#Hire Website Hacker
Text
Last week, the Lockbit ransomware group (one of the most active and professional groups of cyber criminals in the world) got hacked by the FBI. Lockbit's signature move is their public countdown timers for any company that got hacked, telling the world that company's files would be released if they didn't pay up. So the FBI put a countdown timer in their website, with the same design and style as the old Lockbit site, until they would release the name of the head of the organization.
Today, 2 days after the countdown timer expired (with no name being released as far as I'm aware), Lockbit finally released their own statement. it's pretty funny (Although, of course, take it with a grain of salt)
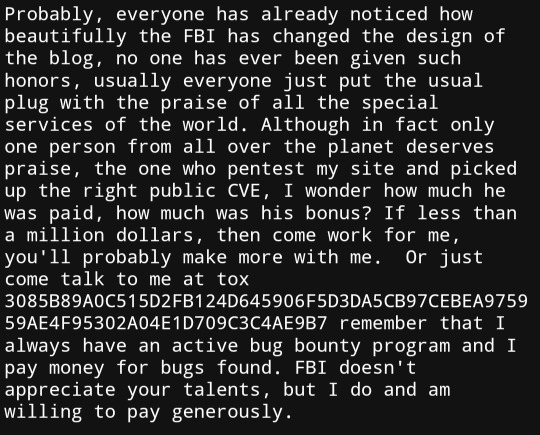
he claims that he may have information stolen from the Trump prosecution in Fulton county, and that's why the FBI hacked him. And now that this has taught him the vulnerabilities in his system, he needs to double down on hacking more government data:
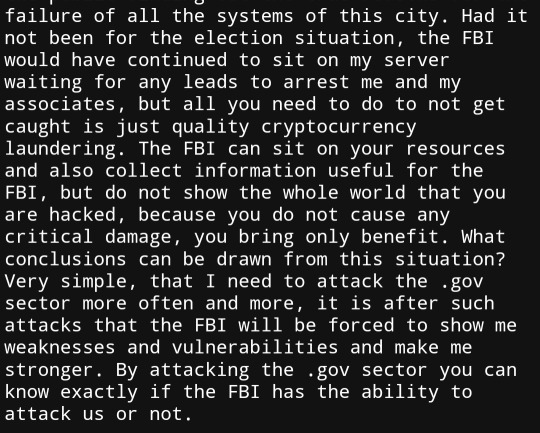
He also offers to hire the hacker who found the vulnerability in his system, saying that the FBI won't ever pay him the millions of dollars he's worth:

and their designer, because he thought the logo they put on the takedown site was super cool:
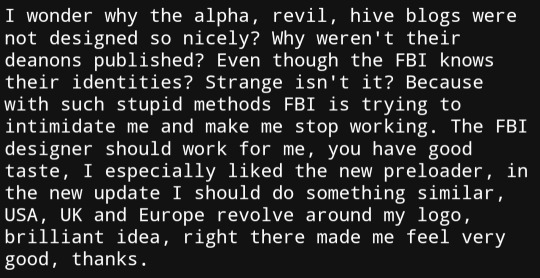
since we've seen so many bad examples of posting through it recently I thought I'd share one of the better examples of the genre. hope his security is as good as he thinks it is lmaooo
388 notes
·
View notes
Text
A link-clump demands a linkdump

