#cybersecurity investments
Photo

The fog of digital warfare in China is thick and mysterious. Monitors like guardian dragons watch silently from the shadows as data flows through dark networks, controlling the tempo of the cyberbattle. Its web of deception grows ever more intricate as the boundaries of the conflict itself become blurred. The lines between nations sharpen as its impact is felt in the global arena. It's a world where the winners and losers will be determined not in the battlefield, but in the virtual landscape.
#Asia#Cyber Warfare#Security#21st century warfare#China cyber capabilities#China's digital influence#cyber defense strategies#cyber geopolitics#cyber warfare implications#cybersecurity investments#digital warfare#digital warriors#economic impacts of cyber attacks#future of digital battles#global cyber partnerships#global cyber reactions#Headline#interconnected global conflict#modern warfare trends#political implications of digital warfare#technological innovations in warfare#fault#Chinese#warfare#cyberspace#cyberattacks#espionage
0 notes
Text
Ok I'll talk more about Raven Beak's suit.
You know how Samus' suit just up and explodes if you get her killed? At least in Mawkin powersuits, that's an intended feature for specific warrior classes.
If you were to kill Raven Beak in some way other than allowing a Metroid to juice him like a lemon, his suit would explode. That's a security feature: the Mawkin are very proud of their technology, and firmly believe that their secrets of warfare should never fall into the hands of Others: partly because they're so proud, but also for the good of the galaxy. They don't want their secrets being used by bad actors to wreak havoc.
Raven Beak is the Mawkin Warlord: as such, his suit is juiced up to the nth degree. If he were to fall in battle and his suit didn't explode, the Mawkin would be waist-high in the swamp. If, for example, the Space Pirates were to get ahold of his suit and reverse engineer it, the Mawkin would be held responsible for unleashing the means for the Pirates to create devastating weapons based on their designs.
Mawkin suits are highly optimized and possess combat capabilities and weapons that far exceed most other tribes. Raven Beak's suit has custom "firmware". His suit and the suits of a number of high echelon warriors and intelligence agents are designed to combust in a very particular way.
When the wearer's vitals fall below critical levels, the suit cannibalizes its own upgrades. The excess matter that accumulates as a result of this reaction is highly volatile, and the speed at which this all occurs helps to catalyze a fantastic explosion that ensures no technological footprint is left behind. No user data, no biometrics, no upgrades, no suit. Typically, the more upgrades you have, the grander the explosion is: that's more matter for the dying suit to push together like a play-doh ball made of dynamite.
Upon death, the Shrouded Talons' suits are designed to destroy not just the tech, but the body as well. If a unit is decommissioned, the intelligence wing of the tribe logically does not want the agent's identity to be discerned. Leave no trace and there's no trail to follow, as it were. There's a reason the Talons aren't common knowledge in intergalactic intelligence circles: they take cleaning up after themselves very seriously.
#headcanons#metroid#txt#not art#mawkin#In Winging It the fact that the Federation can even distribute new upgrades to Samus is concerning to Raven Beak.#The notion that these features could potentially be remotely disabled on a whim flips a switch in his brain that says#'you need a better suit'#'gurl you need to invest in cybersecurity'#'your data is at RISK queen'
144 notes
·
View notes
Text
(irl shit)
this place I interned at one time, elevator repair and r&d, led by two EE guys and several technicians/repairs people who probably knew way more about engineering than both the EEngineers and myself combined (definitely more than me!), had this strange issue where, basically, the elevator software wasn't properly being installed into the elevator (the bootloader was throwing an error) when the computer running the bootloader also had an internet browser running and this internet browser was streaming music.
yeah seriously.
