#Public Distribution System network
Text
So I don't know how people on this app feel about the shit-house that is TikTok but in the US right now the ban they're trying to implement on it is a complete red herring and it needs to be stopped.
They are quite literally trying to implement Patriot Act 2.0 with the RESTRICT Act and using TikTok and China to scare the American public into buying into it wholesale when this shit will change the face of the internet. Here are some excerpts from what the bill would cover on the Infrastructure side:
SEC. 5. Considerations.
(a) Priority information and communications technology areas.—In carrying out sections 3 and 4, the Secretary shall prioritize evaluation of—
(1) information and communications technology products or services used by a party to a covered transaction in a sector designated as critical infrastructure in Policy Directive 21 (February 12, 2013; relating to critical infrastructure security and resilience);
(2) software, hardware, or any other product or service integral to telecommunications products and services, including—
(A) wireless local area networks;
(B) mobile networks;
(C) satellite payloads;
(D) satellite operations and control;
(E) cable access points;
(F) wireline access points;
(G) core networking systems;
(H) long-, short-, and back-haul networks; or
(I) edge computer platforms;
(3) any software, hardware, or any other product or service integral to data hosting or computing service that uses, processes, or retains, or is expected to use, process, or retain, sensitive personal data with respect to greater than 1,000,000 persons in the United States at any point during the year period preceding the date on which the covered transaction is referred to the Secretary for review or the Secretary initiates review of the covered transaction, including—
(A) internet hosting services;
(B) cloud-based or distributed computing and data storage;
(C) machine learning, predictive analytics, and data science products and services, including those involving the provision of services to assist a party utilize, manage, or maintain open-source software;
(D) managed services; and
(E) content delivery services;
(4) internet- or network-enabled sensors, webcams, end-point surveillance or monitoring devices, modems and home networking devices if greater than 1,000,000 units have been sold to persons in the United States at any point during the year period preceding the date on which the covered transaction is referred to the Secretary for review or the Secretary initiates review of the covered transaction;
(5) unmanned vehicles, including drones and other aerials systems, autonomous or semi-autonomous vehicles, or any other product or service integral to the provision, maintenance, or management of such products or services;
(6) software designed or used primarily for connecting with and communicating via the internet that is in use by greater than 1,000,000 persons in the United States at any point during the year period preceding the date on which the covered transaction is referred to the Secretary for review or the Secretary initiates review of the covered transaction, including—
(A) desktop applications;
(B) mobile applications;
(C) gaming applications;
(D) payment applications; or
(E) web-based applications; or
(7) information and communications technology products and services integral to—
(A) artificial intelligence and machine learning;
(B) quantum key distribution;
(C) quantum communications;
(D) quantum computing;
(E) post-quantum cryptography;
(F) autonomous systems;
(G) advanced robotics;
(H) biotechnology;
(I) synthetic biology;
(J) computational biology; and
(K) e-commerce technology and services, including any electronic techniques for accomplishing business transactions, online retail, internet-enabled logistics, internet-enabled payment technology, and online marketplaces.
(b) Considerations relating to undue and unacceptable risks.—In determining whether a covered transaction poses an undue or unacceptable risk under section 3(a) or 4(a), the Secretary—
(1) shall, as the Secretary determines appropriate and in consultation with appropriate agency heads, consider, where available—
(A) any removal or exclusion order issued by the Secretary of Homeland Security, the Secretary of Defense, or the Director of National Intelligence pursuant to recommendations of the Federal Acquisition Security Council pursuant to section 1323 of title 41, United States Code;
(B) any order or license revocation issued by the Federal Communications Commission with respect to a transacting party, or any consent decree imposed by the Federal Trade Commission with respect to a transacting party;
(C) any relevant provision of the Defense Federal Acquisition Regulation and the Federal Acquisition Regulation, and the respective supplements to those regulations;
(D) any actual or potential threats to the execution of a national critical function identified by the Director of the Cybersecurity and Infrastructure Security Agency;
(E) the nature, degree, and likelihood of consequence to the public and private sectors of the United States that would occur if vulnerabilities of the information and communications technologies services supply chain were to be exploited; and
(F) any other source of information that the Secretary determines appropriate; and
(2) may consider, where available, any relevant threat assessment or report prepared by the Director of National Intelligence completed or conducted at the request of the Secretary.

Look at that, does that look like it just covers the one app? NO! This would cover EVERYTHING that so much as LOOKS at the internet from the point this bill goes live.
It gets worse though, you wanna see what the penalties are?

(b) Civil penalties.—The Secretary may impose the following civil penalties on a person for each violation by that person of this Act or any regulation, order, direction, mitigation measure, prohibition, or other authorization issued under this Act:
(1) A fine of not more than $250,000 or an amount that is twice the value of the transaction that is the basis of the violation with respect to which the penalty is imposed, whichever is greater.
(2) Revocation of any mitigation measure or authorization issued under this Act to the person.
(c) Criminal penalties.—
(1) IN GENERAL.—A person who willfully commits, willfully attempts to commit, or willfully conspires to commit, or aids or abets in the commission of an unlawful act described in subsection (a) shall, upon conviction, be fined not more than $1,000,000, or if a natural person, may be imprisoned for not more than 20 years, or both.
