#cyber risk
Text
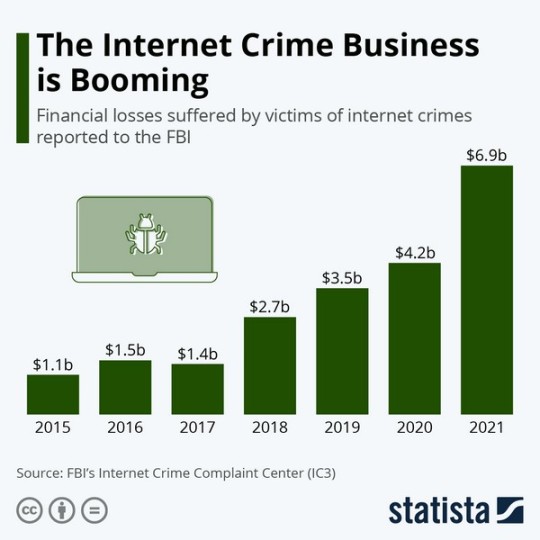
Cyber Crime: Χρονιά ρεκόρ το 2021! - Η έκθεση του FBI
Cyber Crime: Χρονιά ρεκόρ το 2021! – Η έκθεση του FBI
Το Κέντρο Παραπόνων Διαδικτυακού Εγκλήματος (IC3) του FBI δημοσίευσε την Έκθεση Διαδικτυακού Εγκλήματος για το 2021, η οποία καταγράφει την προηγούμενη χρονιά ως έτος ρεκόρ τόσο για τα θύματα του διαδικτυακού εγκλήματος όσο και για τις χρηματικές απώλειες στις Ηνωμένες Πολιτείες.
(more…)
View On WordPress
2 notes
·
View notes
Text
Now corporate boards have responsibility for cybersecurity, too
New Post has been published on https://thedigitalinsider.com/now-corporate-boards-have-responsibility-for-cybersecurity-too/
Now corporate boards have responsibility for cybersecurity, too


A new ruling from the U.S. Securities and Exchange Commission (SEC), known as the Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure, went into effect last fall. The ruling requires public companies to disclose whether their boards of directors have members with cybersecurity expertise. Specifically, registrants are required to disclose whether the entire board, a specific board member, or a board committee is responsible for the oversight of cyber risks; the processes by which the board is informed about cyber risks, and the frequency of its discussions on this topic; and whether and how the board or specified board committee considers cyber risks as part of its business strategy, risk management, and financial oversight.
“In simplest terms, boards are on the hook for management, governance, and disclosure reporting,” explains Keri Pearlson, executive director of the Cybersecurity at MIT Sloan Research Consortium (CAMS). “While there is a lot of interpretation left to do, this we know for sure.”
Also well understood is the increasing likelihood of hacking events and the exponential cost to companies. Despite recent efforts to beef up cybersecurity by companies and governments worldwide, data breaches continue to increase year over year. Data show a 20 percent increase in data breaches from 2022 to 2023. Given the rapid proliferation of digital work and digitization in general, this should come as no surprise. As noted by the SEC in a fact sheet accompanying the recent rulings, “Cybersecurity risks have increased alongside the digitalization of registrants’ operations, the growth of remote work, the ability of criminals to monetize cybersecurity incidents, the use of digital payments, and the increasing reliance on third-party service providers for information technology services, including cloud computing technology.”
Cyber resilience: respond and recover
Pearlson’s ongoing research includes organizational, strategic, management, and leadership issues in cybersecurity. Her current focus is on the board’s role in cybersecurity. In a January 2023 MIT Sloan Management Review article, “An Action Plan for Cyber Resilience,” Pearlson and her co-authors suggest that board members must assume that cyberattacks are likely and exercise their oversight role to ensure that executives and managers have made the proper preparations to respond and recover.
“After all, if we assume every organization has a likely risk of being breached or attacked, and it’s not possible to be 100 percent protected from every attack, the most rational approach is to make sure the organization can recover with little or no damage to operations, to the financial bottom line, and to the organization’s reputation,” says Pearlson. To properly mitigate cyber risk, company leaders must have rock-solid plans in place to respond and recover quickly so that the company can continue to operate. They need to be cyber resilient.
Pearlson compares cyber resilience to Covid resilience practices. “We did things like stay home, wear masks, and get vaccines to both reduce the chances we got Covid, but also to reduce the consequences of getting sick.”
