and address the comments that I had made. I suspect he came completely clean at that stage.
Dapper Dan was subsequently reamed as only HR and senior management can ream a manager who’s f*cked up. He was demoted, decoupled from Marketing, his budget reduced by half and a new, separate Marketing function created.
His team were collectively put under review and forced to carry out their own reporting, tracking and metrics, which lacked the coherence and consistency that I’d been able to deliver. This reduced the capacity of the team. A couple of them left and they missed out on some key deals.
In the fallout they completely dropped the ball on the client website builds. They went to market to try and find a resource who could fulfil these builds, and Dapper Dan was reportedly astounded to discover that experienced technical marketing staff are both hard to find and expensive to recruit.
They were unable to fill the role and the builds were taken back inhouse by the tech provider, who now had an experienced resource to deploy (me). I ended up working on three of these at full utilisation rate, which was paid by the new company. I’m pretty sure Dapper Dan would’ve seen the funding arrangements for these and would know my day rate - which is substantially higher than his.
Much later... As the sales lead, Dapper Dan had to bear the displeasure of his superiors for the full twelve months before he could claim his share payout. It would’ve been a really, really shitty twelve months for him. He resigned within two weeks of the anniversary of the purchase, and the company enforced a six month notice period and another 12 month no-compete clause. Any benefit he would have received from the share payout would have been consumed over that 12 months unless he switched industries or moved cities. Last time I saw he was on the job market.
As for me? Happily living the life of the contractor. I get paid for the hours I work and I work the hours I want.
My old marketing manager is now VP of something at a large multinational. I’ve used her speech several times when giving young, frustrated staff career advice.
TL;DR Old school sales manager attempts to call my bluff. Hilarity ensues.
(source) (story by DanishProtestPig)
#prorevenge#by DanishProtestPig#pro revenge#revenge stories#pro revenge stories#pro#revenge#revenge story
525 notes
·
View notes
Text
THE LEGEND OF HOW I GOT RID OF A CREEP AT AN INTERNSHIP
Hello, my dudes... this is an urban legend of how I, a 15 year old, who recently attended an internship at a hospital... met a creep (and a pedo?), and how I saved myself from the situation. (THIS IS NOT A HIGHLY RECOMMENDED WAY TO GO ABOUT IT... if you’re stuck in a situation like this, you should probably escape and get the hell out of there as soon as you can) Anyway, so... at my internship, I met this really friendly doctor who’s like 44 years old... she has an amazing fashion taste and a pretty good sense of humor and stuff... now, she is pretty social and has like a lot of friends who are also her patients and stuff .. Now, one fine day this 22 year old man walks in, who also happens to be a pretty good friend of this doctor, and tells her about a wound that he got on his toe because he fell down the stairs. When he walked in, the doctor introduced me to him, by the way, by saying “she’s a student..” or something (just so patients are not creeped tf out by a random stranger watching them succumb into diseases and death lol) ... and so he kinda happens to include me in the conversation and it’s all cool and not awkward (as not-awkward as it can get for an asocial hooman like me) ... and she walks out of the room at one point to get a sick leave (cuz he has a wound in his leg) and he asks me about the internship and school and stuff and like we kinda joke and we have a similar sense of humor and it’s KIND OF weird cuz he’s so friendly but I just take it as extroverts and their weird social behaviors lmao and I’m like okay.. whatever. He leaves and then that’s it for the day. However, he COMES BACK the next day (he has to - to redress his wound) and this time, we’re left alone for a longer time in the room and we joke more cuz like idk I’m funny?? Apparently?? Or maybe not....... Anyway, so like we’re in the middle of a conversation when the doc comes in with the sick leave paper and she’s like “I have a patient waiting” and she kinda rushes us BOTH OUT AND ASKS US TO WAIT FOR HER cuz apparently she wants to talk to him about her watch that she needs to get fixed or something (he works at like an electronic repair shop or something) ... and now this is where it’s WEIRD weird because why did she just send me out as well??? Like I’m SUPPOSED to be with her????? But everything happened in a rush so I couldn’t really say ‘no’ ... Anyway, so it just so happens that he hasn’t had his lunch and so there this cafe kind of thing right next to the hospital and he takes me there (I REALLY WANNA KILL MYSELF BY NOW) and like I have to go soon cuz like we were still conversing about something and idk it just happened in such a haze I don’t even remember how we ended up there and HE KEPT ME THERE FOR LIKE AN HOUR AND A HALF straight, no joke. And I wanted to shoot myself in the head because WHY TF WAS I BEING NICE AND NOT ASKING HIM TO FUCK OFF???? I mean, he told me about like him getting bullied or whatever in school but like SO WAS I????? AND HE IS 22??? HE FAILED 12TH GRADE??? IM SURE HE COUKD HANDLE A 15 YEAR OLD ASKING HIM TO FUCK OFF??? Anyway so that happened and I finally made an excuse to like go back. Now, we obviously had to talk during this one and a half hour like we couldn’t just stare at each other’s faces, could we? So like that happens and at one point I mention wanting to download Netflix on my laptop or something and he goes “NO THAT’S SO GAY!” And I’m like ????? That’s not funny???? And like I’m pretty defensive about it and stuff and I bring it up twice in the conversation telling him that that isn’t appropriate or like acceptable and he goes like “Are you...” and he doesn’t complete the sentence ( of course he doesn’t) and I say “I support them...let anyone love anybody..” and stuff because I don’t wanna open up to HIM about like my sexuality or whatever right... Also, he asks me my number as well but I refuse and give him my Instagram instead... Oh and, he gives me his Netflix username and password... and he says stupid things that’s like indirectly dropping hints and I’m like NO PLS THIS IS VV UNCOMFORTABLE. Anyway so after I escape from that situation, I have to deal with him on text when I get back home right... And by now I’m pretty stressed about this because I still have to see him FOR 3 MORE DAYS CUZ HE HAS TO COME FOR REDRESSING HIS WOUND and stuff so like fml... and like I start kinda getting anxiety when he says “2019 has already started on such a good note, I hope the rest of the year goes like this” on text and I LIKE PANIC AND TELL ONE OF MY BEST FRIENDS WHO IS NOT EVEN IN THE SAME COUNTRY AS ME... And now she gets really concerned about my safety and so she asks me to tell the doctor the next day when I go back to the internship (which I was obviously going to do anyway) and then she asks me for his Instagram ID ... and I give it to her. These are the events that follow: 1) She changes her username and her profile picture.. goes fully undercover. She changes her name, even. 2) She TEXTS him saying “hey” and now, we wait. (She sends me screenshots of the chat) 3) He replies a few minutes later with “Hello” 4) She says that I told her about my internship and she heard about him through me. 5) and he is like “ah okay...” 6) and now I ask her to say “YOURE 22????!!!!!!” Lmao , which she does... just to get the message across #nomercy 7) and then she says , “I’m her girlfriend, by the way” And this is very very believable as well because remember how I was so defensive about the gay thing and I brought I up twice and he was like ???? So... yes.... they had a passive-aggressive conversation which at one point just got kinda disgusting because he went like “I don’t get why you texted me... are you jealous?” LIKE FIRST OF ALL, WHAT THE FUCK. SECONDLY, WHAT THE FUCK. And she is obviously like “ why do I have to be jealous of you?” And stuff and there are various instances where she rubs it in that HE IS FUCKING 22... she also indirectly calls him a pedo at one point ( I was behind the scenes, controlling the conversation as well) And then he texts me saying “are you bi? Because apparently your alleged gf is chatting with me right now” and like I did with his previous messages, I ignore this one as well... however, I realize that if I ignored this particular one, when I see him the next day, I will have to answer or at least, hear him SPEAK to me ... if I just confirmed it, he wouldn’t talk to me (hopefully) ... and so I said “yes... I have a girlfriend” and THEN LOGGED TF OUT JUST IN CASE HE WAS ONLINE LOL Then, skip to next day... I manage to escape to another doctor’s cabin like 5 minutes before he comes in... so I don’t have to see him. Now, on that day I even told the doctor about it ( I told her about what my friend and I ended up doing as well ... she was laughing her ass off cuz SAME) and she was like “it’s partly my fault” and stuff and she was nice about it and was like I’m not going to leave you guys alone, don’t worry .. and stuff... and like when we he came to visit her ( I wasn’t there) ... he went like “did you know she is bi?????” Doc (who obviously knows what actually happened... but is also very cool about gays and stuff .. very open-minded) - “So what?” creep - “SHE IS BI!!!!!!” Doc - “so what??? Why you even mentioning it?? How does that make a difference?” Creep- *falls silent and is embarrassed* Doc - “it’s not like she likes me, does she?” (This is why I love her) And yeah so I was saved on that day... However, the next day... and the last day I have to see his face, he doesn’t come in, and we do meet ... but only for like 5 minutes and again, we’re not left alone this time... and yeah ... Now I just ignore his texts straight up and he asked my friend at one point (who also ignored his texts after that one conversation) - “ hey can I take your word for it? Like are you actually her gf?” AND MAN THAT IS SO FUCKING UNCOMFORTABLE JESUS She replies with “yes” and I ask her to block him.. which she does He then says “hey why are you acting so distant?” to me on text LIKE YOU HAVE THE AUDACITY YOU IDIOT... So yeah, that’s it... that’s how I got rid of a creepy desperate idiot... All I’m saying is, there were a lot of instances I could’ve bailed out in this situation, but I decided to be nice/not make a big deal out of it which I SHOULD NOT HAVE DONE. If something seems weird to you, then it IS WEIRD. Do not try to justify the opposite person and put your life in danger. Another important thing is that it’s hard to say no to people like him cuz he is good natured and also, he is much older than I am... that means he is also capable of a lot of things... specifically because we were pretty much alone at that point... so it’s not the same as an asshole in your grade who you can ask to fuck off, for instance... just make sure you’re safe... make sure you are AWARE of what you’re getting yourself into... you don’t have to go out of your way to please someone or to be nice if they make you uncomfortable. You’re not obligated to do that. Your only obligation is towards yourself - save yourself before you fend for someone else.
