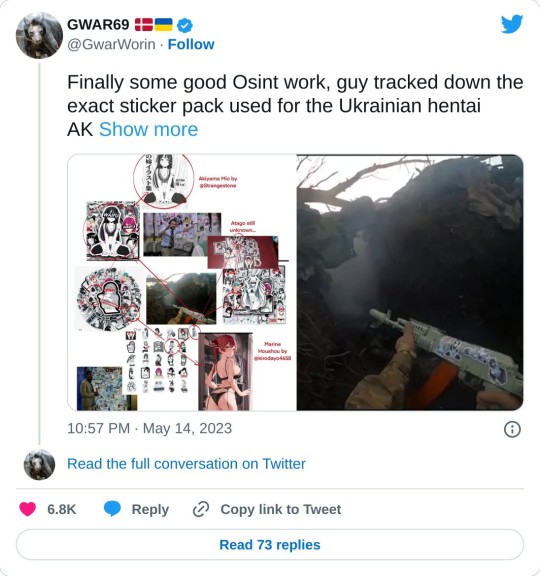
#OSINT
Text




The Fanta Bomb & Improvised Munitions in Ukraine
Improvised munitions including grenades have appeared in Ukraine over the past 12 months. They are often based on drinks cans or bottles and are filled with readily available explosive materials and in some cases fragmentation material for an increased anti-personnel effect. In this video, we look at various types of improvised munition which have been observed in the field.
Check out the video below:
youtube
Check out the full accompanying article here.
#Ukraine#Ukraine War#Improvised Grenades#Bottle Grenades#Can Grenades#Military#OSINT#Grenades#Youtube
358 notes
·
View notes
Text
hi tuglr i wrote about how i solved an OSINT challenge posted by @rhinozzryan !!
it was my first time doing any genealogy work, but i had tons of fun with this one c:
y'all should give it a try if u have some spare time and want to learn a bunch about people who died a few centuries ago, its actually enjoyable :3
https://versary.town/blog/breakdown-of-a-geolocation-genealogy-challenge/
169 notes
·
View notes
Text
Deep dive to Spam bots on Tumblr (Spoiler: FSB mentioned)
(TL;DR: Russian business man is heavily investing into companies behind the bots, mentions of FSB, Shell companies in tax-evasion and weak business law countries, Huge industry and money laundering)
I got annoyed about the bots on tumblr, so I decided to do some investigation into who is behind them and funding the operation, here is my findings:

The graph shows how a network of “affiliate marketing” companies for “dating” services is connected and some of the key players behind said companies
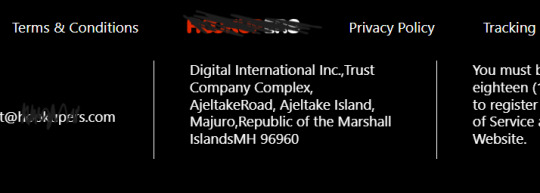
The first “company” I ran into is called “Digital international Inc” and it is shown as the “legal entity” behind of many of the websites the bots tend to link to, it also has its address listed in the Marshall Islands.
By looking at trademarks owned/filed by that company, we find 2 more companies/trademarks that are/were owned by the same legal entity.
First of these is called “Mirelia Services Co.”, currently known as “Mirelia Networks”, which lists its main business as “advertising and marketing” and is registered at the same address as “Digital International”.

