#cyber security awareness
Text
The 5 Common Cybersecurity Threats And How To Protect Against Them

Cybersecurity is an ever-growing concern for individuals and businesses alike. With the increasing reliance on technology and the internet, the threat of cyber-attacks is becoming more prevalent. In this blog post, we will look at the five common cybersecurity threats and how to protect against them.
1. Phishing
Phishing is one of the most common cybersecurity threats. Attackers will send emails or messages that appear to be from a legitimate source, such as a bank or a government agency, to trick the recipient into providing sensitive information. This information can include login credentials, credit card numbers, and other personal information. To protect against phishing, it is essential to be sceptical of unsolicited emails or messages. Never click on links or provide information without verifying the authenticity of the sender. Additionally, many companies and organisations offer training programs to help employees recognise and avoid phishing attempts.
2. Ransomware
Ransomware is a type of malware that encrypts a victim’s files and demands payment in exchange for the decryption key. This can be devastating for businesses, as it can prevent them from accessing important files and data. To protect against ransomware, it is essential to back up your important files regularly. This will ensure that you have a copy of your data that can be restored in the event of an attack. Additionally, keeping your operating system and antivirus software up to date can help prevent malware from being installed on your computer.
3. Malware
Malware is any software designed to harm a computer or network. This can include viruses, worms, and Trojans. Malware can be spread through email attachments, downloads, and even through visiting compromised websites. To protect against malware, it is essential to keep your operating system and antivirus software up to date. Additionally, be cautious of suspicious emails or downloads, and never install software or open attachments from unknown sources.
4. Social engineering
Social engineering is the use of psychological tactics to manipulate people into revealing sensitive information. This can include phishing, pretexting, and baiting. Social engineering attacks can be challenging to detect and prevent, but there are steps you can take to protect yourself. Again, be sceptical of unsolicited emails or messages and never reveal personal information without verifying the authenticity of the sender. Additionally, many companies and organisations offer training programs to help employees recognise and avoid social engineering attempts.
5. Distributed Denial of Service (DDoS) attack
DDoS attacks involve overwhelming a website or network with traffic from multiple sources to make it unavailable to users. This can be devastating for businesses, as it can prevent customers from accessing their websites or services. To protect against DDoS attacks, it is essential to implement security measures such as firewalls and intrusion detection systems. Additionally, working with a managed service provider that can monitor your network and respond to attacks in real time can help prevent and mitigate DDoS attacks.
In conclusion, it is crucial to be aware of the common cybersecurity threats and take the necessary steps to protect yourself and your organisation. By being sceptical of unsolicited emails or messages, keeping your operating system and antivirus software up to date, being cautious of suspicious downloads, having a proper backup in place and considering working with a managed service provider, you can significantly reduce your risk of falling victim to a cyber-attack. It is also essential to stay informed and up to date on the latest threats and trends in cybersecurity so that you can adapt your security measures accordingly. Remember, prevention is always better than cure, so take the time to secure your systems and data.
This blog post was originally published here.
0 notes
Text
Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity
In today’s interconnected world, where the internet serves as the backbone of communication, commerce, and information exchange , the importance of cybersecurity cannot be overstated.
From personal data breaches to large-scale cyber attacks on governments and corporations, the digital landscape is fraught with threats that constantly evolve in sophistication and scale.
As we navigate this complex ecosystem, understanding the significance of cybersecurity becomes paramount to protecting our privacy, safeguarding our assets, and preserving the integrity of our digital infrastructure.

The Cyber Threat Landscape
Cyber threats come in various forms, ranging from malware and phishing attacks to ransomware and DDoS (Distributed Denial of Service) assaults.
These threats exploit vulnerabilities in software, networks, and human behavior to gain unauthorized access, steal sensitive information, or disrupt critical services.
Best Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity-2024.
With the proliferation of connected devices and the advent of the Internet of Things (IoT), the attack surface has expanded exponentially, presenting new challenges for cybersecurity professionals and organizations worldwide.
The Stakes of Cybersecurity
The consequences of cyber attacks can be severe and far-reaching, impacting individuals, businesses, and governments alike. For individuals, falling victim to identity theft or financial fraud can result in substantial financial losses and emotional distress.
