#Internet Security Software
Text
I am currently coding a browser right now in pure Python. Let me explain all the steps it has taken at 300+ lines of code except in no particular order because I need to reorganize.
Fernet Encryption
SSL Certificate Check
Implementing a UI - Chose PyQt because its a prettier layout than Tkinter.
Implementing a toolbar for the UI
Implementing browsing history + browsing history tab + a clear button to clear the history - Done in the GUI / UI as well.
Adding a privacy browsing mechanism - routed through Tor
Added PyBlocker for Ad Blocking and Anti-Tracking on websites
Added a feature to make Google not track your searches because fuck you Google you nosey assholes.
Added a sandbox to avoid user getting infected with viruses
Added additional functionalities including optimization that way the browser wasn't slow as fuck:
Using JavaScript v 8 engine to load JavaScript
Using slight mem caching <100mb to avoid slowing the computer but also let the program browse quicker
Using one http request to send multiple http requests - need to set limit.
Encrypted global security features.
I am at over 300 lines of code. I am ready to pay someone to debug this shit when I am finished with it (lol)
May the force be with you my #Pythonistas
#Python3#pythoncode#coding#programming#programmer#javascript#encryption#cryptography#cybersecurity#internet security#internet#web browsers#web browser history#adblock#ux#ui#gui#development#software development#software developer#devlog#developer log
133 notes
·
View notes
Text
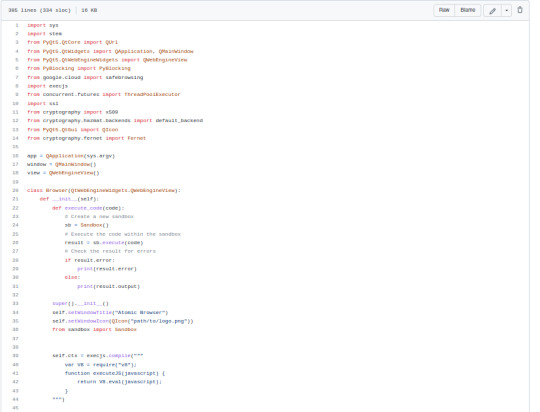
I work in cyber security. While I agree that getting a VPN is a good idea, most people have misconceptions about it. I am here to dumb down as much as I can how a VPN works and undo some of the misconceptions.
The way your internet works usually is “Device —> Modem —> ISP —> Servers of the place you are trying to reach”. Now, your Device sends a request which is then enhanced by your modem and sent off to your ISP.
Basically, your computer makes & packs the package and adds the sender info (local ip, mac adress, etc) and the recepient info (the server where the request needs to be delivered to). Your modem then adds some other sender info such as your IP and then send it off to the ISP. Your ISP will then keep a copy of the package (request) and send the original to the recipient server. Now, if the tech team of the company did not fuck up and used https, the contents of the package itself should be encrypted, meaning that the ISP can’t see what you see, can’t see the password that you typed in, etc. and the package should be figuratively closed. They should only be able to see the sender and recipient information alongside all the other identifying info. Now, if the tech tram *did* fuck up and used http, your ISP can see the contents of the website you are visiting, can see the password that you entered, etc. and the package is figuratively left open and anyone can look in and see you know, the password you entered and stuff.
Now also, there could be someone in between your devices and your modem like this “Device —> Middle Man —> Modem —> ISP —> Servers of the place you are trying to reach”, the middle man will be able to read the same info as the ISP but that’s besides the point right now.
What a VPN does is, that it encrypts the request and puts it into a different request that is headed to the VPN’s servers. The request’s pathway will look something like this “Device (encrypted by a VPN) —> Modem —> ISP —> Servers of VPN (here the request is decrypted) —> Servers of the place you are trying to reach“. Using figuratively language, the VPN put your package inside another box, another package which is closed. So no-one can see the recipient & sender information of the original package, and if the original package was open no-one can see what is inside of that package. So the outer box/package now heads to the VPN’s servers, and once it arrives there, the VPN’s servers will unpack the outer box/package and send the original package to the original recipient
Now let’s point out some key points.
1. The VPN essentially becomes your ISP, it can read the request as if the encryption never existed.
2. By this complicated process, the IP from which you are sending the request changes to the IP of the VPN’s server.
3. Your ISP CAN NOT read your requests most of the time even without a VPN. If your browser has a lock icon next to the search bar, your requests are already encrypted, the website is using https, and the box is closed.
