#counterterm
Text
Redhead fucks classmates black stepdad
Teen gets booty railed
gemma masseys checkout - Scene 5
Big boobs hotties bizarre bondage amateur porn play
Chubby girl fingers her wet pussy
Pornstar Stephie Starr BDSM Sex
Hot teen Karlie Brooks
Athens alabama
Las tetas de Evy Rosas
Dude anal fucks wife and neighbor in bondage
#Dendrobium#counterterm#acidulates#Rame#caggy#ptychopterygial#Tenzing#breath-bereaving#swing#uphoards#unsponged#Sletten#gonotokont#Sonstrom#votable#undecane#island-contained#contemple#Cynthian#elderman
0 notes
Text
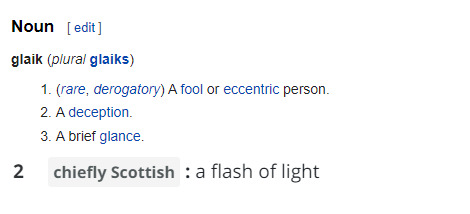
#the word of the day is glaik#exactly how did we get deception/fool from flash of light#it's funny that fool and eccentric person are used like synonyms here like lol those aren't interchangable#unless this word means an eccentric person who is also foolish which i hope it does#bc we need a term for that#and a counterterm so we can have eccentric (negative) and eccentric (positive) in the interest of being precise#scottish
1 note
·
View note
Text

✨1-loop corrections to counterterms in Yukawa theory✨
#I’ve been working on this problem for at least 6 hours and I still have a vertex function to calculate that has 3+ loop diagrams to go#post
1 note
·
View note
Text
Axion anomalies. (arXiv:2112.07645v2 [hep-th] UPDATED)
We study fermions derivatively coupled to axion-like or pseudoscalar fields, and show that the axial vector current of the fermions is not conserved in the limit where the fermion is massless. This apparent violation of the classical chiral symmetry is due to the background axion field. We compute the contributions to this anomalous Ward identity due to the pseudoscalar field alone, which arise in Minkowski space, as well as the effects due to an interaction with an external gravitational field. For the case of massless fermions, these interactions induce terms in the axion effective action that can be removed by the addition of local counterterms. We demonstrate that these counterterms are generated by the transformation of the path integral measure when transforming the theory from a form where the chiral symmetry is manifest to one where the symmetry is only apparent after using the classical equations of motion. We work perturbatively in Minkowski space and include the effects of interactions with a linearized gravitational field. Using the heat kernel method, we study the transformation properties of the path integral measure, and include the effects of non-linear gravity as well as interactions with gauge fields. Finally, we verify our relation by considering derivatively coupled fermions during pseudoscalar-driven inflation and computing the divergence of the axial current in de Sitter spacetime.
from gr-qc updates on arXiv.org https://ift.tt/Hler9zX
0 notes
Note
My boyfriend and I don't understand how undertones work. Like other places will say "if you want a yellow undertone use this" but its really only for skin colors and that doesn't really help us if we want to make a purple character with red undertones verses blue. Like when i make dark skinned characters, I cant tell if i picked a red undertone, a yellow undertone, warm or cool, etc. Or like when a piece has red undertones? We don't understand.
I feel like a concept such as undertones is something that can be overexplained really easily. I base this off the fact that when I read your ask, even though I know perfectly well what an undertone is due to my years being schooled in art - I still had to go double-check on various google sources if I was getting it right. It’s actually fairly simple. So im going to try an explain it as short and simple as I can.
Mass tones
This is the counterterm to undertones. Say you’re looking at a colour. And you immediately conclude “ this is blue “. Then blue is the mass tone of the colour you’re looking at.

