#Cybersecurity education
Text
Beyond Change Healthcare
The continued onslaught of cybersecurity attacks which if anything are only getting worse have impacted the healthcare system in dramatic fashion with the payment network brought down by the attack on Change Healthcare.
Healthcare under Cyber Attack
I keep hoping that we all get better at combatting these attempts to breach our data and that overall vigilance rises as we become more wary of…

View On WordPress
#cyber attacks#cyber awareness#cyber defense#cyber hygiene#cyber resilience#cyber safety#cyber threats#CyberCrime#Cybersecurity#cybersecurity awareness#cybersecurity best practices#cybersecurity challenges#cybersecurity culture#cybersecurity education#cybersecurity measures#cybersecurity news#cybersecurity protocols#cybersecurity resources#cybersecurity risks#cybersecurity solutions#cybersecurity strategy#cybersecurity tips#cybersecurity training#cybersecurity trends#data breach#data encryption#data protection#data security#Digital Health#Healthcare
0 notes
Text
Cybersecurity Education: Your Path to Becoming a Digital Guardian in an Ever-Changing Landscape
In an era dominated by digital technologies, the importance of cybersecurity has never been greater. As cyber dangers and attacks proliferate, the requirement for qualified professionals capable of protecting against them grows. In this article, we look at how cybersecurity education can help individuals become digital guardians in an ever-changing landscape of cyber threats.
The Growing Importance of Cybersecurity:
With the fast proliferation of digital infrastructure and the increasing interconnection of systems, potential vulnerabilities and dangers have grown dramatically. Organizations in all industries confront ongoing risks to their digital assets, ranging from large-scale data breaches to sophisticated ransomware assaults. As a result, there is an urgent demand for skilled cybersecurity specialists who can predict, detect, and successfully neutralize these risks.
Cybersecurity Education: Laying the Groundwork:
Cybersecurity education sets the framework for individuals to obtain the skills and knowledge required to address the wide range of difficulties provided by cyber attacks. Students learn about basic concepts like network security, cryptography, threat analysis, and incident response through comprehensive training programmes. Furthermore, they learn about emerging technologies and dynamic attack vectors, which prepares them to respond to changing threat landscapes.
Practical Experience and Hands-on Learning:
One of the distinguishing features of cybersecurity education is the emphasis on practical experience and hands-on learning. Students can use their theoretical understanding in real-world circumstances by modeling cyber attacks and defense techniques in controlled conditions. By participating in practical exercises including penetration testing, vulnerability assessments, and forensic analysis, students gain vital skills that may be applied directly to industry.
Specialization and certification:
Cybersecurity education provides a wide number of specialization options, allowing students to personalize their learning experience to their specific interests and professional aspirations. Whether they specialize in network security, cloud security, ethical hacking, or digital forensics, students can pursue certificates and qualifications that confirm their cybersecurity skills. These qualifications not only boost credibility, but they also strengthen employment prospects in a competitive labor environment.
Addressing the skill gap:
Despite the increasing demand for cybersecurity workers, there is a major skills gap in the business. Individuals who invest in cybersecurity education not only position themselves for profitable career prospects, but they also help to close the essential skills gap. Cybersecurity experts play an important role in boosting organizations' overall security posture and protecting digital assets from changing threats by engaging in continuous learning and professional development.
Conclusion:
In conclusion, cybersecurity education is the foundation for those seeking to become digital guardians in an ever-changing landscape of cyber threats. Students who get the necessary information, skills, and certifications can pursue rewarding jobs in cybersecurity, where they play an important role in defending against malicious actors and protecting the integrity of digital systems. As technology advances, the demand for qualified cybersecurity experts will grow, making cybersecurity education more important than ever.
Join the CACMS Institute for comprehensive cybersecurity education today. Receive hands-on practical instruction and guidance from our seasoned experts. Take the first step towards becoming a digital guardian in the ever-changing world of cyber threats.
For further information and to enroll, please call +91 8288040281 or visit CACMS!
Secure your future in cybersecurity with CACMS Institute.
#cacms institute#cacms#techeducation#techskills#digital landscape#ethical hacking course#ethical hacking training#ethical hacking course in Amritsar#ethical hacking certification#Cybersecurity education#cybersecurity course in amritsar
0 notes
Text
Heads up: Threatening software detected; opening the file is prohibited.
