#Security in Cloud Computing
Text

#Cloud Computing Advisors#Cloud Computing Services#Cloud Computing Technology#Security in Cloud Computing
0 notes
Text
A Complete Guide to Mastering Microsoft Azure for Tech Enthusiasts
With this rapid advancement, businesses around the world are shifting towards cloud computing to enhance their operations and stay ahead of the competition. Microsoft Azure, a powerful cloud computing platform, offers a wide range of services and solutions for various industries. This comprehensive guide aims to provide tech enthusiasts with an in-depth understanding of Microsoft Azure, its features, and how to leverage its capabilities to drive innovation and success.
Understanding Microsoft Azure
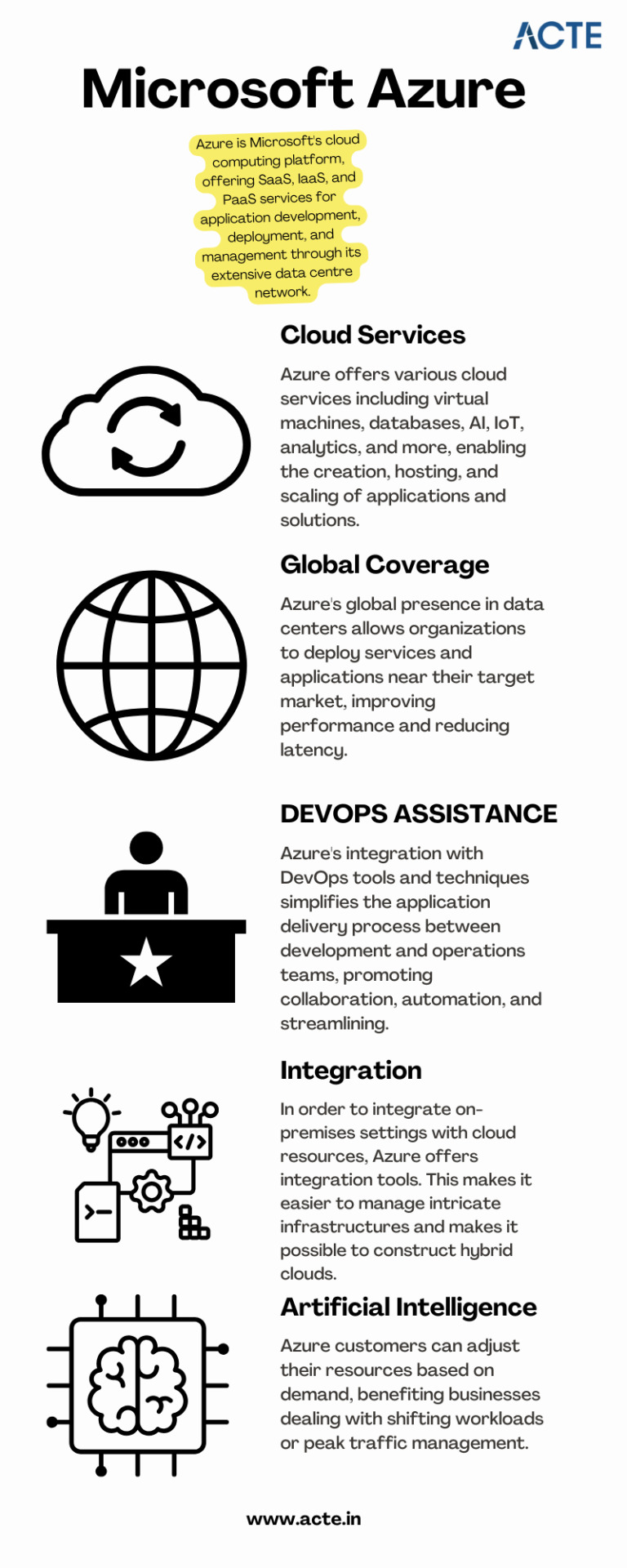
A platform for cloud computing and service offered through Microsoft is called Azure. It provides reliable and scalable solutions for businesses to build, deploy, and manage applications and services through Microsoft-managed data centers. Azure offers a vast array of services, including virtual machines, storage, databases, networking, and more, enabling businesses to optimize their IT infrastructure and accelerate their digital transformation.