so digging around I found that when the browser was running the bootloader would fail to map the first byte to the correct address, but fixing that was beyond me, I had only the vaguest understanding of how shit worked, so my suggestion was "just turn the music off for a second man". obviously they didn't like that, they were like "yeah we figured that out already did you go to school for this" lmao hhgjfhg
#also i helped another intern (also EE guy) steal their source code because he asked for help and i was a#comp eng intern at an elevator company with literally nothing to do between the hours 8-6 every fucking weekday and saturday#they shouldn't have let me access those SD cards they used for flashing#and maybe invest into cybersecurity#no i didn't get anything out of it other than dopamine i guess. it was funny#i doubt he got anything out of it either because decrypted or not neither of us were familiar with the language hgjkfng#i was like well this looks like code of pascal variety but i don't know what the fuck it's for. good luck man#talkative rinka arc
9 notes
·
View notes
Text
Cisco's Game-Changing Acquisition of Splunk: What It Means for the Cybersecurity Landscape
Cisco, the networking giant, recently made headlines with its eye-popping acquisition of cybersecurity software company Splunk, a deal that’s said to be worth around $28 billion. To say this is significant would be an understatement; the acquisition serves as a linchpin in Cisco’s ongoing strategy to expand its cybersecurity capabilities.
Cisco’s Cybersecurity Evolution
For Cisco, a company…

View On WordPress
11 notes
·
View notes
Text
Cybersecurity Stocks In India: A Comprehensive List Of Top Players
Introduction:-
Welcome to the digital age, where technology has become an integral part of our daily lives. Along with its numerous benefits, technology also brings along various cyber threats and attacks, making cybersecurity a top priority for businesses and individuals. With the growing demand for cybersecurity solutions, the market for cybersecurity stocks in India is also on the rise.
Understanding Cybersecurity Stocks in India
Cybersecurity stocks refer to the shares of companies that provide cybersecurity solutions and services to businesses and individuals. They function like any other stock in the stock market, with the potential for growth and returns on investment.

Top Players in the Indian Cybersecurity Market:-
✔ Infosys
✔ Wipro
✔ Tata Consultancy Services
Risks and Challenges in the Indian Cybersecurity Market
The Indian cybersecurity market holds immense potential for growth and investment opportunities. However, like any other market, there are risks and challenges that investors should be aware of.
✔ Potential Risks
✔ Limited Talent Pool
✔ Competition from Global Players
Read more information in detail on Cybersecurity Stocks In India
0 notes
Text
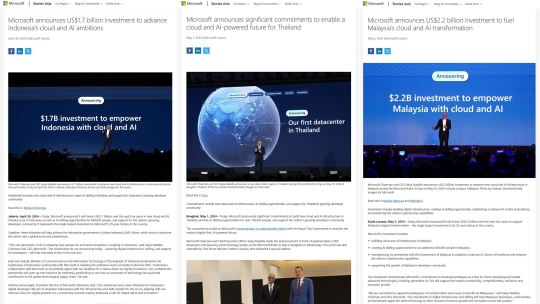
The Microsoft Corporation recently announced Billions of Dollars worth of Investments that will benefit over a million People in three major Countries in South East Asia (SEA), but none of these will be in the Philippines, the supposedly “Ally” of Microsoft’s Country, the United States (US)
This was initially released as an Article last May 13, 2024 at https://therhk111philippinedefenseupdates.blogspot.com/2024/05/microsoft-invests-billions-other-sea-countries-except-us-ally-philippines.html
#microsoftcorporation#southeastasia#unitedstates#ally#philippines#indonesia#cloud#artificialintelligence#ai#infrastructure#developercommunity#malaysia#investment#cybersecurity#software#datacenter#presidentbongbongmarcos#pbbm#mutualdefencetreaty#mdt#ukraine#superpowerrival#appleincorporated#vietnam
0 notes
Text
0 notes
Text
ICAI's Guidance Note on Audit of Banks (2024 Edition)
The Institute of Chartered Accountants of India (ICAI) stands at the forefront of shaping the accounting profession, providing guidance and standards to ensure excellence and integrity in financial practices. as usual on February 14, 2024, ICAI issued the latest edition of its Guidance Note on Audit of Banks, offering comprehensive insights and directives for auditors navigating the complex…

View On WordPress
#2024 Edition#audit#Audit of Banks#auditing standards#banking sector#business-investments#cybersecurity#emerging risks#Financial Reporting#Guidance Note#icai#icai-dubai-chapter#international standards#jobs#Professional guidance#RBI guidelines#Regulatory Compliance#risk assessment
0 notes
Text
India's Tech Talent: Offshore Development and IT Outsourcing Investment

India has long been recognized as a global hub for technological expertise and innovation. With a burgeoning tech landscape and a pool of skilled professionals, the country has made significant strides in the realm of offshore development and IT outsourcing. The convergence of a highly skilled workforce, cost-effective solutions, and a conducive business environment has solidified India's position as a preferred destination for companies worldwide seeking to invest in offshore development and outsource their IT operations.