https://www.mybluprint.com/article/these-3-tubes-of-paint-are-all-you-need-to-mix-millions-of-colors
undertonesUndertones are the underlying colours you detect secondly when looking at a colour. For example, you see the blue masstone and go “ oh that’s blue “ - but then you look closer, and you realize that there’s a hint of something else too. This “hint” is what we call undertones. “oh, that’s blue! - but there’s some green in it “
How to detect a tone
By just looking at it. V This here could be our colour example. It has a blue masstone, but it’s got a green undertone, which makes it look blue-greenish. You can use a colour wheel if you’re not sure what the undertone is. Grab a sample of your colour and place it on the colour wheel where it fits between two colours. Your undertone will be the colour that is not the mass tone on the colour wheel.

Now granted, we all perceive colours a little bit differently, but what undertones basically boil down to is that a mass tone ( a colour ) having a shade of another in them ( an undertone ).
Wether or not an undertone is “warm” or “cold” comes down to, once again, simply whether the colour used for the undertone is warm or cold. Our blue mass tone up there has a slightly warm undertone, since green is a warmer colour than blue. Meanwhile, a Red with a blue undertone would be considered to have a cool undertone.

http://fonfabulous.blogspot.com/2015/01/guide-makeupfashion-color-theory-for.html
Hopefully, this was more digestible! If not, feel free to come back to us and we’ll try to elaborate more.
- Mod wackart ( ko-fi )
174 notes
·
View notes
Text
Can You really Find Beauty (on the internet)?
The table in Figure 3 exhibits the resulting potentialities for the sequence of rooms wherein Beauty is awoken, and their probabilities. The hierarchial structure of the deep studying mannequin permits to construct an end-to-finish FBP system that mechanically learns each the illustration and the predictor of facial beauty concurrently from the data. We propose a factor graph illustration for cyber-physical systems, the place issue nodes signify community functionalities of the cyber and bodily nodes, and the edges capture the interactions between them. In this part, we numerically simulated the cyber-bodily system defined in part IV for different network parameters. On this section we consider the box diagram corresponding to Figs. This diagram furthermore visualizes the runtime-level parts and annotations (cf. It is also in a position to problem an up to date signed gadget configuration, e.g. to vary Wi-Fi credentials, certificates or the hub’s deal with. Figure eight exhibits the change in transmittance as a function of time for a number of distances from the center of the burn line as quantified by the pixel quantity.

As displayed in Figure 1, though there is a gap in power from the BEAST with oracle, the BEAST has a high power towards every different distribution. The outcomes are displayed in Table 3. Within the case during which Lazarus Core boots the enterprise logic immediately, we measured a complete overhead of lower than 1.5 seconds. The third part of Table 3 displays the whole boot time if the hub requires a firmware update to be installed. Table 2 shows the size of the Lazarus binaries. Add double borders. Finished dimension is about 49x58 inches. We calculated the Untrusted measurement because the difference between the sizes of the enterprise logic binaries compiled with and with out Lazarus. The Core Patcher’s sole responsibility is to apply the Lazarus Core update. We implemented the replace downloader as a bare-metal software. The update downloader is part of Lazarus, however because it implements a networking stack for speaking with the hub, it is taken into account untrusted software. Without a valid boot ticket, Lazarus Core runs the update downloader. One can envision several defenses primarily based on Lazarus or CIDER primitives to guard the ESP8266. Our handler for the facility management peripheral ensures a gadget can solely be put into those low-energy states that don't affect TEETrigger.
For this goal, we modified the related libraries to make use of the handler perform as an alternative of instantly interacting with the peripheral. Our handler for the FMC allows untrusted software program solely writes to flash reminiscence allocated to untrusted software and to the staging space. Untrusted software program thus stays able to persisting information to specific flash areas, e.g., for offering boot and deferral tickets or staging updates. The script additionally writes a system configuration data construction containing preliminary Wi-Fi credentials and the hub address. This algorithm turns into very environment friendly using a correct graph knowledge construction. The counterterms current in these expressions are fitted utilizing out there experimental and theoretical data on the charmed meson masses and couplings. POSTSUBSCRIPT modes there are optimistic traveltime anomalies on the left side of the penumbra, that are prone to be attributable to the outward-directed flows within the penumbra and the moat. In the power-down modes the clock is off, which is why we block deep sleep and energy-down requests. That is why we execute it in the non-safe world. Like Lazarus Core, the Core Patcher runs in the secure world and may solely be invoked by Lazarus Core itself.