In other words, the current, protection-oriented approach most companies take to cyber is not enough. Protection only helps us mitigate issues we know about. But cyber criminals are innovative, and we don’t know what we don’t know. They seem to continually find new ways to break into our systems. Pearlson talks about the need to be resilient and how that kind of thinking comes from the top. “While boards have been getting reports on cybersecurity for a long time, these are typically once a year and not focused on the data that boards need to ensure their companies are resilient,” says Pearlson.
In their May 2023 Harvard Business Review article, “Boards Are Having the Wrong Conversations About Cybersecurity,” Pearlson and co-author Lucia Milică comment on the inadequacy of typical cybersecurity presentations during board meetings, which usually cover threats and the actions or technologies the company is implementing to protect against them. “To us, that is the wrong perspective for board oversight. We know we cannot be completely protected, no matter how much money we invest in technologies or programs to stop cyberattacks. While spending resources to protect our assets is critical, limiting discussions to protection sets us up for disaster.”
Instead, the conversation needs to focus on resilience. For example, instead of going into detail in a board meeting on how an organization is set up to respond to an incident, members must focus on what the biggest risk might be and how the organization is prepared to quickly recover from the damage should that situation happen.
Assessing risk using a Balanced Scorecard approach
To that end, Pearlson developed the Board Level Balanced Scorecard for Cyber Resilience (BSCR), designed to help boards and management have more productive discussions and understand the organization’s biggest risks to cyber resilience. Inspired by Kaplan and Norton’s Balanced Scorecard, a well-known tool for measuring organizational performance, Pearlson’s BSCR maps these key risk areas into four quadrants: performance, technology, organizational activities (such as people and compliance requirements), and supply chain. Each quadrant includes three components:
A quantitative progress indicator (red-yellow-green stoplight) based on the organization’s existing framework for cybersecurity controls such as CISA Cybersecurity Performance Goals (CPG), NIST SP 800-53, ISO 27001, CIS Controls or other controls assessments;
The biggest risk factor to organizational resilience according to C-level leaders; and
A qualitative action plan, where C-level leaders share their plan to address this risk.
The scorecard helps orient board reporting and conversation on the focus areas around which the organization should be concerned in the event of a cyberattack — specifically, the technology, the financial side of the business, the organizational side, and the supply chain. While some companies may require other quadrants, the idea is that each of those focus areas should have quantitative measures. By looking at these indicators together in a single framework, leaders can draw conclusions that might otherwise be missed.
“Having controls is nothing new, particularly for publicly traded companies that have a program for measuring and managing their cybersecurity investments,” says Pearlson. “However, there is a qualitative risk that often doesn’t come across in those measurements. While a typical control may measure how many people failed the phishing exercise, which is an important component of cybersecurity, the scorecard encourages businesses to also understand what is at risk and what is being done about it.” You can read more about the scorecard in this recent Harvard Business Review article.
Providing boards the information they need
The vast majority of leaders understand they are in jeopardy of an attack — they just don’t know how to talk about it or what to do about it. While it’s easiest for cyber executives to report on technology metrics or organizational metrics, this information does not help the board with their job of ensuring cyber resilience. “It’s the wrong information, at least initially, for conversations with the board,” says Pearlson.
Throughout Pearlson’s research, cybersecurity leaders, board directors, and other subject matter experts expressed their interest in key information about system assets, proactive capabilities, and how quickly they could recover. Some wanted to better understand what data types their company maintained, where they were maintained, the likelihood of compromise, and the impact that compromise would have on business operations. More than half of the participants wanted to know the financial dollar value involved with breaches or cyberattacks on their organization.
Pearlson’s BSCR helps to put these risks in the context of specific areas or processes that are core to the business and to address nuances, such as: is this an immediate risk or a long-term? Would a compromise in this area have a minimal impact or a huge impact?
“A Balanced Scorecard for Cyber Resilience is the starting place for the discussions about how the business will continue operations when an event occurs,” says Pearlson. “It is not enough to invest only in protection today. We need to focus on business resilience to cyber vulnerabilities and threats. To do that, we need a balanced, qualitative assessment from the operational leaders who know.”
Pearlson teaches in two MIT Sloan Executive Education courses that help individuals and their organizations be more resilient. Designed for non-cyber professionals, Cybersecurity Leadership for Non-Technical Executives helps participants become knowledgeable in the discussion. Cybersecurity Governance for the Board of Directors assists board members, C-suite leaders, and other senior executives in quickly gathering essential language and perspectives for cybersecurity strategy and risk management to better carry out their oversight and leadership responsibilities.