In an era where the digital world is as intrinsic to our lives as the air we breathe, the relevance of cybersecurity can not be overemphasized. Secure mobile apps , every download, and every apparently innocuous online interaction brings with it the possible risk of inviting malicious software right into our digital sanctuaries. This write-up aims to illuminate why downloading and install or opening destructive programs on your computer system is not simply dangerous-- it belongs to unlocking to your electronic home to a host of unwelcome effects.
Malicious software application, or "malware," is a wide term that encompasses numerous kinds of damaging software program, including viruses, trojans, worms, ransomware, and spyware, to name a few. These electronic threats are developed with purposes that vary from benign mischievousness to straight-out malevolent functions, such as stealing individual details, pirating computer resources, or securing documents for ransom money.
Cyber hygiene of downloading or opening a documents that harbors malware can trigger a domino effect of occasions that jeopardize your computer's safety and security and honesty. Here's a failure of why it's perilous:
1. ** Personal Info Theft **: Many types of malware are created to stealthily infiltrate your system and pilfer delicate data such as passwords, financial details, and individual identity details. This information can then be made use of for illegal tasks, marketed on the dark internet, and even bring about identification burglary.
2. ** System Damage **: Certain malware variations can corrupt documents, alter or delete important system data, and in extreme instances, make a computer inoperable. This not only interrupts individual or company operations but can additionally result in the loss of important data.
3. ** Source Hijacking **: Some malicious programs, like cryptojacking malware, clandestinely use your computer system's sources to mine cryptocurrency, considerably decreasing your system and potentially creating lasting damage to elements as a result of overheating or overuse.
4. ** Ransomware **: Probably one of the most nefarious forms of malware, ransomware secures your files, securing you out of your very own data. The wrongdoers then demand a ransom for the decryption trick. Paying the ransom, nonetheless, does not ensure the return of your information and additional funds the cycle of cybercrime.
5. ** Personal privacy Violation **: Spyware and certain kinds of trojans can check your activities, log keystrokes, and even turn on video cameras and microphones without authorization, bring about an extensive intrusion of privacy.
Shielding on your own from these digital threats entails a combination of watchfulness and the usage of cybersecurity tools. Always validate the resource of your downloads, avoid opening email add-ons or links from unidentified senders, and use thorough anti-viruses software application that supplies real-time defense, routine updates, and system scanning capabilities.
Enlightening oneself on the characteristics of phishing attempts and rip-off sites is also important. These commonly function as the distribution devices for malware. Search for HTTPS in web addresses, and watch out for sites that display inadequate design, spelling, and grammar mistakes, or that request unnecessary personal information.
To conclude, Secure coding standards is much better than remedy" has actually never ever been even more applicable than in the context of digital safety. The short-term adventure or benefit of downloading an unknown documents fades in contrast to the possible threats. By exercising safe surfing practices and arming your system with robust protection steps, you can substantially alleviate the risk of malware and guard not just your digital life, however your reality too.
#Secure computing#Phishing scams#Spyware threats#Hacking protection#Cybersecurity tips#Vulnerable software#Email attachment safety#Internet phishing#Digital security#Malicious URLs#Online fraud prevention#Security patches#Firewall protection#Virus scan#Secure passwords#Two-factor authentication#Cybersecurity education#Malicious code#Cyber hygiene#Data encryption#Secure networks#Security vulnerabilities#Malware quarantine#Cyber defense strategies#Suspicious activity monitoring#Identity theft protection#Secure file sharing#Malware signatures#Cyber risk management#Secure online transactions
1 note
·
View note
Text
Staying Relevant: Balancing Learning and Life as an Ethical Hacker
Have you experienced burnout while trying to develop your skills and you just don't have the time to do everything? Finding balance is the key to improving your skills in a healthy way. In this article, I explore healthy habits to grow without burning out
