#csrf
Text
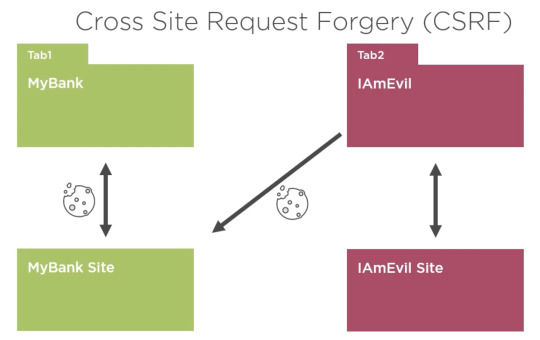
This graphic (in an online Angular course) amuses me. Of course, I know about CSRF, I've been a web developer as long as there have been web developers.
5 notes
·
View notes
Text
Un Web Application Firewall français
Avec la multiplication des attaques sur les sites web, et la découverte presque quotidienne de nouvelles failles, le suivi devient difficile.
C'est pour cela que nous avons créé ProtectMy.site !
C'est un Web Application Firewall. Il se place entre votre site et vos visiteurs pour filtrer le traffic malicieux et inutile. C'est jusqu'à 50% de charge en moins sur votre serveur !
Il bloque les attaques en détectant les signatures des tentatives d'injection SQL, d'exploitation de faille XSS, etc... Il connait déjà plus de 3 millions d'adresses IP malveillantes.
Nous avons déjà les profils pour la protection des sites WordPress, Drupal, Magento, Prestashop, etc... Donc sa mise en place est rapide.
#cybersécurité#cyberprotection#wordpress#prestashop#magento#ddosattack#sqlinjection#xss#csrf#web application firewall
1 note
·
View note
Text
Navigating the Risks of JavaScript in Web Development
JavaScript is the linchpin of interactive web experiences, fueling everything from form validation to video streaming. While JavaScript enriches user engagement, it also raises significant security considerations. This post examines JavaScript's potential for misuse and the best practices to mitigate these risks.
The Dual Facets of JavaScript
JavaScript’s ability to execute on the client side is a bedrock feature of dynamic web pages, empowering developers to script complex features and responsive user interfaces. Unfortunately, the same capabilities that streamline user experience can also be exploited for malicious purposes.
Potential Misuse Cases
Malicious actors can leverage JavaScript for a range of harmful activities, including:
Data Theft: Scripts can covertly transmit personal data to unauthorized parties.
Session Hijacking: Exploiting cookies or session tokens to impersonate users.
Malware Distribution: Executing scripts that install harmful software on users' devices.
Understanding misuse scenarios is the first step in fortifying web applications against such threats.
Notable Attack Vectors: XSS and CSRF
The two most prevalent JavaScript-based threats are Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF). Each exploit different aspects of web application interaction with the user.
Cross-Site Scripting (XSS)
XSS attacks involve inserting malicious scripts into otherwise benign web pages. These scripts activate when unsuspecting users interact with the web pages, leading to unauthorized actions or data exposure.
Defense Strategy:
Input Encoding: Systematically encode user-generated content before displaying it on the web, effectively defanging embedded scripts.
Use of CSP: Employ a Content Security Policy to specify legitimate sources for executable scripts and resources.
Cross-Site Request Forgery (CSRF)
In CSRF attacks, attackers con the victim's browser into performing unintended actions on a site where the victim is authenticated, ranging from changing a user profile to initiating financial transactions.
Defense Strategy:
Anti-CSRF Tokens: Deploy one-time tokens that must accompany each form submission, ensuring requests originate from the site's own pages.
Cookie Attributes: Set 'SameSite' attributes on cookies to limit their flow to requests originating from the site that set them.
Building Defenses into JavaScript
Deploying defensive coding practices is essential to protect against the weaponization of JavaScript. Here are tactics developers can leverage:
Input Validation and Sanitization
Vigilant validation and sanitization of user input are fundamental:
// Validate acceptable characters (e.g., alphanumeric for a username)
function isValidUsername(username) {
return /^[a-zA-Z0-9]+$/.test(username);
}
Implementing a Content Security Policy (CSP)
CSP can significantly reduce the success rate of XSS attacks:
Content-Security-Policy: default-src 'self'; script-src 'self' https://trusted.cdn.com;
Managing Cookie Security
Correctly setting cookie attributes can prevent CSRF:
document.cookie = "sessionToken=xyz123; Secure; HttpOnly; SameSite=Strict";
Enlisting Users in Their Defense
While technical defenses are critical, empowering users to protect themselves can add another layer of security:
Educate Users: Regularly inform users on the importance of browser updates, installing security extensions, and recognizing phishing attempts.
