#Mobilehacks
Photo
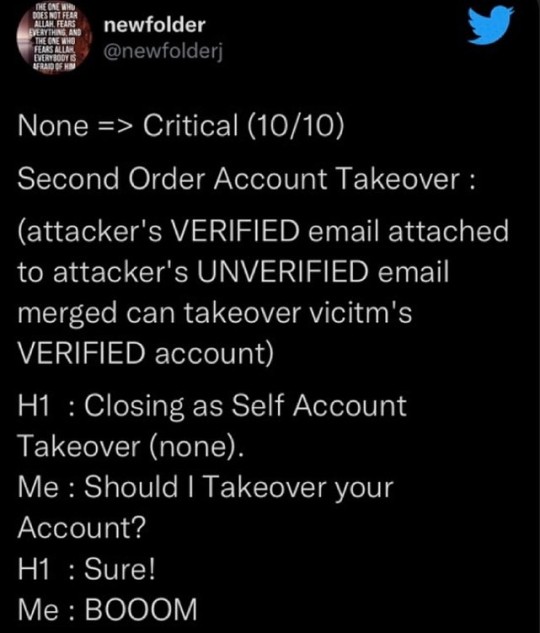
Daily Tweets. #tweets #tweetsfromtwitter #hackertweet #hackerinstagram #biohacking #applicationsecurity #lifehacks #mobilehacks #penetrationtesting #offensivesecurity https://www.instagram.com/p/ClRSbmVy0Mq/?igshid=NGJjMDIxMWI=
#tweets#tweetsfromtwitter#hackertweet#hackerinstagram#biohacking#applicationsecurity#lifehacks#mobilehacks#penetrationtesting#offensivesecurity
4 notes
·
View notes
Text
How to protect your phone from hackers in Tamil

#smartphones#hacking#cybersecurity#smartphonehacks#techtips#iphonehacks#techhacks#mobilehacks#phonehacks
0 notes
Text
Amazing Mobile Tips and Tricks | Normal Mobile Users Need to Know

some mobile tips and tricks that can improve your mobile experience:
More details click here
0 notes
Text
Collect Evidence of Your Unfaithful Partner by Mobile Hacker
Uncover signs of infidelity by hiring a skilled mobile hacker. Obtain discreet evidence to confront suspicions and make informed decisions.

Infidelity can be a devastating blow to any relationship, causing heartbreak and shattered trust. In such situations, it's natural to seek answers and clarity, and sometimes that means collecting evidence to confirm suspicions. With the advent of technology, particularly mobile devices, one method gaining attention is through mobile hacking. This article aims to delve into the complexities of this issue, from understanding mobile hacking to the ethical considerations surrounding it.
📌Signs of an Unfaithful Partner
Before considering extreme measures like mobile hacking, it's crucial to recognize the signs of an unfaithful partner. Here are some signs that may indicate an unfaithful partner:
Behavioral Changes: Pay attention to any sudden shifts in behavior, such as increased irritability, moodiness, or unexplained absences. Changes in routine without a valid explanation could be a red flag.
Secrecy with Devices: If your partner suddenly becomes overly protective of their phone, laptop, or other devices, it might indicate they are hiding something. They may start keeping their devices locked or constantly checking messages when they didn't before.
Unusual Communication Patterns: Notice if your partner has started communicating more frequently with someone new, especially if they seem secretive about it. They might also become defensive or evasive when questioned about their interactions.
Lack of Interest in Intimacy: A decline in physical intimacy or a sudden disinterest in being close to you could signal emotional or physical infidelity. Pay attention to any changes in affection or desire for closeness.
Increased Focus on Appearance: If your partner suddenly starts paying more attention to their appearance, such as going to the gym more often or buying new clothes, it could be a sign that they are trying to impress someone else.
Unexplained Expenses: Keep track of any unexplained expenses or withdrawals from joint accounts. If your partner is spending money on gifts, meals, or activities without a reasonable explanation, it could be a sign of infidelity.
Gut Feeling: Trust your instincts. If something feels off in your relationship, even if you can't pinpoint exactly what it is, it's important to acknowledge and address those feelings. Your intuition can be a powerful indicator of underlying issues.
📌Why mobile hack is needed
Confirm Suspicions: Mobile hacking may be needed to confirm suspicions of dishonesty or infidelity within a relationship. By accessing messages, call logs, or social media accounts, individuals can gather evidence to validate their concerns and make informed decisions about the future of the relationship.
Ensure Safety: In cases where there are concerns about safety or well-being, such as suspected abuse or criminal activity, mobile hacking may be necessary to gather evidence for protection. By monitoring communications or tracking location data, individuals can take proactive steps to ensure their safety or that of others.
Protect Personal Data: With the increasing prevalence of cyber threats and data breaches, mobile hacking may be required to protect personal data from unauthorized access. Ethical hackers or security professionals can identify vulnerabilities in systems or applications, helping individuals and organizations strengthen their cybersecurity defenses and safeguard sensitive information.
Parental Monitoring: Parents may need to use mobile hacking techniques to monitor their children's online activities and ensure their safety in the digital world. By tracking their children's communication, social media interactions, and internet browsing habits, parents can identify potential risks and intervene to protect them from harm.
Recover Lost Information: In situations where individuals have lost access to their own accounts or data due to forgotten passwords or technical issues, mobile hacking may be necessary to recover valuable information. By using ethical hacking techniques, individuals can regain access to their accounts and retrieve important data, preventing potential loss or damage.
📌How to Hire a Mobile Hacker
Hire a professional mobile hacker It is very important to keep certain things in mind. Some of the points attempted are:
Research and Vet: Start by researching reputable hacking services or professionals online. Look for reviews, testimonials, and recommendations from trusted sources to vet their credibility and reliability. Ensure they have a track record of ethical conduct and successful outcomes.
Verify Expertise: Verify the expertise and experience of the mobile hacker. Look for certifications, qualifications, or previous work that demonstrates their proficiency in mobile hacking. Ideally, they should have experience in the specific type of hacking you require, whether it's accessing devices, recovering data, or monitoring communications.
Ensure Legal Compliance: Before hiring a mobile hacker, ensure they operate within the bounds of the law. Discuss the legality of the hacking services they offer and confirm that they adhere to ethical standards and privacy regulations. Avoid engaging with hackers who engage in illegal activities or compromise personal privacy.
Communication and Transparency: Establish clear communication channels with the mobile hacker and ensure transparency throughout the hiring process. Discuss your objectives, concerns, and expectations openly, and ask any questions you may have about the hacking process. A professional hacker should be transparent about their methods, potential risks, and limitations.
Agree on Terms and Payment: Once you've selected a mobile hacker, agree on the terms of the engagement and payment arrangements. Ensure that all terms, including scope of work, timelines, and fees, are clearly outlined in a written contract or agreement. Be wary of hackers who demand full payment upfront or refuse to provide written documentation of the engagement terms.
🔯 Related: How To Find A Good Phone Hacker
📌Seeking Professional Help
If suspicions persist or the situation becomes too overwhelming to handle alone, don't hesitate to seek professional help. Relationship therapy or counseling can provide valuable support and guidance in navigating difficult emotions and decisions. Additionally, consulting with a legal expert can offer clarity on your rights and options moving forward.
📌Advantages of mobile hacks

