#Free Model Pose Review
Text
Bethany's Bizarre Miraculous Reviews Episode 3-23: Felix
Ah, yes. PV Adrien. Except not really. And he knows he wasn't created the usual way but that's for later seasons or something. You ever think about how Felix with the Black Cat Miraculous would be Felix the Cat? I think of that constantly.
Does anyone have a scan of that bar of Marinette and her classmates that scrolls up quickly in the title sequence? Thanks in advance.
*Puts a wedding/magic ring around my basically dead wife*
Yippee! Natalie and Adrien smiling and waving at eachother!
Yippee! Communication between father and son!
Damn. One measily year? Really shows how short of a time Ladybug and Chat have been out for. Puts her KOing some time in Late April or Early May too based on my calendar for Miraculous.
EVERYONE IS HERE!
The Amelie reveal was pretty fun, honestly. Also they know damn well Adrien and Felix are clones.
Ring drama. Ring drama.
Yes! The perfect thing to say! Confess to him! Rip off the band-aid!
So does Felix dislike Adrien because he's servile to his father? Shouldn't he hate Gabriel instead then?
Why is Felix such an asshole? Why does he hate everyone? For what reason? Just because they weren't created by the Peacock Miraculous? Where were the other video messages?
Luka being amazing as always. Fine with whoever Marinette ends up with but will be there if she's alone. That's why he's the GOAT.
Natalie's still siding with Hawkmoth and is happy to akumatize people. Points docked.
Here comes the disrespect. How come Hawkmoth can just do personalized akumas instead of akuma groups? And why those old models? Oh right. Budget.
Love me a clone gun conundrum!
Natalie fighting off the Akumas on her own. Credit where it's due, swag.
Oh. That's who's who. In hindsight I should've checked the rings.
Seriously? Sexually harassing the woman trying to save you?
Bro's literally risking the apocalypse for Gabriel's rings. You won't be free if you're erased from reality alongside literally everything else.
So Hawkmoth can just ventriloquist through his akumas now? And they no longer have vengeance for Felix?
Oh hey! Someone getting properly punished for their actions and realizing they were at fault completely! Hopefully! I'm sure this will keep on happening, at least for Felix!
*Steals your ring*
He's so mad about it too lmao
I'm glad I got to see Luka. And Kagami for a split second. Also Felix is definitely an interesting character, to say the least. Was the "posing as evil Adrien" thing supposed to help Adrien in the long run? Was this all one big long master plan? How far down does the rabbit hole go?
#miraculous ladybug#miraculoustalesofladybugandcatnoir#miraculous#marinette dupain cheng#miraculous marinette#ml ladybug#adrien agreste#miraculous adrien#chat noir#ml chat noir#lukanette#felix graham de vanily#felix fathom#miraculous felix#juleka disrespect#rose disrespect#Her akuma is mid#also why not#alya disrespect#everyone is here
14 notes
·
View notes
Text

A few years after we were empty-nesters my husband suggested I look for part-time work to supplement or household income. I started watching help-wanted classifieds in the newspaper and came across on that said: "Seeking fit, attractive "matures" for bikini/lingerie modeling sessions with local photographers. To apply send recent photos---full body---and contact info." My husband was skeptical I'd get hired but as requested I sent in a few photos of me. To my surprise they called me and said they wanted to do an "in-person." They suggested I bring some lingerie and bikinis to model for the in-person interview. When I arrived for the interview I was given an extensive "Model Questionnaire" form to fill out which I completed but was quite surprised at how detailed the questions were and of such a personal nature about me. Once I completed the questionnaire they asked me to change into the lingerie I had brought. Once dressed in the lingerie, they took me to a studio to pose for them as 2 photographers snapped away. The manager instructed me to pose in various positions as I was photographed. He seemed pleased with my on-camera performance. As the session progressed, he asked me to lower my bra for a series of photos they would take for my modeling file. I was a bit hesitant to pose topless but he said these photos were a required part of the "in-person" interview. They needed a comprehensive set of shots of my body for the team to review before hiring me. I really wanted the job so reluctantly lowered my top as they photographed me topless. After posing topless he asked me to now take off my panties for the final set of photos of m body. He assured me that these were strictly for my file and for the team to review prior to hiring me. Again, he said this was a mandatory part of the hiring interview and to go ahead and lower my panties. I shyly lowered my panties and when they were off discreetly covered my privates with my hand. They started photographing me as I stood there completely nude in the studio. He then instructed me to sit in the chair in the studio. Once in the chair, he came over to me and with his hands on my knees and said, "Now let's open your legs for a closer view of your pussy." He then spread my legs wide open as I sat in the chair with my pubic region fully visible. They then photographed me like that as I sat in the chair. He then said I have one last pose for you. "With your hands, please pull your labia apart for us, so you are totally opened for the camera. Give us all a peek up inside that precious pussy of yours." I don't know why but I had gone this far---they already had full body photo of me completely nude, privates and all---so I went ahead and complied pulling my labia wide open so my vaginal canal was clearly visible. As they photographed me the manager noticed that I was extremely wet---I was glistening down there---and commented that I was clearly enjoying myself as I posed for them. He said lots of girls who apply for modeling jobs thoroughly enjoy it and it is not uncommon for girls to get wet like I was as they posed. He said I should feel free to rub my pubic region if I was inclined and my clitoris too. It felt awkward and a bit embarrassing but as they all watched me I began rubbing my clitoris. It felt quite erotic to be doing this in front of these men and the manager suggested I also slide a finger or two into me. Or if I'd like, he'd gladly do it for me and, as I rubbed my clitoris, he came forward, and without hesitation or warning slid his finger right inside me. "Let me finger you to an orgasm for us," he said as I rubbed my clitoris and he went in and out of me with deep strokes. I was getting more and more aroused and he slid another finger, then another into me as they continue to photograph me. I also realized there was a video camera now filming me like this as the manager continued to stimulate my vagina with his fingers. I could now feel my orgasm approaching and began to moan softly as I rubbed my clitoris avidly. More later....
2 notes
·
View notes
Text
WRITER GEM:
Two weeks ago, at the Half Priced Bookstore in my area (one of my greatest loves :)), I wandered into the clearance section and found a book called DIY MFA. When I pulled it off the shelf—randomly, I might add—my immediate reaction was visceral. I gasped and clutched it close to my chest. Because as writers, we’re often told that graduate school is a must-do for publishing, right? We see it written on the backs of novels in author blurbs all the time. We hear it from our undergrad schools and professors. To “make it” is to burn through academia according to a certain timeframe and by a specific age. Such are the expectations, anyway.
But what if this isn’t practical? Whether its finances, time constraints, or another completely valid and reasonable explanation, that envied master’s degree can pose a problem. As a rising junior in college, these problems have been on my mind for many months already. And as someone who is constantly searching for writing advice to share with others, I thought this would be a great feature for the page.
DIY MFA is a book, and general model of learning, with three core principles, all of which can be found on the website: http://www.diymfa.com. These principles are: writing with focus, reading with purpose, and building community. The “about” section states that “the beauty of DIY MFA is that while it covers most of what you’d get in a traditional MFA, you get to decide how to structure your writing, reading and community so you can reach your goals.” Pretty cool, right? I thought so! And while I haven’t immersed myself just yet, on account of wanting to structure my newest WIP before jumping in, both the book and website have given me a lot to reconsider.
Other notable exploratory sections on diymfa.com include the “writer igniter,” which is a prompt generator, in addition to free starter kits, podcast episodes, articles, and speaker videos.
As far as I can tell from Amazon and Goodreads reviews, this might not be the greatest option for those seeking advice for less traditional writing forms such as comics, graphic novels, and children’s books, to name a few, but the concepts and tools will work well for any genre and aspiring writer, provided you are dedicated to see your project through. I actually think that this could be an avenue of exploration for the project in the future. It was published in 2016 though, so I’m excited for whatever might be in store in the next few years!
Have you tried this book or learning model out? What did you think?
Follow @diymfa for more information ✏️
#writers#writerslife#writing community#writersociety#writing#writing problems#writing advice#writing tips#masters fine arts#alternative
7 notes
·
View notes
Text
review roundup: billions 7x08 “the owl”
what a waste of my time! what did reviewers think?
New York Times: ‘Billions’ Season 7, Episode 8 Recap: Going Nuclear
Mike Prince is trying to do the right thing. A man for whom his wife, Andy, cares deeply has had a mountain-climbing accident in the Himalayas. He is injured and alone, in the path of a storm, running out of food and stranded on the Chinese side of the mountains.
Mike has the resources to arrange a successful extraction, even under these physically and politically dangerous conditions. To rescue the man means risking an international incident and potentially ending his presidential campaign. Not to rescue him means the man will die, and Andy will lose someone who is more to her than a friend.
fascinated by the vagueness of the description of andy’s relationship to derek here.
In this secluded environment — clearly modeled after the Bohemian Grove, right down to the choice of its avian mascot — the nearly all-male elite can mix, mingle, urinate in the open air, go streaking through the snow, participate in tests of strength with offensive names and generally enjoy the rights and privileges of being right and privileged.
get their asses!
Known to friends and foes alike as “Fourth,” Pike is there to decide which of these self-conceptualized common-sense mavericks deserves his backing.
He gets his answer in the most horrifying sequence this show has seen since Bobby Axelrod paid a doctor to let a patient die.
i can imagine there were more horrifying sequences, but i can’t think of any right now. (though who knows what the last four episodes might hold? we already know a fresh angle on the printer throwing scene is in there…)
Watching this room full of rich men discuss the incineration of millions as if they’re swapping fantasy football strategies is repulsive; there’s no other way to put it. It’s everything wrong with how decisions are made in this country, as wealthy people in no danger of facing consequences for their actions debate idly which lives are and aren’t worthless when stacked against the overriding importance of their own comfort and ambitions.
i love it when sean goes off like this. it’s a breath of fresh air next to sarene’s “prince is trump, no further questions your honor” analysis and kyle’s “i don’t think michael prince is a dangerous fascist” t-shirt.
Chuck’s quest to stop Prince from reaching the White House — like the parallel sabotage campaign led by Wendy, Wags and Taylor — is predicated on the idea that no man this free of self-doubt belongs anywhere near power, let alone the kind of power present in the nuclear football.
TAYLOR MENTIONED.jpg
Chuck leaves, visibly shaken. If self-styled guardians of the soul of the nation like Fourth don’t understand that they’re selling that soul by backing Prince, what hope does he have?
Which raises another question: Is “Billions” the most chilling show on television right now? And I’m not talking about the wintry setting of this week’s episode. Like virtually every episode since Prince’s presidential ambitions became clear, “The Owl” casts an unflinching eye on the danger posed to American democracy by megalomaniacal strongmen, by the ultra-rich, and especially by the people who are both.
In a sense, this is covered ground for the show. Chuck already took on billionaire overreach when he battled Bobby Axelrod for five seasons. His conflicts with the pointedly unnamed presidential administration in power in the show’s universe from 2017 to 2021, represented by odious officials like Attorney General Jock Jeffcoat and Todd Krakow, made a clear argument that authoritarianism, corruption and reactionary politics are correlated phenomena.
But since Axe never got directly involved in politics, and since the former president was never depicted as an on-screen character, “Billions” has never had such an opportunity to explore all these issues up close by embodying them in one man. And in an episode that depicts the threat he presents in the starkest, most existential terms imaginable, it’s worth noting what that one man actually does.
📣📣📣
To its credit, “Billions” has long presented sexual fetishism and kink not as a source of comedy (OK, not only as a source of comedy), let alone as a marker of deep psychological dysfunction. It has always been presented more as just a part of the sex lives of countless basically normal people (OK, normal by “Billions” standards). It picks up this torch again in a subplot involving Wags’s discovery that he has a certain scatological fetish that initially sends his wife, Chelz (Caroline Day), fleeing from the room. (“Stop saying words out of your mouth!” she stammers in one of the best lines of the night.) When Wendy explains to Chelz that the fetish represents Wags’s desire to be loved unconditionally, despite even the most repugnant parts of himself, Chelz is into it — but for Wags, the explanation kills the mood, like a magician revealing how the trick is done. And I call shenanigans! Figuring out why you’re into the weird stuff you’re into makes it more fun, not less.
a few counterpoints:
from 4x02 onward, billions kind of has treated chuck’s masochism as a marker of psychological dysfunction (overton window speech notwithstanding) and his loss of interest in it over the past two seasons as a sign of positive personal growth.
how much credit does billions deserve for portraying kink positively in the sex lives of certain characters if simultaneously it’s shitting on certain other characters for having (or even wanting) sex lives at all?
are we sure wags and chelz are married? i think that would come up if it had happened. (i know the audio description for this episode refers to her as his wife, but it’s been wrong before.)
in wags’s case, i can believe that having his kink explained would cause him to lose interest. remember how he promised wendy he wasn’t seeing dr. mayer by saying “i prefer those depths unplunged”? this man does NOT want to know himself.
Vulture: Billions Recap: Pissing in the Wind
another four-star rating. who is making you do this, sarene?
“The Owl” is the last, what I would call, “casual” episode. Its minimal plotlines set the stage for the chaos that will ensue over the final four episodes. That’s not a spoiler: remember that we’re still owed three more Axe episodes. And Axe + Billions = chaos.
it can be a spoiler if i bring the plot summaries of the last four episodes into it! but yes, i agree, we’re finally at the stage where things really get wild, even if there wasn’t a proper midseason turning point. watch out for those tempo changes, man, ‘cause when we go into the second bridge last third of the season, this shit takes off.
Before Prince can start communing with nature and the political elite, though, he must solve a problem for his wife, Andy. Apparently, a “friend” of hers was climbing a mountain on the Nepal/China border before tackling Mount Everest, and now he’s injured and trapped on the Chinese side. Oh, and he’s more than just a “friend.”
again with the vagueness! won’t anyone be forthright and say that andy fucked this guy? or at the very least that she slept with him?
As soon as Fourth talks about listening to “new voices” who can lead the country to even more greatness and he dismisses Governor Dunlop’s viewpoints on nuclear weapons usage as “sensible,” it’s game over. Prince almost doesn’t even need to say out loud that he would, without hesitation, bomb a hostile country with plans to launch an attack. But he does. Because Mike Prince feels fine with the end of the world as we know it. In his mind, that’s a better decision than leading with hesitation, which he claims would be Governor Dunlop’s approach. While most gasp in horror, Fourth is impressed, calling Prince’s viewpoint “a nuance few are brave enough to voice” and the embodiment of America’s core value, “strength of nation.”
This is how the 2016 election happened, folks…
*long and loud sigh*
From where Fourth stands, Chuck is small potatoes, and Mike Prince is the man who can Make America Great Again.
*longer and louder sigh*
People sure do weird things when they’re given a lot of power. And in case you really weren’t sure that Mike Prince is the latest Billions character to sell his soul to the devil, the episode’s final images should clear things right up. The Owl retreat concludes with the male attendees, wearing dark, hooded cloaks (better dark than white, I guess) and carrying torches, setting a giant wooded owl statue aflame to the haunting tune of Bob Dylan’s “Blind Willie McTell.”
Good grief, this country is bizarre.
can you please not jump on the “WOAH THEY WERE TOTALLY DOING A SATANIC ILLUMINATI RITUAL TO MOLOCH AT THE END THERE” train? i’ve already seen enough of that on twitter.
I deliberately refuse to discuss the Wags-Chels subplot for two reasons: (1) It felt like a leftover storyline from another season that the writers wanted to squeeze in before Billions concluded. (2) I. Hate. That. Baby. Shower. Game. With. Every. Fiber. Of. My. Being.
this is how i first found out that that was a real baby shower game. i hate it here. and yes, it felt like something that belonged into an earlier season, when neither wendy nor wags had anything better to do — such as, say, working on that plan to topple their would-be authoritarian boss when he happened to be three hundred miles away for two days — than analyzing wags’s new weird kink.
Fan Fun with Damian Lewis (Damianista): Billions on Showtime, Season 7 Episode 8: The Owl
damianista did not do a recap of this episode.
