#Detection
Photo

Detection - esuthio
228 notes
·
View notes
Text
Researchers detect a new molecule in space
New Post has been published on https://thedigitalinsider.com/researchers-detect-a-new-molecule-in-space/
Researchers detect a new molecule in space
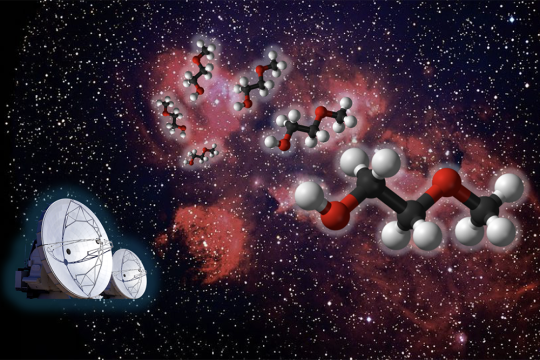

New research from the group of MIT Professor Brett McGuire has revealed the presence of a previously unknown molecule in space. The team’s open-access paper, “Rotational Spectrum and First Interstellar Detection of 2-Methoxyethanol Using ALMA Observations of NGC 6334I,” appears in April 12 issue of The Astrophysical Journal Letters.
Zachary T.P. Fried, a graduate student in the McGuire group and the lead author of the publication, worked to assemble a puzzle comprised of pieces collected from across the globe, extending beyond MIT to France, Florida, Virginia, and Copenhagen, to achieve this exciting discovery.
“Our group tries to understand what molecules are present in regions of space where stars and solar systems will eventually take shape,” explains Fried. “This allows us to piece together how chemistry evolves alongside the process of star and planet formation. We do this by looking at the rotational spectra of molecules, the unique patterns of light they give off as they tumble end-over-end in space. These patterns are fingerprints (barcodes) for molecules. To detect new molecules in space, we first must have an idea of what molecule we want to look for, then we can record its spectrum in the lab here on Earth, and then finally we look for that spectrum in space using telescopes.”
Searching for molecules in space
The McGuire Group has recently begun to utilize machine learning to suggest good target molecules to search for. In 2023, one of these machine learning models suggested the researchers target a molecule known as 2-methoxyethanol.
“There are a number of ‘methoxy’ molecules in space, like dimethyl ether, methoxymethanol, ethyl methyl ether, and methyl formate, but 2-methoxyethanol would be the largest and most complex ever seen,” says Fried. To detect this molecule using radiotelescope observations, the group first needed to measure and analyze its rotational spectrum on Earth. The researchers combined experiments from the University of Lille (Lille, France), the New College of Florida (Sarasota, Florida), and the McGuire lab at MIT to measure this spectrum over a broadband region of frequencies ranging from the microwave to sub-millimeter wave regimes (approximately 8 to 500 gigahertz).
The data gleaned from these measurements permitted a search for the molecule using Atacama Large Millimeter/submillimeter Array (ALMA) observations toward two separate star-forming regions: NGC 6334I and IRAS 16293-2422B. Members of the McGuire group analyzed these telescope observations alongside researchers at the National Radio Astronomy Observatory (Charlottesville, Virginia) and the University of Copenhagen, Denmark.
“Ultimately, we observed 25 rotational lines of 2-methoxyethanol that lined up with the molecular signal observed toward NGC 6334I (the barcode matched!), thus resulting in a secure detection of 2-methoxyethanol in this source,” says Fried. “This allowed us to then derive physical parameters of the molecule toward NGC 6334I, such as its abundance and excitation temperature. It also enabled an investigation of the possible chemical formation pathways from known interstellar precursors.”
Looking forward
Molecular discoveries like this one help the researchers to better understand the development of molecular complexity in space during the star formation process. 2-methoxyethanol, which contains 13 atoms, is quite large for interstellar standards — as of 2021, only six species larger than 13 atoms were detected outside the solar system, many by McGuire’s group, and all of them existing as ringed structures.
“Continued observations of large molecules and subsequent derivations of their abundances allows us to advance our knowledge of how efficiently large molecules can form and by which specific reactions they may be produced,” says Fried. “Additionally, since we detected this molecule in NGC 6334I but not in IRAS 16293-2422B, we were presented with a unique opportunity to look into how the differing physical conditions of these two sources may be affecting the chemistry that can occur.”
#2023#ALMA#Astronomy#Astrophysics#atoms#chemical#chemistry#college#complexity#data#Denmark#detection#development#Discoveries#earth#ether#fingerprints#form#France#how#interstellar#it#learning#Light#Machine Learning#measure#measurements#members#mit#molecules
14 notes
·
View notes
Video
Lade Round Sound mirror by Robert Craig
Via Flickr:
#shingle#detection#technology#experiment#1930s#Greatstone#Lydd on Sea#lade#sound mirror#dungeness#Romney Marsh#Kent#English Channel#England#flickr
11 notes
·
View notes
Text
Dreambite by Rudok's Tavern