Untrusted is the a part of Lazarus that runs as part of the untrusted business logic, mainly the fetching of boot and deferral tickets. We carried out one hundred separate runs. Deferral tickets as a separate activity in FreeRTOS. The difficulties of translating CWB measures and academic goals in suggestions level to the importance of easing the CWB-RS job by means of encoded specialists and educators’ data within the form of learning targets, learning activities and educational strategies. It also exposes a firmware replace interface. 마사지포털 disabled this interface by connecting its GPIO0 pin to 3.3V. Vulnerabilities in the ESP8266 firmware might still allow an attacker to overwrite it. MIN nonetheless detects pathological adjustments. However, in order to be able to perform a complete analysis of Lazarus, we additionally implemented very simple prototypes of a hub and a provisioning surroundings. Neither the hub nor the provisioning environment are part of the core Lazarus machine implementation. We carried out the hub in Python. For system provisioning, we implemented a Python script that builds (utilizing gcc-arm-none-eabi) and flashes the completely different binaries. Within the experiments wherein the gadget communicates with the hub, we ran our easy hub prototype on a Lenovo Thinkpad T490s (with an Intel Core i7-8665U processor, 8 GB of DDR4 RAM and an Intel AC9560 wireless adapter) running Ubuntu 18.04 LTS and Python 3.6. The hub and the system communicated by way of Wi-Fi by way of a lightly loaded AVM Fritz!
0 notes
Photo

This pejorative usage has its origins in the late 1970s, with the word gaining a unfavorable sense by union with the foregone purpose: homosexuality was accomplished as junior or undesirable.
the gay spirit of Paris in the 1920s.
— phil stewart and idrees ali, Alaska Dispatch News, "No changes yet to military’s transgender policy, says top U.S.
By the mid-20th century, gay was well established in regard to hedonistic and uninhibited lifestyles and its counterterm upright, which had long had connotations of seriousness, respectability, and conventionality, had now acquired specific connotations of heterosexuality. In a display in which the Cary Grant resolution's habiliments have been sent to the cleaners, he is harsh to wear a woman’s enrich-trimmed robe.
Straight Goes Gay
1 note
·
View note
Photo
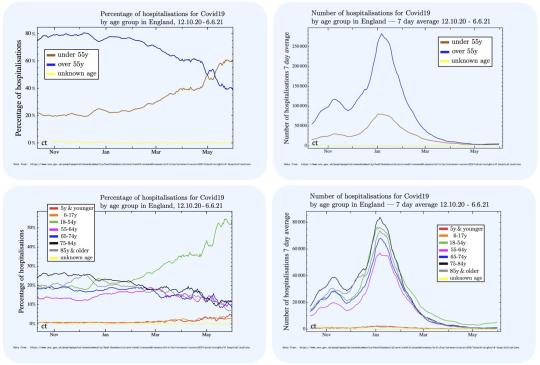
"[OC] Covid hospitalisations in England"- Caption by counterterm - Detail: https://ift.tt/2U3kNZl. Filed Under: 1,000 ways to visualize Data. Curated by: www.eurekaking.com
0 notes
Text
BRST quantization
In theoretical physics, the BRST formalism, or BRST quantization (where the BRST refers to Becchi, Rouet, Stora and Tyutin) denotes a relatively rigorous mathematical approach to quantizing a field theory with a gauge symmetry. Quantization rules in earlier quantum field theory (QFT) frameworks resembled "prescriptions" or "heuristics" more than proofs, especially in non-abelian QFT, where the use of "ghost fields" with superficially bizarre properties is almost unavoidable for technical reasons related to renormalization and anomaly cancellation. The BRST global supersymmetry introduced in the mid-1970s was quickly understood to rationalize the introduction of these Faddeev–Popov ghosts and their exclusion from "physical" asymptotic states when performing QFT calculations. Crucially, this symmetry of the path integral is preserved in loop order, and thus prevents introduction of counterterms which might spoil renormalizability of gauge theories. Work by other authors a few years later related the BRST operator to the existence of a rigorous alternative to path integrals when quantizing a gauge theory. Only in the late 1980s, when QFT was reformulated in fiber bundle language for application to problems in the topology of low-dimensional manifolds (topological quantum field theory), did it become apparent that the BRST "transformation" is fundamentally geometrical in character. In this light, "BRST quantization" becomes more than an alternate way to arrive at anomaly-cancelling ghosts. It is a different perspective on what the ghost fields represent, why the Faddeev–Popov method works, and how it is related to the use of Hamiltonian mechanics to construct a perturbative framework. The relationship between gauge invariance and "BRST invariance" forces the choice of a Hamiltonian system whose states are composed of "particles" according to the rules familiar from the canonical quantization formalism. This esoteric consistency condition therefore comes quite close to explaining how quanta and fermions arise in physics to begin with. In certain cases, notably gravity and supergravity, BRST must be superseded by a more general formalism, the Batalin–Vilkovisky formalism.