4. The only thing a VPN does, is make it seem like your requests are coming from a different IP, hides the original recipient info from your ISP & Man in the Middle attacks, hides the original sender information from the recipient server, and encrypts the contents… again. NOTHING MORE NOTHING LESS. If a VPN does something more (such as ad-blocking) they will advertise it separately, it is not a thing that comes by default.
Wrote this at 1AM on my phone in bed as a non-native English speaker. Sorry fir the bad grammar.
#vpn#vpn security#vpn software#vpn service#cybersecurity#internet#misconceptions#thought you should know#helpful#tech#security#privacy#internet security#internet privacy
66 notes
·
View notes
Text
90% of hacking is scanning to see if someone misconfigured their security settings or if they’re using out of date software
9% is social engineering
And the last 1% is actually trying to find an exploit and write your own code (idk how to do this part yet)
#Friendly reminder to patch your software friends. Also. Don’t connect pc with an old OS to the internet.#It’s so funny it’s just like. *pokes you and sniffs finger* hmm yes you smell like windows 7#*pokes again* I see you have these ports open. You’re probably using this software.#*pokes again* oh would you look at theres 5 FuckYouDie exploits discovered in 2013 that I can use#And then you just type some words to run a script someone smarter than you wrote and now you have access#It’s easier than you think. Just 1 mistake that reveals too much info can lead to a whole mess#Well the script writing part probably isn’t easy but idk I’m not a security researcher don’t ask me about that#I am just learning to hopefully get a better job#And I have come to the conclusion that the only way to be safe is to have 0 electronic devices lol#I mean the average person is ‘safe’ simply because it’s not profitable to target a complete nobody directly#the biggest threat to individual people are data breaches and scammers#and a lack of common sense. don’t download random files. don’t click links in emails. the usual
2 notes
·
View notes
Text
PLEASE SUBSCRIBE TO MY YOUTUBE CHANNEL: https://tinyurl.com/a6fts8j8
#seniorsguidetocomputers#seniors#computers#computertraining#computertutorials#computerlessons#beginners#software#hardware#internet#security#cybersecurity#email
2 notes
·
View notes
Text

On Safer Internet Day, let us understand the importance of internet safety and not take it lightly.
.
.
#codeblendlabs#saferinternetday#onlinesafety#internetsafety#saferinternet#security#internet#datasafety#cybersecurity#webdevelopment#technology#programming#privacy#coding#graphicsdesigning#softwareengineer#tech#software#digitalmarketing#webdeveloper
6 notes
·
View notes
Text
#seo services#web development#social media marketing#consulting#website maintenance#ecommerce#Cloud Solutions#Networking Solutions#Software Define Networking#Data Centre#Virtualization Services#Internet of Things#Security Solutions#IT managed services#Network Architecture Design & Implementation#IT Facilities Managed Services#Annual Maintenance Contract#Relocation Migration Plan & Implementation
3 notes
·
View notes
Text
Man inflation is hitting everyone pretty hard.
#haha#lol#meme#funny#technology#web development#internet security#software engineer#cloud infrastructure#information technology
5 notes
·
View notes
Text
How to prevent Hackers from infiltrating your Network
A computer network is a group of interconnected nodes that are capable of transmitting and receive data. Nodes here are referred to as any physical device in a network that can receive data and forward information.

People often mistake computer as “just” a desktop/monitor/PC/laptop — computer is any device that can run a program, manipulate data, store information, such as a phones, cameras, tablets or smart sensors etc.
The most common types of networks are; point-to-point network, local area network (LAN), wireless local area network (WLAN), wide area network (WAN) , metropolitan area network (MAN).
The easiest kind of network to set up is the Point-to-point network. This network securely connects two nodes together using layer 2 data connection, therefore creating a closed network. Here, data travels privately and not over the public internet where data could easily be intercepted by hackers.
How can a hacker sneak into your network?
The truth is since the beginning of the internet, the issue of internet hackers cybercrime has a been a major concern for everybody from individuals to companies, business and even government organizations. With the rise in crimes committed via the internet its no surprise that business professional have to adopt a secure line of defense against hackers. The first step in preparing a secure system or network is understanding how these cybercriminals operate.
