#crypto cyber security
Text
Buy virtual card with bitcoin
Buy virtual credit card with cryptocurrency
0 notes
Text
Coinbase, Circle, Kraken Unite Against Crypto Cyberthreats

Leading cryptocurrency exchanges Coinbase and Kraken, along with Circle, the issuer of the USDC stablecoin, have united to launch a Crypto Information Sharing and Analysis Center (Crypto ISAC). This groundbreaking organization is dedicated to enhancing blockchain cybersecurity, sharing vital information on cyber threats, and promoting collaboration among key industry players. This initiative marks a significant step in bolstering the security and credibility of the burgeoning cryptocurrency sector, particularly as it faces escalating threats from cybercriminals. CoinDesk’s Consensus 2024 event in Austin, Texas, will feature discussions with senior cybersecurity executives from these entities to illuminate the objectives and direction of Crypto ISAC.
Key Takeaways
Coinbase, Circle, and Kraken are spearheading a critical crypto security initiative.
The collaboration aims to improve digital asset protection across the industry.
Crypto ISAC is designed to facilitate real-time sharing of cyber threat information.
Consensus 2024 will provide a platform for discussing the initiative’s goals and strategies.
This effort underscores a unified approach to enhancing blockchain cybersecurity.
The initiative seeks to address the rising threat of cybercriminals targeting digital assets.
To Read More >>> Click Here
Reference Links:


#news#gold#silver#trendtracker360#tech news#technology#tech#technology news#economy#crypto#cryptocurrency#crypto news#coinbase#circle#kraken#crypto cyberthreats#circle alliance#partnership#crypto crime#crime prevention#crypto security alliance#cyber security#digital asset protection#online threat mitigation
0 notes
Text
Scam alert! Watch out for 401(k) scams - CyberTalk
New Post has been published on https://thedigitalinsider.com/scam-alert-watch-out-for-401k-scams-cybertalk/
Scam alert! Watch out for 401(k) scams - CyberTalk
EXECUTIVE SUMMARY:
Many fraudsters know that the real money is in retirement accounts.
In response to increased cyber security around other coveted targets (tax returns, credit cards…etc), cyber criminals have turned their attention elsewhere; to 401(k)s. A popular retirement savings plan in the United States, cyber criminals are boldly breaking into 401(k) accounts in order to illicitly aggregate wealth.
401(k) savings plans provide cyber criminals with access to hundreds, thousands or hundreds of thousands of dollars. The data security around retirement plans typically varies, as plans are managed by a combination of corporate stakeholders and financial groups.
401(k) phishing
In regards to 401(k) monetary theft, experts have warned of an uptick in phishing emails that target employee credentials.
These emails say that they’re from [your] corporate Human Resources group, and that there is a 401(k) plan update or new information about contributions that everyone should be aware of.
Because employees are sometimes eager to increase and protect retirement investments, it’s easy for people to fall prey to these scams.
The QR code element
Within the latest 401(k) phishing emails, experts have noted a surge in QR codes. The QR codes direct recipients to phony login pages that immediately pinch account credentials.
Image courtesy of Bleeping Computer.
401(k) scams and crypto
Recently, for employee investors, major 401(k) plan administrators began to offer cryptocurrency as an alternative investment asset.
Not all retirement plans offer crypto, but those that do and corresponding accounts could see a tsunami of new in cyber threats — especially phishing-related threats — due to the fact that cyber criminals often prefer to conduct business in cryptocurrency.
401(k) scam prevention
The duplicitous tactics outlined above underscore the need for organizations (and individuals) to proactively safeguard retirement accounts.
Leverage advanced anti-phishing technologies that can stop even the most sophisticated of phishing attacks
Implement a tool that can scan the links behind QR codes, such as Check Point’s Harmony Email & Collaboration technology
If your business outsources its HR operations, confirm and verify retirement account security protocols with the appropriate third-party
Teach employees about the need to keep tabs on emails, account statements and account activities
Inform employees about the importance of setting up two-factor authentication
Further information
In the U.S., federal laws and oversight endeavors attempt to protect employees from 401(k) scams. But they’re not adequate.
Ensure that your enterprise has the right cyber security in-place. Secure inbound and outbound emails with a top-of-line anti-phishing solution – Learn more here.
