Text
Zmap - Single Packet Network Scanner Designed For Internet-wide Network Surveys
Zmap - A Fast Single Packet Network Scanner Designed For Internet-wide Network Surveys #Designed #ethernet #fast
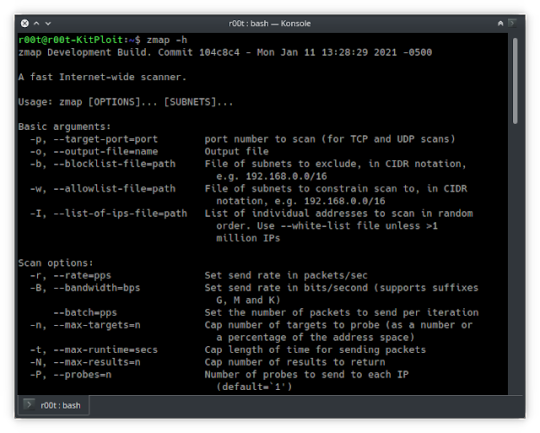
ZMap is a fast single packet network scanner designed for Internet-wide network surveys. On a typical desktop computer with a gigabit Ethernet connection, ZMap is capable scanning the entire public IPv4 address space in under 45 minutes. With a 10gigE connection and PF_RING, ZMap can scan the IPv4 address space in under 5 minutes.
ZMap operates on GNU/Linux, Mac OS, and BSD. ZMap currently has…
View On WordPress
#Designed#ethernet#fast#Internet Wide Scanning#Internetwide#mac#Network#Network Scanner#packet#scan#Scanner#Scanning#Single#Surveys#ZMap
7 notes
·
View notes
Text
Sigurlx - A Web Application Attack Surface Mapping Tool
Sigurlx - A Web Application Attack Surface Mapping Tool #Application #Attack #AttackSurface #BugbountyTool #Mapping
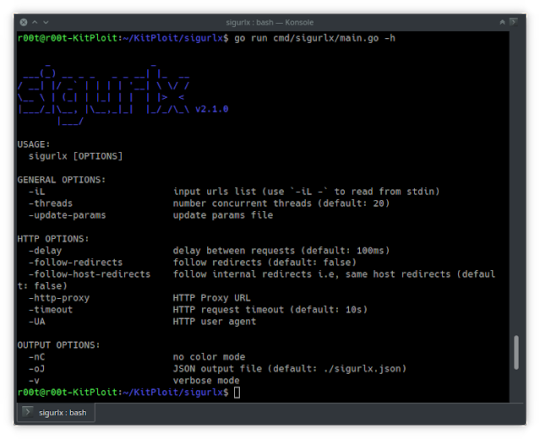
sigurlx a web application attack surface mapping tool, it does …:
Categorize URLs URLs’ categories:
> endpoint
> js {js}
> style {css}
> data {json|xml|csv}
> archive {zip|tar|tar.gz}
> doc {pdf|xlsx|doc|docx|txt}
> media {jpg|jpeg|png|ico|svg|gif|webp|mp3|mp4|woff|woff2|ttf|eot|tif|tiff}
Next, probe HTTP requests to the URLs for status_code, content_type, e.t.c
Next, for every URL of category…
View On WordPress
#Application#Attack#Attack Surface#Bugbounty Tool#Mapping#Multiple Probers#Reconnaissance#Risks Associated#Sigurlx#surface#tool#web
4 notes
·
View notes
Text
MetaFinder - Search For Documents In A Domain Through Google
MetaFinder - Search For Documents In A Domain Through Google #Documents #domain #Google #Metadata #MetaFinder #python3
Search For Documents In A Domain Through Google. The Objective Is To Extract Metadata.
Installing dependencies:
> git clone https://github.com/Josue87/MetaFinder.git
> cd MetaFinder
> pip3 install -r requirements.txt
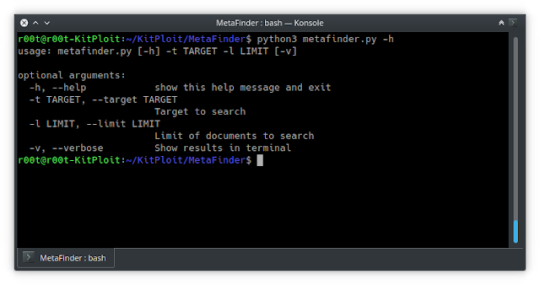
Usage
python3 metafinder.py -t domain.com -l 20 [-v]
Parameters:
t: Specifies the target domain.
l: Specify the maximum number of results to be searched.
v: Optional. It is used…
View On WordPress
8 notes
·
View notes
Text
WPCracker - WordPress User Enumeration And Login Brute Force Tool
WPCracker - WordPress User Enumeration And Login Brute Force Tool #Brute #Brute-force #Enumeration #Force #linux
WordPress user enumeration and login Brute Force tool for Windows and Linux
With the Brute Force tool, you can control how aggressive an attack you want to perform, and this affects the attack time required. The tool makes it possible to adjust the number of threads as well as how large password batches each thread is tested at a time. However, too much attack power can cause the victim’s server…