You’ve heard it before – cybersecurity is a field that evolves at a blindingly fast pace. The tools, techniques, and technologies threatening networks transform rapidly. As an ethical hacker, your skills can become obsolete within months if you aren’t continuously upgrading your knowledge. Point #4 on our hacker roadmap deals with knowing the latest and greatest when it comes to the state of…

View On WordPress
#burnout#certifications#conference#continuous learning#Cyber Security#cybersecurity education#cybersecurity skills#Ethical Hacking#hacker skills#infosec community#leadership#learning plan#maintaining balance#microlearning#Penetration Testing#pentesting methodologies#personal development#podcast#red team operations#security news#security policies#security tools#time management#trends#vulnerability assessments#work-life balance
1 note
·
View note
Text
How to Spot Instagram Social Engineering Scams

View On WordPress
#Bot detection#Bots#Bots to inflate numbers#Browser hijackers#Clicks#Command and control server#Concert scams#Contest scams#Contests#Copyrights#Cyber awareness#Cyber safety tips#Cyber threats#Cybercrime#Cybersecurity#Cybersecurity best practices#Cybersecurity education#demographics#Digital threats#Direct email#Domain name verification#Domain names#Events#Fake accounts#Fake giveaways#Fake profiles#Fake publishing agents#followers#Fraudulent schemes#Impersonation prevention
1 note
·
View note
Text
Cybersecurity: Follow 7 Best Practices to Protect Personal Data Now
Introduction:Recognizing the Need for Cybersecurity1. PasswordsUse Secure and Original PasswordsLength and ComplexityAvoid Using Personal InformationCreate a Unique Password for Each AccountPassword Manager2FA, or two-factor authentication2. Maintain Up-to-Date Software and EquipmentUpdates to the operating systemUpdates for web browsersAntivirus and security software updates3. Warning: Phishing…

View On WordPress
#best practices#cybersecurity#cybersecurity education#data backups#data privacy#online security#personal data protection#phishing attacks#secure Wi-Fi networks#software updates#strong passwords#two-factor authentication
0 notes
Text
Online Security in the Age of AI: Protecting Your Data and Privacy
In the age of artificial intelligence (AI), cybersecurity concerns have grown exponentially. As AI continues to advance, so do the capabilities of cybercriminals who use sophisticated tools and techniques to exploit vulnerabilities in the digital world. In this article, we’ll explore the challenges and risks associated with online security in the AI era, and provide practical tips for protecting…

View On WordPress
#AI-powered attacks#Artificial Intelligence#cyber threats#cybersecurity education#data privacy#deepfakes#device security#network security#online security#password management#two-factor authentication
0 notes
Text
DOD Officials Push For Contractors To Hire Through - And Start - Cybersecurity Apprenticeship Programs
DOD Officials Push For Contractors To Hire Through – And Start – Cybersecurity Apprenticeship Programs
PLEASE CLICK IMAGE TO ENLARGE
“DEFENSE SCOOP” Written by Billy Mitchell
” As the Department of Defense looks for new ways to bring more cybersecurity talent into its ranks, a pair of top DOD officials have called on defense contractors to consider hiring professionals who don’t have formal college educations, namely through apprenticeships.
In a memo issued Tuesday, DOD CIO John Sherman and…

View On WordPress
#Cybersecurity Apprenticeship Programs#cybersecurity education#government contracting#Government Contractors
0 notes
Text
CISA-Funded Project Enables Students With Disabilities to Learn Cybersecurity
CISA-Funded Project Enables Students With Disabilities to Learn Cybersecurity
Home › Training & Certification
CISA-Funded Project Enables Students With Disabilities to Learn Cybersecurity
By Ionut Arghire on June 29, 2022
Tweet
Cybersecurity workforce development organization CYBER.ORG on Monday announced the launch of Project Access, a national effort to provide cybersecurity education to blind and visually impaired students.
Courtesy of the Cybersecurity and…
View On WordPress
0 notes
Text
Ao3 DDoS attack- an explanation
For anyone missing their fanfics (like me), this article gives an general outline what going's on with Ao3.
For anyone hoping that they might be able to get to their fanfics soon, I suggest not getting your hopes up. Ao3 may be up in a couple hours (hopefully) , but there's a possibility that could last for several days depending on how how severe the attack is and how many resources the attackers have, Ao3 is handling this attack, and what response plans they have in place.
Some things to know if you're not familiar with DDoS attacks... it's time to use my education.
Disclaimer: I'm not affiliated with Ao3 other than being a user. I don't know what security measures they have in place, or what their security is. This is my personal- though knowledgeable- thoughts what may be going on behind the scenes.