While it's important to acknowledge the risks and ethical considerations associated with mobile hacking, some individuals may perceive certain advantages in specific contexts. However, it's crucial to emphasize that these perceived advantages do not justify or outweigh the potential consequences and ethical concerns involved. Here are some points that some individuals might consider advantages of mobile hacks:
Gathering Evidence: In situations where there are genuine concerns about safety or well-being, such as cases of suspected abuse or criminal activity, accessing information through mobile hacking could potentially provide evidence to protect oneself or others.
Parental Control: Some parents may use mobile hacking as a means of monitoring their children's online activities to ensure their safety and well-being. This can include tracking their whereabouts, monitoring their communication with strangers, and safeguarding them from potential online threats.
Security Testing: Ethical hackers or security professionals may use mobile hacking techniques to identify vulnerabilities in systems or applications. By uncovering weaknesses, they can help organizations strengthen their cybersecurity measures and protect against malicious attacks.
Data Recovery: In instances where individuals have lost access to their own accounts or data due to forgotten passwords or technical issues, mobile hacking might be seen as a last resort for recovering valuable information.
Awareness and Education: Understanding how mobile hacking works and its potential consequences can raise awareness about digital security among individuals and organizations. This knowledge can empower people to take proactive measures to protect their personal information and prevent unauthorized access.
📌Final Touch
In conclusion, dealing with suspicions of infidelity is a challenging and emotionally taxing experience. While mobile hacking may seem like a solution, it's essential to consider the ethical and legal implications carefully. Open communication, trust, and respect are the foundation of any healthy relationship, and maintaining these values should always be prioritized.
#mobilehacking#mobile hacker#hackerslistco#hackerslist#cybersecurity#hacking#hackers#hacker#us hackers#phone spy
0 notes
Text
What to do if your phone is hacked?