(2) CIVIL FORFEITURE.—
(A) FORFEITURE.—
(i) IN GENERAL.—Any property, real or personal, tangible or intangible, used or intended to be used, in any manner, to commit or facilitate a violation or attempted violation described in paragraph (1) shall be subject to forfeiture to the United States.
(ii) PROCEEDS.—Any property, real or personal, tangible or intangible, constituting or traceable to the gross proceeds taken, obtained, or retained, in connection with or as a result of a violation or attempted violation described in paragraph (1) shall be subject to forfeiture to the United States.
(B) PROCEDURE.—Seizures and forfeitures under this subsection shall be governed by the provisions of chapter 46 of title 18, United States Code, relating to civil forfeitures, except that such duties as are imposed on the Secretary of Treasury under the customs laws described in section 981(d) of title 18, United States Code, shall be performed by such officers, agents, and other persons as may be designated for that purpose by the Secretary of Homeland Security or the Attorney General.
(3) CRIMINAL FORFEITURE.—
(A) FORFEITURE.—Any person who is convicted under paragraph (1) shall, in addition to any other penalty, forfeit to the United States—
(i) any property, real or personal, tangible or intangible, used or intended to be used, in any manner, to commit or facilitate the violation or attempted violation of paragraph (1); and
(ii) any property, real or personal, tangible or intangible, constituting or traceable to the gross proceeds taken, obtained, or retained, in connection with or as a result of the violation.
(B) PROCEDURE.—The criminal forfeiture of property under this paragraph, including any seizure and disposition of the property, and any related judicial proceeding, shall be governed by the provisions of section 413 of the Controlled Substances Act (21 U.S.C. 853), except subsections (a) and (d) of that section.
You read that right, you could be fined up to A MILLION FUCKING DOLLARS for knowingly violating the restrict act, so all those people telling you to "just use a VPN" to keep using TikTok? Guess what? That falls under the criminal guidelines of this bill and they're giving you some horrible fucking advice.
Also, VPN's as a whole, if this bill passes, will take a goddamn nose dive in this country because they are another thing that will be covered in this bill.
They chose the perfect name for it, RESTRICT, because that's what it's going to do to our freedoms in this so called "land of the free".
Please, if you are a United States citizen of voting age reach out to your legislature and tell them you do not want this to pass and you will vote against them in the next primary if it does. This is a make or break moment for you if you're younger. Do not allow your generation to suffer a second Patriot Act like those of us that unfortunately allowed for the first one to happen.
And if you support this, I can only assume you're delusional or a paid shill, either way I hope you rot in whatever hell you believe in.
#politics#restrict bill#tiktok#tiktok ban#s.686#us politics#tiktok senate hearing#land of the free i guess#patriot act#patriot act 2.0
894 notes
·
View notes
Text
me when companies try to force you to use their proprietary software

anyway
Layperson resources:
firefox is an open source browser by Mozilla that makes privacy and software independence much easier. it is very easy to transfer all your chrome data to Firefox
ublock origin is The highest quality adblock atm. it is a free browser extension, and though last i checked it is available on Chrome google is trying very hard to crack down on its use
Thunderbird mail is an open source email client also by mozilla and shares many of the same advantages as firefox (it has some other cool features as well)
libreOffice is an open source office suite similar to microsoft office or Google Suite, simple enough
Risky:
VPNs (virtual private networks) essentially do a number of things, but most commonly they are used to prevent people from tracking your IP address. i would suggest doing more research. i use proton vpn, as it has a decent free version, and the paid version is powerful
note: some applications, websites, and other entities do not tolerate the use of VPNs. you may not be able to access certain secure sites while using a VPN, and logging into your personal account with some services while using a vpn *may* get you PERMANENTLY BLACKLISTED from the service on that account, ymmv
IF YOU HAVE A DECENT VPN, ANTIVIRUS, AND ADBLOCK, you can start learning about piracy, though i will not be providing any resources, as Loose Lips Sink Ships. if you want to be very safe, start with streaming sites and never download any files, though you Can learn how to discern between safe, unsafe, and risky content.
note: DO NOT SHARE LINKS TO OR NAMES OF PIRACY SITES IN PUBLIC PLACES, ESPECIALLY SOCAL MEDIA
the only time you should share these things are either in person or in (preferably peer-to-peer encrypted) PRIVATE messages
when pirated media becomes well-known and circulated on the wider, public internet, it gets taken down, because it is illegal to distribute pirated media and software
if you need an antivirus i like bitdefender. it has a free version, and is very good, though if youre using windows, windows defender is also very good and it comes with the OS
Advanced:
linux is great if you REALLY know what you're doing. you have to know a decent amount of computer science and be comfortable using the Terminal/Command Prompt to get/use linux. "Linux" refers to a large array of related open source Operating Systems. do research and pick one that suits your needs. im still experimenting with various dispos, but im leaning towards either Ubuntu Cinnamon or Debian.