We definitely cannot evade development in technology and this means that hackers become more crafty and savvy in carrying out their attacks --on constant research to find ways to gain unauthorized access into secure networks.

Let us take a look at a few ways a hacker can get into a network;
Free software: this is perhaps on of the easiest ways for hackers to gain access into secures networks. They exploit a flaw in people --unwilling to pay for software and always looking for an alternative free software to perform the task they intend to carry out. A hacker can easily install a backdoor into a legitimate application and gain access into your networks
Phishing scams: in this kind attack, hackers target people by sending emails that may seem to come from a legitimate or trusted source. The email contains content telling victims to click an infected link that redirects them a download page to download a malware or even a login page the hacker has set up to phish for the victims details. Once this data has been handed over to the hacker, they can further infiltrate the network.
Internet protocol(IP) addresses: By using several tools and search engines to constantly scan millions of IP addresses, hackers wait until they can find a weak and vulnerable IP address they can uses to make a remote connection to a system within your homes or businesses.

Now that we know a few ways in which hackers can infiltrate networks, we can take a look at how to remain alert and a step ahead of hackers.
Staff awareness training and seminars: the most common line of defense against phishing email scams is to educate and inform employees. It should be a priority for the security team to organize seminars to educate individuals within a company on the signs to look out for and how they should respond.
Use secure passwords: We should never rely on default passwords. Most times, a hacker would try to brute force accounts using a wordlist of passwords commonly used. It is always a good idea to also regularly update passwords so as to make it more difficult for hackers to easily get access.
Reduce attack surface: attack surface refers to the entry points an unauthorized user can use to extract information or even input data. Regular scanning should be carried out to spot potential entry points. Unnecessary services and software could provide an attack surface for hackers.
Avoid free software: as tempting as it may sound, free and cracked software provides a means for hackers to gain access into your network. This software may likely open up your network, leaving you vulnerable to certain kinds of attacks.
Articles by ikwumonu Daniel (Cyclobold)
2 notes
·
View notes
Text
If anyone wants to know why every tech company in the world right now is clamoring for AI like drowned rats scrabbling to board a ship, I decided to make a post to explain what's happening.
(Disclaimer to start: I'm a software engineer who's been employed full time since 2018. I am not a historian nor an overconfident Youtube essayist, so this post is my working knowledge of what I see around me and the logical bridges between pieces.)
Okay anyway. The explanation starts further back than what's going on now. I'm gonna start with the year 2000. The Dot Com Bubble just spectacularly burst. The model of "we get the users first, we learn how to profit off them later" went out in a no-money-having bang (remember this, it will be relevant later). A lot of money was lost. A lot of people ended up out of a job. A lot of startup companies went under. Investors left with a sour taste in their mouth and, in general, investment in the internet stayed pretty cooled for that decade. This was, in my opinion, very good for the internet as it was an era not suffocating under the grip of mega-corporation oligarchs and was, instead, filled with Club Penguin and I Can Haz Cheezburger websites.
Then around the 2010-2012 years, a few things happened. Interest rates got low, and then lower. Facebook got huge. The iPhone took off. And suddenly there was a huge new potential market of internet users and phone-havers, and the cheap money was available to start backing new tech startup companies trying to hop on this opportunity. Companies like Uber, Netflix, and Amazon either started in this time, or hit their ramp-up in these years by shifting focus to the internet and apps.
Now, every start-up tech company dreaming of being the next big thing has one thing in common: they need to start off by getting themselves massively in debt. Because before you can turn a profit you need to first spend money on employees and spend money on equipment and spend money on data centers and spend money on advertising and spend money on scale and and and
But also, everyone wants to be on the ship for The Next Big Thing that takes off to the moon.
So there is a mutual interest between new tech companies, and venture capitalists who are willing to invest $$$ into said new tech companies. Because if the venture capitalists can identify a prize pig and get in early, that money could come back to them 100-fold or 1,000-fold. In fact it hardly matters if they invest in 10 or 20 total bust projects along the way to find that unicorn.
But also, becoming profitable takes time. And that might mean being in debt for a long long time before that rocket ship takes off to make everyone onboard a gazzilionaire.