Enable Security Features: Encourage users to install Firefox and use privacy-focused Browser extensions like uBlock Origin.
Conclusion
JavaScript's agility is a double-edged sword; its seamless integration into web pages can also serve nefarious purposes. Recognizing the potential for misuse compels us to employ rigorous defensive measures. Whether through stringent input handling, careful session management, or leveraging robust browser security features, a proactive approach to JavaScript security is the greatest defense against its weaponization. As technologies advance and threats evolve, so too must our strategies for maintaining web security and user trust.
#ko-fi#kofi#geeknik#nostr#art#blog#writing#twitter#xss#csrf#javascript#web development#dev#coding#programming#csp#content security policy#cross site scripting#information security#security#secure coding#infosec
1 note
·
View note
Video
youtube
WithMockUser and Spring CSRF FAIL!
0 notes
Video
youtube
WithMockUser and Spring CSRF FAIL!
0 notes
Text
In an era where the exchange of data across the web has become ubiquitous, safeguarding the integrity and security of web applications is paramount. Among the array of vulnerabilities that can threaten the trustworthiness of these applications, Cross-Site Request Forgery (CSRF) stands as a particularly insidious adversary. By the end of this comprehensive guid, you will possess the knowledge and tools to fortify your web applications against CSRF threats effectively.
0 notes
Text
Application Security : CSRF
Cross Site Request Forgery allows an attacker to capter or modify information from an app you are logged to by exploiting your authentication cookies.
First thing to know : use HTTP method carefully. For instance GET shoud be a safe method with no side effect. Otherwise a simple email opening or page loading can trigger the exploit of an app vulnerability
PortSwigger has a nice set of Labs to understand csrf vulnerabilities : https://portswigger.net/web-security/csrf
Use of CSRF protections in web frameworks
Nuxt
Based on express-csurf. I am not certain of potential vulnerabilities. The token is set in a header and the secret to validate the token in a cookie
Django
0 notes
Link
This article will show you how to set up an Http4s server to correctly protect against cross-origin requests and CSRF.
0 notes
Text
Cisco Patches High-Severity Bugs in Email, Identity, Web Security Products
Cisco Patches High-Severity Bugs in Email, Identity, Web Security Products
Home › Vulnerabilities
Cisco Patches High-Severity Bugs in Email, Identity, Web Security Products
By Ionut Arghire on November 03, 2022
Tweet
Cisco this week announced the release of patches for multiple vulnerabilities across its product portfolio, including high-severity defects in identity, email, and web security products.
The most severe of these issues is CVE-2022-20961 (CVSS score of 8.8),…
View On WordPress
0 notes
Link
#xss#BugBounty#vulnerability#Exploit#BugHunting#RCE#CyberSecurity#Vulnerabilities#Hacking#VAPT#CSRF#Malware#Pentest#Redteam#Infosec#AppSec#SSRF
0 notes
Text
[tumblr] api won't let me retrieve messages i've sent, even though i can clearly see [tumblr] itself calling the same api endpoint when it retrieves messages
#/v2/conversations/messages#[tumblr]#programming#is it like csrf or is it just not available to third parties
7 notes
·
View notes
Text
CodeIgniter 4 CSRF Token with Ajax Request
When we develop any application, security should be taken care of it. Security always be the first thing when we are planning for a secure application. In CodeIgniter 4 applications, we have few security library provided by the help of which we can do it in a easy way.
Inside this article we will see CodeIgniter 4 CSRF Token with Ajax Request. Cross-Site Request Forgery (CSRF).
0 notes
Text
Laravel API Disable CSRF Token
Laravel API Disable CSRF Token
Laravel API Disable CSRF Token
app/http/middleware/VerifyCsrfToken.php
<?php
namespace App\Http\Middleware;
use Illuminate\Foundation\Http\Middleware\VerifyCsrfToken as Middleware;
class VerifyCsrfToken extends Middleware
{
/**
* The URIs that should be excluded from CSRF verification.
*
* @var array
*/
protected $except = [
'api/*',
];
}
click for more Laravel codes, read in detail…

View On WordPress
0 notes
Text
Honestly my script is pretty good at this point, the only thing I don't understand is how to get the csrf token value without manually grabbing it from the browser
12 notes
·
View notes
Note
wait how did you glitch that favourite drink post? i beseech you to share your ways—fucking about with web dev tools got me nowhere.
Using the web dev tools, look at the payload for the POST request when you create a poll, and think about what might happen if somebody decided to add a feature to a web app but didn't feel like adding input validation to the backend.
Oh, and you'll also need to pay attention to the X-CSRF header.
I believe in you! <3
52 notes
·
View notes
Text
the boop endpoint doesn't check CSRF headers
5 notes
·
View notes