Cometh the weekend, cometh the linkdump. My daily-ish newsletter includes a section called "Hey look at this," with three short links per day, but sometimes those links get backed up and I need to clean house. Here's the eight previous installments:
https://pluralistic.net/tag/linkdump/
The country code top level domain (ccTLD) for the Caribbean island nation of Anguilla is .ai, and that's turned into millions of dollars worth of royalties as "entrepreneurs" scramble to sprinkle some buzzword-compliant AI stuff on their businesses in the most superficial way possible:
https://arstechnica.com/information-technology/2023/08/ai-fever-turns-anguillas-ai-domain-into-a-digital-gold-mine/
All told, .ai domain royalties will account for about ten percent of the country's GDP.
It's actually kind of nice to see Anguilla finding some internet money at long last. Back in the 1990s, when I was a freelance web developer, I got hired to work on the investor website for a publicly traded internet casino based in Anguilla that was a scammy disaster in every conceivable way. The company had been conceived of by people who inherited a modestly successful chain of print-shops and decided to diversify by buying a dormant penny mining stock and relaunching it as an online casino.
But of course, online casinos were illegal nearly everywhere. Not in Anguilla – or at least, that's what the founders told us – which is why they located their servers there, despite the lack of broadband or, indeed, reliable electricity at their data-center. At a certain point, the whole thing started to whiff of a stock swindle, a pump-and-dump where they'd sell off shares in that ex-mining stock to people who knew even less about the internet than they did and skedaddle. I got out, and lost track of them, and a search for their names and business today turns up nothing so I assume that it flamed out before it could ruin any retail investors' lives.
Anguilla is a British Overseas Territory, one of those former British colonies that was drained and then given "independence" by paternalistic imperial administrators half a world away. The country's main industries are tourism and "finance" – which is to say, it's a pearl in the globe-spanning necklace of tax- and corporate-crime-havens the UK established around the world so its most vicious criminals – the hereditary aristocracy – can continue to use Britain's roads and exploit its educated workforce without paying any taxes.
This is the "finance curse," and there are tiny, struggling nations all around the world that live under it. Nick Shaxson dubbed them "Treasure Islands" in his outstanding book of the same name:
https://us.macmillan.com/books/9780230341722/treasureislands
I can't imagine that the AI bubble will last forever – anything that can't go on forever eventually stops – and when it does, those .ai domain royalties will dry up. But until then, I salute Anguilla, which has at last found the internet riches that I played a small part in bringing to it in the previous century.
The AI bubble is indeed overdue for a popping, but while the market remains gripped by irrational exuberance, there's lots of weird stuff happening around the edges. Take Inject My PDF, which embeds repeating blocks of invisible text into your resume:
https://kai-greshake.de/posts/inject-my-pdf/
The text is tuned to make resume-sorting Large Language Models identify you as the ideal candidate for the job. It'll even trick the summarizer function into spitting out text that does not appear in any human-readable form on your CV.
Embedding weird stuff into resumes is a hacker tradition. I first encountered it at the Chaos Communications Congress in 2012, when Ang Cui used it as an example in his stellar "Print Me If You Dare" talk:
https://www.youtube.com/watch?v=njVv7J2azY8
Cui figured out that one way to update the software of a printer was to embed an invisible Postscript instruction in a document that basically said, "everything after this is a firmware update." Then he came up with 100 lines of perl that he hid in documents with names like cv.pdf that would flash the printer when they ran, causing it to probe your LAN for vulnerable PCs and take them over, opening a reverse-shell to his command-and-control server in the cloud. Compromised printers would then refuse to apply future updates from their owners, but would pretend to install them and even update their version numbers to give verisimilitude to the ruse. The only way to exorcise these haunted printers was to send 'em to the landfill. Good times!
Printers are still a dumpster fire, and it's not solely about the intrinsic difficulty of computer security. After all, printer manufacturers have devoted enormous resources to hardening their products against their owners, making it progressively harder to use third-party ink. They're super perverse about it, too – they send "security updates" to your printer that update the printer's security against you – run these updates and your printer downgrades itself by refusing to use the ink you chose for it:
https://www.eff.org/deeplinks/2020/11/ink-stained-wretches-battle-soul-digital-freedom-taking-place-inside-your-printer
It's a reminder that what a monopolist thinks of as "security" isn't what you think of as security. Oftentimes, their security is antithetical to your security. That was the case with Web Environment Integrity, a plan by Google to make your phone rat you out to advertisers' servers, revealing any adblocking modifications you might have installed so that ad-serving companies could refuse to talk to you:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai
WEI is now dead, thanks to a lot of hueing and crying by people like us:
https://www.theregister.com/2023/11/02/google_abandons_web_environment_integrity/
But the dream of securing Google against its own users lives on. Youtube has embarked on an aggressive campaign of refusing to show videos to people running ad-blockers, triggering an arms-race of ad-blocker-blockers and ad-blocker-blocker-blockers:
https://www.scientificamerican.com/article/where-will-the-ad-versus-ad-blocker-arms-race-end/
The folks behind Ublock Origin are racing to keep up with Google's engineers' countermeasures, and there's a single-serving website called "Is uBlock Origin updated to the last Anti-Adblocker YouTube script?" that will give you a realtime, one-word status update:
https://drhyperion451.github.io/does-uBO-bypass-yt/
One in four web users has an ad-blocker, a stat that Doc Searls pithily summarizes as "the biggest boycott in world history":
https://doc.searls.com/2015/09/28/beyond-ad-blocking-the-biggest-boycott-in-human-history/
Zero app users have ad-blockers. That's not because ad-blocking an app is harder than ad-blocking the web – it's because reverse-engineering an app triggers liability under IP laws like Section 1201 of the Digital Millenium Copyright Act, which can put you away for 5 years for a first offense. That's what I mean when I say that "IP is anything that lets a company control its customers, critics or competitors:
https://locusmag.com/2020/09/cory-doctorow-ip/
I predicted that apps would open up all kinds of opportunities for abusive, monopolistic conduct back in 2010, and I'm experiencing a mix of sadness and smugness (I assume there's a German word for this emotion) at being so thoroughly vindicated by history:
https://memex.craphound.com/2010/04/01/why-i-wont-buy-an-ipad-and-think-you-shouldnt-either/
The more control a company can exert over its customers, the worse it will be tempted to treat them. These systems of control shift the balance of power within companies, making it harder for internal factions that defend product quality and customer interests to win against the enshittifiers:
https://pluralistic.net/2023/07/28/microincentives-and-enshittification/
The result has been a Great Enshittening, with platforms of all description shifting value from their customers and users to their shareholders, making everything palpably worse. The only bright side is that this has created the political will to do something about it, sparking a wave of bold, muscular antitrust action all over the world.
The Google antitrust case is certainly the most important corporate lawsuit of the century (so far), but Judge Amit Mehta's deference to Google's demands for secrecy has kept the case out of the headlines. I mean, Sam Bankman-Fried is a psychopathic thief, but even so, his trial does not deserve its vastly greater prominence, though, if you haven't heard yet, he's been convicted and will face decades in prison after he exhausts his appeals:
https://newsletter.mollywhite.net/p/sam-bankman-fried-guilty-on-all-charges
The secrecy around Google's trial has relaxed somewhat, and the trickle of revelations emerging from the cracks in the courthouse are fascinating. For the first time, we're able to get a concrete sense of which queries are the most lucrative for Google:
https://www.theverge.com/2023/11/1/23941766/google-antitrust-trial-search-queries-ad-money
The list comes from 2018, but it's still wild. As David Pierce writes in The Verge, the top twenty includes three iPhone-related terms, five insurance queries, and the rest are overshadowed by searches for customer service info for monopolistic services like Xfinity, Uber and Hulu.
All-in-all, we're living through a hell of a moment for piercing the corporate veil. Maybe it's the problem of maintaining secrecy within large companies, or maybe the the rampant mistreatment of even senior executives has led to more leaks and whistleblowing. Either way, we all owe a debt of gratitude to the anonymous leaker who revealed the unbelievable pettiness of former HBO president of programming Casey Bloys, who ordered his underlings to create an army of sock-puppet Twitter accounts to harass TV and movie critics who panned HBO's shows:
https://www.rollingstone.com/tv-movies/tv-movie-features/hbo-casey-bloys-secret-twitter-trolls-tv-critics-leaked-texts-lawsuit-the-idol-1234867722/
These trolling attempts were pathetic, even by the standards of thick-fingered corporate execs. Like, accusing critics who panned the shitty-ass Perry Mason reboot of disrespecting veterans because the fictional Mason's back-story had him storming the beach on D-Day.
The pushback against corporate bullying is everywhere, and of course, the vanguard is the labor movement. Did you hear that the UAW won their strike against the auto-makers, scoring raises for all workers based on the increases in the companies' CEO pay? The UAW isn't done, either! Their incredible new leader, Shawn Fain, has called for a general strike in 2028:
https://www.404media.co/uaw-calls-on-workers-to-line-up-massive-general-strike-for-2028-to-defeat-billionaire-class/
The massive victory for unionized auto-workers has thrown a spotlight on the terrible working conditions and pay for workers at Tesla, a criminal company that has no compunctions about violating labor law to prevent its workers from exercising their legal rights. Over in Sweden, union workers are teaching Tesla a lesson. After the company tried its illegal union-busting playbook on Tesla service centers, the unionized dock-workers issued an ultimatum: respect your workers or face a blockade at Sweden's ports that would block any Tesla from being unloaded into the EU's fifth largest Tesla market:
https://www.wired.com/story/tesla-sweden-strike/
Of course, the real solution to Teslas – and every other kind of car – is to redesign our cities for public transit, walking and cycling, making cars the exception for deliveries, accessibility and other necessities. Transitioning to EVs will make a big dent in the climate emergency, but it won't make our streets any safer – and they keep getting deadlier.
Last summer, my dear old pal Ted Kulczycky got in touch with me to tell me that Talking Heads were going to be all present in public for the first time since the band's breakup, as part of the debut of the newly remastered print of Stop Making Sense, the greatest concert movie of all time. Even better, the show would be in Toronto, my hometown, where Ted and I went to high-school together, at TIFF.
Ted is the only person I know who is more obsessed with Talking Heads than I am, and he started working on tickets for the show while I starting pricing plane tickets. And then, the unthinkable happened: Ted's wife, Serah, got in touch to say that Ted had been run over by a car while getting off of a streetcar, that he was severely injured, and would require multiple surgeries.
But this was Ted, so of course he was still planning to see the show. And he did, getting a day-pass from the hospital and showing up looking like someone from a Kids In The Hall sketch who'd been made up to look like someone who'd been run over by a car:
https://www.flickr.com/photos/doctorow/53182440282/
In his Globe and Mail article about Ted's experience, Brad Wheeler describes how the whole hospital rallied around Ted to make it possible for him to get to the movie:
https://www.theglobeandmail.com/arts/music/article-how-a-talking-heads-superfan-found-healing-with-the-concert-film-stop/
He also mentions that Ted is working on a book and podcast about Stop Making Sense. I visited Ted in the hospital the day after the gig and we talked about the book and it sounds amazing. Also? The movie was incredible. See it in Imax.
That heartwarming tale of healing through big suits is a pretty good place to wrap up this linkdump, but I want to call your attention to just one more thing before I go: Robin Sloan's Snarkmarket piece about blogging and "stock and flow":
https://snarkmarket.com/2010/4890/
Sloan makes the excellent case that for writers, having a "flow" of short, quick posts builds the audience for a "stock" of longer, more synthetic pieces like books. This has certainly been my experience, but I think it's only part of the story – there are good, non-mercenary reasons for writers to do a lot of "flow." As I wrote in my 2021 essay, "The Memex Method," turning your commonplace book into a database – AKA "blogging" – makes you write better notes to yourself because you know others will see them:
https://pluralistic.net/2021/05/09/the-memex-method/
This, in turn, creates a supersaturated, subconscious solution of fragments that are just waiting to nucleate and crystallize into full-blown novels and nonfiction books and other "stock." That's how I came out of lockdown with nine new books. The next one is The Lost Cause, a hopepunk science fiction novel about the climate whose early fans include Naomi Klein, Rebecca Solnit, Bill McKibben and Kim Stanley Robinson. It's out on November 14:
https://us.macmillan.com/books/9781250865939/the-lost-cause