Where things get interesting is when we look at one of the trademarks that was passed between “Mirelia” and “Digital international”, a trademark for an LGBTQ+ dating app called “Hitwe”,
The trademark application for “Hitwe” is listed as “Rescinded/canceled” but from the original registration documents and later ownership transfer filings, we come across an interesting company
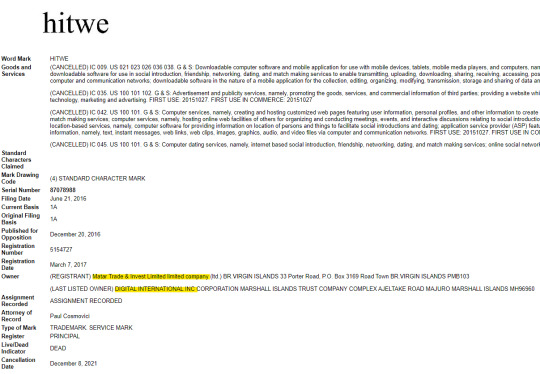
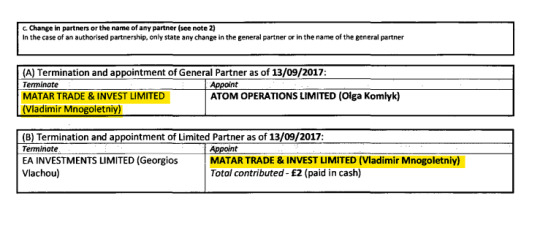
“Matar Trade & Invest Ltd.” This company has other similar “dating” and “marketing” companies linked to it, and is owned by “Vladimir Mnogoletniy”, a Citizen of Russia, who has lived in Ukraine for over 10 years and his runs his businesses there, but interestingly does not seem to have officially moved there, and maintains his Russian Citizenship as his only one.
He is also the CEO or a major of many other companies, the main one being “Genesis”, the company behind a controversial fitness app “BetterMe”, which has been shown to aggressively sell user data to less-than-reputable ad companies and affiliates, as well as being used to redirect money from scam dating sites and lessen the impact of credit card chargebacks from those sites [See footnote 1]
What makes him a particularly interesting individual is that his father, who is a Captain of the Second Rank in the Russian Navy, is doing security work for “Sevmash” - A Russian shipbuilding company, the only one that is making nuclear submarines in Russia. He also co-authored a research paper that talks about “Military Counterintelligence activities”, The other author of said paper is an FSB officer.[See footnote 2]
Sources and footnotes:
Footnote 1: “BetterMe steals traffic” - Article by SH[IT]HAPPENS on Medium
Footnote 2: “Why don’t I no longer shake hands with Vladimir Mnogoletniy.“ - Article by SH[IT]HAPPENS on Medium
Tangent: one of the other companies that I came across that seems to be working with Mirelia is “Traffichunt”, which seems to be one of the companies selling bot spam advertisements as well.

Another interesting thing is that the lawyer who filed for most of the trademarks, has quite a repertoire of similar trademarks under his belt:
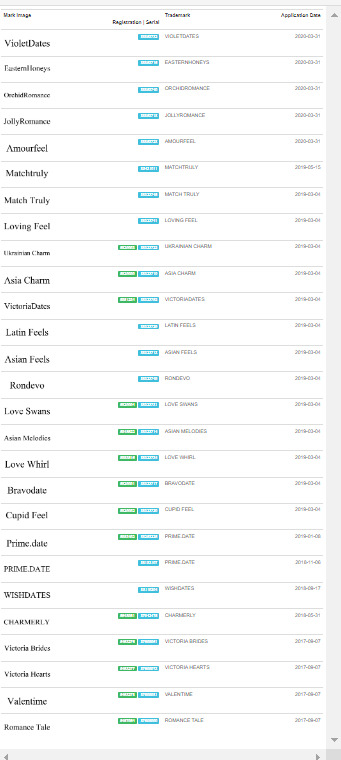
Most of these seem to have been rejected because the address he listed in the applications does not exist
If you read all the way to here, thank you and I hope that bot’s never bother you again.
#spam bots#deep dive#osint#spam#research#i hope i dont get merc'd#tumblr bots#please read#bots#spammers#opsec#phishing#cybersecurity#sex bots#fake accounts#long reads
888 notes
·
View notes
Text
In light of the escalation of state violence at several protests, I have elected to release my findings on the Canary Mission here.
The canary mission is a shady group of Zionists that doxx activists and students that express support for Palestine in an attempt to silence, intimidate, and defame them.
Some time ago, I was able to link the organization to one Howard David Sterling, an American lawyer who invests in Israeli medical firms. I wrote the report on my site here.
More recently, I found the account that runs their tip submission form. The username was included in the resource URL of the banner image of the form, which is hosted on a service called jotforms, under the username “carlossantanajm”
A google dork turned up two potential candidates: a man from eastern Canada, and a the rock musician Carlos Santana, who played a concert in Israel around 2010 despite backlash. Investigation is underway to conclusively prove the involvement of either of these individuals, but data is scarce.
