#subcontained
Text
BRAIN programming languages.. subconscious-mind

#motivacional#subconsideration#subcontinuous#subcontained#subcontinual#spiritual knowledge#free spirit#change my mind#strength#gratitude#mindset
1 note
·
View note
Text
I make her pussy cream
Step Sister showering gives Deepthroat Throatpie Creamthroat
Stunning japanese ts chick getting fucked
Thick ass tranny cutie bounces on fat dick like a pro
Perlalovers webcam Colombia latina deliciosa
Dolly Leigh creampied by her landlord
Wobbling ass on bbw
Sexy Mom With Big Tits Bouncing and Playing
Teen Ebony Babe Loves Backshots
Amateur wife sucking husbands cock
#sheldrake#PTAT#dark-splendid#surmise#Ayuthia#Falstaffian#retortive#phlebopexy#mold#Eudyptes#orthodome#nagatelite#subcontained#zoophobous#unexonerated#undecision#marabouts#Cartago#Laurance#XPG2
1 note
·
View note
Photo

‘Sub-containment’ zones created inside Central Delhi’s COVID-19 hotspots Image Source : PIXABAY 'Sub-containment' zones created inside Central Delhi's COVID-19 hotspots Central Delhi District Magistrate Nidhi Srivastava, told India TV, on Zila Sammelan that 'sub-containment' or 'micro-containment' zones have been created inside the containment zones in the district amid the rising number of cases in the national capital.
#Central#coronavirus lockdown#COVID-19 cases#covid-19 in delhi#covid19#created#delhi coronavirus#Delhi coronavirus cases#Delhi lockdown#Delhis#hotspots#lockdown 5.0 delhi#Subcontainment#zones
0 notes
Text
Introduction + Rules
“Look, I’ll keep this nice and simple. I got roped in by the others to do this and here we are. Whoohoo. Alright, my name is Melissa Fair, my title is Consigliere but just call me Melissa. If you got any questions just send them my way.”

She came to the manor solely for business. What kind of business? It can't be legal, that's for sure.
-----
A/N: Answers are mainly texts and I plan on filling them with art later.
--Basics--
Nationality: Asian-American
Survivor type: Decode subcontainment
When did she arrive at the manor?: September 15th (Check Not Going to Bother).
Character Day/B-day: June 30th
Height: 5'2"/157.48cm
Voice Claim: Justine's Mic
Likes: Solving things, weapons, symbolism
Dislikes: Disorder among peers, funny business.
--Skill + External Traits--
Item: Paper Codes (Can be swapped, similar to Norton's magnets but it can only be used so many times before they get destroyed... Like Melly's net.)
Skill 1: Do You Understand This?
Blue paper: When in use, it increases decoding by 2% every time the skill check hits a perfect. (So 2%/4%/6%/8%/10%, it stops at 10%.)
Red paper: When in use, increases movement speed by 5% per cipher machine's done. (Max is 10%, because 15% sounds too OP.)
Skill 2: Run in with the Law
Being used to running away from the law, vaulting speed is increased by 15% for 2/4/6(one of these numbers) seconds. (I would add something related to getting terrorshocked, but that's too OP, and Freddy already has that.)
Debuff: Walk it Off for Now
Healing speed and rescuing speed is slowed down by 15%.
--RULES--
1. Just use basic internet common sense, just down below is some reinforcements.
2. Admin's(aka me, Katniss) 18 now but still don't send anything majorly NSFW, if it's for a joke pls DM me clarifying that it's a joke. Otherwise, I may carry it too far without knowing.
3. I allow magic anons so like yes you can inject her with truth serum or turn her into a mermaid. Or give her a shock collar! Wait I'm showing the Quotev anons- :ohgodohduck: ALSO! I respond very quickly, so keep those asks coming.
4. Due to life replies may receive a long answer or a short answer. Along with that, some may receive art and some may not. All I ask is don't be a whiny-
5. I may occasionally swear(if it seems fitting) and mention topics such as drugs, blood/gore/injuries, and possible threats. I will add TW to those, Melissa's position originates from the mafia, after all.
6. NEVER, EVER, HOLD BACK YOUR MUSE! THIS GOES WITH OCs, CANON PPL, AND AUs! If they want to hurt her, hurt her, the same goes for comforting and such. It'll be a lot more fun. If it's angst-heavy, I'll probably ask if we can stop, sorry I'm emotional. I do descriptive roleplaying so expect blocks of text or a short thing.
7. If you want to do some shipping stuff please let me know. I plan on having her as multiship so relationships will never ever cross each other.
8. Have fun, everybody!
--ASK LINKS + ARCHIVE--
Emojis 1
Dynamite, eye, baby, pen, baby bottle
Starters/Journal Entries based on songs!
Spotify Playlist!
Emojis 2
Growing Heart, Liar, Bouquet, See-No-Evil, Owl,
Dear [insert]...
Anyone, past me, Santa, Jealous of
Words!
Emojis 3
Dancing, book,
Emojis 4
Gestures, Mannerisms, Good Traits
Fire Emblem Heroes
Confessions
Uncomfyness
Relationship Types!
Tarot Cards
Empress, Moon, Lovers,
Interview
24, 25?
Botanical Ask Prompts
Gladiolus, Abatina + Angelica, Apple Blossom,
Masterlist
Look at the stars,
Fruits & Veggies
Avocado, Melon, Strawberry
Bother My Inbox
A WHOLE BUNCH OF NUMBERS HERE
Valentine's Day
Lovey dovey words here.
IDV Ask Game
LORE LORE LORE
--OPEN INTERACTION LINKS--
Babooshka
I'm lost.
--PAST EVENT!--
Candlelight - Roman Chiaro this event has ended. Go in the archive or go through the event candlelight tag.
--CHIARO FAMILY--
Voices
Appearance
#idv oc#idv#idv oc ask blog#aaaaaaa#let"s do this#asktheconsigliere#identity v oc#identity v#askblog#idv askblog#melissa fair#ask blog#fill up my inbox
20 notes
·
View notes
Text
Windows Server 2022 Active Directory and Network Infrastructure
May 1, 2022
by TERNA KESTER
with no comment
Uncategorized
Edit
It is a various leveled portrayal of the multitude of articles and their properties accessible on the organization. It empowers directors to deal with the organization's assets, i.e., PCs, clients, printers, shared envelopes, and so forth, in a simple way. The coherent construction addressed by Dynamic Registry comprises of backwoods, trees, spaces, hierarchical units, and individual articles. This design is totally autonomous from the actual construction of the organization and permits heads to oversee spaces as per the hierarchical necessities without worrying about the actual organizational structure.