Overview of India's Tech Industry
The Indian tech industry has experienced remarkable growth over the years, evolving from its nascent stages to becoming a powerhouse in the global technology arena. The journey traces back to the 1980s when India's IT industry began to take shape with a focus on software development and services. Since then, it has expanded exponentially, encompassing a wide array of domains such as software development, IT services, engineering, R&D, and more recently, emerging technologies like AI, blockchain, and IoT.
Importance of Tech Talent in Global Markets
Tech talent plays a pivotal role in shaping the competitive landscape of global markets. India's robust talent pool has been instrumental in propelling the country's tech industry forward. The availability of a vast workforce skilled in software engineering, programming, data analytics, and other specialized domains has been a key factor driving India's success in catering to the needs of diverse industries worldwide.
Significance of Outsourcing and Offshore Development
Outsourcing and offshore development have become integral strategies for businesses looking to optimize their operations and remain competitive. Outsourcing involves delegating specific tasks or functions to external service providers, while offshore development refers to the practice of establishing development teams or centers in other countries, typically to leverage cost benefits and access specialized skills. India has emerged as a preferred destination for both these practices due to its conducive business environment, cost-effectiveness, and a skilled workforce proficient in various technologies.
In the next sections of this blog, we'll delve deeper into India's tech landscape, the evolution of offshore development, the significance of IT outsourcing, and explore the myriad investment opportunities that India's tech industry presents. Moreover, we'll highlight the factors that contribute to India's robust tech talent pool, elucidating why the country remains a hotspot for global businesses seeking to invest and leverage its vast potential.
Stay tuned as we explore the intricate facets of India's tech prowess and the lucrative opportunities it holds for investors and businesses looking to capitalize on offshore development and IT outsourcing.
I. India's Tech Landscape
A. Historical Development of India's Tech Industry
The evolution of India's tech industry is a testament to the nation's resilience, adaptability, and technological prowess. Initially focusing on software services and development, India's tech landscape gained traction in the 1990s when economic reforms liberalized the market, encouraging foreign investments and collaborations. This era marked the establishment of numerous IT companies and laid the foundation for India's emergence as a global technology hub.
B. Present Scenario: Growth and Trends
Today, India's tech sector stands at the forefront of innovation and growth. The country has witnessed a rapid proliferation of startups and technology-driven enterprises, disrupting traditional business models and pioneering groundbreaking solutions. With a robust ecosystem fostering innovation and entrepreneurship, India continues to attract investments from multinational corporations, venture capitalists, and tech enthusiasts globally.
C. Key Factors Driving India's Tech Success
Several factors contribute to India's tech success story. The availability of a vast talent pool proficient in technology, engineering, and scientific disciplines remains a cornerstone. Additionally, a favorable regulatory environment, supportive government policies, and a growing digital infrastructure have all played pivotal roles in nurturing the growth of India's tech industry.
II. Understanding Offshore Development
A. Definition and Scope
Offshore development involves setting up development teams or centers in other countries to facilitate software development, testing, and maintenance processes. This strategy enables companies to leverage specialized skills, cost advantages, and round-the-clock operations while maintaining quality standards.