#2022#2023#approach#Article#assessment#assets#beef#board#boards#Business#Business and management#business resilience#c-level#C-suite#cisa#Cloud#cloud computing#Companies#compliance#computing#courses#covid#cyber#cyber criminals#cyber risk#cyberattack#Cyberattacks#cybersecurity#cybersecurity strategy#data
0 notes
Text
Deep pool of capital, cat bonds help meet cyber insurance demand: Beazley CEO
New Post has been published on https://petn.ws/ILEYo
Deep pool of capital, cat bonds help meet cyber insurance demand: Beazley CEO
Commenting this morning alongside his firm’s results announcement, Beazley Chief Executive Officer (CEO) Adrian Cox said that a “deep pool of capital” is required to support growing demand for cyber insurance, while the company’s CUO Bob Quane noted that the capital markets are now stepping up in support.Beazley has helped to pioneer the development of […]
See full article at https://petn.ws/ILEYo
#CatsNews #CatBond, #CatastropheBond, #CyberCatastropheBond, #CyberILSCyberInsuranceLinkedSecurities, #CyberInsurance, #CyberInsuranceLinkedSecurities, #CyberReinsurance, #CyberRisk, #InsuranceLinkedSecurities, #Reinsurance
#Cat bond#Catastrophe bond#Cyber catastrophe bond#Cyber ILS - Cyber Insurance-Linked Securities#cyber insurance#cyber insurance-linked securities#cyber reinsurance#cyber risk#Insurance linked securities#reinsurance#Cats News
0 notes
Text
How Does Ethereum Work?
Ethereum is a blockchain-based computing platform that gives programmers the ability to create and implement decentralised applications, which are those that are not controlled by a single entity. You can design a decentralised application where the decision-making power resides with the application’s users. The Ethereum network is fueled by its own cryptocurrency called ‘ether’.
Here is the details explanation of how does ethereum work for beginners–
Decentralized Network of Nodes:-
Ethereum runs on a decentralised network of machines called nodes, which collaborate to keep the blockchain up to date. The ethereum blockchain, a record of all activities that have taken place on the network, is replicated in every node. To confirm deals and maintain the network’s integrity, nodes converse with one another.
Consensus Mechanism:-
In order to validate transactions and add new blocks to the blockchain, Ethereum uses a consensus method called Proof of Work (PoW), which requires nodes to solve challenging mathematical problems. However, Ethereum is moving towards a Proof of Stake (PoS) consensus method, which will require nodes to stake a certain sum of Ether in order to approve transactions and add new blocks to the blockchain.
Smart Contrats:-
Smart contracts are self-executing contracts with the terms of the agreement between buyer and seller being directly written into lines of code. They are stored on the blockchain and can be executed automatically when certain conditions are met. Smart contracts can be used to automate a wide range of processes and transactions, such as financial transactions, supply chain management, and more.
Ethereum Virtual Machine (EVM):-
The Ethereum Virtual Machine (EVM) is intended to serve as the runtime setting for Ethereum’s smart contracts. It is separated from the rest of the system and sandboxed. This implies that no matter how many times you call a specific function on EVM, it should not in any way affect your data or programmes.
The environment in which Ethereum smart contracts are executed is known as an EVM.
There is a need to run this code because Ethereum has its own Turing-complete scripting language named Solidity.
This job can be carried out by a programme known as the Ethereum Virtual Machine (EVM).
Because it is built on top of the Ethereum network, all of the nodes agree on what code should be executed at any particular moment.
Ethereum Cryptocurrency:-
Ethereum runs on its local token called Ether which serves two primary purposes:
Ether installment is required for applications to perform any operation so that broken and noxious programs are kept beneath control
Ether is compensated as an motivation to the mineworkers who contribute to the Ethereum arrange with their assets- much like bitcoin’s structure.
Each time a contract is executed, Ethereum devours token which is named as ‘gas’ to run the computations.
Ethereum price, Gas and Transaction Fees:-
Ethereum price, Gas and Transaction Fees: Gas is the cost of performing an operation or executing a smart contract on the Ethereum network. Gas is paid in Ether, and the amount of gas required for a transaction is determined by the complexity of the operation or smart contract being executed. Transaction fees are the amount of Ether paid to incentivize nodes to validate transactions and add them to the blockchain.