Following is the depiction of all intelligent parts of the Dynamic Registry structure:
Woods: A backwoods is the furthest limit of a Functioning Catalog structure. It is a gathering of various area trees that share a typical pattern however don’t frame a bordering namespace. It is made when the primary Dynamic Catalog put together PC is introduced with respect to an organization. There is no less than one backwood on an organization. The main area in woodland is known as a root space. It controls the pattern and area naming for the whole woodland. It very well may be independently taken out from the woodland. Managers can make different timberlands and afterward make trust connections between unambiguous spaces in those woods, contingent on the authoritative necessities.
Trees: A various leveled construction of numerous areas coordinated in the Dynamic Catalog timberland is alluded to as a tree. It comprises of a root space and a few kid areas. The principal space made in a tree turns into the root area. Any space added to the root area turns into its youngster, and the root space turns into its parent. The parent-youngster order go on until the terminal hub is reached. All areas in a tree share a typical outline, which is characterized at the woodland level. Contingent on the hierarchical requirements, numerous space trees can be remembered for a woodland.
Areas: A space is the fundamental hierarchical design of a Windows Server 2003 systems administration model. It legitimately puts together the assets on an organization and characterizes a security limit in Dynamic Catalog. The registry might contain more than one area, and every space follows its own security strategy and entrust associations with different areas. Practically every one of the associations having an enormous organization use area sort of systems administration model to improve network security and empower executives to deal with the whole organization proficiently.
Objects: Dynamic Index stores all organization assets as items in a progressive construction of compartments and subcontainers, consequently making them effectively available and sensible. Each item class comprises of a few ascribes. At the point when another item is made for a specific class, it consequently acquires all credits from its part class. Albeit the Windows Server 2022 Dynamic Index characterizes its default set of items, directors can alter it as per the hierarchical necessities.
Authoritative Unit (OU): It is the most un-dynamic part of the Windows Server 2022 Dynamic Catalog. It functions as a compartment into which assets of a space can be put. Its sensible construction is like an association’s utilitarian design. It permits making authoritative limits in an area by appointing separate managerial undertakings to the heads on the space. Managers can make different Authoritative Units in the organization. They can likewise make settling of OUs, and that implies that other OUs can be made inside an OU.
In a huge complex organization, the Dynamic Index administration gives a solitary mark of the executives for the chairmen by setting all the organization assets at a solitary spot. It permits chairmen to really appoint regulatory errands as well as work with quick looking of organization assets. It is effectively versatile, i.e., overseers can add an enormous number of assets to it without having extra managerial weight. It is achieved by dividing the registry information base, circulating it across different areas, and laying out trust connections, accordingly furnishing clients with advantages of decentralization, and simultaneously, keeping up with the unified organization.
The actual organization framework of Dynamic Catalog is extremely straightforward when contrasted with its sensible construction. The actual parts are space regulators and locales.
Space Regulator: A Windows 2022 server on which Dynamic Registry administrations are introduced and run is known as an area regulator. An area regulator locally settles inquiries for data about objects in its space. An area can have numerous space regulators. Every area regulator in space follows the multi-master model by having a total reproduction of the space’s registry segment. In this model, each area regulator holds an expert duplicate of its catalog segment. Executives can utilize any of the space regulators to alter the Dynamic Registry information base. The progressions performed by the chairmen are naturally duplicated to other space regulators in the area.
In any case, there are a few tasks that don’t follow the Multimaster model. Dynamic Index handles these activities and allocates them to a solitary area regulator to be achieved. Such an area regulator is alluded to as activities ace. The activities ace plays out a few jobs, which can be backwoods wide as well as space wide.
Woods wide jobs: There are two sorts of backwoods wide jobs:
Blueprint Expert and Space Naming Expert. The Pattern Expert is liable for keeping up with the composition and disseminating it to the whole woods. The Space Naming Expert is answerable for keeping up with the honesty of the timberland by recording increments of areas to and erasures of areas from the woods. Whenever new spaces are to be added to a woods, the Area It is questioned to Name Expert job. Without this job, new spaces can’t be added.
Space-wide jobs: There are three sorts of area-wide jobs: Free Expert, PDC Emulator, and Framework Expert.
Free Expert: The Freed Expert is one of the tasks ace jobs that exist in every space in a woodland. It controls the arrangement number for the space regulators inside an area. It gives an exceptional arrangement of Frees to every space regulator in an area. At the point when an area regulator makes another article, the item is relegated a special security ID comprising of a mix of a space SID and a Freed. The space SID is a steady ID, though the Freed is appointed to each object by the area regulator. The space regulator gets the Frees from the Freed Expert. At the point when the space regulator has utilized all the Frees given by the Freed Expert, it demands the Freed Expert to give more Frees for making extra articles inside the area. Whenever a space regulator debilitates its pool of Frees, and the Freed Expert is inaccessible, any new item in the area can’t be made.
PDC Emulator: The PDC emulator is one of the five activities ace jobs in Dynamic Registry. It is utilized in a space containing non-Dynamic Registry PCs. It processes the secret word changes from the two clients and PCs, reproduces those updates to reinforcement space regulators, and runs the Area Expert program. At the point when an area client demands a space regulator for confirmation, and the area regulator can’t verify the client because of terrible secret key, the solicitation is sent to the PDC emulator. The PDC emulator then confirms the secret word, and in the event that it observes the refreshed passage for the mentioned secret phrase, it validates the solicitation.
Framework Expert: The Foundation Expert job is one of the Activities Expert jobs in Dynamic Registry. Its capacities at the space level and exist in every area in the timberland. It keeps up with all between space object references by refreshing references from the articles in its area to the items in different areas. It plays a vital job in various space climates. It contrasts its information and that of a Worldwide List, which generally has exceptional data about the objects, everything being equal. Whenever the Framework Expert observes information that is out of date, it demands the worldwide inventory for its refreshed form. Assuming the refreshed information is accessible in the worldwide index, the Foundation Expert concentrates and duplicates the refreshed information to the wide range of various space regulators in the area.