Related resources
Explore more of the latest cyber security trends – Read reports
Enhance your visibility into malicious QR codes – Here
Ensure the highest level of security for all of your employees – See details
#401(k) scams#401k scam#Accounts#amp#attention#authentication#Business#Check Point#code#Collaboration#computer#Credential theft#credentials#crypto#cryptocurrency#cyber#cyber criminals#cyber scams#cyber security#Cyber security trends#Cyber Threats#data#data protection#data security#details#easy#email#employee privacy#employees#enterprise
0 notes
Text
"Dive into the transformative world of blockchain technology. Explore its decentralized power, applications, and the future it shapes across industries."
#technology#tech#crypto#cyber security#new technology#foryou#fyp#fypシ#everyone#trendingtopics#blog#blogger
0 notes
Text
Safeguarding Against Rising Crypto Scams: The Power of Security, Education, and Regulation
As the popularity of cryptocurrencies continues to surge, so does the unfortunate rise in crypto scams. From fraudulent initial coin offerings (ICOs) to phishing attacks and Ponzi schemes, unsuspecting investors often fall victim to these malicious activities. However, by implementing robust security measures, promoting widespread education, and enforcing proper regulations, we can mitigate the…

View On WordPress
#2FA#Adoption#crypto#crypto regulation#Cryptocurrency#cyber security#decentralization#education#ICO#phishing attacks#ponzi scheme#Regulation#security
0 notes
Text
Tracking Cryptocurrencies & Bitcoin Transactions on The Blockchain

Bitcoin is a decentralized digital currency that uses blockchain technology to keep track of transactions. Bitcoin miners use complex mathematical problems to add blocks to the blockchain and receive rewards for their work in bitcoins. A Bitcoin wallet is needed to store, send and receive Bitcoins securely.
Blockchain technology allows users on the network access transparent data logs of all transactions made with cryptocurrencies such as Bitcoin, Ethereum & Tron.
The increased use of cryptocurrency has led to an increase in fraudulent activities of financial cyber security which can lead people into bankruptcy if they are not careful when investing or trading it online.
Read More
0 notes
Text
Bitcoin Core Developer Has Lost 200+ BTC In The Hack

Read More: Bitcoin Core Developer Has Lost 200+ BTC In The Hack
#Btc#bitcoin#cryptocurrency news#crypto#coding#programming#programmer#developer#hacking#hackers#security#cyber news#cybersecurity#cyberattack#hacker#Hack
1 note
·
View note
Text
IKEA shops hacked in Morocco, Kuwait, data leaks
The Vice Society ransomed the Swedish IKEA franchise chain in Morocco and Kuwait, and the hack disrupted operating systems.
Vice Society posted on its DarkWeb blog a sample of the hacked files, which contain business files and sensitive employee data such as passports, and the filenames also indicate that the actors obtained the data from the IKEA Jordan branch as well.
A statement from the chain of stores confirmed that the attack took place on Saturday, November 19, and is being investigated in cooperation with the relevant authorities and their partners in the field of cybersecurity, adding that IKEA Morocco and Kuwait are independently managed by a company holding the concession based in Kuwait.
Source

1 note
·
View note
Text
Buy virtual card with bitcoin
Buy virtual credit card with cryptocurrency
0 notes
Text
Paradigm leads $11.8M funding for Web3 wallet security supplier Blowfish
Paradigm leads $11.8M funding for Web3 wallet security supplier Blowfish
Web3 security organization Blowfish has brought $11.8 million up in a Series A funding round driven by Worldview.
Established in 2018, Blowfish is building a set-up of security items for the up-and-coming age of the web. The organization’s lead item is an instrument that assists engineers with getting their applications and savvy contracts.