Also of note was an investigation by Josh Nathan-Kazis into Megamot Shalom: an elusive organization that acts as a front for the Canary Mission. In the report, data from the Israeli charity register is cited but not provided to prove connections between Megamot Shalom and Aish HaTorah, an organization that focuses on pro-Israel media advocacy.
Funding for Megamot Shalom is contributed by wealthy zionists in the US, through the Central Fund for Israel, which routes the money to the Israeli organization so that the donors can claim it on their tax breaks. The connection between the Central Fund for Israel and Megamot Shalom was confirmed by the 2017 Tax returns of the Hellen Diller Family Foundation, who donated to CFI and labeled the reason as “CANARY MISSION FOR MEGAMOT SHALOM”
Two anonymous sources claim that a man named Jonathan Bash (who has ties to Aish HaTorah) confided in them that he ran the Canary Mission. From this info, six other Megamot Shalom board members were able to be named.
Efforts are Still underway to obtain the charity data cited in the report.
More to come soon, for updates follow the #opmonoxide tag.
11 notes
·
View notes
Text
2024 Supported Org: Bellingcat
Over the past two decades, the American public's faith in mainstream news organizations has dropped precipitously -- in a Gallup survey last year, more than half of respondents indicated that they believe news organizations actively mislead the public. The major organs of mainstream media have made many choices that have cost them the public's trust, often relying on the "both sides" model of reporting at the expense of a full and truthful picture and treating politics as a horse race.
But these organizations are also under significant pressure as they struggle to adapt to the radical technological shifts in our media environment. These shifts have cut into traditional revenue streams, driving news organizations toward the sort of reporting that will generate revenue. They have also created both the possibility of and the need for new approaches to reporting, and many legacy news outlets have struggled to adapt.

Bellingcat is an independent investigative collective of researchers, investigators and citizen journalists that uses cutting-edge technology to engage in fact-checking and open-source intelligence investigation outside the apparatus of major journalistic publications. In addition to doing their own reporting, Bellingcat designs and shares verifiable methods of ethical digital investigation. By publishing walkthroughs to open source research methods and holding tailored training sessions on their use for journalists, human rights activists, and members of the public, they’re broadening the scope and application of open source research. Their research is regularly referenced by international media and has been cited by several courts and investigative missions.
Operating in a unique field where advanced technology, forensic research, journalism, transparency and accountability come together, Bellingcat believes in the need for collaboration and has partnered with news organisations across the globe. Likewise, Bellingcat’s Global Authentication Project (GAP) seeks to harness the power of the open source community by nurturing and encouraging a network of volunteer investigators. Their Justice & Accountability unit, meanwhile, seeks to demonstrate the viability of online open source information in judicial processes.
You can support Bellingcat as a creator in the 2024 FTH auction (or as a bidder, when the time comes to donate for the auctions you’ve won.)
#fth 2024#fanworks charity auction#supported org#bellingcat#investigative journalism#transparency#OSINT
16 notes
·
View notes
Text
Making a small database on the Discord user ecki_lost
Everything will be in comments.
I update at irregular times, when I've found stuff to post
I WILL NOT UPDATE THIS ANYMORE
This is, however a good intro to OSINT gathering, so feel free to learn...
16 notes
·
View notes
Text
Manually Decoding DTMF Through A Spectrogram
While working on a recent CTF, I came across a challenge that required participants to extract a credit card number from a recording of a touch-tone telephone. If you pull your phone out now, turn on your ringer (because it’s almost definitely off), and click on some random numbers on the phone app keypad, you’ll hear the product of what’s known as DTMF, which stands for dual-tone multi-frequency.
I won’t go into the specifics of DTMF and why it exists — the important thing to know is DTMF uses a combination of two distinct tones to create one sound. There is a low tone and a high tone. Today, I’ll be showing you how to decode DTMF by sight through a spectrogram. There are decoders available for free online, so if you come across a problem like this in a CTF, or otherwise, I highly recommend using one of those, purely for speed and convenience. All that being said, this is an interesting process, and just generally a cool thing to know about. It’s the equivalent of converting binary to hexadecimal by hand instead of using an online converter — basically useless — but a great party trick (in the event of attending one, which I highly doubt given you’re reading this — so yeah, basically useless… on that note (or should I say tone (my musically inclined friend has informed me that I should not)), on with the article!)