View On WordPress
#Brute#Brute-force#Enumeration#Force#linux#Login#tool#User#User Enumeration#windows#Wordpress#Wordpress Site#WPCracker
1 note
·
View note
Text
CDK - Zero Dependency Container Penetration Toolkit
CDK - Zero Dependency Container Penetration Toolkit #backdoor #CDK #Container #Dependency #EscapeContainer
CDK is an open-sourced container penetration toolkit, designed for offering stable exploitation in different slimmed containers without any OS dependency. It comes with useful net-tools and many powerful PoCs/EXPs helps you to escape container and takeover K8s cluster easily.
Currently still under development, submit issues or mail [email protected] if you need any help.
Installation
Download latest…

View On WordPress
#backdoor#CDK#Container#Dependency#Escape Container#K8S Penetration Toolkit#Kubernetes#linux#Metadata#MITM#Penetration#toolkit
0 notes
Text
Reconftw - Simple Script For Full Recon
Reconftw - Simple Script For Full Recon #bruteforce #Bugbounty #DalFox #dorks #Enumeration #full #OpenRedirect #recon
This is a simple script intended to perform a full recon on an objective with multiple subdomains
tl;dr
Requires Go
Run ./install.sh before first run (apt, rpm, pacman compatible)
git clone https://github.com/six2dez/reconftw
cd reconftw
chmod +x *.sh
./install.sh
./reconftw.sh -d target.com -a
Features
Tools checker
Google Dorks (based on deggogle_hunter)
Subdomain enumeration (passive,…

View On WordPress
#bruteforce#Bugbounty#DalFox#dorks#Enumeration#full#Open Redirect#recon#Reconftw#Scanner#Script#Simple#subdomain
0 notes
Text
MobileHackersWeapons - Mobile Hacker's Weapons / A Collection Of Cool Tools
MobileHackersWeapons - Mobile Hacker's Weapons / A Collection Of Cool Tools Used By Mobile Hackers #AwesomeList
A collection of cool tools used by Mobile hackers. Happy hacking , Happy bug-hunting
Weapons
OS
Type
Name
Description
All
Analysis
RMS-Runtime-Mobile-Security
Runtime Mobile Security (RMS) – is a powerful web interface that helps you to manipulate Android and iOS Apps at Runtime
All
Analysis
scrounger
Mobile application testing toolkit
All
Proxy
BurpSuite
The BurpSuite
All
Proxy
hetty
Hetty…

View On WordPress
#Awesome List#Bugbounty#Bugbountytips#COLLECTION#Cool#Hacker039s#Hackers#Malware Analysis#Mobile#MobileHackersWeapons#Mobilehacks#Scanner#Tools#Weapons
0 notes
Text
HosTaGe - Low Interaction Mobile Honeypot
HosTaGe - Low Interaction Mobile Honeypot #android #honeypot #HosTaGe #Interaction #Malware #Mobile #ssh #wireless
HosTaGe is a lightweight, low-interaction, portable, and generic honeypot for mobile devices that aims on the detection of malicious, wireless network environments. As most malware propagate over the network via specific protocols, a low-interaction honeypot located at a mobile device can check wireless networks for actively propagating malware. We envision such honeypots running on all kinds of…
View On WordPress
1 note
·
View note
Text
BigBountyRecon - Utilises 58 Different Techniques On Intial Reconnaissance On The Target Organisation
BigBountyRecon - Utilises 58 Different Techniques On Intial Reconnaissance On The Target Organisation #BigBountyRecon
BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of initial reconnaissance on the target organisation. Reconnaissance is the most important step in any penetration testing or a bug hunting process. It provides an attacker with some preliminary knowledge on the target organisation. Furthermore, it will be useful to gain…