#capitalism#open source#firefox#thunderbird#mozilla#ublock origin#libreoffice#vpn#antivirus#piracy#linux
368 notes
·
View notes
Text
John Deere's repair fake-out

Last week, a seeming miracle came to pass: John Deere, the Big Ag monopolist that — along with Apple — has led the Axis of Evil that killed, delayed and sabotaged dozens of Right to Repair laws, sued for peace, announcing a Memorandum of Understanding with the American Farm Bureau Federation to make it easier for farmers to fix their own tractors:
https://www.fb.org/files/AFBF_John_Deere_MOU.pdf
This is a move that’s both badly needed and long overdue. Deere abuses copyright law to force farmers to pay for official repairs — even when the farmer does the repair. That’s possible thanks to a practice called VIN locking, in which engine parts come with DRM that prevents the tractor from recognizing them until they pay hundreds of dollars for a John Deere technician to come to their farm and type an unlock code into the tractor’s console:
https://doctorow.medium.com/about-those-kill-switched-ukrainian-tractors-bc93f471b9c8
Like all DRM, VIN locks are covered by Section 1201 of the Digital Millennium Copyright Act (DMCA), a 1998 law that criminalizes distributing tools to bypass “access controls,” even if you do so for a lawful purpose (say, to fix your own tractor using a part you paid for). Violations of DMCA 1201 carry a penalty of 5 years in prison and a $500k fine — for a first offense.
This means that Deere owners are locked into using Deere for repairs, which also means that if Deere decides something isn’t broken, a farmer can’t get it fixed. This is very bad news indeed, because John Deere tractors are just computers in a fancy, mobile case, and John Deere is incredibly bad at digital security:
https://pluralistic.net/2021/04/23/reputation-laundry/#deere-john
That’s scary stuff, because John Deere is a monopolist, and a successful attack on the always-connected, networked tractors and other equipment it supplies to the world’s farmers could endanger the global food supply.
Deere doesn’t want to make insecure tractors, but it also doesn’t want to be embarrassed by security researchers who point out that its security is defective. Because security researchers have to bypass Deere tractors’ locks to probe their security, Deere can leverage DMCA1201 into a veto over who gets to warn the public about the mistakes it made.
It’s not just security researchers that Deere gets to gag: the company uses its repair monopoly to threaten farmers who complain about its business practices, holding their million-dollar farm equipment hostage to their silence:
https://pluralistic.net/2022/05/31/dealers-choice/#be-a-shame-if-something-were-to-happen-to-it
This all adds up to what Jay Freeman calls “felony contempt of business model,” an abuse of copyright law that allows a monopolistic corporation to reach beyond its own walls and impose its will on it customers, critics and competitors:
https://locusmag.com/2020/09/cory-doctorow-ip/
If Deere was finally suing for peace in the Repair Wars, well, that was wonderful news indeed — as I said, a seeming miracle.
But — like all miracles — it was too good to be true.
The MOU that Deere and the Farm Bureau signed is full of poison pills, gotchas, fine-print and mendacity, as Lauren Goode documents in her Wired article, “Right-to-Repair Advocates Question John Deere’s New Promises”:
https://www.wired.com/story/right-to-repair-advocates-question-john-deeres-new-promises/
For starters, the MOU makes the Farm Bureau promise to end its advocacy for state Right to Repair bills, which would create a repair system governed by democratically accountable laws, not corporate fiat. Clearly, Deere has seen the writing on the wall, after the passage in 2002 of Right to Repair laws in New York and Colorado:
https://www.eff.org/deeplinks/2022/06/when-drm-comes-your-wheelchair
These two bills broke the corporate anti-repair coalition’s winning streak, which saw dozens of state R2R bills defeated:
https://pluralistic.net/2021/05/26/nixing-the-fix/#r2r
Deere’s deal-with-the-devil is a cynical ploy to brake R2R’s momentum and ensure that any repairs are carried out on Deere’s terms. Now, about those terms…
Deere’s deal offers independent repair shops access to diagnostic tools and parts “on fair and reasonable terms,” a murky phrase that can mean whatever Deere decides it means. Crucially, the deal is silent on whether Deere will supply the tools needed to activate VIN locks, meaning that farmers will still be at Deere’s mercy when they effect their own repairs.
What’s more, the deal itself isn’t legally binding, and Deere can cancel it at any time. Once you dig past the headline, the Deere’s Damascene conversion to repair advocacy starts to look awfully superficial — and deceptive.
One person who wasn’t fooled is sick.codes, the hacker who has done the most important work on reverse-engineering Deere’s computer systems, culminating in last summer’s live, on-stage hack of a John Deere tractor at Defcon:
https://pluralistic.net/2022/08/15/deere-in-headlights/#doh-a-deere
Shortly after the announcement, Sick.codes tweeted how the fine-print in the MOU would have prevented him from doing the work he’s already done (including “a direct stab at me lol”):
https://twitter.com/sickcodes/status/1612484935495057409
As with other instances of monopolistic, corporate copyfraud — like, say, the deceptive Open Gaming License — the John Deere capitulation is really a bid to take away your rights, dressed up as a gift of more rights:
https://mostlysignssomeportents.tumblr.com/post/706163316598407168/good-riddance-to-the-open-gaming-license
[Image ID: Hieronymus Bosch's painting, 'The Conjurer.' The Conjuror's shell-game table holds a small John Deere tractor that the audience of yokels gawps at. One yokel is wearing a John Deere hat. The conjurer is holding a wrench.]