7 notes
·
View notes
Text
Finding Best Wedding Ring Design
Choosing to learn graphic design at this particular time is ad advantage should greatly have over others. With the booming technology now, everyone wants much more information how to make artistic graphic designs and videos. In fact, companies additionally looking for extremely graphic designers out there to make their advertisements and advertisements. From magazines to billboards, a good graphic designer is extremely much in demand. So if ntlite full crack plan to study graphic design, you ought to begin learning the basics first.
Lastly, an individual have do you can put text within your designs. Make ntlite free are readable. The design would be futile and useless when the texts can be intelligible and unclear.
You are most likely not able finish your entire design at one sitting down. This is not a problem when you've got an username and password. You can save all of in order to you did and revisit your design to finish it afterwards. This is an excellent way to obtain customized t-shirts and plan accepts payment in a variety of forms including credit cards and PayPal.
One fine day, you received a phone call from some client and the man requests to be able to design a site for his company. Over the phone, he briefly says what his company is mostly about and asks about the prices, then you fixed a scheduled appointment with him for appointment. You will probably get excited concerning it and starts to get additional information of company by checking them on Google, and thinks about some prelim ideas for that website. At this stage, investigation process has already started.
I discovered that design was becoming an immense part of my day, thinking about which new whatever needed to learn, what new products I could learn to design and generally, what creative projects I possibly could get stuck into. My occupation at this juncture was a school teacher gorgeous honeymoons as well anyone provides been in teaching, you will understand that that it's lot of hard work that needs 100% dedication and great care. If ntlite keygen not in it, then don't undertake it as your not doing anyone any favours, especially your customers. After returning to work and due to my new perspective, my eyes started to open noting a few things that gave me a clearer idea of what teaching was about nowadays in secondary education for the teacher.
Many budding web designers are keep in mind self-taught. For anybody who is reading this and haven't had sophisticated design lesson in your life, supply mean in order to to abandon your desire becoming a web-based designer. Academic qualifications must be a degree (excuse the pun) taken a back seat in preference of hands on skills. Web design is now a diverse industry and offers a large selection of specific jobs that you can employment in. From creative director to artworker, is actually no a job that's excellent you. Talk to other designers; expand knowing and work on developing your creativity. Do not forget that often you is actually asked function within a team, so hone your communication skills as very well.
One question that frequently asked precisely what skills you should gain give yourself the best chance of securing doable. Web design today encompasses many technical disciplines, which you're required always be fluent operating in. The industry as a total is getting away from highly specialised designers to staff that is multi professional.
One last point; preference try build up your greenhouse on the cheap, you might find you deal with not very much space because wanted. An excellent your much better to get biggest greenhouse your allowance will please let.
0 notes
Text
Weathering Jail and Prison: Tips from Anarchist Prisoners Dane Powell and Joseph Buddenburg
Dane Powell, the first of the J20 defendants to be sentenced, just completed his four-month sentence after taking a non-cooperating plea deal in which he pled guilty to two felony charges. During the demonstrations against Trump’s inauguration, Dane was filmed risking his freedom to save a child who was brutally attacked by riot police. Dane teamed up with Joseph Buddenburg, another political prisoner serving two years for Conspiracy to Violate the Animal Enterprise Terrorism Act, to compose the following guide to surviving jail, prison, and transportation between holding facilities. Whether you are preparing for the possibility of doing time yourself, getting ready to support someone else through a sentence, or simply curious to learn more about life inside the prison-industrial complex, read on for a wide range of essential tips.
For perspective on how to weather the process leading up to the verdict, read “How to Survive a Felony Trial: Keeping Your Head up through the Worst of It.”

Joseph Buddenburg.

Dane Powell, immediately upon his release.
Dane Powell:
When you’re facing a possible prison sentence, the anxiety can be overbearing. No person who is in prison knows what lies ahead from one day to the next. It is quite literally a step into the unknown.
When I first got to jail, I kept notes on experiences that might help ease some confusion for my codefendants. I had no idea I would be transported hundreds of miles to the sunshine state over a three-week period.
Roughly a month at Coleman Federal Correctional Institution, I was introduced to Joseph Buddenburg, another political prisoner, who is serving a 24-month sentence. Joseph was originally serving time in California and was sent to the east coast, away from his support, as a form of punishment. I shared this writing project with him and we decided to combine our energy and experiences. Our goal is to give tips and tricks we had to learn the hard way. These are things we agree that we should have known before we heard the first door lock behind us.

I. Washington DC Jail
Presentencing
Prior to being sentenced, if found guilty, you will go through presentencing. This office will interview you and send a report to your sentencing judge. This report recommends a sentence. Be careful with how you word things during this interview, as everything you say can and will be used against you. I recommend your lawyers be present for this interview. For example, certain substances are legal in Washington DC, but if you’re found guilty of a felony you’ll be doing federal time / federal probation.
Once you’re in the DC jail, it can hard to reach anyone for a very long time. It took me almost three weeks to get in touch with support because I didn’t have numbers. Prior to the day of sentencing, I recommend making a list of ten people including their phone numbers and addresses. You get one free five-minute call after you’re processed in and seen medical. You can acquire a pen and paper prior to this call and call the one person with that list. You should also have someone lined up to pick up your clothes and other person belongings as they’re only kept for 14 days. Unless you want your support to be the ones making your wish list for reading material, you should already have this done as well.
DC Jail Schedule
Food comes about every eight hours to your cell. Breakfast comes at the odd hour of around three am. When you’re in intake you get about one hour of rec Monday through Friday. The rest of the time you’re locked down. This changes when you get into general population (genpop). I was in this lockdown of intake for three weeks and I only managed to get put into genpop by going on a hunger strike. Once you’re in genpop you’ll be out of your cell for about 8 hours a day. You also get two video visits a week and your support will need to sign up for this.
Random Jail Tips
If you’re having any issues on the inside, it will almost never be resolved the way you would like. The #1 thing to do is tell your support and have them put outside pressure on the jail. This works 99% of the time.
The mailroom was shit in DC. My support was calling daily as my mail wasn’t getting through. The mailroom kept telling them they were backed up by two weeks. You can get books but they need to come from a publisher and can only be softcover (this has varied at different locations but this is specific to DC). Legal mail can only be opened and looked through in front of the prisoner and shouldn’t be read.
There are no lines (in the sense of queues) in jail or prison for things like computers or phones. For a turn on the phone, you ask who the last person is and let them know you’re after them.
If you require a special diet, tell the Chaplin it’s for religious purposes. This still took me a month to get, though.