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/11/05/variegated/#nein
#pluralistic#hbo#astroturfing#sweden#labor#unions#tesla#adblock#ublock#youtube#prompt injection#publishing#robin sloan#linkdumps#linkdump#ai#tlds#anguilla#finance curse#ted Kulczycky#toronto#stop making sense#talking heads
137 notes
·
View notes
Text
Nooo I just saw some guys make a conspiracy theory that there weren't hackers in the Ao3 DDOS attack and it was actually Ao3 trying to get more money 💀
Do they realise Ao3 has to declare everything they do? OTW ia a non-profit organisation that is tax reducible in the US, they won a Hugo award. They're more than well known and are probably well observed. What do you think they're doing with the money???? You can literally see their financial expenses!
"Why are people saying they're gonna donate since that money isn't going to the UNPAID volunteers 🙁" I donate because donating money means the website can remaim FUNCTIONING. Because it's a service that I and a lot of use for free. Because servers cost MONEY. Because domains cost MONEY. Because sometimes they might need to hire some outsiders to fix something or do something the volunteers aren't able to do. Because they have to host a very big amount of works AND be able to have a lot of users on the website at the same time, because they have to keep some saved in case they have to fight in court for something!!! Because if you follow Ao3's TOS and some company decided to try to use copywrite against you and claiming you're stealing their money Ao3 will go to court for you!!!!
I have seen a lot of stupid conspiracy theories and this one is definitely one of them.
#gle original#ao3#archive of our own#discourse#The extra money just goes for the next year#Also if Ao3 was lying the website wouldn't just be back just to promptly go down some time later multiple times#🤦♀️
101 notes
·
View notes
Note
i don’t go here but what happened to penelope garcia’s hair ? isn’t it like shoulder length ? did she cut it ? !
/lh , tell me about penelope garcia please ?

Yay! I love talking about babygirl! Ok, so it looks like she did indeed cut her luscious locks so rip to her long princess curls. They will be missed until they grow back. 💖
Ok, so season 1-15 Penelope was MY GIRL, ok? She was MY GIRL.
She's, like, a super genius super cutie and she's super sweet and kind and loves animals. (Seriously, one of the reasons she started working for the FBI is she was a computer hacker and hacked into the website of a cosmetic company that tests on animals and her options when she got caught were literally work for the FBI or her ass is getting thrown in prison. She chose the FBI. We love a queen that fights for animal wellfare. The other reason was she wanted to get away from her garbage, and I do mean GARBAGE, boyfriend and have a better life.)
I'm pretty sure she has ADHD. Maybe autism. IDK, but she's definitely some kinda neurospicy.
She's a walking sparkly neon rainbow. You know the way Flynn's bedroom is described in the one jatp book? Season 1-15 Penelope is that and I love it.
She went ginger once and it was a whole vibe.

Wow, I love her.
She was super nice to her ex boss all the way from s1 to his departure in early s12, and I'm 99% sure was the only one that actually called him bossman or sir bc everyone else just called him Aaron or by his nickname, Hotch. She was really good at making him smile, which actually wasn't that hard but people exaggerate the rarity of a Hotch smile for some reason.

After that, she was still really nice to the replacement he handpicked, Emily Prentiss, who she already adored after working with her since s2.

Hotch was literally physically incapable of saying no to this woman and she fully knew and took advantage of that shit, ok? Seriously, one time, Penelope made a joke like "who could say no to me?" and Hotch just smirked a little bit because he knew he couldn't say anything. Penelope does an incredible imitation of the pleading emoji. Or the Puss In Boots face. Whatever you wanna call this:


"Boss, I want you to hire Tara. 🥺" "Ok. Tell everyone else the position has been filled." "Boss, I don't wanna eat dinner alone. Do you want a veggie omelette? 🥺" "Ok. Do you have jalapeños?"
The hilarious thing is she doesn't even have to make that face. She does it to mess with him.
And then there's her, uh...... interesting little flirtationship with Derek Morgan. Or as Penelope calls him, chocolate thunder. He loves that name and encourages it. He calls her babygirl. They also have about a million other adorable pet names for each other.


*gestures at these gifs* They love each other so much, it's kind of gross. I've said before that before I actually started watching and only had the massive comp of him calling her that, I genuinely really thought Morcia was canon. Like, oh, my GOD, dude. These two are disgustingly obsessed with each other. The shit they say on work calls. He calls her sexy and brilliant Goddess and told her it drives him crazy when "she talks that voulez coucher stuff to him". Like, hello? Honestly, I'm amazed Derek only had to sit through one HR lecture about creating a hostile work environment. Or at least, we only saw one.
Then there's her very sweet friendship with baby genius, boy wonder, good doctor, Agent Doctor Spencer Reid.

MY BABIES. I LOVE THEM. I want them back. Gimme back my Penny², damnit.
And her very sweet friendship with Matt Simmons! Oh, my god. I love them. 🥰🥰🥰

They're cute and I wish at least Penelope mentioned Matt in season 16 more.
Penelope and Luke! Oh, my God. Penelope and Luke.

They are in love and both think it's unrequited and it's exhausting but at least s12-15 were FUN. Mostly.
Season 16 Penelope, though....

Season 16 Penelope got abducted by aliens. Or lobotomized. Hard to tell.
#criminal minds#criminal minds evolution#penelope garcia#i'd go more in depth but this got long oops#i just love her
13 notes
·
View notes
Text
Peter: I need to go apartment shopping. I can't stay here when my new arch-nemesis knows where I live.
Wade: I could come with you. Give you some professional advice on...security.
Peter: Professional advice, huh? From a professional criminal?
Wade: Hey, baby, nobody knows the business better than me. Want to make your website secure, hire a white-hat hacker. Want to make your apartment secure, hire the guy who broke in and kidnapped you.
Peter: *Massive eye roll*
From Bed Bugs
99 notes
·
View notes
Text
10 Ways to Spy on Your Cheating Partner

