#network attack protection
Text
Defending Against Distributed Denial of Service (DDoS) Attacks: Mitigation Techniques and Strategies
DDoS attacks are a serious threat to organizations of all sizes, and their impact can be significant and costly. Read more...
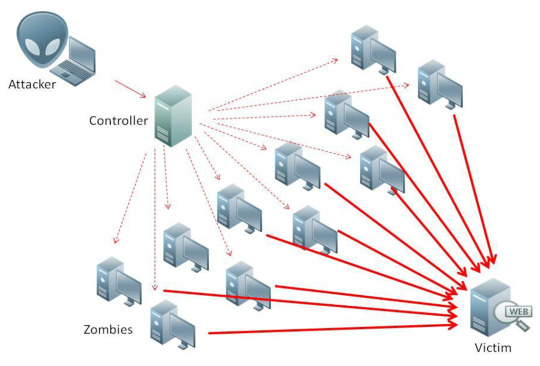
Distributed Denial of Service (DDoS) is a type of cyber attack that aims to overload and overwhelm a website, network, or server with a massive amount of traffic. In a DDoS attack, the attacker typically uses a network of compromised computers (known as a botnet) to flood the target with traffic, rendering it inaccessible to legitimate users. DDoS attacks can be extremely disruptive and costly,…
View On WordPress
#attack detection#black hole routing#cloud-based protection#cyber attacks#cyber security#DDoS attacks#load balancing#mitigation techniques#network security#Network segmentation#rate limiting#traffic filtering
6 notes
·
View notes
Text
Network Security Threats
A network attack is an attempt to gain unauthorized access to a company's network to steal data or engage in other harmful activities. The following are the two types of network assaults:
(more…)

View On WordPress
#cyber attacks#cyber security threats#cyber threats#network protection best practices#Network Security Threats#what is network attack#what is Network Security Threats
1 note
·
View note
Text
Everywhere Security: Protecting Modern Organizations from Threats
Sanjay Mohindroo
Sanjay Mohindroo. stayingalive.in
Navigating the Complexities of Cybersecurity with Confidence
In today’s digital era, cybersecurity is not merely a necessity but a strategic imperative. As organizations embrace the opportunities of digital transformation, Everywhere Security emerges as a guiding light, offering a unified approach to cybersecurity that empowers organizations…

View On WordPress
#API integrations#Cloud Security#cyber defense#cyber resilience#cyber strategy#Cyber Threats#cyber-attacks#cyber-security#Cybersecurity#Data Protection#Digital Transformation#Everywhere Security#hybrid work#innovation#IT Security#modern organizations#Network Security#news#phishing#Ransomware#Sanjay K Mohindroo#Sanjay Kumar Mohindroo#sanjay mohindroo#Security#security solutions#technology#threat detection#threats#Zero Trust
0 notes
Text
How to Protect Your Business From Cyber Threats
Cybersecurity is a major topic every business owner should be discussing. Here is some info from FRC that we hope helps.
Imagine we’re sitting down over a cup of coffee, and you’ve just asked me how to shield your trucking business from the ever-looming shadow of cyber threats. It’s a digital age dilemma, but I’m here to walk you through some straightforward strategies to bolster your defenses.