#rudok's tavern#dreambite#magic weapons#very rare#light#finesse#shortsword#sword#swords#dreams#dreaming#dark#psychic#psionic#cursing#health#healing#recovery#leeching#detection#perception
10 notes
·
View notes
Text
fated mates? oh, no no no. fated ENEMIES. TWO HALVES OF THE SAME SOUL DESTINED TO DOOM BOTH EACH OTHER AND ALL OF HUMANITY.
#vagueposting#vague posting#soulmates#soul enemies#fated mates#fated enemies#am i referring to my own characters?#yes#do i care?#no#not particularly#soulmate au#detection#oc#character rambles#friends to enemies
2 notes
·
View notes
Text
// detection spoilers
these pieces are unfinished but I love them so much I have to share the sketches immediately


I kept seeing this quote everywhere, and it fit Jamison and Fitz so well that I had to draw them. this is based on an event I have planned for the 3rd/4th season finale.
without spoiling anything else, I'll just say this: everything goes horribly, horribly wrong.
#fitz hawthorne#jamison davis#detection#detection comic#detection comic official#oc#original character#art#sketch#digital aritst#digital drawing#digital art#digital artwork#wip stuff#art wip#drama#my comic#my series#my webcomic#my webseries#wip#work in progress#finale#queer artist#small artist#artists of tumblr#artists on tumblr#sad gay people#this is a horror series#do you really expect things to end well for anyone
11 notes
·
View notes
Text
Buzzing with Potential: Bees and Organic Semiconductors Unite for Explosive Plume Detection
Picture this: a team of honey bees working alongside cutting-edge technology, helping us detect explosive plumes in a fraction of the time it takes to train dogs. It may sound like a scene from a sci-fi movie, but researchers have harnessed the power of nature and combined it with the capabilities of organic semiconductor films to create a biohybrid system that could revolutionize explosive detection.
Traditionally, dogs have been our allies in sniffing out dangerous explosives due to their exceptional olfactory prowess. But training these canine heroes can take months, and there are limitations to their availability and accessibility. This is where our tiny friends, the honey bees, step in. With their incredible sense of smell and quick learning abilities, bees are proving to be a formidable force in the world of explosive detection.
At the heart of this biohybrid system lies the organic semiconductor film. These thin, flexible films are engineered to mimic the capabilities of a dog's nose. By capturing and amplifying the odor molecules present in an explosive plume, they provide valuable information to the bees, who can quickly and accurately identify the presence of explosive materials.
The training process for bees in this biohybrid system is remarkably efficient. In just a matter of hours, these remarkable insects can be trained to associate a specific odor, emitted by the organic semiconductor film, with a sugar solution reward. Through a process called classical conditioning, the bees quickly learn to extend their proboscis, or tongue, in response to the targeted odor, signaling the presence of an explosive plume.
Not only do bees learn this association quickly, but they also showcase impressive retention of this information. Studies have shown that bees retain their training for several days, allowing them to be consistently reliable in detecting explosive plumes over an extended period.
One of the major advantages of using bees in this biohybrid system is their sheer numbers. A hive can house thousands of bees, providing us with a scalable and versatile detection system. Additionally, bees are easily transportable and can be deployed to various locations, making them highly adaptable for different scenarios, such as airports, public spaces, or even disaster zones.
The collaborative efforts of nature and technology offer us a glimpse into an efficient, cost-effective, and sustainable solution for explosive detection. By utilizing the honey bee's natural abilities and combining them with the innovation of organic semiconductor films, we can potentially enhance our security measures, while also respecting and preserving the environment.
However, it's important to note that this biohybrid system is still in its early stages of development. Challenges such as optimizing the organic semiconductor films' sensitivity and stability, as well as ensuring the safety and well-being of the bees, need to be addressed before widespread implementation can occur. Researchers are actively working towards overcoming these hurdles and refining the system to ensure its effectiveness and reliability.
As our understanding of nature and technology continues to evolve, so does our ability to create groundbreaking solutions. The honey bee biohybrid system holds tremendous promise in the field of explosive plume detection. With bees' remarkable learning capabilities and the power of organic semiconductor films, we are on the cusp of a new era in security technology. The future is buzzing with potential, and these tiny creatures might just be the key to unlocking it.