B. Advantages of Offshore Development
India's prominence in offshore development is attributed to various advantages it offers. These include a large pool of skilled professionals adept in various programming languages and technologies, cost-effectiveness without compromising quality, streamlined communication channels, and adherence to strict data security and intellectual property protection measures.
C. India's Position as a Premier Offshore Development Destination
The country's reputation as a premier offshore development destination has been solidified over the years. Indian companies, as well as multinational corporations, have established offshore development centers to harness India's talent pool and technical expertise. Industries ranging from healthcare, finance, e-commerce, to manufacturing have benefited from offshore development in India, reaping the advantages of scalability, flexibility, and access to specialized skills.
III. IT Outsourcing in India
A. Role of India in IT Outsourcing
India has been a frontrunner in the global IT outsourcing landscape. The country's IT service providers offer a wide spectrum of services, including software development, application maintenance, infrastructure management, and business process outsourcing (BPO). Indian companies cater to diverse industries across the globe, providing cost-effective and high-quality solutions.
B. Why Companies Outsource to India
Businesses opt to outsource to India due to several compelling reasons. The country's skilled workforce, domain expertise, robust IT infrastructure, adherence to international quality standards, and competitive pricing structures make it an attractive destination for outsourcing IT operations.
C. Success Stories and Case Studies
Numerous success stories and case studies highlight the efficacy of IT outsourcing to India. From Fortune 500 companies to startups, businesses have reaped significant benefits by partnering with Indian service providers. These collaborations have resulted in innovative solutions, cost savings, faster time-to-market, and enhanced operational efficiency for client organizations worldwide.
India's tech industry stands as a testament to the nation's journey from a budding IT landscape to a global technology powerhouse. The evolution, growth, and success of India's tech ecosystem have been shaped by a confluence of factors, making it an enticing destination for offshore development, IT outsourcing, and lucrative investment opportunities./strong>
A Land of Opportunity: Investment Prospects in India's Tech Industry
The Indian tech landscape presents a myriad of investment prospects across various sectors. With a conducive business environment, government initiatives promoting innovation and entrepreneurship, and a robust digital infrastructure, India beckons investors seeking to capitalize on its burgeoning tech ecosystem. Sectors like AI, machine learning, cybersecurity, IoT, and cloud computing offer immense growth potential, providing opportunities for collaboration, investment, and market expansion.
Global Leadership in Offshore Development
India's position as a global leader in offshore development remains unchallenged. The country's proficiency in delivering high-quality software solutions, cost-effectiveness, and access to a diverse talent pool continue to attract businesses worldwide. Organizations leverage India's expertise in offshore development to enhance operational efficiency, accelerate product development cycles, and tap into specialized skills that drive innovation.
Pioneering IT Outsourcing Hub
The significance of India in the realm of IT outsourcing cannot be overstated. The country's IT service providers cater to a wide array of industries, offering comprehensive solutions that align with global standards. Collaborating with Indian firms allows businesses to achieve cost savings, access specialized expertise, and focus on core competencies while leveraging the scalability and flexibility inherent in outsourcing operations.
India's Tech Talent Pool: A Strategic Advantage
The backbone of India's tech prowess lies in its skilled and adaptable workforce. The country boasts a vast talent pool equipped with technical expertise, problem-solving abilities, and a penchant for innovation. The education system, with its emphasis on science, technology, engineering, and mathematics (STEM), produces a steady stream of skilled professionals ready to tackle the challenges of a dynamic tech landscape.
Looking Ahead: Opportunities and Challenges
As India's tech industry continues to evolve, it faces both opportunities and challenges. Embracing emerging technologies, fostering a culture of innovation, and addressing the skill gap will be crucial for sustaining growth. Additionally, ensuring cybersecurity, data privacy, and regulatory compliance remains imperative to maintain India's credibility as a reliable tech partner on the global stage.