Hacking has become increasingly common on mobile devices in the past few years. A hacker could be watching your every move, whether it's gaining access to your personal information or even your credit card details. With more than a billion mobile phone users worldwide, mobile hacking is becoming an increasing problem. In this article, you'll learn about how cybercriminals hack your phone and what you can do to protect yourself from them!
Now share your Thoughts with us in the 𝗖𝗼𝗺𝗺𝗲𝗻𝘁 section
Read the full blog: https://bit.ly/3g3zpTL
0 notes
Text
[Media] Thanks Mobile Hacker
Thanks Mobile Hacker
We want to give credit to the creators of the videos we used in our posts.
▫️ t.me/androidMalware
▫️ youtube.com/@mobilehacker
▫️ instagram.com/mobile_hacker0
#video #channel
1 note
·
View note
Video
youtube
HOW TO RECORD VIDEOS USING MIC IN YOUR MOBILE PHONE
1 note
·
View note
Text
MobileHackersWeapons - Mobile Hacker's Weapons / A Collection Of Cool Tools
MobileHackersWeapons - Mobile Hacker's Weapons / A Collection Of Cool Tools Used By Mobile Hackers #AwesomeList
A collection of cool tools used by Mobile hackers. Happy hacking , Happy bug-hunting
Weapons
OS
Type
Name
Description
All
Analysis
RMS-Runtime-Mobile-Security
Runtime Mobile Security (RMS) – is a powerful web interface that helps you to manipulate Android and iOS Apps at Runtime
All
Analysis
scrounger
Mobile application testing toolkit
All
Proxy
BurpSuite
The BurpSuite
All
Proxy
hetty
Hetty…

View On WordPress
#Awesome List#Bugbounty#Bugbountytips#COLLECTION#Cool#Hacker039s#Hackers#Malware Analysis#Mobile#MobileHackersWeapons#Mobilehacks#Scanner#Tools#Weapons
0 notes
Photo

Welcome to the CAEHP i.e. the Complete Android Ethical Hacking Practical Course . My name is DEBAYAN DEY and i will be your Instructor for the CAEHP Course. CAEHP is one of the Most Comprehensive Real World 100% Hands-On Practical Approach on Android Ethical Hacking...!!! Now this course is designed for anyone who is interested in learning how an attacker attack and get the information from the victim. CAEHP is designed by keeping in mind that most of us are not having laptops or computer machine to work for most of the time. Thats why in this course curriculum , you need not require any laptop or computer system. Only you need an android device and this entire course is 100% practical based ! isn't this amazing ??? You may see 6 or 7 section today , once you land in this course after few weeks , you'll see more sections and videos are added up. so this is the advantage of taking this course that you'll get regular updates about the new features and attacks and how you , as an individual can prevent yourself from such an attack. so currently in CAEHP course , we have 6 Section + 1 Optional Section and 1 Bonus Section #hacking #hackinglife #hackingtheplanet #hackingfriday #cybersecurity #mobilehacks #penetrationtesting #ethicalhacking #hackingout #kalilinux #hackingmarathon #hackinginstagram #hackingexposed #hackingdata #hackingbegins #hackinggame #hackingforgood #hackingnews #hackingeducation #hackingsimulator #metasploit #hackingthehuman #hackingchallenge #hackingtool #hackingworkshop (at Bangalore, India) https://www.instagram.com/p/CB7KlGoFE4b/?igshid=lzpoybnqjn7r
#hacking#hackinglife#hackingtheplanet#hackingfriday#cybersecurity#mobilehacks#penetrationtesting#ethicalhacking#hackingout#kalilinux#hackingmarathon#hackinginstagram#hackingexposed#hackingdata#hackingbegins#hackinggame#hackingforgood#hackingnews#hackingeducation#hackingsimulator#metasploit#hackingthehuman#hackingchallenge#hackingtool#hackingworkshop
1 note
·
View note
Text
Hacking Cases
Primary Hackers are offering the best services for hacking cases at affordable prices. Phone hacking is a critical security issue so we will project done within 2 hours. Visit our website today to learn more.
1 note
·
View note
Text
Watch "የእርስዎ ሞባይል መጠለፍ እና አለመጠለፉን እንዴት ማወቅ ይችላሉ? እንዴት ሊጠለፉ ይችላሉ? እንዴትስ ከጠላፊዎች ማምለጥ ይቻላል? hacked not hacked" on YouTube
youtube
#infotainment#technology#wondershare#electronics#computertips#mobilehack#artificial intelligence#metal#Youtube
1 note
·
View note
Link
in this article, we’ll share the way to Hack unlimited health with the Call of Duty Mobile hack. By hacking unlimited health you are able to defeat your enemy so easily, You do not die no matter what! Bluezone, Bulletsfall damage, vehicle damage, and explosions don’t reduce your health!.
1 note
·
View note
Link
#mobile pentesting#Mobile#Hacking#Android#BurpSuite#Bugbounty#AndroidPentest#MobilePentest#MobileHacking#AndroidHacking#VAPT#Malware#AndroidRAT
0 notes
Photo
अपने MOBILE📱 को हैक होने से कैसे बचाएं? How to secoure mobile from hacking? #besttips #avoidhacking #hack #mobilehacking #kdrathore #instagood (at Jodhpur - The Blue Heaven) https://www.instagram.com/p/CRyAN2KrHLg/?utm_medium=tumblr
0 notes