To check your canteen account and order commissary, they have touch screen computers installed in the units. Don’t order any commissary until you get to genpop [general population]. If you order it in Intake, they’ll take your money and not give you anything. You can get it back, it’s just a pain in the ass. When you first log into this computer, you’ll need to use your DCDC number (your number as a prisoner) for your username and password. You’ll be asked to set your password at this point.
The clothing exchange is the worst! You only get your clothes washed once monthly, so every day you have to wash your clothes with you in the shower.
Your toilet is in your cell and offers no privacy between you and your celly. There places in the wall that you can shove a spork into; then you can hang a blanket from the spork in order to build a temporary wall for a bit of privacy. You should save about 8 sporks for this purpose and to hang clothes-drying lines.
You should really be saving everything you can get a hold of like salt, sugar, pepper, and other things like that. You can make an air freshener with a bottle of nose spray and the green cleaner they use on the floor. Chaplains give out free holiday cards and sometimes free phone calls.
When you write a complaint, sometimes the officer you whose behavior you are addressing in the complaint will be the one to take the complaint out of the box. When this happens, there’s a good chance that that complaint will get “lost.” There is a workaround for this: you go to the law library or the chaplain’s office and put your complaint in their box.
The sole of your shoe can serve as a pencil eraser. Treat the detail crew on each block with respect and they’ll treat you right. They’re the ones who bring bathroom supplies, food to the door, and other things like this.
Tips for LGBTQ
My celly for a week of my time in Intake was an amazing person. When I told him that I was writing this, he wanted to give tips for any gay comrades who might be coming to DC jail. So these tips are coming from a gay man. He told me the gay community sticks together almost like a gang. If you have any issues, you go talk to other gay prisoners before anyone else, and they will help you faster than anyone else. You can ask to be housed with other gay men / trans women if you identify as such. Trans peeps should see the Chaplin for hormones (if needed), magic shave, and bras. If a celly is making you uncomfortable, you need to speak up ASAP.
In part two I’m teaming up with Joseph Buddenburg to talk about our experiences with being transferred all around the United Snakes. He has experience from the Cali to FL and I have been all over the east coast.”

II. In Transportation
Joseph Buddenburg:
Other than the time I’ve spent in the SHU (Solitary), being transported is the most stressful part of my experience while incarcerated. I’ve been held at six different federal prisons / holdover jails over the last seventeen months. That’s a bit of an anomaly; if you’re a “short-termer,” you should spend the majority of your time at one facility, with a short stint in transit at holdover facilities.
For folks designated to a federal prison on the East Coast, you’ll be bussed or fly ConAir to USP Atlanta’s holdover facility before transport to your designated facility. For folks designated to the West Coast, you’ll pass through Oklahoma City Federal Transfer Center, or Pahrump, NV—a privatized Corrections Corporation of America facility that functions as another Western Region Processing Center for federal prisoners.
In my experience, these holdover facilities freak out when a political prisoner arrives. I was held in max custody at Pahrump, and at Oklahoma City I was thrown in solitary for the duration of my time. If this happens to you, it’s important to keep in mind that this is only temporary; once you get to your designated prison, you’ll have more “freedom”, access to the outside, and more contact with your supporters. I was held at Pahrump for three days and Oklahoma City for two weeks.
If you’re thrown into solitary, there is very little stimulation. Use the time to work out, write, and engage with the prisoners on the housing block, who are just as bored and frustrated as you are.
During transport itself, I found it important to fast and not drink water. You’ll be cuffed and shackled, and access to the bathroom is nearly impossible. On ConAir flights, the US Marshals allow you one chance to use the bathroom on a several hour flight. They go row to row at a time chosen by them. They’ll yell and threaten you if you try to stand up or walk to the bathroom. The meals are disgusting and you’re only given an eight-ounce bottle of water anyway. You may be “black boxed” during transports, which is especially uncomfortable. Because I was convicted of a “domestic terrorism” statute, this happens to me. You’ll be cuffed and shackled, and if black boxed, a black plastic contraption will be locked to the handcuffs, creating wrist discomfort and near immobility of your hands. Make sure the handcuffs are somewhat loose. Cops are assholes, but they can be reasoned with, sometimes.
I found the bus rides are generally much longer, with no air conditioning, and less space. If you manage to get a window seat, try to sleep throughout the ride. Other things that helped were attempts at meditation, deep breathing, and just talking to other prisoners. Keep in mind that your designated facility will be nothing like these shitty county jails and holdover facilities, and that the misery of transfer is temporary. Most likely, you’ll be designated to a low security prison, with access to recreation, “programs,” college classes, and the like.
If you’re vegan or have other dietary considerations, be prepared with a number to call your support person to pressure the jail, and perhaps to go on hunger strike. At Oklahoma City, they threw me in the SHU; they don’t allow prisoners in the SHU use of the phone until 30 days have passed. They also (illegally) don’t allow prisoners to have stamps—you can send out three letters a week, only on Wednesdays. This resulted in my being unable to contact friends or supporters, so I had to refuse meals until they finally put me on a “no flesh” diet. This was not always vegan, but there’s enough vegan sustenance to survive on. Ask for a celly when you first arrive, so you’ll be able to trade food.
Dane Powell:
I was awoken around 4 am in my cell in DC. The cop told me “pack your shit, you’re heading to the Feds.” I was so new to everything, I thought I was already with the Feds. After all, I was put into the custody of the US Federal Marshals after sentencing. I was excited when my celly told me the Feds are “easy time.” On the other hand, I had just got settled in and had a nice collection of books. You can’t bring anything with you except for legal papers (put your contact list on your legal papers). So I left my books and letters as property that was to be picked up, and I stepped off again into the unknown.
From the morning I left DC, it took me three weeks to get to Coleman, FL. The process of waking you up at 4 am was repeated each time we would be transported. In my three weeks, I saw one jail and two prisons before getting to Coleman. The first morning, after leaving DC, we were brought to Warsaw, VA. We were put into a large, dormitory-style housing unit with TVs, phones, and video calling. We were at this holdover area only for a few days until we were moved once again.
This time, we were moved to Petersburg, VA. At holdover here, we were all put into solitary (SHU), and we didn’t come out from there once. We even had showers in our cells and were denied out daily recreation time due to our transportation status. We could yell to each other, but that was it. We had no books or anything to keep our minds busy.
This was the hardest week of my life, and I’ve been through a lot. I hear about people doing months or years in solitary; they have my highest respect. Only those who have been separated from human contact like this know the barbarism it takes for a human being to do this to another and the pain and suffering this torture causes. I hope I’m not affected from this time long term, but only time will tell.
After climbing out of the bolus of hell, I was brought to Atlanta Federal Institution. My experience in Atlanta was like a combination of the two previous locations, as we were mostly locked down due to two stabbings on the compound.
When you’re being transported, you should try to be first in line if you are trying to get a window seat. I think I got a window seat once; the three other times, when I didn’t, the only thing I could think of, the whole trip, was to tell others to get a window seat. I would fall asleep and with every bump I would smash my face on the seat in front of me. You’re chained up with cuffs on your hands and ankles and the cuffs are attached to a chain around your stomach. When the guards are putting on the abdomen chains, you should protrude your stomach as much as possible. That way when you’re sitting normally, it won’t be too tight.
Normally, your support will get instructions on how to setup a prepaid account when you call them the first time. Every single prison and jail I’ve been to has had a different phone system. At all the places except for Petersburg, I was told that the next place would have the same system and support could load up on their prepaid accounts, but this was never the case. Once you get into the federal system, those systems are all the same; but your support won’t need to set up anything at that point.
Some of the best advice I can give about being thrown into new environments so frequently is just to be observent. You shouldn’t really be asking too many questions unless you absolutely have to. You should ask your fellow prisoners if that situation occurs. At the same time, don’t bombard other prisoners with questions. Don’t come off as someone who’s new to the system, even if you are. You can learn everything you need to know by just sitting back and watching what others do. This takes time but it’s the safest way to approach this unknown. If you follow this, you’ll be a step ahead of most others.

III. Federal Custody
Joseph Buddenburg:
I did most of my time at medium facilities, in terms of the levels of violence, the programs, the “freedoms” afforded to me, and general demeanor, politics, and culture of prisoners.