Moreover, the compromise of personal data can lead to reputational damage and undermine trust in online services and platforms. Best Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity-2024. In the corporate sphere, data breaches can have devastating implications, ranging from regulatory fines and legal liabilities to loss of intellectual property and market competitiveness.
Moreover, the disruption of business operations due to cyber attacks can result in significant revenue losses and damage to brand reputation. In extreme cases, cyber attacks targeting critical infrastructure, such as power grids and transportation systems, can pose a threat to public safety and national security.
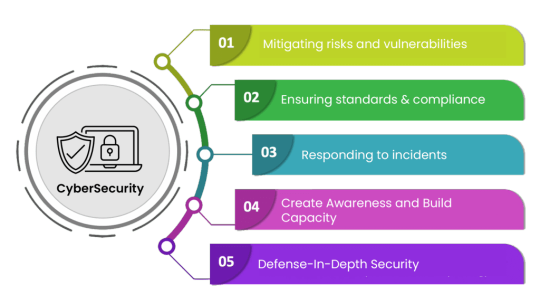
The Role of Cybersecurity
In light of these challenges, the role of cybersecurity is to mitigate risks, detect threats, and respond effectively to cyber incidents. This encompasses a wide range of measures and practices aimed at fortifying defenses, enhancing resilience, and fostering a culture of security awareness. Best Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity-2024 Some key pillars of cybersecurity include:
1. Risk Management
Identifying and prioritizing potential risks based on their likelihood and impact is essential for allocating resources effectively and implementing appropriate controls. This involves conducting risk assessments, establishing risk tolerance thresholds, and developing mitigation strategies tailored to the organization’s needs and priorities.
2. Security Controls
Implementing robust security controls is critical for protecting against a diverse array of cyber threats. This includes deploying firewalls, intrusion detection systems, antivirus software, and encryption protocols to safeguard networks and data assets.
Additionally, implementing access controls, least privilege principles, and multi-factor authentication mechanisms can help prevent unauthorized access and limit the blast radius of security incidents. Best Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity-2024.
3. Incident Response
Despite best efforts to prevent cyber attacks, breaches and incidents may still occur. An effective incident response plan enables organizations to detect, contain, and mitigate the impact of security breaches in a timely and coordinated manner.
This involves establishing clear roles and responsibilities, defining escalation procedures, and conducting regular drills and tabletop exercises to test the efficacy of response capabilities.
4. Security Awareness
Human error remains one of the weakest links in cybersecurity defenses. Educating employees and end users about common threats, phishing scams, and best practices for securely handling sensitive information is essential for fostering a security-conscious culture.
This includes providing regular training sessions, phishing simulations, and awareness campaigns to reinforce good security habits and empower individuals to become vigilant guardians of their digital assets. Best Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity-2024.
The Evolving Landscape of Cybersecurity
As technology continues to advance and cyber threats evolve, the field of cybersecurity must adapt and innovate to stay ahead of adversaries. Artificial intelligence and machine learning algorithms are increasingly being leveraged to enhance threat detection, automate incident response, and augment human capabilities in analyzing vast amounts of security data.
Moreover, the rise of cloud computing, mobile devices, and remote work arrangements has reshaped the traditional perimeter-based security model, necessitating a shift towards more dynamic and context-aware approaches to defense.
Zero-trust security architectures, micro segmentation, and secure access service edge (SASE) frameworks are emerging as key paradigms for securing distributed environments and hybrid infrastructures. Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity.
Furthermore, collaboration and information sharing among industry stakeholders, government agencies, and cybersecurity professionals are essential for fostering collective defense and addressing shared threats effectively.
Initiatives such as information sharing and analysis centers (ISACs), threat intelligence sharing platforms, and public-private partnerships play a vital role in promoting collaboration, facilitating threat intelligence exchange, and building resilience against cyber attacks.
Conclusion- Best Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity-2024
In conclusion, cybersecurity is not merely a technical challenge but a fundamental imperative for the digital age. As our reliance on technology grows, so too does the need for robust cybersecurity measures to protect our digital assets, preserve our privacy, and uphold the trust and integrity of the online ecosystem.