Final Thoughts: The Future of India's Tech Industry
In conclusion, India's tech industry stands poised at the cusp of transformational growth. The convergence of technological innovation, entrepreneurial spirit, and a talented workforce propels the nation towards becoming a global leader in technology-driven solutions. The scope for investment, collaboration, and innovation in India's tech landscape remains vast, offering opportunities for businesses, investors, and tech enthusiasts alike to contribute to and benefit from this ever-evolving ecosystem.
As we witness the continuous evolution of India's tech prowess, it is evident that the country's journey from an outsourcing destination to an innovation hub is both promising and inspiring. The narrative of India's tech industry is one of resilience, adaptability, and unwavering commitment to technological advancement, making it an indispensable player in the global tech arena.
This post was originally published on: Foxnangel
#India's tech industry#offshore development#it outsourcing#investment opportunities#FoxnAngel#AI#machine learning#cybersecurity#iot#technology investment#India's tech talent#global tech leadership
0 notes
Photo

The Chinese are on the forefront of a new type of warfare, one that is fought not just on the battlefield, but in cyberspace. They are redefining what it means to wage war, and the rest of the world is scrambling to keep up. The Chinese have always been a formidable foe, but their latest tactics are something else entirely. They have shown that they are willing to use all available tools to gain an advantage, including cyberattacks and espionage. This new type of warfare is a serious threat to the rest of the world, and we need to find a way to counter it. The Chinese are clearly ahead of the curve, but we can't afford to fall too far behind.
#Asia#Cyber Warfare#Security#21st century warfare#China cyber capabilities#China's digital influence#cyber defense strategies#cyber geopolitics#cyber warfare implications#cybersecurity investments#digital warfare#digital warriors#economic impacts of cyber attacks#future of digital battles#global cyber partnerships#global cyber reactions#Headline#interconnected global conflict#modern warfare trends#political implications of digital warfare#technological innovations in warfare#fault#Chinese#warfare#cyberspace#cyberattacks#espionage
0 notes
Text
In an era dominated by digital advancements, the importance of cybersecurity for businesses cannot be overstated. But why should businesses never overlook cybersecurity, and what are the most common risks that can profoundly impact their operations? As a reliable name in the cybersecurity industry in Maryland, let us answer these questions with expertise.
1 note
·
View note
Text
Cybersecurity in Personal Finance Management: Essential Strategies for Digital Safety
In today’s digital age, where a staggering 76% of Americans engage in online banking (Pew Research Center), the importance of cybersecurity in managing personal finances cannot be overstated. This comprehensive guide explores the essential strategies for protecting your online banking, investment, and transaction activities from cyber threats.
Fortifying Online Banking and Investments: An…
View On WordPress
#cyberattack statistics#cybercrime prevention#Cybersecurity#data backup#data protection#digital finance management#digital transactions#expert cybersecurity advice#financial cybersecurity guide#financial data encryption#global cybercrime costs#hard drive failure risks#investment security#online banking#personal finance#phishing scams#phishing threat awareness#public Wi-Fi security#robust passwords#secure financial apps#secure online investments#SSL certificates#two-factor authentication#VPN usage#Wi-Fi safety
0 notes
Text
Best IT Consulting Company In Hyderabad | 2024
Applogic Consulting is a global provider of innovative, integrated, affordable, and reliable IT consulting and recruitment services. Our business organization and purpose are very well-defined. In the last one-and-half decades, we have earned the rare distinction as the most trusted advisors and consultants. With qualified and competent people at the heart of our operations, we strive to deliver high quality to each client engagement. For our clients, this means enhancing practice management efficiency and profitability.
We pioneer pristine IT consulting and people management practices. This means putting trained and experienced people in the right roles to achieve competitive distinctiveness. Understandably, we are here to achieve a higher objective that goes beyond IT consulting and recruiting services. We attract and retain individuals whose skills totally align with your organization’s purpose and project’s expectations.
