#its what i based the bug eye off of so it behaves in a similar way. hehehehehe.
Note
MACCC!! for the fanfic ask game thing. ummm i don't know a specific word 2 send but i am intrigued. eyes emoji. (<<on computer and do not want 2 look up emojis just to copy/paste one) what r u writing!!! what's ur fav passage in it so far!!!! i wanna hear abt ur writing!!!!
omg whiskey i forgot we were not mutuals while i was in my fanfic writing arc. omg. i have not written a fic since we became mutuals holy shit !!!!!! absolutelyly insane . ANYWAY i write about my ocs all the time and also silly little self indulgent stories that i dont share bc theyre just for me. BUT. CURRENLTY. i missed writing fics so i am in a months long hiatus of a fic for mission to zyxx which is a silly improv comedy podcast that i was super into right before i got into trigun !!!!!!!! its my beloved ever. however the trigun brain worms overtook me before i finished my fic and i have not gone back to work on it much :( i WANT to finish it tho bc the fandom is very small annnd i literally read every single fic in the ao3 tag in the span of like a week. i need 2 add to it.
ANYWAY basics of the fic (spoilers for mission to zyxx incoming !!) :
the main character has a bug egg laid in his eye and throughout all of season 2 it just grows in his eye and makes it look all fucked up until the s2 finale where the egg hatches and another character pulls his eye out before the bug makes his head explode. << its not as fucked up as it sounds bc this is a full comedy podcast so everything is played for goofs and this moment only lasts a total of like 6 seconds but i am a sucker for body horror especially when it involves gross bugs so !!! i am judt rewriting that scene with my own headcanons ans making it scary and emotional 😌 hi my names mac ghostiezone and i love horror and gay people.
I HAVE TO REREAD MY ENTIRE WIP TO FIND A PART TO POST i cant believe ur making me do this (<< THANK U I HAVE NOT LOOKED AT IT IN WEEKS) apologies in advance for my setup i like 2 write on my phone in the middle of the night so my google docs is in perma-darkmode:

<< we love an alien mind contrrol parasite that makes a usually cowardly docile character behave like a monster 😌😌😌😌
#oh no im feeling the shame of posting a fic involving characters with stupid silly names.#anyway this is sooooo non-canon compliant i just wanted an excuse to be self indulgent and write about fucked up bugs#have u ever heard of leucochloridium.#its a type of parasite that lives in snails eyes and makes them all banded and pulsing to attract birds to eat the snail <3#its what i based the bug eye off of so it behaves in a similar way. hehehehehe.#linked a video to the snail parasite in the descriptiion for the fic i cant wait for people to be so disgusted bc of me >:]#something about me is i love 2 put weird gross biology in fics literally all the time forever#THANK U WHISKEY. GOD I NEED 2 FINISH THIS#i haaaate posting my writing eith no context bc it makes me self aware of how silly it sounds. but also i like 2 talk about my writing#whiskey u missed my fanfic phase i wrote about cwilbur so fucking much my favorite guy ever#SOMETHI G ABOUT ME IS THAT I LOVE 2 TALK ABOUT SEA CREATURES IN MY WRITING#NOTICE I FUCKING MENTION A CUTTLEFISH IN A UNIVERSE WHERE CUTTLEFISH DO NOT EXIST AND ARE NEVER BROUGHT UP EVER#im incurable. fish are too interesting#i use used to use dead fish eye metaphors in descriptions of ghostbur sooo much .#<< unsettling ghostbur is/was my biggest agenda when i was making dsmp content#ANYWAY. THANK U#I LOVE U#friends!!!#asks#anachronistic-falsehood
6 notes
·
View notes
Text
COSMIC - S3:E4; Chapter Four, The Sauna Test - [Pt. 2]
A Will Byers x Reader Series
𝘔𝘪𝘬𝘦, 𝘓𝘶𝘤𝘢𝘴, 𝘢𝘯𝘥 𝘞𝘪𝘭𝘭 𝘳𝘦𝘤𝘳𝘶𝘪𝘵 𝘌𝘭, 𝘔𝘢𝘹 𝘢𝘯𝘥 𝘠/𝘯 𝘵𝘰 𝘩𝘦𝘭𝘱 𝘵𝘩𝘦𝘮 𝘭𝘦𝘢𝘳𝘯 𝘸𝘩𝘰 𝘵𝘩𝘦 𝘔𝘪𝘯𝘥 𝘍𝘭𝘢𝘺𝘦𝘳'𝘴 𝘩𝘰𝘴𝘵 𝘪𝘴 𝘸𝘩𝘪𝘭𝘦 𝘙𝘰𝘣𝘪𝘯, 𝘚𝘵𝘦𝘷𝘦, 𝘢𝘯𝘥 𝘋𝘶𝘴𝘵𝘪𝘯 𝘳𝘦𝘤𝘳𝘶𝘪𝘵 𝘴𝘰𝘮𝘦𝘰𝘯𝘦 𝘵𝘰 𝘴𝘯𝘦𝘢𝘬 𝘪𝘯𝘵𝘰 𝘓𝘺𝘯𝘹.
📝: lmaooooooo this just gets gayer and gayer 💀💀
||𝟑𝐑𝐃 𝐏𝐄𝐑𝐒𝐎𝐍 𝐏𝐎𝐕||
"Do you copy? This is a code red."
The rising sun makes its way through the blinds in Max's bedroom, its gentle yellow rays split into several thin beams and casting out over the three sleeping bodies splayed over one another on the floor. El's body still curled into Y/n's arm, her hair a mess. Y/n was splayed out on her stomach, crooked, as her head had edged its way onto Max's pillow and her legs fell over El's. All the while, a sleeping Max had resorted to using the back of Y/n's shoulder as a pillow.
And they were snug as can be, tucked away in sleep, drool threatening to drip from their parted mouths as Lucas's desperate voice rings out from Max's super com.
"I repeat, this is a code red."
The device seems to grow louder with every word, slowly but surely pulling the girls from sleep.
"Max. Do you copy?" Max lifts her head from Y/n's shoulder, scooching back onto her pillow, and begins palming the ground under her bed. "This is a code red."
Her hand finally finds the comms and she senses El lazily rise up onto her elbow. She presses the button and seethes into the microphone.
"Shut. Up."
She slams the antenna down and shuts off the device, throwing it back under the bed. Y/n hums into the pillow, eyes still closed.
"Mm... what's red?" She asks through clenched teeth, still much too tired to even move her jaw.
"Nothing," Max yawns.
She turns over in bed, nestling back into the rainbow sheets and finding herself nearly nose to nose with Y/n as El rubs the sleep from her eyes, finally joined them. El just settles her head back into her pillow, her tangled hair still falling over her face and blocking out the sun. She let out a soft yawn, letting sleep return to her as she snuggled back into Y/n's arm happy and warm.
⊹ ⊹ ⊹
Lucas stares at his super com in light shock as he looked between his friends perched on either side of him on the basement couch.
"She turned it off."
Simultaneously, Will, Lucas, and Mike's eyes all jump to the phone hanging on the wall.
⊹ ⊹ ⊹
The blaring ring of Max's telephone is the next thing to wake them, and Y/n groans. Max shoots up in anger, her long red hair falling over her glaring face.
"Oh, you have got to be kidding me." She seethes, pulling herself up to her feet.
"Tell him we're not home," Y/n mumbles, still fighting a losing battle with sleep and a foggy mind.
Max stomps across the floor, strategically maneuvering around her friends, and rips the phone off its receiver.
"I'm sleeping. Go away,"
"Max, this is Will—" her hand caught mid-air, the boy's words barely registering to her in time. Reluctantly, she brings the phone back up to her ear. "I need you to stay on the line, and please just listen."
When Will doesn't hear the click of the dial tone, he breathes a sigh of relief. His eyes dart over his shoulder at his waiting friends trying to feed him the words but he ignores them, turning away.
Max frowns into the phone at what he says next, his voice going pleading.
"Is Y/n there?" There's a pause, and Max frowns down at the phone when she thinks she hears light shushing. "And El? Are you guys all together?"
Okay, now she was bugging out a little.
"Why?" She asks, an edge gradually returning to her voice out of concern.
She glances over her shoulder at her two best friends; Y/n had finally opened her eyes and was trying to make sense of her surroundings as she squinted through the sunlight and El was flowing up at her, worried.
"Just, stay together, okay? Something bad happened, is happening, whatever. We don't really know, but we can't take any chances."
"Okay, what are you talking about? What's going on?" She presses.
"Just meet us at Mike's house, and I'll explain. We all will. Just get over here, quickly."
"What?"
"Hurry!"
And then the line went dead.
Max held the phone in her hand, her stare drifting off as Will's words echoed in her mind.
"What'd he say?" El asked.
"Yeah," Y/n yawned, finally pulling herself into a sitting position, her face puffy from sleep. "is everything okay?"
⊹ ⊹ ⊹
"Try Dustin again," Mike says, turning to Lucas.
"He's not answering," Lucas says.
"So, try him again,"
Lucas bites back a sigh and returns to his comms with a sigh. Will picks the phone back up, shooting Mike a knowing look.
"I'll try their house,"
Lucas shoots him a thankful look before returning to his mindless search.
"Dustin, do you copy? I repeat... this. is. a. code red."
⊹ ⊹ ⊹
Dustin watches from the very same ledge as Lynx Transportation hauls a cart full of shipments from Kauffman Shoes and Imperial Panda. But his mind was still spinning, trying to formulate possible answers as to just what he was dealing with as he scouts for their routine.
His eyes had caught on the third armed officer who approached the keypad holding a small plastic card, and Dustin made a mental note.
"That keycard opens the door, but unfortunately the Russian with this keycard has a massive gun,"
Sure enough, the metal doors swung open and the cart is pushed inside. Apart from his cautious glare on the armed guard standing watch, his eyes try to catch whatever lays beyond the threshold.
It looked to Dustin to be a storage room no bigger than his living room, stacked with similar boxes.
"Whatever's in this room, whatever's in those boxes, they really don't want anybody finding it," Dustin concludes as he paces the back room of Scoops Ahoy.
Robin and Steve sit opposite one another in thought.
"But there's gotta be a way in," Robin mutters.
"Well, you know..." Steve stops twirling his hat, quickly reshaping the top with a quick puff of air before dropping it on the table and leaning in with a serious tone. "I could just take him out,"
"Take. Who. Out?" Robin blinked.
"The Russian guard," he answers obviously.
Robin leans back in her seat, nodding sarcastically at him through wide eyes and Steve scoffs.
"What? I sneak up behind him, I knock him out, and I take his keycard. It's easy,"
"Did you not... hear the part about the massive gun?" Dustin asks with crossed arms.
"Yes," Steve snarks, surprised. "Dustin, I did. And that's why I would be... sneaking."
"Ahh," Dustin nods. "Well, please, tell me this, and be honest, have you ever actually..." Dustin gives an all too casual shrug, knowing exactly what button he was pushing. "won a fight?"
"OH-kay, that was one time—"
"—Twice. Jonathan. Year prior?"
"Uh, listen. That doesn't count,"
"Why wouldn't it? Because it looks like he beat the shit out of you."
Robin finds herself laughing, lazily rolling her eyes across the shop as the two continue to bicker.
"It was—"
Her grin slowly falls when her eyes catch something in the corner.
"—You got a fat lip, crooked nose, swollen eye, a lot of blood,"
"...things all added up, yeah they sound bad but..."
As the thought grew into an idea, the grin returned to Robin. "That just might work,"
She was out of the backroom, hand diving into the tip jar faster than they could blink. They scrambled to the window in a baffled frenzy.
"Robin,"
She didn't answer, and when she made a break for the exit, Steve and Dustin tumbled out from the back room.
"Hey, Robin! Hey, what— what are you doing?"
"I need cash," she explains, backing out of the store.
"Well, half of that's mine," he pouts. "Where're you going?"
"To find a way into that room, a safe way. And, in the meantime, sling ice cream, behave, and don't get beat up," she says with an excited smirk. "I'll be back in a jiff!"
With a quick two-finger salute, she had disappeared into the crowd leaving her privately self-proclaimed Dingus Duo at home base.
Steve sighs, looking to Dustin only to find him licking the scooper.
"Oh, dude," he scolds, yanking it out of his hands and returning it to his sling with a twirl. "Come on, man, not my scooper,"
⊹ ⊹ ⊹
The trip to Mike's house had indeed been a quick one. When Max had relayed the message, a grave face became all of them. El and Y/n looked at each other and knew; their fears were being realized. And Max knew there was no more denying it, no matter how much she wanted to. No matter how much she needed to.
"I didn't think it was anything at first," Will says.
He was before his friends - most of them anyway - all of them seated around the coffee table in Mike's basement. He hadn't realized how much he had missed Y/n until he had seen her, nor her him. And neither had left each other's side since they gathered. She was sat beside him on a low footstool, El to her right on the upholstered chair, and him on her left; perched on the arm of the couch to the far right of Mike and Lucas.
Concern was etched on her features, as it was on all of them as they listened intently.
"I mean, I think I just didn't want to believe it." He sighs, locking eyes with Y/n knowingly. "The day I first felt it was at Day of the Dead,"
《•••》
And not unlike only months short of a year prior, when he felt himself ensnared in the terror and icy grip of the monster that lurked in shadows only he could see, Will Byers could feel his skin tightening painfully as goosebumps gripped his neck. It was a chill he hoped he'd never feel again, a chill that had nearly destroyed him and his family and friends. And Y/n. The passionate, fiery, hatred for the girl was the only thing about this icy monster that burned brighter than the horrifying memories it left with him.
"Will?"
Startled, his head is ripped to her direction, arm already slipping away from his neck as she stares at him in worry. She recognized the look in his eyes all too well, and immediately she knew something was amiss.
"Will, what is it?"
《•••》
"The power went out that night, too," Mike says in realization, and Will nods.
"And then I felt it again at the field near the Nelson farm the next day."