View On WordPress
#BigBountyRecon#Bugbounty#Bugbounty Tool#Bugbountytips#Expediate#Intial#Offensive Security#Organisation#Pentest Tool#process#Reconnaissance#Target#Techniques#tool#Utilises
1 note
·
View note
Text
Token-Hunter - Collect OSINT For GitLab Groups And Members
Token-Hunter - Collect OSINT For GitLab Groups And Members #AccessToken #Assets #Collect #Data #Discussions #GitLab
Collect OSINT for GitLab groups and members and search the group and group members’ snippets, issues, and issue discussions for sensitive data that may be included in these assets. The information gathered is intended to compliment and inform the use of additional tools such as TruffleHog or GitRob, which search git commit history using a similar technique of regular expression matching.
How the…

View On WordPress
#Access Token#Assets#Collect#Data#Discussions#GitLab#group#Groups#Included#issue#issues#Members#Members039#OSINT#python#Regular Expressions#Search#Sensitive#Snippets#TLS#Token-Hunter#TokenHunter#truffleHog
0 notes
Text
ImHex - Hex Editor For Reverse Engineers, Programmers
ImHex - A Hex Editor For Reverse Engineers, Programmers And People That Value Their Eye Sight When Working At 3 AM.
A Hex Editor for Reverse Engineers, Programmers and people that value their eye sight when working at 3 AM.
Features
Featureful hex view
Byte patching
Patch management
Copy bytes as feature
Bytes
Hex string
C, C++, C#, Rust, Python, Java & JavaScript array
ASCII-Art hex view
HTML self contained div
String and hex search
Colorful highlighting
Goto from start, end and current cursor…
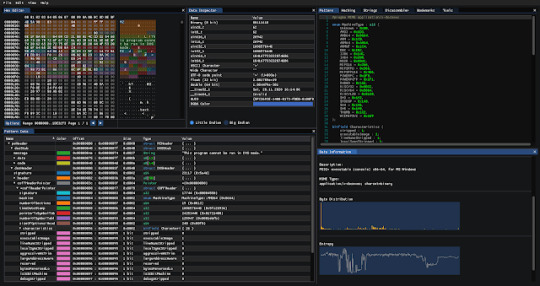
View On WordPress
#Analyzer#Constant Dark Mode#Disassembler#Editor#Engineers#Eye#Hex#Hex Editor#ImHex#macOS#Mathematical Evaluator#Pattern Highlighting#People#Programmers#python#Reverse#Reverse Engineering#Sight#windows#Working
1 note
·
View note
Text
MyJWT - A Cli For Cracking, Testing Vulnerabilities On Json Web Token (JWT)
MyJWT - A Cli For Cracking, Testing Vulnerabilities On Json Web Token (JWT) #CLI #cracking #JSON #JSONWebToken #JWT
This cli is for pentesters, CTF players, or dev.
You can modify your jwt, sign, inject ,etc…
Check Documentation for more information.
If you see problems or enhancement send an issue.I will respond as soon as possible. Enjoy 🙂
Documentation
Documentation is available at http://myjwt.readthedocs.io
Features
copy new jwt to clipboard
user Interface (thanks questionary)
color output
modify jwt…