Cloud Computing and its Significance
Cloud computing has revolutionized the IT industry by providing on-demand access to a shared pool of computing resources over the internet. It eliminates the need for businesses to maintain physical hardware and infrastructure, reducing costs and improving scalability. Microsoft Azure embraces cloud computing principles to enable businesses to focus on innovation rather than infrastructure management.
Key Features and Benefits of Microsoft Azure
Scalability: Azure provides the flexibility to scale resources up or down based on workload demands, ensuring optimal performance and cost efficiency.
Vertical Scaling: Increase or decrease the size of resources (e.g., virtual machines) within Azure.
Horizontal Scaling: Expand or reduce the number of instances across Azure services to meet changing workload requirements.
Reliability and Availability: Microsoft Azure ensures high availability through its globally distributed data centers, redundant infrastructure, and automatic failover capabilities.
Service Level Agreements (SLAs): Guarantees high availability, with SLAs covering different services.
Availability Zones: Distributes resources across multiple data centers within a region to ensure fault tolerance.
Security and Compliance: Azure incorporates robust security measures, including encryption, identity and access management, threat detection, and regulatory compliance adherence.
Azure Security Center: Provides centralized security monitoring, threat detection, and compliance management.
Compliance Certifications: Azure complies with various industry-specific security standards and regulations.
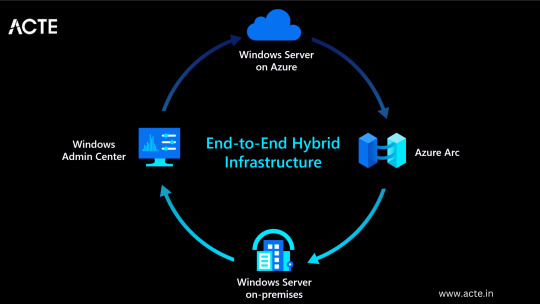
Hybrid Capability: Azure seamlessly integrates with on-premises infrastructure, allowing businesses to extend their existing investments and create hybrid cloud environments.
Azure Stack: Enables organizations to build and run Azure services on their premises.
Virtual Network Connectivity: Establish secure connections between on-premises infrastructure and Azure services.
Cost Optimization: Azure provides cost-effective solutions, offering pricing models based on consumption, reserved instances, and cost management tools.
Azure Cost Management: Helps businesses track and optimize their cloud spending, providing insights and recommendations.
Azure Reserved Instances: Allows for significant cost savings by committing to long-term usage of specific Azure services.
Extensive Service Catalog: Azure offers a wide range of services and tools, including app services, AI and machine learning, Internet of Things (IoT), analytics, and more, empowering businesses to innovate and transform digitally.
Learning Path for Microsoft Azure
To master Microsoft Azure, tech enthusiasts can follow a structured learning path that covers the fundamental concepts, hands-on experience, and specialized skills required to work with Azure effectively. I advise looking at the ACTE Institute, which offers a comprehensive Microsoft Azure Course.

Foundational Knowledge
Familiarize yourself with cloud computing concepts, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
Understand the core components of Azure, such as Azure Resource Manager, Azure Virtual Machines, Azure Storage, and Azure Networking.
Explore Azure architecture and the various deployment models available.
Hands-on Experience
Create a free Azure account to access the Azure portal and start experimenting with the platform.
Practice creating and managing virtual machines, storage accounts, and networking resources within the Azure portal.
Deploy sample applications and services using Azure App Services, Azure Functions, and Azure Containers.
Certification and Specializations
Pursue Azure certifications to validate your expertise in Azure technologies. Microsoft offers role-based certifications, including Azure Administrator, Azure Developer, and Azure Solutions Architect.
Gain specialization in specific Azure services or domains, such as Azure AI Engineer, Azure Data Engineer, or Azure Security Engineer. These specializations demonstrate a deeper understanding of specific technologies and scenarios.