1K notes
·
View notes
Text
Seed networks are community organizations that have multiplied in the past decade in different Brazilian biomes to collect, trade and plant native seeds in degraded areas.
In the Chapada dos Veadeiros area, in Goiás state members of seed networks from several parts of Brazil met for almost a week in early June.
Along with environmental organizations, researchers and government officials, they participated in discussions to boost Redário, a new group seeking to strengthen these networks and meet the demands of the country’s ecological restoration sector.
“This meeting gathered members of Indigenous peoples, family farmers, urban dwellers, technicians, partners, everyone together. It creates a beautiful mosaic and there’s a feeling that what we are doing will work and will grow,” says Milene Alves, a member of the steering committee of the Xingu Seed Network and Redário’s technical staff.
Just in 2022, 64 metric tons of native seeds were sold by these networks, and similar figures are expected for 2023.
The effort to collect native seeds by traditional populations in Brazil has contributed to effective and more inclusive restoration of degraded areas, and is also crucial for the country to fulfill its pledge under international agreements to recover 30 million acres of vegetation by 2030.
Seed collection for restoration in these areas has previously only been done by companies. But now, these networks, are organized as cooperatives, associations or even companies, enable people in the territories to benefit from the activity.
Eduardo Malta, a restoration expert from the Socio-Environmental Institute and one of Redário’s leaders, advocates for community participation in trading and planting seeds. “These are the people who went to all the trouble to secure the territories and who are there now, preserving them. They have the greatest genetic diversity of species and hold all the knowledge about the ecosystem,”
.
The Geraizeiros Collectors Network are one of the groups that makes up Redário. They were founded in 2021, and now gathers 30 collectors from eight communities in five municipalities: Montezuma, Vargem Grande, Rio Pardo de Minas, Taiobeiras and Berizal.
They collect and plant seeds to recover the vegetation of the Gerais Springs Sustainable Development Reserve, which was created in 2014 in order to stop the water scarcity as a result of eucalyptus monocultures planted by large corporations.
“The region used to be very rich in water and it is now supplied by water trucks or wells,” says Fabrícia Santarém Costa, a collector and vice president of the Geraizeiros Collectors’ Network. “Today we see that these activities only harm us, because the [eucalyptus] company left, and we are there suffering the consequences.”
Costa was 18 years old in 2018, when the small group of seed collectors was founded and financed by the Global Environmental Facility. She says that working with this cooperative changed the way she looks at life and the biome in which she was born and raised.
She describes restoring the sustainable development work as "ant work", ongoing, slow. But it has already improved the water situation in the communities. In addition, seed sales complement geraizeiros’ income, enabling them to remain in their territories.
.
The Redário initiative also intends to influence public policies and regulations in the restoration sector to disseminate muvuca, the name given by the networks to the technique of sowing seeds directly into the soil rather than growing seedlings in nurseries.
Technical studies and network experiences alike show that this technique covers the area faster and with more trees. As a result, it requires less maintenance and lower costs. This system also distributes income to the local population and encourages community organizations.
“The muvuca system has great potential [for restoration], depending on what you want to achieve and local characteristics. It has to be in our range of options for meeting the targets, for achieving them at scale,” says Ministry of the Environment analyst Isis Freitas.
Article published August 3rd, 2023
#long post#climate change#climate#hope#good news#more to come#climate emergency#positive news#hopeful#climate justice#news#important#good post#links
199 notes
·
View notes
Text
(4/4) over parts on my profile
Shelby's Instagram
Despite the fact that Shelby said that she and Wilbur started dating in 2022, it seems to me that this is slightly wrong. And their relationship began at the end of 2021. I think so because of the photos of Wilbur and Shelby together on her Instagram. (1-1,5, 2, 3)

In all the photographs (except the last one) absolutely everyone is marked except her and Wilbur.
Sudden facts
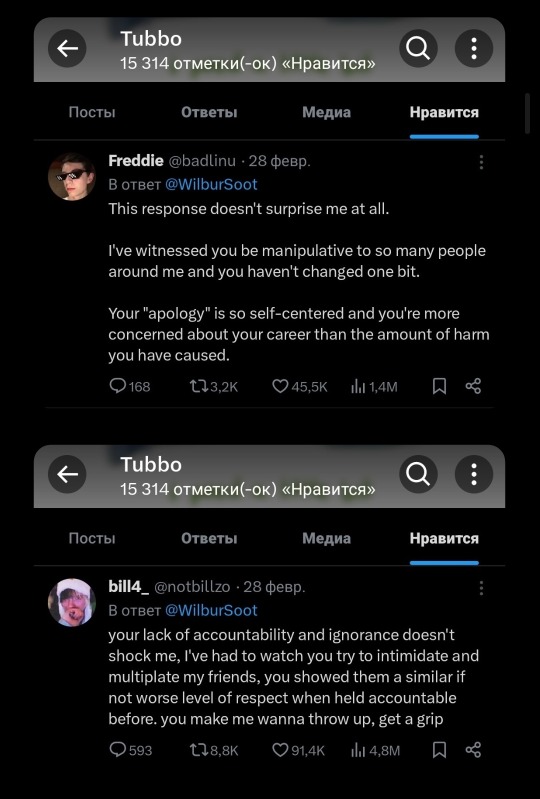
Smajor was the very first of Shelby’s close friends to announce himself; he claimed that he saw abuse in their relationship, but for some reason remained silent. The reason for his silence is unknown.