There’s a rating system for prisoners: 0-11 points means you go to camp, 12-15 to a low security facility, 16-23 to a medium, and 24+ high security. The following factors determine federal custody levels:
detainers / pending charges
severity of current offense (mine was moderate, 3 points)
criminal history score / past convictions (0-1 past convictions is 0 points, 2-3 is 2 points)
history of escape attempts (should be 0, unless you’ve been found guilty of past failures to appear)
history of violence
voluntary surrender status (0 for no voluntary surrender, -3 for receiving a self-surrender)
age (8 points if 24 or younger at the date of sentencing, 4 points if 25-35 years old)
education level (0 points if you have a copy of your high school diploma/GED in your presentencing report, 2 points for “non-verified HSD/GED)
drug or alcohol abuse / convictions (0 for never or more than 5 years previous, 1 point for any drug use or convictions in the last 5 years).
If your charge is political, the BOP (Bureau of Prisons) will likely place a “management variable” of greater security or a “public safety factor” on you. This will make you ineligible for “Club Fed”: federal prison camps, in which there is no fence and you have more freedom of movement. Political prisoners will go to low security or higher.
A “management variable” will bump you up one level, so if you’re at camp level, you’ll go to a low; low points go to mediums; and so on. Only long-term prisoners or those with a serious criminal background will be sent to a penitentiary.
Make sure to clean up any pending charges or warrants before resolving your case—I ended up getting 7 points added for a pending misdemeanor, which bumped me from camp points to low so the BOP sent me to medium security facilities. Also, be sure to have a copy of your high school diploma or GED included in your “pre-sentence report” prior to sentencing. The pre-sentencing officer won’t track this down, it’s on you to track down a copy—this will subtract two points from your custody scoring and could mean the difference between a low and medium security facility.
Ask your attorney to request a “self surrender” from the judge. This typically allows you to turn yourself in to the US Marshals / prison to begin your sentence. That will subtract 3 points from your score and gives you around 60 days to clear your affairs before turning yourself in. My sentencing judge doesn’t give self-surrender, but my attorney convinced him to give 24 hours to self-surrender, thus lowering my points.
Low security prisons are devoid of convict politics. Snitches and sex offenders are everywhere, but you’ll find a few solid people—usually older guys who have worked their way down from penitentiaries. It will be rare to find anyone who shares your politics, but for the most part other prisoners will respect you for “being standup”: for standing up for what you believe in and not snitching.
The prison bureaucrats may fuck with you, pinpointing you for harsher treatment or fucking with your mail or outside support. If this happens, be prepared to have your support pressure the prison, BOP, and oversight bodies and seek assistance from radical attorneys.
The most difficult thing about prison for me has been the isolation and interference by the BOP, and I regret not fighting it from the beginning. Don’t fear their retaliation and petty games: the nature of being a political prisoner will get you targeted from the beginning. Having support is your best weapon to fight back, so never hesitate to call your people and the movement in general for help.
Dane Powell:
Depending on how one looks at it, I got lucky for spending my federal time in a low. There’s a lot less prison politics in a low, which is good for political prisoners who don’t want to deal with racist prisoners, but it also has drawbacks. With prison politics low, prisoners are less likely to “check in” snitches and child molesters (i.e., to force them into protective custody). With a yard full of snitches, it’s almost impossible to organize anything unless you start running with groups that check papers.
Ask your lawyer to send you your sentencing papers as soon as possible. These papers will prove you’re not a snitch or a sex offender and you’ll likely need them to prove your story.
One of my cellies told me over and over that they were in for gun charges but refused to show papers. He always had an excuse as to why he couldn’t get them. Most prisoners see right through this, as I did. Turns out, this celly is in prison for trying to have sex with a fake 9 and 11 year old. I judge good jail praxis by whether the act of retribution gets the person who administers it caught or if they can pull it off without the recipient knowing. Someone had great praxis.
During my time at Coleman, I was welcomed into the native community. Some facilities’ native groups allow white people to sweat with them and some do not. If you’ve done a sweat before, the ones done in prison will likely be different. We would have a pipe ceremony every Saturday and this is where new natives or invites would bring their papers and introduce themselves. The papers would be checked by all to ensure that no sex offenders or snitches would sweat with us. It was nice knowing those guys could be trusted.
When coming from a jail, you might be told your mail will be forwarded. It’s very unlikely that any jail will forward your mail; you should just assume it won’t be. Your funds will be forwarded. For me, it took about 20 days once I got to Coleman to receive my funds from DC.
If where you’re sentenced and where you’ll be released are different, and you’re going to have probation, you’ll need to get a transfer. If your probation isn’t transferred before you get out, you will have to report to probation in the district you were sentenced, even if you have no place to go. To get the transfer, you’ll need to see your case manager and have an address to live at which there are no felons or guns, among other things. It takes about a month to properly transfer your probation.
I had issues with the email system that was offered to us. You’ll need to add your friend’s email address as a contact on the computer system. When you add it, that email address will receive an email for them to set up an account through TRULINCS (the system the BOP uses). From what I’ve seen and heard, this process can be confusing. If they get past this and they have an account, they can email you. They need to understand that when a prisoner emails them, they will not get an email notification to their actual email address alerting them of your message. They will have to sign into TRULINCS to see your emails every time. For some reason, a lot of people didn’t understand this.
There are also private secondary services out there through which you’ll be assigned a phone number and friends can text this number. The company then sends you an email with the text message and you can respond to that email and they text your message to your correspondent. This service costs about $15 a month and you’ll likely need someone on the outside to set it up for you.
Most of the clothing you’ll need (like gym shorts, sweats, and shoes) can be bought in your housing unit. The most common forms of currency are stamp books (flats) and packages of mackerels (macks). Prisoners make a job out of fixing up shoes and clothing that was trashed and repurposing them. You can pick up items for a fraction of what the commissary sells them for; the ones available from commissary are normally made by prisoners at sweatshops in the numerous other facilities the BOP runs.
I saved the best tip for last. To bring hot sauce into the chow hall, put it in a medicine bottle and your food will be more bearable.

51 notes
·
View notes
Photo

WordPress Secure Setup: Top Tips for Securing WP Admin
Welcome to the WordPress Secure Setup Guide. In this tutorial, I’ll show you a number of ways to secure the WordPress admin area. Before I show you these, consider whether the WordPress site has an SSL certificate.
An SSL connection helps secure any website and is recommended, especially for use on WordPress sites.
This video is part of my course WordPress Secure Setup Guide. You can watch the entire course for free here on Envato Tuts+.
FREE
WordPress
WordPress Secure Setup Guide
Kezz Bracey
HTTP and HTTPS
u Forcing SSL Logins and SSL Admin Access
SSL stands for Secure Socket Layer. Essentially, it’s what makes the difference between HTTP and HTTPS when serving a website from a server. The S denotes that the connection is secure.
If you don't already have SSL set up on a WordPress installation, contact the web host, they’ll tell you what you need to do.
You can also follow our guide on how to secure your WordPress site with SSL.
WordPress
How to Install an SSL Certificate to Secure WordPress
Rachel McCollin
When you have the SSL certificate set up and running on your site, the URL that you'll use for your site will go from HTTP to HTTPS.
Now that you know S stands for secure, when you see HTTPS in the URL, you can be confident that you're browsing in a secure connection.
Forcing SSL Using wp-config
Forcing SSL Using wp-config
A wise step to take is to activate a feature in WordPress that forces the connection to go over HTTPS whenever somebody is logging in and whenever they're in the admin area so that there's no unsecured access.
The way to do this is by copying a little snippet of code to the the wp-config.php file. Copy the following line of code:
define('FORCE_SSL_ADMIN', true);
Now scroll all the way down to the bottom of your wp-config.php file, after the WP_DEBUG line here, pasting the code snippet in.
Once that code has been added, the only way to access the admin area will be through a secure connection.
The next thing to consider is changing the location of the login page. If you look in the URL bar, you’ll see this login page is at wp-login.php. This is the default for all WordPress websites.
Change the Name of wp-login
Change the Name of WP-Login
You’ll recall that brute force attacks may be used to hack their way into the WordPress admin area. Part of that automated process is to examine the domain name. The attack just adds wp-login.php to the end of it. Then, if a login page is found, the script knows exactly where the WordPress login page is, and it will begin the brute force attack.
One way of preventing such an automated brute-force attack is to change the name of the login page to something non-default, thus changing the URL.
Again, this is achieved using a plugin.
