#Data security
Text

390 notes
·
View notes
Text
If you've ever used 23andMe to learn more about your family ancestry, you could be eligible for compensation due to a class-action lawsuit against the company.
Law firms in Toronto and Vancouver launched a class-action lawsuit against 23andMe this week in response to a data breach that exposed users’ highly sensitive and valuable personal information earlier this year.
"The action alleges that contrary to their promises, statements and representations, as well as the privacy regulation and industry standards applicable to them, [23andMe] did not introduce, implement or maintain proper or adequate data retention and data protection practices," reads the lawsuit.
Full article
Tagging: @politicsofcanada
#cdnpoli#canada#canadian politics#canadian news#canadian#23andme#23 and me#class action#class action lawsuit#data protection#data security#privacy#data privacy
148 notes
·
View notes
Text

#memes#meme#throwback#lol#funny#lol memes#funny memes#funny meme haha#funny stuff#my job is killing me#my job#cyber security#data security#secure#passwords
26 notes
·
View notes
Photo

Read an article by the civic technology organization Pollicy to learn about the biggest challenges to digital rights for women and discover the different ways to advance women’s digital rights!
👉 http://bit.ly/3YJkUpb
📸 by Gayatri Malhotra on Unsplash
#digital rights#digital activism#digital privacy#digital security#internet freedom#save the internet#internet security#net neutrality#internet shutdown#online privacy#privacy#online safety#cybersecurity awareness#technology#open data#data security#disinformation#misinformation#censorship#free expression#surveillance#women’s rights#feminist#feminism
105 notes
·
View notes
Text
Hey @staff how does hitting the back button count as accepting the Live TOS, and why isn't there a way to subsequently opt out? This is an unforgivable and possibly outright illegal state of affairs and is undeniably a massive breach of privacy, compounded by the fact that even prior to this, tumblr-live domains were accessing my phone despite my having not at that point (accidentally) accepted the TOS.
40 notes
·
View notes
Text
In light of an uptick in the discussion about banning Tiktok, and "all apps steal your data!" I went into a bit of a search on how much data, comparatively, the different apps collect.

Link to source: DailyMail (I know. But their source is Internet 2.0, a reputable cybersecurity organization.)
So uh. Yikes. Like, I know people talk about how much of your data FB collects, but compared to Tiktok??? Even compared to Instagram, which is also owned by FB! You'll want to delete quite a few apps of higher concern before deleting FB for collecting your data.
30 notes
·
View notes
Photo
I absolutely cannot.
43 notes
·
View notes
Text
Looks like Google Chrome browser just opted us all into targeted ads that collect and share our data (again). You should get a notification about this to be able to turn them off, but in case you missed it, be sure to go into "settings" > "privacy and security" > "ad privacy" and turn off all the options.
Also adding an obligatory plug for Firefox here at the end. I have to use Google for work, but otherwise, I use Firefox or Duck Duck Go browsers. Both are available as mobile apps as well.
#chrome#privacy#data mining#data security#Google#they're at it again#also the Firefox mobile browser is pretty good#fwiw
12 notes
·
View notes
Text
A huge deal in this weeks' tech news is there is now confirmation that the spyware in phones has been spying on individuals, and that this is a huge risk to both personal and national security.
Hundreds of thousands of ordinary apps, including popular ones such as 9gag, Kik, and a series of caller ID apps, are part of a global surveillance capability. [It] starts with ads … and ends with the apps’ users being swept up into a powerful mass monitoring tool advertised to national security agencies that can track the physical location, hobbies, and family members of people. … The company says it can also help push malware to targets.
And from another source:
Patternz strikes deals with smaller ad networks, willing to engage in shady practices, to gather the device fingerprints, and to use them to trigger surveillance. … When Apple changed the rules, to require apps to seek your permission before tracking you, it wasn’t long before companies started working on a backdoor method of achieving the same thing: Device fingerprinting.
It really was only a matter of time until someone did this.
Foreign spy company signs up for one of the many real time bidding ad networks, pretends to bid on many many adverts and starts to de-anonymize ad bids. [It] starts unpicking the 45 y/o male who has a gym app that locates him next to the military base, but also drinks in the … pub on the base and visits the cycle-maniac website.
And suddenly you are tracking the colonel at the base.
Quote Sources
An explainer from one of recent researchers to name this
Worse yet, kind of behaviour isn't new, Israel has been doing it on the record for years
The mention of the "Ferengi" the quote sources is what gets me. The colonel's data could go to enemy intel, or it could be used by his own government to ensure he doesn't engage in anti-national acts. A world where money talks louder than any human right.
#tech news#spyware#smart phones#data security#the reason no one has a smart phone on star trek is they already went through this--especially on ferenginar--and decided it wasnt worth it#a scifi world where citizens decided its was better to be alone with ones thoughts and miserable than be in a panopticon and complaisant#star trek#star trek for no good reason but star trek
3 notes
·
View notes
Text