《•••》
Will stopped suddenly when the world plunged away from underneath his feet and the dark feeling returned. All the while, Y/n's voice faded into the distance as he gripped his goosebump-covered neck, looking fearfully out onto the horizon.
"Think they'll carry me if I fake a leg injury?" She chuckles, her voice far away and fleeting from him.
Despite the steady burst of hot air carried through the breeze and the sun beating down on his skin, he felt a total absence of warmth. And like almost like a phantom limb, all he can feel is panic and something dark, and desperate... Something angry.
"Will?"
《•••》
"Then again, yesterday outside Castle Byers,"
《•••》
As Will mingled with the dirt beneath him, the storm pounding against his back soaking him to the bone, he feels it again.
The same feeling he had felt the night before Dustin's return, the day of, and now...
Well, there was no denying it. No more running. This was real, and it wasn't something so easily shaken.
A great change was upon him and his friends, a change none of them were prepared for.
Shakily, he pulls himself to his feet, not entirely sure if the voice calling his name was real.
"Will?"
With a faraway look in his eyes, Will turns to his awaiting friends as his stomach plummets beneath the earth.
《•••》
"What does it feel like?" Max asks from her spot across the coffee table.
"It's almost like..." everyone watches patiently as Will draws on a thoughtful face, for once it seems, struggling for the right words. "You know when you drop on a rollercoaster?"
Y/n, Max, and Mike all nod.
"Mm-hmm,"
"Yeah,"
"Sure,"
"No," El says, still listening intently.
"It's like... everything inside your body is just sinking all at once, but this is worse," Will says, a faraway look in his eyes that Y/n knows all too well. "Your body... it goes cold. And you can't... breath."
Will's eyes jump down his wringing hands when he feels Y/n entwining her left with his right, interlacing their fingers and giving his hand a reassuring squeeze. He feels his shoulders slack at her warm touch and he sends her a thankful look before continuing, feeling just a little braver.
"I've left it before," he says through a wavering voice. "whenever he was close."
《•••》
He fearfully crept towards the front door. He came to a stop when he heard the dreadful sound of wood creaking and he watched in horror as the front door slowly swung open to reveal a reddish-purple sky, and the violent winds were carrying leaves and other debris with it. Something strange was growing around the outside of the house and he felt the familiar sensation returning.
He felt his blood run cold and his skin shriveled up, goosebumps breaking out all over. His breathing picked up and he could feel the hair on the back of his neck stand up as he watched frozen in terror.
《•••》
"Whenever who was close?" Mas asked, fearing the answer she already knew.
Will tried to remind himself he was in the presence of his love and his friends but fear still gripped his lungs and threatened to steal his voice. Finally, with a trembling breath, he spoke the truth none of them wanted to hear, changing the rest of their summer - and possibly the rest of their lives - forever.
"The Mind Flayer."
《•••》
"Go away!"
It got closer. It was swooping in like a vulture but Will didn't give in.
"Go away! Go away!" Tears were streaming down his face, and the monster got closer.
《•••》
Y/n's eyelids fall closed at the mention of the monster that brought so much harm and grief to her and the lives of her loved ones as the truth hits her completely. Just the sight of his convulsing body and his weeping mother that day out on the field when the Mind Flayer got him was traumatic enough. Her eyes flicker back open, back onto the equally horrified looks of her friends and her grip on her boyfriend's hand tightens.
"I closed the gate," El reasons.
"I know, but," for a moment, WI loses his voice again and he clings to Y/n's touch like a lifeline bringing him back. He fears the words he is about to speak, not only for his sake but for everyones. For Y/n's. But the fear was too great to keep quiet. If it was even a real possibility, it had to be stopped. As soon as possible. "What if he never left?"
Shakily, he looks around the room with horror hidden within his hazel irises until they land on Y/n, full of grief. His voice was soaked with apology, unable to contain his worry.
"What if we locked him out here with us?"
Y/n's head turns to meet El's eyes, the two share an equally concerned and knowing gaze from beside one another. Her stomach was twisting into knots, the horrible, sickly feeling of dread that had been building for the past two nights was finally realized.
||𝐖𝐈𝐋𝐋'𝐒 𝐏𝐎𝐕||
"This is him," I say, throwing a spare piece of paper on the D&D table before us all. The six of us all stood together, finally surrounding the D&D table for all the wrong reasons but there's no time to think about that now. I grab the charcoal in hand and began frantically scribbling an all too familiar shape in charcoal. "All of him,"
"But that day on the field," I explain. "part of him attached itself to me,"
I fight the intrusive memory trying to overwhelm me, bringing back the phantom chill that has always lingered since that day.
《•••》
He stood frozen, now trapped in the swirling fog. Several black tendrils spawned from the mass and invaded Will and he could feel the evil presence as it possessed his body and settled in his very soul.
《•••》
I yank my hand across the page, pulling up my dirtied palm to show my friends before nodding to my left.
"Y/n got him out of me,"
《•••》
"I think it's an earthquake!" Mike cries.
A light breeze picks up in the tunnel from where they're headed, carrying with it a warm toasty wave of heat that answered their question.
"No, not an earthquake!" Dustin's eyes went wide from behind his goggles as he looked to the others excitedly. "It's Y/n!"
•••
The Henderson child had managed to pull herself from unconsciousness, and she now stood across the bed. Her arms were stretched out before her and a blazing fire resided in her eyes, a grunt pulled from deep within her throat. Three bloody lines where his nails had caught her ran diagonally down her vein-covered face. Each vein protruded from her skin as blood poured from her nose and ears.
Like a broken dam, all that raw power trapped inside her burst free. Y/n was a supernova, a sight to behold as everything inside her exploded all around her.
•••
Will's mouth opens in another scream and a billowing cloud of inky black smoke escapes. It twists and unravels out from between his lips like a pitch-black tornado.
《•••》
"and El closes the gate,"
I flip the page back over and my eyes trail across my friends' faces thoughtfully, the last of the pieces falling into place as I explain.
"The part that was still in me, what if it's still in our world?"
《•••》
It grows larger and larger, circling over the boy and looms over the entire room as it had the last few days. Will's body goes limp, falling back onto the mattress as the dark mass zips across the room and through the front door breaking it open.
Nancy quickly recovers her footing and chases it out of the door to assure it's leaving for good. Sure enough, when she reaches the porch she spots the black dust circle the trees before disappearing into the sky.
《•••》
I plant my charcoal-dusted hand on the paper, leaving behind a faint trace of black.
"In Hawkins," I conclude.
"I don't understand," Max began. "The Demodogs died when El closed the gate. If the brain dies, the body dies,"
Y/n shook her head gravely from beside me, standing up a little straighter after leaning against the table.
"But the brain didn't die," she sighed heavily in realization. "Not all of it. So the part that was in control, lost. And so did the army, but, enough must have survived... And now after all this time..." She trailed off.
Mike nodded from beside me.
"Exactly," he said. "We can't take any chances. We need to assume the worst... The Mind Flayer is back."
I feel Y/n shift uncomfortably from beside me, her eyes drilling holes into the paper as she chews on her lip and I feel a tug in my chest. But the others were still looking towards me, waiting, and so was she so I continued.
"And if he is," I begin, hesitant to tear my eyes away from her. "He'll want to attach himself to someone again. A new me,"
Once again my eyes meet with all my friends as the very air around grows thicker, and Lucas finally concludes what we all fear.
"A new host,"
I nod and the room falls quiet again at the challenge laid before us.
It was difficult enough facing an enemy as powerful and ruthless as the Mind Flayer, but I think it helped our chances considerably he attached himself to me; someone who already had some insight on his territory, the Upside Down. Not only that, but I was indescribably lucky enough to have the people I have in my life who fought for me. The chief, Bob, my friends. Jonathan and my mom, and of course Y/n.
But his next victim could be anybody, and that's what makes him even more dangerous.
Finally, Y/n broke the silence - the second time she had spoke since the news had been broken. If I thought she was terrified before, I was dead wrong. I saw pure dread growing in her eyes as they trailed from El's and up to mine, widened and shining. It was with a plunging stomach I knew she had our first clue.
"Oh, no,"
· · ─────── ·𖥸· ─────── · ·
Shop Palestine: Support artisans and craftworkers in Palestine
Hadeel: A UK alternative to the resource above!
Trans Housing Coalition Fund
· · ─────── ·𖥸· ─────── · ·
Tag List:
@dickkwad @iblesstherainsdown-in-africa @miscellaneoustoasts @happyandlonely-blog @peeperparkour @ba-responds @bibliophilesquared @blogforhoes @witch-of-all-things-soft @shawkneecaps @whothefuckstolemykeds @daughter-of-the-stars11 @stranger-things4 @kpopanimegirl @nightbu-g @lozzybowe @gizmofishersupremacy @spiderbitch69420
❥ Let me know if you would like to be added to or removed from the taglist! ❥
#you'll float queue#cosmic#cosmic 3#will byers x reader#reader insert#will byers x you#x reader#stranger things#stranger things 3#stranger things x reader#st x reader#st#st3#st 3x04#3x04#y/n henderson#will byers#max mayfield#el hopper#lucas sinclair#mike wheeler#dustin henderson#steve harrington#robin buckley#billy hargrove#the mind flayer
44 notes
·
View notes
Text
Warning: This is not an endorsement or encouragement for you to start behaving in illegal or immoral behaviour. I am not held responsible for any trouble you decide to get into; or what you do I encourage people to use my information I post in a responsible way and not violate any state or federal laws
History Of The Dark Web
The Deep Web and it’s Dark Web brother have been in the public eye more than usual in the past few years. Once the things that happen on the hidden part began having an impact on the day to day and safety of our lives, ordinary people started to take an interest. That doesn’t mean the hidden part of the internet is a recent development. It’s just about as old as the internet itself!
Now days tho it is dangerous if you are less then tech savvy and it could turn deadly for a new person stumbling onto the dark side of the internet where things like killers for hire, Drugs, Guns, Fake Money, and even Identities and people can be bought! You can only guess what can happen if you stumble onto one of these sites without knowing and ask the wrong questions!
1980
The history of the hidden web is almost as old as the history of the internet itself. Obviously, the same technology that made the internet and the web possible, also makes the Dark Web possible thanks to its architecture and designs. Which is why it is fair to pin the start of the Dark Web to ARPANET. Which is the direct precursor to the internet of today? While ARPANET may not have had a Dark Web as we know it now from the start, it wouldn’t take long before people started to make use of this technology for things they wanted to keep a secret. It turns out that the first ever online sale happened in the early 70s and was in fact cannabis. Students at Stanford sold weed to students at MIT, using ARPANET. Remember that at this point most people didn’t have personal computers, much less home internet access.
In the 1980s, access to the internet for normal citizens is still a dream. This was the decade when everything needed for a worldwide web would fall into place. In the early 80s, the TCP/IP standard is solidified. By the mid- 80s personal computers and modems are, if not affordable, at least available for anyone to buy. Internet pioneers also invented the domain name system we use to resolve website names during this decade.
Data havens emerge as an idea at this time as well. Since the world was going global, worries about where data should be stored came to the fore. Storing your data in a haven meant sending it out of the country to a territory that had better legal protection against government spying. At the extreme, data havens would be in no country at all. They would be built on structures or vessels out in international waters . A similar idea to seasteading. Actual data havens in the 80s popped up in the Caribbean islands.(Or as it turns out and which is slowly starting to be developed the Decentralized web run off the BlockChain and which has the potential to be way more secure then the darkweb)
1990's
The 1990s are without a doubt the time when the World Wide Web went mainstream. Thanks to web technologies like HTTP and FTP along with graphical computers capable of running a web browser, there was a sudden mainstream appeal to this whole internet thing.
Towards the end of the 1990s, there was a real leap in the technologies that allowed large amounts of data, such as multimedia, to be shared online. MP3 technology in particular lead to a massive shakeup of the music industry. Thanks to like the likes of Napster, people could perform illegal peer-to-peer exchanges of ripped and compressed music. This caused a complete meltdown among musicians and music executives. Lars Ulrich famously sued Napster which was really symbolic of the battle between old and new school. Today the music industry has adapted and streaming subscriptions are the norm. Without Dark Web alike peer-to-peer exchanges it’s doubtful we’d have the consumer-friendly online media world of today.
2000
The Dark Web proper really got its start in March of 2000 with the release of Freenet. The service still exists today and provides a censorship-resistant way to use the web. It is a true implementation of the Dark Web and provided a way for plenty of illegal information to pass around. This included illegal pornographic material and pirated content. Of course, actually exchanging money anonymously is still incredibly hard at this point, since you have to use cash. So Freenet doesn’t lead to any black market activity to any significant degree.
A data haven called HavenCo was established in Sealand (a seasteading micronation) which promised to store sensitive information in a place where no government could stick its nose. It seemed like a Dark Web dream, but by the early 2010s HavenCo was dead.
The most important Dark Web development of all time happened in 2002, with the release of TOR or The Onion Router. It was created by non-other than the US government, as a way to help their own operatives remain untraceable. It’s no exaggeration to say that the Dark Web of today could not exist without this technology.
Late in the 2000s came the advent of cryptocurrency in the form of Bitcoin. The final piece of the puzzle needed to make the Dark Web really click.
The Early 2010's
The 2010s represent the era where cryptocurrency and TOR met to create the first proper black markets. The pioneer was the Silk Road, which is now long defunct. Despite taking all the important figures out behind the Silk Road, it has seemingly done little to stop the trade of drugs and other illegal goods and services over the Dark Web.
This is the era in which the Dark Web becomes a topic of public concern, rather than just something discussed as cyber security conferences. Many mainstream articles emerge that explain the difference between the massive Deep Web and the relatively tiny Dark Web.
It becomes especially scary when it emerges that terrorists are using the Dark Web to communicate and coordinate. Ironic, given what the US created TOR for originally. Research published showing that the Dark Web is mainly being used to commit crimes.