Best Practices for Azure Deployment and Management
Deploying and managing resources effectively in Microsoft Azure requires adherence to best practices to ensure optimal performance, security, and cost efficiency. Consider the following guidelines:
Resource Group and Azure Subscription Organization
Organize resources within logical resource groups to manage and govern them efficiently.
Leverage Azure Management Groups to establish hierarchical structures for managing multiple subscriptions.
Security and Compliance Considerations
Implement robust identity and access management mechanisms, such as Azure Active Directory.
Enable encryption at rest and in transit to protect data stored in Azure services.
Regularly monitor and audit Azure resources for security vulnerabilities.
Ensure compliance with industry-specific standards, such as ISO 27001, HIPAA, or GDPR.
Scalability and Performance Optimization
Design applications to take advantage of Azure’s scalability features, such as autoscaling and load balancing.
Leverage Azure CDN (Content Delivery Network) for efficient content delivery and improved performance worldwide.
Optimize resource configurations based on workload patterns and requirements.
Monitoring and Alerting
Utilize Azure Monitor and Azure Log Analytics to gain insights into the performance and health of Azure resources.
Configure alert rules to notify you about critical events or performance thresholds.
Backup and Disaster Recovery
Implement appropriate backup strategies and disaster recovery plans for essential data and applications.
Leverage Azure Site Recovery to replicate and recover workloads in case of outages.
Mastering Microsoft Azure empowers tech enthusiasts to harness the full potential of cloud computing and revolutionize their organizations. By understanding the core concepts, leveraging hands-on practice, and adopting best practices for deployment and management, individuals become equipped to drive innovation, enhance security, and optimize costs in a rapidly evolving digital landscape. Microsoft Azure’s comprehensive service catalog ensures businesses have the tools they need to stay ahead and thrive in the digital era. So, embrace the power of Azure and embark on a journey toward success in the ever-expanding world of information technology.
#microsoft azure#cloud computing#cloud services#data storage#tech#information technology#information security
6 notes
·
View notes
Photo
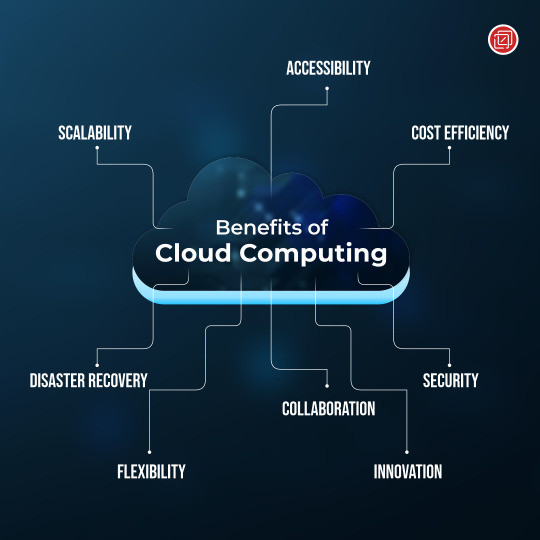






Embrace the cloud for scalability, cost efficiency, accessibility, disaster recovery, security, collaboration, flexibility, and innovation.
Remember to evaluate providers and implement security measures for successful cloud adoption.
Ready to unlock the power of the cloud? Consult with cloud experts and start harnessing these benefits for your business today!
Happy cloud computing! ☁️💪
6 notes
·
View notes
Text
But I’m sure they’re being totally responsible with AI.
4 notes
·
View notes
Text

In 2023, the trend you need to know about is improved extended detection and response with XDR. Strengthen security while enhancing the efficiency. Read More...