115 notes
·
View notes
Text
The Nova Scotia government says it is investigating the theft of personal information stolen through a global privacy breach to a third-party file transfer system the province was using.
The province has yet to determine what information may have been taken or how many Nova Scotians could be affected by the breach to software company MoveIt's products, Cyber Security and Digital Solutions Minister Colton LeBlanc said in a Sunday news conference.
Full article
Tagging: @politicsofcanada
#cdnpoli#canadian politics#canadian news#canadian#canada#nova scotia#data breach#data security#privacy#security breach
37 notes
·
View notes
Text
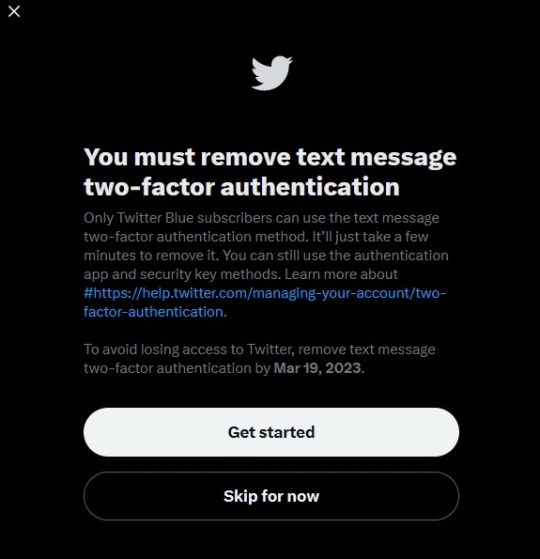
Google will start purging inactive accounts.
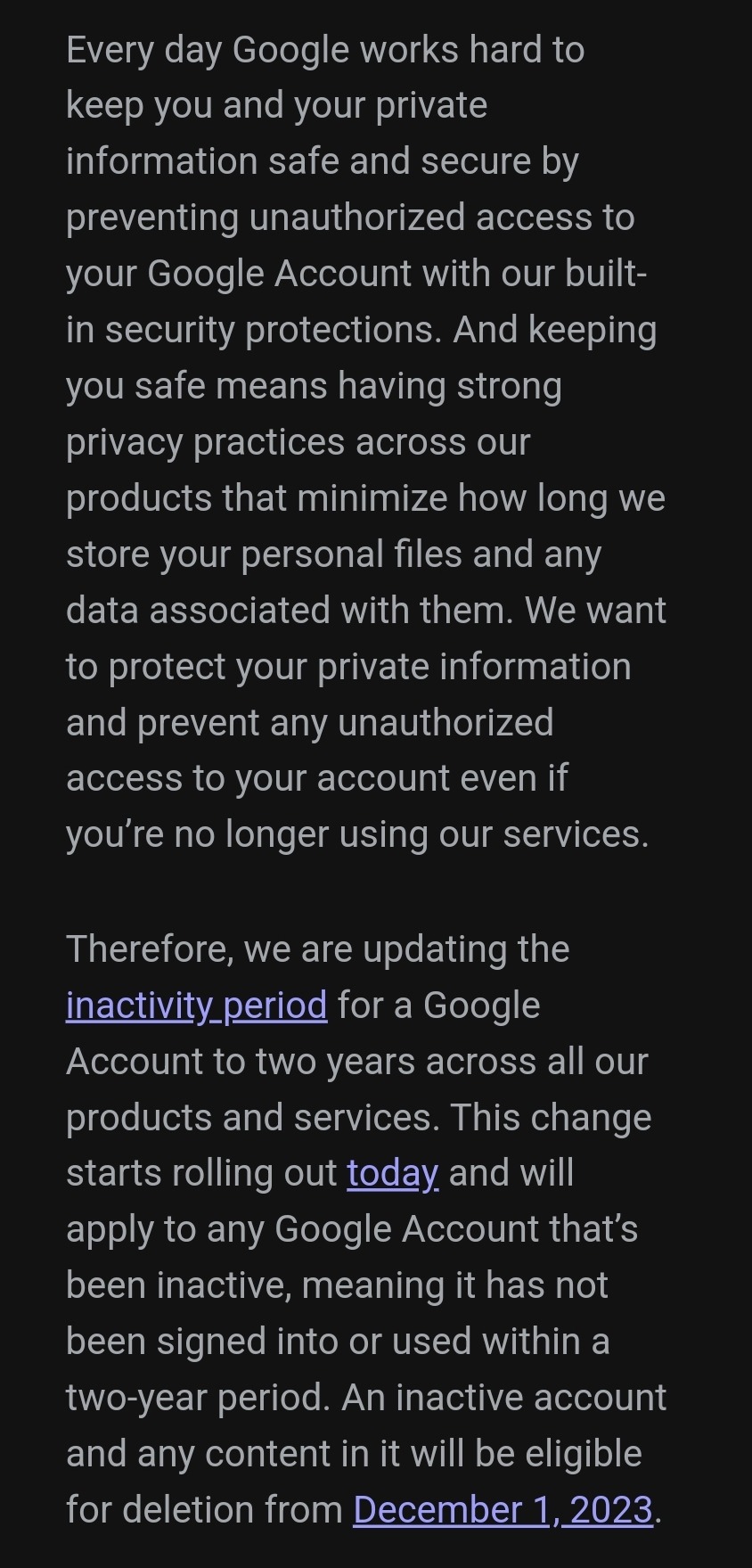