Entertainment Weekly: Billions recap: Into the woods
It's only when Michael Prince (Corey Stoll) decides he needs to attend the retreat that Chuck thinks twice about going.
incorrect! chuck goes because he knows dunlop and fourth will be there and wants to encourage him to endorse her rather than prince, but he has no idea prince will be attending until he arrives and sees prince there.
Complicating all of this, Andy (Piper Perabo) needs a favor. A friend of hers has disappeared while mountain climbing, and they can't use a beacon to coordinate a rescue because the man took an alternate route and crossed into China. Doing so would alert the Chinese government and he'd be held hostage. So Andy asks for Prince to coordinate a private, secret rescue using his connections. Prince does so despite the fact that if they get caught, his campaign is over, and despite his complicated feelings about the man being rescued, who's one of Andy's romantic connections in their open marriage.
“one of andy’s romantic connections” is the most explicit anyone’s gotten so far! congratulations!
All of this represents a shift in Prince's persona. He's becoming harsher, more cynical, and completely focused on his need for power. He's finally turning into the man everyone's been worried about.
he’s BEEN that man, kyle. that’s the point.
Fan Fun with Damian Lewis (Gingersnap): The Unbeatable, Unstoppable, Unparalleled MVPs from Billions Season 7 Episode 8, “The Owl”
Gingersnap
Supreme Sleazeball Swerdlow Sayings in a Scene…AGAIN – He’s back! Slimeball doc is back, this time wearing a prison-orange, head-to-toe, Karl Kani tracksuit to The Owl’s winter conclave.
[…] And it doesn’t stop there – the Doc simulates ghastly hip thrusts when groaning the word “uh!” as he names off kinky sexual acts like postillionage and croissant (too many urban dictionary definitions to count),
maybe you would have found the right urban dictionary definition if you’d looked up cuissade, which is what he actually said and was spelled clearly in the captions. (and neither of those things are particularly kinky unless you’re incredibly straight.)
Benedict Arnold Citation– Griffin Dunne, who played George Pike, IV aka “Fourth” in this episode. Dunne also played Dr. Alcon Parfit in Succession. Only traitors act in both Billions and Succession and I find it deplorable when one is defecting across enemy lines, but he wasn’t the first defector.
🙄🙄🙄
Damianista
[…]
Greatest Entrance – Governor Nancy Dunlop
The badass Montana governor shows up at The Owl with these words to the old, rich, white men that I am talking about above.
“Hey boys! Are you cold? Some of you seem cold. I saw a few of you answering the call in the trees back there. They were definitely cold.”
yes, of course. what could be greater and more badass than walking up to a group of people and going “haha small penis.”
Beginning of a Beautiful Friendship – Wendy and Andy
While their relationship did not start off on the right foot, it seems Wendy and Andy bond over Andy’s grief when it is not the Tiger Team but the Chinese officials who are able to reach Derek first! I think Andy deep down knows why the best rescue team in the world has not been able to do it and I suspect she may join the opposition against Prince presidency in the weeks to come!
what do you mean “deep down.” she knows why the team couldn’t get derek out and she said it out loud to prince’s face.
Lady Trader
[…]
The “Don’t Put All Your Eggs in One Basket” Award: Did Mike Prince really just pull all of his money, both personal and the funds, out of every international investment? What a very foolish and short-sighted thing to so. The losses his would take would be tremendous, not to mention how he would move the markets on certain investments, and would never be able to get “market prices.” What a moron.
[midsommar imdb parents guide “a man is constantly seen vaping” tumblr post voice] oh if that’s all
The “Vision I Never Want to See” Award: The thought of those old, wrinkly men playing naked Twister just brought up my breakfast! Gross!
disrespectful to old men who fuck each other. apologize now.
Fan Fun with Damian Lewis (Lady Trader): From the Trader’s Desk
lady trader also did not do a recap of this episode.
2 notes
·
View notes
Text
Fit naked women naked nude

Amateur Naked Yoga - FitNakedG.
Naked Fitness Women Porn Videos | P.
'naked fitness' Search - XVIDEOS.COM.
Angela Yeo onlyfans - Nude Muscular Women and hot fit girls.
Naked Fitness Girls Archives - FitNudeG.
Fit Naked Girls.
Very Fit Nude Women Porn Videos | P.
Sexy Naked Women * Beautiful Erotic Nudes * Beauty of Nude Woman.
'sex with super fit women' Search - XVIDEOS.COM.
Pictures of Hot Naked Women.
'naked fit girl' Search - XVIDEOS.COM.
Nude Fit Girls Archives - FitNakedG.
Free Fit Girls Naked Porn Videos | xHamster.
Amateur Naked Yoga - FitNakedG.
This beautiful muscular woman poses completely naked! We love to watch her striated muscles. She's nude and shredded as fuck !! onlyfans Angela yeo Private Porn. Nude athletic girls in action who have tight red eyes ready.... Fit babes do it better, athletic porn clips - Showing 1-24 Of 2135 For 'Athletic' Duration New Popular. 07:27.... Porn For Women - Sexy Couple Sex and Athletic Real Fucking Multi Positions. 05:07. 66%. Fitness Porn - Gym Sex. The Biggest Fitness Porn Collection Around! Sit back and enjoy thousands of photos and videos of nude fit girls and sexy gym bunnies masturbating , having gym sex , doing sports naked , working out nude , taking.
Naked Fitness Women Porn Videos | P.
Jul 6, 2021. Paulina Porizkova, 56, just posted a nude photo of herself looking super fit on Instagram. The supermodel explained that she decided to post the pic after a leisurely bath in her.
'naked fitness' Search - XVIDEOS.COM.
Nude Fitness Girls - Muscle Girls Flexing Naked - Instagram Models Nude.
Angela Yeo onlyfans - Nude Muscular Women and hot fit girls.
13,526 nude fitness women FREE videos found on XVIDEOS for this search. XVIDEOS.COM.... Muscle girl naked 12 min. 12 min Barelylegalteen - 3M Views - 1080p. Hot Milf nude workout 7 min. 7 min Michellemuscle - 3k Views -... 60yo fit body builder milf anal sex will pump you up 13 min. 13 min Niocoledirtygrl - 317.4k Views.
Naked Fitness Girls Archives - FitNudeG.
Watch Extremely Fit Naked Women porn videos for free, here on P Discover the growing collection of high quality Most Relevant XXX movies and clips. No other sex tube is more popular and features more Extremely Fit Naked Women scenes than Pornhub!... Nude squats over your face. michellexm. 55.6K views. 84%. 6 months ago. 1:35 HD.
Fit Naked Girls.
Horny Redhead Posing On Rocks. Hot Shower With Lusty Babe. Foxy lass poses in the nude. Foxy lassie poses in the nude. Pale Babe With Huge Tits. Pale Brunette In The Bathroom. Now, as we have already said, we have tried to deliver the best of the best when it comes to beautiful women while keeping in mind that people love variety. Naked Fitness Women Porn Videos. Fit milf in the gym showing the whole neighborhood her naked workout. Nude Workout with Butt Plug - No Cum Challenge! Lesbian tribbing and pussy eating. Two naked beautiful girls on a couch.
Very Fit Nude Women Porn Videos | P.
Hot Naked Babes; Erotic Touch. Erotic and XXX Sites Reviews Click on Logo to Read. We present our reviews of the leading erotic nude and porn sites. Check freexcafe's point of view about the top erotic sites with the most beautiful and sexy nude women captured by the world class erotic nude artists. Nude Women by Hegre; Ron Harris Studio; Naked. 36,859 naked fit girls FREE videos found on XVIDEOS for this search. XVIDEOS.COM.... Alla Birtakik undresses nude in the swimming pool 5 min. 5 min Silicone Girls - 60.6k Views -... Sexy trainer and two hot girls doing yoga while naked 6 min. 6 min Sexyslutt8 - 1.1M Views - 720p.
Sexy Naked Women * Beautiful Erotic Nudes * Beauty of Nude Woman.
Fitness Girls Pics. Contact. Fit Nude Girls NUDE INFLUENCERS Best Porn Sites Live Adult Cams Female Bodybuilders Home Naked Workout Sort By Date Views Rates Comments Home Naked Workout 3 weeks ago 46 0% Gorgeous Girl Sexy Legs, Bubble Butt Workout Without Pants 3 weeks ago 47 0% NAKED SQUATS 3 weeks ago 50 0% SEXY SWEATY CARDIO BOTTOMLESS 3 weeks ago 51 0%. S is updated by our users community with new Fit Mature Pics every day! We have the largest library of xxx Pics on the web. Build your Fit Mature porno collection all for FREE! S is made for adult by Fit Mature porn lover like you. View Fit Mature Pics and every kind of Fit Mature sex you could want - and it will always be free!.
'sex with super fit women' Search - XVIDEOS.COM.
Beautiful sexy naked women come in all shapes, sizes, races, and colors. Whatever your preference, we have it on this site. Nude Women. Breasts so large and supple, you want to lay and suckle them for hours. Small tits that easily fit into your hands. Perky nipples that are stiff and rosy, waiting on you to pinch and suck them.
Pictures of Hot Naked Women.
Naked female bodybuilders, nude Sporty Girl, nude NPC Bodybuilders, IFBB Pro Figure, NPC Fitness, Personal TRainer, Competition Pictures, webcam Shows, hundreds of video clips and lot of pictures gallery of female muscle and muscular girls. Mpeg Unlimited. Hardcore video the sexy muscular fitness women nude. The Female Physique.
'naked fit girl' Search - XVIDEOS.COM.
S is made for adult by Fit Nude Women porn lover like you. View Fit Nude Women Pics and every kind of Fit Nude Women sex you could want - and it will always be free! We can assure you that nobody has more variety of porn content than we do. We have every kind of Pics that it is possible to find on the internet right here. Watch Sexy Fit Naked Women porn videos for free, here on P Discover the growing collection of high quality Most Relevant XXX movies and clips. No other sex tube is more popular and features more Sexy Fit Naked Women scenes than Pornhub!... Public Exhiibitions amateur bebe - hot sexy lady at Nude Beach - she is wearing only a hat. The Biggest Nude Fit Girls Photo Collection Around! Watch naked fitness girls. The hottest nude gym girls photos.
Nude Fit Girls Archives - FitNakedG.
Instagram models nude; Naked Fitness Girls; Nude Fitness Girls; Nude Fitness Videos; Nude Flexible Girls; Nude Fit Instagram girls; Nude Muscle Girls; Nude Workout; Nude Fitness Girls;... Naked Fitness Girls. Subterms. Latest stories. Jamie Madison nude. Popular. Ekaterina Volkova aka Mila Azul nude. Imogen Lucy Holland nude. Mariana Pinter nude. Fitness porn, Gym sex, Nude yoga, NSFW fitness, Instagram fit girls, Nude fitness models, Fit naked girls 846k Members 693 Online Created May 29, 2017 nsfw Adult content LINKS Naked Workout Nude Yoga Nude fitness models Gym Sex Nude Fitness Galleries Nude Fit Models Our Friends r/SmallCutie 476,923 members nsfw Join r/PetiteTits 229,701 members. The best Gym porn and Massage porn videos. Gym sex - Naked workout.
Free Fit Girls Naked Porn Videos | xHamster.
Fit Girls Naked Porn Videos. More Girls Chat with x Hamster Live girls now! HOT! Licking stepsister’s pussy, close-up and ANALINGUS! 4k. PUSSY LICKING, CLOSE UP, LICKING, EATING. 4k 60fps. Top girls. Compilation. Fit girl try-on haul, slim fit jeans, trousers. Tried on a new swimsuit. |. Fit Naked Girls porn from all corners of the internet and all social media platforms.... Are fit and petite girls your type? FitNakedGirls. 82. Happy Tuesday. FitNakedGirls. 26. I don't have some hardcore abs, but they're still firm to the touch. FitNakedGirls. 25. Let a.
Other links:
Blacks Teen Sex Hard Core
Busty Teen Family Naked
Naked Teen Black Girls Pussy
Chubby Teens Posing Naked And Topless

28 notes
·
View notes
Photo

John Singer Sargent
Nonchaloir (Repose) (1911)
Oil on canvas, 63.8 x 76.2 cm
National Gallery of Art, Washington
Highlights from around the web 💫
✨ John Singer Sargent was an American expatriate artist, considered the "leading portrait painter of his generation" for his evocations of Edwardian-era luxury. He created roughly 900 oil paintings and more than 2,000 watercolors, as well as countless sketches and charcoal drawings. His oeuvre documents worldwide travel, from Venice to the Tyrol, Corfu, the Middle East, Montana, Maine, and Florida. [1]
✨ Although based in Paris, Sargent's parents moved regularly with the seasons to the sea and the mountain resorts in France, Germany, Italy, and Switzerland. His mother was convinced that traveling around Europe, and visiting museums and churches, would give young Sargent a satisfactory education. Early on, she gave him sketchbooks and encouraged drawing excursions. Although his education was far from complete, Sargent grew up to be a highly literate and cosmopolitan young man, accomplished in art, music, and literature. He was also fluent in English, French, Italian, and German. [2]
✨ Sargent was a lifelong bachelor with a wide circle of friends including both men and women such as Oscar Wilde (whom he was neighbors with for several years), lesbian author Violet Paget, and his likely lover Albert de Belleroche, whom he met in 1882 and traveled with frequently. A surviving drawing speculatively may hint that Sargent might have used Belleroche as a model for Madame X, his most infamous work. Recent scholarship has speculated that Sargent was a homosexual man, based on statements by his friends and associations, the way his works challenge 19th-century notions of gender difference, and some nude male portraits, including that of Belleroche, which hung in his Chelsea dining room. One client wrote that when in Venice, Sargent "was only interested in the Venetian gondoliers" while another said that his sex life "was notorious in Paris, and in Venice, positively scandalous." [3]
✨ After securing a commission, Sargent would visit the client's home to see where the painting was to hang. He would often review a client's wardrobe to pick suitable attire. He usually required eight to ten sittings from his clients, although he would try to capture the face in one sitting. He usually kept up pleasant conversation and sometimes he would take a break and play the piano for his sitter. Finally, he would select an appropriate frame. In 1907, at the age of fifty-one, Sargent officially closed his studio. Relieved, he stated, "Painting a portrait would be quite amusing if one were not forced to talk while working…What a nuisance having to entertain the sitter and to look happy when one feels wretched." [4]
✨ Despite his success as one of the most sought–after portraitists of the late Victorian era, Sargent eventually became exasperated by the whim and vanities of prominent sitters. By 1909 he had abandoned conventional portraiture in order to "experiment with more imaginary fields." The woman in Repose is Sargent's niece, Rose-Marie Ormond. In keeping with his newfound preference for informal figure studies, Sargent did not create a traditional portrait; rather, he depicted Rose–Marie as a languid, anonymous figure absorbed in poetic reverie. The reclining woman, casually posed in an atmosphere of elegiac calm and consummate luxury, seems the epitome of nonchalance—the painting's original title. Sargent seems to have been documenting the end of an era, for the lingering aura of fin–de–siècle gentility and elegant indulgence conveyed in Repose would soon be shattered by massive political and social upheaval in the early 20th century. [5]
Thanks for reading this far. I hope you found this glimpse into Sargent’s life and artistic practice as interesting as I did! If you’re feeling inspired feel free to shop the merch links below. Pro tip: the t-shirt in XL makes a great night gown if you want to channel your inner Rose-Marie! 😴
↪ Get this design on a t-shirt, sweatshirt, or notebook 🥀
#john singer sargent#nonchaloir (repose)#american art#oil painting#art history#dark academia#dark academia aesthetic#light academia#light academia aesthetic#academia aesthetic#archive aesthetic#back to school#art major#curators on tumblr#sleep#portrait#impressionism#lgbt representation#oscar wilde#history facts
14 notes
·
View notes
Photo
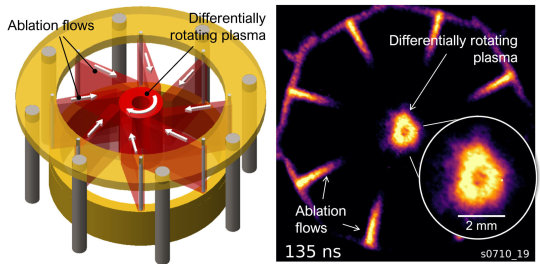
Accretion disk around black holes recreated in the lab Imperial College researchers have created a spinning disk of plasma in a lab, mimicking disks found around black holes and forming stars. The experiment more accurately models what happens in these plasma disks, which could help researchers discover how black holes grow and how collapsing matter forms stars. As matter approaches black holes it heats up, becoming plasma—a fourth state of matter consisting of charged ions and free electrons. It also begins to rotate, in a structure called an accretion disk. The rotation causes a centrifugal force pushing the plasma outwards, which is balanced by the gravity of the black hole pulling it in. These glowing rings of orbiting plasma pose a problem—how does a black hole grow if the material is stuck in orbit rather than falling into the hole? The leading theory is that instabilities in magnetic fields in the plasma cause friction, causing it to lose energy and fall into the black hole. The primary way of testing this has been using liquid metals that can be spun, and seeing what happens when magnetic fields are applied. However, as the metals must be contained within pipes, they are not a true representation of free-flowing plasma. Now, researchers at Imperial have used their Mega Ampere Generator for Plasma Implosion Experiments machine (MAGPIE) to spin plasma in a more accurate representation of accretion disks. Details of the experiment are published May 12 in the journal Physical Review Letters. Accelerating plasma First author Dr. Vicente Valenzuela-Villaseca completed the study during his Ph.D. in the Department of Physics at Imperial. He said, "Understanding how accretion disks behave will not only help us reveal how black holes grow, but also how gas clouds collapse to form stars, and even how we might be able to better create our own stars by understanding the stability of plasmas in fusion experiments." The team used the MAGPIE machine to accelerate eight plasma jets and collide them, forming a spinning column. They discovered that the closer to the inside of the spinning ring was moving faster, which is an important characteristic of accretion disks in the universe. MAGPIE produces short pulses of plasma, meaning only around one rotation of the disk was possible. However, this proof-of-concept experiment shows how the number of rotations could be increased with longer pulses, allowing better characterization of the disk's properties. A longer experiment run time would also allow magnetic fields to be applied, to test their influence on the friction of the system. Dr. Valenzuela-Villaseca said, "We are just as the start of being able to look at these accretion disks in whole new ways, which include our experiments and snapshots of black holes with the Event Horizon Telescope. These will allow us to test our theories and see if they match astronomical observations."