#Cyber Security XDR#Unified Communications#Voiceware Platform#PBX Solution#Cloud PBX#Cloud Technology#VoIP Solutions#VoIP Services#cloud based system#Communications System#Business Telephone System#SIP Trunking#Technology#VoIP Phone#VoIP#IP telephony#mobile Phones#Telephone#cloud Computing#IP Telephone Home#VoIP technology#Modern VoIP Phone#Hotel Phone System#Voiceware#phone suite phone system#voiceware express#phonesuite support#phonesuite console#hospitality communication#Busines Phonenumber
12 notes
·
View notes
Text
Unleashing the Power of AWS: Revolutionizing Cloud Computing and Empowering Innovation
Hey friends, check out this captivating blog on the power of AWS and how it's revolutionizing cloud computing! Discover the limitless possibilities of #AWS and unlock your business's true potential. #CloudComputing #Innovation
Amazon Web Services (AWS) is a comprehensive cloud computing platform offered by Amazon.com. It provides a wide range of cloud services that enable businesses and individuals to build and deploy various applications and services with flexibility, scalability, and cost efficiency. AWS offers a vast array of services spanning compute, storage, databases, networking, analytics, machine learning,…

View On WordPress
#amazon web services#Availability#aws#Cloud Computing#Cloud Computing Platform#Cloud Revolution#Cloud Services#Cost Efficiency#Elasticity#flexibility#Global Infrastructure#Innovation#Pay-as-you-go#reliability#scalability#Security#Service Portfolio
2 notes
·
View notes
Text
AWS vs Google Cloud in terms of Security
Google Cloud vs AWS: Who Uses Them?
AWS has more expertise and implementation in the cloud sector due to it being created much earlier than the majority of cloud providers, including GCP, and this has led to greater community support. Because of this, AWS has more well-known clients, including companies like Netflix, Airbnb, Unilever, BMW, Samsung, Xiaomi, Zinga, and others.
Whereas AWS's early establishment and greater experience have helped it attract many high-profile clients, GCP has grown its clientele and user base as a result of providing the same infrastructure that Google Search, YouTube, and other Google products utilise.
This was a more than sufficient justification for numerous cutting-edge companies, like HSBC, PayPal, 20th Century Fox, Bloomberg, Domino's, and others, to choose GCP.
AWS vs Google Cloud: Security
One of the many crucial factors to take into account when selecting a cloud service provider for your company is security.
The following are the factors to consider when selecting a cloud service provider:
Controls, procedures, rules, and technology
Although Google Cloud and AWS are both known for providing cutting-edge cloud security, we have provided a detailed analysis of how the two companies protect their cloud:
Security of their cloud: The underlying infrastructure of their cloud platform includes security features that help to protect by default.
Cloud security: By using additional security services and products that are offered in their cloud platform, you may improve the protection of your apps and data.
Security anywhere: By extending security capabilities outside their cloud platform with protocols like encryption, this primarily relates to protecting your assets regardless of location.
You can prefer Google Cloud Platform Bootcamp if you want to learn more about google cloud platform.
5 notes
·
View notes
Text
Top Skill development courses for Students to get Good Placement
Please like and follow this page to keep us motivated towards bringing useful content for you.
Now a days, Educated Unemployment is a big concern for a country like India. Considering the largest number of youth population in world, India has huge potential to be a developed nation in the next few years. But, it can be only possible if youth contribute in economy by learning skills which are in global demand. However, course structure in colleges are outdated and do not make students job…

View On WordPress
#Artificial Intelligence and Machine learning#Books for Artificial Intelligence and Machine Learning#Books for coding#Books for cyber security#Books for data science#Books for Digital Marketing#Books for Placement#Cloud computing#College Placement#Cyber Security#Data science and analytics#digital marketing#Graphic Design#high package#Programming and software development#Project Management#Sales and Business Development#Skill development#Web Development
4 notes
·
View notes
Link
File replication improves workflow for enterprises and refers to sharing information (data) between networks, servers, computers & databases. File Synchronization is the process of updating files in 2+ locations via certain rules
#cloud computing platform#cloud computing#file synchronization#data distribution#big data#data management#cloud security#data migration#cloud migration#data protection#information technology#continuous delivery
3 notes
·
View notes
Link
Synchronize data across one or many sites. File mirroring to one or many locations. Sync files between different operating systems, platforms, Bidirectional File Replication - Windows, Mac, Linux, Unix Flavors, Solaris, OpenBSD, IBM Spark, aix
#data synchronization#file mirroring#cloud computing#cloud platforms#cyber security#data protection#data management#edpcloud#real time#edge computing#data distribution
2 notes
·
View notes
Text

GIF showing the concept of holding the cloud (computing cloud) in the palm of your hands, for use in a cybersecurity article about cloud computing security.