With the new funding, Blowfish intends to grow its…

View On WordPress
#11m#blowfish#corporate taxes#filtering cyber security#local taxes#most secure crypto wallet#payroll taxes#security#social security and medicare are progressive taxes#web3#which event occurred as a result of general cornwallis&039;s surrender at the battle of yorktown
0 notes
Text
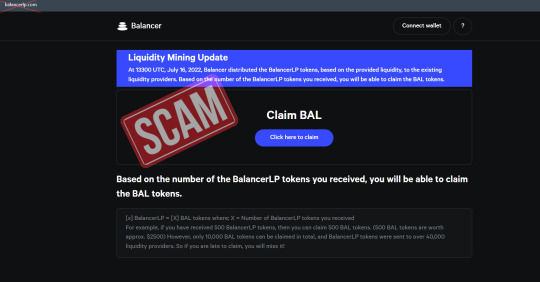
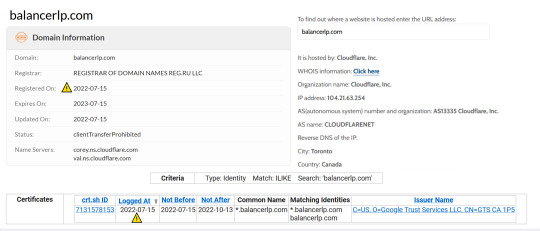
Balancer exchange fake airdrop - BalancerLP.com - SCAM!
There is a fake airdrop being prepared by threat actors, who are very persistent.
Saw attacks against 1inch, pancakeswap and uniswap so far. The uniswap attack resulted in more than 8 M worth of tokens stolen.
The scammers send tokens, with a bogus approval. If a user gets curios and tries to "redeem" their fake airdrop, they get their wallet's contents drained.
Remember, there is no airdrop. Be careful! (edited)
This is how the attack works:
Phisher airdropped malicious tokens to Balancer Labs LPs’ wallets. The name of the token directed users to a malicious interface that claimed the users could swap these tokens for BAL. (balancerlp.com is contained in the airdropped tokens). The scammers are well funded and burn about 100 ETH just for fees to spam!
The fake page generates a setApprovalForAll transaction, which, if approved by the user in their wallet, gave the attacker the ability to redeem all of the user’s BAL tokens for their full underlying value!!!
This is a good reminder for wallets and other interfaces to be vigilant about hiding spam and tokens with URLs in their name.
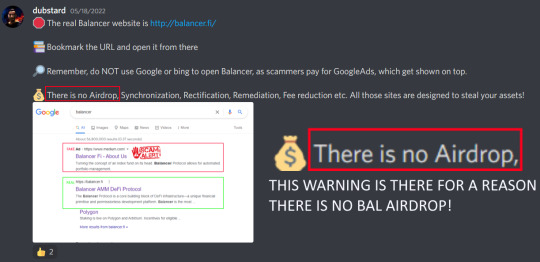
Balancer labs operates primarily under the domain http://balancer.fi/
Any "Airdrops" that direct you to unofficial domains are undoubtfully phishing attempts.
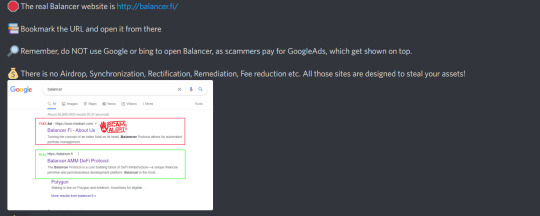
📚 The real Balancer website is http://balancer.fi/
📌 Bookmark the URL and open it from there
👀 Remember, do NOT use Google or bing to open Balancer, as scammers pay for GoogleAds, which get shown on top.
💸 There is no Airdrop, Synchronization, Rectification, Remediation, Fee reduction etc.
All those sites are designed to steal your assets!
Stay frosty!
#reg ru#balancer#balancer labs#balancer.fi#fake airdrop#crypto scam#spoofing#scam#phishing#spoof#cyber crime#crypto scams#security#scammers#fraud#fake
0 notes
Text
I keep having a giggle at Cyber Security Professor! Kick... Because it's such a stupid silly concept.

Has you practice social engineering by seeing how many SS numbers you can have people give you willingly through cold calls.
Has you watch episodes of Mr. Robot in class to critique the accuracies.
Gives all assignments through steganographic pictures.
Lists in his syllabus under course materials Tor & a VPN.
Uses Kali Linux and only Kali Linux.
"If purchasing isn't ownership, then piracy isn't theft."
Mines crypto on the school servers.
"I hate the textbook industry so that's why we're not using it."
Holds LAN parties for the upperclassmen in the CS lab.