First off, let’s talk about the elephant in the room: cyber threats. They’re not just a problem for the tech industry;…

View On WordPress
#access control#antivirus software#cloud storage#cyber attacks#cyber threats#cybersecurity#cybersecurity laws#data protection#digital transformation#employee training#encryption#firewalls#incident response#legal compliance#malware#network security#password policies#phishing attacks#ransomware#secure communication#software updates#trucking industry#vendor security#VPN
0 notes
Text
Cybersecurity: Follow 7 Best Practices to Protect Personal Data Now
Introduction:Recognizing the Need for Cybersecurity1. PasswordsUse Secure and Original PasswordsLength and ComplexityAvoid Using Personal InformationCreate a Unique Password for Each AccountPassword Manager2FA, or two-factor authentication2. Maintain Up-to-Date Software and EquipmentUpdates to the operating systemUpdates for web browsersAntivirus and security software updates3. Warning: Phishing…

View On WordPress
#best practices#cybersecurity#cybersecurity education#data backups#data privacy#online security#personal data protection#phishing attacks#secure Wi-Fi networks#software updates#strong passwords#two-factor authentication
0 notes
Text
Firewall Friday: Network Security - Protecting Your Network from Threats
Welcome to Firewall Friday, where we dive into the exciting world of network security with a touch of humor and relatable analogies. In this edition, we’ll explore the importance of network security and how firewalls act as the guardians of your network, protecting it from potential threats. Get ready to embark on a hilarious and informative journey as we use common analogies, playful emojis, and…

View On WordPress
#access control#brute force attacks#data encryption#employee education#firewall#hackers#intruders#intrusion prevention#multi-layered defense#network protection#network security#packet inspection#patch management#security incident response#spoofing
0 notes
Text
Cyber Insurance: Protecting Your Business from Cyber Threats
What Is Cyber Insurance? Protect Your Business from Cyber Threats
#Lewandowski #BiggestMediaScam #Cryptocurency #thebabyfloki #ThursdayThoughts #INDWvsAUSW #Pawan_Khera #BoycottGermany
Hello everyone, As you you all know we are advancing rapidly in the field of Technology and our life is becoming digitized, we are coming towards Technology and Cyber Insurance because of that we are forcing ourselves to the threat of cyber attacks and data breaches. Morever you should know that businesses, in particular, are vulnerable to these threats, as you know that they handle sensitive…

View On WordPress
#Business assets#Business continuity#Business insurance#Cyber insurance#Cybersecurity#Data breaches#Data protection#Hacker attacks#Information security#Insurance coverage#IT security#life insurance#Network security#Online security#Privacy protection#Risk management#Small business#Technology protection#Technology risks#what is cyber insurance
1 note
·
View note
Text
DCxDP Fanfic idea: Wrong Number
Bruce prides himself in keeping all of his networks secured. If he didn't make it himself, he had the funds and connections to get him the best working on his systems.
He had backup plans in case the systems were ever hacked, of course, but he had yet to encounter a cyber attack that wasn't beaten away by his firewalls or his team.
Babs and Tim were far more feral when booting out unwanted guests. The level of protection was also transferred to his other systems that weren't Batman-related, just to make sure the connection between Bruce and Batman was never made.
That's why he never really checks his personal phone's caller ID, not the one he gave out as Brucie Wayne, but the one Bruce used for his real life without any masks- civilian or vigilante. The only ones who had the number- and the access- were his children and Alfred.
Not even the Justice League- those who were aware of his identity- knew of this number.
Bruce is in the middle of typing up a report for the next Wayne Board meeting when his personal phone rings. He figures it's Dick giving him a call to update him on his drive home or maybe Jason, as his son was planning on going to college.
"Go for Papa Bruce," He says, knowing his kids hate his phone greeting and doing it deliberately to spite them.
There is a long pause where he can't help but smirk thinking his child is either rolling their eyes or cringing too hard to properly speak. Eventually, a voice cracks over the speaker.
"Hello. I'm selling cookies to raise money for my own star. Would like to buy a box from me?" says a boy, not one he has taken in. The voice is young maybe not even double digits yet. Bruce is alarmed.
"Who are you?! How did you get this number?" He demands, yanking his phone to his face and seeing, with a chill, a phone number out of state.
His system had been compromised. By a child. By accident.
"My name is Danny!" The boy chirps. "I sell cookies. Like the Girl Scouts, but I'm a boy, and I don't scout."
"That's rather fantastic, lad. What kind of cookies are you selling?" Bruce asks to keep the boy on the line while sending an email blast to the others. It's a string of numbers that are code for compromise so they all know to close any communication channel until it's safe to get back on.
"Chocolate chip. Mint Slim. Oatmeal and peanut butter. I made them myself!"
Right. Bruce hooks up his phone, tracing the call. The signal bounces off the call, swinging up to a salute and falling back down to earth. In seconds he has the boy's location. It pings in a small town right outside of Star City.
He sends Barry a private message. His friend is already on the way to the location. He'll get the boy in a few seconds.