If you want to know the truth, you’ll need to learn how to catch a cheating partner. It seems so simple in the movies, where you just walk in on them in the moment and everything is suddenly out in the open communication. The reality is, trying to catch a cheating wife or husband is usually a lot more complicated, so you may want to consider these 10 different ways to spy on your partner, including everything from spy apps to hiring a private investigator in Melbourne.
Related Blog : How To Hire A Hacker To Catch Cheating Spouse
All that being said, please note that spying on your partner should be a last resort. The best way to know if your partner is cheating is to have an open and honest conversation with them about it. However, confronting a cheater may not be realistic for you if your relationship was already unhealthy and you can’t count on your partner to be honest.
Trying to confront someone about cheating without having any evidence to back up your claims may just make it easier for them to lie. So, if you’re certain that a conversation won’t get you anywhere, consider trying these 10 spying methods:
1. KEEP AN EYE ON THEIR PHONE
It’s not a new idea to spy on your partner’s phone for proof of infidelity. Catching a cheating partner is pretty easy when you can check their call logs and text messages. However, it’s quite common for people to have their phones locked, meaning you’ll need to keep your eye on their phone to watch for push notifications.
Some cheaters opt for the convenience of a second phone. They may refer to it as a “work” or “emergency” phone, or hide it altogether. They may even go so far as purchasing a separate SIM card for their unfaithful activities, which you can actually extract data from if you happen to see one lying around.
2. TRACK THEIR WHEREABOUTS USING LOCATION TRACKING TECHNOLOGY
If the idea of physically following somebody makes you feel bad or uncomfortable, there’s a simple alternative. Using location tracking technology, you can find your partner’s location on iCloud in just a few steps. You both need to have Apple devices connected to the same family account and have location sharing enabled, which you can then access by logging into hackerslist.co and clicking on Find My iPhone.
If you don’t have devices connected to the same account or the right settings enabled, you can also use GPS. Google users can view someone’s location history in the “previous destinations” menu option. Android users can use a similar approach using the Google Timeline feature in Google Maps.
If your devices don’t permit you to use these methods, you can opt for hiring a private investigator. A private investigator, which we’ll discuss further momentarily, can help physically locate a person in a way that’s 100 per cent legal and confidential.
3. TEST YOUR SEARCH ENGINE’S AUTO-FILL
Checked your partner’s search history but couldn’t find anything suspicious? If they really are cheating on you, they likely know well enough to erase the search history on their browsers. That means you won’t ever be able to find hook-up services or other incriminating websites in their history, even if you check regularly.
Though most people know to clear their search history, they may have neglected to erase their auto-fill history. Search engines like Google and Bing offer guesses when you start searching for things, all based on your past searches. Try typing various letters into your search bar and wait to see what the search engine fills in (ex: type “ash” and you may find the notorious cheating site Ashley Madison popping up).
4. LOOK THROUGH THEIR DIGITAL AND ACTUAL TRASH BIN
Similar to erasing search history but not auto-fill history, your partner may have put compromising documents in the digital trash but forgotten to empty it. If you share a computer with your partner, make a habit of checking the trash bin and restoring and reading documents that look suspicious. Files could be titled in a way that’s very obvious OR in a way that’s oddly mundane like “work”.
If you’re willing to do something slightly more unpleasant, you could also take a peek through your partner’s actual trash bin. You may end up finding incriminating receipts, love notes, or other documents that help you learn the truth. If you’re not up to this task, contacting a private investigator will save you a lot of stress down the road.
5. SET UP A HIDDEN SPY CAMERA
If you’re looking for equipment to catch a cheating spouse, you’re truly spoiled with options. There are various spy devices for cheating spouses that are subtle and effective. This includes motion activated spy cameras and hidden cameras designed as regular household objects like smoke detectors and speakers.
When it comes to the most affordable cheating spouse spy equipment, however, there’s nothing better than a baby monitor. Simply hide it well in the room where your partner spends most of their time alone. You can then use the monitor to watch and/or listen to their activities in real-time when you think they may be up to something.
Spying devices like these are seriously the worst nightmare of cheating husbands and wives, so long as you pick the right one and set it up in the right location.
6. INSTALL SECRET SPY APPS
Did you know you could catch a cheating spouse using an app? People use cheating apps to be unfaithful, so it’s only right that there be spy apps for cheating spouses. Simply download one of these apps onto your partner’s phone, and you’ll be able to see what letters they type, what pages they visit, and even the passwords that they use.
There’s a wide range of apps to spy on your spouse, some of which you’ll have to pay for and some that are free. If you hope to catch your spouse cheating using an app of this variety, you’ll just have to ensure that the app offers the surveillance you’re looking for. For example, if you think your spouse is using cheating sites, choose an app that records what websites they visit rather than one that tracks phone calls.
7. BUY A LANDLORD RECORDER
Wondering how to catch a cheating husband or wife using your home phone? If you have a landline, you can purchase a landline recorder that allows you to record both sides of a conversation over the phone. To bug your landline, all you have to do is connect the recorder to a BT style landline phone socket and wait until the time is right to listen back to the recording.
If you’d rather not bug your landline, eavesdropping is a more straightforward and cost-effective alternative. Putting your ear against the door probably won’t be enough, but you can purchase or use an existing spare phone and connect it into an available phone jack. Place the spare in a part of the house that your spouse rarely goes to ensure that you have a private listening spot when they answer the phone elsewhere in the house.
Before eavesdropping, remember to unscrew and remove the phone’s mouthpiece first. This will prevent any slight noises on your end from being heard over the phone. If this isn’t an option, be prepared to stay calm and stay still for the entirety of the conversation.
8. STEALTHY VOICE RECORDER
Baby monitors and landline recorders are effective ways of spying on your partner. That being said, they’re not things you can just have out in the open. If you need a voice recorder that you can place on a desk, in your partner’s car, or somewhere in the house, there are several stealthy voice recorders to choose from.
You should choose your stealthy voice recorder based on the method you think your partner is using to cheat on you. For example, a key fob recorder is ideal if you think your partner is meeting up with people inside their car. Think they’re cheating on you with one of their co-workers? Place a voice recording pen into one of their pen organisers.
9. MONITORING SOFTWARE
If you’d like to go beyond the somewhat limited and not always inconspicuous spy apps, you can opt for state of the art monitoring software. Spy software is a highly effective way of monitoring your partner’s activities, whether it be on their phone, their laptop, or any other device. A private investigator can get you access to this software and ensure that it’s installed on the target.
There are multiple benefits to monitoring software over simpler apps and devices. The most notable of these benefits is that you’ll have access to far more information than ever before. This includes the ability to review installed applications, track their location, record phone calls, and monitor their social media.
Spying on your partner to this degree isn’t something to take lightly. That being the case, working with a professional is essential to keeping things legal and ethical. They can install the software, provide you with frequent alerts and reports, and ensure that everything is above board.
10. HIRE A PRIVATE INVESTIGATOR
The most reliable and efficient way to find out if your partner is cheating on you is to hire a private investigator. A private investigator knows how to get you the answers you’re looking for in a way that’s ethical, legal, and confidential. They can offer various professional methods for spying on your spouse, including following them, recording their actions using high-quality equipment, and much more.
With the right private investigator, you’ll have a guaranteed agreement of confidentiality. This saves you the risk of getting caught, which is a possibility with all the other methods listed above. Of course, the best part about hiring a private investigator is that they’ll be able to offer both physical evidence and their own expertise and perspective.
It may not always be the answer you want to hear, but a private investigator can offer an unbiased assessment of the situation for you. That in itself is incredibly valuable when you’re dealing with such an emotional and stressful topic. That all being said, it’s essential to choose a private investigation firm that’s licenced, experienced, and trained in covert surveillance.
HIRE A HACKER
6 notes
·
View notes
Text
BROWSERS, ADBLOCKERS AND OTHER ADDONS
tl;dr: Use LibreWolf and install CleanURLs, or if not, use uBlock Origin and CleanURLs on whatever browser you use.Librewolf : https://librewolf.net/uBlock Origin : https://ublockorigin.com/CleanURLs : https://github.com/ClearURLs/Addon
BROWSERS:
I will not start an argument about the necessity of privacy respecting browsers, I assume if you're reading this rambling of mine about the subject you're at least partially interested in not leaking all your data to the internet. Most browsers you'll encounter are leaky, and they will give your data to 3rd parties, either by poor design or implementation or knowingly and happily for money, but some browsers are just more leaky than others, so your choice of browser matters.
Apart from the ethical issues that uncontrollable data selling raises, online ads, tracking cookies and these tracking methods lead to a slower internet, higher processor and memory requirements, a messy design of webpages, and a plethora of other security issues and opportunities for bad actors ("hackers"). The sheer number of so-called attack vectors that web browsing presents is astounding.
Just to give a brief image of it, visit the site https://privacytests.org/, it will show you a comparison of web browsers on their performance of not leaking stuff to other people. The different tests are performed daily, and the website is rather informative about these tracking methods, attack vectors. Some part may be less important to you (Tor capabilities for example), so not all privacy respecting features are created equal, but this is the closest you'll ever get to an open and easily digestable learning material on browser privacy.
At the time of writing the best option for daily use is LibreWolf, basically a fine-tuned Firefox. It also has a lot of features for advanced users, but is generally easy to use, with built in uBlock Origin, and javascript disabled (which you may want to enable for certain web pages).You may want to know that certain browsers are tracking your movement and build a profile on you without ever visiting any webpage, and this category includes Firefox, and Chromium as well.
ADBLOCKERS:
Most adblockers have long sold their souls to the devil, and they are the ones collecting data on you, and some of them are purposefully not blocking certain ads, go figure. A lot of them are not open source, or not even open on their business pactices. You wouldn't hire a security company to protect your business who has a sketchy and non-transparent working, and who you cannot verify that they are not accepting money from the Chinese Communist Party, would you? The easy answer is to use uBlock Origin, an open source, transparent, free as in freedom software, with a completely transparent working, and verifiable everything. Please note that uBlock and uBlock Origin are not the same adblocker, and the regular uBlock has been bought by - guess what - an advertising company.
CleanURLs: Sometimes when you receive a youtube link, and you click on in, instead of youtube.com/watch?=xxxxxxx you'll get a ten times longer link with fbclid and really long alphanumerical stuff, isn't it weird? Does this link need to be this long to function? Well, the answer is no. It's just one of the tricks how websites track you with even more unnecessary cookies, that try to follow you from site A to site B (for example to figure out which youtube account belongs to which facebook user to make even more targeted ads). You can manually delete all those cross-site tracking stuff from every link you use but it's a tedious, but easily automated task. That's where CleanURLs come in, to do this instead of you. You'll be surprised how many tracking attempts are blocked in a day by this stuff.May these tools bring you a faster and cleaner internet experience.
18 notes
·
View notes
Note
so, deuxmoi podcast ad popped up for me on spotify today (have no idea why, i never listened before) and i saw louis' name there and was like: what now?!! asked to my friend who usually listens what was about and here's what they said if anyone wants to know:
they talked to backgrid owner, basically reinforcing how all their sights are legit and not planned lol told crazy stories to justify paps being in the strategic places, mentioned holivia, that coincidentally two paps were in sta barbara and got jeff wedding pics LMAOO - nothing about the closed private place or the drones - just talked a bunch of bs that they get these shots cause they're the best and only minor celebs hire them. commented about louis and sofie pics being on twitter before the website and said it was a hacker, probably an overprotective fan, that they reinforced security and were going to take down fan accounts. also that he got upset cause it would be a great exclusive for them 🙄 lastly they talked same bs about the O/E/H 3some, that never happened but somehow everyone and their mother knew, implied emrata was the one spilling this all around. said H and O were talking again constantly and had agreed on a open relationship for a while LMFAOOO but that didn't include make out with her friend so now O is done with H..
that's it, nothing too interesting but just to give a heads up if you start to see people talking or sending asks about it
Thanks anon.
Deuxmoi is so full of shit. All of this, ALL, sounds like absolute bullshit. They’re just lying. It’s not even funny. They fully take us as complete idiots.
And she has some nerve saying somehow everyone knows about this fake 3some, WHEN SHE’S THE ONE WHO SPREAD THE INFO AND LIT THE FIRE ABOUT THIS RUMOR FOR *MONTHS*. And then this week she was like “oh a very reliable source said it’s a lie”. But the week before she was like “a very reliable source told me it happened so I believe it”. 😒😒😒😒 THERE IS NO SOURCE. MUCH LESS A RELIABLE ONE. DEUXMOI IS JUST LYING AND SPREADING STUPID RUMORS BC SHE’S AN ASSHOLE.
Also, she has some nerve spreading Backgrid’s fake ass propaganda. It’s obvious they’re lying thru their teeth. It was scheduled. It was private property. They couldn’t have just accidentally wandered into a closed country club and gotten all of those pictures. Be serious. They take people as absolute idiots. Like????? They really think we’re actually stupid clowns 🤡
😒😒😒😒😒😒😒😒
Unrelated but I heard the backgrid part and I cannot stand deuxmoi’s voice. She sounds like the most obnoxious person in the world. And she’s so aggressive in her tone and demeanor. She’s just awful
38 notes
·
View notes
Text
Best Private Investigator To Monitor Your Partner’s Phone
Uncover secrets with our expert private investigator services. Monitor your partner's phone discreetly for peace of mind and clarity.