By investing in cybersecurity awareness, education, and innovation, we can collectively strengthen our defenses and navigate the complexities of the digital realm with confidence and resilience. Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity. Best Safeguarding the Digital Realm: Exploring the Vitality of Cybersecurity-2024.
0 notes
Text
youtube
Cybersecurity is the practice of protecting computer systems, networks, data, and digital information from various threats and attacks, with the goal of ensuring the confidentiality, integrity, and availability of these resources. In today's highly interconnected and digital world, cybersecurity plays a crucial role in safeguarding sensitive information and maintaining the functionality of critical infrastructure.
In the digital landscape, various entities, including individuals, businesses, governments, and organizations, face an array of cyber threats such as hacking, malware, phishing, ransomware, and data breaches. These threats can lead to financial losses, privacy violations, disruption of services, and even compromise national security.
To counter these threats, cybersecurity employs a multifaceted approach that involves technical solutions, policies, and human behavior. It encompasses a variety of disciplines, including information security, network security, application security, and more.
The importance of cybersecurity has grown exponentially with the increasing reliance on technology for personal, business, and government operations. As more and more sensitive data is stored, transmitted, and processed electronically, the risks associated with cyber threats have become more sophisticated and diverse.
Protecting yourself from online security threats is crucial in today's digital age, where cyberattacks and data breaches have become commonplace. Implementing effective security measures can help safeguard your personal information, financial data, and overall online presence.
By taking some comprehensive steps to protect your online security, you can significantly reduce the risk of falling victim to cyberattacks, data breaches, and other online threats. While no security measure is foolproof, a combination of awareness, vigilance, and proactive precautions can greatly enhance your online safety.
Escaping The Dangers: Ensuring Your Online Security
#cyber security#cybersecurity#what is cyber security#ethical hacking#escaping the dangers#ensuring your online security#LimitLess Tech 888#importance of cybersecurity#cyber security awareness#types of cyber security#why cybersecurity is important#cyber security basics#cyber security explained#how cyber security works#introduction to cybersecurity#cyber crime#dangers of online security#how to ensure your safety#how to stay safe online#cyber security threats#Youtube
0 notes
Text
youtube
Cybersecurity is the practice of protecting computer systems, networks, data, and digital information from various threats and attacks, with the goal of ensuring the confidentiality, integrity, and availability of these resources. In today's highly interconnected and digital world, cybersecurity plays a crucial role in safeguarding sensitive information and maintaining the functionality of critical infrastructure.
In the digital landscape, various entities, including individuals, businesses, governments, and organizations, face an array of cyber threats such as hacking, malware, phishing, ransomware, and data breaches. These threats can lead to financial losses, privacy violations, disruption of services, and even compromise national security.
To counter these threats, cybersecurity employs a multifaceted approach that involves technical solutions, policies, and human behavior. It encompasses a variety of disciplines, including information security, network security, application security, and more.
The importance of cybersecurity has grown exponentially with the increasing reliance on technology for personal, business, and government operations. As more and more sensitive data is stored, transmitted, and processed electronically, the risks associated with cyber threats have become more sophisticated and diverse.
Protecting yourself from online security threats is crucial in today's digital age, where cyberattacks and data breaches have become commonplace. Implementing effective security measures can help safeguard your personal information, financial data, and overall online presence.
Escaping The Dangers: Ensuring Your Online Security
#cyber security#cybersecurity#what is cyber security#ethical hacking#escaping the dangers#ensuring your online security#LimitLess Tech 888#importance of cybersecurity#cyber security awareness#types of cyber security#why cybersecurity is important#cyber security basics#cyber security explained#how cyber security works#introduction to cybersecurity#cyber crime#dangers of online security#how to ensure your safety#how to stay safe online#cyber security threats#Youtube
0 notes
Text
Tech Consulting Firm To Help Your Business Grow
In the dynamic landscape of technology-driven business evolution, securing the services of a proficient technology consultant is paramount for navigating emerging tech trends.