"How much for a box of chocolate chips? Those are my favorite." Bruce tells the boy, voice whimsical as his Brucie persona demands.
In an unsure tone, the boy pauses, then whispers, "I don't know. No one ever let me get this far."
"How about twenty for a box of dozen? I'll buy five boxes for each of my kids that live at him," Bruce tells him, and the boy gasps.
"That could buy me one whole night in a hotel!"
Bruce's insides freeze. What did he mean-
"Hey! No! Let go!" Danny suddenly screams. Bruce's heart launches- he hates it when kids get hurt, especially those that sound like Danny- until Barry's voice comes over the speaker.
"I got him, Mr. Wayne. Thank you for alerting the Justice League Hotline." That's code for This is not a threat to you Batman and Bruce allows himself to relax just a little.
"Narc!" The boy shouts, outraged, before the call drops. Barry is likely taking over the situation, which means Bruce can leave it in his capable hands.
After reassuring his kids that he is fine and that they are all safe, he suits up and meets the Flash in the Watch Tower. There, he learns that Danny is only seven years old and has been living on the streets for a while.
The boy had been surviving by baking some cookies to sell on the side of the street- where did he bake them? The boy would not say- until he got the bright idea to try to sell through phone calls like he had seen on TV.
He punched in random numbers at the community center phone and gave his pitch about a star, thinking people would be more willing to buy from him if he had an excellent reason.
Barry had left him with CPS, but he looked devastated about that. It turned out that Danny was a meta and had likely been kicked out of his home once it was found out based on what he said of his parents.
Bruce felt he should assure Barry that Danny was fine and look into his placement to help settle his more sensitive teammate's nerves.
He was unhappy that Danny was not in a good placement; there were far too many reports from a concerned neighbor to make him think it was a safe place. Given the fact that placement had a lot of meta kids that "fell through the cracks," Bruce worried he had just stumbled across a trafficking ring.
He would sick Barry and Jason on them. Just to ensure they wouldn't see the light of day again.
Still, that did not fix his mistake with Danny, the little cookie seller.
Bruce hacked into the system to move Danny. He thought about where he would move the young child but ultimately had him in Wayne Manor.
Just until he could confirm that he would be safe. He certainly didn't think about the adorable little boy who called him with his heart in his hand and got sent to a terrible place for three weeks because of Bruce.
Danny arrived at Wayne Manor with a happy little bounce and a chipper outlook on life than Bruce was expecting. "If it isn't Mr. Narc!"
God, he going to adopt the boy, isn't he?
(Danny has been thrown into a different universe, aged down to a child. He survived by overshadowing people into letting him spend the night baking cookies.
He was thrown into a somewhat typical home, but the nosy neighbor down the street took far too much notice of his overshadowing, and now he was being moved again.
Maybe he can terrorize Mr. Narc now instead? )
#dcxdpdabbles#dc x dp crossover#Danny de-age#Dimension travel#Crack#Basically He overshaowed people and everyone lost their minds about it#Barry will fight Bruce for Danny#Danny will make it his life goal to be Bruce's life hell
2K notes
·
View notes
Text
Random Plot Points
A little about me as a writer, I love daydreaming about adventure stories. I usually know the general set up and larger plot points but oftentimes struggle with the how, how do characters get from point A to point B.
So, I made a list of random challenges for my characters that I look at when I'm stuck.
Sharing in case helpful to others! (intended for adventure, sci-fi, fantasy stories)
characters are delayed/blocked/experience a natural disaster (storm, fire, flood, avalanche, earthquake, epidemic, etc) (BONUS and forced to take a detour from the original path)
character(s) is trapped (quick sand, fall through ice, in room filling with poison, on sinking ship, in a trash compactor on the Death Star, etc) (BONUS- fall into hidden room and discover something)
characters go to a festival/ball/party/political summit (where inevitably it all goes wrong)
character(s) overhears a secret (at bar, at party, from a whispered conversation below them in a stairway, etc)
characters are attacked by an animal or mysterious force
characters(s) caught in a mob/riot
character wins/loses something in a bet
character is brainwashed or possessed
character is stranded/lost
character is poisoned
character succumbs to injury or illness
characters are chased/ attacked by antagonists
character is captured or arrested (and needs to be rescued)
character is kidnapped and kidnappers make a demand for their release (financial ransom, exchange of information, prisoner exchange, etc)
character(s) go undercover to retrieve information
characters decide to steal something they need for their quest (weapon, magical object, money, information, etc). (BONUS- time for a well-planned heist!)