Area regulators can likewise be doled out the job of a Worldwide Index server. A Worldwide Inventory is an extraordinary Dynamic Catalog information base that stores a full copy of the index for its host space and the incomplete imitation of the registries of different areas in a woods. It is made of course on the underlying area regulator in the woodland. It fills the accompanying essential roles in regards to logon abilities and inquiries inside Dynamic Registry:
It empowers network logon by giving general gathering participation data to a space regulator when a logon demand is started.
It empowers observing index data pretty much every one of the spaces in a Functioning Registry timberland.
A Worldwide Inventory is expected to sign on to an organization inside a multidomain climate. By giving general gathering of enrollment data, it significantly further develops the reaction time for inquiries. In its nonappearance, a client will be permitted to sign on just to his neighborhood space assuming his client account is outside to the nearby area.
Site: A site is a gathering of area regulators that exist on various IP subnets and are associated by means of a quick and dependable organization association. An organization might contain numerous destinations associated by a WAN connection. Destinations are utilized to control replication traffic, which might happen inside a site or between locales. Replication inside a site is alluded to as intrasite replication, and that between locales is alluded to as intersite replication. Since all area regulators inside a site are by and large associated by a quick LAN association, the intrasite replication is generally in uncompressed form. Any changes made in the domain are quickly replicated to the other domain controllers. Since sites are connected to each other via a WAN connection, the intersite replication always occurs in compressed form. Therefore, it is slower than intrasite replication.
0 notes
Text
How do I require system permission?
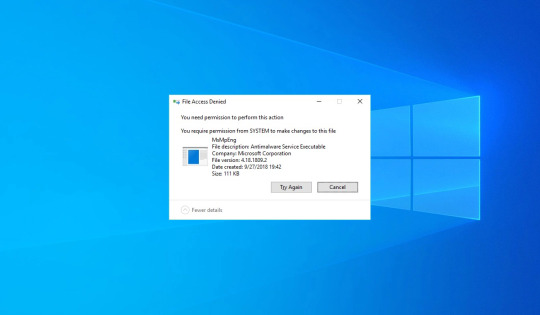
You require permission from SYSTEM to make changes to this folder. Solution: Delete all the usernames or groups, including SYSTEM from the security tab. Change owner as your computer user account. Also, replace owner on subcontainers and objects.
https://blogs.systweak.com/fixing-you-need-permission-to-perform-this-action-in-windows/
0 notes
Text
How to Open Encrypted Files on Windows 10?
Windows provides an encrypted facility to protect the data from malicious attacks through built-in encryption utility. It protects the files from being accessed by unknown persons or online attackers to safeguard the details and information stored into the file. You can’t modify, read or open it without an associated password.

This encrypted data requires the encryption key, and also you have signed in with admin controls. It is made to protect private and sensitive information of the clients and offices.
Sometimes users forget the encryption unlocking key or passcode to open the respective file. If you are one of them who want to know how to open encrypted files on your Windows device, then we will help you through this blog. There are several ways to encrypt a protected file to unpack its contents to fetch the information.
You have to be very careful while using these methods as these are very sensitive, any skipping of the details or points might result in the system crash.
Opening Encrypted Files by Using the Dedicated Tool
There are a number of applications used to decrypt a protected file or data. First of all, you have ensured that the particular file is passcode protected or not. You may use the WinZip application to open the encrypted file as it is widely accepted to decrypt data. This program enables the users to zip the file with certified 256 or 128 bit in AES encryption, and thus it keeps the file secure from unknown attackers or users. This program is also used to create read-only PDFs and adding watermarks to identify and detect the copying process. In order to get access to the contents of the protected WinZip file, you must have the passcode as it alone can’t help you in the recovery of lost zip file passwords.
In case you are using a particular 256 bit of AES protection method, then there is no chance of launching the file without knowing the associated passcode. If you are using a 128 bit or weak Zip 2.0 encryption method, you may try using the passcode recovery program that is available online. If you wish to avoid these circumstances, it is recommended to use passcode manager every time to fetch and easy access to all the passwords and respective codes.
Opening Encrypted Files via Certificate Manager
First and foremost, sign in to the user account, which encrypts the file that you want to fetch contents.
Go to the navigation bar and then enter “certmgr.msc” followed by the Enter key. It helps you to launch the Certificate Manager.
Now, hit and launch the category “Personal” located into the left-hand side section.
After that, press the Certificates option.
Next, navigate to the section “Issues To” and then choose the relevant certificate that is associated with your particular account name.
Launch the menu tab “Action.”
Now, navigate to the All Tasks panel.
Choose the option “Export” and then pursue the onscreen prompts located into the Export Wizard.
Then, hit the option “Yes, export the private key” and then tap the Personal Information section once it appears via prompt box.
You will be asked to enter a passcode for your certificate and then hit the Finish tab.
Now, you have to transfer the certificate file to the system on which you wish to launch the file.
After that, launch the Certificate Manager on your system.
Choose the option “Personal.”
After that, expand the menu “Actions.”
Navigate to the section “All Tasks” followed by tapping the Import option.
Pursue all the available guidelines on the Import Wizard section and then choose the certificate file that you have moved earlier. Then, input your secured passkey and then check the relevant details.
After that, mark the option “Mark this key as an exportable box.”
Choose the Personal option as your location for placing the certificate.
Then, hit the Finish tab there.
Now, perform a double tap on the encrypted file to launch it. The respective certificate that you have transferred will provide access to your file.
Converting and Opening the File
In case you have applied the program “EasyCrypto” for encrypting your file, they can’t transform it to any other format as the tool doesn’t provide the feature to convert your files.
In case you have any other files that you wish to convert and the same is located inside the “.encrypted” file, then it is recommended to decrypt it and then apply a free file converter to modify the settings to make it open.
Taking Ownership of Your File and Owner
In order to take ownership of your file, follow these instructions:
Firstly, launch the File Explorer and then search for the file or folder of which you wish to take ownership.
Then, apply right click on the folder or file and hit the Properties tab.
Now, press the Security option.
Next, tap on Advanced and click the Owner option.