Today
The Dark Web of today is reportedly in decline. Despite this, there is an incredible variety of hidden services and significant information exchange happening out of sight of the mainstream web. It doesn’t really matter that the Dark Web is relatively small compared to the surface web as a whole. Its impact is disproportionately large. Small groups of hackers collaborating on the Dark Web can bring a multi-billion Dollar internet company to its knees. Hackers end up impacting millions of users.
Darknet black markets are also thriving and putting both traditional and new synthetic drugs into the hands of anyone who wants them. Cryptocurrency has been the biggest factor in this maturation of the Dark Web.
Now you know the basic history of the dark web,. now lets get into the history of the newer technologies that help run the dark web and keep it secure technologies like TOR and the Cryptocurrencies that helps collect payment from the goods that are sold on the dark web.
History Of Tor
Tor is based on the principle of ‘onion routing’ which was developed by Paul Syverson, Michael G. Reed and David Goldschlag at the United States Naval Research Laboratory in the 1990’s. The alpha version of Tor, named ‘The Onion Routing Project’ or simply TOR Project, was developed by Roger Dingledine and Nick Mathewson. It was launched on September 20, 2002. Further development was carried under the financial roof of the Electronic Frontier Foundation (EFF).
The Tor Project Inc. is a non-profit organization that currently maintains Tor and is responsible for its development. The United States Government mainly funds it, and further aid is provided by Swedish Government and different NGOs & individual sponsors.
The U.S. National Security Agency (NSA) has called Tor “the King of high secure, low latency Internet anonymity.” And similar comments by BusinessWeek magazine, “perhaps the most effective means of defeating the online surveillance efforts of intelligence agencies around the world”.
Another speculation made is that Tor takes its funding from the U.S. Government which may lead to the assumption that NSA may have compromised the identities of individual Tor users. However, the executive director Andrew Lewman has disclaimed any confederations with NSA.
How it works
Tor works on the concept of ‘onion routing’ method in which the user data is first encrypted and then transferred through different relays present in the Tor network, thus creating a multi-layered encryption (layers like an onion), thereby keeping the identity of the user safe.
One encryption layer is decrypted at each successive Tor relay, and the remaining data is forwarded to any random relay until it reaches its destination server. For the destination server, the last Tor node/exit relay appears as the origin of the data. It is thus tough to trace the identity of the user or the server by any surveillance system acting in the mid-way.
Other than providing anonymity to standalone users, Tor can also provide anonymity to websites and servers in the form of Tor Hidden Services. Also, P2P applications like BitTorrent can be configured to use the Tor network and download torrent files.
Is It Safe
Various claims have been made to compromise Tor’s anonymity and security from time to time. The most famous one was the Bad Apple Attack in which the researchers claimed to have identified around 10k IP addresses of active BitTorrent users who were connected via Tor.
The Heartbleed bug was behind another major compromise in April 2014 which halted the Tor network for several days.
Traffic Fingerprinting is a method used to analyze web traffic by analyzing the patterns, responses, and packets in a particular direction. This technique can be used to attack the Tor network by making the attacker’s computer act as the guard. The main vulnerability was found at its exit points where the level of security is very low as compared to the rest of the Tor network.
The History of cryptocurrencies
In 1983, the American cryptographer David Chaum conceived an anonymous cryptographic electronic money called ecash. Later, in 1995, he implemented it through Digicash, an early form of cryptographic electronic payments which required user software in order to withdraw notes from a bank and designate specific encrypted keys before it can be sent to a recipient. This allowed the digital currency to be untraceable by the issuing bank, the government, or any third party.
In 1996, the NSA published a paper entitled How to Make a Mint: the Cryptography of Anonymous Electronic Cash, describing a Cryptocurrency system first publishing it in a MIT mailing list and later in 1997, in The American Law Review (Vol. 46, Issue 4).
In 1998, Wei Dai published a description of "b-money", characterized as an anonymous, distributed electronic cash system. Shortly thereafter, Nick Szabo described bit gold. Like bitcoin and other cryptocurrencies that would follow it, bit gold (not to be confused with the later gold-based exchange, BitGold) was described as an electronic currency system which required users to complete a proof of work function with solutions being cryptographically put together and published. A currency system based on a reusable proof of work was later created by Hal Finney who followed the work of Dai and Szabo.
The first decentralized cryptocurrency, bitcoin, was created in 2009 by pseudonymous developer Satoshi Nakamoto. It used SHA-256, a cryptographic hash function, as its proof-of-work scheme. In April 2011, Namecoin was created as an attempt at forming a decentralized DNS, which would make internet censorship very difficult. Soon after, in October 2011, Litecoin was released. It was the first successful cryptocurrency to use scrypt as its hash function instead of SHA-256. Another notable cryptocurrency, Peercoin was the first to use a proof-of-work/proof-of-stake hybrid.
On 6 August 2014, the UK announced its Treasury had been commissioned to do a study of cryptocurrencies, and what role, if any, they can play in the UK economy. The study was also to report on whether regulation should be considered.
Definition
According to Jan Lansky, a cryptocurrency is a system that meets six conditions:
The system does not require a central authority, its state is maintained through distributed consensus.The system keeps an overview of cryptocurrency units and their ownership.The system defines whether new cryptocurrency units can be created. If new cryptocurrency units can be created, the system defines the circumstances of their origin and how to determine the ownership of these new units.Ownership of cryptocurrency units can be proved exclusively cryptographically.The system allows transactions to be performed in which ownership of the cryptographic units is changed. A transaction statement can only be issued by an entity proving the current ownership of these units.If two different instructions for changing the ownership of the same cryptographic units are simultaneously entered, the system performs at most one of them.
In March 2018, the word cryptocurrency was added to the Merriam-Webster Dictionary
What is Blockchain
A blockchain, originally block chain, is a growing list of records, called blocks, that are linked using cryptography.[1][6] Each block contains a cryptographic hash of the previous block, a timestamp, and transaction data (generally represented as a Merkle tree).
By design, a blockchain is resistant to modification of the data. It is "an open, distributed ledger that can record transactions between two parties efficiently and in a verifiable and permanent way". For use as a distributed ledger, a blockchain is typically managed by a peer-to-peer network collectively adhering to a protocol for inter-node communication and validating new blocks. Once recorded, the data in any given block cannot be altered retroactively without alteration of all subsequent blocks, which requires consensus of the network majority. Although blockchain records are not unalterable, blockchains may be considered secure by design and exemplify a distributed computing system with high Byzantine fault tolerance. Decentralized consensus has therefore been claimed with a blockchain.
Blockchain was invented by a person (or group of people) using the name Satoshi Nakamoto in 2008 to serve as the public transaction ledger of the cryptocurrency bitcoin. The identity of Satoshi Nakamoto is unknown. The invention of the blockchain for bitcoin made it the first digital currency to solve the double-spending problem without the need of a trusted authority or central server. The bitcoin design has inspired other applications, and blockchains that are readable by the public are widely used by cryptocurrencies. Blockchain is considered a type of payment rail. Private blockchains have been proposed for business use. Sources such as Computerworld called the marketing of such blockchains without a proper security model "snake oil".
Structure
A blockchain is a decentralized, distributed and public digital ledger that is used to record transactions across many computers so that any involved record cannot be altered retroactively, without the alteration of all subsequent blocks. This allows the participants to verify and audit transactions independently and relatively inexpensively. A blockchain database is managed autonomously using a peer-to-peer network and a distributed timestamping server. They are authenticated by mass collaboration powered by collective self-interests. Such a design facilitates robust workflow where participants' uncertainty regarding data security is marginal. The use of a blockchain removes the characteristic of infinite reproducibility from a digital asset. It confirms that each unit of value was transferred only once, solving the long-standing problem of double spending. A blockchain has been described as a value-exchange protocol. A blockchain can maintain title rights because, when properly set up to detail the exchange agreement, it provides a record that compels offer and acceptance.
Blocks
Blocks hold batches of valid transactions that are hashed and encoded into a Merkle tree. Each block includes the cryptographic hash of the prior block in the blockchain, linking the two. The linked blocks form a chain. This iterative process confirms the integrity of the previous block, all the way back to the original genesis block.
Sometimes separate blocks can be produced concurrently, creating a temporary fork. In addition to a secure hash-based history, any blockchain has a specified algorithm for scoring different versions of the history so that one with a higher value can be selected over others. Blocks not selected for inclusion in the chain are called orphan blocks. Peers supporting the database have different versions of the history from time to time. They keep only the highest-scoring version of the database known to them. Whenever a peer receives a higher-scoring version (usually the old version with a single new block added) they extend or overwrite their own database and retransmit the improvement to their peers. There is never an absolute guarantee that any particular entry will remain in the best version of the history forever. Blockchains are typically built to add the score of new blocks onto old blocks and are given incentives to extend with new blocks rather than overwrite old blocks. Therefore, the probability of an entry becoming superseded decreases exponentially as more blocks are built on top of it, eventually becoming very low. For example, bitcoin uses a proof-of-work system, where the chain with the most cumulative proof-of-work is considered the valid one by the network. There are a number of methods that can be used to demonstrate a sufficient level of computation. Within a blockchain the computation is carried out redundantly rather than in the traditional segregated and parallel manner.
Block time
The block time is the average time it takes for the network to generate one extra block in the blockchain. Some blockchains create a new block as frequently as every five seconds. By the time of block completion, the included data becomes verifiable. In cryptocurrency, this is practically when the transaction takes place, so a shorter block time means faster transactions. The block time for Ethereum is set to between 14 and 15 seconds, while for bitcoin it is 10 minutes.
Hard forks
A hard fork is a rule change such that the software validating according to the old rules will see the blocks produced according to the new rules as invalid. In case of a hard fork, all nodes meant to work in accordance with the new rules need to upgrade their software.
If one group of nodes continues to use the old software while the other nodes use the new software, a split can occur. For example, Ethereum has hard-forked to "make whole" the investors in The DAO, which had been hacked by exploiting a vulnerability in its code. In this case, the fork resulted in a split creating Ethereum and Ethereum Classic chains. In 2014 the Nxt community was asked to consider a hard fork that would have led to a rollback of the blockchain records to mitigate the effects of a theft of 50 million NXT from a major cryptocurrency exchange. The hard fork proposal was rejected, and some of the funds were recovered after negotiations and ransom payment. Alternatively, to prevent a permanent split, a majority of nodes using the new software may return to the old rules, as was the case of bitcoin split on 12 March 2013
Decentralization
By storing data across its peer-to-peer network, the blockchain eliminates a number of risks that come with data being held centrally. The decentralized blockchain may use ad-hoc message passing and distributed networking.
Peer-to-peer blockchain networks lack centralized points of vulnerability that computer crackers can exploit; likewise, it has no central point of failure. Blockchain security methods include the use of public-key cryptography. A public key (a long, random-looking string of numbers) is an address on the blockchain. Value tokens sent across the network are recorded as belonging to that address. A private key is like a password that gives its owner access to their digital assets or the means to otherwise interact with the various capabilities that blockchains now support. Data stored on the blockchain is generally considered incorruptible.
Every node in a decentralized system has a copy of the blockchain. Data quality is maintained by massive database replication and computational trust. No centralized "official" copy exists and no user is "trusted" more than any other. Transactions are broadcast to the network using software. Messages are delivered on a best-effort basis. Mining nodes validate transactions, add them to the block they are building, and then broadcast the completed block to other nodes. Blockchains use various time-stamping schemes, such as proof-of-work, to serialize changes. Alternative consensus methods include proof-of-stake. Growth of a decentralized blockchain is accompanied by the risk of centralization because the computer resources required to process larger amounts of data become more expensive.
Openness
Open blockchains are more user-friendly than some traditional ownership records, which, while open to the public, still require physical access to view. Because all early blockchains were permissionless, controversy has arisen over the blockchain definition. An issue in this ongoing debate is whether a private system with verifiers tasked and authorized (permissioned) by a central authority should be considered a blockchain. Proponents of permissioned or private chains argue that the term "blockchain" may be applied to any data structure that batches data into time-stamped blocks. These blockchains serve as a distributed version of multiversion concurrency control (MVCC) in databases. Just as MVCC prevents two transactions from concurrently modifying a single object in a database, blockchains prevent two transactions from spending the same single output in a blockchain. Opponents say that permissioned systems resemble traditional corporate databases, not supporting decentralized data verification, and that such systems are not hardened against operator tampering and revision. Nikolai Hampton of Computerworld said that "many in-house blockchain solutions will be nothing more than cumbersome databases," and "without a clear security model, proprietary blockchains should be eyed with suspicion."
Permissionless
The great advantage to an open, permissionless, or public, blockchain network is that guarding against bad actors is not required and no access control is needed. This means that applications can be added to the network without the approval or trust of others, using the blockchain as a transport layer.
Bitcoin and other cryptocurrencies currently secure their blockchain by requiring new entries to include a proof of work. To prolong the blockchain, bitcoin uses Hashcash puzzles. While Hashcash was designed in 1997 by Adam Back, the original idea was first proposed by Cynthia Dwork and Moni Naor and Eli Ponyatovski in their 1992 paper "Pricing via Processing or Combatting Junk Mail".
Financial companies have not prioritised decentralized blockchains.
In 2016, venture capital investment for blockchain-related projects was weakening in the USA but increasing in China.[37] Bitcoin and many other cryptocurrencies use open (public) blockchains. As of April 2018, bitcoin has the highest market capitalization.
Permissioned (private) blockchain
Permissioned blockchains use an access control layer to govern who has access to the network. In contrast to public blockchain networks, validators on private blockchain networks are vetted by the network owner. They do not rely on anonymous nodes to validate transactions nor do they benefit from the network effect. Permissioned blockchains can also go by the name of 'consortium' blockchains.