characters need to protect/ retrieve/ destroy something
characters uncover a network of spies (up to you if they're unexpected allies or antagonists)
characters discover hidden passageway, room, ruins etc that leads to an important clue
characters forced to hide from someone/something
characters need to escape
characters lured into trap set by villain (BONUS if the villain doesn't even care who wins but only goaded them to learn how a magical object works, the extent of heroes powers, emergency response system of a government, etc)
characters set trap for villain (BONUS- use someone or something important as bait) (if in Act 2, they fail)
characters reveal critical information to villain in disguise
a character is mistaken for someone else (and then is wrongfully arrested, receives information not intended for them, etc)
characters receive help (hitch a ride, get help hiding from captors, get help escaping somewhere, etc) from an unlikely new ally
characters forced to team up with an unlikely ally/ morally grey character, etc
characters learn something from simple library research (an oldie but a goodie)
characters just literally just stumble upon or witness something important (secret weapon, secret society etc)
characters uncover a secret map/ coded message on the back of an old unassuming document (time for a classic treasure hunt!)
someone escapes from prison (an old villain or an old ally) that changes the quest
someone is being blackmailed (or otherwise forced to act against the protagonists)
someone is discredited (rumor, disinformation campaign etc)
something stolen from your characters
something (document, magical object, money) turns out to be fake
OR, something unassuming turns out to have special powers or meaning
something is hacked (defense system, infrastructure, bank, private records, etc)
something critical is attacked (important bridge, port, bank/ financial system, safehouse, capitol building, character's familial home, etc.)
a computer virus is unleashed
a biological weapon is unleashed
a piece of information the characters believed was true, is false
an ancient myth turns out to be true
a secret is made public
A law is changed or a vote on a critical piece of legislation loses/wins
a political opponent wins an election/ a political ally loses an election
character(s) help a passerby (from raiders, local tyrant, beast, mystical force, etc)
characters "follow the money" and realize someone who was thought to be their ally is actually working for... (crime syndicate, villain, local tyrant etc)
#writeblr#writing tips#outlining#writing resources#writing prompts#writing#prompt list#fantasy writing
2K notes
·
View notes
Text
Humans are weird: Minecraft
Alien: What is the point of this game?
Human: It doesn’t have one; you can do whatever you want.
Alien: Can I burn this world and leave nothing but ash?
Human: Disturbingly specific but go ahead.
------------
Alien: How do I get wood?
Human: Punch some trees.
Alien: ………..
Alien: Punch some trees.
Human: Yup.
Alien: Are you mocking me?
Human: What?
Alien: Do you think I’m some sort of joke?
Alien: An object of ridicule for your amusement!?
Human: Okay, before you over react let me just show you.
Alien: *Starts reaching for sword when they see the human literally start punching trees for wood*
Alien: Oh. *Puts sword away* My apologies.
-------------
Human: Why aren’t you playing?
Alien: There is a monster in my home.
Human: Is it an ender man?
Alien: No.
Human: Skeleton?
Alien: No.
Human: Creeper?
Alien: Nope.
Human: …………
Human: Zombie?
Alien: Thwarp no.
Human: *Takes controller and goes inside the house* What could it possibly be-
*Sees creature*
Human: That is a pig.
Alien: It is the stuff of nightmares.
Human: What the hell is scary about a pig?
Alien: Look into its eyes.
Alien: It has no soul; no remorse.
----------------
Alien: What are you making?
Human: A doomsday device.
Alien: Are you allowed to build that on a public server?
Alien: Surely the admins would seek to stop you.
Human: They can’t stop it if they can’t find it.
Alien: What did you build?
Human: I placed a claim block, fifty blocks down, and started a cow farm.
Alien: That doesn’t sound so bad.
Human: There are currently five hundred cows in a four block pen.