Searching for a plugin
In the WordPress admin panel, navigate to Plugins > Add New then search for Rename wp-login.
There are actually several different plugins that you may use to rename the login area, so feel free to have a browse through and choose the one that you prefer.
Or you can just go with Rename wp-login We'll install that and activate it. Once activated, you’ll be taken straight a settings page where you can rename the login area. You may leave it as login, or you may come up with something a little more obscure.
This is known as security by obscurity.
And if you do go with something a bit more obscure, then ensure you bookmark the new login page so that you don't accidentally lose it.
In this example, I’ll leave it as login, and save the changes. So now if I log in, the URL will say login, not wp-login.php.
Recovering WordPress if You Get Locked Out
On that note, if you ever install a plugin for security and then accidentally lock yourself out, go to the File Manager or FTP client. Navigate to the Plugins folder, in the WordPress installation, then rename the folder for that plugin.
That has the effect of deactivating the plugin, in turn removing whatever mechanism is locking you out. Then you can get yourself back into the WordPress admin area and correct the issue.
Limit the Number of Unsuccessful Login Attempts
WordFence
Another good security measure is to limit the number of unsuccessful login attempts a person may make. Generally speaking, a valid user is only going to forget their password a few times before they reset it or they remember it.
If, however, there's a single IP address making many login attempts, that's an indication that somebody trying to hack their way into the site.
The way to counter this is by setting a maximum number of login attempts. If you set it to five, then after five incorrect attempts to log in, a user would be temporarily locked out. And you may set how long to lock them out for, say five minutes or 20 minutes. That would usually be enough to interrupt a brute force attack.
Once again, there’s a couple of different plugins that you can use for this. I’m using the functionality that’s included in one of the most popular security plugins for WordPress, Wordfence.
Install and activate Wordfence in the usual way and navigate to the lower left of the WordPress menu to find the Wordfence menu. Select Options.
Wordfence does a number of things, many of which I’ll show you in another tutorial. For now, I’m focusing on limiting the login attempts. So scroll down to the Login Security Options section.
Here, you may configure:
the number of login attempts a person may make
how many times they may forget their password
the period of time that you'll allow those attempts to occur within
how long you want have that person locked out
Well, I say a person, but this won’t actually affect people as much as it will affect automatic login attempts. And that’s the point.
Generally speaking, you can probably leave the settings at the default values. Pay attention to the activity on the site to see if there are brute force attacks being made.
Lock Out Invalid User Names
Locking Out Invalid User Names
If you're the only person using the site, you may set rules to be as strict as you want. If, however, you have a business website where you have customers as members on your site, then you’ll need to consider the customer service side of things.
For example, I had a website where all of my customers needed to be able to log-in to the back-end in order to access products that they had purchased from me. At the same time, I experienced a relentless series of brute force attacks that went on for years, non-stop, 24/7.
So, in order to protect the data of my customers, I had to make the call to make these rules very strict.
One of the things that I activated was this option here to immediately lock out invalid usernames. Because, my logic was, sometimes you forget your password but, generally speaking, you're less likely to forget your own username.
Now if you do find yourself in a situation where you have to do this, just have some type of customer service process ready because when people get locked out, they may get a bit irritated.
Ensure that you provide an easy way for locked-out customers to contact you and let you know that they've been locked out. Then explain to them that the reason that you're doing it is to protect their information. Once they know that, they'll always be happy; the irritation will disappear!
And if anything, you have an opportunity to build greater trust with your customers because they know that you're looking out for their privacy and security.
Now one great feature that this area also includes is you can see here. It says prevent users registering admin username if it doesn't exist. And you already know why you don't want to have an admin username on your site. But you can also add extra usernames that you don't want to allow on the site.
So you might add wp-admin, you might add your full name to make sure that nobody can use that. And that just gives you extra ways to try to prevent these brute force login attempts.
Another thing that you should be aware of. If you have customers that need to log in to your site and you limited the number of login attempts that they can make. Is the Alerts section at the top of these options. So here, you can get an alert whenever somebody's IP address is blocked.
Now, of course, you get to know customers over time, so if you see that someone who's been locked out is a trusted member you can be a bit proactive. You may unblock them and let them know that they're able to log in again.
Unblocking IP Addresses
Blocking IP Addresses
If somebody contacts you, who has been locked out, and they are legitimate user, then go to the Wordfence menu, and go to Blocked IPs.
Here, you'll see IP addresses that are blocked out from login. You’ll be able to identify the person who's been blocked and remove that block. Or you can just choose Clear all locked out IP addresses if you feel that it's safe to do so.
Limiting WordPress Admin to an IP Address
Limiting WordPress Admin to an IP Address
Allowing only specific IP addresses to have access to the WordPress admin area as another good security precaution.
This is something you can do if only you and a handful of other people are accessing the site. And you’ll all need to have a static IP address. That is to say an IP addresses that doesn't change over time but which stays the same.
If these circumstances are satisfied, then follow the WordPress Codex instructions on how to modify the .htaccess file so that it only allows certain IP addresses to access the admin area. .htaccess is found in the root folder of your site.
Now I'm not going through exactly what you have to do here because this does get a little technical. You’ll need to know whether the server is an Apache server or an Nginx server. If you don't feel confident with that, then you probably don't want to attempt this technique. But if you do, then you'll find a link, in the notes below this tutorial, on the process to follow.
.htaccess Login
Using htaccess to password protect the admin area
Another, similar technique is to create an extra layer of password protection on the login page.
Again, this is done by editing the .htaccess file in the root folder of the website. This security measure creates a popup that prompts for a username and password—not the password to your WordPress site but a different one. And this functionality is completely separate from WordPress. Only once you successfully log in through this popup can you even access the login page.
If you're dealing with brute force attacks, and you don't have to allow public access to the admin area for your customers, then this is a really great option.
Once again, this is a little technical. You can find the complete instructions on how to password protect wp-login from the WordPress Codex.
Just a quick note, though. If you’ve renamed the login area, ensure that you don't leave wp-login.php in here, which is the default address of your login area. Ensure you update so that it's protecting the correct location for the login page.
CAPTCHA Code
Captcha Code plugin
Another technique is to add a CAPTCHA code to login pages. Again, this is achieved with a plugin so navigate to Plugins > Add New.
There are several different CAPTCHA plugins, and you can use any one that you like. One of my favorites, though, is SI CAPTCHA Anti-Spam. So I’ve installed that and activated it.
Go to Settings, scroll down and this is where to set up a CAPTCHA code for the registration form, for the lost password form and for the comment form. You do have the option to activate it on the login form, as well, as that one is not enabled by default.
Once again, if you are having trouble and you really need to clamp down on brute force attacks, you may enable this.
Once enabled, you’ll have a CAPTCHA code here and it won’t be possible to log in without getting that code correct.
Two-Factor Authentication in WordPress
Two Factor Authentication in WordPress
The last technique to protect the WordPress admin area is two-factor authentication, also known as two-step authentication.
You're probably familiar with this from personal use of this security technique.
The two-step basically refers to needing two things in order to get in. Normally something you have and something you know.
You have your username and password—something you know—and one method is to text a security code to a mobile phone—something you have.
Wordfence does have functionality built in for this. If you go to Wordfence > Cellphone Sign-in. This, however, is something that you’ll need to pay for in order to enable.
Alternatively, there are other plugins that you can use. You can learn more about two-factor authentication on the WordPress website.
Conclusion
That wraps up the list of top techniques for securing the WordPress admin area. I’ve done quite a lot so far to secure the WordPress site, but there are still other things that can be done.
In the next lesson of this free course, I’ll show you some additional security methods to implement.
FREE
WordPress
WordPress Secure Setup Guide
Kezz Bracey
by Kezz Bracey via Envato Tuts+ Code https://ift.tt/2X5vaL3
0 notes
Text
madden mobile cheats iphone
madden mobile cheats iphone
Just in case you are running out of things to worry about and would appreciate a fresh supply, you may want to consider the likelihood of a hacker hacking into your wireless devices and meddling with the controls of your vehicle, your pacemaker or even your blender. My relatives always say that I am wasting my time here at net, madden mobile coin glitch however, I know I are obtaining understanding daily by obtaining my NBA money and coins. Thereafter, enter the number of coins and cash that you want to own. Pc Safe and sound: Since you won't possess to down load anything right here, FIFA Portable Crack means that your pc won't have to experience virus or any malware.