Billzo appears, emerging from his year-long silence with a statement that he, too, saw how Wilbur manipulated him and his friends. At the same time, Billzo, like Smajor, did not talk about this until the persecution against Sut began. The reason for his silence is also unknown.
After this, Tubbo liked Bilzo and Freddie's answer
Wilbur's moments
Wilbur and others have repeatedly confirmed and joked about the fact that Wilbur has an addiction to alcohol. Wilbur himself admitted this on Quackity's stream.
Amid Wilbur and Shelby's relationship, Technoblade died. Techno's death could have made Wilbur very depressed, especially considering that Wilbur had frequent panic attacks as a child, as well as severe anxiety.
Wilbur more than once asked not to idealize him, he said a lot about the fact that he was a bad person.
He said that he had been mentally ill since childhood and that he would soon undergo therapy. And for some time Will was so apathetic and depressed that he didn’t even get out of bed and the only one who was at least somehow worried about him and forced him to look after him was Tommy, who was 17 at that time.
Also one of the streams from 2023, where he mentions his problems with mental health and that it has become worse
"Wilbur, if you weren't a little bit handsome, everyone would think you're wrongun" - Tommy's joke (6:25)
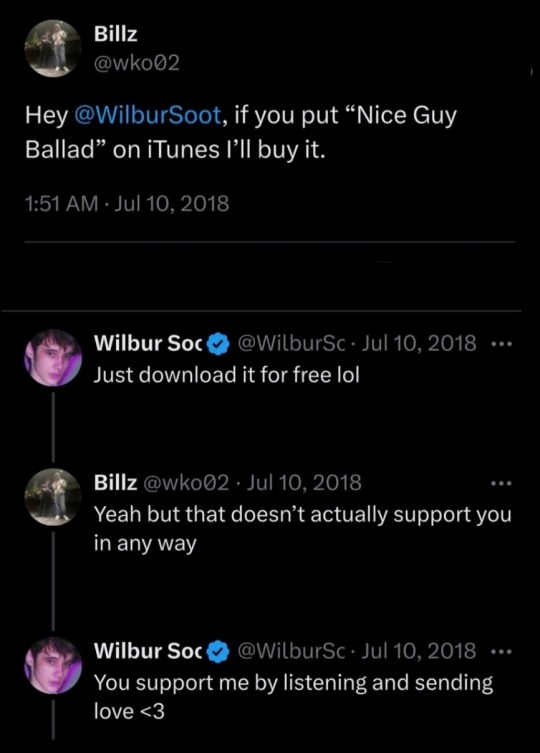
Shelby also said that Will doesn't care about his fans, and he only wants fame and money from them. Officially, tickets for his concert cost from 49+ pennies. Tommy talked about this when he went to the cmwyl concert. And Bilzo himself said on Twitter that he would buy Will’s ttrack «The "Nice Guy" Ballad» if he put it up, and Bilzo replied that he could listen to it for free.
Wilbur also supports feminism.
Shelby's cousin
Cousin Shelby said that it was not Wilbur who abused Shelby, but she who abused him. (There is no evidence that this is Shelby’s cousin, so the information is not accurate)
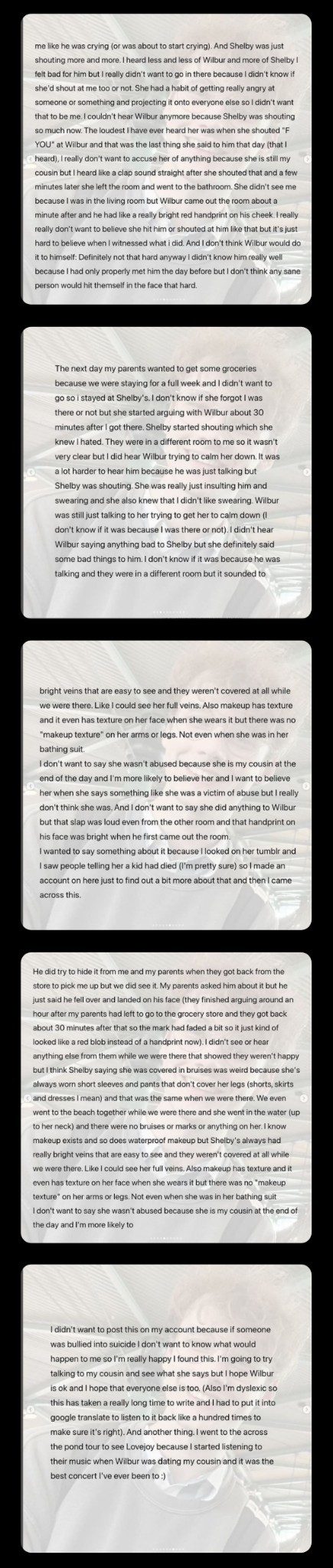
Shelby responded to this within 40 minutes, but at this point, her reply has been deleted.