Human: I have seen the amount of lag it generates drive men to madness.
Alien: You are the worst of your species.
---------------
Alien: How goes it?
Human: I’ve created a massive creeper farm.
Alien: Dear gods why?!?!
Human: I want to see what happens when one of them is hit by lightning.
Alien: Why?
Human: I heard that it turns them into a super creeper.
Alien: Why would you want to make the sentient explosive even deadlier?
Human: To leave as a surprise for that griefer who blew up my chicken farm last week.
Alien: Ah.
----------------
Alien: What are you building today?
Human: A nether portal
Alien: Is that the purple doorway thing in front of you?
Human: Yup.
Alien: What does it do?
Human: It’s a portal to this world’s version of hell.
Alien: WHAT?!
Alien: Is that not dangerous?
Human: I mean, I want glow stone for my city; and the only place to get glow stone is in the nether.
Alien: I weep for this world that has you as its caretaker.
---------------
Alien: Why is all the sand from my beach gone?
Human: Needed it.
Alien: For what?
Human: Copious amounts of TNT.
Alien: Do I even want to know why?
Human: Remember that village that I defended only for the golem to attack me?
Alien: Yeah.
Human: Good.
Human: Because that memory of yours is all that is left of it.
-----------
*stumbling down extensive mine network to find human friend deep underground.*
Alien: You ever coming topside again?
Alien: I just found these things called “Pandas” and they are adorable.
Human: Not until I find a diamond.
Alien: Oh gods, here we go again.
Human: There’s only fucking copper down here!
Human: What the hell can I even use for copper!?!
Alien: I think you can make lightning rods out of them.
Human: Oh yeah, sure, lightning rods.
Human: I’m sure those will be useful SIXTY BLOCKS UNDERGROUND!!!!
------------
Human: What’s this?
Alien: I’ve created an elaborate rail system that will allow me to transfer the citizens of one village to another village to make it a super village!
Human: Isn’t that considered kidnapping and human trafficking?
Alien: ………..
-------------
Alien: I have created these five iron golems to protect my home.
Alien: Nothing shall destroy it while I am away!
*Alien leaves into mines*
*Returns after an hour of mining to find the entire home destroyed by creepers*
Alien: What the flarp!
Alien: Where are my go-
*Turns to see all five golems distracted by some flowers*
-------------
Alien: Something just occurred to me.
Human: What’s that?
Alien: If you can use the portal to this nether, why can’t things down there use it to escape?
Human: Pfft.
Human: That’s impossible.
Alien: Is it?
Human: *Dramatic pause before sprinting over to portal with alien behind him*
*Both arrive to find legion of pigmen pouring out from the portal*
Alien: Congratulations, you created the end times.
Alien: I hope that glow stone was worth it.
Human: *draws sword* It really was.
#HUMANS ARE WEIRD#humans are insane#humans are space orcs#humans are space oddities#funny#writing#original writing#niqhtlord01#minecraft
2K notes
·
View notes
Text
Advanced Persistent Threats: Understanding the Characteristics, Tactics, and Strategies for Prevention and Mitigation in Today's Cyber Landscape
A detailed read on Cyber security in today's digital landscape. Happy Sunday everyone!
Advanced Persistent Threats (APTs) are a type of cyber attack that is specifically targeted at organizations or individuals to steal sensitive information or disrupt operations. These attacks are carried out by highly skilled and organized hackers who use sophisticated techniques to gain access to networks and systems. In this paper, we will discuss APTs in detail, including their…

View On WordPress
#Advanced Persistent Threats (APTs)#Cyber attack mitigation#Cyber attack prevention#Cyber risk management#cyber threats#Cybersecurity#Data protection#Employee education#Endpoint protection#Incident response#Least privilege#Network segmentation#Security assessments#Security audits#Threat intelligence
2 notes
·
View notes
Text
every 36 hours American sends Israel more bombs to kill civilians, but with delays in shipping Israel is now accusing America of purposefully delaying supplying them with genocide tools.
us officials have apologized and assured Israel the massacre is still on schedule, and it snot on purpose.