Also, if the idea of the DDoS attack is scaring you in anyway- take a deep breath. It's going to be OK, even if my post may come across as dark (if so, I am sorry about that). It only meant to inform and educate Tumblr users on what is going on, and what might Ao3 may be doing. Do not panic just because of this post.
So, let's get started.
a. DDoS stands for distributed Denial of Services attacks. So that means the attackers is using multiple third party devices (such as other servers, botnets*) to make so many requests (think millions per minute) to the Ao3 servers that the servers use up all their resources, preventing us legitimate users from using them.
b. A slight side note- I've heard some people say that it's because of one person that Ao3 is down. It may just be one person, but setting up a DDoS attack is easier with a team. It is likely it is a group of attackers behind this- most attacks have multiple people involved in one form or another. This isn't the most relevant point I have, but just something people should know- there may be more than one attack.
c. To stop this attack, Ao3 is going to have to block all malicious traffic from reaching the servers. However, since this is a distributed attack, they are going to have to block multiple IP addresses. This is going to take some time.
d. We also have to consider if Ao3 has a response plan in place. Response plans are, as the name suggests, what the organization does in the case of an event. For ao3, that means who are they going to contact to fix this issue. But if there isn't a response plan in place already, it going to take longer for them to stop the attack because they're fixing this on the go- a difficult thing to do.
e. Once the attack has been stopped, it won't be over for Ao3, there are two more things they need to do- complete forensics to determine any possible damage to their servers and complete an After Action Review.
e1. While it is most likely that everything will be back to normal system wise after the attack has stopped, Ao3 would be smart to conduct forensics on their system to see if there are any anomalies (malware or indications of a breach). Attackers sometimes use DDoS attacks to cover their tracks when they hack into a system. Not likely here, considering the target won't have super sensitive information that an attacker wouldn't bother with trying to get. But the possibility is always there- however small.
e2. if they want to mitigate the risk of such attacks happening again- they need to complete After Action review (AAR). In AAR, Ao3 is going to have to look at what happened, and determine what they can do to ensure this doesn't happen so easily again. Hopefully, this means writing up or editing and improving their response plan, improving their security measures, etc.
f. Most importantly, your information is unlikely to be compromised. The most damage you will receive is not being able to access Ao3's servers. Ao3 has said that you don't need to change your passwords if you have an account. That being said, if you have a weak password, definitely change it anyway. (like I'm talking is you're using weak passwords. See the following link for what weak and strong passwords are: https://security.harvard.edu/use-strong-passwords )