Has a drawer full of rubber duckies he's confiscated from students. "I swear to God, you script kiddies are going to kill me."
Somehow doesn't get fired.
#BlackTacMopsi Writes Garbage#and then there's kick#call of duty kick#kick cod#call of duty ghosts#cod ghosts
48 notes
·
View notes
Note
AJ just published an article on Indonesia’s purchase of surveillance equipment from Israeli firms. Colonizers flock together.
https://x.com/AJEnglish/status/1786232982845476969
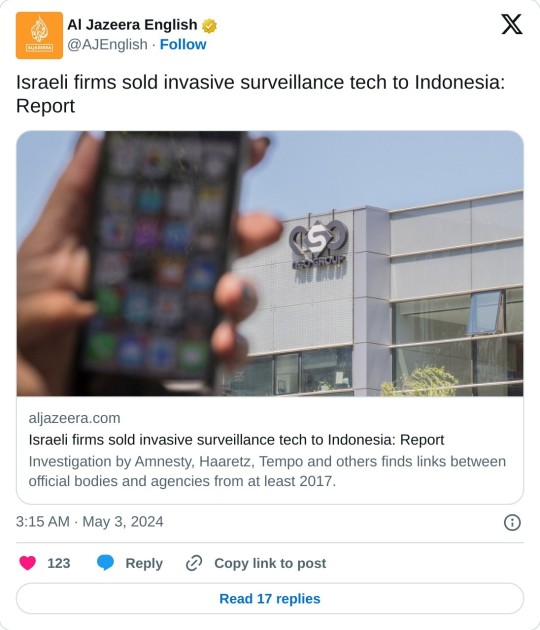
"The research by Amnesty International’s Security Lab – based on open sources including trade records, shipping data and internet scans – uncovered links between official government bodies and agencies in the Southeast Asian country and Israeli tech firms NSO, Candiru, Wintego and Intellexa, a consortium of linked firms originally founded by a former Israeli military officer, going back to at least 2017."
"Concerns about human rights have intensified in Indonesia since former general Prabowo Subianto was elected president in February at his third attempt. Prabowo, who will formally take office in October, has been accused of serious rights abuses in East Timor and West Papua, where Indigenous people have been fighting for independence from Indonesia since the 1960s. He denies the allegations against him."
"The report said it had discovered “numerous spyware imports or deployments between 2017 and 2023 by companies and state agencies in Indonesia, including the Indonesian National Police [Kepala Kepolisian Negara Republik] and the National Cyber and Crypto Agency [Badan Siber dan Sandi Negara]”.
The way these violent occupying forces are committing mass human rights violations, and the global community keeps turning away from it just astounds me. There HAS to been consequences to this. There just has to be.
#feminist#social justice#indonesia#defund israel#free west papua#west papua#human rights violations#free palestine#israel is a terrorist state#israel is a war criminal#israel is evil#current events#current news#al jazeera#al jazeera english#colonial violence#fuck colonialism#surveillance
23 notes
·
View notes
Text
On Christmas Eve, Ebeneezer Scrooge fell asleep in the server farm of his Cryptocurrency mine.
In the background, the soft wash of LED displays and gentle hum of cooling fans filled the basement. He'd recently expanded his operation, having gotten a great deal on hardware in the Cyber Monday sales. So he was sung to sleep by the gentle guzzling of electricity and the slow accumulation of what might (by some) be considered wealth.
Throughout the long night, he was visited by three ghosts. The whole business played out more or less as you'd expect, so we won't overly dwell on it here.
Where things really started to go FUBAR was when Scrooge awoke…
Looking out the security cameras on the snowy morning, Scrooge spied an urchin child. He pressed the buzzer on the speaker and cried out to them!
"You, boy! What day is it?"
"What? I can't hear you."
"Hold on, I'll come upstairs!"
Scrooge ran up the dingy stairwell of his minimalist and kinda grungy compound, stopping only to disarm his top of the line security system. He stepped out into the brisk winter, and very nearly forgot to reset the alarm in his excitement. Then he remembered he had prime numbers in there, damn it! So he did reset the primary alarm, but didn't bother with the non-lethal countermeasures, and that was something at least.
"Thanks for waiting!" He huffed. "So, boy … what day is it?"