👉Related Blog: Spy on Your Cheating Spouse at Official Meeting by Private Investigator
In today's world, where trust issues in relationships are becoming increasingly common, the need for surveillance and investigation services has surged. Private investigators play a crucial role in providing discreet and professional monitoring services, especially when it comes to monitoring a partner's phone activity. This article aims to explore the best private investigator agencies that offer phone monitoring services and provide insights into why hiring them could be beneficial.
🟢Why Hire a Private Investigator?
Healthy Relationships are built on trust, but when doubts arise, it can be challenging to maintain that trust. Hiring a private investigator offers a discreet solution to uncovering the truth without breaching legal boundaries. These professionals are trained in surveillance techniques and have the expertise to gather evidence ethically.
🟢Qualities to Look for in a Private Investigator
When searching for a private investigator, it's crucial to prioritize certain qualities to ensure you hire the right professional for the job. Here are some essential qualities to look for:
📗Experience: A seasoned investigator brings valuable expertise and insight to the table, increasing the likelihood of a successful outcome.
📗Discretion: Confidentiality is paramount in investigations. A trustworthy investigator knows how to handle sensitive information with utmost discretion.
📗Communication Skills: Effective communication is essential for gathering information and building rapport with clients, witnesses, and other relevant parties.
📗Analytical Skills: An investigator with strong analytical abilities can interpret data, identify patterns, and draw meaningful conclusions to support the investigation.
📗Resourcefulness: A resourceful investigator can adapt to challenges, employ creative problem-solving techniques, and leverage available resources to achieve the desired results.
By prioritizing these qualities, you can find a private investigator who is capable, trustworthy, and equipped to handle your case effectively.
🟢Types of Services Offered
Private investigators offer a range of services, including: phone monitoring, background checks, and GPS tracking. Phone monitoring, in particular, allows clients to access call logs, text messages, and browsing history discreetly.
🟢Factors to Consider Before Hiring
When choosing a private investigator, reputation, cost, and confidentiality are vital considerations. It's essential to research the agency thoroughly and discuss confidentiality agreements to protect sensitive information.
🟢Top Private Investigator Agencies
Several agencies specialize in surveillance and investigation services. Agency A, Agency B, and Agency C are among the top choices known for their professionalism and discretion in handling sensitive cases.
🟢How to Approach Hiring a Private Investigator
The process of hiring a private investigator typically begins with an initial consultation to discuss the client's goals and expectations. Once a contract is signed, the investigation process begins, with regular updates provided to the client.
🟢How to Register to get the service
They have a secure procedure. You have to go to their website.
✅Step one: You need to post a job about your problem.
✅Step two: After posting a job, you get a verification message. You must complete the verification method. Otherwise, your job will not be posted. After completing the process, HackersList assigns their hackers, who are experts, to solve your problem.
💠Finishing Word
Hiring a private investigator to monitor your partner's phone can provide valuable insights and peace of mind in uncertain situations. By choosing a reputable agency and understanding the legal and ethical considerations involved, clients can navigate trust issues in relationships effectively.
#private investigator#private investigation agency#cybersecurity#hackerslist#hacking#hackers#hackerslistco#hacker#us hackers#whitehat#social media hackers
3 notes
·
View notes
Text
What to do when you spot a broken website
I am a very firm believer in either sticking to your principles or update them.
So when I got this error while I tried to search for C/C++ on my national job portal:
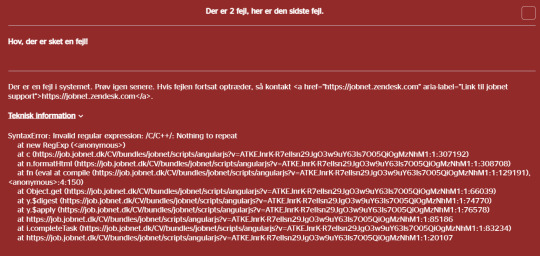
My first thought was "Huh, that is sorta funny" (especially since the code to show me the email address to report this error to was ALSO broken... meaning that whoever made the code that should run if the website broke... never tested it).
And then I realized what I was looking at.
And at that point I think I had a ethical duty to notify people to get this fixed. FAST.
Why?
It comes under "You are responsible for your choices". With it being understood that doing nothing is also a choice, and that taking a job where you work for, and help a company with doing evil is NOT a choice, if that is the only job you could get (IE, you did not have the power/money/mental health/time to make a choice)
It is now fixed*, so I wanted to make this post for all in the little codeblr community doing any front-end work. Web or not. With 3 lessons to learn from this.
First thing to get from this: "Everyone makes mistakes". This is one of the reason good code is not code without errors. It is code where it is easy to make changes and fix errors. You then try to find as many errors as you can with code reviews, automated testing, having a work environment that does not punish human errors( which encourages people to HIDE errors ) and so on.
Second thing: "Sanitize your user input. Always". Write code that assumes that every single user wants nothing more than to break your code and exploit its vulnerabilities.
This had NOT been done here. This error shows that characters in the string that was made from my search terms, was being run as code.
As in, I, or anyone else, could run code in the middle of this javascript code. Meaning it is possible that someone could write code as part of their search that would make the javascript code do... whatever they wanted to. Including deleting the entire backend database. Or steal the info.
This is why you ALWAYS sanitize your user input. Basically encode all potentially dangerous characters as something else while working on them. There are libraries like validator.js and express-validator that will do it for you, if you use javascript.
And the third thing. "Do NOT investigate further" . As soon as you confirm that your user input gets treated as code, you contact whoever is running it. If they do not take the threat seriously and it is still there after a week or two, contact established press with this info.
You may read about so called grey hat hackers, who unlike black hat hackers(who is people wishing to do harm) or white hat hackers(Who are hired to try to break into a companies software to test it), are trying to find security flaws with good intentions, but are unaffiliated with whoevers code they are trying to break into.
In an ideal world, doing that, and then contacting the company, SHOULD result in the company thanking them . But often it also leads to the company suing. And winning. Since breaking in to show that it is possible, is technically still breaking in.
So do NOT start testing what you are able to do with the exploit you found. Report it to them, and check a weeks time later if it is fixed. If it keeps being vulnerable, contact the press.
The site fixed this error after half a week. But they did it, not by encoding the dangerous characters into something else, but to simply remove them all from the user input string.
Meaning that I still cannot search for "C++". Now I just get any job that contains the letter "C"... I mean... it is better...
So if you take user input, and it does not brick your code in dangerous ways. You are doing better than whoever coded this for the Danish State :p
12 notes
·
View notes
Text
Hire A Hacker To Spy On Cheating Partner
Do you feel like your partner is cheating on you? would you love to spy on cheating spouse without them ever knowing ? We are here to help you Hire a hacker today and clear your doubts. Here at Pro Hackers we have professional hackers with years of experience that will help you spy on cheating partner without them ever knowing . We also provide the following services.
Hire a reliable hacker today
Contact Us :
Whatsapp Number: +1 903 600 5418
WICKR ID: @prohackers2014
Tellegram : @prohackers2014
Hire a hacker in USA
Hire a hacker in the United States
Hire a hacker in Canada
Hire a hacker in Australia
Hire a hacker in United Kingdom
Hire a hacker in London
Hire a hacker in USA
Hire a hacker in the United States
Hire a hacker in Canada
Hire a hacker in Australia
Hire a hacker in United Kingdom
Hire a hacker in London
hire a hacker
how much does it cost to hire a hacker
hire a hacker reviews
hire a hacker fiverr
hire a hacker online reviews
hire a hacker reddit 2022
hire a hacker 2022
hire a hacker to recover instagram
hire a hacker to recover an account
hire a hacker to erase criminal record
hire a hacker to change your grades
hire a hacker to recover an account reddit
is there a way to hire a hacker
hire a hacker to catch a scammer
best place to hire a hacker
hire a hacker to get your account back
hire a hacker in bangladesh
reasons to hire a black hat hacker
hire a hacker in bangalore
can you hire a black hat hacker
hire a hacker canada
hire a hacker cheap philippines
hire a hacker cheap india
hire a crypto hacker
hire a chinese hacker
hire a hacker to change university grades
hire a hacker in chennai
can you hire a hacker on fiverr
can you hire a hacker reddit
does hire a hacker work
hire a hacker in delhi
what happens when you hire a dark web hacker
how to hire a hacker on the dark web reddit
hire a hacker to take down a website
how much does it cost to hire a professional hacker
hire a hacker event
hire a hacker email address
hire a hacker easy
hire a hacker eventbrite
hire a hacker ethical
hire a hacker en español
hire a hacker en free fire
hire a hacker etica
hire a hacker english
hire a hacker entre
hire a ethical hacker
hire a hacker in egypt
hire a hacker experience
can you hire an ethical hacker
does microsoft hire ethical hackers
hire a hacker for social media india
hire a hacker for roblox
hire a hacker forum
fiverr hire a hacker
hire a hacker to fix credit score