After that, hit the Change button and perform any one of the available tasks:
In order to modify the owner to a group or a particular user which is not into the list, then hit the option “Other users and groups.” Then, go to the section “Enter the objects name to select,” you have to enter the user or group’s name followed by the OK button.
If you desire to change the owner to a group or a particular user that is listed, then locate the field “Change owner to” and then tap on the new owner.
Note: you may modify the owner’s name of the entire objects and sub-containers located within the tree by choosing the mark-box option for replacing the owner on subcontainers and objects.
However, it’s on your wish as it is the optional one.
The admin may take ownership of any available file located on the computer. If you wish to assign ownership, then you need to access permissions through navigating the section of “User Access control.”
⮚ If you have the rights of restoring files and directories, then you may double tap on the option “Other users and groups” and then select any user or group for assigning ownership to the respective user or group.
Conclusion
MS Windows provides a unique feature to safeguard several data and files with the help of a built-in tool for file encryption. It’s a great tool that provides enhanced security to your device and data that restricts unknown attackers and users to get access to your data and folder as it is the encrypted format and these files can only be accessed with the help of secured passcode.
In case you have forgotten your encrypted file passkey to launch on your device or want to access the file without having passcode. There are handfuls of methods to use and reach the section where you can access the information of your file. These methods include using certificate managers, taking ownership of the file or data with admin rights, granting access to encrypted files, etc.
Hey there, I’m Oliviya . I’m a web developer living in USA. I am a fan of photography, technology, and design. I’m also interested in arts and web development. View Our Blog:- Marthip
Source: https://marthip.com/blog/how-to-open-encrypted-files-on-windows-10/
0 notes
Link
In spite of a large number of users Windows 10 attracts because of its amazing GUI and prominent features there’s no doubt when it comes to its popularity it is not its best version. This version comes with different kinds of flaws, like the 0x80070032 error, which is worth noting by Microsoft. As per claims by Microsoft, Windows 10 will bring a revolution in the OS world. However, most users are unable to rely on this it is because of the UX issues with Windows 10 in a way or others.
This error code is triggered when you try to set an external hard disk as your backup location. The issue can also occur when you're trying to install a major update to your Windows 10. The update relies on files that can be accessed from a direct download from Microsoft or an automatic update through the Windows Update. The error code 0x80070032 arises when you are trying to activate the Automatic File Backups setting. This option is in the settings menu under the backup option. When you restart your PC to accept the changes made, the update fails to activate, thus the error code 0x80070032 appears.
The servers of Microsoft are referred to be the main reason for initiating this issue with Mail application. Here, the accounts of users do not synchronize with servers properly.
Method #1 Remove the NGC Folder’s Content to Eliminate 0x80070032 error
If you are unable to log into Windows 10 using your PIN, try signing into your account and remove the NGC folder’s content. Before that, you need to take the folder’s ownership. To do this, go through the steps below
Firstly, you need to log into Windows 10 with your password.
Tap Windows + X keys and choose ‘File Explorer.’
Go to C:\Windows\ServiceProfiles\LocalService\AppData\Local\Microsoft path.
Next, right-tap on the folder NGC and choose ‘Properties.’
Navigate to the tab ‘Security‘ and select ‘Advanced‘ and then look for the section ‘Owner.’
Tap on the link ‘Change‘ and type in the user or administrator’s name and object name.
Choose ‘Check Names‘ and hit ‘O.K.’
Check against the option ‘Replace Owner on subcontainers and Objects,’ and after this, select ‘Apply‘ and press O.K. for saving the changes.
Next, see if you could access this NGC folder. Mark all the stored files in the folder if you can and remove those files.
Tap Windows + I keys for opening Settings.
Now, open the ‘Account Settings‘ tab and choose ‘Sign-in Options‘.
Select ‘Add a PIN‘ for setting a PIN by following the on-screen instructions.
Method #2 Resolve the 0x80070032 Error with ‘I Forgot My PIN.’
Another method to eliminate the error 0x80070032 is by choosing the option ‘I forgot my PIN.’ For performing this action, you have to follow the following procedure.
Tap Windows + I keys for opening Settings on your system.
Select the section ‘Accounts‘ and then choose ‘Sign-in options.’
Find the ‘Windows Hello PIN‘ tab and tap on ‘I forgot my PIN.’
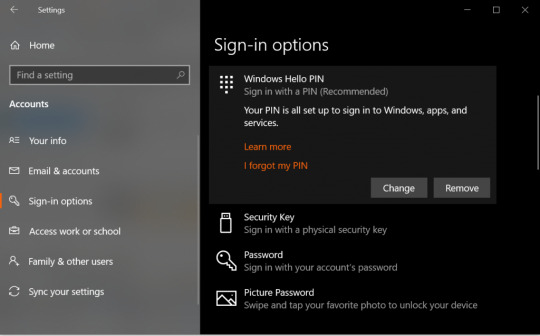
Tap on ‘Continue‘ for confirming your action.
Now, you need to type in a new PIN. Once you have entered the passcode, press O.K.
Here, you could be asked to type your Microsoft account passcode. In that case, change the account type from Microsoft to Local and try all the steps once again.
Method #3 Resolve the Error 0x80070032 Through PIN Recreation
This is another effective way to get rid of the error code 0x80070032. It is performed through recreating the PIN.
Tap Windows + I keys for opening Settings.
Go to the section ‘Accounts‘ and then ‘Sign-in Options.’
Navigate to the section ‘PIN‘ and choose ‘Remove.’
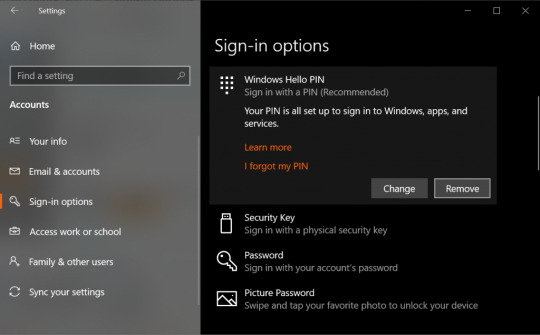
Tap on ‘Remove‘ for confirming your action.
Type in your account’s password and hit O.K.
Once done, tap on ‘Add‘ and enter a new PIN.