Note — Standard DTMF — two tones, four levels per tone.
As of iOS 15.7, this tutorial is still relevant. I am looking for more samples (other phone brands and software models) to determine how accurate this is cross-platform. If you’re interested in contributing, there will be some information at the end explaining how.
I’ll be using this audio file - https://voca.ro/1dr1J1gbyw5B
(This is from the CyberSoc Wales “personalbanker” challenge)
The first thing I did was put the recording through a spectrogram program. There are plenty available for free online; personally, I like using Academo, because it includes lines that will help with quick sight-reading later on. (https://academo.org/articles/spectrogram/).
You may be better off downloading software (Audacity is fantastic), should you require a spectrogram for a longer recording. Academo is not scalable beyond 10 seconds, so you can use it, but you’re going to be taking quite a few screenshots.
The first thing I did was drop the recording from the challenge into Academo.
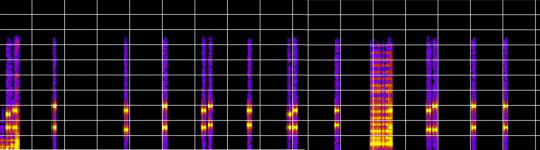
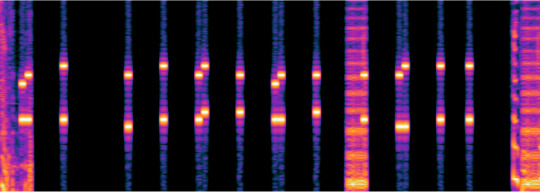
A spectrogram is a visual representation of the frequency content of an audio signal as it changes over time. In the image above, I’ve isolated the beeps produced by the clicking of the phone keypad. This section of the recording is longer than 10 seconds, so I also spliced together two screenshots. Any discrepancies you may notice in the image above are a product of that.
Each vertical line of dots represents one beep, and thus, one number. You’ll notice that there are two horizontal rows per beep, this is the magic of DTMF. There are 8 total frequencies involved in the DTMF system. The original DTMF keypad was laid out in a 4x4 format (below). The letter keys (A, B, C, and D) are no longer used for personal telecommunication. For digital decoding purposes, you will almost certainly not come across the letter keys, although they are still used by amateur radio operators, payphones, and the occasional equipment control system.

I was starting from scratch, with no knowledge of how a spectrogram worked with DTMF, so the first thing I did was create two recordings of myself clicking each number in my phone app (I am using iOS 15.7 on my iPhone XR).
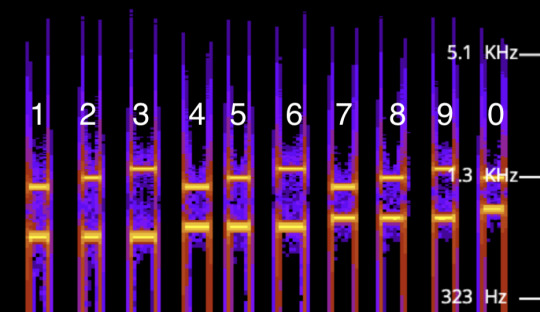

What you’ll begin to notice is that each number has its own combination of low and high tones. If you want to try to figure out the system on your own, now is the time.
Each variation in height represents a tone at a specific Hz. In order to decode this manually, you do not need to know the specific Hz of each number, you just need to understand the relational position of each tone, informed by its Hz.
I ended up throwing the original audio into Audacity so that I could create my own lines on the spectrogram for demonstration purposes.
First, I’m going to turn down the contrast to make it a little easier to see.

Now, I’m going to add some lines to match up the similar tones.