That's what I have to say for now. Again, this post is not associated with the team at Ao3, I am independent and have no insider knowledge, just knowledge from being a security student. Ao3 will likely say more in the future, so keep an eye for it, and hopefully we'll be able to back to our fics.
If you have any questions about this attack or general cybersecurity, my asks are open, there are comments, and I will respond to them as quickly as I can. If you are in security, and I got something here, please tell me because I do not want to spread misinformation or cause panic.
Heard from your mother (she don't recognize you), I'll be waiting for you.
*compromised computers or other devices with internet connection with malware
#ao3#cybersecurity#cyberattack#sorry this is a long post#there may be some spelling or something is written badly#i wrote this in one sitting and i barely proofread so im sorry#I will clarify if anyone is confused by anything i said#the goal is to educate anyone willing#not alarm anyone#not what i usually post but i got excited when I saw the DDoS banner on Ao3 and wrote this in an dopamine craze
15 notes
·
View notes
Text
youtube
2 notes
·
View notes
Text
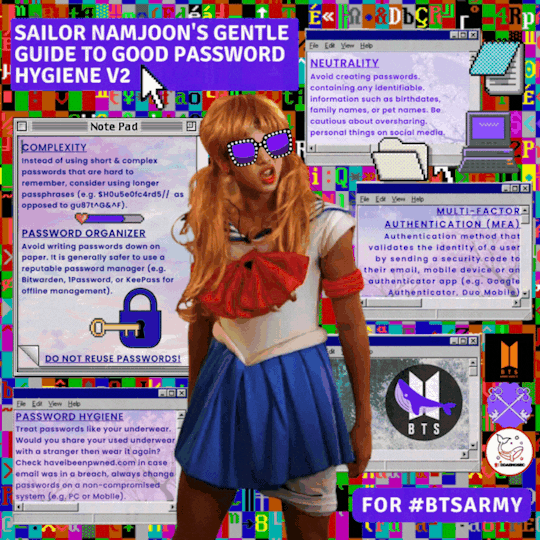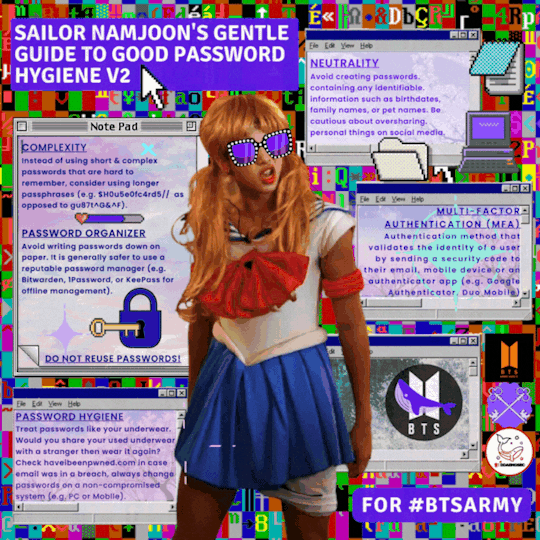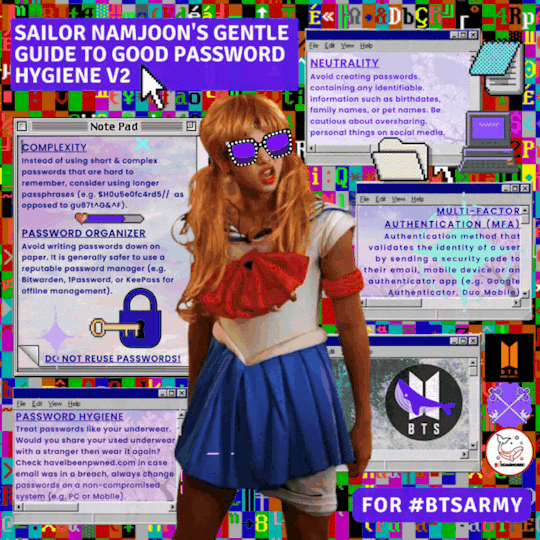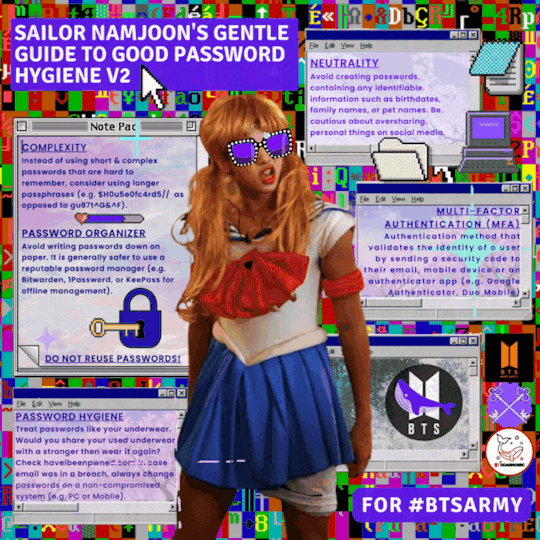

Contributors
ddaengsec
btsarmysafety
ArmyCompSci
#bts#btsarmy#bts army#bts rm#passwords#infosec#information security#cybersecurity#hacking#cybersecurity awareness#cybersecuritytips#security awareness#security education#bts fanart#cybersecurity tips#lastpass#1password#privacy#internet#digital privacy
9 notes
·
View notes
Text
Future of AI: Predictions and Trends in Artificial Intelligence
Introduction: Exploring the Exciting Future of AI
Artificial Intelligence (AI) has become an integral part of our lives, revolutionizing the way we work, communicate, and interact with technology. As we delve into the future of AI, it is essential to understand the predictions and trends that will shape this rapidly evolving field. From machine learning to predictive analytics, natural language processing to robotics, and deep learning to ethical considerations, the possibilities seem limitless. In this article, we will explore the exciting future of AI and its potential impact on various industries and aspects of our lives.
The Rise of Machine Learning: How AI is Evolving
Machine learning, a subset of AI, has been a driving force behind the advancements we have witnessed in recent years. It involves training algorithms to learn from data and make predictions or decisions without explicit programming. As we move forward, machine learning is expected to become even more sophisticated, enabling AI systems to adapt and improve their performance over time.