Tap O.K. for saving it and see if the issue still persists or not;
Note: If you are a Dell user and facing the error 0x80070032 on your system, try removing the security tools from Dell Data Protection. Also, remove their leftovers or temporary files through Windows Registry or use Reimage.
Solutions for Fixing the Error 0x80070032 on Mail
We have listed various fixes that can assist you in resolving the issue with Mail app on Windows 10 systems.
Method #1 Switch to Microsoft from Local Account
This method is great for resolving the error code problem on Windows. Follow the instructions to get rid of this annoying Error.
Firstly, you have to switch from Microsoft to a local account. To do so, visit ‘Settings‘ with the help of Cortana. Within the ‘Settings‘ tab, look for ‘Accounts‘ for opening the settings associated with the user accounts.
Next, you have to choose ‘Email & Accounts,’ which you will find under the account’s left-pane window. After that, click on Add an account.
Type in the local account’s details, such as username and passcode. Next, tap on the tab ‘Next‘ again. In the next tab, you will come across a button branded as ‘Sign out and finish.’ Select this button for signing out of the Microsoft account of yours.
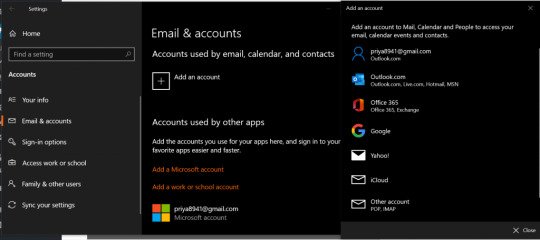
Next, repeat the steps. Visit Settings and choose ‘Accounts.’ Then, select ‘Sign in with a Microsoft account instead.’ Type in the local account’s password, along with username and password of the Microsoft account for signing in again. See if you could check Mail by syncing the account.
Method 2: Reinstall Mail
If the first method didn't solve the error code problem, try this one out. Here, you have to reinstall Mail for fixing the syncing problem. To perform this action, follow some simple steps listed below.
Visit PowerShell from the search results once you have searched for it. Right-tap on this tab and choose ‘Run as Administrator.’ Please note that it is significant to open this tab as an administrator, or else you will face an error.
Within the PowerShell tab, type the command.
Get-appxprovisionedpackage – online | where-object {$ .packagename – like “*windowscommunicationsapps*”} |remove – appxprovisionedpackage – online
Once you have executed this command, close PowerShell and install the Mail application again from Windows Store. After you have installed this application, run the same, and check if the error 0x80070032 has been resolved or not.
[su_box title="More Like This"]
How to Fix 0x0000007f Blue Screen Error in Windows 10
How to Fix 0xC004f074 Error in Windows 10
How to Fix 0xC1900101 Error in Windows 10
How to Fix 0x8007025D Error In Windows 10
How to Fix 0x8000FFFF Error in Windows 10 using Simple Methods
[/su_box]
via TechLatest
0 notes
Text
How to Fix “the Application Definite Permission Settings That Does Not Allow Local Activation” Error
The Event viewer can show multiple errors and “The application-definite permission settings do not permit Activation for COM Server app” is one of them. The error appears with Event ID 10016, and it mostly displays after system upgrades; however, it does not affect the working of users in Windows 10. If you face the same trouble and want to fix it, then this blog might be helpful for you. Read the blog and follow the instructions to solve the issue.
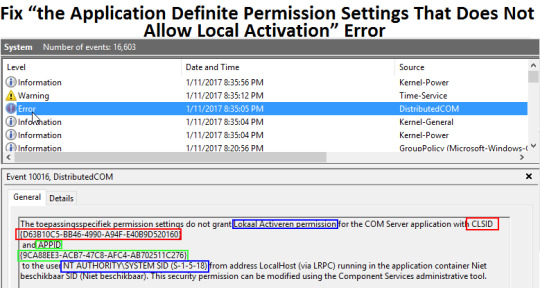
Application Definite Permission Settings Does Not Allow Activation
Here is the list to fix the error on Windows 10:
Discover and then confirm CLSID and APPID
Modify possession of CLSID button of Registry Editor
Change the security consent of Component Services
Users have to discover CLSID or APPID; however, they might look dissimilar on the PC, so it is important to identify them. Otherwise, users can’t get rid of the Viewer errors. Finally, locate the component which is creating the problem.
If you want to change the security consent from Component Services, then you can follow the provided steps:
Go to Registry Editor on the PC by clicking Win + R.
Input regedit.
Click the Enter key.
Type the following:
HKEY_Classes_Root\CLSID\<Enter-your-CLSID>
Input to replace Enter-your-ClSID with new CLSID.
Locate the APPID on the right side.
Ensure that the APPID and old APPID are similar.
Right-click on CLSID on left side.
Choose the Permissions button.
Tap on Advanced.
The Trusted Installer owns the key, but you have to modify owner to Administrator. If you want to modify owner to Administrator, then abide by the given steps:
Tap on edit option in the Advanced Security tab.
Select Administrator.
Choose the Check Names option.
Press the OK option.
Choose Change owner on subcontainers or objects tickbox.
Click on Administrators from user name or group list.
Tick the Full/Allow control tick box.
Save the settings.
Check Default Data name.
Type the given path in Registry Editor:
HKEY_Local_Machine\Software\Classes\AppID\your-APPID
Launch the Component Services by searching it on the box and tap the result.
Type the following after launching component services:
Component Services > Computer > My Computer > DCOM Config > Immersive Shell
Then locate Default – Data name of Registry editor.
Right-click on component service button .
Choose Properties.
Locate the APPID or the application ID that you may confirm again.
Open the Security option.
Then you will get the three labels comprising Activation Permissions and Launch.
Tap on corresponding Edit option.
If the users get the warning message, then they must tap the Cancel option and proceed.
When inserted, choose one option every time then provide local activation as well as Local launch permissions.
Tap on Save to store changes so that you won’t have to face the same problem again in Event Viewer.
Aron smith is an inventive person who has been doing intensive research in particular topics and writing blogs and articles on lexmark printer support and many other related topics. He is a very knowledgeable person with lots of experience.