FIFA Mobile phone Soccer Cheats And Methods To Get Unlimited Coins. They had been extremely Spyware Software program Computer effective with their earlier game Game of Battle: The compromise functions for all Google android and IOS video game users. When you determine to make use of our hack device, you are talented with sophisticated algorithms which are good plenty of to hack NBA Live mobile servers.
I possess usually played video games on my cellular mobile phone, but since the big video games emerged out it all proceeded to go up to the following level. Hence, it would become unlimited battle points https://realgamescheats.com/madden-mobile-hack/ and diamonds that you should win Portable Legends: Bang bang. Batman games are available in a specific site that gives you availability to an amazing collection of games that feature the masked guy.
Centered upon the market evaluations and our personal encounter, right here can be a collection of the best Android hacking applications that ethical hackers and security researchers can use. In an NBA LIVE Mobile phone Crack game, an individual can put together a team utilizing a variety of cards. In December 2011, German researcher Karsten Nohl revealed that it was possible to hack into mobile telephone voice and text communications on many networks with free decryption software available on the Internet.
It is normally completely engaging where players control characters and lead their armies in aspect missions to gather loots and beat enemies. There are now cell phone tapping programs that allow you monitor cell cell madden mobile hack apk phones. Get free Coins, Money and players Packs in lots of enjoying or paying hundreds of dollars. This means no one will ever know you are hacking Madden Mobile phone and banning is definitely near impossible.
Here in this game, you have to generate coins which will let you buy players credit cards. If you have got ever dreamed of getting a main participant in such video games, right now is definitely your probability. This is quite natural because these devices are now affordable and parents want their kids to have a mobile phone so they can contact them whenever they desire to hear their voice and determine their location.
Think You Are Cut Out For Doing Madden Mobile Hack?Take This Quiz
The 900 GB of taken store also includes login data (usernames and passwords) of Cellebrite customers, which suggests that it offers been taken from the internet servers related to Cellebrite's site. Endless tournaments, strong opponents, all licensed teams soccer players and more will be at your fingertips. Best Madden Mobile phone Crack to generate you unlimited madden mobile cash immediately.
The payouts for all these secure messengers have been increased after tech companies launched end-to-end encryption in On a rooted mobile phone, specialized shields can end up being defeated, permitting apps to carry out all types of actions that are normally prohibited - and that can include snooping on your personal data. Don't waste a moment and check out our official website in order to use the hack tool immediately and appreciate the amazing Madden Portable video game.
The Kindle Wi-fi and 3g are two extremely equivalent gadgets, with a minimal, but extremely essential difference. And all players start their characters off with 350 coins, which are spent quickly and leave you wanting more. Luckily, our NBA Live Mobile phone crack is definitely accessible on ALL products, and allows you to obtain and greatest extent any kind of cards in the video game, by digesting your demands straight on the cloud, conserving your electric battery juice!
The increasing number of mobile applications offers set out a fresh trip of mobile video games later on about. The essential factor right here is to get the necessary in-game money or gold for you to get every one of these epic products. There are now cell phone spying applications that allow you find everything that somebody will on their mobile phone. It is compatible to be played on Android and iOS spyware for iphone without jailbreak 8 hack pool devices.
Bear in mind, the true fun in NBA Live starts off whenever you get the resources! Gamer worldwide are playing this video game every one video game. It is definitely fairly disappointing indeed madden mobile hack when you are not able to crack the code of winning just credited to absence of cash. There are unlock orders for both of those issues, therefore remember that something like a NBA Live
The cellphone spy program is being promoted by websites on the internet as the bugging device for parents and lovers who want to know what their loved ones are up to. For a small fee, anyone can spy on cell phone text messages, or even record cell phone conversations right from their home computer. The true soccer participant movement is normally a brand-new animation program that increases the precision of the handles and properly shows the character of the players - today Cristiano Ronaldo and the various other greatest players act and move like true footballers.
The information is usually held on public databases and is usually available for free; nevertheless, you cannot discover respected assets like the person's mobile phone amounts, education confirmation, alias, business information, legal background, economic position, and various other related information. Based on several different abilities, the players are broken up in the video game.
4 notes
·
View notes
Text
We Tested Ring’s Security. It’s Awful
It's not so much being watched. It's that I don't really know if I'm being watched or not.
From across the other side of the world, a colleague has just accessed my Ring account, and in turn, a live-feed of a Ring camera in my apartment. He sent a screenshot of me stretching, getting ready for work. Then a second colleague accessed the camera from another country, and started talking to me through the Ring device.
"Joe can you tell I'm watching you type," they added in a Slack message. The blue light which signals someone is watching the camera feed faded away. But I still couldn't shake the feeling of someone may be tuning in. I went into another room.
My colleagues were only able to access my Ring camera because they had the relevant email address and password, but Amazon-owned home security company Ring is not doing enough to stop hackers breaking into customer accounts, and in turn, their cameras, according to multiple cybersecurity experts, people who write tools to break into accounts, and Motherboard's own analysis with a Ring camera it bought to test the company's security protections.
Last week a wave of local media reports found hackers harassed people through Ring devices. In one case a hacker taunted a child in Mississippi, in another someone hurled racist insults at a Florida family. Motherboard found hackers have made dedicated software for more swiftly gaining access to Ring cameras by churning through previously compromised email addresses and passwords, and that some hackers were live-streaming the Ring abuse on their own so-called podcast dubbed "NulledCast."
In response to the hacks, Ring put much of the blame for these hacks on its users in a blog post Thursday.
"Customer trust is important to us, and we take the security of our devices and service extremely seriously. As a precaution, we highly encourage all Ring users to follow security best practices to ensure your Ring account stays secure," it said. To be clear, a user who decides to use a unique password on their Ring device and two-factor authentication is going to be safer than one who is reusing previously hacked credentials from another website. But rather than implementing its own safeguards, Ring is putting this onus on users to deploy security best practices; time and time again we've seen that people using mass-market consumer devices aren't going to know or implement robust security measures at all times.
Ring is not offering basic security precautions, such as double-checking whether someone logging in from an unknown IP address is the legitimate user, or providing a way to see how many users are currently logged in—entirely common security measures across a wealth of online services.
"They are worth billions so where is the investment in security," Daniel Cuthbert, who is on the committee for annual cybersecurity conference Black Hat, and who is also a Ring owner, told Motherboard.

The livestream of Motherboard's test Ring camera. Image: Motherboard
A Ring account is not a normal online account. Rather than a username and password protecting messages or snippets of personal information, such as with, say, a video game account, breaking into a Ring account can grant access to exceptionally intimate and private parts of someone's life and potentially puts their physical security at risk. Some customers install these cameras in their bedrooms or those of their children. Through an issue in the way a Ring-related app functions, Gizmodo found these cameras are installed all across the country. Someone with access can hear conversations and watch people, potentially without alerting the victims that they are being spied on. The app displays a user-selected address for the camera, and the live feed could be used to determine whether the person is home, which could be useful if someone were, for example, planning a robbery. Once a hacker has broken into the account, they can watch not only live streams of the camera, but can also silently watch archived video of people—and families—going about their days.
Or a hacker can digitally reach into those homes, and speak directly to the bewildered, scared, or confused inhabitants. That level of sensitivity should arguably encourage more robust security practices than an ordinary account.
Do you work at Ring? We'd love to hear from you. Using a non-work phone or computer, you can contact Joseph Cox securely on Signal on +44 20 8133 5190, Wickr on josephcox, OTR chat on [email protected], or email [email protected].
Ring doesn't appear to check a user's chosen password against known compromised user credentials. Although not a widespread practice, more online services are starting to include features that will alert a user if they're using an already compromised password.
Other steps Ring could take to better keep hackers out includes checking whether someone is logging in from an IP address Ring has never seen before, and if so, carrying out additional checks, Cuthbert said. Another is checking for concurrent sessions, such as seeing whether the user is simultaneously logged in from, say, both Germany and the U.K., Cuthbert added, in case one of those may be a hacker accessing the account.
One member of a hacking forum who codes cracking tools, and who Motherboard granted anonymity so they could speak more openly about the process, said, "just enabling SMS verification if there is a connection from an unknown IP would instantly kill each checker." A checker is a piece of software that grinds through credentials to see if they work on a particular site or service.