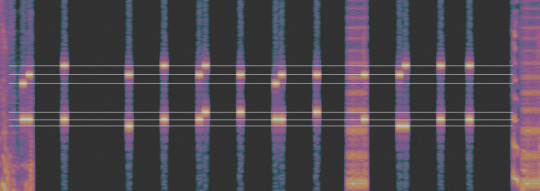
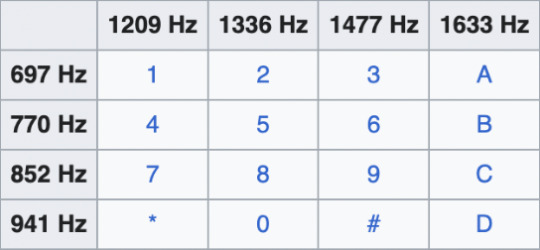
At this point, we have 6 layers of lines, there are no 0s present in this recording, if there were, we would have another line just above the bottom three. The use of the original DTMF structure with the ABCD keys would give us another line above the top three.
The simplest way to proceed is to categorize each set into Low, Medium, and High. You could choose any system — 1, 2, 3; a, b, c; whatever works for you. I recommend the LMH system because it’s visual and easy to keep track of.
I filled out the table below to show each numerical combination.

Two letters per number, each representing Low, Medium, or High (ultra High in the case of 0).
The first letter represents the top layer, and the second letter represents the bottom.
The corresponding Hz are listed in the third row for your reference.
I’ll walk you through the decoding process for the first two and then you can try the third.
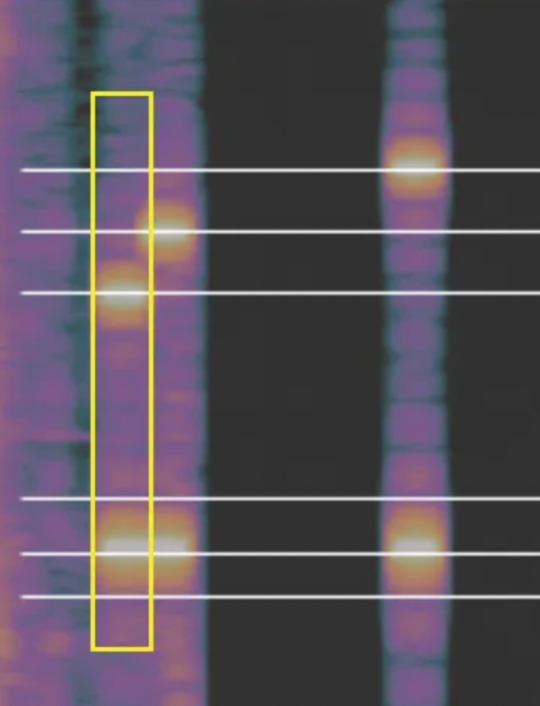
We’re going to look at the first column of tones (boxed in yellow).
This represents one number.
The first tone is crossed by the lowest of the top lines, it is marked L.
The second tone is crossed by the medium bottom line, it is marked M.
Together, they are LM — which, upon referencing the chart, is 4.
The second one is MM, which is 5.
Now try the third. (full answer at the end, scroll up now if you’d like to try it on your own — try it with lines or without!)
Once you get a feel for this, the process becomes much faster. The lines are purely for demonstrative purposes, with a little practice you’ll be able to quickly do this without lines.
And that’s how to decode DTMF manually through a spectrogram! Is it useless? Yes! Is it fun? That’s debatable!
If you’d like to help me compare cross-platform DTMF signaling, take a screen recording that captures you pressing 1234567890 on your phone keypad. Send the file to me through one of the methods outlined below. Please include your phone model and its latest software.
Discord — Adler#7210
Email me — [email protected]
If you’re seeing this on Tumblr, send me a DM!
Medium link - https://medium.com/@adler7210/manually-decoding-dtmf-through-spectrogram-562e4b0b99c3
The final answer to the CTF challenge — 4562 6598 4585 2366
Anyway, thanks for reading, enjoy decoding!
34 notes
·
View notes
Text
Here are ten different things you can use OSINT for:
Investigative journalism: Journalists can use OSINT to research and investigate stories, gather facts and uncover hidden information.
Due diligence: Companies can use OSINT to conduct background checks on potential employees, partners or suppliers.
Competitive intelligence: Businesses can use OSINT to gather intelligence on their competitors, such as pricing strategies, marketing campaigns, and product launches.