Wallets and Interaction with the Ethereum Network:-
In order to participate in the Ethereum network, users need to have a wallet that supports the Ethereum protocol. This wallet allows users to send and receive Ether and other Ethereum-based tokens, as well as interact with smart contracts and dapps on the network. Users can interact with the Ethereum network using web-based wallets, hardware wallets, and software wallets.
0 notes
Text
Digitalisation, Risk and Resilience -Jon Hall, Patricia Lustig, Gill Ringland
This article is worthy for Australia to reflect in the post Optus cyber attack incident.
People are increasingly dependent on digital systems, and digitalization is clearly changing many aspects of life. Legal structures and other forms of regulation are lagging, as are many systems and processes. Take for example the proposal from the European Parliament that “In the long-term, the possibility of creating a specific legal status of “electronic persons” for the most sophisticated autonomous robots, so as to clarify responsibility in cases of damage, should also be considered” reflects concern over autonomous vehicles.
One particular aspect of the digital risk landscape is the issue of digital resilience -- the ability of digital systems to provide an ongoing service to users, and the risks that accompany it if our digital systems are not fit for purpose.
The authors estimate that the annual cost to the UK economy of software failure could be about £30 bn. This compares with cost of road accidents of about £15 billion. How does this cost manifest itself? It is a cost borne by organizations, the public and private sector, and individuals, rather than the software or hardware supplier.
It is manifested in one of three ways, which are qualitatively different:
Interruptions that cause minutes of disruption such as those that require restarting a program with few or no effects on data integrity, but inconvenience to the end user. These would not be tracked in the ICO framework;
System interruptions that halt operations for hours and involve significant repair and restoration costs, with costs to the organization and end user. These could be tracked in the ICO framework;
System collapse that requires substantial rebuilding of data or other system elements or that create substantial harm in other systems (such as power outages on an electrical grid). These would be tracked by the ICO framework.
The question we asked at the beginning – are digital systems fit for purpose – raises issues of system design, end user support as well as resilience, and increased risk. System design is the province of IT professionals. End user support is often the province of customer service or marketing. We think that resilience – the ability of digital systems to provide an ongoing service to users – will be of increasing utility to the board and owners of organizations, and to governments wishing to manage digital risks, as the economy tries to recover.
Source: Compass September 22-Association of Professional Futurist
0 notes
Text
Data breaches are costing more – what companies need to know
Data breaches are costing more – what companies need to know
The United States was the costliest country for an average total cost of a data breach for the 12th year running at $9.44 million, a 4.3% increase from 2021. Canada ranked third at $5.64 million, higher by 4.4% compared to last year.
Also in the top five was the Middle East, in second with $7.46 million. The UK and Germany rounded out the list, with $5.05 million and $4.85 million…
View On WordPress
0 notes
Text
Maintaining secure systems with expectations of flexible work
Maintaining secure systems with expectations of flexible work
Article by SailPoint APAC identity strategist, Gary Savarino.
Across New Zealand, there has been a significant shift in employee expectations when it comes to flexible working. Most office workers feel they’ve proved they can work successfully from home, and as much as employers try, things aren’t going back to the way they were anytime soon. With the world opening up and thousands of Kiwis…

View On WordPress
0 notes
Text
Attention Alert

Just logging in quickly to point out everyone needs to get something like Malwarebytes Anti-Malware or something just in case. Spread to people you know @deepspacebase @thesunnahthebetter @chilemango @sense-and-sensitivity @7amas1umblrspokesman @pottedfairies @jaquesmes @mun-akoon @siwar-fen @thecrownedgoddess @hila-monster @niqabisinparis @rasouli @livingmosaic @mithiyaan @whenplantingforests @greengrace @lilylived @sharksandlemons @naramdil @musicandthoughts @nearlyheadlesspeeves @el-shab-hussein @istandwithpalestine @bisan-is-trying @willow-al-najjar @huzni @opencommunion @ehud1564 @mhtyr @rabbigfirlee @holyfigtree @keepingtheflowersalive @kashmirichaiwithmehr @foreverrgrateful @decolonize-the-left @thefearnfaith @sailermoon @somethingaboutsomethingelse @palestiniansunset @palipunk @palestinianliberator @palestiniasim @mangokulfi @palestine-info-uncensored @storiesfromgaza @wearenotjustnumbers2 @the-palestinian-khalifa @baluchx. Try to spread the warning to be careful about what is clicked on, especially from the propaganda machine itself.