I'm not gonna explore the dynamic of Israel being able to demand anything of America, especially demanding weapons from their supply. like what are they gonna do to America? shoot us with the weapons we don't give them??
but anyway, this response form officials should put to rest any excuse about how Biden is being "forced" to do this or has any reluctance.
The United States has slowed the pace of its military aid to Israel compared to the beginning of the war, according to a report quoting an Israeli official Friday that American officials denied.
As ties between the Biden administration and Israel become increasingly strained over the humanitarian crisis in Gaza, the unnamed senior Israeli official told ABC News that supply shipments “were coming very fast” when the war erupted after Hamas’s October 7 attack, but “we are now finding that it’s very slow.”
The official said Israel was running out of 155 mm artillery shells and 120 mm tank shells. The official also said that it required sensitive guidance equipment, without elaborating.
According to the official, it was not clear what was causing the slowdown.
The Israel Defense Forces refused to comment on the report.
US officials told the network that there was no deliberate delay in aid shipments and that no policies have changed.
Both Israeli and US officials acknowledged American frustrations with the war and the mounting death toll in Gaza, the report said, but US sources said the White House has not signed off on any decision to leverage military support to pressure Israel to do more to protect civilians.
@el-shab-hussein @ubernegro
614 notes
·
View notes
Note
The last post you re logged about arrestability and the Palestine Action network is something I've been thinking about a lot, and I feel really stuck on. It feels like any movement in the imperial core that wants to take actual direct action is going to find itself targeted by feds, but the ways that you can protect against that severely preclude it's ability to grow and find new recruits. Like, activism in the labor sphere can do more direct things because it doesn't have to be illegal, but I cant imagine that that will stay the case once a political labor party that's actually shutting things down. How does one make a mass movement that takes direct action but is able to prevent itself from getting shut down? I don't know, do you have any thoughts on this?
It's been done a hundred times before in the face of the same pressures, so the first order of business should be studying and learning from the experiences of successful labour movements.
Putting that aside, the key things are, in whatever words, militancy and deniability. By militancy, I mean the organisational understanding that you are in direct conflict with the bourgeois state (at a higher or lower intensity) and that your immediate priority should be making yourself immune to attack, followed only afterwards by taking offensive action. Militancy, then, means the recognition that the ultimate aim of the movement is the complete material domination and destruction of institutions that currently field armies and police networks. From the very first step, from the organisational nucleus, it needs to be understood that you are engaging in a pitched battle from within the enemies camp - which leads to the second key item, deniability.
Deniability, here, largely means compartmentalisation. Essentially every successful revolutionary movement has had a separation between the aboveground, legal struggle, and the underground, illegal struggle. To a certain degree, this is a genuinely covert or clandestine effort - undisclosed armed groups known only to a select few in the parent organisation, attributed funding through the laundering of the parent organisation. It is both essential that any armed cell is dependent entirely on the wide, integrated mass workers movement and that this cell is not actually widely known; hence, the parent organisation. If the cell were undisclosed but not integrated to a mass political organisation, it would not have revolutionary character, and be indistinguishable in practice from a common organised crime or terrorist group. It's ability to carry out correct actions would be incidental, and not self-correcting. If the cell had mass character but was not undisclosed, it would present a target to the bourgeois state and be destroyed. The strategy of asymmetric warfare is to strike at the enemy's undefended targets and to refuse to provide any defended targets for the enemy - this applies organisationally, too.
What needs to be stated, here, is that, given the connection to the mass movement, everything needs to be done only when the situation is correct. The size of a workers organisation necessary to support and supply even a single armed cell with laundered funding, safehouses, and information is extremely large, and will not be possible until a significant level of organisational base has been built and developed. Even once it is possible to support an armed cell, the political situation will very likely only warrant fairly low-intensity actions, like industrial sabotage. Again, though, the principal task of the militant - and the irregular fighter, the guerrilla in particular - is the preservation of one's own forces, over and above the destruction of the enemy. In real practice, there is no overabundance of caution, only hesitation - and the way to consistently and repeatedly carry out simple acts of industrial sabotage is by having three people work with the support of thirty-thousand. There can and must be a continuum of support, of different levels of action, between simply 'protest-organiser who pays dues to the aboveground labour organisation', to 'union salt who is a source of information on a worksite', to 'directly involved in organising and carrying out illegal acts'. The key metric for correct connection between the underground and aboveground sides of the movement is: if the actions of the underground were revealed, the mass base of the aboveground should be in support of it. The purpose of underground organising is not to go ahead of the people and start shooting cops (until the struggle has escalated to that intensity, and people are demanding that type of protection), it is to avoid providing a target for the bourgeois state.