Law enforcement: Law enforcement agencies can use OSINT to investigate crimes, track down suspects, and gather evidence.
Risk management: OSINT can help organizations to assess and mitigate risks related to their operations, investments, or other activities.
Cybersecurity: Companies can use OSINT to monitor and detect cyber threats, such as data breaches, phishing attacks, and malware.
Reputation management: OSINT can help companies to monitor their online reputation, by tracking social media conversations, news articles and reviews.
Academic research: Researchers can use OSINT to gather data for academic studies, such as social media sentiment analysis, online surveys, and user-generated content analysis.
Humanitarian aid: OSINT can assist in disaster relief operations by gathering information on the location and needs of affected populations.
Personal security: Individuals can use OSINT to protect their personal information and privacy, by monitoring their online presence and identifying potential threats or risks.
15 notes
·
View notes
Text



Turkish Heavy Machine Guns in Ukraine
Turkey has provided a huge range of military equipment to Ukraine, in this video we'll look at Turkish-made M2 heavy machine guns and an unusual rotary grenade launcher in service with the Ukrainian Armed Forces.
youtube
Check out the accompanying article here.
#Ukraine War#M2 Browning#Machine Guns#Heavy Machine Guns#OSINT#Ukraine Russia War#Ukraine Conflict#Youtube
98 notes
·
View notes
Text
Online and Safe
True Crime genre sometimes deals with the aftermath of what could happen when dealing with stalkers. Often, too often in fact, women are simply not taken seriously when reporting a stalker to the authorities. Sadly, we cannot really count on them to protect us – they are effective at punishing an already done act, not so much at actually preventing it from happening. Restraining orders may help, but can you really count on them to scare away a dedicated stalker?
This article will try to illuminate the dangers of posting innocuous information, how to deal with an active case of cyber-stalking, and what you can do to protect yourself. In the end, it’s the one thing you have control over.
Stuff happens offline, too
Start with going through your already existing social media accounts and scrapping all photos of yourself and other people close to you. Do not worry! Facebook and Instagram both have features where you can download all of your old photos into a folder, so you don’t have to lose them forever – just keep them offline. Remove all tags from other people's photos, too.
It seems like a big hit at first, but does it actually matter if those photos are online? Don't let the good old "if it's not on FB, it didn't happen" get to you.
Best thing would be to completely delete those accounts all together, but if you're not all convinced about this, or you need certain social media accounts for your work or studies, you can always set them to private and be very picky of who you allow to see your information.
If you really want to post photos online for that dopamine rush you get when people "like" or "heart" them, do not post photos of yourself.
Do not post photos of inside your bedroom, do not post photos of inside your house, or your school or workplace. It's like giving a potential stalker a blueprint of places where you frequently go to, where you spend a lot of time, where you sleep and eat and relax (and let your guard down).

The meta of social media
Do not connect your phone number to any social media account. All your other accounts can be easily found once your phone number is revealed to the stalker, as well as your e-mail address. If a malicious third-party has your e-mail address, it's not that hard to get you locked out of your accounts and have your DMs read.
When it comes to social media accounts, avoid using your real name. Be as anonymous as you can be, and if a certain social media platform won’t let you do that, consider not joining it at all. When choosing a new username, make sure it’s not related to anything in your life.
Change your @ or username every now and then to keep them off your track, if the platform allows it. Keep separate and unrelated usernames for different platforms - be a Dandelion_Salad on Twitter, a Miniscule_Inconvenience on Reddit, just a random adjective in front of a random noun formula works great. Make sure there are no recognisable patterns in form of similar profile pictures, banners, bio descriptions, stuff like that. It's okay to keep things empty, too.
You cannot be “TorontoGirlie04”. You cannot be "NebraskanQueen99". You definitely cannot be "LadyThatLivesInThisParticularStreetBecauseItSoundsCool02".
You can, however, be “SnowGlobe23875728” or adopt a beloved character's name (any takers for "DipperGalaxy092930"?). Get creative and play around with the names, make a list of usernames you like, and use those instead.
EXIF is important
In case you didn't know, here's a little lesson on how uploading photos work, and how 4chan tracked down the guy who stood on salad in a Burger King. The key is in the EXIF data.