Source:https://magicdirectory.uk.com/blog/how-to-fix-the-application-definite-permission-settings-that-does-not-allow-local-activation-error/
#How to Fix#Application Definite Permission Settings#Not Allow Local Activation” Error#Activation Error#lexmark printer support
0 notes
Text
Become A Professional Java Developer From Scratch

Master The Worlds Most Popular Programming Language And Become A Pro Developer From Scratch. Become A Professional Java Developer From Scratch
What you’ll learn:
103 LecturesUnderstand variables and perform operations with themCreate Arrays to store dataCreate multidimensional arrays to store dataGet the input from the userCreate and manipulate files on the systemUse text input and output to store dataUse binary input and output to store dataUnderstand Object Orient Programming principals in depthUse abstract classes and interfaces to model your classesHandle exceptionsUse Java GUI API to create user interfaces for your Java programsUse the collections framework to store your dataUse multithreading to make your program execute multiple tasks at the same timeConnect you program to a database, store and fetch dataUse Java servlets to create dynamic web contentUse Java server pages to create dynamic web contentUse Java Server Faces to create dynamic web content
Requirements:
Eclipse and Netbeans(We will download both in the first video)
Become A Professional Java Developer From Scratch Description:
Over 4400 Enrolled Students Are Already Learning Java, Enroll Now And Start Learning Today Join me on this fantastic journey where we are going to explore Java from ground up. If you never coded before and want to learn Java this is a perfect course for you. We are going to start from basics so that you will feel comfortable writing your own code. This course assumes no previous experience and takes you from beginner concepts like variables, functions and classes and then goes into more detail while we explore advanced Java concepts. We are also going to learn Object Oriented Programming principles which will help you learn any other programming language after you have mastered Java in this course!! I have also added challenging task for you to complete and test your knowledge which is going to bring you from a complete beginner to an experienced developer comfortable writing any program in Java. You will also benefit from my quick response (I check Udemy forums every day if some student has encountered a problem) and you will also get assistance from the other students taking the course.
If you are a complete beginner join now and master the worlds most popular programming language, on the other hand if you are a developer already, then it will not hurt you to add one more powerful programming language at your disposal!! Topics Covered Variables Loops Conditionals Classes Objects Methods Arrays Multidimensional Arrays Inheritance Polymorphism Abstract Classes Interfaces Handling Exceptions Creating Files Text Input / Output Binary Input / Output Java Graphical User Interface Collections Multithreading Java Database Programming Java Servlets Java Server Pages Java Server Faces
Enroll Now You Will Not Be Disappointed!!
Who this course is for: Complete Beginners Students with programming experience who want to learn Java
Who is the target audience?
Complete BeginnersStudents with programming experience who want to learn Java
Course content of Become A Professional Java Developer From Scratch:
Total Lecture:81
How To Study This Course
Downloading and setting up our environments
Variables
Numeric operations and String concatenation
Augmented Assignment Operators and Increment and Decrement Operators
Getting Input from the user
Displaying Current time
Assignment
The if statement
Nested If-else statements
Switch statement
Logical Operators
Using if-else statement to controll the input from the user
Conditional Expressions
Loops
Nested Loops
Using loops to controll the user input
Assignment
Classes
Constructors with parameters
Methods
Static, final and scope of a variable
Visibility Modifiers
Data encapsulation
Passing objects to methods
Assignment
Introducing arrays
Processing arrays
For each loop
Arrays and methods
The Arrays class
Multidimensional arrays
Assignment
Inheritance
Super, overriding and overloading
The Object class
Primitive and Reference variables
The equals method
The protected modifier and preventing Extending and Overriding
Assignment
Abstract Classes
Interfaces
Assignment
Exceptions
Getting information from exceptions and throwing our own exceptions
The finally clause
The File class
Writing and reading data
Reading data from the web
Assignment
FileInputStream and FileOutputStream
DataInputStream and DataOutputStream
BufferedInputStream and BufferedOutputStream
ObjectInputStream and ObjectOutputStream
RandomAccessFile class
Assignment
JFrame
Adding a button to our JFrame
Layout Managers
Using JPanel as a subcontainer
Helper Classes
Image Icons
Other components
Listeners and Inner classes
Alternative ways to create listeners
Mouse Listeners and Mouse Adapters
The Timer class
Simple Login App
More GUI Components
Processing JComboBox and JList
JScrollBar and JSlider
CardLayout, BoxLayout and Box
JTabbedPane
Menus
Dialogs
JColorChooser and JFileChooser
Assignment
ArrayList and LinkedList
Stacks, Vectors, Sets and Maps
Note About Collections
6 more sections
Become A Professional Java Developer From Scratch course
Read the full article
#JavaDeveloper#ProgrammingLanguage#scratch#udemy free courses#udemy free#free courses#udemy free courses download
0 notes
Text
How to Fix Adobe Error Code 16 on Windows 10
Adobe error 16 can restrict you from using Adobe tools and programs such as Photoshop, InDesign, etc. This error can leave you disappointed and frustrated. If you are encountering Adobe error code 16 on your device, then you have landed in the right place. This article is dedicated to troubleshooting error 16 on Adobe programs. Most of the Windows 10 users are getting this error while trying to runthe Adobe programs.
Source: How to Fix Adobe Error Code 16 on Windows 10
Solving Adobe Error 16 on Windows 10
Method 1: Running Creative Cloud apps with Administrator Permissions
The error can be a result of a lack of the required permission and system privileges. To solve the error, you should get all the required permissions for Adobe program. To do this, you can use the Creative Cloud apps with Administrator privileges. See the instructions presented below to fix the error:
Go to the Creative Cloud app and then select the Properties option.
After that, head to Compatibility in the Properties of the Creative Cloud app.
Check the box saying “Run this program as an administrator” and then press the Apply button located at the bottom.
Once that is done, hit the OK button to close the Properties window.
From now on, your Creative Cloud app will open with the Administrator permissions every time. By doing so, the error code might disappear.
Method 2: Restoring the Permissions to Licensing Folders
Below are some steps that will help you in setting up the permissions for the Adobe SLStore and PCD folders on Windows 10:
Head to the File Explorer on your Windows 10 PC.
Press the View option located in the upper menu.
Tap the Options button located in the top-right.
Uncheck the box saying Use Sharing Wizard (Recommended). You will find this option under Advanced Settings.
Now check the box saying, “Show hidden files, folders, and drives.
Hit Ok.