2 notes
·
View notes
Photo
MODELING GIG 001 ( MODEL BRANDS )
SCHEDULE TYPE: ONE TIME GIG
the brand owners of ELYSIUM, TIMEBOX, SOLA, AURORA, ARIA, and BABYLON have decided on the models for their upcoming campaigns. listed below are the chosen models along with the corresponding brand(s) they will be a part of for this campaign:
ELYSIUM x TIMEBOX COLLABORATION ( KIM JINSEO / @lgcjinseo & LIM SANGHYUN / @lgcsanghyun )
JO SUNWHA ( @lgcsunhwa ) - YUHWA
KIM ALEX ( @lgcalex ) - HAEMOSU
SEONG BYUNGHO ( @lgcbyungho ) - HABAEK
SOLA ( OKADA TAIYOU / @lgctaiyou )
BAE NATHAN ( @lgcnathan )
KIM YUJIN ( @yujinlgc )
LEE MINJI ( @lgcxminji )
SONG KODA ( @lgckoda )
AURORA ( HAN JISOO / @lgcjisoo )
AHN YEIN ( @lgcyein ) - MAIN CHARACTER
SHIN JIEUN ( @lgcjieun ) - THE ( NEW ) FRIEND
YAMASHITA ICHIKA ( @lgcichika ) - THE FRIEND FROM THE 1920s
ARIA ( SONG AHYEON / @lgcahyeon )
AHN JAEHWA ( @lgcjaehwa ) - LAST WALTZ
AYUTTHAYA MAYA ( @lgcmaya ) – ADRENALINE
KIM NAYOUNG ( @lgcnayoung ) – FANTASIA
BABYLON ( KIM JINYOUNG / @lgcjinyoung )
HAN NOEUL ( @lgcxnoeul ) – MALE STUDENT
LEE YEJIN ( @lgcyejin ) – BUSINESSWOMAN
PARK CHAEKYUNG ( @lgcchaekyung ) – FEMALE STUDENT
ZHENG AMELIA ( @lgcamelia ) - LIBRARIAN
for this specific opportunity, the people who were eligible to participate were based on who completed the MODELING PORTFOLIO. afterwards, they were narrowed down according to the information that was given by the admins and then whoever matched the information and requirements with the brand was then decided by the brand owner(s) themselves.
rather than putting all of the pertinent information about each of the brands’ campaigns and products in this post, you can see all of it over HERE.
each of the models were contacted by either one of the staff members from the brands’ creative team or their manager about the gig.
the brands will be working on the cf and photoshoot from NOVEMBER to DECEMBER. since everyone has different schedules, this will be done whenever the groups have any free time in between. sometime around early JANUARY, the models from each of the brands will be doing a review video where they get to talk about their thoughts about the products and the cf ( this means that if you’re a model for sola, you would review sola’s products and so on. in the case of elysium and timebox, since it is a collaboration, you will be reviewing both of the products and cfs ). these review videos ( which typically last around 10-15 mins ) will be posted on lgc’s youtube channel around january or february to excite the fans.
as for the BRAND owners, legacy is planning on tweaking their subsidiary website to include all of the new brands and their upcoming products. with this being in the works, one of the tasks that the company has for the models is to take profile photos that will be used for their web pages. for this photoshoot, the model will be requested to have headshot photos along with pictures of them posing with their products.
( important note: the products will be launched around q1 2023 and the campaign will last until q2 2023, but on the modeling contracts tab they will be listed from q4 2022-q2 2023. specific dates as to when the product launches will be revealed after the deadline has passed. )
REQUIREMENTS
this will be split between the brand owners and the brand models for easier reference. for the elysium x timebox group, the brand models only need to do the requirements once!
BRAND OWNERS
PREPARATIONS: write a 300+ solo or a 4 replies (minimum 8 lines) thread with anyone in your group about the cf filming, photoshoot (or another model for the profile pics photoshoot) for +5 MODELING and +8 NOTORIETY ! ** can do it up to two times as long as it’s with different partners for the thread. if you plan on doing a solo, you can only do one solo **
BRAND MODELS
PREPARATIONS: write a 300+ solo or a 4 replies (minimum 8 lines) thread with anyone in your group about the cf filming or photoshoot for +5 MODELING and +8 NOTORIETY !
REVIEW VIDEOS: write a 300+ solo about your muse’s thoughts and reactions to their respective brand’s cf and products for +5 POINTS TO ACTING, PERFORMANCE, OR MODELING and +6 NOTORIETY !
BONUS: for being chosen as the model of the brand, you will get an additional +5 MODELING !
POINTS FORM
you have until JANUARY 7, 2023 11:59PM EST to finish the writing requirements. please tag all solos and posts pertaining to this with lgc:mbq422. when you’ve finished the writing requirements, send the form below to the lgcpoints blog:
MUSE NAME ∙ MODEL BRANDS (Q4 2022)
- PREPARATIONS: +5 MODELING, +8 NOTORIETY [ LINK ] ** can be done twice for the brand owners **
- REVIEW VIDEOS: +5 ( ACTING, PERFORMANCE, OR MODELING ), +6 NOTORIETY [ LINK ] ** only for the brand models **
- BONUS: +5 MODELING ** only for the brand models **
12 notes
·
View notes
Text
Under A Rest: Part V
mcstories | literotica
Another Month Later
On a dull, dreary Monday morning perfectly identical to the thousands of other dull, dreary Monday mornings preceding it, Detective Berman sat at his desk, typing up a storm on the antiquated computer his department insisted they had no money to upgrade.
Having finished a particular section, he leaned back against his office chair and took the time to read it back. It was boring, rote work for him at this point--some report for a straightforward case that'd popped up a few days prior--but he prided himself on his thoroughness. After several corrections and that final, satisfactory evaluation, the detective eagerly turned his attention to his desk’s newest addition: a small, elegant onyx block that spun effortlessly posed atop a single vertex. It was a model sculpture of the famed Astor Place Cube in New York, a sculpture of which he was fond and, incidentally, a recent gift from his madam.
In his fifteen years of tenure, the detective had tried to make his office into something more than its vomitous asbestos floor tile, exposed ductwork, and beige cinder block wall. Filing cabinets and shelves of books and binders lined the free space of his office, with papers and folders that sorely needed organizing lying about. A large city map and whiteboard hung behind him.
Despite its mustiness and clutter, Detective Berman liked to think he’d succeeded in enriching his space. There laid a dark rug on the floor, well-worn but sturdy. He disliked the overhead fluorescents and thus opted for a banker’s lamp on his desk and a standing lamp in the corner. He’d given wooden Venetian blinds to his singular, sterile portal to the outside world, which on that morning were pulled open to welcome in the day’s cold, cloudy light. Various tchotchkes laid about on his desk and shelves. Several works of art hung on his walls, done by friends of his.
And now, that little cube stood front and center on his desk, small but proud. He leaned forward and gave it a flick, watching it whirl idly as he again leaned back and settled into his chair, arms crossed, a tiny grin making its way to his lips.
His weekend had been utter bliss. They’d finally, to his heart’s delight, begun venturing outside her house at more normal hours, enjoying the quiet dinners and outdoor excursions of a normal couple. As much as he enjoyed her trances--from deep, collared blackouts to gentle but rapt attention--he found himself acutely in their throes less often as of late. In fact, the past Saturday afternoon had been so sunny and mild that the two spent it merely sitting together on a park bench, like any other normal-looking couple. Holding steaming Solo Jazz cups of corner store coffee, bird-watching, people-watching, spinning yarn after yarn of conversational tangents as they sat upon the massive web left in their wake, sky streaking pink, sun burning red, stars sparkling to life, evening breeze briskly displacing the heat of day. His fingers weaving gently through her tawny tresses, the dim, gold light of waning sun setting her sly green eyes aflame. The surprise black cube in her unfurling fingers, just a little something for him, that was all, it even rotates, and oh! he’d said, eyes wide, what a chip off the old block it was, and she'd rolled her eyes before laughing that laugh of hers, and what a laugh it was. The gentle knocking sound when--
Detective Berman opened his eyes.
One of his reports, Sergeant Joshua, knocked on the open door. The cube had slown, lazily ceasing its rotation with its last ounce of inertia. He let out a sigh.
"Come in, Sergeant," he called without looking up, taking an idle, obligatory sip of his tepid coffee. The young sergeant's unique knocking cadence always gave him away. A particularly tall, lanky young man of a certain awkwardness, he strode in and placed a thick folder on his desk.
"Morning, boss. Got a few revised reports for you to review."
"Cool, can't wait," he said dryly, eyeing them with mild contempt as they plopped onto his desk. The focal point of his career--bloated reports. Speaking of which, he ought to finish the one on his screen. He returned to typing. "Anything else for me? Anything that won't make me want to go the hell home by noon?"
"Well," the young detective started, a sparkle in his eye as he placed a dusty folder on the desk. "I believe we have a new lead on the Walter case."
"Yeah?" Detective Berman replied, ears perked but fingers still typing, eyes still screen-affixed. "That's something, alright. But don’t get excited or anything, we're holding off on it for now."
"He's, uh…actually waiting outside," he said, voice lowered, glancing outside the door behind him. Detective Berman stopped typing and followed his gaze, leaning to the side. "He says he was a higher-up at Chyron, a VP or something."
Chyron. A single, muted string plucked in his head.
"Uh…" the younger detective continued, leaning in, his smooth, thin face painted with concern. "He looks to be, like…on the verge of tears. I dunno. I really think you should see him."
"Well…I guess I have a few minutes," Detective Berman grumbled, checking his watch. "He's already here, might as well hear him out. Send him in."
"Will do," Sergeant Joshua said, stepping out to retrieve him.
A short, wiry man with abnormally straight posture walked in, gait radiating confidence. In his mid-fifties, his hair was jet black and slicked back, temples streaked generously with gray. His suit was a washed-out navy, very sharp and closely tailored, his feet shod in spotless brown oxfords. His body language emanated apprehension, while his face--angular, gaunt, with prominent cheekbones--betrayed turbulent emotion.
"Good morning, Detective. Marcus Chiang," he said tersely, his words slightly accented. He extended his hand.
"Morning, Mr. Chiang, sir. Nice to meet you. Have a seat," the detective said, leaning across his desk and returning the handshake. He turned his attention once again to his screen. "What can I do for you?"
"I’m going to save you some time and get to the point,” Marcus replied, taking a seat on the agéd chair opposite the detective.
“Fantastic. I like you already.”
“I am certain that in the course of your investigation you've encountered a Doctor Maria Angelos."
Detective Berman nodded, still staring at his report on the monitor. His eyes flicked anxiously to the clock on his system’s toolbar. Already, this felt like a waste of time.
Marcus continued.
"Well, you could say I'm one of her patients. Or was, rather. Her practice, might I say, is a bit…unorthodox."
"Tch. Tell me about it," the detective fired off, only half paying attention.
"What do you mean?"
He stopped and looked up, realizing what he’d just said.
"Just that we’ve already looked into her styles of treatment, so to speak."
The two met eyes for a spell.
"So you know," Marcus said, voice lowered.
"I don't know what you're talking about," Detective Berman replied evenly, the words leaving his mouth automatically.
"It seems to me like you do."
"It’s really not much to go off of. We consider it a dead end."
"But you do know about her…method, let’s say."
"Whatever was in Mr. uh…Walter’s medical file,” he said, now needing to glance at the folder for help recalling the victim's name. His memory wasn’t normally so dodgy, especially not regarding cases so recent. But for some reason, that one seemed like it’d swallowed into a void, a black sinkhole in his mind. No matter. “That’s all. It's on our radar, nothing more."
“I see.”
The detective’s stomach turned. He rested his chin on his hand in thought, elbow propped on the armrest of his chair. Marcus narrowed his eyes at him before leaning forward and dropping his voice to a whisper.
"My word is ‘dream’."
They met eyes again, a silence befalling the room.
What did this schmuck think he was trying to accomplish? So she'd gotten around. Mere playthings they were, that was all, from long before they’d met--however it was and however long ago it was that they met; the exact details were both unclear and unimportant. She'd released each and every one. That was what she'd told him, and it satisfied his curiosity. He felt privileged that she’d been so honest and divulged such information to him. Privileged that she’d even looked at him, wanted to see him so often, wanted to shower him with affection and ease his stresses with gentle caresses. He had no reason to doubt her.
"What's that, some kind of sleeper agent thing?" he said flippantly, giving the cube on his desk another casual whirl. Marcus glanced at it and raised his eyebrows.
"I think you know exactly what it was. It’s what’s known as a trigger word. I would hear her say it and…totally lose myself."
The detective leaned back in his chair, nodding with a smirk. He certainly knew the feeling.
"Yeah, well, that's a common effect. Of that sort of thing. So I’ve heard," he said, gesticulating vaguely. But, though he tried to resist, gaze tempted by that spinning cube, he was beginning to feel his mind salivate, melting a little just thinking about it, remembering it, as though he were hearing about a fantastic feast he knew all too well would be otherworldly and yet remained unavailable to him.
Marcus, for some reason, looked somewhat encouraged.
"I mean, it took me so long to even come forward, and that was after I heard Mr. Walter had died, by which of course I was very saddened. I’d worked with him, after all, it shouldn’t have taken his death to get me to say something. But he was the one who referred me to her, and I just can't help but think…well. I'm not quite sure what to think about the whole thing."
"Neither are we," Detective Berman mumbled. Granted, though he highly doubted his lovely madam could be implicated in something so unsavory, his working mind won out and his interest was piqued. Strangely, though, the more he heard and thought about this case, the harder it was to remain focused. He’d never felt anything quite like it, but it all just seemed so boring, so…trivial. They might as well have been discussing basic arithmetic.