Amtex Systems, a key player in this domain, distinguishes itself by providing tailored solutions for businesses seeking to leverage cutting-edge technology securely for sustainable growth.

How Amtex Systems Facilitates Technological Growth:
Holistic Cybersecurity Integration:
Tailoring strategies for seamless integration of emerging technologies while prioritizing robust cybersecurity measures.
Implementing cutting-edge innovations to fortify businesses against evolving cyber threats.
Client-Centric Customization:
Adopting a consultative approach to comprehend the unique challenges and goals of each client.
Personalizing technology solutions with a dedicated focus on meeting cybersecurity needs.
End-to-End Technological Support:
Offering comprehensive services encompassing strategic planning, technology road mapping, software development, and system integration.
Providing ongoing support to ensure sustained efficiency and security in the evolving tech landscape.
Pioneering Innovations in Cybersecurity:
Staying at the forefront of tech trends, particularly in cybersecurity, through continuous research and implementation.
Leveraging advanced technologies such as AI-driven threat detection to enhance cybersecurity measures.
Agile Solutions for Adaptive Security:
Navigating the dynamic tech landscape with an agile approach to ensure businesses remain flexible.
Adopting the best ways to enhance cybersecurity and proactively adapting to emerging threats for long-term security.
Conclusion: In conclusion, We emerge as a pivotal ally for businesses seeking secure and efficient technological growth. With a commitment to holistic cybersecurity, client-centric customization, end-to-end technological support, pioneering cybersecurity innovations, and agile solutions, Amtex Systems is not just a technology partner but a strategic guide for unlocking businesses' full potential in the digital era.
Strategic Technology Consulting Services | Amtex Systems
0 notes
Text

Dark Net Email #Shorts
In this video, we will talk about the highest level of security, privacy and anonymity you can achieve using the dark web email providers. Watch this video dark net email and know more about it.
#dark net#dark net email#dark net email shorts#security professional#cyber security course#how do you get to the dark web#best free email service#dark web search engine#how to access the dark web safely#how to learn cyber security#cyber security awareness#top 20 email providers#inside the dark web#dark web browser#what is dark web#cyber security training#cyber security types#dark web login#dark web videos
0 notes
Text
youtube
I will show you a couple methods to generate PGP keys and we will also see some of the attributes that we need to configure in order to generate a secure key. Once you have the key, we will also see how to use them to securely exchange the information.
#pretty good privacy#pgp public key#cybersecuritytv#how to learn cyber security#cyber security awareness#cyber security training#cyber security#Youtube
0 notes
Text
how cybersecurity can impact us when Data breaches and loss of personal information

I. Introduction
Cybersecurity is the practice of protecting devices, networks, and sensitive information from unauthorized access, use, disclosure, disruption, modification, or destruction. In today’s digital age, cybersecurity is more important than ever, as the amount of personal and sensitive information stored online continues to grow.
One of the biggest threats to cybersecurity is data breaches, which occur when an unauthorized individual or group gains access to sensitive information. Data breaches can result in the loss of personal information, such as credit card numbers, social security numbers, and other sensitive information. The consequences of data breaches can be significant, both for individuals and organizations. In this blog post, we will explore the different types of data breaches, the consequences of data breaches, and how to protect yourself and your organization from data breaches and loss of personal information.
II. Types of Data Breaches
There are many different types of data breaches, but some of the most common include:
Hacking: This occurs when an unauthorized individual or group uses technology to gain access to sensitive information. Hackers may use a variety of techniques, including malware, phishing, and social engineering to gain access to personal information.
Phishing: This occurs when an individual or group uses email, social media, or other online communication to trick individuals into providing sensitive information. Phishing scams are often designed to look like legitimate communications from banks, government agencies, or other organizations.
Insider threats: This occurs when an individual with authorized access to sensitive information misuses that access to steal or compromise the information. Insider threats can be caused by employees, contractors, or others with authorized access to sensitive information.
Examples of real-world data breaches include the 2017 Equifax data breach, which affected 147 million people and resulted in the loss of personal information such as social security numbers, birth dates, and addresses. Another example is the 2020 Twitter hack, where 130 high-profile twitter accounts were compromised, and tweets were sent from the accounts asking people to send Bitcoin to a specific address.