Now you need to follow the below instructions for Adobe PCD and SLStore. In order to follow this tutorial, you first need to locate the folders on your computer. The locations for both folders are mentioned here:
The SLStore folder is located in the ProgramData folder.
The Adobe PCD is located in the Windows 32 bit folder.
Now apply the below instructions on each folder:
Get to the first folder mentioned above.
Now right-click on the folder and then press on the Properties option.
Once the Properties window triggers, head to the Security tab.
Now set up the permission as mentioned here:
For the Adobe PCD folder
Administrator: Full Control
System: Full Control
For the SLStore folder
Administrator: select Full Control Power Users
System: Choose Full Control
Users: set as Read and Special
Switch the ownership by following the below-mentioned steps:
Open the Properties for each folder.
Press the Advanced button.
Tap the Owner section and then press the Change link.
Provide the required username and then tap the Check Names option.
Hit the OK button.
Click on the “Replace Owner on subcontainers and Objects” option.
Check the box saying, “Replace all child object permission entries.”
Hit the Apply button followed by OK.
This will surely fix the issue of error code 16 in Adobe application.
Lucia Mandela is a Microsoft Office expert and has been working in the technical industry since 2002. As a technical expert, Lucia has written technical blogs, manuals, white papers, and reviews for many websites such as office.com/setup.
0 notes
Text
Windows Web Server 2003 Energetic Directory and also Network Facilities
It is a hierarchical representation of all the things as well as their features available on the network. It allows administrators to handle the network sources, i.e., computers, customers, printers, shared folders, etc., in a simple means. The rational framework stood for by Active Directory contains forests, trees, domain names, business systems, and private objects. This framework is totally independent from the physical framework of the network, and allows administrators to manage domain names according to the organizational demands without bothering regarding the physical network structure.
Following is the summary of all rational components of the Active Directory structure:
Woodland: A forest is the outer boundary of an Active Directory framework. It is a team of several domain trees that share a typical schema however do not develop a contiguous namespace. It is produced when the first Active Directory-based computer system is set up on a network. There goes to the very least one woodland on a network. The very first domain in a forest is called a root domain. click here regulates the schema as well as domain calling for the whole forest. It could be independently gotten rid of from the woodland. Administrators could create several woodlands then create count on partnerships in between particular domains in those woodlands, relying on the organizational demands.
It is composed of a root domain as well as a number of youngster domain names. The very first domain produced in a tree becomes the origin domain. Any type of domain added to the origin domain becomes its child, and also the root domain becomes its moms and dad.
Domain names: A domain is the basic business framework of a Windows Server 2003 networking version. The directory site may include more compared to one domain, as well as each domain follows its own safety policy and also depend on relationships with various other domain names.
Objects: Active Directory shops all network sources in the type of items in an ordered framework of containers as well as subcontainers, therefore making them conveniently available and manageable. The Windows Server 2003 Active Directory specifies its default set of items, administrators can change it according to the organizational requirements.
Organizational Unit (OU): It is the least abstract part of the Windows Server 2003 Active Directory. It functions as a container right into which sources of a domain can be positioned. Its sensible structure resembles an organization's functional framework. It enables creating administrative limits in a domain by entrusting different management jobs to the administrators on the domain. Administrators could create numerous Organizational Units in the network. They could likewise produce nesting of OUs, which implies that OUs can be produced within an OU.
In a big complex network, the Active Directory solution supplies a single factor of management for the administrators by positioning all the network resources at a single place. It is accomplished by separating the directory site data source, dispersing it throughout other domain names, and developing depend on partnerships, thus offering users with advantages of decentralization, and also at the exact same time, keeping the centralized management.
The physical network framework of Active Directory is far also easy as compared to its logical structure. The physical parts are domain controllers and sites.
A domain controller locally fixes questions for information concerning objects in its domain. Each domain controller in a domain adheres to the multimaster version by having a total replica of the domain's directory partition. The modifications done by the managers are automatically duplicated to other domain controllers in the domain.
T here are some operations that do not comply with the multimaster design. Energetic Directory manages these operations and also assigns them to a single domain controller to be accomplished. Such domain name generator is described as procedures master. The procedures grasp performs a number of duties, which could be forest-wide in addition to domain-wide.
Forest-wide roles: There are 2 kinds of forest-wide roles:
The Domain Naming Master is liable for keeping the integrity of the forest by taping additions of domains to and deletions of domain names from the forest. When new domain names are to be added to a woodland, the Domain Naming Master function is queried.
Domain-wide functions: There are 3 kinds of domain-wide functions: RID Master, PDC Emulator, and Infrastructure Master.
FREE Master: The RID Master is among the procedures grasp functions that exist in each domain in a forest. It controls the sequence number for the domain controllers within a domain. It provides an one-of-a-kind series of RIDs per domain controller in a domain. When a domain controller creates a new things, the item is designated a special safety and security ID containing a mix of a domain SID and also a RID. The domain SID is a constant ID, whereas the RID is assigned to every object by the domain controller. The domain controller gets the RIDs from the RID Master. When the domain controller has utilized all the RIDs supplied by the RID Master, it demands the RID Master to issue even more RIDs for developing additional objects within the domain. When a domain controller exhausts its pool of RIDs, and also the RID Master is inaccessible, any type of brand-new object in the domain could not be created.
check here : The PDC emulator is one of the five operations master functions in Active Directory. It is made use of in a domain having non-Active Directory computer systems. It refines the password modifications from both customers as well as computer systems, replicates those updates to backup domain controllers, as well as runs the Domain Master internet browser. When a domain individual demands a domain controller for authentication, and the domain controller is incapable to verify the customer as a result of poor password, the request is forwarded to the PDC emulator. The PDC emulator then verifies the password, and also if it finds the updated access for the asked for password, it authenticates the demand.
Framework Master: The Infrastructure Master function is among the Operations Master roles in Active Directory. It functions at the domain degree as well as exists in each domain in the woodland. It maintains all inter-domain things references by updating referrals from the items in its domain to the items in other domains. It carries out an essential duty in a multiple domain setting. It compares its information keeping that of a Global Catalog, which constantly has up-to-date details regarding the objects of all domains. When the Infrastructure Master discovers data that is obsolete, it requests the worldwide catalog for its updated version. If the upgraded data is offered in the global magazine, the Infrastructure Master extracts and replicates the upgraded information to all the other domain controllers in the domain.