#tagged as many people I think may have/already clicked on it#spread the word#and be careful#keeping on top of things isn't without risk sometimes#cyber security
701 notes
·
View notes
Text
In today’s world of Alpha technologies, lot many are facing challenges to stay updated on these. The ambitious one’s are gearing up to learn and master these for their income. However, there are few who are trying to curb these as opportunities to cheat innocent learners.
The techniques are used to show big and deliver little becomes common. I see this as unethical and we shall have strong media practices to curb these goons.
What are potential channels to restrict it? Share here-
3 notes
·
View notes
Text
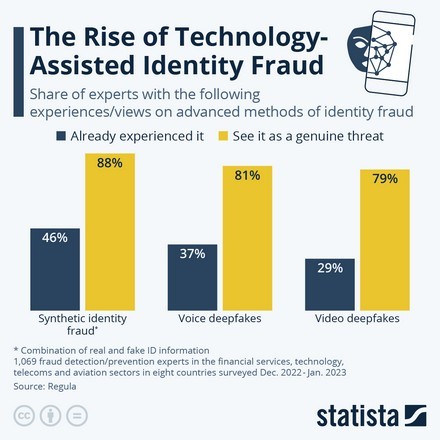
Απάτη στην εποχή του AI - Deep fakes και το αντίδοτο
Η λεγόμενη τεχνητή νοημοσύνη είναι ένα αμφιλεγόμενο θέμα για διάφορους λόγους, όπως ο χειρισμός των πνευματικών δικαιωμάτων, η χρήση ενέργειας, οι ανησυχίες σχετικά με το απόρρητο και τα chatbots όπως το ChatGPT που μερικές φορές δίνουν λανθασμένες απαντήσεις.
Continue reading Απάτη στην εποχή του AI – Deep fakes και το αντίδοτο
View On WordPress
0 notes
Text
The MSSP perspective: CISO insights into stronger security - CyberTalk
New Post has been published on https://thedigitalinsider.com/the-mssp-perspective-ciso-insights-into-stronger-security-cybertalk/
The MSSP perspective: CISO insights into stronger security - CyberTalk


Gary Landau has been leading IT and information security teams for over 25 years as part of startups as well as large global organizations. He is currently a Virtual Field CISO with Unisys Security Services, where he supports companies in many different industries. His mantra is “keep making it better” and he is passionate about continuously improving system reliability, performance, and security.
In this interview, Gary Landau unpacks valuable ideas, processes and solutions that can help businesses succeed in becoming more cyber secure. This is a fascinating read for any security professional eager to make an impact.
What are the most significant cyber security threats that your clients are currently facing?
The main cyber security threats most customers are worried about are AI and deepfakes. But where they really should be worried is around the basics — things like vulnerability management and credential protection.
As security protections have improved, I see more attacks around credentials — making credential protection and identity proofing more essential for our customers. There’s an adage that attackers don’t break in, they log-in. We’ve recently seen a lot more sophisticated fraud and credential-based attacks, especially due to improvements in AI.
We also see concerns about service desks needing to be more sophisticated in how they’re doing identity proofing, so that the service desks are not duped into resetting passwords for non-legitimate callers. In fact, a lot of organizations are starting to eliminate password resets by service desks altogether in favor of more sophisticated and automated identity proofing and password reset solutions.
Can you describe your customers? Is there a typical profile that you serve?
Our customers tend to be medium-to-large enterprises, and they can be in the public or private sector. There isn’t a single vertical that we focus on — we have customers from different industries. I’ve helped our customers in state and local governments and global enterprises — many different verticals. I’ve also spent recent years working with higher education institutions.
In your experience, what are the primary drivers that compel organizations to seek out MSSP services?
One unfortunate driver has been organizational breaches or attacks. Sadly, some organizations don’t realize that they need MSSP services like ours until after they are breached or have their business disrupted. In many cases, organizations aren’t benefiting or saving money by trying to manage all of their security in-house. In many instances, organizations have tools that they just don’t fully utilize because they don’t have the experienced nor trained staff to manage them. Also, maintaining the right staffing levels in-house can be challenging. In those cases, there is no advantage to keeping those services in-house. It becomes less expensive and more efficient to use an MSSP than to try and maintain that internal expertise. Plus, by using an MSSP, organizations have coverage even if their in-house staff turns over.
Can you walk us through your approach to assessing an organization’s cyber security needs and tailoring your services accordingly?