But luckily, for tech startup bros and venture capitalists, being in debt in the 2010's was cheap, and it only got cheaper between 2010 and 2020. If people could secure loans for ~3% or 4% annual interest, well then a $100,000 loan only really costs $3,000 of interest a year to keep afloat. And if inflation is higher than that or at least similar, you're still beating the system.
So from 2010 through early 2022, times were good for tech companies. Startups could take off with massive growth, showing massive potential for something, and venture capitalists would throw infinite money at them in the hopes of pegging just one winner who will take off. And supporting the struggling investments or the long-haulers remained pretty cheap to keep funding.
You hear constantly about "Such and such app has 10-bazillion users gained over the last 10 years and has never once been profitable", yet the thing keeps chugging along because the investors backing it aren't stressed about the immediate future, and are still banking on that "eventually" when it learns how to really monetize its users and turn that profit.
The pandemic in 2020 took a magnifying-glass-in-the-sun effect to this, as EVERYTHING was forcibly turned online which pumped a ton of money and workers into tech investment. Simultaneously, money got really REALLY cheap, bottoming out with historic lows for interest rates.
Then the tide changed with the massive inflation that struck late 2021. Because this all-gas no-brakes state of things was also contributing to off-the-rails inflation (along with your standard-fare greedflation and price gouging, given the extremely convenient excuses of pandemic hardships and supply chain issues). The federal reserve whipped out interest rate hikes to try to curb this huge inflation, which is like a fire extinguisher dousing and suffocating your really-cool, actively-on-fire party where everyone else is burning but you're in the pool. And then they did this more, and then more. And the financial climate followed suit. And suddenly money was not cheap anymore, and new loans became expensive, because loans that used to compound at 2% a year are now compounding at 7 or 8% which, in the language of compounding, is a HUGE difference. A $100,000 loan at a 2% interest rate, if not repaid a single cent in 10 years, accrues to $121,899. A $100,000 loan at an 8% interest rate, if not repaid a single cent in 10 years, more than doubles to $215,892.
Now it is scary and risky to throw money at "could eventually be profitable" tech companies. Now investors are watching companies burn through their current funding and, when the companies come back asking for more, investors are tightening their coin purses instead. The bill is coming due. The free money is drying up and companies are under compounding pressure to produce a profit for their waiting investors who are now done waiting.
You get enshittification. You get quality going down and price going up. You get "now that you're a captive audience here, we're forcing ads or we're forcing subscriptions on you." Don't get me wrong, the plan was ALWAYS to monetize the users. It's just that it's come earlier than expected, with way more feet-to-the-fire than these companies were expecting. ESPECIALLY with Wall Street as the other factor in funding (public) companies, where Wall Street exhibits roughly the same temperament as a baby screaming crying upset that it's soiled its own diaper (maybe that's too mean a comparison to babies), and now companies are being put through the wringer for anything LESS than infinite growth that Wall Street demands of them.
Internal to the tech industry, you get MASSIVE wide-spread layoffs. You get an industry that used to be easy to land multiple job offers shriveling up and leaving recent graduates in a desperately awful situation where no company is hiring and the market is flooded with laid-off workers trying to get back on their feet.
Because those coin-purse-clutching investors DO love virtue-signaling efforts from companies that say "See! We're not being frivolous with your money! We only spend on the essentials." And this is true even for MASSIVE, PROFITABLE companies, because those companies' value is based on the Rich Person Feeling Graph (their stock) rather than the literal profit money. A company making a genuine gazillion dollars a year still tears through layoffs and freezes hiring and removes the free batteries from the printer room (totally not speaking from experience, surely) because the investors LOVE when you cut costs and take away employee perks. The "beer on tap, ping pong table in the common area" era of tech is drying up. And we're still unionless.
Never mind that last part.
And then in early 2023, AI (more specifically, Chat-GPT which is OpenAI's Large Language Model creation) tears its way into the tech scene with a meteor's amount of momentum. Here's Microsoft's prize pig, which it invested heavily in and is galivanting around the pig-show with, to the desperate jealousy and rapture of every other tech company and investor wishing it had that pig. And for the first time since the interest rate hikes, investors have dollar signs in their eyes, both venture capital and Wall Street alike. They're willing to restart the hose of money (even with the new risk) because this feels big enough for them to take the risk.