III. Consequences of Data Breaches
Data breaches can have serious consequences, both for individuals and organizations. Some of the immediate consequences of data breaches include:
Financial loss: Data breaches can result in the loss of money, as individuals may be held responsible for fraudulent charges or other financial losses.
Reputational damage: Data breaches can damage the reputation of organizations and individuals, as customers may be less likely to trust them in the future.
Loss of trust: Data breaches can result in the loss of trust between individuals and organizations, as individuals may be less likely to share sensitive information in the future.
Data breaches can also result in the compromise of personal information, which can lead to serious long-term consequences such as identity theft and online fraud. For example, if an individual’s social security number is compromised in a data breach, they may be at risk of identity theft, where the attacker uses the stolen information to open credit card accounts or take out loans in the individual’s name.
IV. Protecting Yourself and Your Organization
To protect against data breaches, individuals and organizations can take steps to secure their sensitive information. Some best practices include:
Implementing strong passwords: Strong passwords can help prevent unauthorized access to sensitive information.
Using encryption: Encryption can help protect sensitive information by making it unreadable to unauthorized individuals.
Regularly updating software: Keeping software up to date can help protect against security vulnerabilities.
Organizations also have a responsibility to protect their customers’ personal information. This includes implementing security measures to prevent data breaches, as well as quickly responding to data breaches when they do occur. This can include not
ifying customers of a data breach, providing resources and support to customers who may have been impacted, and taking steps to prevent similar breaches from happening in the future.
V. Conclusion
In conclusion, data breaches and the loss of personal information can have serious consequences for individuals and organizations. It is important to be aware of the different types of data breaches and the steps that can be taken to protect against them. By implementing strong passwords, using encryption, and regularly updating software, individuals and organizations can take steps to protect themselves from data breaches and loss of personal information. It’s also important for organizations to take their responsibility to protect their customers’ personal information seriously and to respond appropriately in the event of a data breach.
🔔 please like share and subscribe my channel ‼️
🌈 Connect with me on social 🎉
►► E-mail : [email protected]
►► WordPress : https:/www.grocery-x.com/
►► Medium : https://grocery-x.medium.com/
►► Quora : https://www.quora.com/profile/Grocery-Shop-3
►► Blogger : https://grocery-x.blogspot.com/
►► Tumblr : https://www.tumblr.com/grocery-x
►► YouTube : https://www.youtube.com/@grocery-X
►► Goo blog : https://blog.goo.ne.jp/grocery-x
►► pixnet : https://www.pixnet.net/pcard/groceryx1416/
►► skyrock : https://grocery-x.skyrock.com/
🎦 Watch related playlists🌐
WELCOME TO MY GROCERY — X LEARN ENGLISH PODCAST
►► https://youtu.be/NMOdbzaMhKA
►► https://youtu.be/v_yR1VAm8eU
►► https://youtu.be/Hd7ZMEcZiZo
►► https://youtu.be/dRhUDK35eDo
►► https://youtu.be/h9J4J08CA5k
►► https://youtu.be/YKtdTLDfNno
►► https://youtu.be/eUqWSUl42OI
►► https://youtu.be/mK5OqnD4GNk
►► https://youtu.be/QZfejKWKlVU
❤️ AFFILIATE LINKS 💖
►► link1 : https://www.digistore24.com/redir/449013/Grocery-X/
►► link2 : https://www.digistore24.com/redir/449013/Grocery-X/
►► link3 : https://www.digistore24.com/redir/449013/Grocery-X/
►► link4 : https://www.digistore24.com/redir/449013/Grocery-X/
►► link5 : https://www.digistore24.com/redir/449013/Grocery-X/
►► link6 : https://originality.ai?lmref=C7F8gA
►► link7 : https://pictory.ai?ref=grocery56
►► link7 : https://murf.ai/?lmref=7x4Peg
#Cybersecurity#Cyber Security Awareness#Cybersecurity Awareness#Cyber Security Services#Cyber Security Solutions
0 notes
Text
The National Security Alliance and the U.S. government are in charge of it. Cyber security awareness is essential, given how crucial security is today.