What Shelby violated
You can read more about Shelby's violations from VikaVivii (RIP♡) on Twitter.
Article 188 - Libel, administrative violation
Article 189 - Insult inflicted in a public speech, or in a printed or publicly displayed work, or in the media. Administrative violation.
Article 203-1 - Illegal actions regarding information about private life and personal data. Administrative violation.
Article 343 - Distribution of pornographic material (intimate photos and videos of Wilbur). Criminal article.
Im actually not sure about this
Article 352 - Unlawful acquisition of computer information (Wilbur’s personal data). Administrative violation or criminal for up to two years.
Article 355 - Violation of the rules for operating a computer system or network. Administrative violation.
Chapter 2 Article 3 - Disrespect for Wilbur's Life
Chapter 2 Article 5 - Dissemination of Wilbur Sweat's personal information without his mutual consent to these actions, thereby violating his integrity
Chapter 1-2 Article 11 - disrespect for the honor and dignity of William Gold, distributing purely personal information and supporting doxxing towards Wil.
Chapter 2 Article 12 - condemnation of Wilbur Soot for his thoughts and beliefs, which have the right to be expressed.
Victims from SupportShubleSquad
Aiden (@VikaVivii) is a 15-year-old child who was subjected to domestic violence and who was one of Wilbur's active supports. He actively looked into the situation, talked about the holes in Shubble's story, and covered the petition (authored by @kinokonyai) which outlines the laws that Shelby violated. Due to bullying and threats of doxxing, on 03/07/24, I jumped from the balcony, before that I wrote a couple of posts on my Twitter account, saying goodbye. Afterwards, Aiden's close friend (@ZaneDeYala) confirmed his death and said that Aiden's mother would speak out about it later.
Miles (@Wilbees_xx) - 16 years old, tried to commit suicide with an overdose of pills. Based on his brother's statement, we know that Miles is currently in the hospital and getting help.
M (@weirdobur) - wanted to commit suicide, but luckily he couldn’t, now he’s decided to step away from the Internet for an indefinite period.
⬆️
Shelby left her Twitter account for the purpose of “resting.” At the same time, deleting messages and banning those people who talk about Aiden and Miles.
“I didn’t ask for threats on my behalf.” Didn’t stop her fans from bullying, but also supported it herself. It has long been known that she liked wishes for the death of Wilbur and leaking his personal information, but as soon as this was noticed, she removed the likes.
On TinaKiten, Shelby was pressured by the supports, forcing her to speak out about the situation and take sides, despite the fact that she was not even Wilbur’s friend, but an acquaintance.
3rd Shelby's stream
On March 24, Shelby streamed after a break of 2 weeks.
16:30 she began to talk about how you can’t trust the words of others, about how people wish death to each other, and how they wish death to her every day. After that, she began to talk about the trust “adult kids” have in adults, and how she felt in the company of such adults.
23:17 she said that children are stupid: “cause they are kids, they are stupid,” and then immediately qualified her statement with how unfairly the younger generation is treated. She then began to talk about brotherly relationships between teenagers and adults, clearly alluding to the relationship between Wilbur and Tommy, but without directly saying so, she talked about the manipulation of children by adults. That when a teenager needs help, this adult will never come. She said that friendships with age differences should be more respectful, especially towards children.
Later she mentions Philza saying that he is a great person and we should follow his example. In “brotherly” relationships there should not be any friendly blows or jabs (More than half of the relationships between brothers and sisters are exactly like that. Especially when someone is older).
She later said that it was terrible to deal with teenagers in friendships: “because they are so young and you are so fucking old. What are you doing."
27:19 “If you ever been one of this people, (cause we saw this happen before too), where you were caught, (where you in massive platform), of violence, over a lot of teenagers and children. And in privet you are being an abusing people, manipulating and abusing teenagers. I just think, if you are one of these people who are caught and say: “I'm sorry, I'm gonna work on myself” - I think that is a lie if you ever come back. I think if you have been caught clearly irresponsible with this position of power over teenagers, that if you actually out of them working in a sorry, you'd voluntarily never come back, if you really were sorry. I just couldn’t ever believe it if you put yourself right back into the same shoes...” At this point, she was clearly talking about Wilbur, accusing him of manipulating and abusing teenagers.
31:08 she started talking about teenagers who commit suicide. She started laughing at them, covering it up with the words that she was laughing at herself, at her situation. She said that these children are lying, because you can look up their phone number and use it to find information or find their parents. And finally ask them about this situation. She said that she found all this and checked it out. But she did not provide any evidence.