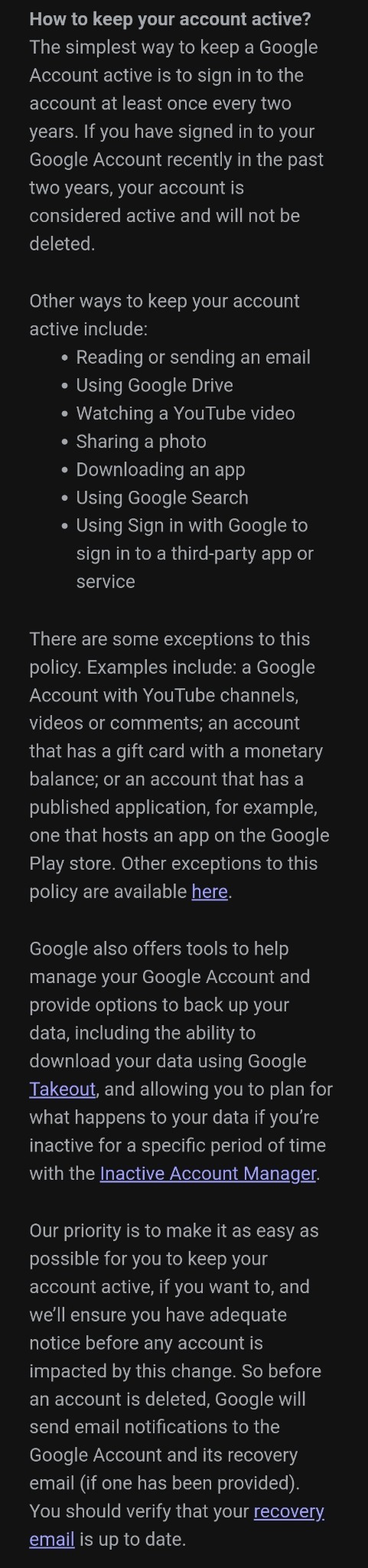
TLDR; if you haven't used your Google acocunt for 2 years, google will consider it inactive, and after a grace period of a few months and reminders of the inactivity, they will delete your account starting on December 1st, 2023. The email used for the deleted account cannot be used again.
If you do not want your inactive google account deleted, please sign into it before December 2023. Might be a good idea to back up the data on your google drive as well.
#google#twitter#data security#privacy#google drive#ao3#open internet#internet safety#internet#webcore#idk what tags people use to spread this#my posts#important
10 notes
·
View notes
Text
I've just explained to my mother how local councils do surveys of their tenants and assuaged her paranoia that somehow the council will know her answers if she's honest.
It makes me wonder how many people think they need to lie on these sorts of surveys because they think their answers will be read and they'll be identified for them in a negative way.
So let me reassure y'all here too.
The way most studies and surveys are done is, generally, as follows:
Survey is designed and sent out
Data collected from the surveys gets shoved on a database for analysis
Personal information is removed from the data and the remaining data is anonymised so you're not identified in it. For example: Participant 1 [personal data removed] : survey answers here : choose to be contacted [y/n]
The information that identifies if someone wanted to be contacted is stored separately and has no identifying information connected to their survey answers.
Survey data (minus the personal information) is analysed and used for whatever reason it was collected.
The end.
In the case of my council, they're using an independent third party to collect the data to make it doubly safe for pariticpants to answer honestly. This makes the survey a Blind Survey. Aka survey taker and survey data recipient don't know who answered what or why.
Anonymity is guaranteed, basically.
I know there's lots of worry and concern about the privacy around surveys and data collection and analysis but, any decent survey will do as the above states and that means you're safe from persecution for your answers.
If a survey offers you the choice of being contacted or participating in a focus group, then your personal information is Stored Separately And Used For Only That Thing. It doesn't get connected to your survey answers.
So please, be reassured with this. My mother is, thankfully.
#Survey#Research#Data protection#Data security#UK gov#Council survey#Idk what else to tag this as tbqh
34 notes
·
View notes
Text
Cloud and Data: A sidewalk!
In a world where 10 million data generate each hour, is there any business identity without data? Apart from the hypothetical world that pushes businesses to adopt a plan that is enriched towards an unattainable goal for objectives stepping forward through the wave of optimism, can any spectrum of business meet the goal without a shower of data?
Read the full blog.
2 notes
·
View notes
Text
Ignorance is a Choice

