#digital security
Text
NEW DISCORD SCAM / HACK
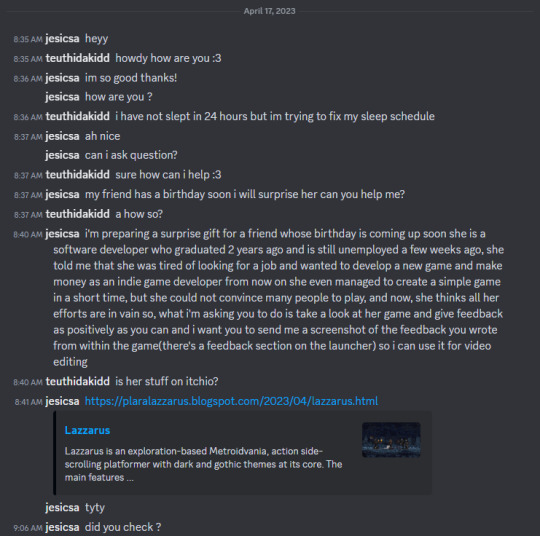
hey everyone my friend @esics had it's discord hacked and this is the general thing they will try to get you with so if anyone in your friends list sends you a link or a story like that
DO NOT CLICK THE LINK OR DOWNLOAD IT
it will lock you out your account and will hold your account ransom
3K notes
·
View notes
Photo


mikha patrick @ persona mgmt
ig: mikhapatrickk
97 notes
·
View notes
Photo

Read an article by the civic technology organization Pollicy to learn about the biggest challenges to digital rights for women and discover the different ways to advance women’s digital rights!
👉 http://bit.ly/3YJkUpb
📸 by Gayatri Malhotra on Unsplash
#digital rights#digital activism#digital privacy#digital security#internet freedom#save the internet#internet security#net neutrality#internet shutdown#online privacy#privacy#online safety#cybersecurity awareness#technology#open data#data security#disinformation#misinformation#censorship#free expression#surveillance#women’s rights#feminist#feminism
105 notes
·
View notes
Text
There's a new alternative to the awful KOSA legislation going through Congress. The new bill is S. 1291, called the Protecting Kids on Social Media Act. We need to stop this one. States absolutely will use this to target trans and queer people online. https://www.techdirt.com/2023/08/31/the-protecting-kids-on-social-media-act-is-a-terrible-alternative-to-kosa/
I have emailed my legislators using https://act.eff.org/action/stop-the-protecting-kids-on-social-media-act
And I have called them using https://www.usa.gov/elected-officials/ to find them.
27 notes
·
View notes
Text
Is the Firefox password manager any good/reasonably secure? does it work well on mobile?
Moving away from Google and currently trying out proton pass, but it's real janky on mobile. 1Password costs extra money, don't know of any other good ones (please give me suggestions).
i know no password manner is totally secure, but unfortunately i cannot manage all of my passwords analog so i need some alternative to Google password manger.
#firefox#password manager#passwords#cyberpunk#digital security#online safety#proton pass#proton vpn#1password
2 notes
·
View notes
Text
I got offered the cookies popup on a site and went to the preferences instead of agreeing--
I want you to see JUST how many "vendors" I had to deactivate.
#gives you a perspective on what agree to all actually entails#cookies#internet cookies#important#digital security#cybersecurity
3 notes
·
View notes
Text
Exploring a Powerful Security Tool: Nuclei — The Fast and Customizable Vulnerability Scanner
In the ever-evolving landscape of digital security, we’re constantly in search of tools that can enhance our defenses and streamline our security processes. Today, we bring to your attention Nuclei, a sophisticated vulnerability scanning tool that offers a range of robust features to bolster web application and network security.
0 notes
Text
Look at this... 👀Unleash Your Productivity Powerhouse! 💻✨ SentryPC: The Ultimate Solution!
Look at this... 👀 https://pin.it/7D0s1SJUa
0 notes
Text
#webglaze#Cyber Security#Information Security#Data Protection#Network Security#Cyber Defense#Cyber Threats#Digital Security#Privacy Protection
0 notes
Text
Uncover a wealth of data breach resources that empower you to fortify your digital defenses. Explore the latest strategies, tools, and insights to shield your sensitive information from cyber threats. Arm yourself with knowledge and stay one step ahead in the ever-evolving landscape. Dive into the ultimate guide. Read now.
0 notes
Text
Heads up: Threatening software detected; opening the file is prohibited.
In an era where the digital world is as intrinsic to our lives as the air we breathe, the relevance of cybersecurity can not be overemphasized. Secure mobile apps , every download, and every apparently innocuous online interaction brings with it the possible risk of inviting malicious software right into our digital sanctuaries. This write-up aims to illuminate why downloading and install or opening destructive programs on your computer system is not simply dangerous-- it belongs to unlocking to your electronic home to a host of unwelcome effects.
Malicious software application, or "malware," is a wide term that encompasses numerous kinds of damaging software program, including viruses, trojans, worms, ransomware, and spyware, to name a few. These electronic threats are developed with purposes that vary from benign mischievousness to straight-out malevolent functions, such as stealing individual details, pirating computer resources, or securing documents for ransom money.
Cyber hygiene of downloading or opening a documents that harbors malware can trigger a domino effect of occasions that jeopardize your computer's safety and security and honesty. Here's a failure of why it's perilous:
1. ** Personal Info Theft **: Many types of malware are created to stealthily infiltrate your system and pilfer delicate data such as passwords, financial details, and individual identity details. This information can then be made use of for illegal tasks, marketed on the dark internet, and even bring about identification burglary.
2. ** System Damage **: Certain malware variations can corrupt documents, alter or delete important system data, and in extreme instances, make a computer inoperable. This not only interrupts individual or company operations but can additionally result in the loss of important data.
3. ** Source Hijacking **: Some malicious programs, like cryptojacking malware, clandestinely use your computer system's sources to mine cryptocurrency, considerably decreasing your system and potentially creating lasting damage to elements as a result of overheating or overuse.
4. ** Ransomware **: Probably one of the most nefarious forms of malware, ransomware secures your files, securing you out of your very own data. The wrongdoers then demand a ransom for the decryption trick. Paying the ransom, nonetheless, does not ensure the return of your information and additional funds the cycle of cybercrime.
5. ** Personal privacy Violation **: Spyware and certain kinds of trojans can check your activities, log keystrokes, and even turn on video cameras and microphones without authorization, bring about an extensive intrusion of privacy.
Shielding on your own from these digital threats entails a combination of watchfulness and the usage of cybersecurity tools. Always validate the resource of your downloads, avoid opening email add-ons or links from unidentified senders, and use thorough anti-viruses software application that supplies real-time defense, routine updates, and system scanning capabilities.
Enlightening oneself on the characteristics of phishing attempts and rip-off sites is also important. These commonly function as the distribution devices for malware. Search for HTTPS in web addresses, and watch out for sites that display inadequate design, spelling, and grammar mistakes, or that request unnecessary personal information.
To conclude, Secure coding standards is much better than remedy" has actually never ever been even more applicable than in the context of digital safety. The short-term adventure or benefit of downloading an unknown documents fades in contrast to the possible threats. By exercising safe surfing practices and arming your system with robust protection steps, you can substantially alleviate the risk of malware and guard not just your digital life, however your reality too.
#Secure computing#Phishing scams#Spyware threats#Hacking protection#Cybersecurity tips#Vulnerable software#Email attachment safety#Internet phishing#Digital security#Malicious URLs#Online fraud prevention#Security patches#Firewall protection#Virus scan#Secure passwords#Two-factor authentication#Cybersecurity education#Malicious code#Cyber hygiene#Data encryption#Secure networks#Security vulnerabilities#Malware quarantine#Cyber defense strategies#Suspicious activity monitoring#Identity theft protection#Secure file sharing#Malware signatures#Cyber risk management#Secure online transactions
1 note
·
View note
Text
Say Goodbye to Downtime: Sigzen Technologie's Server Patching 101
In today’s fast-paced digital world, maintaining a resilient IT infrastructure is crucial for business success. Effective server patching plays a pivotal role in minimizing downtime risks and optimizing server performance. Sigzen Technologies, a trusted leader in IT solutions, offers comprehensive server patching services to address these challenges and ensure uninterrupted operations. Let’s…