32:37 “Because it is a crime to tell people kiil themselves” (She herself does nothing with her team ShelbySupporSquad, who wish people kys (kill themselves) every day)
39:50 “You are waiting for more information, maybe before you call someone a lying bitch”
(I’ve been waiting for more information for more than a month)
At 41 minutes, she began to talk about how many people began to share their stories and that she was proud of them, and that she was glad that many of them found a way out of the situation.
44:22 «I've seen so many excuses, I've just seen so many excuses that I think that not okay and I think that actually disrespect, I've seen people use excuses of depression to excuse some behavior, I think that such disrespect to anyone who felt depressed, because feeling depressed is not a pass to abuse people, because that are you sealing to imply. It's just not an excuse for abuse, no one of this excuse for abuse, mental illness not is excuse for abuse, because for forgetting part that took it to a level where they were abusing somebody else. And that's not okay, that's not.»
Many people began to get angry at this statement, it seems to me that basically there is nothing wrong here, but she still cannot judge depression, since she is not a professional.
55:45 Aimsey joined via Discord call until 1:09:34 (they were discussing cartoons)
1:11:17 she started talking about safety on the Internet (don’t tell your age, if you’re being bullied, tell your loved ones, etc.)
1:12:53 “Important to have a slightly adult to go to, because you don’t want to go to your parents and they can never be able to understand...”
Deleted post
I would also like to note that this post has been deleted from the «Wilbur music» channel.
Tupac posters
A moment that fans noticed. Shelby has a poster of Tupac, the rapper convicted of rape, on his wall.
I checked this and can finally confirm the information. It would be fine if she had only one poster hanging out of ignorance, but the fact that she has two posters is suggestive.

Sorry boys
On March 30, Sorry boys posted a post in which, on behalf of Tommy, they declare that they will go on a break, but before that they will release one video, he also wrote that they have as many as 5 filmed videos, but they will not post them.
Wilbur in Brighton?
On April 9, a video from a LoveJoy fan appeared on TikTok, in which he filmed Wilbur congratulating him (someone) on his birthday: «Just birth, happy birthday to “name”» (I didn’t fully understand what he said, because spoke quickly). This happened at the airport.
They also began to say that Wilbur had become visible again in Brighton. Most likely Wilbur came from New York where he temporarily lived with LoveJoy.
The owner of the video posted a verification post that he had recently meet Wilbur. The video was filmed back in December 2023. And it was filmed by a friend who was flying with LoveJoy on the same rail.

Spotify UK & Ireland

33 notes
·
View notes
Note
Does going out and feeding the homeless count as a political action?
this is a very contextual question imo--let me just say at the outset that obviously, feeding the homeless is good (a controversial opinion, i know, please hold your slavish praise for my contrarian credentials).
as for whether it constitutes--specifically effective--political action, that very much depends on what it is being done alongside and in service of. in and of itself, i do not think it is effective political action to only provide food to people. & in fact the very impersonal, top-down, apolitical 'charitable' model of food distribution is in fact a useful sticking plaster for the economic systems that lead to people being homeless and hungry in the first place
so what makes it effective political action? well, firstly, i think a bare minimum necessity (whether the food initiative is of a revolutionary communist nature or not) to avoid a charitable organization being complicit in the continued functioning of the system is to use every opportunity, especially media attention afforded by the work, to excoriate the government and social systems that allowed this to happen. i think if you do charity work and then accept media headpats and 'heartwarming: orphans saved from mulcher' coverage without fighting back against that narrative at every opportunity, you are not doing effective political action.
that brings you to one way in which feeding people can be useful political action, if you use the action to publicize and emphasize the fact that you are having to do this as a staggering intentional failure of policy and society.
secondly, i think that there is again a difference between an impersonal act of charity and an act of support: if you are using the provision of food to build community, getting to know your unhoused neighbours, creating stable and lasting informal support networks that can still do work (however minimal) in the event of the serverance of external funding or the collapse of the food provision program, then what you are doing is much more effective as revolutionary political action because you are building something.
thirdly, there is a level on which improving the material conditions of the proletariat can always provide an avenue for revolutionary politics, in the same way that i think revolutionary communists should support, say, minimum wage increases or legal efforts for worker's protections (although not to the point of investing themselves in electoral politics), i think it's a pretty straightforward concept that people who have food to eat are more capable of organizing and particiapting in class struggle. but in this case you need to be organizing, agitating, and reaching out alongside the food provision measures.
so--tldr: it depends! obviously it is always a pretty straightforwardly morally good thing to do, but whether it is effective communist political action substantially depends on the circumstances and context of it.
160 notes
·
View notes
Text
At midnight, the Yukon government was hit by a cyberattack that shut down the website and public facing government websites, according to the territorial government. Some internal systems were also down, but have since been resolved.
“The type of attack we are experiencing sends abnormally high levels of traffic to our network to overwhelm our systems, but these types of attacks do not try and access information,” reads a Facebook post on the morning of Sept. 14 by the Government of Yukon.
An email update after noon on Sept. 14 indicates the cyberattack is known as a distributed denial-of-service attack.
A denial-of-service attack occurs when attackers flood an internet server with traffic and overwhelm it, triggering a crash.