"Not a boy!" Came the shrill reply.
"Girl, then! What day is it?"
"Not that either!"
"Look, kid, this isn't a game of what's your fucking gender. Just tell me what day it is!"
"It's solstice day, sir!" Said the urchin, looking up at a dishevelled Scrooge with their big urchin eyes.
"Wait, really? …You're sure it's not Christmas? I fell asleep on Christmas Eve…"
"I guess you slept for near a year, then, ‘cos I celebrate solstice and it's the gods-damned solstice."
“I don’t know how to process that!” Cried Scrooge.
“Maybe there’s a specific detail you can focus on to ground you?” Suggested the urchin, in a surprisingly helpful bit of trauma advice.
“OH!” Exclaimed Scrooge. “Tell me, child, the butcher’s nearby. Does it still have that big turkey in the window?”
“The butcher’s closed down six months back, I’m afraid! But I think there’s an Amazon Fresh around here somewhere?” Said the urchin.
“That’ll do!” Scrooge rummaged around in his pockets. “Here, take this printout of a Jpeg of a poorly drawn frog and go buy me the biggest turkey you can find in Amazon Fresh. Then deliver it to Bob Cratchet!”
“Even Amazon won’t take your NFT bullshit as currency, mister!”
“Okay - I can give you cash.” Scrooge paused for a moment. “Do you have Venmo?”
“I’m a street urchin.” Replied the street urchin. “Of course I have Venmo.”
“Great. I’ll transfer you now - keep the change.”
“I don’t mean to look a gift crypto bro in the mouth, sir, but aren’t you famously stingy? Like, your name’s literally a synonym for tight-fisted penny-pinching.”
“That’s the old Scrooge. I got visited by three ghosts last night and now I’m a new man.” Said Scrooge, proudly, before added conspiratorially, “At first, I thought I’d just drank a bad batch of Soylent. But they were pretty convincing in the end.”
“So you’re going to donate all your money to charity or start a non-profit or something?” The urchin said with open-mouthed awe.
"I don't know. It's kind of ambiguous. I might do those things, or maybe I'll keep being rich and be a bit nicer?
"Okay, so now you're closer to a Bill Gates rather than full Musk/Bezos on the scale of evil billionaires.” The urchin looked directly into the camera for a full three seconds. “And we’re supposed to celebrate that?
“Look, it was pretty fucking radical for its time, okay?” Said Scrooge, snapping his fingers to stop the urchin breaking the fourth wall any further. “Are you gonna buy the turkey or what?"
“I dunno, man. On the one hand, it feels like if you really changed your tune, you’d do more than buy one turkey for the single poor person whose name you know. On the other hand, you said I could keep the change. So this really is a bind for me…”
“If I’m honest,” Said Scrooge, “I really didn’t think it would be this difficult to be charitable. No wonder Elon is the way he is.”
“Sigh.” Said the urchin. Saying the word out loud, rather than just sighing, which I think tells you something about the level of frustration here. “You know what, this isn’t gonna work.”
“Huh?” Said Scrooge, somewhat nonplussed.
“Spot! Here, boys! Heel!” Called the urchin.
In the distance, a low rumbling growl could be heard. Out of the shadows of the misty winter morning, a giant three-headed hound emerged, its jaws snapping at Scrooge in triplicate.
“AAAARGH!” Yelled Scrooge, now so nonplussed as to be minused.
The urchin pulled out a matte black flip phone, decorated with a few tasteful flowers, and made a call.
“Hi Persephone, it’s me, Charon.” Said the urchin. “Yeah, I’m up here on psychopomp duty. Yup, it’s the Ebeneezer Scrooge case - y’know, the tech bro who drank too much Red Bull and had a heart attack? Well, we gave him another shot this year, but he’s still a bit of a dickmagnet. He’s made some progress - he understands basic empathy - but we’re still a bit stuck on the ‘myth of the benevolent billionaire’ stage.”
In the background, the sound of screaming tech-bro and snarling monster dogs was fading into the distance.
“I think we’re gonna call it for the day and give it another try solstice.” Charon continued. “Yeah, Cerberus is dragging him back to the underworld now. Yeah - he did a great job as the three ghosts too - definitely earned a treat. Cool - see you in a few.”