Disadvantages of private blockchain
Nikolai Hampton pointed out in Computerworld that "There is also no need for a '51 percent' attack on a private blockchain, as the private blockchain (most likely) already controls 100 percent of all block creation resources. If you could attack or damage the blockchain creation tools on a private corporate server, you could effectively control 100 percent of their network and alter transactions however you wished." This has a set of particularly profound adverse implications during a financial crisis or debt crisis like the financial crisis of 2007–08, where politically powerful actors may make decisions that favor some groups at the expense of others, and "the bitcoin blockchain is protected by the massive group mining effort. It's unlikely that any private blockchain will try to protect records using gigawatts of computing power — it's time consuming and expensive." He also said, "Within a private blockchain there is also no 'race'; there's no incentive to use more power or discover blocks faster than competitors. This means that many in-house blockchain solutions will be nothing more than cumbersome databases."
Blockchain analysis
The analysis of public blockchains has become increasingly important with the popularity of bitcoin, Ethereum, litecoin and other cryptocurrencies. A blockchain, if it is public, provides anyone who wants access to observe and analyse the chain data, given one has the know-how. The process of understanding and accessing the flow of crypto has been an issue for many cryptocurrencies, crypto-exchanges and banks. The reason for this is accusations of blockchain enabled cryptocurrencies enabling illicit dark market trade of drugs, weapons, money laundering etc. A common belief has been that cryptocurrency is private and untraceable, thus leading many actors to use it for illegal purposes. This is changing and now specialised tech-companies provide blockchain tracking services, making crypto exchanges, law-enforcement and banks more aware of what is happening with crypto funds and fiat crypto exchanges. The development, some argue, has lead criminals to prioritise use of new cryptos such as Monero. The question is about public accessibility of blockchain data and the personal privacy of the very same data. It is a key debate in cryptocurrency and ultimately in blockchain.
Types Of Blockchain's
Currently, there are at least four types of blockchain networks — public blockchains, private blockchains, consortium blockchains and hybrid blockchains.
Public blockchains
A public blockchain has absolutely no access restrictions. Anyone with an Internet connection can send transactions to it as well as become a validator (i.e., participate in the execution of a consensus protocol). Usually, such networks offer economic incentives for those who secure them and utilize some type of a Proof of Stake or Proof of Work algorithm.
Some of the largest, most known public blockchains are the bitcoin blockchain and the Ethereum blockchain.
Private blockchains
A private blockchain is permissioned. One cannot join it unless invited by the network administrators. Participant and validator access is restricted.
This type of blockchains can be considered a middle-ground for companies that are interested in the blockchain technology in general but are not comfortable with a level of control offered by public networks. Typically, they seek to incorporate blockchain into their accounting and record-keeping procedures without sacrificing autonomy and running the risk of exposing sensitive data to the public internet.
Hybrid blockchains
A hybrid blockchain simply explained is a combination between different characteristics both public and private blockchains have by design. It allows to determine what information stays private and what information is made public. Further decentralization in relation to primarily centralized private blockchains can be achieved in various ways. Instead of keeping transactions inside their own network of community run or private nodes, the hash (with or without payload) can be posted on completely decentralized blockchains such as bitcoin. Dragonchain uses Interchain to host transactions on other blockchains. This allows users to operate on different blockchains, where they can selectively share data or business logic. Other blockchains like Wanchain use interoperability mechanisms such as bridges. By submitting the hash of a transaction (with or without the sensitive business logic) on public blockchains like bitcoin or Ethereum, some of the privacy and blockchain concerns are resolved, as no personal identifiable information is stored on a public blockchain. Depending on the hybrid blockchain its architecture, multi cloud solutions allow to store data in compliance with General Data Protection Regulation and other geographical limitations while also leveraging bitcoin's global hashpower to decentralize transactions.
Getting Started On The Darkweb
Technically, this is not a difficult process. You simply need to install and use Tor. Go to www.torproject.org and download the Tor Browser Bundle, which contains all the required tools. Run the downloaded file, choose an extraction location, then open the folder and click Start Tor Browser. That's it.
The Vidalia Control Panel will automatically handle the randomised network setup and, when Tor is ready, the browser will open; just close it again to disconnect from the network.
Depending on what you intend to do on the Dark Web, some users recommend placing tape over your laptop's webcam to prevent prying eyes watching you. A tinfoil hat is also an option. If you're reading this to find out about torrent files.
The difficult thing is knowing where to look on the Dark Web. There, reader, we leave you to your own devices and wish you good luck and safe surfing. And a warning before you go any further. Once you get into the Dark Web, you *will* be able to access those sites to which the tabloids refer. This means that you could be a click away from sites selling drugs and guns, and - frankly - even worse things.
Aggregation sites such as Reddit offer lists of links, as do several Wikis, including http://thehiddenwiki.org/ - a list that offers access to some very bad places. Have a quick look by all means, but please don't take our linking to it as an endorsement to go out and get your self in trouble and please note I am not responsible for what you do
Also, Dark Web sites do go down from time to time, due to their dark nature. But if you want good customer service, stay out of the dark!
How to download Tor browser?
NOTE:Altho TOR is secure it is still advisable to download a 3rd party Virtual Private Network (VPN) as it will give you a much greater chance of not being intercepted and anything you can do to repel the people looking for what you are doing the better! ok, now lets get started
The Tor Project Inc. has released Tor Browser which is a modification of an Extended Support Release version of Mozilla Firefox browser. The browser is portable so that it can be used from an external media and also reduces the hazel of installation. Tor Browser removes the browsing history and cookies after every use, thus reducing the risk of any cookie tracking. We can set-up SOCKS (Socket Secure) based applications to use the Tor network by configuring them with a loop-back address.
Tor Browser removes the browsing history and cookies after every use, thus reducing the risk of any cookie tracking. We can set-up SOCKS (Socket Secure) based applications to use the Tor network by configuring them with a loop-back address.
The Tor browser is available various desktop operating systems including Windows, Linux, and MacOS. You can visit this link to download Tor browser.
How to install Tor browser on Windows?
Run the Tor Browser setup.Choose your desired language.On the next windows, choose the destination folder. Using Tor would be easy if you choose the Desktop as the destination.Click Install.
The setup will create a folder named Tor Browser on your Desktop. Open the folder, and run the shortcut file to use Tor Browser.
For Linux, you’ll have to extract the downloaded file either using the command line or a file extractor application.
Tor Browser for Android
Orbot – a proxy with Tor for Android devices.
Orfox – a mobile version of Tor Browser for Android devices.
The Guardian Project, a global developer community founded by Nathan Freitas, is to be credited for the development of these apps.
Tor Browser for iOS
An official Tor browser app for iOS is available on the App Store.
Tor Alternatives
Hornet is a new anonymity network that provides higher network speeds compared to Tor. I2P and Freenet are other anonymity networks which can act as Tor alternatives. Also, Tails and Subgraph OS are Linux-based distributions with built-in Tor support.
Should I Use Tor?
Tor has proved to be an excellent medium for safe, secure and anonymous web presence available to a user at no cost. The developers of Tor didn’t intend it to become a hotbed of illegal activities, but evil-minded people have leveraged Tor for their benefits. The Tor project has led to an optimistic approach towards censorship and surveillance-free internet.
You can use Tor if you want to conceal your identity on the web or access some website that blocked in your region. But refrain yourself from doing anything that’s above the law because nothing is fool-proof and they can still catch you. Also, accessing your social media accounts over Tor can expose your identity. This being said me personally I use TOR only for my dark web research and visits. I do not access no websites with a commercially available router extension (IE: Com, Net, Org, Or anything else) the only extension that is run through tor is .onion extensions. The reason being is that any other extensions have the possibility to provide backdoor access to any an all of your information that is run while it is active.
NOTE: TOR's cookies are not dumbed until after you close the browser so it is still possible to track you if your browser is left open after you visited any other sites.
Steps For Safety(CH3)
Step 1: Plan ahead.
There are plenty of reasons companies and individuals may want to access the Dark Web. SMBs and enterprise companies in particular may want to monitor Dark Web portals for stolen corporate account information. Individuals may want to monitor sites for evidence of identity theft. Facebook's encrypted site, located at facebookcorewwwi.onion, is a feature-rich method of accessing the social network using end-to-end encryption.
Set a goal, make plans, and stay focused. Be mindful of purpose. Make sure you know what information you're looking for and why you're logging on to the encrypted web. For example, if you're a reporter and need to communicate with sources, focus on PGP, email, and encrypted communication. If you're searching for credit card information, look for Silk Road-type markets that sell hacked data.Get what you need, safely disconnect TOR and Tails, then log off.
Step 2: Obtain a new USB flash drive.
Purchase a new 8 GB or larger USB flash drive. Make sure you use a fresh, unused drive. You will install Tails, and Tails only, directly on your storage device.
Step 3: Prepare your local machine.
Ideally, use a fresh laptop. This isn't an option for most users, so instead do everything in your power to secure and isolate mission-critical information.
Back up critical data and local files.Make sure your hardware is optimized and malware-free.
Step 4: Download Tails and TOR.
TOR and Tails are available on the TOR Project website. Access download links directly from https://www.torproject.org. Insert your USB drive and follow the instructions on https://tails.boum.org.
Step 5: Browse safely.
Common portals and search engines:
DuckDuckGoThe Hidden WikiOnion.linkAhmia.fiGramsTorch
Encryption is strong, but not impenetrable. The FBI discovered and exploited vulnerabilities in the TOR network. Though the agency refused to disclose the source code used to penetrate the network, undoubtedly law enforcement agencies around the world monitor and operate on the Deep Web. Members of the TOR project vowed to patch network holes and strengthen the protocol.
Many of the best general deep web search engines have shut down or been acquired, like Alltheweb and CompletePlanet. Still, a few are hanging around to get you started:
DeeperWeb – Deep web search engine that leverages Google SearchThe WWW Virtual Library – The original index of the web, but more of a directory than a search engine.Surfwax – Indexes RSS feeds. Not certain this is still working…IceRocket – Searches the blogosphere and Twitter
These are all okay, but specialized search engines tend to be better than general ones for finding info on the deep web. If you’re looking for a court case, for example, use your state or country’s public records search. If you need academic journals, check out our article on using deep web search engines for academic and scholarly research. The more specific you can be, the better, or else you’ll just end up with the same search results that you would find on Google. If you need a specific file type, like an Excel file or a PDF, learn how to specify searches for that type of file (e.g. type “filetype:PDF” in your DeeperWeb query).
How to access the dark web on Android with Tor Browser
The official Tor Browser is now available on Android. You can get it from the Play Store or the Tor downloads page. As of writing, Tor Browser for Android is still in alpha, and additionally requires you install Orbot as a prerequisite.
The Tor Browser is the most popular dark web browser. Once Tor Browser is installed, you can now access those .onion dark net websites.
Using A VPN over TOR Or Vice Versa
A VPN allows a user to encrypt all the internet traffic traveling to and from his or her device and route it through a server in a location of that user’s choosing. A VPN in combination with Tor further adds to the security and anonymity of the user.
While somewhat similar, Tor emphasizes anonymity, and a VPN emphasizes privacy.
Combining them reduces risk, but there’s an important distinction in how these two tools interact. Let’s first discuss Tor over VPN.
If you connect to your VPN and fire up Tor Browser, you’re using Tor over VPN, this is by far the most common method. All your device’s internet traffic first goes to the VPN server, then it bounces through the Tor Network before ending up at its final destination. Your ISP only see’s the encrypted VPN traffic, and won’t know you’re on Tor. You can access .onion websites normally.
5 notes
·
View notes
Text

The Oregon Dark-eyed Junco, which breeds in the west, couldn't be confused with the Slate-colored Dark-eyed Junco of the east
Dark-eyed Juncos, Backyard Gems, Come in a Dazzling Array of Colors
The six flavors of junco were long considered separate species. Recent science shows that they instead boldly exhibit evolution in real time.
Forget the solstice; the first day of winter for me, growing up in New Jersey, came with the arrival of Dark-eyed Juncos to the yard. The small, round songbirds are easily recognized by their characteristic hops—forward and sideways on the ground, perhaps beneath a feeder—and flash of white tail feathers when they flutter to a nearby branch. And without fail, the juncos always seemed to materialize with the year’s first snowfall. Indeed, John James Audubon himself called the species Snow Bird.
In New Jersey, and anywhere in the country east of the Great Plains, snowbirds are a handsome slate color, with a bright white belly in addition to its white outer tail feathers, and an adorable pink beak. Little did I know, though, that if I ventured west, I’d discover a whole new world of multicolored Dark-eyed Juncos that have no particular association with snow. These five western varieties, which each breed in a different region, look so distinct from one another that, until the 1970s, they were considered separate species.
But they aren’t separate species—at least, not yet. The regional varieties of junco will still mate and interbreed randomly wherever their ranges meet, which means they are all the same species. “It’s probably speciation in action,” says Ellen Ketterson, an Indiana University biologist who has studied Dark-eyed Juncos for 45 years. “We think we have to go to the Galapagos or Hawaii to see that. But this is a backyard bird that offers that kind of challenge to our understanding.”
The birds' evolutionary story goes back some 10,000 to 13,000 years, to the retreat of North America’s glaciers, according to recent DNA evidence. Before then, the northern half of what is now the United States was smothered in ice. Then, the climate warmed and those glaciers receded, exposing largely unpopulated terrain ripe for colonization. Ancestral juncos (likely Yellow-eyed Juncos or relatives) migrated north and spread across the continent. Since then, some groups became isolated enough to evolve new color variations in what scientists now believe is “one of the fastest cases of speciation known in vertebrates.”