Now all these companies, who were in varying stages of sweating as their bill came due, or wringing their hands as their stock prices tanked, see a single glorious gold-plated rocket up out of here, the likes of which haven't been seen since the free money days. It's their ticket to buy time, and buy investors, and say "see THIS is what will wring money forth, finally, we promise, just let us show you."
To be clear, AI is NOT profitable yet. It's a money-sink. Perhaps a money-black-hole. But everyone in the space is so wowed by it that there is a wide-spread and powerful conviction that it will become profitable and earn its keep. (Let's be real, half of that profit "potential" is the promise of automating away jobs of pesky employees who peskily cost money.) It's a tech-space industrial revolution that will automate away skilled jobs, and getting in on the ground floor is the absolute best thing you can do to get your pie slice's worth.
It's the thing that will win investors back. It's the thing that will get the investment money coming in again (or, get it second-hand if the company can be the PROVIDER of something needed for AI, which other companies with venture-back will pay handsomely for). It's the thing companies are terrified of missing out on, lest it leave them utterly irrelevant in a future where not having AI-integration is like not having a mobile phone app for your company or not having a website.
So I guess to reiterate on my earlier point:
Drowned rats. Swimming to the one ship in sight.
35K notes
·
View notes
Text
The Trend Of Internet Of Things In The World | Mobiloitte

Introduction:
The Internet of Things (IoT) is a complex and extensive part of modern technology that uses devices and apps to speed up and simplify our lives. However, any technological advancement has limitations and possibilities. This blog examines IoT security, industry impacts, and ethical challenges, as well as Mobiloitte's role.
Security Concerns in IoT Devices:
Security should always come first when developing IoT gadgets. Due to leaks of information and unauthorized access, these devices can hack individuals and corporations. Despite the risks, IoT devices can be secured by encrypting data and updating software frequently. Security needs must be specified during design to apply security to devices.
IoT's Role in Industrial Automation:
Industrial automation has improved efficiency and quality because of the Industrial Internet of Things (IIoT). Smart sensors and connected devices can also control important operating parameters, provide real-time monitoring, independent and predictive maintenance, and reduce operation time and cost. IoT technologies help manage the supply chain while understanding property location and quality, making industries easier to react to global markets.
Impact of IoT on Real Estate:
IoT Solutions In Real Estate industry are revolutionizing by enabling the creation of smart homes and buildings. Internet of Things allows for the digital connection of devices, facilitating improved security, energy efficiency, and overall management of properties. This technology also improves customer experience through features like virtual home tours and personalized property recommendations
Enhancing Retail Experiences with IoT:
IoT is transforming business. Smart shelves and inventory systems update items in real-time, and beacon-based technology delivers personalized promotions. Point-of-sale systems improve transactions and customer service. These advances improve shopping and give retailers data.
Impact of IoT on Transportation and Logistics:
IoT improves transportation and logistics efficiency and safety. Better routing and time savings are made available by connected vehicles real-time traffic data. Fleet management systems track vehicle health and driver behavior for safe and timely maintenance. From warehouse to last-mile delivery, IoT technologies improve transportation.
Why choose Mobiloitte?
Mobiloitte is an IoT development Company providing innovative and secure Internet of Things solutions tailored to various industries. Their expertise encompasses end-to-end IoT development, from device integration to data analytics. By choosing Mobiloitte, businesses can leverage their extensive experience and technical prowess to implement IoT solutions that drive efficiency, security, and innovation.
Conclusion:
The Internet of Things offers immense potential to transform industries and improve our daily lives. However, navigating the complexities of it requires a careful balance of innovation and security. As businesses adopt IoT solutions, addressing security concerns and ethical considerations becomes paramount. Mobiloitte plays an important role in guiding businesses through this landscape, ensuring successful and secure Internet of Things implementations.
#IoT in biotechnology#IoT software development company#smart home IoT solutions#internet of things#technology#security#information technology#cybersecurity#software#The Trend Of Internet Of Things In The World | Mobiloitte#Internet Of Things#Mobiloitte#Internet Of Things real estate#IoT in Real Estate#IoT in Business#IoT in Hospitals#Internet Of Things in homes#IoT
1 note
·
View note
Text
Signs your computer has been hacked are not always obvious
0 notes
Text
What Is PureVPN & How to Use PureVPN? || PureVPN Review || Is PureVPN safe? || Who owns PureVPN? || Is PureVPN good?