#ko-fi#kofi#geeknik#nostr#art#blog#writing#bees#biohybrid#explosives#detection#semiconductor#organic#honeybee#technology#nature
2 notes
·
View notes
Text

Interested in learning Development and Testing?
#biometric#detection#processing#normalization#extraction#matching#webdevelopment#software testing#training#placement#programming
14 notes
·
View notes
Text

Placing an Ad is as important as designing it. Run each account without the risk of getting banned by the super-smart algorithm. How? Well, VMLOGIN has made it possible. The virtual browsing platform is exceptionally good in eliminating broken links and misleading creatives. Plus, run hundreds of accounts with zero risk. Isn’t it amazing?
Connect With Us:
Free trial link: https://www.vmlogin.us/free-trial.html
Download link: https://www.vmlogin.us/download.html
Tutorials: https://www.vmlogin.us/help/
Telegram Official Channel:https://t.me/vmloginUS
#virtualbrowser#searchsafely#datasafetyy#virtualplatform#dataprotection#Secured#platform#freesuffering#incognito#vmlogin#software#digitalchain#detection#secureconnection#protection#securitymanagement
1 note
·
View note
Text
Leak Detection Service

We are Providing Line Leak Detection Service in Underground Pipes South London, Surrey, Berkshire, Hampshire, UK England leak Detection Company Call Us 03334444564 Near me Leak Detection in Underground and Pool Leak Pipes We tend to take it for granted that water will come out of the tap and that this water will be safe to drink or “potable” as a technical term, rarely do we consider
2 notes
·
View notes
Text


I underestimate just how much voice actors can accomplish by doing extra unlisted credits in the recording booth’s group session. But it’s also BECAUSE of my experience listening to some examples during my maturity, that I find some old DM episodes (which I never got a chance to see growing up) boring, once I pinpoint the similar vocal tones from those 4 80’s actors doing unlisted credit characters too.
Still, am I wrong that Sammy Boy voiced Zog?
#layouts#screenshots#hobby#habit#youtube#sensory#sound#hearing#experience#heightened hearing#autistic spectrum#i ❤️ voice actors#detection#unlisted credits#group#recording booth#too obvious#old enough to distinguish#donatello 2003#heart turtles#sam riegel#teenage mutant ninja turtles 2003#donny kun#too inexperienced back then#vocal tones#it’s a game to me#tmnt 2003 season 1#similarities#obscure#discreet
2 notes
·
View notes
Text
Anticipating the future of malicious open-source packages: next gen insights
New Post has been published on https://thedigitalinsider.com/anticipating-the-future-of-malicious-open-source-packages-next-gen-insights/
Anticipating the future of malicious open-source packages: next gen insights