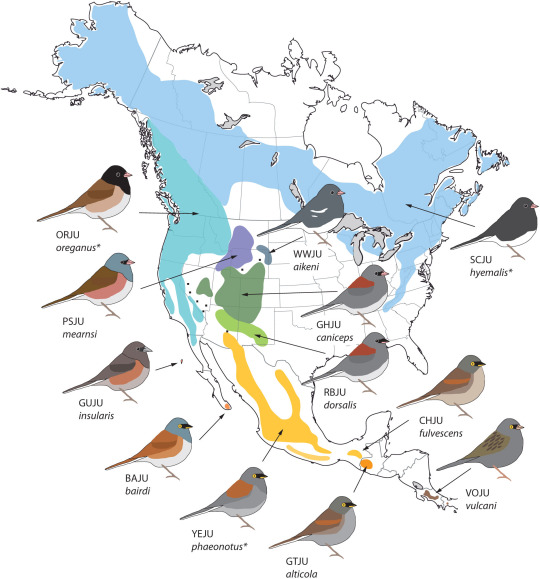
This map by Borja Milá of Museo Nacional de Ciencias Naturales in Madrid, one of Ellen Ketterson's collaborators, shows the various Dark-eyed and Yellow-eyed Junco color varieties across North America. Based on DNA evidence, Milá's work suggests that Dark-eyed Juncos evolved from Yellow-eyed Juncos that migrated north from Mexico into the United States and Canada in the past ~13,000 years after glaciers receded. It includes a Dark-eyed Junco variety not covered in this article: the recently described Guadalupe Junco (GUJU), which breeds only on the tiny Guadalupe Island off the coast of Baja California. (Key, counter-clockwise from top left: ORJU=Oregon; PSJU=Pink-sided; GUJU=Guadalupe; BAJU=Baird's; YEJU=Yellow-eyed; GTJU=Guatemalan Yellow-eyed; VOJU=Volcano; CHJU=Chiapas; RBJU=Red-backed; GHJU=Gray-headed; WWJU=White-winged; SCJU=Slate-colored) Photo: Borja Milá, Museo Nacional de Ciencias Naturales
The different regional junco groups don’t really behave differently (though their songs differ some). They all nest on the ground, eat seeds and bugs, and hop to and fro. “Juncos seem to be acting like juncos pretty much wherever I go,” Ketterson says. “That’s in keeping with this notion that to whatever degree they are different, it’s recent.” In other words, their feather colors have changed—but that’s about it. And feather color is a more flexible trait than you might think.
“All you really need is changes in a gene, or even in regulation of a gene in a known pathway, to turn a feather from white to black, or black to red,” she says. “It’s pretty superficial, literally, and it could happen pretty fast.” The future of these varieties is also uncertain. Modern climate change could further isolate the groups and potentially lead to more varieties—or it could remove the current barriers, allowing them to reproduce with each other in which case they'd lose their differences.
There are about 15 different Dark-eyed Junco subspecies in North America, which can be lumped into the six groups described below. Most of these, aside from the red-backed form, are somewhat migratory—so even though they separate out in summer to breed, in winter they commingle. Out west in winter, you can even spot multiple junco flavors in the same flock.
Slate-colored Junco

This is your classic snowbird, which breeds in forests from Alaska to Newfoundland, north through the boreal forest and south through the Appalachian Mountains to Georgia. A male has a gray head (sometimes closer to black, sometimes tinged brown), chest, back, and wings, and a bright white belly; a female is similar with a paler brown wash.
Oregon Junco

This is the most widespread and variable subspecies group in western North America. The Oregon junco breeds in forest habitats from southern Alaska down to Baja California and east to Nevada. The head of the adult male can vary (by region) from black to medium gray, the wings are gray or brownish gray, and the back and sides vary (again, by region) from dark brown to reddish brown to pinkish. The lower belly is white. A female looks similar, with a paler wash.
Pink-sided Junco

Pink-sided juncos breed in the high-elevation forests of the northern Rocky Mountains, from southern Alberta to eastern Idaho and western Wyoming, including Yellowstone National Park. Males have a medium-gray head and breast, a dark smudge around their eyes, pinkish sides, brown back and wings, and a white belly. Like other Dark-eyed Juncos, the females are browner than the males.
Gray-headed Junco

Males of this group don't only have a medium-gray head, but also gray sides, chest, and belly, with some white on the lower belly. They have a rusty back and, like the pink-sided junco, gray-headed males have a black smudge around their eyes. They breed in the southern Rocky Mountains from Colorado to central Arizona and New Mexico.
White-winged Junco

White-winged males look similar to the slate-colored juncos, but they're larger, with a relatively longer bill and tail, have white wingbars (these are most prominent in fall and winter, after molting, and sometimes wear off, so they can't be relied upon for ID), and significantly more white in the tail. They breed in a small geographical area: the Black Hills of South Dakota, a rugged landscape dotted by ponderosa pines.
Red-backed Junco

These rare juncos live in the southern mountains of Arizona and New Mexico, not far from where Yellow-eyed Juncos range—and they look quite similar to Yellow-eyed Juncos, except for eye color. They sport a bi-colored bill—dark gray on top, silvery on the bottom—a gray head, lighter gray throat and breast, gray and rust wings, a red back, and dark eyes, with a dark eye smudge. They are mostly non-migratory, with some altitudinal migration.
— National Audubon Society, December 25, 2019
1 note
·
View note
Text
How Frontend Developers Can Empower Designer’s Work
How Frontend Developers Can Empower Designer’s Work
Sandrina Pereira
2019-10-16T12:30:59+02:002019-10-17T08:06:08+00:00
This article is mostly directed at you, dear Frontend Developer, who enjoys implementing user interfaces but struggles in aligning expectations with designers you work with. Perhaps you are referred to as the “UI Developer” or “UX Engineer.” Regardless of the title that you carry around, your job (and as well as mine) consists of more than breathing life into design files. We are also responsible for filling the gap between the design and development workflows. However, when crossing that bridge, we are faced with multiple challenges.
Today, I’d like to share with you practical tips that have helped me to collaborate more efficiently with designers in the past years.
I believe it’s our job, as UI Developers, to not only help designers in their journey to learn how the web works, but also to get to know their reality and learn their language.
Understanding UX Designers’ Background
Most of the UX designers (also referred to as Web Designers or Product Designers) out there took their first steps in the design world through tools like Photoshop and Illustrator. Perhaps they were Graphic Designers: their main goal was to create logos and brand identities and to design layouts for magazines. They could also have been Marketing Designers: printing billboards, designing banners and creating infographics.
This means that most UX designers spent their early days designing for print, which is a totally different paradigm from their current medium, the screen. That was their first big challenge. When dealing with print, designers cared about pixel alignment, but on a fixed area (paper). They didn’t have to contend with a dynamic layout (screens). Thinking about text breaking or states of interactions was simply not part of their job either. Designers also had complete freedom over colors, images, and typography without performance constraints.
Fortunately, there have been many efforts from the self-taught UX designers community, to teach development fundamentals, discuss whether designers should learn to code and understand how to best perform hand-off to developers. The same held true for the development side as well (more about that in a minute.) However, there is still friction happening between the two fields.
On the one hand, designers complaining each time an implementation doesn’t match their designs or feeling misunderstood when those are rejected by the developers without a clear explanation. On the other hand, developers might take for granted that designers know something technical when that might not be true. I believe we can all do better than that.
Embracing A New Way Of Thinking
The websites and apps that we are building will be displayed on a wide range of screen sizes. Each person will use them on multiple devices. Our common goal is to create a familiar experience across their journeys.
When we, as developers, think that designers are being picky about pixel alignments, we need to understand why that is. We need to recognize that it’s beyond fidelity and consistency. It’s about the sum of all the parts working together. It’s cohesion. We have to embrace it and do our best to accomplish it. Learning the fundamentals of design principles is a good starting point. Understand the importance of selecting the right colors, how the hierarchy works, and why white space matters.
Note: There’s an online course known as “Design for Developers” and a book called “Refactoring UI” — both are great to get you started. With these, you’ll be able to implement user interfaces with a sharp eye for detail and gain significant leverage when communicating with designers.
Magnifying Your Designers’ Awareness
You might take for granted that designers know the web as much as you do. Well, they might not. Actually, they don’t have to! It’s our responsibility, as developers, to keep them updated with the current state of the web.
I’ve worked with the two sides of this spectrum: Designers who think that anything can be built (such as complex filters, new scroll behaviors or custom form inputs) without giving browser compatibility a thought. Then, there are designers with assumptions about the “low limitations of the web” and just assume by themselves that something is impossible to implement. We need to show them the true possibilities of web design and not let the limitations hold back their skills.
Teach Them Code, Not How To Code
This seems contradictory but bear with me: knowing how to code is at the core of a developer’s job. We work in a fast-paced industry with new stuff popping up every day. It would be a hypocritical request from us to demand designers to learn how to code. However, we can help them to understand code.
Sit next to the designer you work with for 15 minutes and teach them how they can see for themselves whether the specs of an element are correct and how to change them. I find Firefox Page Inspector remarkably user-friendly for this.
Nowadays, it’s a joy to visualize layouts, debug CSS animations and tweak typography. Show them a ready-to-use code playground like Codepen for them to explore. They don’t need to know all CSS specs to understand how the layout paradigm works. However, they need to know how elements are created and behave in order to empower their daily work.
Include Designers In The Development Process
Invite designers to join you in the stand-up meeting, to be part of the QA process and to sit down with you while you refine visual details in your implementations. This will make them understand the constraints of the web and, soon enough, they’ll recognize why a feature takes time to implement.
Ask Designers To Include You In Their Design Process
You’ll realize that they do much more than “make things pretty”. You’ll learn more about the research process and how user testing is done. You’ll discover that for each design proposal they show to you, several other studies were previously dropped. When designers request a change, ask the reason behind it, so you can learn more about the decisions being made. Ultimately, you’ll start to understand why they are picky about white space and alignments, and hopefully, soon you’ll be too!
I find it crucial to treat frontend development as a core part of the design process, and design as a core part of the development process. Advocating a mindset where everyone gets the chance to be involved in the design and development cycle will help us all to better understand each other’s challenges and to create great experiences as well.
We May Use Different Tools, But We Must Speak The Same Language
Now that we are starting to understand each other’s workflow a little better, it’s time for the next step: to speak the same language.
Looking Beyond The Code Editor
Once you start to pay attention to your surroundings, you’ll be better equipped to tackle problems. Get to know the business better and be willing to listen to what designers have to say. That will make you a team member with richer contributions to the project. Collaborating in areas beyond our expertise is the key to creating meaningful conversations and mutual trust.
Using UI Systems As A Contract
Ask designers to share their design system with you (and if they don’t use one, it’s never too late to start). That will save you the bother of handpicking the colors used, figuring out margins or guessing a text style. Make sure you are familiar with the UI System as much as they are.
You might already be familiar with the component-based concept. However, some designers might not perceive it in the same way as you do. Show them how components can help you to build user interfaces more efficiently. Spread that mindset and also say bye-bye to similar-but-not-equal-names: header vs hero, pricing info vs price selector. When a piece of the user interface (a.k.a ‘a component’) is built, stride to use the same names so they can be reflected in both design and code files. Then, when someone says, “We need to tweak the proposal invitation widget,” everyone knows exactly what is being talked about.
Acknowledging The Real Source Of Truth
Despite the fact that the user interface is first created in the design files, the real source of truth is on the development side. At the end of the day, it is what people actually see, right? When a design is updated, it’s a good idea to leave a side note about its development status, especially in projects where a large number of people are involved. This trick helps to keep the communication smooth, so nobody (including you) wonders: “This is different from the live version. Is it a bug or hasn’t so-and-so been implemented just yet?”
Keeping The Debt Under Control
So, you know all about technical debt — it happens when the cost to implement something new is high because of a shortcut we took in the past to meet a deadline. The same can happen on the design side too and we call it design debt.
You can think about it like this: The higher the UX & UI inconsistency, the higher the debt (technical and design). One of the most common inconsistencies is in having different elements to represent the same action. This is why bad design is usually reflected in bad code. It’s up to all of us, both as designers and developers, to treat our design debt seriously.
Being Accessible Doesn’t Mean It Has To Be Ugly
I’m really pleased to see that both we, as developers and designers, are finally starting to bring accessibility into our work. However, a lot of us still think that designing accessible products is hard or limits our skills and creativity.
Let me remind you that we are not creating a product just for ourselves. We are creating a product to be used by all the people, including those who use the product in different ways from you. Take into account how individual elements can be more accessible while keeping the current userflows clear and coherent.
For example, if a designer really believes that creating an enhanced select input is necessary, stand by their side and work together to design and implement it in an accessible way to be used by a wide range of people with diverse abilities.
Giving Valuable Feedback To Designers
It’s unavoidable that questions will pop up when going through the designs. However, that’s not a reason for you to start complaining about the designers’ mistakes or about their ambitious ideas. The designers are not there to drive you mental, they just don’t always intuitively know what you need to do your job. The truth is that, in the past, you didn’t know about this stuff either, so be patient and embrace collaboration as a way of learning.
The Earlier The Feedback, The Better
The timing for feedback is crucial. The feedback workflow depends a lot on the project structure, so there isn’t a one-size-fits-all solution for it. However, when possible, I believe we should aim for a workflow of periodic feedback — starting in the early stages. Having this mindset of open collaboration is the way to reduce the possibility of unexpected big re-iterations later in the road. Keep in mind that the later you give the designer your first feedback, the higher will be the cost for them to explore a new approach if needed.
Explain Abstract Ideas In Simple Terms
Remember when I said that performance was not a concern of the designers’ previous jobs? Don’t freak out when they are not aware of how to create optimized SVGs for the web. When faced with a design that requires a lot of different fonts to be loaded, explain to them why we should minimize the number of requests, perhaps even take advantage of Variable Fonts. Asides from loading faster, it also provides a more consistent user experience. Unless designers are keen to learn, avoid using too many technical terms when explaining something. You can see this as an opportunity of improving your communication skills and clarifying your thoughts.
Don’t Let Assumptions Turn Into Decisions
Some questions about a design spec only show up when we get our hands dirty in the code. To speed things up, we might feel tempted to make decisions based on our assumptions. Please, don’t. Each time you turn an assumption into a decision, you are risking the trust that the design team puts on you to implement the UI. Whenever in doubt, reach out and clarify your doubts. This will show them that you care about the final result as much as they do.