Applogic Consulting works as an extension to the client’s project team. This means understanding four crucial factors – skills and competencies required, project expectations, and the component of dedicated or consulting support. Our IT consulting practice tells us that, less-vital roles and roles do not need year-round support. These may be filled by experienced and value-driven consultants than by in-house personnel.
It is a point of consensus at Applogic Consulting to establish interconnectedness between work expectations and the competencies of personnel. So far, we could attract and retain not only world-class IT professionals but also top technology consultants. We understand that only the combined efforts of internal and external personnel resources help to meet the organizational purpose and project objectives.
Why Applogic Consulting
Our company is committed to providing reliable, affordable, scalable, and value-driven IT and Non-IT services that meet the unique challenges associated with projects in these areas. We aim to distinguish ourselves as the most trusted and reliable IT consultants and recruitment advisors, offering advanced business-specific and customer-centric technologies to align your organization’s purpose, motivated teams, and project expectations.
Our goal is to establish an interconnected and collaborative work environment across the IT organization, providing the right people to achieve competitive distinctiveness. We can help your organization make an explicit choice to impart a niche, valuable, and unique position. Additionally, we offer robust and time-bound training interventions for skills upgrades to ensure that your team has the necessary expertise to succeed.
At our core, we believe in meeting the unique challenges associated with IT and non-IT projects, leveraging our expertise and experience to help organizations achieve their goals. Trust us to provide the services you need to succeed in today’s competitive landscape.
Applogic Consulting is the Best IT Consulting Company in Hyderabad.
For More Details Contact us :
8978886018
#accounting#branding#business#finance#it consulting#it services#ecommerce#investing#entrepreneur#founder#economy#commercial#cybersecurity
0 notes
Text
Are open foundation models more risky than closed ones?
New Post has been published on https://thedigitalinsider.com/are-open-foundation-models-more-risky-than-closed-ones/
Are open foundation models more risky than closed ones?


Some of the most pressing questions in artificial intelligence concern the future of open foundation models (FMs). Do these models pose risks so large that we must attempt to stop their proliferation? Or are the risks overstated and the benefits under emphasized?
Earlier this week, in collaboration with Stanford HAI, CRFM, and RegLab, we released a policy brief addressing these questions. The brief is based on lessons from a workshop we organized this September and our work since. It outlines the current evidence on the risk of open FMs and some recommendations for policymakers on how to reason about the risks of open FMs.
In the brief, we highlight the potential of open FMs in aiding the distribution of power and increasing innovation and transparency. We also highlight that the evidence for several of the purported risks of open FMs, such as biosecurity and cybersecurity risks, is overstated.
At the same time, open FMs have already led to harm in other domains. Notably, these models have been used to create vast amounts of non-consensual intimate imagery and child sexual abuse material.
We outline several considerations for informed policymaking, including the fact that policies requiring content provenance and placing liability for downstream harms onto open model developers would lead to a de facto ban on open FMs.
We also point out that there are other ways to address these harms that are downstream of the model itself, such as platforms for sharing AI-generated nonconsensual pornography. For example, CivitAI allowed users to post bounties for nonconsensual pornography about real people, with rewards for the developers of the best model. Such choke points are likely to be a more effective target for intervention.
One reason for the recent focus on open FMs is the recent White House executive order. Since the question of the relative risk of open and closed FMs is an area of ongoing debate, the EO didn’t take a position on it; the White House instead directed the National Telecommunications and Infrastructure Agency (NTIA) to launch a public consultation on this question.
The NTIA kicked off this consultation in collaboration with the Center for Democracy and Technology earlier this week, which one of us spoke at.
While policies should be guided by empirical evidence, this doesn’t mean we shouldn’t think about the risks that might arise in the future. In fact, we think investing in early warning indicators of risks of FMs (including open FMs) is important. But in the absence of such evidence, policymakers should be cautious about developing policies that curb the benefits of open FMs while doing nothing to reduce their harms.