#cyber security awareness day#cyber security awareness#cyber security awareness month 2022.#cisa cybersecurity awareness month#cyber security awareness month ideas#cybersecurity awareness month champion#cyber security awareness month 2022 theme#cyber awareness#army cyber awareness#cybersecurity awareness month#cyber awareness training#national cybersecurity awareness month#cyber security training for employees#cyber awareness 2022
0 notes
Text
The Importance Of Cyber Security Training For IT Professionals

Cyber security is a rapidly growing concern for businesses of all sizes, and IT professionals play a critical role in protecting an organisation from cyber threats. However, to effectively protect an organisation from cyber-attacks, IT professionals must be adequately trained in cyber security best practices.
One of the most important reasons for IT professionals to receive cyber security training is to stay current with the latest threats and vulnerabilities. The cyber threat landscape is constantly evolving, and new threats and vulnerabilities are discovered regularly. IT professionals who are not adequately trained may not be aware of the latest threats or may not know how to protect against them effectively. As a result, they may inadvertently leave an organisation vulnerable to cyber-attacks.
Another vital reason for IT professionals to receive cyber security training is to comply with industry regulations and standards. Many industries are subject to strict regulations and standards when it comes to data protection, and IT professionals must be aware of these regulations and standards to ensure compliance. Without proper training, IT professionals may not be aware of the specific regulations and standards that apply to their organisation, which can result in non-compliance and potential fines.
IT professionals are also responsible for implementing and maintaining cyber security technologies and tools. However, without proper training, IT professionals may not know how to properly configure and use these tools, which can leave an organisation vulnerable to cyber-attacks. Additionally, IT professionals must be trained to use these tools effectively to detect and respond to security incidents in a timely manner.
Furthermore, cyber security training for IT professionals is also essential to ensure that they understand the company’s security policies and procedures. This is especially important for those who have access to sensitive information or who are responsible for managing access controls. Understanding these policies and procedures can help IT professionals to identify and prevent potential security incidents.
In conclusion, cyber security training for IT professionals is essential to ensure that they can effectively protect an organisation from cyber threats. By staying current with the latest threats and vulnerabilities, complying with industry regulations and standards, implementing and maintaining cyber security technologies and tools, and understanding the company’s security policies and procedures, IT professionals can help minimise the risk of data breaches and other security incidents.
This blog post was originally published here.
0 notes
Text
Protecting Your Business-Critical Data From Insider Threats

Although today’s technology-driven era has made information sharing and data access very efficient, it has brought forth a new set of challenges. One of the primary challenges businesses face is the rising threat to data security. However, the threat to business data does not always come from external actors.
Worryingly, the greatest threat to business-critical data comes from human elements inside an organization. Since data is the lifeline of most businesses in this digital environment, any compromise can jeopardize operations and bring them to a sudden halt. To avoid this, organizations need to be aware of the threats posed by insiders and implement necessary measures to prevent them.
In this blog, we’ll discuss the cybersecurity risks businesses face from insider threats and how you can mitigate them.
Actors and motivations behind insider threats
There are two main types of actors behind all insider threat incidents — negligent insiders who unwittingly act as pawns to external threats and malicious insiders who become turncloaks for financial gain or revenge.
Negligent insiders – These are your regular employees who do their jobs but occasionally fall victim to a scam orchestrated by a cybercriminal. These actors do not have any bad intentions against your company. However, they are still dangerous since they are involved in a large proportion of all insider threat incidents.
Negligent insiders contribute to data security breaches by:
Clicking on phishing links sent by untrusted sources
Downloading attachments sent from suspicious sources
Browsing malicious or illegitimate websites using work computers
Using weak passwords for their devices
Sending misdirected emails to unintended recipients
Malicious insiders – These are disgruntled employees who wreak havoc on your data security for financial gain or revenge. Disgruntled employees can manipulate the company’s tools, applications or systems, and while financial gain is the top reason behind most malicious insider actions, it isn’t always the case. Despite being rare in occurrence, these threats often have much more severe consequences since the actors have full access and credentials to compromise your security.