Don’t Do Workarounds By Yourself
When you are asked to implement a design that is too hard, don’t say “It’s impossible” or start to implement a cheap alternative version of it by yourself. This immediately causes friction with the design team when they see their designs were not implemented as expected. They might react angrily, or not say anything but feel defeated or frustrated. That can all be avoided if we explain to them why something it’s not possible, in simple terms and suggest alternative approaches. Avoid dogmatic behaviors and be open to collaborating on a new solution.
Let them know about the Graceful Degradation and Progressive Enhancement techniques and build together an ideal solution and a fallback solution. For example, we can enhance a layout from flexbox to CSS Grid. This allows us to respect the core purpose of a feature and at the same time make the best use of web technologies.
When it comes to animations, let’s be real: deep down you are as thrilled to implement the next wow animation as much as the designers are to create it. The difference between us and them is that we are more aware of the web’s constraints. However, don’t let that limit your own skills! The web evolves fast, so we must use that in our favor.
The next time you are asked to bring a prototype to life, try not to reject it upfront or do it all by yourself. See it as an opportunity to push yourself. Animations are one of the pickiest parts of web development, so make sure to refine each keyframe with your designer — in person or by sharing a private synced link.
Think Beyond The Ideal State — Together
Here’s the thing: it’s not all about you. One of the designers’ challenges is to really understand their users and present the designs in the most attractive way to sell to the Product Manager. Sometimes they forget about what’s beyond the ideal state and developers forget it too.
In order to help avoid these gaps from happening, align with designers the scenario requirements:
The worst-case scenario
A scenario where the worst possibilities are happening. This helps designers to say no to fixed content and let it be fluid. What happens if the title has more than 60 characters or if the list is too long? The same applies to the opposite, the empty scenario. What should the user do when the list is empty?
Interaction states
The browser is more than hovering and clicking around. There are a bunch of states: default, hover, focus, active, disable, error… and some of them can happen at the same time. Let’s give them the proper attention.
The loading state
When building stuff locally, we might use mocks and forget that things actually take time to load. Let designers know about that possibility too and show them that are ways to make people perceive that things don’t take that long to load.
Taking into consideration all these scenarios will save you a lot of time going back and forth during the development phase.
Note: There’s a great article by Scott Hurff about how to fix bad user interfaces that will take us a step closer to an accessible product.
Embrace Change Requests
Developers are known for not being too happy about someone finding a bug in their code — especially when it’s a design bug reported by a designer. There are a lot of memes around it, but have you ever reflected how those bugs can compoundingly rot both the quality of the experience as well as your relationship when these design bugs are casually dismissed? It happens slowly, almost like falling asleep. Bit by bit, then all at once. Designers might start out saying, “It’s just a tiny little detail,” until the indifference and resentment builds up and nothing is said. The damage has then already been done.
This situation is two-fold: both to your peers and to your work. Don’t let that happen. Work on what’s coloring your reaction. A designer being ‘picky’ can be inconvenient, but it can also be an engineer’s shallow interpretation of attentiveness and enthusiasm. When someone tells you that your implementation is not perfect (yet), put your ego aside and show them how you recognize their hard work in refining the final result.
Go Off The Record Once In A While
We all have tasks to deliver and roadmaps to finish. However, some of the best work happens off the record. It won’t be logged into the TO DO board and that’s okay. If you find a designer you have a rapport with, go sneak into their workspace and explore together new experiments. You never know what can come from there!
Conclusion
When you are willing to learn from the design team, you are also learning different ways of thinking. You’ll evolve your mindset of collaboration with other areas out of your experience while refining your eye for creating new experiences. Be there to help and be open to learning, because sharing is what makes us better.
This article wouldn’t be possible without the feedback of many great people. I want to gratefully thank to the designers Jasmine Meijer and Margarida Botelho for helping me to share a balanced perspective about the misunderstandings between designers and developers.
Related Reading on SmashingMag:
“Design For Developers” by Mason Gentry
“Working Together: How Designers And Developers Can Communicate To Create Better Projects” by Rachel Andrew
“How Frontend Developers Can Help To Bridge The Gap Between Designers And Developers” by Stefan Kaltenegger
“Which Podcasts Should Web Designers And Developers Be Listening To?” by Ricky Onsman

(ra, yk, il)
0 notes
Text
How Frontend Developers Can Empower Designer’s Work
How Frontend Developers Can Empower Designer’s Work
Sandrina Pereira
2019-10-16T12:30:59+02:002019-10-16T10:36:17+00:00
This article is mostly directed at you, dear Frontend Developer, who enjoys implementing user interfaces but struggles in aligning expectations with designers you work with. Perhaps you are referred to as the “UI Developer” or “UX Engineer.” Regardless of the title that you carry around, your job (and as well as mine) consists of more than breathing life into design files. We are also responsible for filling the gap between the design and development workflows. However, when crossing that bridge, we are faced with multiple challenges.
Today, I’d like to share with you practical tips that have helped me to collaborate more efficiently with designers in the past years.
I believe it’s our job, as UI Developers, to not only help designers in their journey to learn how the web works, but also to get to know their reality and learn their language.
Understanding UX Designers’ Background
Most of the UX designers (also referred to as Web Designers or Product Designers) out there took their first steps in the design world through tools like Photoshop and Illustrator. Perhaps they were Graphic Designers: their main goal was to create logos and brand identities and to design layouts for magazines. They could also have been Marketing Designers: printing billboards, designing banners and creating infographics.
This means that most UX designers spent their early days designing for print, which is a totally different paradigm from their current medium, the screen. That was their first big challenge. When dealing with print, designers cared about pixel alignment, but on a fixed area (paper). They didn’t have to contend with a dynamic layout (screens). Thinking about text breaking or states of interactions was simply not part of their job either. Designers also had complete freedom over colors, images, and typography without performance constraints.
Fortunately, there have been many efforts from the self-taught UX designers community, to teach development fundamentals, discuss whether designers should learn to code and understand how to best perform hand-off to developers. The same held true for the development side as well (more about that in a minute.) However, there is still friction happening between the two fields.
On the one hand, designers complaining each time an implementation doesn’t match their designs or feeling misunderstood when those are rejected by the developers without a clear explanation. On the other hand, developers might take for granted that designers know something technical when that might not be true. I believe we can all do better than that.
Embracing A New Way Of Thinking
The websites and apps that we are building will be displayed on a wide range of screen sizes. Each person will use them on multiple devices. Our common goal is to create a familiar experience across their journeys.
When we, as developers, think that designers are being picky about pixel alignments, we need to understand why that is. We need to recognize that it’s beyond fidelity and consistency. It’s about the sum of all the parts working together. It’s cohesion. We have to embrace it and do our best to accomplish it. Learning the fundamentals of design principles is a good starting point. Understand the importance of selecting the right colors, how the hierarchy works, and why white space matters.
Note: There’s an online course known as “Design for Developers” and a book called “Refactoring UI” — both are great to get you started. With these, you’ll be able to implement user interfaces with a sharp eye for detail and gain significant leverage when communicating with designers.
Magnifying Your Designers’ Awareness
You might take for granted that designers know the web as much as you do. Well, they might not. Actually, they don’t have to! It’s our responsibility, as developers, to keep them updated with the current state of the web.
I’ve worked with the two sides of this spectrum: Designers who think that anything can be built (such as complex filters, new scroll behaviors or custom form inputs) without giving browser compatibility a thought. Then, there are designers with assumptions about the “low limitations of the web” and just assume by themselves that something is impossible to implement. We need to show them the true possibilities of web design and not let the limitations hold back their skills.
Teach Them Code, Not How To Code
This seems contradictory but bear with me: knowing how to code is at the core of a developer’s job. We work in a fast-paced industry with new stuff popping up every day. It would be a hypocritical request from us to demand designers to learn how to code. However, we can help them to understand code.
Sit next to the designer you work with for 15 minutes and teach them how they can see for themselves whether the specs of an element are correct and how to change them. I find Firefox Page Inspector remarkably user-friendly for this.
Nowadays, it’s a joy to visualize layouts, debug CSS animations and tweak typography. Show them a ready-to-use code playground like Codepen for them to explore. They don’t need to know all CSS specs to understand how the layout paradigm works. However, they need to know how elements are created and behave in order to empower their daily work.
Include Designers In The Development Process
Invite designers to join you in the stand-up meeting, to be part of the QA process and to sit down with you while you refine visual details in your implementations. This will make them understand the constraints of the web and, soon enough, they’ll recognize why a feature takes time to implement.
Ask Designers To Include You In Their Design Process
You’ll realize that they do much more than “make things pretty”. You’ll learn more about the research process and how user testing is done. You’ll discover that for each design proposal they show to you, several other studies were previously dropped. When designers request a change, ask the reason behind it, so you can learn more about the decisions being made. Ultimately, you’ll start to understand why they are picky about white space and alignments, and hopefully, soon you’ll be too!
I find it crucial to treat frontend development as a core part of the design process, and design as a core part of the development process. Advocating a mindset where everyone gets the chance to be involved in the design and development cycle will help us all to better understand each other’s challenges and to create great experiences as well.
We May Use Different Tools, But We Must Speak The Same Language
Now that we are starting to understand each other’s workflow a little better, it’s time for the next step: to speak the same language.
Looking Beyond The Code Editor
Once you start to pay attention to your surroundings, you’ll be better equipped to tackle problems. Get to know the business better and be willing to listen to what designers have to say. That will make you a team member with richer contributions to the project. Collaborating in areas beyond our expertise is the key to creating meaningful conversations and mutual trust.
Using UI Systems As A Contract
Ask designers to share their design system with you (and if they don’t use one, it’s never too late to start). That will save you the bother of handpicking the colors used, figuring out margins or guessing a text style. Make sure you are familiar with the UI System as much as they are.
You might already be familiar with the component-based concept. However, some designers might not perceive it in the same way as you do. Show them how components can help you to build user interfaces more efficiently. Spread that mindset and also say bye-bye to similar-but-not-equal-names: header vs hero, pricing info vs price selector. When a piece of the user interface (a.k.a ‘a component’) is built, stride to use the same names so they can be reflected in both design and code files. Then, when someone says, “We need to tweak the proposal invitation widget,” everyone knows exactly what is being talked about.
Acknowledging The Real Source Of Truth
Despite the fact that the user interface is first created in the design files, the real source of truth is on the development side. At the end of the day, it is what people actually see, right? When a design is updated, it’s a good idea to leave a side note about its development status, especially in projects where a large number of people are involved. This trick helps to keep the communication smooth, so nobody (including you) wonders: “This is different from the live version. Is it a bug or hasn’t so-and-so been implemented just yet?”
Keeping The Debt Under Control
So, you know all about technical debt — it happens when the cost to implement something new is high because of a shortcut we took in the past to meet a deadline. The same can happen on the design side too and we call it design debt.
You can think about it like this: The higher the UX & UI inconsistency, the higher the debt (technical and design). One of the most common inconsistencies is in having different elements to represent the same action. This is why bad design is usually reflected in bad code. It’s up to all of us, both as designers and developers, to treat our design debt seriously.
Being Accessible Doesn’t Mean It Has To Be Ugly
I’m really pleased to see that both we, as developers and designers, are finally starting to bring accessibility into our work. However, a lot of us still think that designing accessible products is hard or limits our skills and creativity.
Let me remind you that we are not creating a product just for ourselves. We are creating a product to be used by all the people, including those who use the product in different ways from you. Take into account how individual elements can be more accessible while keeping the current userflows clear and coherent.
For example, if a designer really believes that creating an enhanced select input is necessary, stand by their side and work together to design and implement it in an accessible way to be used by a wide range of people with diverse abilities.
Giving Valuable Feedback To Designers
It’s unavoidable that questions will pop up when going through the designs. However, that’s not a reason for you to start complaining about the designers’ mistakes or about their ambitious ideas. The designers are not there to drive you mental, they just don’t always intuitively know what you need to do your job. The truth is that, in the past, you didn’t know about this stuff either, so be patient and embrace collaboration as a way of learning.
The Earlier The Feedback, The Better
The timing for feedback is crucial. The feedback workflow depends a lot on the project structure, so there isn’t a one-size-fits-all solution for it. However, when possible, I believe we should aim for a workflow of periodic feedback — starting in the early stages. Having this mindset of open collaboration is the way to reduce the possibility of unexpected big re-iterations later in the road. Keep in mind that the later you give the designer your first feedback, the higher will be the cost for them to explore a new approach if needed.
Explain Abstract Ideas In Simple Terms
Remember when I said that performance was not a concern of the designers’ previous jobs? Don’t freak out when they are not aware of how to create optimized SVGs for the web. When faced with a design that requires a lot of different fonts to be loaded, explain to them why we should minimize the number of requests, perhaps even take advantage of Variable Fonts. Asides from loading faster, it also provides a more consistent user experience. Unless designers are keen to learn, avoid using too many technical terms when explaining something. You can see this as an opportunity of improving your communication skills and clarifying your thoughts.
Don’t Let Assumptions Turn Into Decisions
Some questions about a design spec only show up when we get our hands dirty in the code. To speed things up, we might feel tempted to make decisions based on our assumptions. Please, don’t. Each time you turn an assumption into a decision, you are risking the trust that the design team puts on you to implement the UI. Whenever in doubt, reach out and clarify your doubts. This will show them that you care about the final result as much as they do.
Don’t Do Workarounds By Yourself
When you are asked to implement a design that is too hard, don’t say “It’s impossible” or start to implement a cheap alternative version of it by yourself. This immediately causes friction with the design team when they see their designs were not implemented as expected. They might react angrily, or not say anything but feel defeated or frustrated. That can all be avoided if we explain to them why something it’s not possible, in simple terms and suggest alternative approaches. Avoid dogmatic behaviors and be open to collaborating on a new solution.
Let them know about the Graceful Degradation and Progressive Enhancement techniques and build together an ideal solution and a fallback solution. For example, we can enhance a layout from flexbox to CSS Grid. This allows us to respect the core purpose of a feature and at the same time make the best use of web technologies.