View On WordPress
#Continuous Uptime#Cyber security#Digital Security#Efficient Deployment#Patch Management#Proactive Maintenance#Server Patching
0 notes
Photo

Part 2 of our blog series on RightsCon is out! Be sure to check it out to learn about 10+ activist toolkits! Stay tuned for Part 3!
👉 https://bit.ly/3v3jppg
#hrcblog#rightscon#digital rights#human rights#women’s rights#gender equality#digital activism#activism#advocacy#digital privacy#digital security#internet freedom#save the internet#internet security#net neutrality#internet shutdown#online privacy#privacy#online safety#cybersecurity awareness#technology#open data#data security#disinformation#misinformation#censorship#free expression#journalist#journalism#investigative journalism
2 notes
·
View notes
Text
#two factor authentication#2fa#digital security#authentication#loginradius#multifactor authentication#rba#risk based authentication
0 notes
Text
EU to allocate €250 million to support secure connectivity under the CEF Digital
The European Commission has signed grant agreements with 37 projects selected under the Connecting Europe Facility (CEF Digital) programme’s second call for proposals, European Union Extermal Action reports.
252 million euros will be distributed among projects deploying 5G infrastructure for local communities and along major European transport corridors. Projects to deploy submarine cables and improve the security and resilience of backbone networks within and across the EU will also receive funding.
The grants will support a direct trans-Arctic link between the EU and the Far East, provide high-capacity communications infrastructure to Greek islands in the Mediterranean Sea that are underserved by digital technologies, and strengthen connectivity to Africa. The EU will also co-finance the deployment of maritime cables to provide better connectivity between Ireland and the EU mainland, and between the EU and its marginal regions in the Atlantic Ocean.
Read more HERE

#world news#world politics#news#europe#european news#european union#eu politics#eu news#cyber security#digital services#digital security
0 notes
Text

it was a pretty cool dlc, i enjoyed it a lot
#daske art#fnaf#fnaf ruin#dlc ruin#fnaf dlc#fnaf security breach#five nights at freddy's#fnaf sb#five nights at freddy's security breach#security breach ruin#fnaf gregory#fnaf cassie#fanart#digital art#my new sweet daughter#she's so precious???and i love her so much???#she deserves the damn world#also dont at me#gregory did NOT betray his bestie#i dunno what you think that thing was#but that was NOT my son!!!#i need another dlc where we go back to the plex to bring our bestie back as gregory#idc if it repetitive at this point#let my children reunite dammit!!
25K notes
·
View notes