#Data encryption
Photo
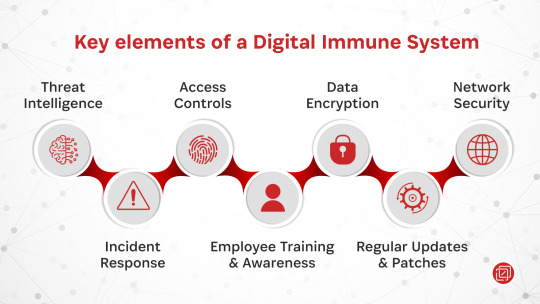
Don't let cyber threats take you down - fortify your digital assets with a Digital Immune System! 🔒🛡️
Discover the key elements, including threat intelligence, data encryption, and network security, that keep your data safe and secure.
#digital immune system#key elements#cyber threats#digital#intelligence#data encryption#network security#data#security
3 notes
·
View notes
Text
y'all. stop saying to encrypt my data and my messaging systems and shit and actually TELL me HOW to do that.
#like seriously#telling people to do shit but not explaining how#is absolutely bullshit#roe v wade#data encryption
4 notes
·
View notes
Text
Data Encryption
Unlocking the Secrets of Data Encryption with Century Solutions Group!

At Century Solutions Group, we're not just keeping your data safe; we're turning it into digital Fort Knox! With data encryption, we're like the superheroes of cyberspace – protecting your valuable information from prying eyes and cyber villains alike.
So, why is data encryption so important? Well, imagine your data as a top-secret recipe . You wouldn't want just anyone peeking at your secret ingredients, right? That's where encryption comes in! It scrambles your data into an unreadable mess for anyone without the secret key to decode. Talk about keeping your digital cupcakes safe from the cookie monsters!
Don't leave your data vulnerable to cyber-criminals – trust Century Solutions Group to keep it under lock and key with state-of-the-art encryption solutions. Your secrets are safe with us! #DataEncryption #DigitalFortKnox #CenturySolutionsGroup – https://centurygroup.net/managed-it-solutions/data-backup/
1 note
·
View note
Text
Beyond Change Healthcare
The continued onslaught of cybersecurity attacks which if anything are only getting worse have impacted the healthcare system in dramatic fashion with the payment network brought down by the attack on Change Healthcare.
Healthcare under Cyber Attack
I keep hoping that we all get better at combatting these attempts to breach our data and that overall vigilance rises as we become more wary of…

View On WordPress
#cyber attacks#cyber awareness#cyber defense#cyber hygiene#cyber resilience#cyber safety#cyber threats#CyberCrime#Cybersecurity#cybersecurity awareness#cybersecurity best practices#cybersecurity challenges#cybersecurity culture#cybersecurity education#cybersecurity measures#cybersecurity news#cybersecurity protocols#cybersecurity resources#cybersecurity risks#cybersecurity solutions#cybersecurity strategy#cybersecurity tips#cybersecurity training#cybersecurity trends#data breach#data encryption#data protection#data security#Digital Health#Healthcare
0 notes
Text
Data Safety in the Cloud Era: Effective Backup Strategies for Multi and Hybrid Environments