When it comes to animations, let’s be real: deep down you are as thrilled to implement the next wow animation as much as the designers are to create it. The difference between us and them is that we are more aware of the web’s constraints. However, don’t let that limit your own skills! The web evolves fast, so we must use that in our favor.
The next time you are asked to bring a prototype to life, try not to reject it upfront or do it all by yourself. See it as an opportunity to push yourself. Animations are one of the pickiest parts of web development, so make sure to refine each keyframe with your designer — in person or by sharing a private synced link.
Think Beyond The Ideal State — Together
Here’s the thing: it’s not all about you. One of the designers’ challenges is to really understand their users and present the designs in the most attractive way to sell to the Product Manager. Sometimes they forget about what’s beyond the ideal state and developers forget it too.
In order to help avoid these gaps from happening, align with designers the scenario requirements:
The worst-case scenario
A scenario where the worst possibilities are happening. This helps designers to say no to fixed content and let it be fluid. What happens if the title has more than 60 characters or if the list is too long? The same applies to the opposite, the empty scenario. What should the user do when the list is empty?
Interaction states
The browser is more than hovering and clicking around. There are a bunch of states: default, hover, focus, active, disable, error… and some of them can happen at the same time. Let’s give them the proper attention.
The loading state
When building stuff locally, we might use mocks and forget that things actually take time to load. Let designers know about that possibility too and show them that are ways to make people perceive that things don’t take that long to load.
Taking into consideration all these scenarios will save you a lot of time going back and forth during the development phase.
Note: There’s a great article by Scott Hurff about how to fix bad user interfaces that will take us a step closer to an accessible product.
Embrace Change Requests
Developers are known for not being too happy about someone finding a bug in their code — especially when it’s a design bug reported by a designer. There are a lot of memes around it, but have you ever reflected how those bugs can compoundingly rot both the quality of the experience as well as your relationship when these design bugs are casually dismissed? It happens slowly, almost like falling asleep. Bit by bit, then all at once. Designers might start out saying, “It’s just a tiny little detail,” until the indifference and resentment builds up and nothing is said. The damage has then already been done.
This situation is two-fold: both to your peers and to your work. Don’t let that happen. Work on what’s coloring your reaction. A designer being ‘picky’ can be inconvenient, but it can also be an engineer’s shallow interpretation of attentiveness and enthusiasm. When someone tells you that your implementation is not perfect (yet), put your ego aside and show them how you recognize their hard work in refining the final result.
Go Off The Record Once In A While
We all have tasks to deliver and roadmaps to finish. However, some of the best work happens off the record. It won’t be logged into the TO DO board and that’s okay. If you find a designer you have a rapport with, go sneak into their workspace and explore together new experiments. You never know what can come from there!
Conclusion
When you are willing to learn from the design team, you are also learning different ways of thinking. You’ll evolve your mindset of collaboration with other areas out of your experience while refining your eye for creating new experiences. Be there to help and be open to learning, because sharing is what makes us better.
This article wouldn’t be possible without the feedback of many great people. I want to gratefully thank to the designers Jasmine Meijer and Margarida Botelho for helping me to share a balanced perspective about the misunderstandings between designers and developers.
Related Reading on SmashingMag:
“Design For Developers” by Mason Gentry
“Working Together: How Designers And Developers Can Communicate To Create Better Projects” by Rachel Andrew
“How Frontend Developers Can Help To Bridge The Gap Between Designers And Developers” by Stefan Kaltenegger
“Which Podcasts Should Web Designers And Developers Be Listening To?” by Ricky Onsman

(ra, yk, il)
0 notes
Text
Have less than one year before Microsoft cuts off Windows 7
When Windows 10 launched in 2015, PC users were confronted with a dilemma. Microsoft had in many enthusiasts eyes been making blunder after blunder in their efforts to turn what we all thought was a perfectly functional operating system into some kind of idiot, friendly, touchscreen fisher-price. Looking nonsense and on top of trying to fix what ain't broke, Microsoft wanted unprecedented access to their users, data and resolved to just force system updates when you're right in the middle of something and all for what DirectX 12. So many power users ended up sticking with Windows 7 and are still using it today, but they have a problem. If you're one of these individuals, you now have less than one year before Microsoft, cuts off Windows 7.
You may not want to risk an upgrade, but, as Aragorn said, to fit in in the Great Hall of EDS upgrading is upon you whether you would risk it or not. Wait. I don't think that's quite what he said. You know what else is close. I can almost smell it. So close, that's our sponsor! It won't help you with your Windows, 7 problem, but they still G skills. Trident II royal series, ddr4 memory, features a polished, aluminium heat spreader, that's available in both gold or silver and a crystalline light bar that radiates beautiful RGB check it out at the link below [ Music ].
Now you might not realize this, but in spite of Microsoft, practically giving away Windows 10 even to those with pirated installations, most users stuck with Windows 7, rather than upgrading, either to eight or ten something that only finally changed late last year in December, net market share Reported that Windows 10 installations rose above Windows 7 for the first time and now account for nearly 41 percent of the user base compared to Windows 7 37 percent. Now, hopefully, that number is going to continue to go down as we get closer to January 14. 2020.
The day that Windows 7 dies because otherwise we are gon na - have some serious problems because, yes, yes, ok, Windows, 7, it's not gon na die. It'S not like you just turn on your computer and it doesn't turn on anymore. It'S just going to stop receiving feature, updates, bug, fixes and, most importantly, security updates, which are very important if you want to, I don't know, continue Oh safe using the Internet. Now, as it did for previous versions of Windows, Microsoft is offering extended security updates, or, yes, you, ECU for Windows, 7 enterprise and pro additions up until January 2023. But this extended the update service won't come cheap and adding insult to injury. The price will double each year, so three years of support is gon na cost.
A hundred and seventy-five bucks for enterprise licenses and three hundred and fifty for windows 7 pro og, also, if you're a mega ball or PC gamer thinking, yeah no problem. 350 bucks looks like what mid tier graphics card. Sorry, I've got some bad news for you, too. Esu is only available for volume license subscriptions which are usually held by companies or schools. So business is running Windows, 7 machines on Microsoft's, Azure cloud as part of the Windows virtual desktop program, those folks get ESU for free, but again baller gamers. I would imagine that scenario doesn't apply to you. So then, if you're just a regular Windows, 7 user with a personal license, what can you do well before we get too deep into your options?
Let'S take a look at why people want to hold on to Windows 7, like that grudge against their brother for stealing the last piece of their birthday cake, even though they told them that they were saving it for later and hid it away way in the back Of the fridge - so you wouldn't know it was there Windows 7 was, is kind of fantastic. It'S mature, stable and reliable and offers a great amount of control over the way it behaves. Its interface is functional, familiar and extremely customizable, and it's got all your settings just the way that you like them. I mean. Furthermore, I wouldn't be surprised if anyone upgrading now has a program or two that would either require a new, not to mention costly license to run on Windows 10 or that isn't available for it at all and there's other little creature comforts typing in the search bar Retrieves results that make sense instead of a Windows setting you weren't, looking for or a web result from big windows, 7.
Doesn'T incessantly ask you to send more of your personal information to Microsoft or decide on its own when it's time to update whether you like it or not, updates are available? Sorry, you know what I'm actually kind of in the middle of something kind of Roger that updating now, but as awesome as Windows 7 is. There are quite a few cons to staying with it past the end date for extended support. Besides lacking the latest antivirus protections, Windows 7 won't have Windows, 10 features like device guard, UEFI, secure boot and Windows, hello, which offer higher overall security for your system, and while gaming performance is about the same, some things like system boot times are slower in Windows 7.
Compared to Windows 10, so it turns out Microsoft, software engineers weren't sitting around playing beer pong for the last 78 years. Also, if you're worried about future proofing at all, which you should be at least a little bit. Windows, 7 is not a great bet, as software and even hardware makers eventually do stop providing support for legacy operating systems. So, even if you pay for es, you support only lasts for three years and costs more than a Windows 10 license and you might be able to upgrade for free anyway, yep, even though Microsoft officially ended their offer for a free upgrade to Windows. 10 from Windows. 7 or 8 many users have reported successful, fully activated upgrades by using Microsoft's official upgrade utility, and even if you have to pay bare with me for a moment here, Windows 10 might not be as bad as you think. There are a lot of happy users out there who appreciate its combination of the efficiency and customization of Windows 7 and the modern design of Windows 8 and despite Microsoft's best efforts.
There is actually a fair bit that you can do to minimize their data collection and postpone system updates until absolutely necessary, or at least until it's convenient, so we're gon na have some resources for you guys for this linked in the video description. But let's say you drop a line at Windows: 10. Fine, you say I'll! Stop using Windows 7, but hashtag, never Windows, 10 whoo tell you guys are serious cuz that hashtag there well, for you guys. There are other options. First up, there's Windows. 8.1. I mean I doubt that you guys have stuck with Windows 7 for this long, just to get into the OS that Gabe Newell called a catastrophe, and it's data, collection and update system are kind of similar to Windows 10, but at least it'll be getting security updates,
Though, realistically now that Microsoft has learned from their mistake of supporting Windows, XP for like ever that'll, probably only buy you a couple of years. So maybe that's not a great option. So then, what how about Oh Mac OS, while Apple's desktop OS, has come a long way and is obviously used by many tech enthusiasts? The thing is, I don't see many windows, 7 diehards willingly affecting to apples Camp Plus. You would need to either buy a totally new computer or begin the long, arduous process of trying to turn your existing PC into a hackintosh. Now it might be doable, but even most hackintosh enthusiasts are pretty open about what a finicky experience that is leaving Linux. Now, a couple of years ago,
I would have said that that's madness, but Linux is a more viable option than ever before, even for gamers. Now we're planning another follow-up, video on Valve's proton compatibility software, but for now the main thing you need to know about it is that it makes an ever growing list of Windows. Games run flawlessly on Linux and community reports indicate that thousands more run pretty well. As for the non-gamers popular Linux, distros like Ubuntu work great for productivity, focused views, especially if the majority of your work is done on the web, and there are even distros that borrow heavily from Windows for their interface, like Linux Mint. So your homesickness will at least be saved a little and then, of course, there's the last option. Stick with Windows 7 hold fast as your destruction edges ever closer.
So you goodbye to hardware or software upgrades and just well just don't browse the internet after January 14th. 2012, with regards to that option, I mean you know what Godspeed you brave bastard, but, needless to say, we don't actually recommend doing that. What we do recommend, though, if you need to build a beautiful website without the hassle, is Squarespace with Squarespace is all in one platform, you just pick a template and turn your text throw in your pictures, design a logo they've got all kinds of amazing tools and Boom, you have a website, it might not be a very good website. It might not have a lot of important information on it, but that's on you, sir or ma'am. It'S not on Squarespace, because they have tons of amazing help that you can leverage they offer webinars. Full series of help guides and you can contact their 24/7 customer support via live chat and email.
If you're ever having trouble, and if you already have a third party domain, you don't have to give it up, you can just transfer it to Squarespace plus with Squarespace. You get tons of e-commerce features to help you sell merch or services online and easily manage your inventory and orders so head over to Squarespace comm /l tt and get 10 % off your first purchase. We'Re gon na have that linked below. So thanks for watching guys, we just like this video. You can hit that button. I'M sorry! It'S a really bad news. I get it, but if you liked it hit like get subscribed or maybe consider checking out where to buy the stuff, we featured Windows 10. I guess at the link in the video description also down, there is our merch store, which has cool shirts like this one and our community forum, which you should totally join. We should have where you can now buy it, a bunch of CD canonical we'll ship. You one if you pay like a couple bucks, I think you can yeah but and don't pay for Linux either way. It'S free. It'S kind of the point.
0 notes
Text
Why are people so hyped about EOS and EOSIO? Is EOS Ethereum’s biggest competition
Why are people so hyped about EOS and EOSIO? Is EOS Ethereum’s biggest competition
After staying a year in its Initial Coin Offering (ICO) stage, EOS or Block.one finally started launching version 1.0 of their open-source blockchain protocol – EOSIO. EOSIO is a platform and an ecosystem that will allow developers to build applications for commercial and corporate use cases. The project is more than anticipated, as cryptocurrency enthusiast have invested in the Initial Coin Offering more than a year ago. EOS was first introduced in 2017 and the only question for this time period was: Will EOS live up to the hype and deliver a great product?
Their whitepaper sure sounds great with free transactions, millions of transactions per second and a platform that will allow developers to build great applications. EOS can be a great competitor to Ethereum, providing similar or better solutions, but the project has a lot to prove. Block.one raised more than 4$ billion in its record breaking year-long Initial Coin Offering, which broke the previous record that Telegram set earlier this year. Telegram broke the records, raising 1.7$ billion in two private pre-sales, later canceling its Initial Coin Offering because of the raised large amount.
What is EOS and EOSIO?
The stakes are high for Block.one and EOS, but if executed right EOS might facilitate itself as a leading cryptocurrency. Currently, EOS is 5th by market cap and has already attacked the leaders, overtaking some of the previous leaders like Litecoin, Stellar, Cardano and IOTA. EOS will be a decentralized blockchain platform and network with new or updated key features. The EOSIO software will have improved database, authentication, communication, accounts, application features and scheduling between multiple cores.
EOS will allow developers to build blockchain applications on its platform that can scale between commercial and large scale business applications. These applications will be similar to Ethereum’s, but will provide more scalability potential. The launch of the 1.0 version of EOSIO is a crucial moment for Block.one, the whole project and a beginning of EOS’ potential. EOSIO will be maintained by a Delegated Proof of Stake system, that was originally created by Larimer and his platform – Steemit. This Delegated Proof of Stake system will be used for achieving consensus and is going to address some issues of Proof of Stake and Proof of Work.