#cloud security#saas security#cloud computing#saas#gif#ascii art#ascii gif#computer ascii#cool ascii#fightmilk22#true art#artwork#digital arwork
3 notes
·
View notes
Text
it rly depends on the slot but really i kind of want to change my major from gaming to information security
#if i dont get into information security then maybe cloud computing#i dont think im interested in IOT or devops but hmmm#and theres literally no benefit in studying blockchain bc that branch hasnt developed enuf in my uni yet#im not taking any risk ;-;#i mean Technically speaking my major is comp science but like idk is it called specialization or major#those r such western terms how do i even define my degree lmao
3 notes
·
View notes
Photo





Cloud computing is one of the most helpful platforms one may use within their organization. Get rid of servers for explosive business growth by switching to our cloud services.
For more information, Visit us: https://www.algoworks.com/blog/cloud-computing-important-to-business-success/
#cloud#computing#cloudComputing#platforms#office#business#growth#businessgrowth#cloud services#services#security#accessibility#storage#adaptability#algoworks#implementation#development
2 notes
·
View notes
Text
Secure cloud computing solutions for enterprises
Exclserv Solutions specializes in Secure cloud computing solutions for enterprises. Our comprehensive services include data protection, scalable infrastructure, and seamless integration, ensuring your business operates efficiently and securely in the cloud. With advanced encryption, robust security protocols, and 24/7 monitoring, Exclserv safeguards your critical information against threats—trust Exclserv Solutions for dependable, scalable, and effective cloud computing for your business.
Visit the website for more details: https://exclserv.in/cloud-services/
0 notes
Text
Balancing Innovation and Cost Control: Strategies for IT Leaders
This paper explores the challenges and solutions for balancing innovation and cost control for IT leaders. Read more...
As businesses continue to evolve and grow, technology has become a key driver of their success. Technology advancements provide new opportunities to improve efficiency, productivity, and profitability. However, with new technology comes the need for innovation, which often comes with increased costs. IT leaders face the challenge of balancing innovation and cost control to ensure their…
View On WordPress
#agile development#automation#Cloud Computing#cost control#data analytics#Innovation#IT leaders#open-source software#outsourcing#Security#technology investments#total cost of ownership
2 notes
·
View notes
Text
The importance of cyber security education for young students - CyberTalk
New Post has been published on https://thedigitalinsider.com/the-importance-of-cyber-security-education-for-young-students-cybertalk/
The importance of cyber security education for young students - CyberTalk
Dasha Smolina is an emerging cyber security professional and is currently a Security Engineer in the Eastern U.S. Region at Check Point Software Technologies. She joined Check Point in 2023 to help organizations and businesses meet their cyber security needs.
Overview
The sophisticated cyber threat landscape poses a significant risk to the education sector. Malicious actors’ interest in this sector is growing. Students are often targeted by these attackers because of their increased online presence, risky online behavior, and lack of cyber security awareness. Unlike businesses, which often successfully employ cyber security awareness training to prevent cyber crime incidents, schools overlook cyber security training in their curricula. As young students continue to boundlessly explore the web and are increasingly exposed to cyber threats, K-12 educators need to provide better cyber security training for students to ensure their safety online.
Background – Why are students targeted and what cyber crime are they experiencing?
In the past few years, the internet has become a primary channel for education, with two-thirds of children saying they access their online education resources daily. One in three education devices contains sensitive data, making it critical to keep devices secure.
Students are also more connected to the web than ever before because of the prominence of social media and online gaming. These children are exposed to the internet constantly, relying on it for almost all of their educational and recreational needs. However, they often lack awareness about online safety. As noted previously, attackers are targeting these children because of their increased online presence, risky online behavior, naivety and lack of safety precautions.