One of the key trends in machine learning is the rise of deep learning, a technique inspired by the structure and function of the human brain. Deep learning algorithms, known as neural networks, are capable of processing vast amounts of data and extracting meaningful patterns. This has led to significant breakthroughs in areas such as image recognition, natural language processing, and autonomous vehicles.
Predictive Analytics: Unleashing the Power of AI in Decision-Making
Predictive analytics, powered by AI, is transforming the way organizations make decisions. By analyzing historical data and identifying patterns, AI systems can predict future outcomes and provide valuable insights. This enables businesses to optimize their operations, improve customer experiences, and make data-driven decisions.
In the future, predictive analytics is expected to become even more accurate and efficient, thanks to advancements in machine learning algorithms and the availability of vast amounts of data. For example, AI-powered predictive analytics can help healthcare providers identify patients at risk of developing certain diseases, allowing for early intervention and personalized treatment plans.
Natural Language Processing: Revolutionizing Human-Computer Interaction
Natural Language Processing (NLP) is a branch of AI that focuses on enabling computers to understand and interact with human language. From voice assistants like Siri and Alexa to chatbots and language translation tools, NLP has already made significant strides in improving human-computer interaction.
In the future, NLP is expected to become even more advanced, enabling computers to understand context, emotions, and nuances in human language. This will open up new possibilities for virtual assistants, customer service bots, and language translation tools, making communication with technology more seamless and natural.
Robotics and Automation: AI's Impact on Industries and Jobs
AI-powered robotics and automation have the potential to revolutionize industries and reshape the job market. From manufacturing and logistics to healthcare and agriculture, robots and automated systems are already making significant contributions.
In the future, we can expect to see more advanced robots capable of performing complex tasks with precision and efficiency. This will lead to increased productivity, cost savings, and improved safety in various industries. However, it also raises concerns about job displacement and the need for reskilling and upskilling the workforce to adapt to the changing job landscape.
Deep Learning: Unlocking the Potential of Neural Networks
Deep learning, a subset of machine learning, has gained immense popularity in recent years due to its ability to process and analyze complex data. Neural networks, the foundation of deep learning, are composed of interconnected layers of artificial neurons that mimic the structure of the human brain.
The future of deep learning holds great promise, with potential applications in fields such as healthcare, finance, and cybersecurity. For example, deep learning algorithms can analyze medical images to detect diseases at an early stage, predict stock market trends, and identify anomalies in network traffic to prevent cyberattacks.
Ethical Considerations: Addressing the Challenges of AI Development
As AI continues to advance, it is crucial to address the ethical considerations associated with its development and deployment. Issues such as bias in algorithms, privacy concerns, and the impact on jobs and society need to be carefully considered.
To ensure the responsible development and use of AI, organizations and policymakers must establish ethical guidelines and regulations. Transparency, accountability, and inclusivity should be at the forefront of AI development, ensuring that the benefits of AI are accessible to all while minimizing potential risks.
AI in Healthcare: Transforming the Medical Landscape
AI has the potential to revolutionize healthcare by improving diagnosis, treatment, and patient care. From analyzing medical images to predicting disease outcomes, AI-powered systems can assist healthcare professionals in making more accurate and timely decisions.
In the future, AI is expected to play an even more significant role in healthcare. For example, AI algorithms can analyze genomic data to personalize treatment plans, predict disease outbreaks, and assist in drug discovery. This will lead to improved patient outcomes, reduced healthcare costs, and enhanced overall healthcare delivery.
Smart Cities: How AI is Shaping Urban Living
AI is transforming cities into smart, connected ecosystems, enhancing efficiency, sustainability, and quality of life. From traffic management and energy optimization to waste management and public safety, AI-powered systems can analyze vast amounts of data and make real-time decisions to improve urban living.
In the future, smart cities will become even more intelligent, leveraging AI to optimize resource allocation, reduce congestion, and enhance citizen services. For example, AI-powered sensors can monitor air quality and automatically adjust traffic flow to reduce pollution levels. This will lead to more sustainable and livable cities for future generations.
AI in Education: Enhancing Learning and Personalization
AI has the potential to revolutionize education by personalizing learning experiences, improving student outcomes, and enabling lifelong learning. Adaptive learning platforms powered by AI can analyze student data and provide personalized recommendations and feedback.