EXIF is short for Exchangeable Image File, and it basically stores all the information about the photo - exact location and time it was taken, at what aperture and shutter speed, if flash was used, basically everything. Most modern devices store this metadata within photos, and this is very easy to check.
The good news is that a lot of online hosting websites strap the EXIF data off the photos when they're uploaded to save space and bandwidth. The bad news is that not all of them do that, specially imageboards and forums.
But there are ways to circumvent it. The simplest way to scrap the EXIF data is to take a screenshot of the photo, and then uploading the screenshot instead of the original photo. This method should become a habit, as many platforms claim they don't store this information, but if they slip up, it will be an "oopsie" for them, and lots of headache for you.
Here is a link to EXIF Data Viewer to check for yourself. It can also be done within the settings of photos on phones. A good article on how to remove EXIF data on different devices and operating systems.
Please be careful with EXIF, as it can open a can of worms in the wrong hands.
Posting pictures of places you’re visiting should only be done after you’re not at the place anymore. Consistently posting your location in real time is not a very bright idea, specially if it’s from new places that are not familiar to you. Even famous people, who’s boundaries everyone tramples over and follows them around and somehow this is perfectly normalised, get really mad about their real-time location being posted for everyone to see.

"Social" in social media
Awareness of how social engineering works is of utmost importance. All the advice above is rendered useless if one is not careful enough and reveals the information unwittingly.
Making a post into the online nether to complain about the loud 90s music coming from a bar down the street from you seems quite innocent, until a person with bad intentions goes through your account’s history only to find a plethora of unrelated information about you that they can triangulate to find out almost everything about you. It rained heavily last Saturday and you couldn’t go see a really cool art exhibition in your city? You just gave a potential stalker valuable information.
That little voice in your head that makes you hesitate for a second before you blurt out your location should be absolutely listened to, don't drown it in self-gaslighting. We are basically socialised not to listen to our gut instinct, to give everyone the benefit of the doubt, until something bad happens, and then it's our fault for "allowing" it. Listen to your lizard brain, listen to your self-preservation instinct. It is very strong in women. You may be deemed a cold-hearted bitch, but at least you will keep your bodily autonomy.
Peer pressure is often where we falter. Find it in yourself not to fall for it, whether it's making an account on this new cool (and completely unsafe) "alternative" to Twitter, or sending nudes. Opinions of people you will not see after you graduate are temporary. Stalking can last for decades.
It's okay to lie about your gender online. No one really needs to know it, anyway. We're all ephemeral pixels on machines to each other. But posts and comments are online forever, and the more you talk about yourself, the more a stalker can piece together about your life. In that regard, avoid voluntarily giving information to provide context for your comment, ie "As 21f, I think...". It's usually useless info for people participating in the conversation, and it is absolutely invaluable to a stalker. Worse yet, it might even get people to start stalking you.
Do not use TikTok.
You will not "go viral". You will not "become TikTok famous". You will not "get sponsored".
All you do is post videos of yourself. In your room, in your school, in your workplace, in your favourite coffee shop. All the places you frequent, displayed freely for any prying eyes, and that might be taken away from you once the potential stalker decides to start reaching out from the shadows.
But I am a brand
Many ladies utilise social media to promote their creative work, and it's a great way to do so. Before you even start popping up on social media with your beautiful art, consider making a completely separate e-mail address. ProtonMail offers a great service. It takes a couple of minutes to set up, and you don't have to offer the blood of your firstborn to be allowed access. You can also create multiple accounts without any issues.
It doesn't really matter what your field is, whether it's making music, watercolour paintings, photography, or written word, you will want to create a closed circle with that e-mail (that is not connected to your real name). In other words, create your very own social media cosmos, where all the links only lead to the desired platforms of your own choice, and never to your personal pages. Your Carrd/Linktree only aggregate links to platforms where you've used the new e-mail to sign up. Make sure it's impenetrable and untraceable.
Do not use your personal e-mail address as a backup for your business e-mail. This is imperative!
Post only your creative stuff, never reveal any information about your person. Reblog, retweet, and like other people's stuff that you enjoy to fill up your pages, if content is your concern or you're in a creative lull. Do not fill it with pictures of your hand holding a Starbucks cup in front of a recognisable building. Definitely share memes, those are always great.