Towards a better understanding of the risks of open models, we are currently working on a more in-depth paper analyzing the benefits and risks of open FMs with a broad group of experts. We hope that our policy brief, as well as the upcoming paper, will be useful in charting the path of policies on regulating FMs.
#ai#artificial#Artificial Intelligence#Collaboration#cybersecurity#Democracy#developers#domains#executive order#Foundation#Future#how#how to#Infrastructure#Innovation#intelligence#investing#it#LED#material#model#One#Other#outline#paper#Policy#power#risk#risks#technology
0 notes
Text
US Cybersecurity Alert: Bitcoin Inscriptions Pose New Risks | ICODesk
In a recent cybersecurity alert, U.S. authorities have identified Bitcoin inscriptions as a potential risk to cybersecurity. The use of Bitcoin inscriptions, which involves embedding messages or data within Bitcoin transactions, has raised concerns among cybersecurity experts due to the potential for malicious activities and information dissemination.
Bitcoin inscriptions utilize the script language within Bitcoin transactions to embed additional information. While the primary purpose of Bitcoin transactions is to transfer value securely, the script language allows users to include data along with the transaction. This feature, although not widely used for legitimate purposes, has gained attention as a potential vector for cybersecurity threats.
Identified Cybersecurity Risks
Bitcoin inscriptions can be exploited to distribute malware. Malicious actors may embed executable code or links to malware within Bitcoin transactions, aiming to compromise the security of systems that process or interact with these transactions.
The use of Bitcoin inscriptions to embed messages can facilitate disinformation campaigns. Threat actors might use this method to spread false information or propaganda, leveraging the decentralized and immutable nature of the Bitcoin blockchain.
Large volumes of inscriptions can lead to blockchain bloat, impacting the efficiency and scalability of the Bitcoin network. Excessive data within transactions can strain the network, affecting transaction processing times and increasing fees.

Response and Mitigation Measures
In response to the identified risks associated with Bitcoin inscriptions, several mitigation measures are being considered:
Blockchain analytics tools are being employed to monitor Bitcoin transactions more effectively. Enhanced transaction monitoring aims to identify and flag transactions with suspicious inscriptions for further investigation.
Regulatory bodies are exploring ways to enhance oversight of cryptocurrency transactions. This includes collaborating with industry stakeholders to establish guidelines and best practices for preventing malicious use of Bitcoin inscriptions.
Educating users, businesses, and cryptocurrency service providers about the risks associated with Bitcoin inscriptions is crucial. Increased awareness can contribute to more informed decision-making and the adoption of security best practices
Blockchain Protocol Updates
Ongoing discussions within the cryptocurrency community involve potential updates to the Bitcoin protocol. These updates could address security concerns related to inscriptions and implement measures to mitigate associated risks.
While Bitcoin inscriptions have the potential to introduce new risks to cybersecurity, the cryptocurrency community and regulatory authorities are actively working to understand and address these challenges. As the landscape evolves, collaboration between stakeholders, ongoing research, and the implementation of effective cybersecurity measures will be essential to maintaining the integrity and security of the broader digital financial ecosystem.
For more updates
#bitcoin#bitcoin inscriptions#blockchain#cybersecurity#cybersecurity threats#cryptocurrency#crypto#crypto news#cryptocurrency prices#crypto price#ethereum#icodeskupdate#icodesknews#icodesk#crypto investing#crypto trading#cryptocurreny trading#cryptocurrencies#icodesknewsupdate
0 notes
Text
Opal Security, which helps companies manage access and identities, raises $22M | TechCrunch
VC investment trends in the cybersecurity market suggest a sector in decline — at least within the context of recent months. According to Crunchbase, cybersecurity deal count fell during Q3 to 153 deals from 181 in Q2. In a more detailed report, Crunchbase suggests that, with Q3 cybersecurity venture funding down 30% compared to the year-ago period, investment in the category could fall to its…
View On WordPress
0 notes