In the evolving digital landscape, data safety has become a paramount concern, especially with the widespread adoption of cloud computing. Organizations are increasingly relying on multi-cloud and hybrid environments to store, process, and manage their data. This shift necessitates a robust strategy for backing up data to ensure its safety and availability in the face of cyber threats, technical failures, or natural disasters. This article delves into effective backup strategies for multi and hybrid environments, emphasizing the importance of securing data across diverse platforms and networks.
Understanding Multi and Hybrid Environments
Before diving into backup strategies, it's essential to understand the nuances of multi-cloud and hybrid environments. A multi-cloud environment uses services from multiple cloud providers, such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP), to leverage the unique benefits of each. A hybrid environment, on the other hand, combines cloud computing with on-premises infrastructure, allowing for more flexible data deployment and operational strategies.
The Significance of Data Safety
Data is the lifeblood of modern organizations, driving decision-making, operational efficiency, and innovation. The loss or compromise of data can lead to significant financial losses, reputational damage, and regulatory penalties. As such, data safety in multi and hybrid environments is not just a technical requirement but a strategic imperative.
Key Strategies for Effective Data Backup
1. Comprehensive Risk Assessment
The first step in creating an effective backup strategy is to conduct a comprehensive risk assessment. This involves identifying critical data assets, potential threats, and the impact of data loss. Understanding these factors helps in designing a backup solution that addresses the specific needs and vulnerabilities of an organization.
2. Implementing a 3-2-1 Backup Rule
A widely recommended practice is the 3-2-1 backup rule, which suggests having at least three copies of your data, stored on two different media, with one copy located offsite. In the context of multi and hybrid environments, this could mean having backups on a physical server, a cloud service, and another cloud or offsite facility.
3. Leveraging Cloud-native Backup Solutions
Many cloud providers offer native backup solutions that are designed to seamlessly integrate with their services. These solutions often provide automated backups, easy recovery options, and robust security features. Utilizing cloud-native backups can simplify the backup process and ensure data is protected across all cloud services used by an organization.
4. Ensuring Data Sovereignty and Compliance
When implementing backup strategies in multi-cloud and hybrid environments, it's crucial to consider data sovereignty and compliance with regulatory requirements. This includes understanding where data is stored, who can access it, and how it is protected. Compliance frameworks such as GDPR, HIPAA, and CCPA may dictate specific requirements for data backup and recovery processes.
5. Regular Testing and Monitoring
An effective backup strategy is not a set-it-and-forget-it solution. Regular testing and monitoring are essential to ensure backups are complete, up to date, and recoverable. This includes conducting regular drills to restore data from backups and monitoring backup processes for failures or irregularities.
Conclusion
As organizations navigate the complexities of multi-cloud and hybrid environments, the importance of data safety cannot be overstated. Implementing effective backup strategies is crucial for protecting against data loss and ensuring business continuity. By assessing risks, adhering to best practices like the 3-2-1 backup rule, leveraging cloud-native solutions, maintaining compliance, and conducting regular tests, organizations can safeguard their most valuable asset—data—in the cloud era.
0 notes
Text
Features of the Most Reliable VPN Services
In today’s interconnected world, where privacy concerns and data breaches are rampant, Virtual Private Networks (VPNs) have emerged as indispensable tools for safeguarding online activities. However, not all VPN services are created equal. While some may offer flashy features or enticing deals, the true mark of reliability lies in a set of core features that distinguish the best from the rest. In…