Best ways to prevent insider threats and protect data
When a business falls victim to a data security breach, it faces more than just financial repercussions. The organization’s reputation, competitive advantage and intellectual property often suffer following an insider threat incident. Additionally, there are regulations that impose hefty fines on businesses for allowing such a breach to occur. Therefore, you must be proactive when it comes to combating insider threats.
Detecting insider threats
Certain factors can help you identify insider threats before you experience a full-blown breach:
Human behavior: A potential insider with malicious intent against an organization will often exhibit abnormal behavior. For instance, an employee trying to access privileged information and frequently working unusual hours could be red flags to monitor.
Digital signs: Before a major breach due to insider threats, you may witness abnormal digital signs like downloading a substantial amount of data, high bandwidth consumption, traffic from unknown sources or unauthorized use of personal storage devices.
Defense strategies against insider threats
There are a few strategies that you can implement throughout your organization to minimize the possibility of insider threats.
Insider threat defense plan: First, you must define what constitutes abnormal behavior in your employees and set up alerts for digital signs in your IT environment. Most importantly, you need to limit access to critical data to only those whose job function requires it, and you must provide unique credentials for them.
Data backup: Backups are essential to protect your data in case of an unavoidable loss. With regular backups for your critical data, your business can get back up and running after a security breach involving an insider. Before you back up your data, you should classify the data worth protecting and create a strategy accordingly.
Employee training: When properly trained, employees could be your first line of defense against various cyberthreats. Create an organizational-level best practices policy that outlines clear instructions on personal device policies, passwords, remote working, etc
Reach out to us to protect your critical data
As the cost of insider threats is expected to rise over the years, having a trusted partner by your side to protect your data can go a long way towards securing your business.
With our years of expertise in data security and storage, we can help you incorporate innovative strategies to protect your company. Give us a call today!
https://www.infradapt.com/news/protecting-your-business-critical-data-from-insider-threats/
#cyber security#cyber security awareness#Cybersecurity#it security#IT Service#IT Support#Managed Services#MSP#Network Security
1 note
·
View note
Text
UK Cyber Security- Secure Your Company
Hackers create major problems in running the IT department of a business. The problem arises when a data breach takes place. This problem is one of those that can ruin your business without you even knowing it. Silently, this can deny you in the race between your rivals. Researchers have demonstrated that 62% of organizations have admitted to the daily data breaches they suffer, and only 34 % of these organizations have an effective security system in place that can prevent them. It creates pure pressure in your mind and in your business that is very undesirable.
People went out of their way to provide them with a solution and that's where business cyber security came in. As almost 100% of people in the UK use the Internet and every business has an IT part of their business, Cyber security in the UK is one of the most important features you can look for.

You have two options regarding the security of your computer and the Internet. Prevent data breaches even before they happen and have a solution that can show you the perfect process that can fix the situation. Cyber incident response is the best solution if you want to stay safe from becoming the next victim of cybercrime.
With the right Internet security response, you can benefit from immediately actionable security alerts, valuable intelligence, and incident context, and enable adaptive response to complex cyber threats. On the other hand, have an incident response plan. With various new and unique data breach methods and cyber threats, it is almost impossible to have a system ready to stop these attacks. That's why it's imperative to have a plan to escape the aftermath of an attack, and many computer security companies use the best plans that can reduce the impact of these attacks.
Cyber Network Security in the UK is one of the most widely used techniques and this has made it possible for every organization to enjoy hassle-free business and business. Keeping in mind that the Internet is one of those things that have become the first part of our daily lives for professional and personal reasons, taking advantage of the right security is the best thing you can do. As more businesses get established, cyber security requirements also increase. If you don't pay enough attention to the security of your IT part, you could suffer damage.