At the higher levels of struggle, the existence of the underground becomes an open secret, which, with proper growth, coincides with the underground reaching a size and strength that it can begin to take up the mantle of the mass movement itself, and effectively transform itself into the parent organisation of the aboveground legal struggle. Until then, the model is that of a large political party leading a mass movement in every type of legal and semi-legal action under the sun (in strikes, civil unrest, and parliamentary campaigns), fiercely supporting those who do break the law (through legal and bail support, public campaigns, and protection), while the types of illegal actions the movement needs are carried out covertly.
TL;DR: Build a mass movement, or all you'll get are ecoterrorists and activists in prison.
463 notes
·
View notes
Text
Sectors That Should Implement Cyber Security Software
Currently we are living in a digital world, where we need a totally another kind of security. This security is needed to keep our data, credentials, computers, servers, etc. safe and this security is given the name of cyber security. Some businesses think that they don’t need cyber security softwares because they don’t have too much of dealing with computers and so on. To some extent, this is right, but this is also correct that some sectors need them more than any other and here in this blog post, we will be having a look at top industries that should make adequate arrangements related to cyber security.

E-Commerce
Online shopping has phased out the conventional method of shopping and currently, the most used way of shopping. This is given the name of ecommerce industry that has to involve in taking highly confidential data from customers like that card details, CVV number, bank account details, OTPs and so on. Hence, this can be said without any doubt that this one industry needs cyber security software as well as check point software more than any other. By using them, they can let their customers browse and shop confidently, without and fear of data breach or their details being compromised.

Finance
During the pandemic period, financial institutions were the worst hit in terms of cyber attacks and also cyber threats. This proves the fact that financial institutions need this software and then, they should also take ensures to prevent such threats and cyber attacks. For example, mobile banking apps should have an option for biometric authentication because it is more confusing and difficult to access as compared to numeric or even alpha-numeric passwords.

Healthcare
Healthcare sector bloomed a lot during the pandemic and as a result, became the top favourite of cyber attackers in terms of breaching, hacking, etc. The reason is all the most sensitive data of a person is stored in hospital databases and from there, it’s very easy to access them. By using these check point software as well as Voip technology on cyber security, these health care centres can trace every threat and mitigate it successfully. For this, they have to make sure that every password, device, file and user must be extremely well-fortified and AI cyber security software should be used.
#cyber security software#check point software#check point software australia#Cyber security technologies#cyber security solutions#Protection on cyber threat#digital signage solutions#digital signage device security#Software To End Cyber Attacks#Security develops intelligent enterprise#leading cybersecurity services company#cyber security solutions and services#cyber security across networks#Powerful Cyber Security Software Tools#cyber security on voip phone system#office phone security system#communication solutions#cloud solutions VoIP Technology#wireless security with guest access
0 notes
Text
Hackdra - Pro+
Cybersecurity is becoming an increasingly important aspect of businesses, as the threats of malicious actors increase. As a result, organizations are turning to smart contract audit, penetration testing, bug bounty programs, blockchain security and cybersecurity consulting services to protect their systems and data from being compromised. These services can help organizations identify vulnerabilities in their systems and networks before they can be exploited by malicious actors. Smart contract audit helps organizations ensure that their contracts are secure and compliant with industry standards. Penetration testing helps companies detect potential weaknesses in their networks that could be exploited by attackers. Bug bounty programs allow companies to reward ethical hackers for finding vulnerabilities in their systems before they can be exploited. Blockchain security provides an extra layer of protection for companies that use distributed ledger technology (DLT). Finally, cybersecurity consulting services provide advice and guidance on how to improve the overall security posture of an organization.