View On WordPress
#A#Cross-Platform Compatibility#Customer Support#Customer support availability#Data encryption#Data encryption standards#Data Protection#Data protection measures#Encryption protocol security#Geo-restriction#Geo-restriction bypass#Geo-restriction circumvention#Internet safety#Internet safety assurance#Kill switch#Kill switch feature#Leak protection#Leak protection mechanism#Network reliability#Network reliability assessment#No-logs guarantee#No-Logs Policy#Online Privacy#Online privacy protection#Privacy policy assurance#Privacy protection#Secure Connection#Secure connection establishment#Security encryption#Server network
0 notes
Text
The Quantum Enigma: How Unbreakable Code and Lightning Speed Will Change Everything
The Quantum Enigma: How Unbreakable Code and Lightning Speed Will Change Everything #quantumcomputing #dataencryption #dataprocessing #technology #science #quantumsupremacy #quantumcryptography #QKD #cybersecurity #futureofcomputing
Introduction
Imagine a world where the locks on your most sensitive data – bank records, medical histories, even government secrets – could crumble in minutes. That’s the potential danger of quantum computing, but it’s also where the promise of an unprecedented technological revolution lies. The world of computing is on the brink of this seismic shift, fueled by the emergence of quantum…
View On WordPress
#cybersecurity#data encryption#data processing#future of computing#QKD#Quantum Computing#quantum cryptography#quantum supremacy#science#technology
1 note
·
View note
Text
Heads up: Threatening software detected; opening the file is prohibited.
In an era where the digital world is as intrinsic to our lives as the air we breathe, the relevance of cybersecurity can not be overemphasized. Secure mobile apps , every download, and every apparently innocuous online interaction brings with it the possible risk of inviting malicious software right into our digital sanctuaries. This write-up aims to illuminate why downloading and install or opening destructive programs on your computer system is not simply dangerous-- it belongs to unlocking to your electronic home to a host of unwelcome effects.
Malicious software application, or "malware," is a wide term that encompasses numerous kinds of damaging software program, including viruses, trojans, worms, ransomware, and spyware, to name a few. These electronic threats are developed with purposes that vary from benign mischievousness to straight-out malevolent functions, such as stealing individual details, pirating computer resources, or securing documents for ransom money.
Cyber hygiene of downloading or opening a documents that harbors malware can trigger a domino effect of occasions that jeopardize your computer's safety and security and honesty. Here's a failure of why it's perilous:
1. ** Personal Info Theft **: Many types of malware are created to stealthily infiltrate your system and pilfer delicate data such as passwords, financial details, and individual identity details. This information can then be made use of for illegal tasks, marketed on the dark internet, and even bring about identification burglary.
2. ** System Damage **: Certain malware variations can corrupt documents, alter or delete important system data, and in extreme instances, make a computer inoperable. This not only interrupts individual or company operations but can additionally result in the loss of important data.
3. ** Source Hijacking **: Some malicious programs, like cryptojacking malware, clandestinely use your computer system's sources to mine cryptocurrency, considerably decreasing your system and potentially creating lasting damage to elements as a result of overheating or overuse.
4. ** Ransomware **: Probably one of the most nefarious forms of malware, ransomware secures your files, securing you out of your very own data. The wrongdoers then demand a ransom for the decryption trick. Paying the ransom, nonetheless, does not ensure the return of your information and additional funds the cycle of cybercrime.
5. ** Personal privacy Violation **: Spyware and certain kinds of trojans can check your activities, log keystrokes, and even turn on video cameras and microphones without authorization, bring about an extensive intrusion of privacy.
Shielding on your own from these digital threats entails a combination of watchfulness and the usage of cybersecurity tools. Always validate the resource of your downloads, avoid opening email add-ons or links from unidentified senders, and use thorough anti-viruses software application that supplies real-time defense, routine updates, and system scanning capabilities.
Enlightening oneself on the characteristics of phishing attempts and rip-off sites is also important. These commonly function as the distribution devices for malware. Search for HTTPS in web addresses, and watch out for sites that display inadequate design, spelling, and grammar mistakes, or that request unnecessary personal information.
To conclude, Secure coding standards is much better than remedy" has actually never ever been even more applicable than in the context of digital safety. The short-term adventure or benefit of downloading an unknown documents fades in contrast to the possible threats. By exercising safe surfing practices and arming your system with robust protection steps, you can substantially alleviate the risk of malware and guard not just your digital life, however your reality too.
#Secure computing#Phishing scams#Spyware threats#Hacking protection#Cybersecurity tips#Vulnerable software#Email attachment safety#Internet phishing#Digital security#Malicious URLs#Online fraud prevention#Security patches#Firewall protection#Virus scan#Secure passwords#Two-factor authentication#Cybersecurity education#Malicious code#Cyber hygiene#Data encryption#Secure networks#Security vulnerabilities#Malware quarantine#Cyber defense strategies#Suspicious activity monitoring#Identity theft protection#Secure file sharing#Malware signatures#Cyber risk management#Secure online transactions
1 note
·
View note
Text
Reliable website hosting is the bedrock of secure financial transactions online. From data encryption to uptime guarantees, it's the key to building trust and ensuring safety in financial operations. #WebsiteHosting #SecureTransactions #Cybersecurity
#Website Hosting#Financial Transactions#Online Security#Data Encryption#Secure Transactions#Cybersecurity#Trustworthiness
1 note
·
View note
Text
5 Easy Ways To Improve Salesforce Data Backup Recovery Strategy
In today's data-driven world, businesses rely heavily on Customer Relationship Management (CRM) systems like Salesforce to manage their customer information, track sales, and drive growth. However, even the most robust platforms are not immune to data loss or system failures. That's why having a solid Salesforce data backup and recovery strategy is crucial for ensuring business continuity. In this blog post, we'll explore five easy ways to enhance your Salesforce data backup and recovery strategy.
Regularly Scheduled Backups:
The foundation of any effective data recovery strategy is regular data backups. Salesforce provides a built-in data export tool that allows you to export data in a structured format, such as CSV or Excel. Set up a routine schedule for these exports to ensure that your data is backed up consistently. Depending on your organization's needs, you may choose to perform daily, weekly, or monthly backups.
Automate Your Backups:
Manually exporting data can be time-consuming and prone to errors. To streamline the process, consider automating your Salesforce data backups using third-party backup solutions. These tools can schedule and execute backups automatically, ensuring that your data is consistently and reliably backed up without manual intervention.
Store Backups Securely:
Backing up your Salesforce data is only half the battle. Equally important is where you store those backups. Utilize secure and redundant storage solutions, such as cloud storage platforms like Amazon S3 or Google Cloud Storage. Implement encryption and access controls to safeguard your backups from unauthorized access.
Test Your Recovery Process:
Having backups is essential, but they're only as good as your ability to recover data from them. Regularly test your data recovery process to ensure that it works as expected. Document the steps, and make sure that your team is familiar with the recovery procedures. Conducting mock recovery drills can help identify and address any potential issues before they become critical.
Monitor and Alerting:
Proactive monitoring is key to identifying data backup and recovery issues early. Implement monitoring and alerting systems that notify you of any backup failures or anomalies. This way, you can take immediate action to rectify issues and minimize data loss in case of a failure.
Consider Salesforce Data Archiving:
As your Salesforce database grows, it can become challenging to manage large volumes of data efficiently. Salesforce offers data archiving solutions that allow you to move older or less frequently accessed data to a separate storage location. This can help reduce storage costs and improve system performance, making your data recovery strategy more manageable.
In conclusion, enhancing your Salesforce data backup and recovery strategy doesn't have to be complicated. By implementing these five easy steps, you can significantly improve your organization's ability to recover critical data in the event of data loss or system failures. Remember that data is the lifeblood of your business, and a robust backup and recovery strategy is your insurance policy against unforeseen disasters.
#Salesforce best practices#Data loss prevention#Backup automation#Data retention policies#Data encryption#Salesforce customization#Data recovery testing#Backup monitoring#Data recovery procedures#Data backup optimization#Salesforce data protection#Backup reliability#Data restoration#Backup storage solutions#Data backup documentation#Salesforce metadata backup#Data backup strategy evaluation#Data backup policies#Salesforce data backup best practices
0 notes
Text
The OSI model provides a standardized framework for the interaction and communication between various networking protocols and technologies within a network. It breaks down the communication process into seven distinct layers, each with specific responsibilities, and ensures that data communication between devices is seamless and uniform. One significant layer in the OSI model is the Presentation Layer.
#osi model#layer 6#presentation layer#cybersecurity#security#networking#data compression#data encryption#infosectrain#learntorise
0 notes
Text
Secure Your Data with Advanced Data Encryption Techniques | Insignia Consultancy
Discover the power of data encryption and how it shields your personal and business information from unauthorized access. Stay one step ahead of cyber threats with our advanced encryption solutions.
#Data Encryption#snowflake developers#business consulting firm#company for digital marketing#servicenow#saphana#ar vr development company
0 notes
Text
Firewall Friday: Network Security - Protecting Your Network from Threats
Welcome to Firewall Friday, where we dive into the exciting world of network security with a touch of humor and relatable analogies. In this edition, we’ll explore the importance of network security and how firewalls act as the guardians of your network, protecting it from potential threats. Get ready to embark on a hilarious and informative journey as we use common analogies, playful emojis, and…