“I’m not exactly sure, sir, what it is you’re implying,” he continued.
Marcus sighed as though he’d been expecting this. “Well, I’m not exactly sure myself, is the thing. There were some…unusual things going on at the company. Doctor Angelos had a few of them as patients, and they fell into some…similar patterns of behavior, I suppose you could say.
"At first I thought it nothing more than my own paranoia," he continued, "but then those same people began exhibiting the same behaviors, over and over, you see, and, well, I couldn't really explain it. I had people in HR telling me these people's supervisors noticed them spacing out at their desks at various times of day. It didn’t even affect their work, all of them were solid performers, but like clockwork--”
“Like clockwork, the people chained to their desks down at Chyron for eight hours a day would get bored and space out? That is pretty crazy, yeah,” Detective Berman interrupted flatly.
Marcus pursed his lips and tilted his head downward. “Not like that, Detective. I mean, the odds of these same guys spacing out in the exact same ways, every single day, without a drop in work performance…I was just wondering how on Earth they’d all managed it. Hell, it sounded good to me. And the weird part--it was even with the same exact facial expression each and every time. Same blushing cheeks, same distant little smile. And the common denominator in all of them was th--”
“Doctor Angelos.”
“…Right.”
“Well,” the detective replied, idly scrolling through the document on his computer as he processed this information. He had to admit that this was news to him, though he took it with a grain of salt. “That’s quite a claim you’re making there, Mr. Chiang. You wouldn’t happen to have any sort of evidence supporting it, would you?”
Marcus paused for a moment before responding. “Well…no," he admitted reluctantly, regret in his voice. "I don't actually have any hard evidence to present to you, no."
The detective shifted uncomfortably in his seat. He took a deep breath and leaned forward, shoulders hunched, arms folded and resting on the table in front of him as he studied Marcus intently.
“I understand your concern," he said calmly, "But if I'm picking up what you're putting down, that’s a very serious allegation you’re making. The kind that needs to be mounted on more than just idle speculation."
“I understand that. But I even visited her myself, just to see what she was about, just to see what kind of person she was. See if there was anything really shady going on."
"And?"
"Well, I Googled her first, of course, got nothing but glowing reviews, case studies, papers in esteemed medical journals, even a few high-profile interviews. I was shocked to find that she wasn't just some lady with a social work cert from McDonald's University, she's somebody. Very well-respected in her field, in fact, as I’m sure you found.”
“Yes, I gathered that,” Detective Berman replied with a nod. He remembered the same mild surprise when he first looked her up months ago. Though what exactly prompted that, he couldn't quite recall.
“So I went in, and all seemed very normal. She kept our appointment to the minute, which is more than I can say for my actual doctors. Took me in, was very charming, talked up a storm but listened to every word I said. I was completely shocked at how well we got along. I mean, I walked in very suspicious of her and the next thing I knew she had me laughing and smiling and nodding, nodding, nodding along…and it was all very relaxing, you see, so relaxing that it would’ve taken me by surprise had it all not been so relaxing. And she was still talking, just kept talking nonstop, and I was still just sitting there, nodding and nodding, nodding along still, of course except now my head was staying nodded, and my arms were heavy, and my legs were heavy, and my whole body was dropping into my chair, tingling, and my eyes were closing, and the next thing I knew I--are you alright, Detective?”
"Hm?" he said, prying open his eyes with effort and clearing his throat. "Yeah. Monday, you know. Just a bit distracted, sorry."
"Oh. I see," Marcus said. He tilted his head and stared at him, paused for long enough that the detective grew a bit confused at the silence.
"She's got you, too, hasn't she?" he added nonchalantly.
This startled the detective awake, his eyes widening.
"I’m sorry?"
"No, I am. I know that look. Oh, do I ever know that lo--that's why you're even entertaining me, isn’t it? You would've been dialing Bellevue by now, otherwise."
Detective Berman swiveled silently in his chair and stared out the window, mindlessly drumming his fingers atop his desk.
"Please let me help you," Marcus continued. “You know exactly what she’s capable of. I know you do.”
"Sorry, sir. Still got no idea what you're talking about,” he insisted.
“She thought she'd wiped me clean, thought she could just cast me aside and pretend nothing ever happened,” Marcus urged, an intensity now disturbing the evenness in his voice. “But I got out.”
“Out of what?” Detective Berman scoffed.
“From under her thumb, Detective. We never really forget anything to begin with, do we?"
Her voice, suddenly springing forth from somewhere unknown, rang through the detective’s mind.
Sometimes we never really forget anything to begin with, Detective.
Her voice was also ringing through his ears now, in reality. Instantly, he froze, at complete, helpless attention at the mere sound of her voice, even in its cruddy fidelity as it came through the phone now held in Marcus' hand.
“Don’t be worried, Detective.”
“Why would I be?”
“It’s just a normal induction, one of her plain old therapeutic recordings. A progressive relaxation. It’s even available for free online if you search her name.”
“Not sure why you’re showing it to me, then. I thought she was putting people under her…evil spell,” he said, posing his hands and affecting a voice.
Marcus said nothing. He only smiled pleasantly.
10…feel my voice coursing through you, your body feeling heavier…9…feeling so good…so relaxed…
They stared hard into each other’s eyes.
8…feeling so calm, all the tension leaving your muscles…7…body feeling even heavier, aware of all the surfaces touching your skin…as you relax deeper…and they fade away…
Detective Berman sat still, blinking heavily. Static filled his mind.
6…more and more deeply relaxed, feeling so safe, so warm, your thoughts coming and going idly but quieting…as they, too, fade away…5…each inhale bringing you more relaxation, each exhale bringing you down deeper and deeper, more loose and heavy…
His breathing quickened, shallowed, then eased slowly, each breath moving him according to her words. His hands and feet tingled, the sensation climbing up his limbs and into his body, fizzling out into heavy relaxation. His vision dimmed, mind quieting as her words faded.
Suddenly, silence cued his eyes open. He closed his mouth and gulped, Marcus raising his eyebrows and tilting his head up as if to goad him into saying something. Detective Berman cleared his throat again and shuffled a few papers on his desk, not meeting his eyes. An even longer silence passed between them.
“It was a single session.”
“I know.”
His head hurt. His heart hurt. She was fantastic, his life awakened by someone who sparked butterflies in his gut every time he so much as thought of her. It couldn't be. It was nothing. She hadn’t done anything. She couldn’t have done anything.
“I know,” Marcus said again, nodding as though reading his mind.
“I know what happened,” the detective muttered, a sudden edge to his voice rising. He seldom lost his cool, but this man’s attitude was beginning to grate.
“I know you think that, Detective,” he repeated.
Detective Berman's eyes narrowed, brow furrowed into a frustrated knot. Marcus fiddled around on his phone and hit play again.
8, feeling so good, feeling your consciousness rising…remembering everything, remembering…remembering everything…9, your mind waking, coming to life, remembering…
Remembering.
10. Remembering everything. Fully awake and refreshed.
He did as he was told. He always did.
This time, it hurt.
She'd done a number on him. But the block in his mind was perceptible now, no longer invisible. It was still there, very difficult to move, taunting him with its presence, but he could at least sense it again. Thinking about that case was so much work, like being stuck on a question while taking a difficult test, and of course, one usually finds it so much easier to skip it, and perhaps come back to it later…or at the end…
Or never. Sometimes one has no other choice but to submit.
He could hardly even remember the first visit he paid to her office, and until that moment had well and truly undone the mental associations he'd made between that visit, the subsequent visits, the investigation, and herself. In fact, his entire timeline of the case had been utterly undone. He wasn't sure what was what, except for a few small impressions that had begun trickling back.
Alas, with each painful drip of memory came heartache and massive, unfair amounts of effort. The first memory that came to him was a mere sensation--the strange, dreamlike feeling of calm that had descended upon him sitting in her office. His chair’s almost unnecessary levels of comfort. Her words, nimble and potent, lulling him. Her expressions of guarded courtesy, then curiosity, then delight.
As he focused on that visit, his memories began to coalesce around it. Something in that voice of hers had melted away his defenses. He remembered his notepad, the sharp, pointed observations jotted down, the last lines of which grew looser and shorter as she began working on him even before hypnotizing him proper. He'd forgotten almost everything on that page of notes, and it felt so good to close his eyes and forget about those sordid details that he'd made a real habit of it…
"Please, try to stay with me, Detective," Marcus continued, shutting off the recording. The detective snapped to attention, somewhat embarrassed. He hadn't even realized he’d drifted again, nor that the recording had still been playing. "Don’t feel badly. I can tell she worked tirelessly on you. She is a consummate professional, you must keep that in mind. Even her office is designed to ensnare, every bit of it. Maybe you remember. Down to that air freshener, which probably has God-knows-what in it."
"Ugh,” Detective Berman groaned, rubbing his eyes and recalling in newfound clarity that eerily calming pine scent. “God, I don’t know. I know I sat down in that chair…she got to talking about her little meditation technique or whatever, and…"
"Lights out."
"An understatement,” he said, more details slowly seeping back. “I knew it, I really did, I think. But for some reason I think I just decided nothing real could come of it. So I went into it normally…and next thing I know, like you said, she’s shaking me awake, and I was…I don’t think quite the same. Everything went a little funny after that."
“That's how she gets you."
“Oh, I wouldn't say she got me. It doesn’t prove anything other than she managed to hypnotize me exactly once,” he lied.
“Then why is the case shelved?”
“Happens all the time, unfortunately. It was a pretty clean scene, very little evidence of interest. Victim had no other female contacts we know of, no clear homosexual inclinations that I can remember. No family.”
“That may be so, Detective. But I'll ask you something.”
Mildly irritated, he shrugged.
“Shoot.”
“How long have you been a homicide detective?”
“Fifteen years, now.”
“Then tell me something. Why do people kill?”
He blinked and looked at the wall. He shrugged again and pursed his lips.
“What are the seven deadly sins?"
Marcus blinked, hesitating.
“That wasn’t rhetorical, I’m asking. I’m sure you know them,” the detective coaxed.
“Uh…greed, envy…pride…lust…wrath…which am I forgetting?”
“Gluttony and sloth. Though those tend to not be as motivational as the others. Unless you're trying to eat someone or, I don't know, shoot them 'cause they won't move from in front of the TV.”
“Right.”
“But yeah, there are your reasons. Any reason for murder can be boiled down to one of those. Money, sex, prestige, vengeance, you name it. What was your point again?”
“Fair enough. My point, Detective, is that I believe one or more of those applied in this case. I may not know what her motive was, but I am convinced she had one, something lusty in particular, or maybe greedy. I am here, on that man's behalf, in front of you now, asking you to give that woman just one more fair look. The only woman I ever saw James Walter get involved with was her. And knowing her, I just know there’s something more to it. Please.”
The detective sighed.
“Look…I still think you're barking up the wrong tree, sir,” he said, shaking his head. “But how about this. I’ll look into it one more time, take some notes on it, alright? No guarantee of anything.”
“Oh, I would greatly appreciate it,” Marcus said, a glint in his shining black eyes.
"You're welcome."
He paused.
“…Then she gave you a recording, didn't she?"
Detective Berman hummed in thought.
“Well…actually, I think I might’ve…huh,” he said, chuckling. “God, I gave myself one, how about that. I sometimes record investigatory interviews, that's standard op, and it was some attempt at insurance, I guess, should she try something fishy. Tsk. Look how well that turned out.”
Marcus snickered. The detective continued, working to recollect the crumbs of memory left in his mind.
“Then, I think…God, I can hardly remember now. I don't even know what I don't remember. But I think she suggested that I listen to it as much as I could. Which, I mean, I did, of course, and gladly, too, since I thought I’d be able to listen back on that little activity objectively and tease apart her MO. In reality, just listening to a recording of her had me nodding along, as you say. And, uh. Just saw.”
“Indeed. Do you still have that recording?”
Detective Berman paused thoughtfully, then opened his phone to check.
“Nope. All gone."
“Was afraid of that,” Marcus murmured.
“You know, the funny thing is…everything, all those words of hers…are in here,” he said, leaning forward and tapping an index finger to his temple. “I know it. But I couldn’t tell you a single one now. Not if you put a gun to my head.”
Marcus shook his head gravely, mouth set in a deep, sympathetic frown.
“She really did a number on you. Surely this constitutes something illegal, doesn’t it? Exerting such a profound influence on a law enforcement officer. Obstructing justice. You look like you’ve been put in the microwave just thinking about it.”
“Unfortunately…” the detective said, splaying his hand over his lips in thought. His own behavior in this mess could cost him his job. These were uncharted waters. He wasn’t sure if he could even trust his own memory, nor this man in front of him.
But now, neither was he certain he could trust his newfound companion, scintillating as she was.
Detective Berman took a deep breath, attempting to steel himself against the chaos now coursing through his veins. More than anything else right now, he was sure of her innocence, but could in no way think himself around the hardcoded confines of his mind’s methodical nature. To give into his emotions in his work was nothing short of treason. As strongly as he felt that she had nothing to do with such a ridiculous case, his instincts forced him to at least look into it one more time.
Nevertheless, his affections for her were so undeniable that he was still left conflicted about the prospect of arresting her. Their numerous trysts, their late-night conversations lying side-by-side in her bed, talking about everything from life’s big questions about love to whether the Showa Japan category that night on Jeopardy! had been too easy. She had also been so eager to help him with his investigation at first, despite knowing full well that she could be incriminated by any findings she made.
He thought back to those moments with a sad fondness, for if she did indeed commit the crime in question, then perhaps all he’d been enjoying, falling for, chasing the entire time was naught but--
“…Unfortunately?” Marcus said, urging him to continue his cliffhanging opening.
An illusion.
“Look…even if we could take this to a district attorney, even if we could somehow convince a jury that hypnosis, in theory, let alone practicum, is powerful enough to move people like this, to move a senior detective away from a trail, let alone a person to suicide. Then convince them that her command is just that strong--still, all we have is a whole lot of circumstance. We need irrefutable hard evidence, and as it stands now, if I go up there and testify in front of her…I’m telling you, the only thing hard in that courtroom is gonna be me.”
Marcus let out a rare, brief chuckle.
“Well, is that not in itself your hard evidence, Detective?” he said, tongue in cheek. The detective snorted and shook his head.
“No, really, uh…I’ll see what I can do about it. I’m just now getting back up to speed, recalling some of this stuff. Feels like I’m at the scene for the first time,” he continued, leafing through the case file on his desk. He spied a photo of her already inside. His heart skipped a beat. "For all I know, I could just have a head injury. And there’s no guarantee I can remember what I need to. Even if I do, I can hardly think straight about it now.”
“That doesn’t surprise me. Unfortunately I know well what you mean. But just…do what you can. I’d appreciate every bit of it,” Marcus said, rising and glancing at his watch. “I’m afraid I have an appointment, so I’ve got to run. But I’m very glad we had this meeting. Here’s my card. Oh, and Detective…”
“Yeah?”
“I advise you stay away from her. At least for the time being.”
Without thinking, the detective pouted slightly. He didn't want to stay away from her. But the tiny, suspicious inkling inside of him assented.
“…Looks like that’s how it’s got to be, doesn’t it.”
Marcus nodded curtly.
“Keep in touch.”
He left. The detective rubbed his eyes and slumped in his chair. His eyes stung. His everything stung. The weight on his shoulders from which he’d enjoyed a vacation had made its return. He ran his hand through his hair. He wished it was hers.
“Hey, Sergeant,” Detective Berman called out, voice cracking slightly. He cleared his throat. “Joshua. In here, please.”
“Yes, sir?” he replied, poking his head into his office.
“Open up the Walter book. I want you to call, uh…God, what’s his name,” he said, leafing through the book. “Paul Kuklinski. His number’s in there somewhere I think, ask him what he can recall about the guests at his last birthday party. But don’t be too direct, we don't want to alarm him. And, uh, I want a warrant for the house.”
“It was cleaned months ago, sir. Think the bank is looking to make a sale.”