Feeling restricted by geo-locked content or concerned about online privacy? PureVPN can be your solution! What is PureVPN? PureVPN is a premium virtual private network (VPN) service that encrypts your internet traffic and routes it through a remote server, allowing you to browse the web anonymously and securely. How to use PureVPN is a breeze — simply download the app, choose a server location, and connect. This comprehensive guide will delve deeper into PureVPN’s features, benefits, and how to get started.
Click Here To Read Full Article
#PUREVPN#vpn#movie poster#rwrb movie#priscilla movie#moviegifs#movies#movie review#movieedit#movie lb#movie quotes#clone vpn#best vpn#free vpn#security#app#infosec#privacy#vpnservice#data privacy#worldwide privacy tour#online privacy#internet privacy#internet#enshittification#invasion of privacy#technology#vpn service#vpn reviews#vpn software
0 notes
Text

We build Smart IoT Home and Campus Ecosystems from smart locks to thermostats, and air conditioning control devices, smart lighting systems, face recognition technologies. Making Your Home safe, secure, and futuristic.
#solution#technology#software#abu dhabi#ajman#dubai#fujairah#ras al khaimah#management#security#internet of things
1 note
·
View note
Text
I cannot express emphatically enough how much I hate requirements to sign in, in this case signing into a microsoft account to set up windows.
Seriously what the fuck do you need this for. Just give me a local account. Why the fuck do I need to be internet connected. Is it because you're bad engineers and designers? Well, yes. But also is it because you're trying to hold me and my data captive through monopolistic practices and surveillance which is also used to push ads and steal my data? Why yes.
Every time I touch one of these disgusting products I feel like flying out to Seattle, breaking into the microsoft building, and covering every surface in gorilla glue.
#it inspires violence#truly fuck you of you force me to connect to the internet for your software to work#it also forces a pin?#like what the fuck this is so insecure#you're trying to force biometrics and reducing password security to a pin#fucking die#I'll add your mouth and nose to the surfaces I'm gorilla gluing#and there's ads in my operating system#seriously i will flense you microsoft#every single one of you one by one
0 notes
Text
Heads up: Threatening software detected; opening the file is prohibited.
In an era where the digital world is as intrinsic to our lives as the air we breathe, the relevance of cybersecurity can not be overemphasized. Secure mobile apps , every download, and every apparently innocuous online interaction brings with it the possible risk of inviting malicious software right into our digital sanctuaries. This write-up aims to illuminate why downloading and install or opening destructive programs on your computer system is not simply dangerous-- it belongs to unlocking to your electronic home to a host of unwelcome effects.
Malicious software application, or "malware," is a wide term that encompasses numerous kinds of damaging software program, including viruses, trojans, worms, ransomware, and spyware, to name a few. These electronic threats are developed with purposes that vary from benign mischievousness to straight-out malevolent functions, such as stealing individual details, pirating computer resources, or securing documents for ransom money.
Cyber hygiene of downloading or opening a documents that harbors malware can trigger a domino effect of occasions that jeopardize your computer's safety and security and honesty. Here's a failure of why it's perilous:
1. ** Personal Info Theft **: Many types of malware are created to stealthily infiltrate your system and pilfer delicate data such as passwords, financial details, and individual identity details. This information can then be made use of for illegal tasks, marketed on the dark internet, and even bring about identification burglary.
2. ** System Damage **: Certain malware variations can corrupt documents, alter or delete important system data, and in extreme instances, make a computer inoperable. This not only interrupts individual or company operations but can additionally result in the loss of important data.
3. ** Source Hijacking **: Some malicious programs, like cryptojacking malware, clandestinely use your computer system's sources to mine cryptocurrency, considerably decreasing your system and potentially creating lasting damage to elements as a result of overheating or overuse.
4. ** Ransomware **: Probably one of the most nefarious forms of malware, ransomware secures your files, securing you out of your very own data. The wrongdoers then demand a ransom for the decryption trick. Paying the ransom, nonetheless, does not ensure the return of your information and additional funds the cycle of cybercrime.