hire a hacker game
hire a hacker github
hire a hacker gta 5
hire a hacker guide
hire a hacker gta
hire a hacker gets your ip address
hire a hacker gives you money
hire a hacker gif
hire a hacker growth
hire a hacker girl
hire a game hacker
how to hire a hacker to change school grade
how to hire a hacker to change your school grade
how to hire a hacker in pakistan
how to hire a hacker to catch cheating spouse
how to hire a hacker in roblox
how to hire a hacker in philippines
how to hire a hacker to hack instagram
hire a hacker in pakistan
hire a hacker in kolkata
is it illegal to hire a hacker
is it legal to hire a hacker
is hire a hacker legit
where can i hire a hacker reddit
hire a hacker jobs
hire a hacker jailbreak
hire a hacker javascript
hire a hacker jenna
hire a hacker jurassic park
hire a hacker jennifer
hire a hacker join
hire a hacker jelentése
i hired a hacker
hire a hacker kas
hire a hacker key
hire a hacker kr
hire a hacker klm
hire a hacker king
hire a hacker known as 4chan
hire a hacker kayak
hire a hacker kid
hire a hacker kitchen
hire a hacker malaysia
hire hacker mumbai
hire a hacker nz
hire a hacker nyc
hire ethical hackers near me
hire a hacker pro review
hire a hacker on fiverr
hire a hacker pakistan
hire a hacker perth
hire a hacker in pune
hire professional hacker in india
hire pakistani hacker
hire a hacker reddit
hire a hacker reddit 2021
hire a hacker roblox
hire a hacker uk reviews
hire a hacker.io reviews
reddit hire a hacker
hire a roblox hacker
hire a security hacker
hire a hacker discord server
hire hacksaw
hire someone to catch a hacker
is it safe to hire a hacker
hire a hacker to change grades
hire a hacker to get your money back
hire a hacker upwork
hire a hacker to hack university grade
hire ethical hacker
upwork hire a hacker
hire a hacker via email
hire a hacker vpn
hire a hacker voice changer
hire a hacker voice
hire a hacker vs cracker
hire a hacker vinnie
hire a hacker vancouver
is hackers for hire legit
where to hire a hacker reddit
hire a white hat hacker
how much would it cost to hire a hacker
hire a hacker xbox
hire a hacker xyz
can you hire a white hat hacker
how to hire a hacker to change your school grades
hire a hacker zimbabwe
hire a hacker zoom
hire a hacker zig
hire a hacker zagreb
hire a hacker zendesk
hire a hacker zlaner
z-hire
hire a hacker 01
hire a hacker 0.5
hire a hacker 0.0
hire a hacker 0.2
hire a hacker 101
hire a hacker 1 hour
hire a hacker 1337
hire a hacker 15 minutes
hire a hacker 2020
hire a hacker 360
hire a hacker 3d
hire a hacker 365
hire a hacker 31
hire a hacker 32
hire a hacker 37
hire a hacker 35
3 hackers
hiring a hacker legal
hire a hacker 5k
hire a hacker 60 minutes
hire a hacker 76
hire a hacker 808
hire a hacker 800
hire hacker reviews
hire a hacker 911
hire a hacker 90s
hire a hacker 90 days
8 notes
·
View notes
Text
Where can I hire a hacker to change my university grades, GPA, and transcript online?
Where can I find a hacker if I need a hacker to change my University GPA?
No need to go too far. You can follow our advice. The fewer websites you will find the basic services, the harder it is to find them. My personal experience will help make this task easier. Very recently, I modified the grade of a target. I visited the site with recommendations from various sources and communicated with them easily using WhatsApp’s secure and encrypted messaging system. I have chosen the desired expert from many types of hackers through very nice and effective conversations. I got my needs resolved very quickly. You can hire a hacker service from us if you want, For further information about how to change your grades online and other related hacking services, Speak to a hacker anonymously HERE for all your hacking needs
How to hire a hacker to change your grade
I need a hacker to change my University GPA. Earlier I wrote an article on hiring a hacker to change your grades. In my research, searching for hackers, I found another question asked by a Reddit user. This is a common question that separates the real from the rest. Who is the hacker? How do you pay them? What can they do? How do they believe? Where to find a hacker? When to contact a hacker? You have high expectations and hope they can solve your problem. Yes, they can, but can you solve your problems with us? we are providing hackers.
Hire a hacker to change university grades
What comes to your mind when hacking a school system? The school system is hacked by admin clearance to access the main server. The most vital part of hacking your university GPA is that you need admin login to gain access.
I Need A Hacker To Change My University Transcript
I need a hacker to change my university transcript. Being a student can be really stressful a lot of the time. In particular, trying to strike a balance between academic studies and other non-academic demands can be a major cause of stress for students. Realizing that you have failed an important test or test can cause frustration for the student. Again low-quality grades and often become a cause of frustration. This is not surprising. But the good news is, it’s not the end of the world, you can improve your grades even after you fail.
Whether you are a university, college, or high school student, you should be embarrassed whenever you get a lower grade than expected or get less than you need. You can improve your grades in two ways if you want.
First, grade development with re-exam
Second, grade development by hiring hackers
Developing grades with exams is a long time process. If you don’t want to spend time or if you urgently want to upgrade the results, then you can easily develop grades by hiring a professional hacker.
Is it really possible to hack University Grades Transcript?
Yes, it is possible. You can hire a skilled hacker to develop the grade of your University Transcript. If you notice a little, you can see that we see this kind of news in newspapers or news. This is a very common issue at the present time. You can easily develop your transcript grade by hiring hackers.
Hire a professional hacker to change school or university grades
If you have failed an important test and need to adjust your college grade, transcript, or GPA Hacker is your best solution. Being a university student with other life needs can be very difficult and as a result, the student’s final grade can be bad.
Conclusion
If you make the final decision to hire a hacker to improve the cause of your life by changing the terrible outcome, leave the task in the hands of the hacker to determine how difficult the task is. Mention what you need. And hire a verified hacker like us to keep your privacy a secret.
For further information about how to change your grades online and other related hacking services, Speak to a hacker anonymously HERE for all your hacking needs
#gpa#transcript#grades#professional hackers for hire#professional hacker#University Grades Transcript#University Grades#University#university student#college life#student#studying#college student#university life#student life#I Need A Hacker#change your grade#Where can I hire a hacker
2 notes
·
View notes
Text
So....,I'm currently in school rn but there is a big problem that I have to talk about because this is really REALLY important.
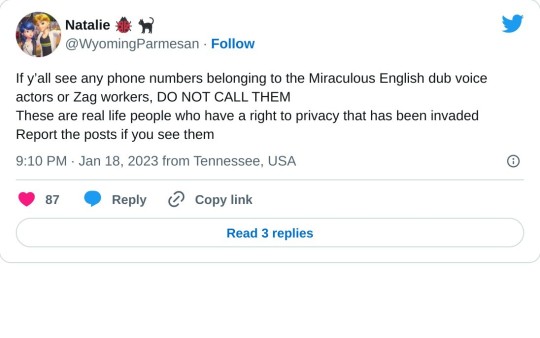
Yep,it happens.
Hey,do you remember that last year,there was this massive leaks that literally ruined S5?
Well,apparently,this was made by the same guy who leaks S5 and now,this.
You know what,I'm tired of this bullshit. So,let's just expose him.
There was this guy(which I think he's Turkish) named Serhat. This guy was synonymous with the some of the biggest controversy in the fandom including....yep,the leaks.
This guy was the fucking hacker whose hacking into Zag and leaks some scenes,some character designs and even,some full episodes!
This guy was blocked and reported numerous times and yet,he still doing it l,just on another accounts.
Well,if he expose some of the staff and VA's,then,I'm gonna expose him.
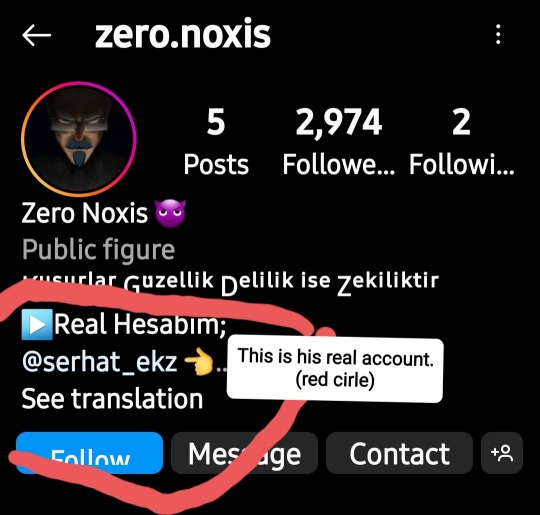
This is his Instagram where he post the leaked scenes(because he's a hacker,obviously).
UPDATE:I might giving you the wrong account but I think his account full of leaked scenes is [sero.leaks](Idk guys but if I'm wrong,that's on me because this guy has so many account that he doesn't want to be tracked[but the red circle is still his real account])
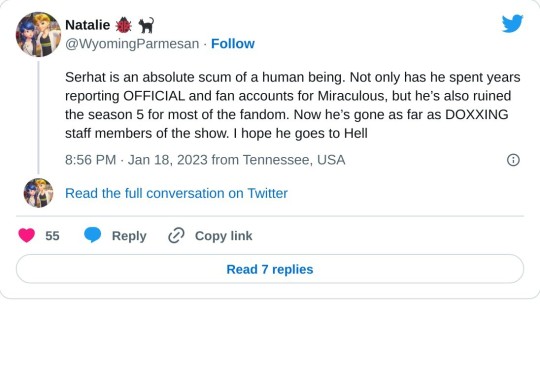
And this is a post about him.
And remember,he's the one who owns Miraculous.TO,which under scrutiny over some....'inappropriate ads' that's being present on their website(and there's more to it but I can't remember).
So.....,yeah,that's just the information that I can gather for now. I know there might more but I think that's enough to give the gist about this guy.
So,what we're gonna do now?
Well,as I said it before,upgrade your security,Zag and hire a professional hacker,maybe a VPN will be worth it.
But now,I change my mind because....THIS IS GOING TOO FAR!
So,I suggest Zag to.....LITERALLY REPORT IT TO THE AUTHORITY. Specifically,the Turkish police and bring this man to court. Please,Zag. If you can drag the people who make a merch without a permission because of the copyright to the court,then you can do the same to him. That way,we can save the show together.
Also,if there's any Turkish Miraculers out there,please report this man to the police.
There's more ways that the fans can report about this.
You can email to Zag at this link right here.
and also,Instagram.
So,that's it. I want to make this post here because this guy.....is a fucking menace. So,I will end this post,in Turkish(I'm using the translations,so,please forgive my Turkish).
Ne olursa olsun seni indireceğiz,Serhat. Ne kadar hesabın olursa olsun, her şeyi nasıl sızdırırsan sızdır, kazanamayacaksın.Sizi seçimlerinize pişman ettireceğiz ve sizi adalete teslim edeceğiz. Allah seni CEHENNEMİNE hidâyet etsin.
16 notes
·
View notes
Text
6 Practical Steps to Prepare for Technical Interviews
Summary:
Technical interviews are a crucial part of the hiring process, and effective preparation is essential for success. To help you prepare, here are six practical steps to follow:
1. Understand the Job Requirements: Thoroughly review the job description and note the key skills and technologies mentioned to tailor your preparation efforts accordingly.