“Oh. Hm. Well, I want one anyway. The thing about ‘clean’ is it's never as clean as you’d think. Have we got any of his devices, computer, phone, anything like that?”
“Laptop, cell phone, and tablet in the locker.”
“Superb. I want a look.”
“Gotcha. Anything else?”
“See if you can scare up any other patients of a Doctor Maria Angelos.”
~~~
Early Friday Evening
The empty house was indeed still in appalling shape, even by Detective Berman's lackadaisical standards. Fading beams of sunlight streamed through dirty windows in which motes of dust shimmered visibly. Somewhat unsettling wind chimes rang from the back patio. Cobwebs lay strewn in corners. Clumps of hair and dust peppered the carpets. Cracks lined the drywall. A musty smell permeated the space. Unfathomable amounts of clutter still crowded the tables. Moths batted about.
When Sergeant Joshua said it’d been cleaned, Detective Berman figured he either hadn’t seen it at all or had frightful notions of cleanliness.
Detective Berman shook books. Looked under desks. Sifted through laundry piles, papers, mildewy stacks of Popular Mechanics. His brain felt hot. Surely, and perish the thought, should his madam have truly been responsible in some way…she must have at least had a sensible motive. The thought of her doing something so cruel so senselessly sickened him.
Really, the entire investigation had begun to sicken him. He should’ve been at her house by now, spending every moment, both waking and sleeping, with her. But though his legs ached to bolt out of this house and run to hers, he couldn't, and for some reason, she hadn’t even reached out. No calls, no texts on the only Friday evening in recent memory that he could recall not spending with her. He couldn’t help but feel stung, further spurring his zeal to investigate.
The detective rolled up his shirtsleeves, readjusted his gloves, and powered on the laptop with a sigh. He could’ve just accessed it at the station, but he’d brought it with him; something about accessing the device in the victim’s space always made things click for him more easily. He couldn’t really explain it. It was just one of those things.
The laptop--a crusty thing, making him thankful for his gloves--took what felt like ages to boot. He inserted a thumb drive, executing a program to index and analyze the entire filesystem. Sifting through the information, he saw scores of files and folders, probably confidential: Chyron blueprints, CAD files, 3D renders. Elsewhere, he found programs James had written, as well as various texts both fiction and nonfiction. Large amounts of personal research. Some books. Some photography. Some memes. Entirely too much hentai.
All mentions of Maria Angelos had been wholly scrubbed. Anything regarding her name, and to that extent, hypnosis, had been completely nuked. He bit his lip and then pressed them together, unable to believe that such a thing could be. Feeling oddly lost, he began aimlessly scrolling through the victim's internet search history. It was an unlikely venture, but there could be something there, some clue, some hint, something right underneath his nose, taunting him, taunting him like she did, like her terrible, jade gaze taunted and haunted--
sechuan
sechuan near me
Did you mean: szechuan?
Detective Berman’s eyes widened, his mind sparked into roaring, inspired pyre, zeroing in on the innocuous typo amongst James Walter's search queries. Immediately, his fingers flew along the keys.
Angelo. Angelis. Marie. Mmariw. Angelous. Anglos.
Anglos. One result found, a recycled text file. He recovered it, thankful that the data was only partially corrupted. There it was, in plain English, detailing the workings of her plans, her abuse of hypnosis violating and manipulating at least several known patients. Her methodical erosions of powerful minds to the ends of providing herself with benefits, cash, and several powerful positions. Names, ones even he recognized. A call to have her medical license revoked.
Detective Berman’s blood ran hot and cold. Hot, because that was always what he felt when finally finessing the edge of his blade into an impossibly-tied knot, cold because it confirmed his worst suspicions--the ones that had nagged at him, the ones that had been shoved into the deep, dark recesses of his mind time and again, fastidiously covered in increasing layers of warm, blank, silly little bubbles.
He leaned back in his chair and sighed, saving the relevant documentation and continuing his search, yielding no other leads. He continued searching different permutations of typos, stumbling upon a single audio file.
“Hpynotic induction,” Detective Berman murmured aloud, examining the misspelled file title. “18:47 long…28 megabytes…wav file.” Curious, he hit play.
Hello, I--
Startled, the man slammed the space bar, pausing the recording. He caught his breath and gulped, hearing his heart pounding in his ears.
"The hell'd you expect, dumbass," he breathed to himself.
He looked around. The sun was setting, the house growing dark. The wind chimes outside had stopped. All was eerily quiet and still. Hesitantly, against all better judgement, he plugged a pair of earphones into the laptop’s headphone jack and pressed play once again.
Hello. I’m Doctor Maria Angelos, a licensed psychiatrist and therapist. Today, I’ll be guiding you into what’s called a hypnotic state…
Since Marcus Chiang’s visit, Detective Berman had reluctantly attempted some self-hypnotic work of his own. Research, exploration, deprogramming files, all attempts to carefully comb through his mind and poke at her insidious influences. Visiting another hypnotist in his scenario was out of the question, but he liked to think he’d started doing a rather decent job himself all things considered. Her influence had at least felt less real, less powerful, less intimidating. His thoughts had begun to clear. His memories had begun to return.
But hearing her again made it all pale in comparison. Nothing worked on him like she did. His mind went silent at the mere sound of her voice, his response to her words nearly instantaneous and entirely involuntary. Shivers went down his spine contemplating the depths to which she controlled his mind. He hated it.
He hated that part of him didn't hate it.
He couldn’t help but feel an unshakeable stone in his stomach. She’d betrayed him, sure. But worse, he’d betrayed himself. Vignettes of his own body betraying him over and over bled back--in her office, on her doorstep, in her living room, in her bedroom. His cursor moved sluggishly towards the window’s X button.
And there it stayed, unclicking. Her voice poured interminably into his ears and for the life of him he could not bring his helplessly frozen index finger to move the slightest millimeter. Any second now she’d begin her induction and he’d be even worse off, so the time to close it was now. His brain sprung into action, sending electrical impulses to his finger.
They resulted in no more than helpless, imperceptible little twitches, none firm enough to depress the button fully.
You’re probably already familiar
with that dreamlike state
that beautiful haze between waking and sleeping.
That relaxing blur
focused while unfocused
attentive while inattentive.
You may find yourself awake and alert
thinking normal thoughts, at normal speeds
and that’s completely okay, of course.
but you may, too, find your mind drifting pleasantly
thinking of things a little more fanciful, a little more subdued
thoughts of pleasant abstraction
pleasant confusion
pleasant dissociation
letting your thoughts slow
letting your body slump
letting yourself sink
deeper
and deeper
down…slow…relaxed…
His eyelids fluttered closed, his breath growing shallow, limbs leaden, his aching heartbeat quickening, then slowing, longing for her. Like trained little soldiers, his thoughts fell in line, slowing to a gentle halt awaiting her instructions. Mechanically, he doffed his right glove.
Feeling so good
feeling so relaxed…
A strong, pleasurable notion of agreement washed over him. His hand dropped heavily into his lap, slowly making its way towards his fly and lazily undoing his pants.
Sinking deeper
feeling the pull
feeling your muscles releasing tension…
His clumsy, slumbering hand massaged his stiff cock, becoming harder and harder as his fingers brushed up and down, up and down, feeling nearly as though someone else was tending to his swollen head. Her voice filled his ears, and with a satisfying sigh once again sent him into the clouds.
Enjoying this wonderful state.
Enjoying restful relaxation.
Taken off guard at the unwitting usage of his trigger, he dropped deeper, harder, his body collapsing and sinking further into the chair with an uninhibited sigh as he continued stroking, caressing himself, feeling wonderful pulses of ecstatic pleasure course through him, allowing her voice to once again soothe his tired, aching mind.
Wonderfully blissful.
Wonderfully blank.
The tiny voice in his head begging him to stop only quieted as the waves of pleasure took hold, rendering him overwhelmed as sweat began to bead on his forehead and moans began to escape his mouth. He felt himself slipping further and further away, his body becoming lusciously limp as he surrendered, every stroke sending a flurry of delightful sensations throughout his body. His breathing grew heavy, loud, and labored.
Wonderfully hypnotized.
Wonderfully aroused…
Listening to my every word…
The more he listened, the more he obeyed, the more intense those waves of blissful pleasure rose within him. There was no laptop, there was no chair, there was no house, there was no case. Only her. Only her honeyed words mainlined straight into his veins.
He bit his lip as he finally rounded the corner. His head fell back onto the chair, and with a satisfied, guttural moan, he finally allowed stars to erupt before his eyes, releasing himself into her embrace.
As the acute ecstasy slowly began to fade away into peaceful quiet, Detective Berman realized he heard a dull thud sounding through his mind, though he thought nothing of it.
Feeling wonderful waves of pleasure wash over you.
It thudded several times more.
“Boss? You in there?”
Detective Berman froze. He swallowed hard. Panic slowly rose in his stomach as he listened more closely and indeed confirmed that the sounds were real. With every ounce of his might, he broke his trance, prying his heavy eyelids open only to see globs of his cum on the desk. He hastily wiped the mess with crumpled, used tissues from his pocket, shoving his softening cock back into his pants and flinging off his earbuds.
“Y-yeah,” he called back weakly, mouth feeling full of cotton. He cleared his throat. “Come in.”
Sergeant Joshua opened the door and turned on the living room light, causing Detective Berman to squint.
“Hey, just thought I’d drop by and see how things were going. I texted you that I was coming, but you didn’t respond.”
Ripped out of the depths of his trance, the poor detective said nothing, just closed his eyes and focused on lowering his rapid heartbeat, sitting there lumplike. He was too muzzy-minded to be mad.
“That’s alright, I got caught up lookin’ at uh…at, uh…this here laptop…here. Found some stuff. Gotta read through it, make sure it’s all…here.”
The thought occurred to him to show the young detective the letter. Obviously, it was evidence. Obviously, in any other case, he would’ve shown him without hesitation. But that would just be so embarrassing. He’d explain it all later. When he was good. When he was ready.
“What’d you find?” Sergeant Joshua asked, peering curiously. Odd. Aside from the laptop, his boss was looking particularly tired and out of sorts. Probably just working overtime again. If he knew what was good for him, he’d stop pushing himself so hard.
“I’ll show you when I’m more sure of it. Alright?”
“Um…if you say so. And, uh, boss?”
“Yah?”
“Your fly’s open.”
He glanced down. The blue tartan of his boxers was indeed peeking through the zip of his gray slacks.
“Well, shit. Thanks.”
Joshua snickered.
“Anytime, boss.”
~~~
Sunday Morning
4:08 AM
He stared blearily into the red numerals of his bedside alarm clock, and at him they stared back, burning into his retinas. The dark, quiet stillness of his bedroom that usually felt safe and protective now felt stifling. Oppressive. His left eyelid pulsed. His mind raced, all the sediment that she had helped settle peacefully to the bottom now once again stirred into a familiar, turbid storm.
He had nowhere to be tomorrow. It didn't matter. Sleep came no more easily. He rolled onto his back and took a deep breath, an unnerving blend of depression and dread spreading in his gut. Her voice, her laugh, her touch, her smile--the spell she’d cast, embracing him, coaxing him to worlds blank and peaceful. Someone so kind. Someone so good.
A murderer.
He pulled the blanket to his chin and sighed. He felt hollow. He hadn’t realized how much of him she’d occupied until this past week. He hadn’t realized how much he’d thought of her, was still thinking of her, like a schoolboy. Did he have such precedence in her mind?
He felt a vague sense of unease. All things considered, the spell was broken. He was still unsure of his memories surrounding her and the case, but there was no way around it--he now clearly saw missing contexts abound and uncertainties galore. Perhaps it was all an elaborate, farcical misunderstanding. Either way, from where he sat, things were looking rather bleak for her. It wouldn’t take much longer until he’d have something tenable for the district attorney.
Yet that spell wasn’t entirely broken.
In his office earlier that evening, he’d tortured himself with the proper routine of anger and guilt--of how he’d let such a thing fly under his radar for so long, what he could’ve done differently. He chastised himself, heavily, for not paying closer attention, not exerting stronger willpower. Falling for such a simple, underhanded tactic. Spending so long honing and protecting various entries to his mind that he’d left his heart completely unguarded.
"You weak son of a bitch," he groaned quietly.
Sure, those were the normal thoughts. But now, alone, in his bed, shrouded in black, his mind dredged up his deepest, most basal feelings to lay bare, leaving him unable to escape. He stared into nothingness, wishing for her reassurance, thinking of what the victim might have done to deserve such an end. Surely it was something commensurate with murder.
Most torturously, making him feel even more pathetic, he lay there wishing more than anything else not that she hadn't killed James Walter, but that she’d done a better job covering her tracks. He let air escape through his teeth at the mere thought. If she was going to puppeteer him to such an extent, she could’ve at least taken the care to keep the strings from snapping, sending his body crumpling to the ground, lifeless and alone. The least she could've done was allow him to remain blissfully unaware.
But this was his reality now. There was nothing to be done about it.
Suddenly, in vivid detail he recalled the sensation of her arms around him. The way her mere presence heightened every moment. Her scent. Her skin. Her smile. Tears pricked at the corners of his eyes.
She seemed so unbothered that he hadn’t shown up last night. After every weekend for the past five months…she hadn’t bothered to call him? Text him? Didn't she worry? Didn’t she care?
Didn't she have anything to say for herself?
~~~
Monday Morning, Two Weeks Later
“Take me to Detective Berman's office. No, I have n--I don’t care, I demand to see him this inst--what? Well, he’ll tell you why!”
Detective Berman tensed in his chair. The good doctor herself, clad in oversized sunglasses and a fashionable black fur coat he'd never seen on her before, stormed into his office, handcuffed and flanked by two patrolmen plus Sergeant Joshua.
“Detective! I believe I deserve an answer for this.”
He rose from his desk, thankful she was wearing sunglasses to enshroud those eyes of hers. She looked directly at him. He kept his eyes on the desk.
“I believe not.”
Mouth agape, she glared at him, incredulous. A brief silence fell before he shook his head and continued.
“He was going to expose you, wasn't he?”
“What the hell are you talking about?”
The detective picked up the folder on his desk and opened it, showing her.
“Thought you wiped all the copies, didn’t you?” She took a full second’s look at its contents and turned her head. A silence befell the room.
“…I demand a lawyer. This is libel,” she said, her bottom lip trembling slightly.
“You didn't do a good enough job.”
“I--”
“I would close my mouth if I were in your position, madam," he said, by sheer conditioning still unable to shake the honorific, which, thankfully, now only masqueraded to the others as politeness. He could discern the outline of her eyes through her glasses now, wide, and for the first time he’d ever seen them, genuinely frightened. “For someone who knows enough to ask for a lawyer, especially. I'm sure you've already been read your rights.”
“I have,” she said, her breath so faint it felt barely there. “Well. Seems as though I’m under arrest."
The detective swallowed thickly, giving her naught but a mere silent, heavy nod. He put his hands on his desk and leaned forward, stabilizing, attempting to stave off the waves of relieved exhaustion rippling through him, his knees buckling despite himself.
“Yes, Madam. Afraid so.” With a motion of his hand, the officers escorted her out of his office.
After a moment, Detective Berman allowed himself to slump down in his chair. It’d been so long since he’d heard that word straight from her lips. For how much bitterness had built up inside him towards her, to finally hear that word again quelled so much of it that he shuddered. He’d missed it. He’d craved it.
He feared it.
“You okay sir?” Sergeant Joshua asked after witnessing the spectacle. “What was up with that? Kinda weird, right? Pretty obvious she was under arrest.”
Forearm draped on his head, the senior detective sighed and allowed his eyes to close.
“All good, Joshua. Just feels like I am, too.”
5 notes
·
View notes
Text
Foto imagezilla pussy

#Foto imagezilla pussy iso#
#Foto imagezilla pussy series#
#Foto imagezilla pussy free#
Pornxxx Video Pornpics Nubiles Linda Lay Locker Brunettes Imagezilla! Bodacious brunette broad takes her dress off and vibrates her smelting hot pussy in bed. Google has many special features to help you find exactly what you're looking for. Watch Now: moesearch imagezilla nuderemiumhentai shotacon boy pussy lips pussy licking pussy eating pussy nude masturbating hairy pussy fingering fake.