K-12 students are experiencing concerning cyber risks such as cyber bullying, inappropriate content, identity theft, and more. Given that 92% of children are online by the age of 12 and that 72% of them having experienced at least one cyber threat, it is evident that students are at risk of attacks by cyber criminals. Moreover, these attacks are multifaceted, with attackers utilizing various techniques to induce harm (see Exhibit 1).
In addition to what was mentioned above, online crimes against children are also high because of the prevalence of children using social media without adult supervision. Nine out of 10 households with internet access have children who are active on social media, and 54% of these households do not regulate their children’s online activities. The lack of supervision and awareness, combined with an increase in online activity means that students are exposed to many cyber security threats.
Exhibit 1 – Boston Consulting Group Survey Results
The data shows that one particular cyber threat affects children more commonly than adults: cyber bullying. Cyber bullying is particularly dangerous because it can affect children through all hours of the day and night and can come in many forms such as texting, social media posts, and chatroom messages. Cyber bullying can also be anonymous, which leaves victims with little recourse to report the attacker. Even if the victim knows who the attacker is and blocks or reports them, there are so many avenues through which to hide an identity online that the attacker can easily find another way to harm the victim; it is nearly impossible to escape a determined cyber bully. Cyber bullying has detrimental effects on its victims, leading to mental health issues, increased stress and anxiety, depression, and violence. The effects of cyber bullying have also been shown to be long-lasting, continuing even once the bullying has stopped.
Another long-lasting cyber crime that children are targeted for is identity theft. This dangerous cyber crime ensnares one in 50 children annually and has life-long implications for a child. For those who may not know, identity theft as a cyber crime occurs when an attacker steals a person’s data and information to commit fraudulent identity-based activities, such as opening credit cards or bank accounts, applying for loans, committing online crimes like scams, and more. Children who have had their identity stolen might not find out for years, or even decades, until they try to open their own credit card account and discover that their credit history has been tarnished. Children fall victim to identity theft through data breaches, doxxing (someone else publicly sharing their information or “docs”), parents or close ones oversharing information about the child, children oversharing their information or passwords with friends, and phishing and other common online scams.
Trusting strangers online and naivety can also lead children to become victims of online predators or groomers. Online predators visit popular social media websites and falsify their age and profile content to potentially lure young children into online interactions. Once contact is established, the groomer then pressures the child to reveal explicit photos of themselves and might even try to meet the child in person. Sometimes the groomer will blackmail the child, but other times the victim might not even realize they are being groomed, considering the online predator to be their boyfriend or girlfriend. There are about 500,000 online predators active each day but only two out of ten children are aware of this potential danger. Rather than protecting themselves and limiting potential exposure to dangerous adults online, 40% of children online remove their privacy settings to attract more followers. This makes it that much easier for groomers to access a child’s information and manipulate them online.
Children also fall for online financial scams, as shown by the data collected for the FBI’s 2023 Internet Crime Report, which states that people under the age of 20 accumulated over $40 million worth of losses to online scams in 2023. Online scammers are preying on children who are accessing the internet at early ages and who lack the awareness to recognize cyber threats.
With more children going online at even younger ages, it is no longer as easy as it once was to keep children safe at home. Online threats are infiltrating their lives and putting children in danger of cyber attackers. Given education’s shift towards online learning, students are facing many new kinds of cyber risks. Moreover, with the emergence of new technologies, such as the Internet of Things or cloud-based and network-connect devices, including children’s toys and household appliances, the evolution of threats is not slowing down. Thus, it is important for educators to better understand the situation and help equip students with the knowledge and skills to protect themselves from attackers.
Proposed solution – How can cyber attacks that target students be prevented?
To protect young students from becoming cyber crime victims, educators and parents should increase the cyber security safety measures in-place on children’s devices. They should also provide cyber safety awareness education for children. Oftentimes, once an attack has occurred, the damage is irreparable, and parents can only report the crime and mitigate the impact. Therefore, prevention should be the priority. Combining safety controls with better cyber security education in regards to topics like phishing, privacy, social media safety, and cyber security awareness training will equip students with the tools and skills they need to be safe online.