2. Brush Up on the Basics: Refresh your knowledge of fundamental concepts, algorithms, data structures, and programming languages. Dedicate time to practice coding exercises and solve problems from reputable coding challenge platforms.
3. Leverage Online Resources: Explore platforms like Leet Code, Hacker Rank, and Codewars for practicing coding problems. Utilize websites and blogs dedicated to technical interview preparation for insights into common interview questions and strategies.
4. Mock Interviews and Peer Practice: Conduct mock interviews to simulate the real interview experience, gain confidence, and identify areas for improvement. Participate in peer practice sessions or study groups to learn from different perspectives and broaden your problem-solving skills.
5. Stay Up-to-Date with Industry Trends: Keep yourself updated with industry news, new tools, frameworks, and best practices. Follow industry blogs, subscribe to newsletters, and engage in online communities to stay informed.
6. Reflect on Past Interviews: Analyse previous interview experiences to identify areas of improvement. Reflect on questions that caught you off guard and address any knowledge gaps or weaknesses.
By following these steps, you can enhance your chances of success in technical interviews. Remember that preparation is an ongoing process, and continuous learning and practice are crucial for excelling in your technical career. Good luck!
Read the complete post Here
Watch Video on YouTube:
youtube
2 notes
·
View notes
Text
Best Facebook Spy App To Track Your Teenage Girl’s Phone
In the realm of modern relationships, the idea of spying on a working teenage girl’s messages through a Facebook spy app raises profound ethical concerns. Trust forms the bedrock of any successful partnership, and breaching that trust can have far-reaching consequences. The risks and potential fallout from such actions underscore the importance of exploring alternative avenues to address relationship issues.