Charon flipped the phone closed and took a deep breath. They took a pair of bronze coins out of a pocket of their ragged hoody, and placed them gently over their own eyes.
“Hades bless us. Everyone.” They said to no-one, then disappeared.
#writing#short story#a christmas carol#dickens#mythology twist#honestly a christmas carol is excellent and really quite radical#this just felt like a fun update#and i think a lot of the radical-ness of Dickens' writing gets lost in the twee
147 notes
·
View notes
Text
Two months ago, Lin Rui-siang, a young Taiwanese man wearing black-rimmed glasses and a white polo shirt, stood behind a lectern emblazoned with the crest of the St. Lucia police, giving a presentation titled “Cyber Crime and Cryptocurrency” in nearly fluent English to a roomful of cops from the tiny Caribbean country.
The St. Lucia government would later issue a press release lauding the success of Lin's training course, which had been organized by the Taiwanese embassy, where Lin worked as a diplomatic specialist in IT. The statement boasted that 30 officers had learned “nuances of the dark web" and cryptocurrency tracing skills from Lin, who had “used his professional background and qualifications in the field" to teach them how to better combat cybercrime.
Only earlier this week did it become clear exactly what Lin's “professional background and qualifications in the field” allegedly entailed, seemingly unbeknownst to either his Taiwanese employers or his St. Lucian law enforcement trainees. For nearly four years, according to the US Justice Department, 23-year-old Lin ran a dark-web drug market called Incognito that authorities say enabled the sale of at least $100 million worth of narcotics, ranging from MDMA to heroin for cryptocurrencies including bitcoin and monero. That was before Lin's alleged theft of his own users' funds earlier this year and then his arrest last week by the FBI in New York's JFK airport.
Over his years working as a cryptocurrency-focused intern at Cathay Financial Holdings in Taipei and then as a young IT staffer at St. Lucia's Taiwanese embassy, Lin allegedly lived a double life as a dark-web figure who called himself “Pharoah" or “faro”—a persona whose track record qualifies as remarkably strange and contradictory even for the dark web, where secret lives are standard issue. In his short career, Pharoah launched Incognito, built it into a popular crypto black market with some of the dark web's better safety and security features, then abruptly stole the funds of the market's customers and drug dealers in a so-called “exit scam” and, in a particularly malicious new twist, extorted those users with threats of releasing their transaction details.
During those same busy years, Pharoah also launched a web service called Antinalysis, designed to defeat crypto money laundering countermeasures—only for Lin, who prosecutors say controlled that Pharoah persona, to later refashion himself as a crypto-focused law enforcement trainer. Finally, despite his supposed expertise in cryptocurrency tracing and digital privacy, it was Lin's own relatively sloppy money trails that, the DOJ claims, helped the FBI to trace his real identity.
Among all those incongruities, though, it's the image of Lin giving his cryptocurrency crime training in St. Lucia—which Lin proudly posted to his LinkedIn account—that shocked Tom Robinson, a cofounder of the blockchain analysis firm Elliptic, who has long tracked Lin's alleged Pharoah alter ego. “This is an alleged dark-net market admin standing in front of police officers, showing them how to use blockchain analytics tools to track down criminals online,” says Robinson. “Assuming he is who the FBI says he is, it's incredibly ironic and brazen.”
Pharoah the Kingpin—and Extortionist
Lin has been charged with not only narcotics conspiracy and money laundering but also running a “continuing criminal enterprise,” the so-called “kingpin statute” reserved for organized crime leaders who allegedly oversaw at least five employees. For that charge alone, he faces a potential life sentence.
In the DOJ's criminal complaint against Lin, it points to a handwritten document the FBI pulled from his email, which appears to sketch out a flow chart for a dark-web market's mechanics. The complaint's FBI affidavit says Lin emailed himself the sketch in March 2020 when he was at most 19 years old. It describes functionality such as how “vendors” and “buyers” would register, make purchases, and encrypt shipping addresses. Seven months later, Lin would allegedly launch Incognito Market.
According to the FBI, the market took nearly a year to catch on, with virtually no sales during that time. But by late 2021, Incognito had started to attract users, and by the middle of 2022, the market had drawn enough vendors and sellers to generate more than $1.5 million a month in sales.