Also, EOS’ Delegated Proof of Stake (DPoS) system will allow EOS users to vote on who will be the block producers. They will be responsible for validating transactions and maintaining the blockchain ecosystem. For their work, they will be rewarded with tokens and will constantly be evaluated by the EOS community. If the community is not satisfied by the block producers’ work, they can be fired if the community reaches a consensus by voting. If block producers fail to validate transactions, slow transaction speed, fail to create blocks or others, they won’t be long for the job. A report on EOS came out from the Ledger Inter Dossier, in which it became clear that Steemit’s Delegated Proof of Stake system currently handles thousands of transactions per second. This is a great sign for EOSIO and EOS’ future.
The EOS token sale started back in June of last year and it started as an ERC-20 token. EOS token holders had to register their ERC-20 tokens for a token swap, until earlier this week. All unregistered tokens are virtually useless now and all others were converted in EOS tokens on the platform. The native EOS token will give its owners the right to vote on future development of the project, miners and maintaining the ecosystem and network. Also, users of EOS-based applications will have access to a proportionate amount of resources to the amount of tokens that is staked in these applications. Click here to read just how rich are the richest EOS wallets and addresses.
EOS and Block.one are dedicated on the ecosystem’s future development
As I mentioned above, EOS raised around 4$ billion in their year-long Initial Coin Offering stage. But the company behind EOS, Block.one also managed to raise 50$ million funding from SVK Crypto, a blockchain investment company. They are based in London and they will invest in companies that will build decentralized applications on the EOSIO ecosystem. Mostly, they are focused on investing in decentralized projects that will be connected to social media, technology platforms, logistics or data ownership and security.
Block.one also has a Venture Capital funding program called EOS VC that aims to provide EOS developers and corporations with funding of their projects that use the EOSIO platform. Furthermore, the EOS VS program is dedicated to raise more than 1$ billion that will be used for the funding of future EOSIO projects and decentralized applications. The fund includes the 325$ million EOSIO Ecosystem Fund with Galaxy Digital LP. From all of this, it looks that EOS and Block.one are dedicated to invest in EOS’ future and the future development of the ecosystem.
Block.one’s dedication on developing the system is demonstrated in their decision to let the EOS community solve most of the initial problems that the EOSIO ecosystem has. They used the bounty platform HackerOne to launch a bounty program for bugs to improve their ecosystem and to reward developers who actively help in the system’s development. A software security researcher took full advantage of this and earned 120,000$ in just a week by solving EOS bugs. He discovered twelve vulnerabilities in the EOS software and earned 10,000$ for every bug he solved.
The software security researcher, Guido Vranken used this bounty program from HackerOne and his skills to discover existing bugs in the network. He found twelve bugs and earned himself 120,000$ for his services. He took to Twitter to mention his accomplishments. EOS thanked him and another security developer for their services. Block.one was so impressed that they even offered Guido Vranken a permanent job in the company, but there is no information about if he accepted or not. But he probably didn’t as his expertise allows him to be useful and needed everywhere. Vranken had previous experience in finding software bugs. His fixed software bugs count is around 92, as he has found previously software bugs in big corporations like Slack, Tor, Twitter, OpenSSL, Python, Dropbox, Trello, HackerOne and Yahoo!.
Thank you. A couple more waiting to be rewarded. I think the final tally was $120K but I lost count. Took me about a week.
— Guido Vranken (@GuidoVranken) June 4, 2018
Is EOS and EOSIO the best rival to Ethereum?
The whitepaper of EOS promises to deliver a great project, but we will have to see what will be the end product of Block.one. EOSIO and EOS look promising, but they still have a long way to go. Block.one secured an immense amount of funding for the project, so this has been taken care of. A lot of beta versions of EOSIO have been released previously, with more than 1000 bugs and issues already fixed. Still more than 500 issues are left for the community and developers to fix. Despite the setbacks, over a hundred projects are currently under development on the EOSIO system.
The most famous of these projects is probably Everipedia, which will be an online encyclopedia that will reward its user base with tokens, native to the ecosystem. One of the co-founders of Wikipedia, Larry Sanger is also part of the Everipedia team and is helping with its development. He wants to combat the centralization that is happening with Wikipedia currently.
“The biggest problem today with online information is that it’s controlled by very few players and centralized. This benefits to have only the most hype-driven and salacious information. We can do much better!”
Everipedia is also planning an Airdrop of its tokens to EOS holders. Click here to read more on Everipedia in this quick article.
We will keep our eyes on EOSIO and its great potential. It will be interesting to see how will the network unfold and the upcoming DAPPs. EOS’ feature to allow the creation of DAPPs is a direct competitor to Ethereum. Ethereum’s founder, Vitalik Buterin expressed his concerns on EOS’ DPoS:
“If you try to ensure decentralization, Delegated Proof of Stake will allow all coin holders to vote on who will be the nodes the will run the consortium chain. This, together with the lack of in-protocol economic incentives for these master nodes to behave correctly, and the lack of client-side validation capability, means that there is an extreme reliance on the voting mechanism… Another substantial concern is with voting: in order to win the vote, any delegate would need to have a visible public identity. Anonymous delegating would be very difficult to sustain in the long term. This makes the entire system substantially more vulnerable to political attacks.”
Block.one’s CEO countered Vitalik Buterin on Steemit, by providing points that counter Ethereum’s Proof of Stake algorithm. He said:
“Low voter participation has been addressed over the past 3 years through a combination of voting proxies, easier user interfaces and a reduction on the things that people have to vote for… Furthermore, non-voters do not make things less secure. They keep tokens off the market which still makes it more expensive for an attacker to acquire stake. Whale stakeholders have a huge incentive to vote to protect their wealth and an attacker would have to acquire more stake than the largest whales in the system… Last, EOS is designed around the idea that service providers (DAPP Developers) should cover network costs, not the users. A good application needs a monetization strategy that is independent of network operations. The existence of Steem is all the proof we need to demonstrate the value of free transactions and how we solve the issues with needing stake.”
Both sides have interesting points of view. Competition is great for the technology’s development, so as interesting this feud is, it will be healthy for both projects. With both projects potential being through the roof, only future development of their technology will show us where they are heading. In my opinion both projects are one of the most interesting on the market and if they deliver, they will be among the leaders in the following years.
Stay tuned for an in-depth EOS guide in the following days!
https://ift.tt/2JzN6UV
0 notes
Text
Term 3 Reflection
For your comfort, here is a summary of the stuff I done did this term, and a bit of last term because I can’t remember when exactly Term 2 became Term 3.
Learning Objective 1: Increased awareness of your own strengths and areas for growth
Activity: Going to India for my Duke of Edinburgh award was such an eye opener into just how beneficial doing Bukit Shahbandar is for endurance. Although the altitude was definitely a bit of an obstacle, all those weeks of hiking up and down hills meant that I wasn’t sore after any section of the final expedition. Whilst my fitness was good and the trekking was fine, I noticed that strength is definitely not my strongest (haha, pun intended) asset. Lugging mud bricks to and from the greenhouse made me realise that I was getting tired more quickly than others; if I want to grow in this area, I’d need to start doing more physically straining activities in the future.
Service: I think that by putting in that little bit extra effort, I’ve shown that I am able to make Blackeye have more House spirit. Just by showing enthusiasm with the face paint and sliced oranges, or actually showing up to support the house can have a huge effect on morale, so I want to keep this up next term as I think I can improve it even more and hopefully get the girls in the house to feel a bit more closer to each other.
Learning Objective 2: Undertaking new challenges
Creativity: Singing has definitely been my biggest challenge this year, and I think that I’ve tackled it head on. Grade 8, as the highest level, is naturally difficult, but I passed with merit whilst balancing my workload and other activities. Although I’m still not sure I could get up and sing solo in front of an audience just yet, doing Showcase put me on stage for the first time; at first I was getting anxious over singing one line for a mic-check but by the end of it I wasn’t nearly as bothered.
Activity: Endured an 18 hour bus ride with the same 30 people? Check. Travelled along the Rohtang Pass, one of the most dangerous roads in the world? Check. Adjusted to lower levels of Oxygen? Check. Trekked to the highest post office and beyond? Check. India was full of challenges, and I like to think that, given that I’m alive today, I overcame every single one. As I mentioned earlier, the altitude was the hardest thing to adjust to, as every single action required more effort. Nonetheless, once the initial headaches and queasiness passed, the high altitudes were just part and parcel of the whole expedition, and we just got on with it.
Service: Planning and executing the Shoebox drive had its challenges in organising the school. We relied on the houses to read our emails and follow our instructions, but inevitably there were some hiccups, and things didn’t go to plan. I had to go out and buy extra supplies which could be used to pad out boxes which were looking a bit sad, or the items were inappropriate. The challenge, essentially, was dealing with a large group of people, and we overcame it by using their contributions as a base point before adding our own items to fit the specifications.
As part of the upcoming House Council, it was also a bit of a challenge to step into the shoes of our predecessors - especially as they’re still at school to judge us. Fortunately the council was very supportive and gave us advice on how to be effective in running Blackeye; they agreed that we needed more House spirit, and so that was my challenge. As said in the bit above, I think I successfully achieved this given that it was the end of the year and everyone’s already pretty tired!
Learning Objective 3: Planned and initiated activities or part of an activity
Creativity: One of the best things about Showcase this year was that one of our songs was effectively directed by the girls. As it was inspired by Pitch Perfect, we did it acapella - although we had Miss Marieta there to play supplementary chords in rehearsals so that we could stay in tune. We wanted to make it as true to the original as possible which involved tediously rewinding videos on Youtube after every action and watching so many choreography tutorials. Eventually we figured that the original was too complicated and set about improvising; every girl paired up with another to produce a sound, and it actually turned out pretty good! We also had to choose costumes, being mindful of Brunei’s censorship laws, which was a challenge in itself because everybody needed to be able to bring something appropriate. The final performance did have some errors (like people holding their microphones upside down) but all in all I’m really proud of what we did.
Service: The shoebox drive was an amazing success that we organised ourselves. It was raised that the kids didn’t have basic toys, supplies or hygiene products, and we in the Penan Support group found a way to help alleviate the problem. Collecting over 200 boxes shows that what we did was well received by the school and involved a huge number of people - I definitely think this should be at least an annual if not regular thing that we can do.
Learning Objective 4: Collaborate with others
Creativity: Almost everything in music requires you to work with other people. For my exam, I have to be mindful of the piano, and to make sure that I’m not stepping out of time or pitch. For Showcase, I had to take on parts of songs that I wasn’t all that familiar with so that we produced a good sound when all the parts were put together. It’s not just singing, either - the orchestra, sound technicians and backstage people all work collaboratively to make Showcase such an amazing event.
Action: Duke of Edinburgh hits every single LO. For LO4, it happened on both the expedition and in the residential. In the expedition, it was us against altitude fatigue. I think everybody was empathetic towards anyone who was feeling a bit off, and so we were able to support them through copious amounts of panadol, rehydration salts, and snacks. At the residential, we all had a role to perform with the intention of constructing a greenhouse. The teamwork needed us to communicate with each other so that the work was evenly divided and everybody was comfortable with their job.
Service: The house council is a mix of lots of different people, and we need to be able to work together if we want anything to get done. It’s not just the Blackeye council either: we worked with Ibis for the Leadership training and every other House council to plan for Peace Day.
Learning Objective 5: Shown perseverance and commitment
Creativity: The fact that I was staying at school until 7 on some nights doing Showcase rehearsals, or having extra lessons on weekends in preparation for my singing exam is a testament to the commitment needed for this activity. I think a lot of people assume that, providing you know the song, you can just walk on stage on the day of the performance or the exam and just sing, but there’s a lot more behind the scenes that isn’t appreciated.
Action: The Duke of Edinburgh award requires you to do at least an hour of a Skill, Service and Activity every week; luckily this fits in quite nicely with CAS. I log my activities each week with a little paragraph detailing what I’ve done - this usually includes what I did, what I learnt, and what I’d do differently next week.
Learning Objective 6: Global significance of activity
Action: Stepping out of Brunei and into a remote Himalayan village is already pretty global, as my action was not focused on the local. I also think that by participating in the Duke of Edinburgh international award I’ve been supporting a global cause to get kids outside and doing things that are beneficial to their own communities.
Service: There are hundreds of tribes that are facing or have faced similar issues like the Penan: the Iban, the Ibequois, etc. All of these societies have been or are at risk of being eroded due to other civilisations encroaching onto their land. By being part of the Penan Support group, I would hope that I am showing that these tribes are not facing the struggle alone: there are people who care about their cultures. In the future, I think that we can make this support more public, possibly through the use of social media.
Learning Objective 7: Ethical implications of your actions
Creativity: The ethical implications of my creativity has stemmed from the local customs of Brunei. With fairly strict censorship laws and rules on how to dress and behave publicly, I had to be aware of how I was presenting myself when performing; how I dressed, what I said, how I behaved. In short, the ethical implications of performing were in cultural sensitivity, so as not to offend anybody watching.
Action: At first, I thought the ethical implications of going to Spiti Valley would be ensuring that I behaved appropriately and didn’t inadvertently offend the homestay hosts. Whilst this was true (and I made sure to familiarise myself with local customs, such as leaving some food on my plate to show I was full), there was also the ethics of actually going there. Tourism has had a bit of a negative impact on Spiti, as they cannot cope with the waste generated by tourists. We started to be part of this problem in the amount of bottled water we consumed daily - where do the empty bottles go? Thankfully, Ecosphere had a solution: Lifestraws!
Service: When dealing with the issues of the Penan, it becomes a bit paradoxical: we want to preserve their culture whilst at the same time we are introducing our own ways and products to do so. For the shoebox drive, we made the decision that any items donated should have minimal knock-on effects on the tribe: for example, giving spray deodorant would pollute their environment and mosquito spray would make them less resilient to the bugs.
Learning Objective 8: New or extended skills
Creativity: In doing my Grade 8 singing exam, I had to make my voice familiar with the technicalities. I had to increase my stamina and improve breathing techniques so that I could be strong on long notes, whilst also taking into consideration the general feel of the pieces. I have a tendency to be quite impassive about most things, so one thing I had to improve was the way in which I expressed the piece I was singing. I also think my pronunciation in German, Italian and French has improved.
0 notes