Ori Abramovsky is the Head of Data Science of the Developer-First group at Check Point, where he leads the development and application of machine learning models to the source code domain. With extensive experience in various machine learning types, Ori specializes in bringing AI applications to life. He is committed to bridging the gap between theory and real-world application and is passionate about harnessing the power of AI to solve complex business challenges.
In this thoughtful and incisive interview, Check Point’s Developer-First Head of Data Science, Ori Abramovsky discusses malicious open-source packages. While malicious open-source packages aren’t new, their popularity among hackers is increasing. Discover attack vectors, how malicious packages conceal their intent, and risk mitigation measures. The best prevention measure is…Read the interview to find out.
What kinds of trends are you seeing in relation to malicious open-source packages?
The main trend we’re seeing relates to the increasing sophistication and prevalence of malicious open-source packages. While registries are implementing stricter measures, such as PyPI’s recent mandate for users to adopt two-factor authentication, the advances of Large Language Models (LLMs) pose significant challenges to safeguarding against such threats. Previously, hackers needed substantial expertise in order to create malicious packages. Now, all they need is access to LLMs and to find the right prompts for them. The barriers to entry have significantly decreased.
While LLMs democratise knowledge, they also make it much easier to distribute malicious techniques. As a result, it’s fair to assume that we should anticipate an increasing volume of sophisticated attacks. Moreover, we’re already in the middle of that shift, seeing these attacks extending beyond traditional domains like NPM and PyPI, manifesting in various forms such as malicious VSCode extensions and compromised Hugging Face models. To sum it up, the accessibility of LLMs empowers malicious actors, indicating a need for heightened vigilance across all open-source domains. Exciting yet challenging times lie ahead, necessitating preparedness.
Are there specific attack types that are most popular among hackers, and if so, what are they?
Malicious open-source packages can be applied based on the stage of infection: install (as part of the install process), first use (once the package has been imported), and runtime (infection is hidden as part of some functionality and will be activated once the user will use that functionality). Install and first use attacks typically employ simpler techniques; prioritizing volume over complexity, aiming to remain undetected long enough to infect users (assuming that some users will mistakenly install them). In contrast, runtime attacks are typically more sophisticated, with hackers investing efforts in concealing their malicious intent. As a result, the attacks are harder to detect, but come with a pricier tag. They last longer and therefore have higher chances of becoming a zero-day affecting more users.
Malicious packages employ diverse methods to conceal their intent, ranging from manipulating package structures (the simpler ones will commonly include only the malicious code, the more sophisticated ones can even be an exact copy of a legit package), to employing various obfuscation techniques (from classic methods such as base64 encoding, to more advanced techniques, such as steganography). The downside of using such concealment methods can make them susceptible to detection, as many Yara detection rules specifically target these signs of obfuscation. Given the emergence of Large Language Models (LLMs), hackers have greater access to advanced techniques for hiding malicious intent and we should expect to see more sophisticated and innovative concealment methods in the future.
Hackers tend to exploit opportunities where hacking is easier or more likely, with studies indicating a preference for targeting dynamic installation flows in registries like PyPI and NPM due to their simplicity in generating attacks. While research suggests a higher prevalence of such attacks in source code languages with dynamic installation flows, the accessibility of LLMs facilitates the adaptation of these attacks to new platforms, potentially leading hackers to explore less visible domains for their malicious activities.
How can organisations mitigate the risk associated with malicious open-source packages? How can CISOs ensure protection/prevention?
The foremost strategy for organisations to mitigate the risk posed by malicious open-source packages is through education. One should not use open-source code without properly knowing its origins. Ignorance in this realm does not lead to bliss. Therefore, implementing practices such as double-checking the authenticity of packages before installation is crucial. Looking into aspects like the accuracy of package descriptions, their reputation, community engagement (such as stars and user feedback), the quality of documentation in the associated GitHub repository, and its track record of reliability is also critical. By paying attention to these details, organisations can significantly reduce the likelihood of falling victim to malicious packages.