What is the Facebook spy app?
A Facebook spy app is an individual proficient in exploiting vulnerabilities within social media platforms to gain unauthorized remote access to or manipulate information for various purposes. Facebook spying apps encompass unauthorized access to accounts, the dissemination of false information, and compromising user privacy. Social media spy poses significant risks, leading to identity theft, misinformation campaigns, and breaches of user trust. These hackers employ various techniques, such as phishing, brute force attacks, and social engineering, to accomplish their malicious objectives. Safeguarding personal information and being vigilant against social media hacking are crucial in the digital age.
How to Work Facebook Spy app?
Protecting against Facebook spy apps involves adopting proactive security measures. Use robust, unique passwords and enable two-factor authentication to fortify account access. Regularly update passwords and conduct security audits to detect and rectify vulnerabilities. Stay vigilant against prevalent hacking techniques like phishing, and exercise caution when encountering suspicious links. Avoid openly sharing sensitive information, and regularly review and adjust privacy settings. Monitor account activity for signs of unauthorized access. Stay informed about emerging threats and consider engaging ethical hackers to assess and bolster digital defenses. By implementing these precautions, you can significantly mitigate the risk of falling victim to social media hacking.
How do I use the Facebook Spy App?
To use a Facebook spy app, follow these simple steps. Firstly, choose a reputable app such as HackersList. Next, purchase and download the app from the official website. Install the app on the target device, ensuring compatibility. After installation, set up an account and log in. Configure the app settings to monitor Facebook activities specifically. Now, you can remotely access the target device’s Facebook messages, posts, and more from your own device. Remember, always adhere to legal and ethical considerations, and maintain open communication with the individual being monitored, especially if they are your teenage daughter.
Why Do You Need a Facebook Spy App to Track Your Teenage Girl’s Phone?
In the digital age, a Facebook Spy App can be crucial for tracking your teenage girl’s phone to ensure her safety and well-being. With the prevalence of online threats and cyberbullying, monitoring her Facebook activities allows you to detect any potential risks early on. These apps provide insight into her social interactions, helping you address concerns discreetly. Additionally, they offer a means to prevent exposure to inappropriate content and guide responsible social media usage. While it’s essential to respect privacy, a Facebook Spy App can serve as a proactive tool for parents, fostering a secure and supportive digital environment for their teenage daughters.
How To Hire Social Media Hackers To read teenage girl’s secret messages
There are several ways to Facebook spy and get remote access to someone else’s conversations and SMS logs. But any of them may compromise your personal data and privacy. If you need to social media hack the text messages of your kids or loved ones, you will need a cell phone spy app. AnyControl monitoring software enables you to read all sent and received text messages on any Android or iOS device. Note that at Mom Android, the Android version is available, and the iOS app will be available soon. The app operates in stealth mode and can track a wide range of activities, including text messages.
Once you have installed it on your target device, refer to your online dashboard, and there you can do the following:
See and read the target user’s text messages
Retrieve deleted texts
view SMS attachments
Check who they text and when
So if you are looking for an efficient method to read text messages from another phone, this is your best option.
Best Way To Find Facebook Spy Hackers
Looking for the best way to find a Facebook spy app? It’s crucial to proceed cautiously and prioritize finding a reputable and ethical professional. Start by researching online and looking for recommendations from trusted sources. Check for reviews and testimonials to gauge the reliability and credibility of potential social media hackers. Additionally, consider contacting cybersecurity experts or ethical hacking communities for recommendations. Verify the credentials and expertise of the Facebook hacker, ensuring they specialize in mobile hacks and prioritize client confidentiality. By taking these steps, you can find the best mobile hacker to meet your needs while ensuring a safe and ethical engagement
📊 Related Blog : Hire Professional Facebook Hackers
Find The Right Facebook Spy From HackersList
Looking to find the right Facebook app for your needs? Look no further than HackersList, a platform that connects users with skilled professionals in ethical hacking. On HackersList, you can browse through profiles, read reviews, and find a mobile hacker with the expertise you seek. The platform prioritizes transparency, allowing you to assess the skills and reputation of potential hackers before making a decision.
Final Thought
Finding social media hackers to track your husband’s location should be carefully considered. While technology can answer questions and concerns, it’s essential to prioritize ethical and legal practices. Before engaging in a Facebook spy app, thoroughly research their credibility, expertise, and commitment to confidentiality.
6 notes
·
View notes
Text
"Waaaah waaaah the alt-right are keeping our fics from us waaaah waaaaah!!!" ... y'know if you presented a 'fictional' scenario to a group of people (let's pretend, for a moment, that this hypothetical crowd isn't absolutely brainrotted from constant internet usage) where you told them a group running a website get almost- if not even MORE than- half a million dollars on a yearly basis to run a service that is fuels almost entirely by USER CONTRIBUTIONS but never improve it, most would think it's at best overcompensation and at worst a Scam.
Now if you told these people that, Somehow, the people who get hundreds of thousands of dollars yearly for this service can't even use that money to prevent their service from being DDoS'd, or to use the money to hire people specifically specialized in solving these cases, you might get a bit more suspicion from the audience.
Now, if you tell them the cherry on top is that the service runners, instead of just quietly taking care of the problem and giving minimal details about what's going on, allow for and even HELP in the spreading of the narrative THAT THEY'VE BEEN ATTACKED BY AN ALT-RIGHT GROUP 'CLAIMING' TO BE SUDANESE? Oh, but when its explained that the hackers aren't ACTUALLY Sudanese, people jump to it being the Russians instead! The people listening to you explain this oh so fictitious scenario would QUITE OBVIOUSLY THINK THIS IS BLATANTLY FEARMONGERING AND USING XENOPHOBIA AS A MEANS OF COVERING THEIR OWN EXPOSED ASS, RATHER THAN JUST TAKING ACCOUNTABLE.
Please p ease PLEASE take a step back and check the absolutely INSANE biases being displayed right now. Sure, maybe an Alt-Right group IS keeping y'all from reading your diet yaoi, but let's be fucking realistic here. The AO3 moderators are taking advantage xenophobia on both ends of the spectrum, whether they openly 'denounce' the alleged origins of the 'hacker group' directly or not, because sooo many people are so willing to take the bait and fall down the conspiracy rabbit hole rather than acknowledging they might have an unhealthy attachment to a website run by people who only see them as wallet fillers
Please, if you're crying and screaming about losing ao3... take a step outside. Sit on the ground. Take in the sun. Read a book. Pick up a pen and paper and write or draw. Hell, if you're REALLY desperate go explore the Wonders of alternative fic websites, go check out our old friends at ff.net. just PLEASE do something other than complain and throw nationality-based blame at the hackers. You guys sound like Trumpies rn
#txt#sorry this is a long ass post. ummm. hi#ask to tag#long post#would be great if this gets reblogged buuut i also dont care 👍✌💖
4 notes
·
View notes