2K notes
·
View notes
Text
SUMMARY: Floyd is your most trusted bodyguard.
WARNINGS: Reader gets overwhelmed and grabbed by a reporter.
COMMENTS: this is a direct attack on @siphoklansan I DID NOT FORGET!!!! here is your bodyguard au (and i hope your floyd fever is treated soon <3)

Flashing cameras and screaming reporters was just your way of life. Being a celebrity wasn’t easy. Your life was constantly being monitored by the press, and every single thing you said was taken and scrutinized.
The limousine you were riding in was comfortable, but your stomach was churning with nerves. The award ceremony you were attending for your work had sent you an invite months before, and you were shocked at the prospect of meeting with so many others who shared your passions. It was to be your first event ever, your chance to do some actual networking. It was exciting, but it was also overwhelming.
By the time it was your turn to enter the hall, your nerves had been reduced to tatters and your hands were sweaty in your gloves.
Floyd opens the door and swings his body downwards, making direct eye contact with you as the camera flash and the reporters scream. To an outsider, it might look like he’s teasing you, but you quickly put together that the real reason he’s doing this is to provide you with a safe haven. He’s the one that helps you adjust to the cameras, he’s the one that offers you his hand, he’s the one that protects you from most of the camera flashes with his body. Question after question is being hurtled at you, but you just smile and wave, knowing better than to try and answer them.
Literally seconds before you enter the hall in which the event is being held, Floyd grabs you by the arm and yanks you into his chest. You feel fingers brush against your other wrist a second too late, and your head whips towards the foreign touch.
There’s a reporter standing there, thrusting his microphone into your face with a desperation you’ve never seen before.
“Is it true that you’re seeing someone?” he screams, eyes bulging out of his head.
You flinch at the loud noise and curl into your bodyguard’s chest. You don’t see the look on his face, but you can feel the muscles in his arms flexing and you just know he’s furious.
“Back away from Shrimpy!” Floyd yells back, keeping a firm grip on your waist as he tucks you into his side, “They’re not answerin’ any of your dumb questions!”
You cling to him as he practically drags you inside, away from the reporters and away from the man screaming your name.
“What is he, a super fan or something?” Floyd grumbles, squeezing your waist, “Tch. He should know better than that. Grabbing my Shrimpy.”
You say nothing, staring at the floor in shock. With your rise to fame being fairly recent, you’d never experienced someone actually grabbing at you. It didn’t feel good.
It didn’t feel good at all.
“Hey, you okay?” Floyd murmurs, brow furrowed. This is the first time he’s looked into your eyes since you stepped out of the car, and you feel your breath hitch in your throat when you feel his hand circle your wrists.
“I can go back out there and squeeze that guy for you.” he grits his teeth, sounding so angry it almost scares you.
“No!” you grab onto his shoulder, eyes darting around the entrance hall in a panic, “Don’t, it’s...it’s not worth it.”
Floyd looks up at all the people milling around, talking loudly and laughing. He pouts—an expression you would normally find amusing—and you try to breathe.
“Okay.” he huffs, standing up straight, “You’re right. He looked pretty wimpy, wouldn’t even be a fun squeeze.”
You swallow your panic and try to face the room, but as you take a step forward you realize Floyd is still holding onto your wrist. You look back at him, confused, and he still has that pout on his face.
“I don’t like that he touched you like that.” Floyd says softly, zoned in on your wrist, “Mm...c'mere Shrimpy.”
A strangled squeak leaves your throat as he brings your wrist to his lips and presses a single, gentle kiss to your skin. Your inner wrist burns as he lets it linger, pulling back just enough for you to feel his teeth scrape against the skin.
“Floyd!” you yelp, and he pulls away with a wide grin.
“There. Now you don’t have to think about that bottom feeder anymore.” he giggles, taking his place by your side, “Enjoy the party, Shrimpy.”
#auburn's fics <3#twisted wonderland#disney twisted wonderland#twst#twisted wonderland x reader#disneys twisted wonderland#disney twst x reader#disney twst#floyd leech x reader#floyd x reader#floyd leech fluff#floyd leech#floyd leech is a silly guy
628 notes
·
View notes