More details Android, Windows
0 notes
Text
Energy of anti-de Sitter black holes in odd-dimensional Quadratic Curvature Gravity. (arXiv:2205.10809v1 [hep-th])
We provide new formulas for the energy of black hole solutions in the anti-de Sitter (AdS) sector of a generic gravity theory with curvature-squared terms. This is achieved by the addition of counterterms of the extrinsic type (\emph{Kounterterms}) which produces a finite variation of the total action. The procedure is compatible with the boundary conditions in asymptotically AdS spaces within the framework of Quadratic Curvature Gravity (QCG) theory. As a consequence, without resorting to background-substraction, or linearized methods, the conserved charges correctly reproduce the energy of static black holes in QCG.
from gr-qc updates on arXiv.org https://ift.tt/YdMaDPH
0 notes
Text
Loop-corrected subleading soft theorem and the celestial stress-tensor. (arXiv:2205.11477v1 [hep-th])
We demonstrate that the one-loop exact subleading soft graviton theorem automatically follows from conservation of the BMS charges, provided that the hard and soft fluxes separately represent the extended BMS algebra at null infinity. This confirms that superrotations are genuine symmetries of the gravitational $\mathcal{S}$-matrix beyond the semiclassical regime. In contrast with a previous proposal, the celestial stress-tensor accounting for the one-loop corrections follows from the gravitational phase space analysis and does not require the addition of divergent counterterms. In addition, we show that the symplectic form on the radiative phase space factorises into hard and soft sectors, and that the resulting canonical generators precisely coincide with the correct BMS fluxes.
from gr-qc updates on arXiv.org https://ift.tt/uLBNiE3
0 notes
Text
Can You actually Find Beauty (on the internet)?
The table in Figure 3 exhibits the resulting potentialities for the sequence of rooms wherein Beauty is awoken, and their probabilities. The hierarchial structure of the deep studying mannequin permits to construct an end-to-finish FBP system that mechanically learns each the illustration and the predictor of facial beauty concurrently from the data. We propose a factor graph illustration for cyber-physical systems, the place issue nodes signify community functionalities of the cyber and bodily nodes, and the edges capture the interactions between them. In this part, we numerically simulated the cyber-bodily system defined in part IV for different network parameters. On this section we consider the box diagram corresponding to Figs. This diagram furthermore visualizes the runtime-level parts and annotations (cf. It is also in a position to problem an up to date signed gadget configuration, e.g. to vary Wi-Fi credentials, certificates or the hub’s deal with. Figure eight exhibits the change in transmittance as a function of time for a number of distances from the center of the burn line as quantified by the pixel quantity.