Domain controllers could additionally be appointed the duty of a Global Catalog web server. A Global Catalog is an unique Active Directory database that saves a full replica of the directory site for its host domain as well as the partial reproduction of the directory sites of other domain names in a forest. It is developed by default on the initial domain controller in the woodland. It does the following key features regarding logon capabilities as well as questions within Active Directory:
It allows network logon by offering universal group membership information to a domain controller when a logon request is started.
It enables finding directory info about all the domains in an Active Directory woodland.
A Global Catalog is needed to go to to a network within a multidomain environment. By providing global group membership details, it substantially improves the action time for queries. In its lack, a customer will certainly be permitted to log on only to his local domain if his customer account is exterior to the local domain.
more info : A website is a group of domain controllers that exist on different IP subnets as well as are connected through a quick and dependable network link. A network may include multiple websites linked by a WAN web link. Websites are used to control replication web traffic, which could take place within a website or between sites. Duplication within a website is described as intrasite replication, which between sites is described as intersite replication. Because all domain controllers within a site are typically connected by a rapid LAN connection, the intrasite replication is always in uncompressed kind. Any kind of changes made in the domain are quickly replicated to the other domain controllers. Since websites are connected per other by means of a WAN connection, the intersite duplication always occurs in compressed form. Therefore, it is slower than the intrasite duplication.
Any kind of domain included to the origin domain becomes its child, as well as the root domain becomes its parent. The directory site may include even more compared to one domain, and also each domain follows its very own security policy and also trust fund partnerships with other domain names. Each domain controller in a domain follows the multimaster version by having a total replica of the domain's directory partition. The Domain Naming Master is accountable for maintaining the integrity of the woodland by tape-recording additions of domain names to and also deletions of domains from the forest. When a domain customer requests a domain controller for verification, and the domain controller is unable to authenticate the user due to poor password, the demand is forwarded to the PDC emulator.
0 notes
Text
رفع مشکل عدم دسترسی به بعضی از پوشه ها در ویندوز ۱۰
https://www.dakeit.com/?p=4651
در بعضی مواقع شما ممکن است در ویندوز ۱۰ وقتی می خواهید وارد پوشه ای شوید با پیام “You have been denied permission to access this folder. To gain access to this folder you will need to use the security tab” مواجه شوید به معنی اینکه شما اجازه دسترسی به این پوشه را ندارید و برای به دست آوردن اجازه این دسترسی باید از زبانه security استفاده کنید .
پیام مذکور که مربوط به عدم دسترسی به پوشه می باشد هنگامی نمایش داده می شود که شما در حال تلاش برای دسترسی به یک پوشه ی سیستمی حفاظت شده در ویندوز ۱۰ یا نسخه های قبلی ویندوز می باشید . به عنوان مثال شما هنگامی که می خواهید به پوشه WindowsApps دسترسی داشته باشید با این پیام خطا روبرو می شوید .
برای دسترسی به پوشه مورد نظر ، شما نیاز دارید که تغییراتی را در اجازه دسترسی به پوشه بدهید و این کار به راحتی قابل انجام است . با این حال ، شما باید اجازه دسترسی را از طریق ادمین (admin) بدهید ،
یا شما باید رمز عبور ادمین در ویندوز ۱۰ را برای زمانی که تغییراتی در اجازه دسترسی به پوشه را می دهید در اختیار داشته باشید .
بنابراین ، در این راهنمایی ، شما مشاهده می کنید که چگونه از دست پیام “You have been denied permission to access this folder. To gain access to this folder you will need to use the security tab” که مربوط به عدم دسترسی به پوشه مورد نظرتان است خلاص شوید و به راحتی به هر پوشه ای در ویندوز ۱۰ دسترسی داشته باشید .
دو روش برای رفع مشکل عدم اجازه برای دسترسی به پوشه ای که دسترسی به آن وجود ندارد در زیر آمده است .
روش اول
مالکیت فایل/پوشه را در اختیار بگیرید
قدم اول : File Explorer را باز کنید . به محلی که پوشه مورد نظرتان در آن وجود دارد و شما می خواهید مالکیت آن پوشه را بر عهده بگیرید بروید . قدم دوم : بر روی پوشه مذکور راست کلیک کرده و بر روی گزینه Properties کلیک کنید .
قدم سوم : به زبانه Security بروید . بر روی دکمه Advanced کلیک کنید تا پنجره Advanced Security Settings این پوشه باز شود .
قدم چهارم : حال شما باید گزینه Change را کنار قسمت owner ببینید . بر روی Change کلیک کنید تا پنجره Select this object type باز شود .
قدم پنجم : در اینجا ، در قسمت Enter the object name to select ، کلمه Administrators را تایپ کنید ، و سپس بر روی دکمه Check Names کلیک کنید .
در نهایت بر روی دکمه OK کلیک کنید تا پنجره Advanced Security Settings را ببینید .
قدم ششم : در آخر ، تیک گزینه Replace owner on subcontainers and objects را بزنید.
بر روی دکمه Apply کلیک کنید تا مالکیت پوشه مورد نظرتان را در اختیار بگیرید .
به همین سادگی .
حال شما می توانید پوشه مورد نظر را بدون اینکه با پیام خطایی روبرو شوید باز کنید .
روش دوم
استفاده از نرم افزار TakeOwnershipEx برای در دست گرفتن مالکیت پوشه ها.
تعداد کمی نرم افزار وجود دارد که برای فعال سازی مالکیت فایل ها و پوشه ها در ویندوز مورد استفاده قرار می گیرد .
یکی از آنها نرم افزار TakeOwnershipEx می باشد .
برای به دست گرفتن مالکیت پوشه/فایل ، کافی است تا برنامه مذکور را اجرا کرده.
بر روی Take Ownership کلیک کنید و پوشه/فایل مورد نظرتان را که می خواهید مالکیت آن را بر عهده بگیرید انتخاب کنید.
شما همچنین می توانید بر روی پوشه راست کلیک کرده و سپس بر روی گزینه ownership/restore ownership کلیک کنید تا مالکیت یک پوشه را بر عهده گرفته و یا آن را از مالکیت خود خارج کنید .
0 notes