We have a three step approach, which starts with assessing the organization — and usually it’s based on some sort of security framework. I like the NIST frameworks, like NIST 800-53 and CSF. From the assessment we identify their security gaps and needs. We then propose and implement solutions to address those gaps. Lastly, we continually manage those solutions to make sure the security improvements are sustained. So, it’s an “assess,” “implement,” and “manage” approach.
How does your MSSP ensure the highest levels of security and compliance for clients across different industries, especially given differing regulatory requirements?
Since budgets typically aren’t unlimited, it’s about managing risk to an acceptable level for that organization. We recommend and strive to configure systems according to stringent security benchmarks, such as the NIST frameworks/standards or the CIS benchmarks. Then, irrespective if those benchmarks are for cloud environments or OS configuration settings, we will continuously improve those security settings for our clients to the point where we’re reaching 100% compliance with those recommendations.
Is it correct that cloud security is a specialty of Unisys?
It is. And it’s been a special focus of mine as well. Our focus is on helping businesses improve their services and a big driver is application modernization. What I mean by that is not just moving to the cloud, but modernizing their infrastructure, application processes, and security posture by refactoring legacy systems in the cloud. This helps make them more efficient while also making them more secure. Part of that security in the cloud is aided by our partnership with Check Point, which provides us with a CNAPP.
Could you share a bit about your partnership with Check Point and how that assists your enterprise?
Providing a comprehensive and effective solution requires people, processes and technologies. At Unisys, we have the skilled people and the effective processes, but we need a partner, Check Point, to provide that technology. It takes all three.
#ai#Application modernization#approach#assessment#attackers#benchmarking#benchmarks#budgets#Business#Check Point#CISO#CISO insights#Cloud#Cloud Security#CNAPP#Companies#compliance#comprehensive#credential#credentials#cyber#cyber risk#cyber security#deepfakes#education#enterprise#Experienced#Field CISO#focus#framework
0 notes
Text
There is diversification to be found within cyber cat bonds and ILS: CyberCube
New Post has been published on https://petn.ws/zbze1
There is diversification to be found within cyber cat bonds and ILS: CyberCube
CyberCube, a specialist modelling firm for cyber risks and exposures, has analysed the four 144A cyber catastrophe bonds that have been issued to date and found that there is diversification between them, which it says means these first deals provide a solid base for future innovation.Some $415 million in 144A cyber catastrophe bonds were issued […]
See full article at https://petn.ws/zbze1
#CatsNews #CatBond, #CatastropheBond, #CyberCatastropheBond, #CyberILSCyberInsuranceLinkedSecurities, #CyberInsurance, #CyberInsuranceLinkedSecurities, #CyberReinsurance, #CyberRisk, #InsuranceLinkedSecurities, #Reinsurance
#Cat bond#Catastrophe bond#Cyber catastrophe bond#Cyber ILS - Cyber Insurance-Linked Securities#cyber insurance#cyber insurance-linked securities#cyber reinsurance#cyber risk#Insurance linked securities#reinsurance#Cats News
0 notes
Text
NIGHTMARE IN SILVER WAS REALLY NICE. THEY MANAGED TO MAKE ME LIKE A CYBERMEN EPISODE???? IMPOSSIBLE
#wl26#dw log#like. cybermen actually felt formidable here.#and i know theyre SUPPOSED to be. but usually they just dont feel that way to me ya know#but this time it felt like there were real stakes#+ the risk of the doctor himself getting integrated was really cool#AND THE VISUALS OF HIM FIGHTING WITH THE CYBER PLANNER...#THE COLORS. THE USE OF SIDES N STUFF#VERY CLEVER#watch log
2 notes
·
View notes
Text
#assessment Small#Business asset protection#Business continuity#Business credibility#business finance#Business protection#Commercial insurance#Cyber insurance#Insurance advice#Insurance coverage#Insurance for entrepreneurs#Insurance policies#Insurance tips Risk#Legal requirements#Liability insurance#Professional liability#Property insurance#Risk management#Small business insurance#Worker's compensation
2 notes
·
View notes
Text
The Hive App turning out to be the Fyer Fest of social media 💀
10 notes
·
View notes
Text
Digital transformation has brought many benefits, but it also comes with cybersecurity risks.
Learn about the essential cybersecurity elements that can help you navigate digital transformation safely and protect your business from cyber threats.
Check out our latest article now!
3 notes
·
View notes