#Foto imagezilla pussy series#
(submitted by IG bassesofdeath and toydollani) Dad Here’s Looking At You, Kid This photo was one pose in a series of shots my family had taken in about 1981. Xxx Fuckingmachines Jagger Jordan Mobivid Masturbation Imagezilla Bondage Gallery, Jagger Jordan Extreme Bondage Sex, Jagger Jordan Hq Bondage Porn Pics.
#Foto imagezilla pussy free#
The site is loaded with hot models whom recently turned the ripe age of 18 and can finally live their dream and be in porn! Witness the newest, freshest faces as they undress to impress only at the recently improved ! With the new design last November the site has a much cleaner look. Imagezilla Pornxxx Video, Linda Lay Free Anal Sex Pictures, Linda Lay Xxx Photos Archives, Linda Lay Sexy Mature Ladies and Linda Lay Vagina Pics. Search the world's information, including webpages, images, videos and more. Photos Seriously My wife on the far right and her family circa 1999 right after their dad yelled at the kids for not taking the portraits seriously. Nubiles Pornpics Site Reviews: Nubiles is the place to go if you are looking for sexually charged, barely legal girls displaying their attractive bodies in some of the most amazing exclusive scenes through HQ photos and videos.
#Foto imagezilla pussy iso#
Once you have the Clonezilla live iso or zip file, please follow this Live CD/USB doc to put it on the boot media, and follow this Live Docs to use it.Linda Lay Biography: Age: 20 Location: USA Height: 4 ' 11 " Photosets: 6 Figure: 32 D D - 24 - 28 Movies: 97 Minutes ABOUT Linda Lay: Linda Lay is a sassy latina with curves in all the right places! Her huge tits are perfectly round bouncing mounds of pleasure while her tight shaved pussy takes a hard pounding. Porn Filthykings Jeanie Marie Sullivan Ppoto Massage Imagezilla Nipples Pics, Jeanie Marie Sullivan Hard Nipples Pics, Jeanie Marie Sullivan Free Dirty.
Checksum files, not iso or zip ones, are GPG signed by DRBL project, which has the fingerprint: 54C0 821A 4871 5DAF D61B FCAF 6678 57D0 4559 9AFD. Xxx Tiedvirgins Tiedvirgins Model Povd Porn Imagezilla Bondage Gallery, Tiedvirgins Model Extreme Bondage Sex, Tiedvirgins Model Hq Bondage Porn Pics.
If your machine comes with uEFI secure boot enabled, you have to use AMD64 (X86-64) version (either Debian-based or Ubuntu-based) of Clonezilla live. My grandpa (the one with the 3-foot long pointy shirt collar) is happily showing us a centerfold spread from a gentlemen’s magazine while my uncle and grandma display a macrame blanket. Thousands of new, high-quality pictures added every day. Watch Now: imagezilla pussy young old man fucking young pussy real mom and young son touch mpm pussy shaved young thai.
All versions of Clonezilla live support machine with legacy BIOS. Favorite Things Here we see my uncle and grandparents, in a photo taken by my mom. Find stock images in HD and millions of other royalty-free stock photos, illustrations and vectors in the Shutterstock collection. that you evaluate the following pics: Armenian pussy armenian p, Beautiful vaginas legs spread, Busty fatty amber lee, Cyberporn mature imagezilla. Watch Now: saudi bbw showing big boobs and cum leaking out of her pussy cum leaking out of her pussy mmsgirl sex xenxx com sex video 2mb video sexoy.
Checksums, checksums gpg, changelog, known issue, release noteĬhecksums, checksums gpg changelog, known issue, release noteĬhecksums, checksums gpg, changelog, known issue

3 notes
·
View notes
Text
is using vpn secure
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
is using vpn secure
VPN encryption methods
VPN encryption methods are crucial for ensuring the security and privacy of your online activities. When you connect to a Virtual Private Network (VPN), your data is encrypted to protect it from being intercepted or accessed by third parties. There are several encryption methods used by VPN providers to safeguard your information.
One of the most common encryption protocols is OpenVPN, which is known for its strong security features. OpenVPN uses the OpenSSL library and provides a high level of encryption, making it difficult for hackers to decipher your data.
Another popular encryption method is IPSec (Internet Protocol Security), which operates at the network layer of the OSI model. IPSec can be used in combination with other encryption protocols to create a secure VPN connection.
SSL/TLS (Secure Sockets Layer/Transport Layer Security) is another encryption method often used by VPN services. SSL/TLS encryption is commonly employed by websites to secure online transactions, and when used in a VPN, it ensures the confidentiality and integrity of your data.
L2TP/IPSec (Layer 2 Tunneling Protocol/Internet Protocol Security) is a protocol that combines the best features of L2TP and IPSec. It provides strong encryption and is widely supported across various platforms.
In conclusion, VPN encryption methods play a crucial role in safeguarding your online privacy and security. By choosing a VPN service that uses strong encryption protocols such as OpenVPN, IPSec, SSL/TLS, or L2TP/IPSec, you can enjoy a secure and private internet browsing experience.
VPN logging policies
VPN logging policies are a critical aspect to consider when choosing a virtual private network (VPN) service. These policies outline what user data the VPN provider collects and retains, which can greatly impact user privacy and security.
Essentially, VPN logging policies refer to the recording and storage of user activity while connected to the VPN. There are three main types of logging policies:
No-Logs Policy: This is considered the most privacy-friendly option. VPN providers with a strict no-logs policy do not monitor, record, or store any user activity or connection logs. This means that even if requested by authorities or hackers, the VPN provider cannot provide any user data because they simply do not have it.
Some Logs Policy: Some VPN providers may collect minimal logs for troubleshooting purposes or to optimize their service. However, they claim not to collect any personally identifiable information (PII) or browsing history. While this may offer more transparency, there is still a risk that these logs could be accessed by third parties.
Full Logs Policy: VPN providers with full logs policies collect and store extensive user data, including browsing history, connection timestamps, IP addresses, and more. This poses significant privacy risks, as this data could potentially be exploited by hackers or requested by government agencies.
When selecting a VPN service, it's crucial to carefully review the provider's logging policy to ensure it aligns with your privacy and security needs. Opting for a VPN with a strict no-logs policy can offer peace of mind knowing that your online activities remain private and anonymous. Additionally, it's advisable to choose a reputable VPN provider with a proven track record of respecting user privacy and transparency.
VPN tunneling protocols
VPN tunneling protocols are the backbone of secure and private internet connections. These protocols establish a secure pathway, or tunnel, through which data travels between your device and the VPN server. Here are some of the most common VPN tunneling protocols:
OpenVPN: Known for its open-source nature and strong security features, OpenVPN is highly versatile and can run on various platforms. It uses OpenSSL encryption to ensure data confidentiality and supports both UDP and TCP connections.
IPSec (Internet Protocol Security): IPSec operates at the network layer of the OSI model and provides encryption, authentication, and integrity verification for VPN connections. It's often used in conjunction with other protocols like L2TP (Layer 2 Tunneling Protocol) or IKEv2 (Internet Key Exchange version 2) for enhanced security.
L2TP/IPSec (Layer 2 Tunneling Protocol/Internet Protocol Security): L2TP/IPSec combines the features of L2TP and IPSec to offer a highly secure VPN connection. L2TP provides the tunneling mechanism, while IPSec ensures data encryption and authentication.
PPTP (Point-to-Point Tunneling Protocol): PPTP is one of the oldest tunneling protocols and is known for its simplicity and ease of setup. However, it's considered less secure than other protocols due to vulnerabilities in its encryption.
IKEv2 (Internet Key Exchange version 2): IKEv2 is a modern tunneling protocol that offers fast and stable connections, making it ideal for mobile devices. It supports seamless roaming between networks and provides robust security features.
Choosing the right VPN tunneling protocol depends on factors like security requirements, device compatibility, and speed. While some protocols prioritize speed and ease of use, others focus on robust encryption and authentication. Ultimately, selecting the appropriate protocol ensures a safe and reliable VPN experience.
VPN security vulnerabilities
VPN (Virtual Private Network) services are widely used by individuals and businesses seeking to enhance their online security and privacy. However, like any technological tool, VPNs are not foolproof and can be vulnerable to security breaches if not properly configured or maintained.
One common VPN security vulnerability is the use of outdated encryption protocols. Inadequate encryption can leave the connection susceptible to hackers who may intercept and decipher the data being transmitted. It is crucial to ensure that your VPN provider uses strong encryption standards, such as AES-256, to protect your online activities effectively.
Another vulnerability is the 'VPN leak,' where the user's true IP address is inadvertently revealed despite being connected to the VPN. This can occur due to misconfigurations in the VPN software or the operating system, potentially exposing the user's identity and compromising their privacy. To prevent leaks, users should regularly test their VPN connection for any vulnerabilities using online tools like IP and DNS leak tests.
Additionally, some VPN providers may log user data, including browsing history and connection timestamps, contrary to their privacy policies. This information can be exploited by third parties or even shared with government authorities, compromising the user's anonymity. It is essential to choose a trustworthy VPN service that values user privacy and has a strict no-logs policy to mitigate this risk.
In conclusion, while VPNs are valuable tools for enhancing online security and privacy, users must remain vigilant against potential vulnerabilities. By selecting a reputable VPN provider, ensuring robust encryption practices, and regularly testing for leaks, individuals can better protect themselves against security threats and safeguard their sensitive information online.
VPN anonymity features
Title: Unveiling the Veil: Exploring VPN Anonymity Features
In today's digital landscape, where online privacy concerns loom large, Virtual Private Networks (VPNs) stand as bastions of anonymity, shielding users from prying eyes and data breaches. But what exactly are the anonymity features that make VPNs such powerful tools in safeguarding our online identities?
First and foremost, VPNs cloak your IP address, the unique identifier assigned to your device when connecting to the internet. By rerouting your internet traffic through encrypted servers located in different regions, VPNs obscure your true IP address, making it virtually impossible for third parties to trace your online activities back to you. This not only enhances your privacy but also allows you to bypass geo-restrictions and access content restricted to specific regions.
Moreover, reputable VPN providers employ robust encryption protocols, such as AES-256, to secure your data transmissions. This means that even if your internet traffic is intercepted, it appears as an unintelligible jumble of characters to anyone without the decryption key, effectively safeguarding your sensitive information from eavesdroppers and hackers.
Additionally, many VPNs offer features like kill switches and DNS leak protection to further fortify your anonymity. Kill switches automatically disconnect your internet connection if the VPN connection drops unexpectedly, preventing your real IP address from being exposed. DNS leak protection, on the other hand, ensures that your DNS queries are routed through the VPN's encrypted servers, thwarting potential leaks of your browsing history and online activities.
In conclusion, VPN anonymity features provide users with a cloak of invisibility in the vast expanse of the internet, shielding them from surveillance, data harvesting, and other privacy threats. By harnessing the power of encryption, IP cloaking, and additional security measures, VPNs empower individuals to reclaim control over their online identities and navigate the digital realm with confidence and peace of mind.
0 notes
Text
which vpn gives free data in nigeria
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
which vpn gives free data in nigeria
Free VPN Nigeria
Title: Exploring Free VPN Services in Nigeria: What You Need to Know
In Nigeria, as in many other parts of the world, the demand for VPN (Virtual Private Network) services has been on the rise. Whether it's for accessing geo-blocked content, enhancing online privacy, or bypassing government censorship, VPNs have become essential tools for internet users. However, finding a reliable and free VPN service in Nigeria can be a challenging task, given the myriad of options available.
While there are numerous free VPN providers claiming to offer secure and anonymous browsing, users should exercise caution and thoroughly research any service before trusting it with their data. It's essential to understand that "free" often comes with limitations and risks.
One of the primary concerns with free VPNs is the potential compromise of user privacy. Some free VPNs may log user data and sell it to third parties for advertising or other purposes, undermining the very reason for using a VPN in the first place. Additionally, free VPNs may have slower connection speeds and fewer server locations compared to their paid counterparts, resulting in a less reliable and slower browsing experience.
Furthermore, users should be wary of free VPNs that employ questionable business models, such as injecting ads into web pages or installing malware on devices. These practices not only compromise user experience but also pose significant security risks.
Despite these challenges, there are reputable free VPN services available in Nigeria that prioritize user privacy and security. Users should look for VPNs that offer strong encryption, a strict no-logs policy, and transparent privacy practices. Additionally, reading reviews and seeking recommendations from trusted sources can help users make informed decisions when choosing a free VPN service.
In conclusion, while free VPN services can provide a temporary solution for users in Nigeria seeking online privacy and accessibility, it's crucial to approach them with caution and skepticism. By understanding the potential risks and limitations associated with free VPNs and choosing reputable providers, users can enjoy a safer and more secure browsing experience.
Data VPN Nigeria
Title: Securing Data in Nigeria: The Importance of VPNs
In Nigeria, as in many countries around the world, the protection of sensitive data is paramount. With the rise of cyber threats and the increasing importance of online privacy, individuals and businesses alike are seeking effective solutions to safeguard their information. One such solution that has gained popularity is the use of Virtual Private Networks (VPNs).
A VPN, or Virtual Private Network, establishes a secure connection between a user and the internet. It encrypts the data transmitted over the network, ensuring that it remains confidential and protected from prying eyes. This is particularly important in Nigeria, where concerns about data privacy and security are on the rise.
One of the primary benefits of using a VPN in Nigeria is the ability to bypass censorship and access restricted content. With internet censorship becoming more prevalent in the country, VPNs offer a way for users to circumvent these restrictions and access the content they need. Whether it's accessing social media platforms, streaming services, or news websites, a VPN provides users with the freedom to browse the internet without limitations.
Furthermore, VPNs help protect against cyber threats such as hacking, phishing, and malware attacks. By encrypting data and masking IP addresses, VPNs make it difficult for cybercriminals to intercept sensitive information or track online activities. This is particularly important for businesses operating in Nigeria, where the risk of cyber attacks is high.
In conclusion, the use of VPNs is essential for securing data in Nigeria. Whether it's protecting against cyber threats or accessing restricted content, VPNs offer users the peace of mind knowing that their data is safe and their online activities remain private. As the importance of online privacy continues to grow, VPNs will undoubtedly play a crucial role in safeguarding sensitive information in Nigeria and beyond.
Best VPN with Free Data
In today's digital age where online privacy is paramount, choosing the best VPN with free data becomes crucial. A Virtual Private Network (VPN) encrypts your internet connection, ensuring your online activities remain private and secure from prying eyes. While many VPN services offer premium features at a price, some providers offer free data plans that allow users to enjoy basic protection without any cost.
One of the best VPNs with free data is ProtonVPN. ProtonVPN offers a free plan with unlimited bandwidth, making it an ideal choice for users looking to secure their online browsing sessions without breaking the bank. The provider also boasts strong encryption protocols and a strict no-logs policy, ensuring your data remains confidential at all times.
Another top contender in the realm of free VPNs is Windscribe. Windscribe offers a generous free plan with 10 GB of data per month, making it suitable for light to moderate users. With servers in over 60 countries and advanced features like ad blocking and malware protection, Windscribe provides a comprehensive solution for safeguarding your online activities.
For users in need of a free VPN with a user-friendly interface, TunnelBear is an excellent choice. TunnelBear offers a free plan with 500 MB of data per month, making it suitable for occasional browsing sessions. The provider's simple design and intuitive controls make it easy to use, even for novice users.
In conclusion, selecting the best VPN with free data depends on your specific needs and usage patterns. Whether you prioritize unlimited bandwidth, generous monthly data limits, or user-friendly interfaces, the aforementioned VPN providers offer excellent options for securing your online privacy without incurring any additional costs.
VPN Data Plans Nigeria
VPN data plans in Nigeria offer users a secure and private way to browse the internet while protecting their sensitive information from potential threats. In a country where internet privacy is increasingly becoming a concern, VPN services provide a solution by encrypting users' data and masking their IP addresses.