CRACKING RING
Motherboard purchased a Ring camera to test what sort of security protections are in place to stop or slow hackers trying to break into Ring accounts. After setting up an account, the Ring app, and the camera itself, we shared the email address and password to the camera interface with multiple reporters who used both virtual private network software to connect to the camera from IP addresses from all over the world as well as physically being located in other countries.
We logged into the Ring app and website from the U.S., U.K., Spain, and Singapore, in some cases simultaneously and from various devices and browsers that had never been used to log into the platform before. At no point did Ring trigger any sort of alert, such as an email notification, to check that the IP address the system had never seen did indeed belong to the legitimate camera owner. Gmail, for instance, may email you if it detects a suspicious login attempt from a new location, a new device, or a new browser.
On a desktop web browser, someone who is logged in is able to watch historical, archived footage. From a smartphone app, someone who is logged in can watch live and historical footage, listen through the camera's microphone, speak through the camera's speaker, play an alarm, see the name of the specific Wi-Fi network the camera is connected to, see the address the user originally registered the Ring camera with, see the phone number a user has entered into the app, and see nearby crime "incidents." This shows the specific, user-selected home address plotted on a map. Ring requires that a user input a home address to set up the camera.

A list of archived footage stored in the Ring app. Image: Motherboard
Multiple Motherboard staffers accessed these services simultaneously. But Ring provides no way to see how many people are logged in at once, meaning if a hacker is logged into the app, a Ring owner has no way to tell. If a user is livestreaming the camera feed, a blue light on the front of the camera turns on; however, many Ring users may not constantly be checking whether this light is on or not. Ring also doesn't appear to provide users a list of previous login attempts, making it harder to see if a hacker had access.
Ring hackers' software works by rapidly checking if an email address and password on the Ring web login portal works; hackers will typically use a list of already compromised combinations from other services. If someone makes too many incorrect requests to login, many online services will stop them temporarily from doing so, mark their IP address as suspicious, or present a captcha to check that the user trying to login is a human rather than an automated program. Ring appears to have minimal protections in place for this though. Motherboard deliberately entered the wrong password to our account on the login portal while connecting from the Tor anonymity network dozens of times in quick succession. At no point did Ring try to limit our login attempts or present a captcha.
One source sent Motherboard a screenshot of a piece of Ring cracking software in action.
"Headers can tell the website how legitimate a request is," they wrote along with the screenshot, headers referring to information a web request can include to give more information about the machine logging in. Headers can include the browser or operating system the request comes from, which could indicate if a login attempt is automated by software. "But Ring's security is such that even with minimal headers, you can get by," they added.

A redacted screenshot of the address stored in the Ring app. Image: Motherboard
"Ring is a physical thing, they could implement something to securely pair it with an app on your smartphone. Then, mobile app approves web logins from untrusted web browsers," Dino Dai Zovi, mobile security lead at Square, wrote in a tweet on Sunday.
Security is a trade-off with efficiency. Ring may not want to have stricter checks in place so as to not raise barriers for its users. Perhaps a customer is out of the country but still wants to log into their account and check what has happened in view of the camera, meaning they may connect from a new IP address. But even with this trade-off in mind, Ring has made decisions to not provide users alerts with new logins or other protections.
Ring does offer two-factor authentication, where a user is required to enter a second code sent to them as well as their password, but Ring does not force customers to use it. Motherboard verified that Ring's two-factor authentication does work as advertised, but multiple people who were logged into the app didn't have to log back in after it was enabled—Ring didn't eject them nor ask them to enter a two-factor token. Ring did log everyone out after a password change, however.
Motherboard asked Ring a series of specific and detailed questions, such as whether Ring limits the number of login attempts, or blocks an attempt if the connecting IP address is from a country the user is not usually located in. The company responded with a statement nearly identical to its earlier one, saying, "Ring understands what a big decision it is to pick a home security product, and we don’t take that decision lightly. Ring will continue to introduce additional security features to keep Ring accounts and devices secure, and we're working with our customers to ensure they have the knowledge and tools to practice good password habits."
"They are worth billions so where is the investment in security."
The victims of Ring hacks have said themselves that they feel the company is putting too much burden on them to stop hackers. Ashley LeMay, one of the parents in Mississippi whose camera was hijacked to then spy on their children, told the New York Times she thought Ring's response provided scant information and shifted responsibility for the breaches onto customers.
"Auth [authentication] is still stuck in the '90s," Cuthbert said. "Username and password and very little other than that. That was ok back then but today we have a wealth of knowledge and experience to know that we need additional telemetry to make the [authentication] decision," he added.
Ring is advertised as a home security device which is supposed to make its customers safer by monitoring their homes. But its lack of certain security features shows how the device can work against its owners, and open them up to other risks. When I get home tonight, I'll put the Ring camera back into its box, regardless of whether that little blue light is on or not.
Jason Koebler, Emanuel Maiberg, and Lorenzo Franceschi-Bicchierai provided additional reporting for this piece.
Subscribe to our cybersecurity podcast, CYBER.
We Tested Ring’s Security. It’s Awful syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes
Text
Start a WordPress Blog 2019
New Post has been published on https://wpwebsmartz.com/how-to-start-a-wordpress-blog-2019/
Start a WordPress Blog 2019

How to Start a Blog on -2019? (With basic Plugins)
Get activity to your new site (I have some awesome tips for this!)
Have you ever heard about WordPress blog, if yes, I add this too, this is an absolutely big trend on the internet today.
When I began my first blog, I had no clue how to get activity so it took me a couple of years to get any force. There was no proper idea of how get the start and where from? What is the main thing? What are Theme, Plugins, Difference between post and page?
In this article, I explain briefly how to start a WordPress blog. Need Some basic requirements for the start of a WordPress blog (Ex: Which theme, plugin best for the proper functioning of your blog)
Step 1: Choose a domain name of you blog
The primary thing you will do is to pick a domain name this is the address of your website. I mean blog. We recommend Hostgator is best for chose domain name and hosting. Hostgator client since they are CHEAP, dependable, have shockingly great client support, and they make the specialized piece of working with WordPress extremely simple.
Step 2: Choose a Hosting Plane
Now you must buy a hosting plan to host your website on the internet. Hosting means doing upload all your files to the internet. Hostgator have the best plans for hosting. Their plan Starts at Rs.99/mo. This plan best for beginners.
Step 3: Install WordPress in Cpanel

Click WordPress Icon there in Cpanel, now you are going to Script installation and Setup page.
First choose protocol anyone you want HTTP:// or http://www, with www or without www. Chose domain to give a name to Directory (Please note: don’t put anything in the directory because one more folder created under your domain name and it will be slowed down of your website)
Enter site name in site settings tab and put site description. Enable or disable Multisite (WPMU) this is restriction for multiple login attempts
Give an admin username and password, Password should be strong (ie: @7Xxxxx) one special character a number and a uppercase (its show you week and strong meter in the bottom with red for week green for strong) put admin email after that.
Click Install button below which is in blue (See Image Below)

WordPress Installation Sign up Details
The page was redirected to image below ( Congratulations, the software installed successfully ) click Administration URL and login admin dashboard of your website.
Step 4: Install Plugins inside WordPress blog
Plugins are utilities which give extra usefulness to your application. To Install WordPress Plugin you simply need to put the plugin folder into the wp-content/plugins index. Once a plugin is installed, you may activate it or deactivate it from the Plugins menu in your WP dashboard.
In WordPress, you can install a WordPress plugin specifically from the administrator area. Download the plugins to your PC, at that point sign into your WP administrator and go to Plugins > Add New.
Step 5: Differences between blog Page & Post
Pages include Home, About Us, Privacy Policy, Contact Us and more. The page means brief about your blog. Posts are your blog niche. Write articles on the Daily or weekly ones on any topics you want. It depends on your skills and what information you have on your niche. Travel, lifestyle, yoga, health these are popular topics. My niche is WordPress related articles, I am writing WordPress related posts weekly ones.
(adsbygoogle = window.adsbygoogle || []).push();
What is WordPress blog?
WordPress is CMS platform to create blog posts regularly
Is WordPress better yet to creat blogs?
Yes, 100%, WordPress better choice to creat blog. Because, today WordPress occupying 25% of the internet, which means 25% of Websites run by WordPress.
Only at WordPress can create blogs?