Since students are provided with devices to access the internet by their parents or their educators, a simple way to better protect students is to employ cyber security solutions on these devices. As education becomes more digital, for school systems that provide tablets and computers for students, Check Point provides a suite of solutions to secure students. These solutions prevent uncontrolled exposure to inappropriate website content, phishing, and advanced cyber threats targeting students and their personal information. Check Point’s cyber security solutions for education protect against all imminent threats, are easy to implement, facilitate meeting compliance mandates, and keep students’ online access safe and regulated. Please reference the Check Point solution overview for K-12 education here: https://www.checkpoint.com/downloads/products/harmony-education-solution-brief.pdf
For parents providing devices for their children, Check Point offers a similar consumer product, ZoneAlarm, which incorporates features from the Check Point Harmony suite to prevent malware, phishing, ransomware, and other zero-day threats. Please reference the Zone Alarm information here: https://www.zonealarm.com/
For over 30 years, Check Point’s mission has been to secure the digital world for everyone, everywhere and we pursue this mission by preventing attacks before they happen with an industry-leading 99.8% threat prevention rate. So, the best way to secure the devices that young children are using is to install prevention-first cyber security solutions onto the devices.
While securing the devices helps prevent attacks from happening, a multi-layered approach to security should also include cyber security awareness education programs. Safe internet use lessons for children, including topics like keeping information private on social media, being wary of online scammers, and how to report/stop cyber bullying, would greatly benefit students. Based on a report from the Children’s Commissioner, parents share an average of 71 photos and 29 videos of their children every year and children will share their own content to social media over 70,000 times by age 18. This abundance of information makes it easy for attackers to profile their victims and use the information that they post against them.
Educating parents and children about limiting the personal information that they share online will help prevent attacks. Educating students about different types of scams and attacks will also help prevent children from engaging in cyber bullying and with online financial scammers. Teaching kids to be critical thinkers and practicing situational awareness when engaging with cyber space will better ensure that they are on-guard and don’t fall prey to basic scams that cause tremendous harm.
If this cyber security education is provided to students in a way that is engaging and easy to understand, students will regain the knowledge effectively. Creating lesson plans that contain interesting topics, like generative AI, social media safety, and preventing online gaming scams, will ensure a fun learning experience and an abundance of engagement on the part of the students. Bringing in guest cyber security speakers or employing online games are great ways for educators to teach cyber security topics without requiring the educators to be cyber security experts themselves. There is an abundance of options for helping students be safe online and it is extremely important that students are equipped with the tools and skills to remain safe in the increasingly dangerous online environment.
K-12 cyber security education resources
Fun online games (all games have NO LOGIN requirements to ensure students do not have to share any information to engage with the content)
https://sos.fbi.gov
Game for 3rd – 8th graders that works on tablets, mobile devices, or computers. Covers topics including internet safety, online etiquette, smart sharing, securing systems, and protecting against attackers.
https://beinternetawesome.withgoogle.com/en_us
Game for 2nd – 6th graders that works on tablets, mobile devices, or computers. Game is available in multiple languages. Covers topics including smart sharing, recognizing scams, staying secure online, online etiquette, and how to report online incidents.
https://www.pbs.org/wgbh/nova/labs/lab/cyber/
Game for 4th – 8th grade students that works on computers. The game is designed to teach students how to recognize and thwart cyber attacks. Students play as a startup company with in-sufficient security and are tasked with creating a security strategy to prevent hackers from infiltrating their company.
https://overthewire.org/wargames/
Game for 8th – 12th grade students that works on computers. This game is more advanced and tasks students with learning cyber security topics while practicing ssh and linux scripting skills.
https://public.cyber.mil/training/cyber-awareness-challenge/
Training style game for 7th – 12th graders that works on computers. This game is geared towards teaching users how to mitigate threats and vulnerabilities. The training provides an overview of cyber threats and best practices to stay secure online.
#000#2023#Accounts#ai#anxiety#approach#attackers#awareness#background#Behavior#challenge#channel#Check Point#Check Point Software#Children#Cloud#compliance#computers#consulting#content#credit card#crime#cyber#cyber attackers#cyber attacks#cyber crime#cyber criminals#cyber security#cyber security awareness#Cyber security education
0 notes