Data, the new oil of the modern world (Humby, 2006). At first, it might seem far fetched. However, it is an undeniable fact. In the latest discussion of the course data security and privacy, it has led me to the realization that it is neither my knowledge nor skills that is the most valuable in me. It is my data. Data is like water, very flexible and can be utilized in many forms. From being a guide to solve intricate puzzles of life, to harming another person or myself. To a personal level, the discussion lead me to think that I myself have been exposing the most valuable thing I have for free to tech giants. Despite it, the services they offer are one of the needs in my life. Conflicting ideals that resulted from the newly absorbed knowledge being applied to oneself. In the end, I concluded to limit and monitor the exposure of my own data to the public. My data is my own responsibility. On the other hand, tech giants that possess my data, the best I can do is re-read the terms and conditions meticulously and trust that they will not fall into potential misuse of data. Since, I am already aware that they are using my data for the benefit of not just me, the users, but also for the betterment of their company. In conclusion, they will be responsible for the security of my data, and I will be held accountable to whom I share my data, my privacy. I choose not to be ignorant.
2 notes
·
View notes
Text
SAFEGUARDING YOUR DATA: UNDERSTANDING THE VITAL DIFFERENCE BETWEEN DATA PRIVACY AND DATA SECURITY

Protecting your personal information has never been more critical. But do you know the difference between data privacy and data security? Come join me on an eye-opening adventure into the world of digital protection. We'll unravel the mysteries surrounding data privacy and data security, making it easy for you to grasp these concepts. Gain the essential knowledge you need to keep your data safe, protect your privacy, and ensure your information remains secure. Don't let your digital presence be an easy target – take control now! Together, we'll navigate through the complexities, demystify the jargon, and empower you to safeguard your data with confidence. Get ready to embark on this journey and fortify your digital world!

Imagine you have a valuable possession that you want to share with others, but you want to ensure it doesn't fall into the wrong hands. Data security works in a similar way. It involves sharing data in a manner that guarantees it is protected from unauthorized access or misuse.
Data security encompasses a range of measures and practices aimed at safeguarding data from potential threats such as hackers, data breaches, or accidental disclosure. It involves implementing strong passwords, encryption techniques, firewalls, and access controls to prevent unauthorized individuals from gaining access to sensitive information.
Moreover, data security also involves establishing protocols for securely transmitting and storing data. This includes using secure communication channels, employing encryption during data transmission, and storing data in encrypted or protected environments, both physically and digitally.
In essence, data security is about ensuring that data is shared and stored in a responsible and secure manner, minimizing the risk of unauthorized access or compromise. By implementing robust data security practices, organizations and individuals can protect sensitive information, maintain trust, and mitigate potential risks associated with data breaches or privacy violations.

Data privacy revolves around respecting an individual's rights and preferences when it comes to the sharing of their personal data. It involves ensuring that personal information is shared in the correct way and in line with applicable laws and regulations.
Data privacy acknowledges that individuals have the right to exercise control over their personal information. This includes obtaining explicit consent from individuals before collecting or using their personal data. By obtaining consent, individuals have the opportunity to make informed decisions about how their information is used. Additionally, data privacy ensures that personal data is used only for the specific purposes for which it was collected and communicated to the individual. This prevents data from being used in ways that individuals did not anticipate or agree to. Individuals also have the right to access, correct, or delete their personal data, and data privacy ensures that these rights are respected.
3 notes
·
View notes