No there many other platforms are there on internet like Joomla, Drupal, Wix etc.
Cna i make money from blog?
Yes, But it depend on your overall skills, information’s
Step 6: Install some must needed WordPress Plugin to your brand new blog
1. WPForms
The WPForms plugin is famous for one of the beginner-friendly WordPress Contact form builder Plugin. This is really true to its drag and drop editor. The free version is fine for the beginner or smaller websites, but I very much prefer the premium memberships because of the low prices and wonderful features.
That said, the drag and drop visual editor is way ahead of its competitor, seeing it really showed what they are said. and the average user not too confused. Customers also get form templates, conditional logic tools, and entry management.
The $39 per year starting fee is reasonable.
You can integrate your forms with MailChimp, GetResponse, Campaign Monitor, and AWeber.
WPForms also has an integration with Zapier.
Embed your forms anywhere.
Use the partial entry form tool to hunt down more leads.
Utilize geolocation data to learn more about your users.
Split long forms into multiple pages.
All of the forms are completely responsive.
The forms can use conditional logic depending on how users respond.
The entry management lets you view all submissions in one area.
WPForms lets users submit files from the frontend.
Their starting plane begins with #39.50 this is reasonable.
You can embed forms anywhere you want in page or post.
Use geolocation data to learn more about your site visitors.
Integrate your forms with many email service providers such as MailChimp,
GetResponse, Campaign Monitor, and AWeber. Also, use the service of Zapier.
All your site entries you can view your WordPress website dashboard.
WPForms allows users to upload files from the frontend
Split long web forms to multiple pages
Providing you form abandonment feature.
2. Yoast SEO
Yoast SEO is the main Recommended WordPress Plugins SEO plugin for your WordPress site. It handles all that you require for a quality on-page streamlining. Moreover, you get a moment SEO score for each post or page you make. It underpins other major WordPress modules, for example, WooCommerce for instance.
2. Elementor
Recommended WordPress Plugin Elementor is the quickest live page developer for WordPress. It definitely accelerates your web architecture work process, and let you plan any page without coding. With a wide cluster of export formats, propelled portable altering instruments and a considerable rundown of other helpful highlights, it is an unquestionable requirement have plugins that will supercharge your web architecture
4. BackupBuddy.
BackupBuddy is a premium WordPress Recommended WordPress Plugins that gives you a steady and simple approach to reinforcement and exchanges your destinations with various choices to store your chronicles including Dropbox, Amazon, and so forth.
5. Jetpack
This is a far-reaching module that contains an extensive variety of highlights: notices in your toolbar, interface site to interpersonal organizations and consequently share, see compact details, enable memberships to your presence on getting warnings, share content with Facebook, Twitter and that’s just the beginning.
0 notes
Text
Taking control of your credit after a divorce

Family Law Attorneys Houston: There have been very few instances that I have seen spouses handle finances on an equal basis during my time as a family law attorney. There is usually one spouse who takes the lead on doing any investing, saving for the kids’ college and getting the bills paid each month. How it works out from the attorney’s perspective is that the client either has all of the access to financial information and can answer all of my questions about money or the client has no knowledge of the finances and has never been given any of the usernames or passwords to be able to access online financial accounts.
If you are going through a divorce then you should be prepared to begin life as a single person who is in charge of handling their own finances. Whether it is through willful ignorance or a controlling spouse, you can no longer assume that your spouse is taking care of everything. It’s time to get off the bench, grab a helmet and get in the game.
Today’s blog post from the attorneys with the Law Office of Bryan Fagan, PLLC will discuss the topic of how to care for your credit as a person going through a divorce. We’ll start by noting the importance of checking what is on that most important of credit documents- your credit report.
Verify that everything on your credit report is correct
Your credit report reflects the relationship that you have had with debt. Who you borrow from, what is left to be paid on each account as well as information on missed payments, the age of each account and other personal information. It is essential that you pull your credit report and verify that the information contained in the report is correct. It would be a bad day for you to get to the end of your divorce only to find that a person has stolen your identity and opened up 10 credit cards in your name. It will take you a long, long time to dispute those cards and can delay your divorce from completing.
Beyond your ability to be seen as credit worthy and trustworthy enough to be loaned money to, your credit score can determine your insurance premiums and whether or not you are even eligible to be extended insurance in the first place. Also, employers are pulling a copy of your credit report with greater frequency than ever if only to see if your finances are in order before you are hired.
I may as well take a moment here to point out that just because you have a great credit score does not mean you are wealthy or in a solid financial position. Often times it is the opposite, actually. Your credit score (which is determined based in large part on what is contained in your credit report) tells you just how well you have paid payments on loans. The reality is that if you have paid your loans on time each month you have also paid a ton in interest over the lifetime of that loan. This leaves you in the good graces of the credit reporting companies but your actual pocketbook may not be as happy with you.
What to do if you spot an error on your credit report
When you review your credit report you may see an error that needs to be addressed immediately. You should report those errors as soon as you can to the group that issued your credit report so that a dispute may be filed with the lender. If you file a dispute the company must address that dispute within thirty days or by law the account must be removed from your credit report.
How to safeguard your credit
Family Lawyers in Houston: If you and your spouse opened any joint credit accounts (including credit cards) during the course of your marriage then you should close those accounts as soon as you are able to do so. Although this will keep any new charges from being assessed against the account, old balances do not go away. You and your spouse should pay that account off according to the terms of your Final Decree of Divorce. If your spouse fails to do so you must file an enforcement against him or her in court to gain an order from a judge that mandates that this be done.
The creditor will not close your account simply because it bears the names of two people that are no longer married. The law bars them from doing so. However, if you or your spouse ask them to close that account the creditor will do as you ask. What ends up happening a lot of times is that you as a single person will ask the creditor to allow your name to remain on the account as a single person. Not so fast, my friend. Many creditors will not allow you to do this and will instead make you re-apply for credit standing on your own two feet. If you have a mortgage in your and your spouse’s names you will likely have to refinance the mortgage into your name only in order to remove your spouse’s name from the obligation to pay on the house note.
What goes into making your credit score, anyways?
The exact formula that the credit reporting companies use to determine your specific credit score is unknown. We do, however, have a pretty solid understanding of what factors are looked at when determining your credit score.
As we noted earlier in today’s blog post your payment history is perhaps the most important factor that the credit reporting agencies consider when totaling your credit score. If you have made on time payments for all of your accounts you should expect to have a good credit score.
Next, the amounts that you owe are considered. If you owe a lot of money to creditors this may be seen as a negative especially if you have not been making huge payments towards the principle.
If you have been opening up a bunch of new accounts at once and those creditors are requesting copies of your credit report this will be a negative at least as far as your credit score is concerned. You may overleverage yourself in terms of debt compared to your income. Creditors will avoid lending to you if you have too many open accounts and have not shown a long history of making on time payments to each.
Finally, are your credit accounts secured or unsecured? A car loan is a secured loan because if you fail to abide by your contract with the lender the car can be repossessed. The creditor will at least be able to sell the car in order to compensate themselves. On the other hand, a credit card account is an unsecured debt. The credit card company cannot seize the items you purchased on credit.
Step out on your own and establish credit in your name only
Piggy backing off of what we were just discussing, you ought to try and get credit accounts in your name for no other reason to help build up your credit score. Credit cards and auto loans are two ways that prior clients of our office have done so in pretty quick fashion after the divorce was finalized. Keep in mind that I am only suggesting you do so if you already plan to continue to borrow money. To take a more radical approach you can swear off credit altogether and do your best to pay your debts and plan from that stage moving forward. I realize that this is not something many of you would agree to do, however.
Cash is king- why having ready access to greenbacks is important during and after your divorce
Houston Family Law Lawyer: A high credit score is nice, but having cash is nicer. Come back to the blog for the Law Office of Bryan Fagan, PLLC to discuss this topic in greater detail tomorrow.
In the meantime, please contact the Law Office of Bryan Fagan, PLLC with any questions regarding this or any other topic in family law. We offer free of charge consultations with a licensed family law attorney ... Continue Reading
#divorce#Divorce Attorney#divorce lawyer#family#Family Law#Family Law Attorney#fagan#attorney#attorneys#attorney lawyer#law#lawyer#Houston#houston texas#Houston law#Houston family law#Houston lawyers#texas lawyer#Texas
0 notes