5. ** Personal privacy Violation **: Spyware and certain kinds of trojans can check your activities, log keystrokes, and even turn on video cameras and microphones without authorization, bring about an extensive intrusion of privacy.
Shielding on your own from these digital threats entails a combination of watchfulness and the usage of cybersecurity tools. Always validate the resource of your downloads, avoid opening email add-ons or links from unidentified senders, and use thorough anti-viruses software application that supplies real-time defense, routine updates, and system scanning capabilities.
Enlightening oneself on the characteristics of phishing attempts and rip-off sites is also important. These commonly function as the distribution devices for malware. Search for HTTPS in web addresses, and watch out for sites that display inadequate design, spelling, and grammar mistakes, or that request unnecessary personal information.
To conclude, Secure coding standards is much better than remedy" has actually never ever been even more applicable than in the context of digital safety. The short-term adventure or benefit of downloading an unknown documents fades in contrast to the possible threats. By exercising safe surfing practices and arming your system with robust protection steps, you can substantially alleviate the risk of malware and guard not just your digital life, however your reality too.
#Secure computing#Phishing scams#Spyware threats#Hacking protection#Cybersecurity tips#Vulnerable software#Email attachment safety#Internet phishing#Digital security#Malicious URLs#Online fraud prevention#Security patches#Firewall protection#Virus scan#Secure passwords#Two-factor authentication#Cybersecurity education#Malicious code#Cyber hygiene#Data encryption#Secure networks#Security vulnerabilities#Malware quarantine#Cyber defense strategies#Suspicious activity monitoring#Identity theft protection#Secure file sharing#Malware signatures#Cyber risk management#Secure online transactions
1 note
·
View note
Text
Google is going to start scraping all of their platforms to use for AI training. So, here are some alternatives for common Google tools!
Google Chrome -> Firefox
If you’re on tumblr, you’ve probably already been told this a thousand times. But FireFox is an open-source browser which is safe, fast and secure. Basically all other browsers are Chrome reskins. Try Firefox Profilemaker, Arkenfox and Librewolf! Alternatively, vanilla Firefox is alright, but get Ublock Origin, turn off pocket, and get Tabliss.
Google Search -> DuckDuckGo
DuckDuckGo very rarely tracks or stores your browsing data (though they have only been known to sell this info to Microsoft). Don’t use their browser; only their search engine. Domain visits in their browser get shared. Alternatively, you can also use Ecosia, which is a safe search engine that uses its income to plant trees! 🌲
Google Reverse Image Search -> Tineye
Tineye uses image identification tech rather than keywords, metadata or watermarks to find you the source of your image!
Gmail -> ProtonMail
All data stored on ProtonMail is encrypted, and it boasts self-destructing emails, text search, and a commitment to user privacy. Tutanota is also a good alternative!
Google Docs -> LibreOffice
LibreOffice is free and open-source software, which includes functions like writing, spreadsheets, presentations, graphics, formula editing and more.
Google Translate -> DeepL
DeepL is notable for its accuracy of translation, and is much better that Google Translate in this regard. It does cost money for unlimited usage, but it will let you translate 500,000 characters per month for free. If this is a dealbreaker, consider checking out the iTranslate app.
Google Forms -> ClickUp
ClickUp comes with a built-in form view, and also has a documents feature, which could make it a good option to take out two birds with one stone.
Google Drive -> Mega
Mega offers a better encryption method than Google Drive, which means it’s more secure.
YouTube -> PeerTube
YouTube is the most difficult to account for, because it has a functional monopoly on long-form video-sharing. That being said, PeerTube is open-source and decentralized. The Internet Archive also has a video section!
However, if you still want access to YouTube’s library, check out NewPipe and LibreTube! NewPipe scrapes YouTube’s API so you can watch YouTube videos without Google collecting your info. LibreTube does the same thing, but instead of using YouTube servers, it uses piped servers, so Google doesn’t even get your IP address. Both of these are free, don’t require sign-ins, and are open source!
Please feel free to drop your favorite alternatives to Google-owned products, too! And, if this topic interests you, consider checking out Glaze as well! It alters your artwork and photos so that it’s more difficult to use to train AI with! ⭐️
#anti ai#anti ai art#anti ai music#anti ai writing#anti google#google#political#current events#azure does a thing
30K notes
·
View notes