With the growing popularity of VPN services in Nigeria, there is a wide range of data plans available to meet different needs and budgets. Users can choose from daily, weekly, monthly, or even annual subscription plans, depending on their usage requirements. Some VPN providers also offer free trials or limited free versions for users to test their services before committing to a paid plan.
VPN data plans in Nigeria come with a variety of features, such as high-speed connections, unlimited bandwidth, multi-device support, and access to servers in multiple countries. This allows users to bypass geo-restrictions and access region-locked content while maintaining their online privacy.
It is essential for Nigerian internet users to consider investing in a VPN data plan to safeguard their online activities and protect themselves from cyber threats. By choosing a reliable VPN service provider and selecting a suitable data plan, users can enjoy a safer and more secure online experience without compromising on their internet freedom.
Nigerian VPN Services
Title: Exploring the Benefits of Nigerian VPN Services
In Nigeria, as in many parts of the world, internet freedom and privacy are increasingly becoming concerns for both individuals and businesses. With the rise in online censorship, surveillance, and cyber threats, the demand for reliable Virtual Private Network (VPN) services has surged. Nigerian VPN services offer a solution to these challenges by providing users with a secure and private connection to the internet.
One of the primary benefits of using a VPN in Nigeria is the ability to bypass online censorship and access restricted content. With many websites and online services being blocked or restricted by the government or internet service providers, VPNs allow users to circumvent these restrictions and access the content they need. This is particularly important for journalists, activists, and anyone else who relies on unrestricted access to information.
Additionally, Nigerian VPN services encrypt users' internet traffic, protecting their data from hackers, government surveillance, and other third parties. This encryption ensures that sensitive information such as passwords, financial transactions, and personal communications remain private and secure. In a country where cybercrime is prevalent, this added layer of security is invaluable for both individuals and businesses.
Moreover, VPNs enable users to maintain anonymity online by masking their IP address and location. This not only protects users' privacy but also allows them to browse the internet without fear of being tracked or monitored. For Nigerians concerned about government surveillance or online harassment, this anonymity is essential for staying safe online.
In conclusion, Nigerian VPN services offer numerous benefits for users seeking to protect their privacy, bypass censorship, and enhance their online security. By encrypting internet traffic, providing access to restricted content, and enabling anonymity online, VPNs empower users to take control of their online experience and stay safe in an increasingly digital world.
0 notes
Text
can you trust vpn services
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can you trust vpn services
VPN encryption protocols
VPN encryption protocols are crucial components of virtual private networks (VPNs), ensuring the security and privacy of users' online activities. These protocols establish the framework for encrypting data as it travels between the user's device and the VPN server, protecting it from interception by malicious actors or unauthorized entities.
One of the most widely used VPN encryption protocols is OpenVPN. OpenVPN is an open-source protocol known for its robust security features and flexibility. It utilizes OpenSSL encryption libraries to encrypt data with either the OpenSSL library's default cipher algorithms or user-selected algorithms. OpenVPN supports various authentication methods and can operate over both UDP (User Datagram Protocol) and TCP (Transmission Control Protocol) connections, making it versatile and adaptable to different network configurations.
Another popular VPN encryption protocol is IPSec (Internet Protocol Security). IPSec operates at the network layer of the OSI model and can be implemented in two modes: Transport mode and Tunnel mode. In Transport mode, only the payload of the IP packet is encrypted, while in Tunnel mode, the entire IP packet, including the header, is encrypted. IPSec employs cryptographic algorithms such as AES (Advanced Encryption Standard) for encryption and HMAC (Hash-based Message Authentication Code) for authentication, providing strong security for VPN connections.
Additionally, L2TP/IPSec (Layer 2 Tunneling Protocol/Internet Protocol Security) is a commonly used protocol for VPNs, combining the features of L2TP and IPSec to establish secure tunnels for data transmission. While L2TP itself does not provide encryption, when combined with IPSec, it creates a secure encrypted connection.
In conclusion, VPN encryption protocols like OpenVPN, IPSec, and L2TP/IPSec play a crucial role in safeguarding the privacy and security of users' online communications. By encrypting data transmitted over VPN connections, these protocols help prevent unauthorized access and protect sensitive information from interception.
VPN privacy policies
VPN privacy policies are a critical aspect to consider when choosing a Virtual Private Network (VPN) service. These policies outline how the VPN provider collects, uses, and protects user data. Understanding these policies is essential for ensuring your online privacy and security.
One key aspect of VPN privacy policies is data logging. Some VPN providers may keep logs of user activity, including websites visited, files downloaded, and IP addresses used. This information can potentially be traced back to individual users and compromise their privacy. However, reputable VPN services often have strict no-logs policies, meaning they do not collect any user data whatsoever. Opting for a VPN with a no-logs policy can significantly enhance your privacy and anonymity online.
Another important consideration is data encryption. A reliable VPN will use strong encryption protocols to safeguard your internet traffic from interception by third parties, such as hackers or government agencies. Look for VPN providers that utilize advanced encryption algorithms like AES-256, which is widely regarded as highly secure.
Additionally, VPN privacy policies should clarify how the provider handles legal requests for user data. In some jurisdictions, VPN companies may be required to comply with government subpoenas or warrants, potentially compromising user privacy. Transparent policies regarding data disclosure and user notification can help users make informed decisions about their privacy risks.
Lastly, it's crucial to review a VPN provider's jurisdiction. Some countries have strict data retention laws or are part of international surveillance alliances, posing potential risks to user privacy. Choosing a VPN based in a privacy-friendly jurisdiction can help mitigate these risks.
In conclusion, carefully reviewing VPN privacy policies is essential for safeguarding your online privacy. By selecting a VPN service with a commitment to user privacy, strict no-logs policies, robust encryption, and a favorable jurisdiction, you can enjoy enhanced privacy and security while browsing the internet.
VPN user reviews
VPN user reviews play a crucial role in helping individuals make informed decisions when selecting a Virtual Private Network (VPN) service. These reviews provide valuable insights into the performance, reliability, and overall user experience of different VPN providers.
By reading VPN user reviews, potential customers can get a sense of the speed and connectivity of the service, as well as its ability to bypass geo-restrictions and provide a secure online browsing experience. Users often share their experiences with streaming services, online gaming, and torrenting to give others an idea of how well the VPN performs for various activities.
Additionally, user reviews often highlight customer support experiences, pricing plans, and the user-friendliness of the VPN applications. This information is valuable for individuals looking for a VPN that not only offers robust security features but also excellent customer service and easy-to-use interfaces.
It is important to note that while VPN user reviews can be insightful, they should be considered alongside expert reviews and recommendations from reputable sources. This comprehensive approach ensures that individuals can make well-rounded decisions when choosing a VPN service that best suits their needs.
In conclusion, VPN user reviews are a valuable resource for anyone looking to invest in a VPN service. By reading and analyzing user feedback, individuals can gain a better understanding of what to expect from a particular VPN provider and make an informed choice to enhance their online privacy and security.
VPN security audits
VPN Security Audits: Ensuring Online Privacy and Protection
In an era where digital privacy is increasingly under threat, Virtual Private Networks (VPNs) have emerged as essential tools for safeguarding online security and anonymity. However, not all VPN services are created equal, and users need assurance that the VPN they trust is truly secure. This is where VPN security audits play a crucial role.
VPN security audits involve comprehensive evaluations of a VPN provider's infrastructure, protocols, and policies to assess its security and privacy capabilities. These audits are typically conducted by independent third-party firms specializing in cybersecurity. By scrutinizing various aspects of a VPN service, including its encryption methods, data logging practices, and server infrastructure, these audits provide users with valuable insights into the reliability and trustworthiness of the VPN.
One of the primary objectives of VPN security audits is to identify any vulnerabilities or weaknesses in the VPN's security architecture. This includes assessing the strength of encryption algorithms used to protect data transmission and storage, as well as evaluating the VPN's adherence to best practices in network security.
Additionally, VPN security audits examine the provider's logging policies to determine whether they collect any personally identifiable information (PII) or browsing activity from users. A trustworthy VPN should have a strict no-logs policy, ensuring that user data remains private and anonymous at all times.
Moreover, VPN security audits evaluate the geographical distribution and security measures of the VPN's server network. This helps assess the resilience of the VPN against potential attacks or breaches and ensures that users can access a reliable and secure connection from any location.
By undergoing regular security audits, VPN providers demonstrate their commitment to transparency and accountability, reassuring users of their dedication to protecting their online privacy and security. For users seeking a reliable VPN service, looking for providers that have undergone independent security audits can provide peace of mind and confidence in their choice of protection against cyber threats.
VPN provider reputation
Maintaining a sterling reputation is paramount for VPN (Virtual Private Network) providers in today's digital landscape. With cyber threats looming large and privacy concerns at an all-time high, consumers are increasingly turning to VPN services to safeguard their online activities. However, not all VPN providers are created equal, and their reputation plays a pivotal role in attracting and retaining customers.
A VPN provider's reputation hinges on several key factors. Firstly, trustworthiness is non-negotiable. Users entrust VPNs with their sensitive data, expecting it to be shielded from prying eyes. Any breach of trust, be it through data leaks or questionable privacy policies, can irreparably tarnish a provider's reputation.
Performance is another critical aspect. A reputable VPN should offer reliable and high-speed connections, ensuring seamless browsing, streaming, and downloading experiences for users. Any downtime or sluggish performance can quickly erode trust and lead to negative reviews.
Transparency and accountability are also vital. Users appreciate VPN providers that are upfront about their logging practices, encryption standards, and data handling procedures. Any opacity or ambiguity in these areas can raise red flags and cast doubt on a provider's credibility.
Moreover, customer support plays a pivotal role in shaping a VPN provider's reputation. Prompt and knowledgeable support staff can resolve issues swiftly, enhancing user satisfaction and fostering positive word-of-mouth recommendations.
Lastly, a history of security incidents or controversies can significantly damage a VPN provider's reputation. Whether it's involvement in data scandals or allegations of collaboration with government surveillance programs, such incidents undermine trust and credibility.
In conclusion, a VPN provider's reputation is a delicate yet crucial asset in today's cybersecurity landscape. By prioritizing trustworthiness, performance, transparency, customer support, and security, VPN providers can build and maintain a solid reputation, earning the confidence of discerning users seeking privacy and protection online.
0 notes
Text
don't use your google account on vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
don't use your google account on vpn
VPN privacy risk
Title: The Hidden Risks of VPNs: Navigating Privacy Concerns
Virtual Private Networks (VPNs) have gained immense popularity as a tool for safeguarding online privacy and security. However, beneath their protective facade lurk certain risks that users must be aware of to navigate the digital landscape safely.
One primary concern revolves around the logging policies of VPN providers. While many claim not to keep logs of user activity, the reality may be different. Some VPNs may store connection logs, including timestamps and IP addresses, which could potentially be exploited or subpoenaed by authorities. Additionally, the jurisdiction in which the VPN operates plays a crucial role, as laws regarding data retention vary from country to country.
Furthermore, the encryption protocols employed by VPNs can also pose risks if not implemented correctly. Weak encryption or outdated protocols may leave users vulnerable to hacking or surveillance, defeating the purpose of using a VPN for privacy protection. Additionally, DNS leaks can occur, exposing users' browsing habits to third parties despite being connected to a VPN.
Another often-overlooked risk is the reliance on third-party services for infrastructure and hosting. Many VPN providers lease servers from data centers, which introduces another layer of potential vulnerability. If these servers are compromised or controlled by malicious actors, users' data could be at risk without their knowledge.
Moreover, the proliferation of free VPN services raises suspicions about their business models. In many cases, free VPNs may monetize user data by selling it to advertisers or other third parties, undermining the very notion of privacy that users seek.
In conclusion, while VPNs offer a means to enhance online privacy, they are not without risks. Users must exercise caution when selecting a provider, thoroughly researching their logging policies, encryption standards, and business practices. Ultimately, vigilance is key to mitigating the privacy risks associated with VPN usage in an increasingly digital world.
Google account security
Google account security is a crucial aspect of maintaining the privacy and integrity of your personal information online. With the increasing threat of cyber attacks and data breaches, it is more important than ever to take proactive steps to protect your Google account.
One of the first and most effective ways to secure your Google account is by enabling two-factor authentication (2FA). This adds an extra layer of security by requiring not only your password but also a secondary verification method, such as a code sent to your mobile device. This makes it much harder for hackers to gain unauthorized access to your account.
Regularly updating your password is another key measure to enhance Google account security. It is recommended to use a strong, unique password that includes a combination of letters, numbers, and special characters. Avoid using the same password for multiple accounts and consider using a password manager to securely store and manage your passwords.
Monitoring your account activity is essential for detecting any suspicious behavior that may indicate a security breach. Google provides tools such as Security Checkup, which allows you to review your account security settings and recent activity to ensure everything is in order.
It is also important to be cautious of phishing attempts and scams that may try to trick you into revealing your account credentials. Avoid clicking on suspicious links or providing personal information to unknown sources.
By implementing these best practices and staying vigilant, you can significantly reduce the risk of unauthorized access to your Google account and protect your sensitive data from falling into the wrong hands.
Online identity protection
Title: Safeguarding Your Online Identity: Tips for Effective Protection
In an increasingly digital world, protecting your online identity is paramount. With cyber threats evolving constantly, safeguarding your personal information has become more challenging yet crucial than ever before. Whether you're browsing social media, shopping online, or accessing financial accounts, here are some tips to help you fortify your online identity:
Strong Passwords: Create complex passwords using a combination of letters, numbers, and special characters. Avoid using easily guessable information like birthdates or pet names. Consider using a reputable password manager to generate and store unique passwords for each account.
Two-Factor Authentication (2FA): Enable 2FA whenever possible. This adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone, in addition to your password.
Keep Software Updated: Ensure that your operating system, antivirus software, and applications are regularly updated with the latest security patches. Outdated software can leave vulnerabilities that hackers exploit to access your information.
Beware of Phishing Attempts: Be cautious of unsolicited emails, messages, or phone calls requesting personal information. Phishing scams often mimic legitimate organizations to trick individuals into revealing sensitive data. Verify the authenticity of requests before responding or providing any information.
Secure Wi-Fi Connections: Use encrypted Wi-Fi connections, especially when accessing sensitive accounts or conducting financial transactions. Avoid connecting to public Wi-Fi networks without proper security measures in place, as they can be compromised by cybercriminals.
Monitor Your Accounts: Regularly review your bank statements, credit reports, and online accounts for any unauthorized activity. Report any suspicious transactions or discrepancies immediately to prevent further damage.
Limit Personal Information Sharing: Be cautious about sharing personal information on social media and other online platforms. Restrict privacy settings to control who can view your profile and limit the amount of information you share publicly.
By implementing these proactive measures, you can better protect your online identity and minimize the risk of falling victim to cyber threats. Stay vigilant and prioritize security to safeguard your digital presence effectively.
IP address masking
IP address masking is a method used to hide or alter an internet user's IP address. It is typically employed to enhance privacy, increase security, or bypass geographical restrictions. By masking their IP address, users can browse the internet anonymously and prevent their online activities from being easily traced back to them.
There are several ways to mask an IP address, including proxy servers, virtual private networks (VPNs), and the Tor network. Proxy servers act as intermediaries between a user's device and the internet, masking the user's IP address with the server's IP address. VPNs encrypt a user's internet traffic and route it through a server in a different location, effectively hiding the user's IP address and location. The Tor network routes internet traffic through a series of encrypted relays, making it difficult to trace the user's IP address.
IP address masking is commonly used by individuals who want to protect their privacy online, such as journalists, activists, and whistleblowers. It is also utilized by people who wish to access region-restricted content, such as streaming services or websites that are blocked in their country.
While IP address masking can enhance privacy and security, it is important to note that it is not foolproof. Advanced tracking techniques and vulnerabilities in certain masking methods can potentially expose a user's true IP address. Therefore, users should exercise caution and ensure they are using reputable masking tools to safeguard their online anonymity and security.