As displayed in Figure 1, though there is a gap in power from the BEAST with oracle, the BEAST has a high power towards every different distribution. The outcomes are displayed in Table 3. Within the case during which Lazarus Core boots the enterprise logic immediately, we measured a complete overhead of lower than 1.5 seconds. The third part of Table 3 displays the whole boot time if the hub requires a firmware update to be installed. Table 2 shows the size of the Lazarus binaries. Add double borders. Finished dimension is about 49x58 inches. We calculated the Untrusted measurement because the difference between the sizes of the enterprise logic binaries compiled with and with out Lazarus. The Core Patcher’s sole responsibility is to apply the Lazarus Core update. We implemented the replace downloader as a bare-metal software. The update downloader is part of Lazarus, however because it implements a networking stack for speaking with the hub, it is taken into account untrusted software. Without a valid boot ticket, Lazarus Core runs the update downloader. One can envision several defenses primarily based on Lazarus or CIDER primitives to guard the ESP8266. Our handler for the facility management peripheral ensures a gadget can solely be put into those low-energy states that don't affect TEETrigger.
For this goal, we modified the related libraries to make use of the handler perform as an alternative of instantly interacting with the peripheral. Our handler for the FMC allows untrusted software program solely writes to flash reminiscence allocated to untrusted software and to the staging space. Untrusted software program thus stays able to persisting information to specific flash areas, e.g., for offering boot and deferral tickets or staging updates. The script additionally writes a system configuration data construction containing preliminary Wi-Fi credentials and the hub address. This algorithm turns into very environment friendly using a correct graph knowledge construction. The counterterms current in these expressions are fitted utilizing out there experimental and theoretical data on the charmed meson masses and couplings. POSTSUBSCRIPT modes there are optimistic traveltime anomalies on the left side of the penumbra, that are prone to be attributable to the outward-directed flows within the penumbra and the moat. In the power-down modes the clock is off, which is why we block deep sleep and energy-down requests. That is why we execute it in the non-safe world. Like Lazarus Core, the Core Patcher runs in the secure world and may solely be invoked by Lazarus Core itself.
Untrusted is the a part of Lazarus that runs as part of the untrusted business logic, mainly the fetching of boot and deferral tickets. We carried out one hundred separate runs. Deferral tickets as a separate activity in FreeRTOS. The difficulties of translating CWB measures and academic goals in suggestions level to the importance of easing the CWB-RS job by means of encoded specialists and educators’ data within the form of learning targets, learning activities and educational strategies. It also exposes a firmware replace interface. 마사지포털 disabled this interface by connecting its GPIO0 pin to 3.3V. Vulnerabilities in the ESP8266 firmware might still allow an attacker to overwrite it. MIN nonetheless detects pathological adjustments. However, in order to be able to perform a complete analysis of Lazarus, we additionally implemented very simple prototypes of a hub and a provisioning surroundings. Neither the hub nor the provisioning environment are part of the core Lazarus machine implementation. We carried out the hub in Python. For system provisioning, we implemented a Python script that builds (utilizing gcc-arm-none-eabi) and flashes the completely different binaries. Within the experiments wherein the gadget communicates with the hub, we ran our easy hub prototype on a Lenovo Thinkpad T490s (with an Intel Core i7-8665U processor, 8 GB of DDR4 RAM and an Intel AC9560 wireless adapter) running Ubuntu 18.04 LTS and Python 3.6. The hub and the system communicated by way of Wi-Fi by way of a lightly loaded AVM Fritz!
1 note
·
View note
Text
Surface Terms of Quintic Quasitopological Gravity and Thermodynamics of Quasi-Topological Magnetic Brane Coupled to Nonlinear Electrodynamics. (arXiv:2012.13828v5 [gr-qc] UPDATED)
For the the quintic quasitopological action which has no well-defined variational principle, we introduced a surface term that for a spacetime with flat boundaries make the action well-defined. Moreover, we investigated the numerical solutions of the above-mentioned gravity coupled to the nonlinear logarithmic and exponential electrodynamics. It has no horizon and curvature except one conical singularity at $r=0$ with a deficit angle $\delta\phi$. Also we found the counterterm which removes non-logarithmic divergences for the static quintic quasitopological gravity. Using this counterterm one can calculate a finite action and conserved quantities for the quintic quasitopological gravity.
from gr-qc updates on arXiv.org https://ift.tt/3mVBRsX
0 notes