Source & Reference: https://sites.google.com/view/ardentity-cyber/uk-cyber-security-secure-your-company
#business cyber security#business information security#cyber security management#cyber security awareness#computer security companies
0 notes
Text
5 tips for an effective security awareness program
5 tips for an effective security awareness program
5 tips for an effective security awareness program | Security Magazine
This website requires certain cookies to work and uses other cookies to help you have the best experience. By visiting this website, certain cookies have already been set, which you may delete and block. By closing this message or continuing to use our site, you agree to the use of cookies. Visit our updated privacy and…

View On WordPress
#benchmarking reports#cyber security awareness#employee security#Featured#security awareness training#security culture
0 notes
Text
Research_Overview
It is fair to say, I like keeping busy. One way I do this is through working as a part-time research assistant at my University. The focus of the research is on context aware multifactor authentication (MFA), which is to say, how can we determine users are who they claim to be, using the context their phone and actions provide. This could be looking at their phone specs or typing speed to see if anything changes between each authentication or simply randomizing what form of authentication they use.
But eroz-codes, doesn't that seem like overkill? Well, maybe. The end goal is that this would be implemented in the industrial control systems (ICS) that support a countries critical infrastructure and, in the scope of my research, specifically the energy sector. There is a potential that if a malicious actor were to gain access to an ICS they could do a good deal of permanent damage to said country. This damage could range from small outages across to a full power grid being shutdown. So no, with that in mind, I think context aware MFA has a lot of potential to add a much needed layer of security.
My team is achieving this goal by creating an app that simulates the authentication process. We are seeing how much information we can gain from the user without them having to jump through unnecessary hoops. There is a saying that the challenge in cybersecurity is striking the balance between security and usability. You can have the most secure system in the world, but if it's too difficult for users to navigate, they'll find ways to work around it, compromising security in the process. Hopefully, this will maintain that balance without causing a need for users to find a loop hole.
All in all, I adore what I do. I find the concept intriguing and feel like I am doing something to help keep people safe, which is really what cybersecurity is all about. It's easy, I think, for professionals to feel discouraged when their work goes unappreciated especially in this field when you sometimes only get noticed when something goes wrong. My two cents is what you put into the world is far more important than how you look to it. Feel fulfillment from the fact that you are using your knowledge to protect something and are doing it so well that it seems almost effortless.
#research#context aware mfa#mfa#multifactor authentication#codeblr#cybersecurity#security#cyber security#I dont know if the two cents I gave is a quote#but i love that saying regardless#if anyone knows if it is a direct quote hmu
0 notes
Text
Beyond Change Healthcare
The continued onslaught of cybersecurity attacks which if anything are only getting worse have impacted the healthcare system in dramatic fashion with the payment network brought down by the attack on Change Healthcare.
Healthcare under Cyber Attack
I keep hoping that we all get better at combatting these attempts to breach our data and that overall vigilance rises as we become more wary of…

View On WordPress
#cyber attacks#cyber awareness#cyber defense#cyber hygiene#cyber resilience#cyber safety#cyber threats#CyberCrime#Cybersecurity#cybersecurity awareness#cybersecurity best practices#cybersecurity challenges#cybersecurity culture#cybersecurity education#cybersecurity measures#cybersecurity news#cybersecurity protocols#cybersecurity resources#cybersecurity risks#cybersecurity solutions#cybersecurity strategy#cybersecurity tips#cybersecurity training#cybersecurity trends#data breach#data encryption#data protection#data security#Digital Health#Healthcare
0 notes
Text
Cybersecurity Report: Protecting DHS Employees from Scams Targeting Personal Devices
🔒 DHS Cybersecurity Alert! 🔒 Scammers targeting personal devices threaten national security. Our new report reveals these risks & offers robust solutions - MFA, security software, cybersecurity training & more. Safeguard yourself & critical operations!
Introduction
The digital age has ushered in an era of unprecedented connectivity and technological advancements, but it has also given rise to a new breed of threats that transcend traditional boundaries. Cybercriminals are constantly evolving their tactics, exploiting vulnerabilities in both organizational systems and personal devices to gain unauthorized access, steal sensitive data, and…

View On WordPress
#access controls#antivirus#awareness campaigns#best practices#collaboration#cyber resilience#cybersecurity#cybersecurity training#data backup#data protection#DHS#firewall#government#impersonation#incident response#insider threats#malware#multi-factor authentication#national security#password management#personal device security#phishing#physical security#public outreach#risk assessment#scams#social engineering#software updates#threat intelligence#VPN
0 notes