In the future, AI will play a more significant role in education, enabling personalized learning paths, intelligent tutoring systems, and automated grading. This will empower students to learn at their own pace, bridge learning gaps, and acquire the skills needed for the future job market.
Cybersecurity: Battling the Dark Side of AI
While AI offers numerous benefits, it also poses significant challenges in the realm of cybersecurity. As AI becomes more sophisticated, cybercriminals can exploit its capabilities to launch more advanced and targeted attacks.
To combat the dark side of AI, cybersecurity professionals must leverage AI-powered tools and techniques to detect and prevent cyber threats. AI algorithms can analyze network traffic, identify patterns of malicious behavior, and respond in real-time to mitigate risks. Additionally, organizations must invest in cybersecurity training and education to stay ahead of evolving threats.
Conclusion: Embracing the Future of AI and Its Limitless Possibilities
The future of AI is filled with exciting possibilities that have the potential to transform industries, enhance our daily lives, and address some of the world's most pressing challenges. From machine learning and predictive analytics to natural language processing and robotics, AI is evolving at a rapid pace.
However, as we embrace the future of AI, it is crucial to address ethical considerations, ensure transparency and accountability, and prioritize inclusivity. By doing so, we can harness the power of AI to create a better future for all.
As AI continues to advance, it is essential for individuals, organizations, and policymakers to stay informed about the latest trends and developments. By understanding the potential of AI and its impact on various sectors, we can make informed decisions and leverage its capabilities to drive innovation and positive change.
The future of AI is bright, and by embracing it with an open mind and a focus on responsible development, we can unlock its limitless possibilities and shape a better future for generations to come.
#ai#artificial intelligence#ai power#future of ai#ai cybersecurity#ai in education#future of artificial intelligence#dark side of ai#ai predictions#machine learning#ai education#ai medicine
3 notes
·
View notes
Text
Advanced Persistent Threats: Understanding the Characteristics, Tactics, and Strategies for Prevention and Mitigation in Today's Cyber Landscape
A detailed read on Cyber security in today's digital landscape. Happy Sunday everyone!
Advanced Persistent Threats (APTs) are a type of cyber attack that is specifically targeted at organizations or individuals to steal sensitive information or disrupt operations. These attacks are carried out by highly skilled and organized hackers who use sophisticated techniques to gain access to networks and systems. In this paper, we will discuss APTs in detail, including their…

View On WordPress
#Advanced Persistent Threats (APTs)#Cyber attack mitigation#Cyber attack prevention#Cyber risk management#cyber threats#Cybersecurity#Data protection#Employee education#Endpoint protection#Incident response#Least privilege#Network segmentation#Security assessments#Security audits#Threat intelligence
2 notes
·
View notes
Text
A cybersecurity service without an engineer and a programmer is based on a fraud.
Due to a fact an education is a basis of all qualifications, an engineer and a programmer can represent the cybersecurity service.
Otherwise there is an organized crime to do a fraud, or to defraud an amount of monies from the previous fraud.
Since an act against a law is evident, an investigation is required.
An author Piotr Sienkiewicz
+48 721 951 799
Have a read about an economy.
#A cybersecurity service#A private service#A private sector#An education#Qualifications#A profession#An engineer#A programmer#An economy#A complaint#A consumer#Consumers#A law#A Council
1 note
·
View note
Text

1-Most of the attack (credit scams, account cracking, password stealing, Phishing Etc…) are causing the most damage but strangely they are the easiest to protect yourself against.
Then why People s still fall for them if they are so easy to get rid of them
2-Because They are less technical And more social. Also, some people need some education about how they can protect themselves online. Then how can you protect yourself on the internet?
3-To protect yourself or your privacy online need to what type of hack you may face visiting some website. How do those work? you don’t need to master those.
For example
-You have to know that downloading attachments from an unknown sender is not the best thing to do.
-Identifier suspicious links and avoid clicking on them no matter what And much more.
Check this article here on my blog. for five minute reading, you will be able to protect your social account and password, protect your credit card, and your computer
https://digitalopenings.com/how-to-protect-yourself-on-the-internet/
these hacking are also called Masse attacks because they are not for a specific person but for anyone who can fall for it.
thank you for reading pls give this post a like or share for support
5 notes
·
View notes