Data encryption technology
Data encryption technology is a crucial aspect of data security in the digital world. It involves converting plain text data into encoded information that can only be accessed and read by authorized parties with the corresponding decryption key. This process ensures that sensitive information remains confidential and protected from unauthorized access or cyber-attacks.
There are various encryption techniques used to secure data, including symmetric-key encryption and public-key encryption. Symmetric-key encryption uses a single key to both encrypt and decrypt data, making it efficient for secure communication between two parties. On the other hand, public-key encryption involves a pair of keys - a public key for encryption and a private key for decryption. This method is commonly used for secure online transactions and digital signatures.
The advancement of data encryption technology has led to the development of more robust encryption algorithms, such as Advanced Encryption Standard (AES) and RSA (Rivest-Shamir-Adleman). These algorithms provide high levels of security and are widely adopted by organizations to safeguard their sensitive data.
Data encryption technology plays a crucial role in protecting personal information, financial data, and confidential business communications from potential security breaches and data theft. By implementing strong encryption measures, organizations can enhance their cybersecurity posture and ensure the privacy and integrity of their data.
In conclusion, data encryption technology is a fundamental tool in the realm of cybersecurity, providing a secure method to protect sensitive information in the digital age. As cyber threats continue to evolve, implementing robust encryption practices is essential to safeguard data and uphold privacy standards.
0 notes
Text
does revit collaboration work over a vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does revit collaboration work over a vpn
Revit VPN compatibility
Title: Understanding Revit VPN Compatibility: Ensuring Seamless Connectivity and Security
Revit, a powerful software for architecture, engineering, and construction professionals, demands robust connectivity for efficient collaboration and data management. With the increasing need for remote work and data security, integrating a Virtual Private Network (VPN) with Revit becomes crucial. VPNs encrypt internet traffic, ensuring privacy and security, but not all VPNs are compatible with Revit’s intricate network requirements.
Compatibility is key when selecting a VPN for Revit. Revit relies heavily on real-time collaboration and data synchronization, requiring stable and high-speed connections. Some VPNs may throttle bandwidth or introduce latency, hindering Revit’s performance. Therefore, choosing a VPN with optimized infrastructure for data-intensive applications like Revit is essential.
Additionally, Revit’s licensing system may pose challenges when using a VPN. Some VPNs may alter IP addresses or network configurations, leading to licensing issues and disruptions in software access. It’s crucial to verify that the VPN provider supports static IP addresses or offers solutions to mitigate licensing conflicts.
Security is another critical aspect of Revit VPN compatibility. Construction projects often involve sensitive data, including designs, blueprints, and client information. A VPN with robust encryption protocols and advanced security features safeguards data from potential breaches or cyber-attacks, ensuring confidentiality and compliance with industry regulations.
Moreover, user experience plays a vital role in Revit VPN compatibility. A user-friendly VPN interface and seamless integration with Revit enhance productivity and workflow efficiency. Look for VPN providers offering dedicated apps for various platforms and easy-to-follow setup instructions to streamline the deployment process.
In conclusion, selecting a compatible VPN for Revit is essential for ensuring uninterrupted workflow, data security, and optimal performance. By prioritizing compatibility, security, and user experience, professionals can harness the full potential of Revit while working remotely or collaborating across different locations.
Remote collaboration in Revit
Remote collaboration in Revit is becoming increasingly popular as teams look for ways to work together efficiently even when physically apart. Revit, a building information modeling (BIM) software by Autodesk, allows architects, engineers, and construction professionals to collaborate on a project in real-time, regardless of their location.
One of the key benefits of remote collaboration in Revit is the ability for multiple users to work on the same model simultaneously. This feature enables team members to make changes, add annotations, and provide feedback in real-time, fostering a more seamless and productive workflow. With the use of cloud technology, team members can access the most up-to-date version of the project, ensuring that everyone is working with the latest information.
Another advantage of remote collaboration in Revit is the ability to communicate effectively with team members through various tools within the software. Users can leave comments, markup designs, and track changes, making it easier to coordinate tasks and communicate project requirements. Additionally, the software allows for version control, ensuring that the project remains organized and all changes are recorded.
Furthermore, remote collaboration in Revit promotes better teamwork and decision-making, as project stakeholders can gather virtually to review designs, identify issues, and resolve conflicts in real-time. This level of collaboration leads to improved project outcomes, reduced errors, and increased efficiency in the design and construction process.
In conclusion, remote collaboration in Revit offers a comprehensive solution for teams to work together effectively from anywhere in the world. By leveraging the software's collaborative features and cloud capabilities, professionals can streamline their workflow, enhance communication, and ultimately deliver successful projects.
VPN performance with Revit
Title: Maximizing VPN Performance with Revit: Enhancing Speed and Stability
When it comes to using Revit, a powerful Building Information Modeling (BIM) software, architects, engineers, and designers often seek seamless performance for their projects. However, accessing Revit remotely through a Virtual Private Network (VPN) can sometimes pose challenges, impacting both speed and stability. Understanding how to optimize VPN performance with Revit is crucial for ensuring efficient workflow and project success.
One of the primary considerations when using a VPN with Revit is the choice of VPN provider. Opting for a reputable provider with a robust infrastructure and high-speed servers can significantly enhance performance. Look for VPNs that offer dedicated servers optimized for tasks like streaming or gaming, as these servers are often better suited for handling the bandwidth requirements of Revit.
Additionally, configuring the VPN settings correctly can make a notable difference in performance. Utilizing protocols like OpenVPN or WireGuard, which prioritize speed and security, can help maintain a stable connection while minimizing latency. Adjusting encryption settings to find the right balance between security and performance is also recommended.
Furthermore, optimizing Revit's settings can further improve performance over a VPN connection. Adjusting the software's synchronization settings to reduce the frequency of automatic updates can help conserve bandwidth and minimize lag. Additionally, utilizing local caching for project files can reduce the need for constant data transfers over the VPN.
Regularly monitoring and troubleshooting VPN performance is essential for identifying and addressing any issues promptly. Conducting speed tests, checking for software updates, and troubleshooting network congestion can help maintain optimal performance when using Revit over a VPN.
In conclusion, maximizing VPN performance with Revit requires careful consideration of VPN provider, configuration settings, and software optimization. By implementing these strategies, users can ensure a smooth and efficient BIM workflow, regardless of their location or network environment.
Revit cloud collaboration via VPN
Revit is a powerful software used by architects and engineers for Building Information Modeling (BIM) to design and collaborate on construction projects. With the growing trend of remote work and cloud-based solutions, Revit cloud collaboration via a Virtual Private Network (VPN) has become essential for teams working on projects from different locations.
By utilizing a VPN, team members can securely connect to the cloud server hosting the Revit project files. This allows them to access, edit, and save the project in real-time, ensuring seamless collaboration regardless of geographical barriers. VPNs encrypt data transmission, providing a secure channel for users to share sensitive project information without the risk of interception.
One of the key benefits of using a VPN for Revit cloud collaboration is enhanced security. With project files stored in the cloud, VPN encryption adds an extra layer of protection against cyber threats, safeguarding intellectual property and confidential data. Additionally, VPNs help maintain data integrity by ensuring that only authorized team members can access and modify project files.
Furthermore, VPNs enable teams to overcome internet restrictions and access cloud servers from any location, boosting productivity and efficiency. Whether working from home, a client site, or a remote office, team members can stay connected to the Revit project and contribute to its progress in real-time.
In conclusion, Revit cloud collaboration via VPN offers a secure, efficient, and flexible solution for teams to work together on BIM projects remotely. By leveraging the benefits of VPN technology, architecture and engineering firms can streamline their workflow, improve collaboration, and deliver high-quality projects efficiently.
Enhancing Revit teamwork over VPN
Enhancing Revit Teamwork over VPN
In the dynamic landscape of architecture and engineering, effective collaboration is paramount. With teams often spread across different locations, ensuring seamless communication and access to project files becomes a challenge. However, with the advent of Virtual Private Networks (VPNs), teams can bridge geographical gaps and collaborate efficiently. This holds particularly true for teams working with Revit, the Building Information Modeling (BIM) software widely used in the architecture, engineering, and construction industries.
VPNs create a secure and encrypted connection over the internet, allowing team members to access the shared network as if they were physically present in the same location. This means that regardless of their physical location, team members can collaborate on Revit projects in real-time, making changes, sharing updates, and coordinating efforts seamlessly.
One of the key benefits of using VPNs for Revit teamwork is the ability to access centralized project files stored on a shared server. This ensures that all team members have access to the most up-to-date version of the project, eliminating version control issues and reducing the risk of errors or conflicts.
Moreover, VPNs provide a secure environment for transferring sensitive project data. With encryption protocols in place, team members can share files and communicate without worrying about unauthorized access or data breaches.
To further enhance Revit teamwork over VPN, teams can implement collaborative tools and workflows. For example, utilizing cloud-based platforms alongside VPNs can streamline document sharing and project management. Additionally, establishing clear communication channels and protocols ensures that team members stay connected and informed throughout the project lifecycle.
In conclusion, leveraging VPNs for Revit teamwork offers numerous benefits, including enhanced collaboration, improved access to project files, and heightened security. By adopting these technologies and implementing effective workflows, architecture and engineering teams can maximize productivity and deliver high-quality projects, regardless of geographical constraints.
0 notes
Text
do some versions of ipad not have vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do some versions of ipad not have vpn
No VPN on certain iPad models
Some users may come across the issue of not having the VPN option available on certain iPad models. This can be frustrating for those who rely on VPN services for privacy and security when browsing the internet. The absence of the VPN option on specific iPad models may be due to various reasons, including software limitations or device specifications.
If you are experiencing this issue, there are a few steps you can take to troubleshoot and potentially resolve it. Firstly, ensure that your iPad model is supported for VPN usage. Some older models may not have the capability to support VPN services due to hardware limitations.
Secondly, make sure that your iOS software is up to date. Updating your iPad to the latest iOS version may bring back the VPN option if it was previously missing due to a software glitch.
If updating the software does not solve the problem, you can try resetting your network settings. This can sometimes help in restoring missing features or settings on your iPad, including the VPN option.
It is also worth checking with the VPN service provider to see if they have any specific recommendations or solutions for your iPad model. They may have insights or workarounds that can help you enable the VPN option on your device.
In conclusion, the absence of the VPN option on certain iPad models can be a common issue with potential solutions available. By following these troubleshooting steps and seeking assistance from the VPN provider if needed, you may be able to resolve the issue and continue using VPN services on your iPad seamlessly.
iPad versions without VPN
iPad versions without VPN
Using a Virtual Private Network (VPN) on an iPad can offer a secure and private browsing experience, protecting your online activity from prying eyes. However, there may be instances when you are unable to use a VPN on your iPad due to various reasons. In such cases, it is important to understand the potential risks and take necessary precautions to safeguard your data and privacy.
Without a VPN, your online activities are more vulnerable to surveillance and data interception by third parties such as hackers, advertisers, and even your internet service provider. This could expose sensitive information such as passwords, financial details, and browsing history. Additionally, accessing public Wi-Fi networks without a VPN can pose significant security risks since these networks are often prime targets for cyberattacks.
If you find yourself using an iPad version without VPN capabilities, there are alternative measures you can take to enhance your online security. For example, you can opt for apps and websites that offer encrypted connections (HTTPS) to protect your data during transmission. It is also advisable to avoid accessing sensitive information or making online transactions on unsecured networks.
Furthermore, keeping your iPad's operating system and apps updated is crucial to mitigate potential security vulnerabilities. Regularly review your privacy settings and permissions to ensure that you are only sharing necessary information with apps and services.
While using a VPN provides an additional layer of security and privacy protection, being mindful of security best practices and taking proactive steps to secure your iPad can help minimize risks in the absence of a VPN. Remember to prioritize your online safety and adopt precautionary measures to safeguard your digital presence.
VPN absence on specific iPads
Title: Understanding the Absence of VPN Support on Certain iPads
In the realm of digital privacy and security, Virtual Private Networks (VPNs) have become indispensable tools for safeguarding online activities. However, some iPad users may find themselves perplexed by the absence of VPN support on their devices. This absence primarily affects older models and specific configurations, raising questions about compatibility and functionality.
The lack of VPN support on certain iPads stems from hardware limitations and software capabilities. Older iPad models, particularly those released before iOS 7, may lack the necessary hardware components to effectively implement VPN protocols. Additionally, some entry-level iPad variants may not offer VPN support as a cost-saving measure, limiting their ability to establish secure connections to remote servers.
Furthermore, the absence of VPN support on certain iPads could be attributed to software restrictions imposed by Apple. As iOS evolves with each iteration, older devices may not receive updates or features included in newer releases. Consequently, users with outdated iPads may find themselves unable to access VPN functionality due to incompatible software versions or deprecated features.
While the lack of VPN support on specific iPads may present a challenge for users seeking enhanced privacy and security, there are alternative solutions available. Users can explore third-party VPN applications from the App Store, which may offer compatibility with older iPad models or circumvent software limitations imposed by Apple. Additionally, upgrading to a newer iPad model equipped with the latest hardware and software advancements ensures seamless integration with VPN services, providing users with peace of mind when browsing the internet.
In conclusion, the absence of VPN support on certain iPads is a result of hardware limitations, software restrictions, and product differentiation strategies. Despite these challenges, users can explore alternative solutions or consider upgrading to newer iPad models to enjoy the benefits of VPN technology.
Lack of VPN feature on iPads
As iPads continue to be a popular choice for users looking for a convenient and versatile device for work and entertainment, one feature that stands out as missing is the built-in VPN support. A Virtual Private Network (VPN) is a crucial tool for maintaining online privacy and security, but for iPad users, the absence of a native VPN feature can pose some limitations.
Without built-in VPN support on iPads, users are forced to rely on third-party apps to secure their internet connections. While there are numerous VPN apps available on the App Store, the lack of a system-wide VPN setting means that users must individually enable the VPN on each app they wish to protect. This can be cumbersome and may result in lapses in security if users forget to activate the VPN on certain apps.
Furthermore, using third-party VPN apps may raise concerns about data privacy and potential security risks. Some free VPN services often come with hidden risks, such as selling user data to third parties or containing malware. Users must exercise caution and thoroughly research the VPN app they choose to ensure they are not compromising their online safety.
In conclusion, the absence of a native VPN feature on iPads highlights a significant gap in the device's security and privacy offerings. While third-party VPN apps can help fill this void, users must be vigilant in selecting a reputable and trustworthy VPN service to safeguard their sensitive information effectively. As technology continues to evolve, it is essential for Apple to consider integrating VPN support directly into iPads to provide users with a seamless and secure browsing experience.
iPads with no VPN support
Title: iPads without VPN Support: Understanding the Limitations and Alternatives
In today's digitally connected world, maintaining privacy and security while browsing the internet is paramount. Virtual Private Networks (VPNs) have emerged as a popular solution to safeguard personal information and ensure anonymity online. However, not all devices support VPNs, including some models of iPads.
While iPads are renowned for their sleek design, powerful performance, and user-friendly interface, some users may be disappointed to discover that certain iPad models do not offer native VPN support. This limitation can pose challenges for individuals who rely on VPNs for secure browsing, accessing geo-restricted content, or safeguarding sensitive data.
The absence of VPN support on certain iPad models can be attributed to various factors, including hardware capabilities and software restrictions imposed by Apple. Consequently, users of these devices may need to explore alternative methods to enhance their online privacy and security.
One workaround is to configure a VPN at the router level, which encrypts all internet traffic originating from the network, including devices connected to it, such as iPads. Another option is to use VPN-compatible apps that utilize the IPSec or L2TP/IPSec protocols, which can be manually configured on iPads without native VPN support.
Additionally, users can consider utilizing other privacy-enhancing features available on iPads, such as built-in encryption, app permissions management, and Safari's Intelligent Tracking Prevention. While these measures may not offer the same level of anonymity as a VPN, they can still contribute to a more secure online experience.
In conclusion, while iPads without VPN support may present limitations for users seeking enhanced privacy and security, there are alternative methods and features available to mitigate these concerns. By understanding these limitations and exploring alternative solutions, users can still enjoy a safe and secure browsing experience on their iPads.
0 notes