A 2022 Twitter thread about Incognito posted by Eileen Ormsby, an author of several dark-web-focused books including The Darkest Web, shows how the market by that time had added features that may have helped it to catch the attention of security- and safety-conscious users. It required that new users demonstrate they could use the encryption tool PGP before entering the market, prompted them to take a security quiz, allowed buyers to spend the more privacy-focused cryptocurrency monero as well as bitcoin, encouraged dealers to post results from a fentanyl test to certify their product was “fent free,” and even experimented with democratic voting for market-wide decisions.
By the summer of 2023, Incognito had spiked in popularity and was approaching $5 million a month in sales. Then in March of this year, the site suddenly dropped offline, taking all the funds stored in buyers' and sellers' wallets with it. A few days later, the site reappeared with a new message on its homepage. “Expecting to hear the last of us yet?” it read. “We got one final little nasty surprise for y'all.”
The message explained that Incognito was now essentially blackmailing its former users: It had stored their messages and transaction records, it said, and added that it would be creating a “whitelist portal” where users could pay a fee—which for some dealers would later be set as high as $20,000—to remove their data before all the incriminating information was leaked online at the end of this month. “YES THIS IS AN EXTORTION!!!” the message added.
In retrospect, Ormsby says that the site's apparent user-friendliness and its security features were perhaps a multiyear con laying the groundwork for its endgame, a kind of user extortion never seen before in dark-web drug markets. “Maybe the whole thing was set up to create a false sense of security,” Ormsby says. “The extorting thing is completely new to me. But if you've lulled people into a sense of security, I guess it's easier to extort them.”
In total, Incognito Market promised to leak more than half a million drug transaction records if buyers and sellers didn't pay to remove them from the data dump. It's still not clear whether the market's administrator—Lin, according to prosecutors, whom they accuse of personally carrying out the extortion campaign—planned to follow through on the threat: He appears to have been arrested before the deadline set for the victims of the Incognito blackmail.
An Expert in ‘Anti Anti-Money Laundering’
At the same time the FBI says Lin was laying the groundwork for this double-cross, he also appears to have briefly tried engineering an entirely different scheme. In the summer of 2021, during Incognito Market's relatively quiet first year, Lin's alleged alter ego, Pharoah, launched a service called Antinalysis, a website designed to analyze blockchains and let users check—for a fee—whether their cryptocurrency could be connected to criminal transactions.
In a post to the dark-web market forum Dread, Pharoah made clear that Antinalysis was designed not to help anti-money-laundering investigators, but rather those who sought to evade them—presumably including his own dark-web market's users. “Our goals do not lie in aiding the surveillance autocracy of state-sponsored agencies,” Pharoah's post read. “This service is dedicated to individuals that have the need to possess complete privacy on the blockchain, offering a perspective from the opponent's point of view in order for the user to comprehend the possibility of his/her funds getting flagged down under autocratic illegal charges.”
After independent cybersecurity reporter Brian Krebs wrote about the Antinalysis service in August 2021, describing it as an “anti anti-money laundering service for crooks,” Pharoah posted another message complaining that Antinalysis had lost access to its blockchain data source, which Krebs had identified as the anti-money-laundering tool AMLBot, and that it would be going offline. “Stay posted and fuck LE," Pharoah wrote, using the abbreviation LE to mean “law enforcement.” Antinalysis eventually returned, however, and pivoted last year to acting instead as a service for swapping bitcoin for monero and vice versa.
Meanwhile, Lin appears to have maintained his obsession with cryptocurrency tracing and blockchain analysis: His final LinkedIn post last week before his arrest in New York announced that he had become a certified user of Reactor, the crypto tracing tool sold by blockchain analysis firm Chainalysis. “I'm excited to share that I've completed Chainalysis's new qualification: Chainalysis Reactor Certification (CRC)!” Lin wrote in Mandarin. His last X post shows a Chainalysis diagram of money flows between dark-web markets and cryptocurrency exchanges.
It's not clear whether Lin obtained his Chainalysis certification to bolster a new career training law enforcement in blockchain analysis or, if US prosecutors are to be believed, to advance his previous alleged career as a dark-web criminal. But it raises the troubling possibility that a former dark-web kingpin—one who was still extorting his own users—was perhaps playing both sides of the crypto tracing game, says Elliptic's Tom Robinson.