Turning it around
Now that we've covered most bases, here's a little goodie bag. Something sweet, that will feel oddly familiar to you, as with any woman, because we've been doing this for centuries amongst each other, but for very different reasons.
OSINT.
Open Source Intelligence. A simple name for all the information that is made publicly available, and the very reason why cyber stalking is not taken quite seriously. Actually hacking into accounts is a threshold for many stalkers, and is considered an escalation, because they simply operate on and collect information that their victims share publicly. As stated previously, the victim gives out the information sporadically, and it's seemingly unrelated to themselves, until the stalker goes down the history of the victim's account and puts all the puzzle pieces together.
Simply knowing and collecting information about a person, who decided to share it online for everyone to see, is not a bad thing in itself. It all depends on the intentions behind such collection of information, and what is the purpose of it. Finding out through the interwebs that your long-term boyfriend is married and has kids with another woman because you found their happy family pictures on her Instagram page is basically OSINT. Tracking a person's movements and finding out their place of residence to "keep an eye on them" is basically OSINT.
Since OSINT is simply finding and collecting public data, it is not inherently wrong. It's just data.
Here are some tools that people use. Check yourself. You might be surprised.
GitHub repository called UserRecon, which is a script that scraps the web to figure out where a certain username or e-mail has been used to make an account on various platforms.
OSINT Framework was made to scour the internet, on any platform you can imagine, and find any public information you might need. Open it up and see for yourself just how vast this is, and how easy it is.
My password is...
Surely you've been put into a situation where someone pressured you to share your password with them, whether it's for your e-mail or social media or Snapchat or whatever. Perhaps you've been made to change your password to "Ilovemybf" or something cheesy, without really realising that this gives them access to your accounts.
Here's a list of most commonly used passwords that have been scraped from the internet. All the leaked passwords are in there, and it's fairly easy to automate the process to "guess" your password just using this particular list. The list cannot be named because of doxxing potential, but it currently holds 14 344 391 most common passwords, and it is regularly updated.
These resources can be used to turn things around on to your stalker, if you have an active one right now. You can also check your digital footprint and see how well you've covered your tracks.
Most importantly, do not share your passwords and e-mail with anyone. You might as well kiss goodbye your accounts if you do that. People can be volatile and unpredictable, and no matter how much you trust them in the moment, do not give them the key to turn your whole life upside down if something goes wrong. And something always goes wrong.
Be safe. Be mindful of your privacy. Don't give it for free.

21 notes
·
View notes
Text
If I’m being honest, the most useful skill for hacking is learning to do research. And since Google’s search is going to shit, allow me to detail some of the methods I use to do OSINT and general research.
Google dorking is the use of advanced syntax to make incredibly fine-grained searches, potentially exposing information that wasn’t supposed to be on the internet:
Some of my go-to filters are as follows:
“Query” searches for documents that have at least one field containing the exact string.
site: allows for a specific site to be searched. See also inurl and intitle.
type: specifies the tor of resource to look for. Common examples are log files, PDFs, and the sitemap.xml file.
Metasearch engines (such as SearxNG) permit you to access results from several web-crawlers at once, including some for specialized databases. There are several public instances available, as well as some that work over tor, but you can also self-host your own.
IVRE is a self-hosted tool that allows you to create a database of host scans (when I say self-hosted, I mean that you can run this in a docker container on your laptop). This can be useful for finding things that search engines don’t show you, like how two servers are related, where a website lives, etc. I’ve used this tool before, in my investigation into the Canary Mission and its backers.
Spiderfoot is like IVRE, but for social networks. It is also a self-hosted database. I have also used this in the Canary Mission investigation.
Some miscellaneous websites/web tools I use:
SecurityTrails: look up DNS history for a domain
BugMeNot: shared logins for when creating an account is not in your best interest.
Shodan/Censys: you have to make an account for these, so I don’t usually recommend them.
OSINT framework: another useful index of tools for information gathering.
12 notes
·
View notes
Text
Still unconfirmed balloon - Chinese or .... many countries use weather balloons and others - await confirmation..
2 notes
·
View notes