The fundamental challenge lies in addressing the ignorance regarding the risks associated with open-source software. Many users fail to recognize the potential threats and consequently, are prone to exploring and installing new packages without adequate scrutiny. Therefore, it is incumbent upon Chief Information Security Officers (CISOs) to actively participate in the decision-making process regarding the selection and usage of open-source packages within their organisations.
Despite best efforts, mistakes can still occur. To bolster defences, organisations should implement complementary protection services designed to monitor and verify the integrity of packages being installed. These measures serve as an additional layer of defence, helping to detect and mitigate potential threats in real-time.
What role does threat intelligence play in identifying and mitigating risks related to open-source packages?
Traditionally, threat intelligence has played a crucial role in identifying and mitigating risks associated with open-source packages. Dark web forums and other underground channels were primary sources for discussing and sharing malicious code snippets. This allowed security professionals to monitor and defend against these snippets using straightforward Yara rules. Additionally, threat intelligence facilitated the identification of suspicious package owners and related GitHub repositories, aiding in the early detection of potential threats. While effective for simpler cases of malicious code, this approach may struggle to keep pace with the evolving sophistication of attacks, particularly in light of advancements like Large Language Models (LLMs).
These days, with the rise of LLMs, it’s reasonable to expect hackers to innovate new methods through which to conduct malicious activity, prioritizing novel techniques over rehashing old samples that are easily identifiable by Yara rules. Consequently, while threat intelligence remains valuable, it should be supplemented with more advanced analysis techniques to thoroughly assess the integrity of open-source packages. This combined approach ensures a comprehensive defence against emerging threats, especially within less-monitored ecosystems, where traditional threat intelligence may be less effective.
What to anticipate in the future?
The emergence of Large Language Models (LLMs) is revolutionising every aspect of the software world, including the malicious domain. From the perspective of hackers, this development’s immediate implication equates to more complicated malicious attacks, more diverse attacks and more attacks, in general (leveraging LLMs to optimise strategies). Looking forward, we should anticipate hackers trying to target the LLMs themselves, using techniques like prompt injection or by trying to attack the LLM agents. New types and domains of malicious attacks are probably about to emerge.
Looking at the malicious open-source packages domain in general, a place we should probably start watching is Github. Historically, malicious campaigns have targeted open-source registries such as PyPI and NPM, with auxiliary support from platforms like GitHub, Dropbox, and Pastebin for hosting malicious components or publishing exploited data pieces. However, as these registries adopt more stringent security measures and become increasingly monitored, hackers are likely to seek out new “dark spots” such as extensions, marketplaces, and GitHub itself. Consequently, malicious code has the potential to infiltrate EVERY open-source component we utilise, necessitating vigilance and proactive measures to safeguard against such threats.
#Accessibility#ai#Analysis#applications#approach#attention#authentication#Business#challenge#Check Point#CISOs#code#Community#complexity#comprehensive#Dark#Dark web#data#data privacy#data protection#data science#details#detection#Developer#development#documentation#domains#double#dropbox#Ecosystems
3 notes
·
View notes
Text
obviously people steal things from other people it's one of the oldest tricks in the book but it still always surprises me to learn that people plagiarise because my introduction to the concept was basically being told that if i ever plagiarised anything i would be executed by firing squad and my head would be removed and displayed on a spike outside the walls of the hallowed academic institution i was attending as a warning to others
#🐉#like they were not fucking around they were like you will be BLACKLISTED we will EXILE you there may be FINANCIAL RESTITUTION OWED#if our plagiarism software detects anything suspicious we will FLAY YOU ALIVE IN THE TOWN SQUARE#i still wake up in a cold sweat sometimes wondering if i cited my sources correctly
52K notes
·
View notes
Text
Lamp of Ethereal Azure by Boss Loot


#boss loot#magic items#magic weapons#tools#rare#light#radiant#radiance#glow#lantern#lanterns#vision#sight#invisible#invisibility#breaker#breaking#bane#detection#perception#crystals#crystal#gem#gems
18 notes
·
View notes
Text
I've been trying to develop my art style a bit and I think I've come up with something close to what I'm going for

everything is a little wonky right now, but I feel like I could turn it into something really cool with some practice
(also! I'm planning on drawing a lot over the break, so look out for that if you're interested! I might even start Detection sometime soon)
#seriously#i have been developing this comic#and it's plot#and world building#and soul system#for years now#I really just want to start working on everything#small artist#artists on tumblr#art#sketch#sketches#detection#detection comic#detection comic official#pencil#art style#art stuff#my comic#web comic#my webcomic#comic
7 notes
·
View notes