View On WordPress
#access control#brute force attacks#data encryption#employee education#firewall#hackers#intruders#intrusion prevention#multi-layered defense#network protection#network security#packet inspection#patch management#security incident response#spoofing
0 notes
Text
#Employee monitoring software#Time tracking tool#Productivity monitoring#Attendance tracking#Application monitoring#Website monitoring#Data security#Employee accountability#Remote employee monitoring#Keystroke logging#Screenshot capturing#File and document tracking#Workflow optimization#Data encryption
1 note
·
View note
Text
The Interplay Between Digital Democracy and Data Security: Safeguarding Privacy and Trust
Digital democracy refers to the application of digital technologies and platforms to enhance democratic processes and citizen participation in decision-making. It aims to leverage the power of the internet and other digital tools to increase civic engagement, transparency, and inclusivity in democratic systems.
Digital democracy encompasses various practices and initiatives,…

View On WordPress
#data breaches#data encryption#Data Security#Digital democracy#online participation#privacy protection#secure voting systems#trustworthiness#voter information
0 notes
Text
What is Web3?
Introduction
Web3 is a new iteration of the World Wide Web that is built on decentralized technologies such as blockchain and cryptography. It is designed to give users more control over their data and privacy, and to create a more open and democratic internet.
Web3 is still in its early stages of development, but it has the potential to revolutionize the way we use the internet. It could make…

View On WordPress
#and non-fungible tokens (NFTs).#Blockchain technology#Data encryption#data security#decentralized applications (dApps)#decentralized finance (DeFi)#Global technology#Networking#Peer to peer#Tamperproof#Web3#Www
0 notes