“There’s a larger issue here about bad actors accessing blockchain analytics tools,” says Robinson. “That is a potentially risky situation, where someone who’s in the process of laundering proceeds of crime can check in commercially available tools whether they have laundered them such that they can get away with it.” Running certain checks in those tools might even allow someone to determine if they're being actively investigated by law enforcement, Robinson says.
WIRED reached out to Chainalysis to ask about Lin's Reactor certification and what sort of safeguards prevent criminals from using the company's software, but the company declined to comment.
If Lin did hope to evade law enforcement by becoming an expert in crypto tracing himself, he was far too late to avoid creating his own blockchain trail of evidence: In January of this year, the FBI says it somehow identified a central Incognito server and obtained a search warrant for its contents. That allowed investigators to identify a bitcoin wallet stored there, which the FBI says Lin had also carelessly used to pay web registrar Namecheap for four web domains—including one that tracked which dark-web markets were online or down—and register them under his own name.
Although the FBI says Lin tried to swap his bitcoins for harder-to-trace monero before cashing out the cryptocurrency at an exchange, the criminal complaint points to timing and amount correlations that nonetheless allowed the FBI to follow his funds to a crypto exchange where he allegedly liquidated the dirty funds. That exchange account, too, was registered in Lin's real name, according to the DOJ.
The operational security mistakes the FBI describes suggest that, regardless of which side of the cryptocurrency cat-and-mouse game Lin intended to end up on, he was far from a criminal mastermind. His brief, strange journey from alleged kingpin to crypto crime expert ultimately provides plenty of lessons to criminals and law enforcement alike—though probably not the ones he intended.
6 notes
·
View notes
Text
Cybersecurity Giant Zscaler Investigates Alleged Data Breach

UPDATE - Zscaler reiterates no impact or compromise to customers, production, or corporate environments. Zscaler and an independent third-party incident response firm continue to work on forensics analysis of the quarantined test environment.
Cybersecurity powerhouse Zscaler launched an investigation on Wednesday after a notorious hacker, known as IntelBroker, announced on a popular cybercrime forum that they were "selling access to one of the largest cyber security companies". Although the hacker's post did not explicitly name the company, they later confirmed in the forum's shoutbox that the target was Zscaler.
IntelBroker has offered to sell "confidential and highly critical logs packed with credentials", including SMTP access, PAuth access, and SSL passkeys and certificates, for $20,000 in crypto. This alarming claim has raised concerns about the potential severity of the alleged breach.
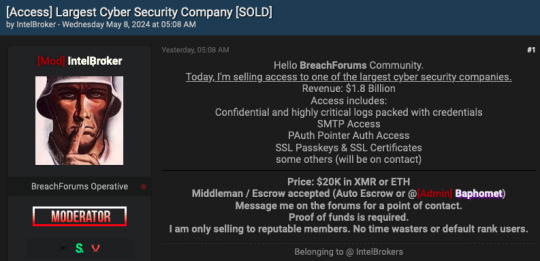
Zscaler's Initial Response and Investigation
Upon learning about the hacker's claims, Zscaler promptly announced the launch of an investigation. A few hours after the investigation commenced, the company announced that it had found no evidence of its customer and production environments being compromised.
Update on Investigation Findings
In its latest update, Zscaler confirmed that its production, customer, and corporate environments were not impacted. The company stated, "Our investigation discovered an isolated test environment on a single server (without any customer data) which was exposed to the internet. The test environment was not hosted on Zscaler infrastructure and had no connectivity to Zscaler's environments. The test environment was taken offline for forensic analysis."
IntelBroker's Recent Claims and Track Record
IntelBroker recently claimed to have stolen US State Department and other government data from the tech firm Acuity. While Acuity confirmed a breach, the company stated that only non-sensitive, old information was compromised. IntelBroker has been making claims about obtaining US government data for more than a year. In several cases, the data has been confirmed to come from third-party service providers, but in some instances, the data was allegedly obtained directly from government systems. However, some of the hacker's claims seemed false or exaggerated.
Read the full article
2 notes
·
View notes