View On WordPress
#CLI#cracking#JSON#JSON Web Token#JWT#MyJWT#Payload#python#Root Me#Testing#Token#vulnerabilities#web
0 notes
Text
SysWhispers2 - AV/EDR Evasion Via Direct System Calls
SysWhispers2 - AV/EDR Evasion Via Direct System Calls #Antivirus #ASM #AVEDR #Bypassing #Calls #CobaltStrike #Direct
SysWhispers helps with evasion by generating header/ASM files implants can use to make direct system calls.
All core syscalls are supported and example generated files available in the example-output/ folder.
Difference Between SysWhispers 1 and 2
The usage is almost identical to SysWhispers1 but you don’t have to specify which versions of Windows to support. Most of the changes are under the…
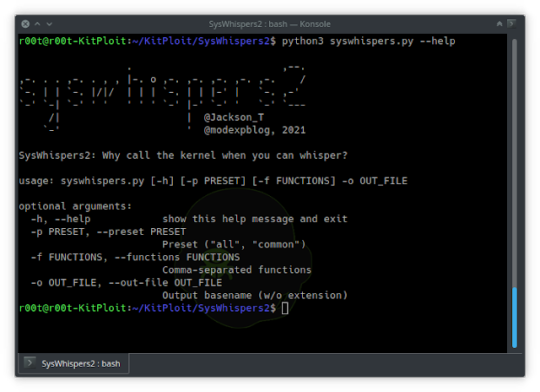
View On WordPress
#Antivirus#ASM#AVEDR#Bypassing#Calls#CobaltStrike#Direct#evasion#Malware#Malware Development#Real Time#Red Teamers#sRDI#Syscalls#System#SysWhispers#SysWhispers2#UserLAnd#windows
1 note
·
View note
Text
ByteDance-HIDS - Next-Generation Intrusion Detection Solution Project
ByteDance-HIDS - Next-Generation Intrusion Detection Solution Project #Architecture #Audition #Behavior
ByteDance-HIDS is a Cloud-Native Host-Based Intrusion Detection solution project to provide next-generation Threat Detection and Behavior Audition with modern architecture.
ByteDance-HIDS comprises three major components:
ByteDance-HIDS Agent, co-worked with ByteDance-HIDS Driver, is the game-changer for the Data Collection market. It works at both Kernel and User Space of Linux System,…
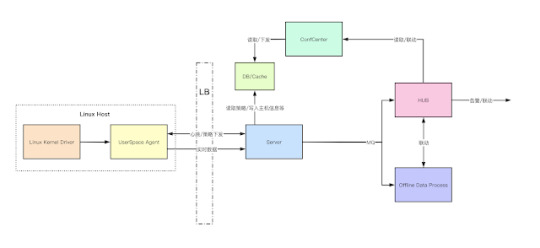
View On WordPress
#Architecture#Audition#Behavior#ByteDance-HIDS#ByteDanceHIDS#CloudNative#Detection#HostBased#Intrusion#Intrusion Detection#linux#Modern#NextGeneration#Project#Provide#security#solution#Threat#Threat Detection
0 notes
Text
Umbrella_android - Digital And Physical Security Advice App
Umbrella_android - Digital And Physical Security Advice App #Advice #android #App #Digital #HumanRightsDefenders #ios
Umbrella is an Android mobile app developed by Security First that provides human rights defenders with the information on what to do in any given security situation and the tools to do it. It allows the user to choose what they want to do, such as: protect data; securely make a call/email; securely access the internet; plan secure travel; protect their office/home; conduct counter-surveillance;…

View On WordPress
#Advice#android#App#Digital#Human Rights Defenders#ios#Journalism#Mobile App#Physical#security#Umbrella#Umbrella_android#Umbrellaandroid
3 notes
·
View notes
Text
RadareEye - Scan Nearby devices [BLE, Bluetooth And Wifi]
RadareEye - Scan Nearby devices [BLE, Bluetooth And Wifi] #BLE #BLEScanner #Bluetooth #BluetoothLowEnergy #Command
A tool made for specially scanning nearby devices[BLE,Bluetooth & Wifi] and execute our given command on our system when the target device comes in between range.
NOTE:- RadareEye Owner will be not responsible if any user performs malicious activities using this tool. Use it for Learning purpose only.
Installation of RadareEye :
git clone…

View On WordPress
#BLE#BLE Scanner#Bluetooth#Bluetooth Low Energy#Command#device#Devices#Execute#InBetween#mac#Nearby#Radare#RadareEye#Range#Scanning#Specially#System#Target#tool#wifi
2 notes
·
View notes
Text
Wprecon - Vulnerability Recognition Tool In CMS Wordpress
Wprecon - Vulnerability Recognition Tool In CMS Wordpress, Developed In Go #cms #CMSWordpress #Developed #golang
Hello! Welcome. Wprecon (WordPress Recon), is a vulnerability recognition tool in CMS WordPress, 100% developed in Go.
Notice:
Why is the project out of updates these days ?! What happens is that I am doing the vulnerability scanner.
Branch Dev
Compile and Install
Features
Random Agent
Detection WAF
User Enumerator
Plugin Scanner
Theme Scanner
Tor Proxy’s
Detection Honeypot
Fuzzing Backup…

View On WordPress
#cms#CMS Wordpress#Developed#golang#Recognition#tool#Vulnerability#Vulnerability Recognition#Wordpress#WordPress Plugin#Wordpress Recon#WordPress Security#Wordpress Theme#Wprecon#WPScan
1 note
·
View note