The broader impact of the cyberattack and who is behind it remain unclear. [...]
Continue Reading.
Tagging: @politicsofcanada
19 notes
·
View notes
Text
AI: A Misnomer
As you know, Game AI is a misnomer, a misleading name. Games usually don't need to be intelligent, they just need to be fun. There is NPC behaviour (be they friendly, neutral, or antagonistic), computer opponent strategy for multi-player games ranging from chess to Tekken or StarCraft, and unit pathfinding. Some games use novel and interesting algorithms for computer opponents (Frozen Synapse uses deome sort of evolutionary algorithm) or for unit pathfinding (Planetary Annihilation uses flow fields for mass unit pathfinding), but most of the time it's variants or mixtures of simple hard-coded behaviours, minimax with alpha-beta pruning, state machines, HTN, GOAP, and A*.
Increasingly, AI outside of games has become a misleading term, too. It used to be that people called more things AI, then machine learning was called machine learning, robotics was called robotics, expert systems were called expert systems, then later ontologies and knowledge engineering were called the semantic web, and so on, with the remaining approaches and the original old-fashioned AI still being called AI.
AI used to be cool, then it was uncool, and the useful bits of AI were used for recommendation systems, spam filters, speech recognition, search engines, and translation. Calling it "AI" was hand-waving, a way to obscure what your system does and how it works.
With the advent if ChatGPT, we have arrived in the worst of both worlds. Calling things "AI" is cool again, but now some people use "AI" to refer specifically to large language models or text-to-image generators based on language models. Some people still use "AI" to mean autonomous robots. Some people use "AI" to mean simple artificial neuronal networks, bayesian filtering, and recommendation systems. Infuriatingly, the word "algorithm" has increasingly entered the vernacular to refer to bayesian filters and recommendation systems, for situations where a computer science textbook would still use "heuristic". Computer science textbooks still use "AI" to mean things like chess playing, maze solving, and fuzzy logic.
Let's look at a recent example! Scott Alexander wrote a blog post (https://www.astralcodexten.com/p/god-help-us-lets-try-to-understand) about current research (https://transformer-circuits.pub/2023/monosemantic-features/index.html) on distributed representations and sparsity, and the topology of the representations learned by a neural network. Scott Alexander is a psychiatrist with no formal training in machine learning or even programming. He uses the term "AI" to refer to neural networks throughout the blog post. He doesn't say "distributed representations", or "sparse representations". The original publication he did use technical terms like "sparse representation". These should be familiar to people who followed the debates about local representations versus distributed representations back in the 80s (or people like me who read those papers in university). But in that blog post, it's not called a neural network, it's called an "AI". Now this could have two reasons: Either Scott Alexander doesn't know any better, or more charitably he does but doesn't know how to use the more precise terminology correctly, or he intentionally wants to dumb down the research for people who intuitively understand what a latent feature space is, but have never heard about "machine learning" or "artificial neural networks".
Another example can come in the form of a thought experiment: You write an app that helps people tidy up their rooms, and find things in that room after putting them away, mostly because you needed that app for yourself. You show the app to a non-technical friend, because you want to know how intuitive it is to use. You ask him if he thinks the app is useful, and if he thinks people would pay money for this thing on the app store, but before he answers, he asks a question of his own: Does your app have any AI in it?
What does he mean?
Is "AI" just the new "blockchain"?
14 notes
·
View notes
Text
Chapter 3. Economy
How will exchange work?
There are many different ways exchange could work in a stateless, anti-capitalist society, depending on the size, complexity, and preferences of the society. Many of these are far more effective than capitalism at ensuring a fair distribution of goods and keeping people from taking more than their fair share. Capitalism has created a greater inequality in access to resources than any other economic system in human history. But the principles of capitalism that economists have indoctrinated the public to accept as laws are not universal.
Many societies have traditionally used gift economies, which can take many different forms. In societies with a modest amount of social stratification, the wealthier families maintain their status by giving gifts, holding lavish feasts, and spreading their wealth; in some cases, they risk the wrath of the others if they are not generous enough. Other gift economies are barely or not at all stratified; the participants simply disown the concept of property and give and take social wealth freely. In his diary, Columbus remarked with amazement that the first indigenous people he encountered in the Caribbean had no sense of property, and gave willingly of all they had; indeed, they came bearing gifts to greet their strange visitors. In such a society, no one could be poor. Now, after hundreds of years of genocide and capitalist development, many parts of the Americas have some of the starkest wealth gaps in the world.
In Argentina, poor people initiated a massive barter network that grew enormously after the economic collapse in 2001 rendered capitalist forms of exchange unworkable. The barter system evolved from simple swap meets into a huge network involving an estimated three million members trading goods and services — everything from homemade crafts, food, and clothing to language lessons. Even doctors, manufacturers, and some railways participated. An estimated ten million people were supported by the barter network at its peak.
The barter club facilitated exchange by developing a credit/currency system. As the network grew, and the capitalist crisis deepened, the network was beset by a number of problems, including people — often from outside the network — stealing or forging the currency. Several years later, after the economy stabilized under President Kirchner, the barter club shrank, but still retained a huge membership considering it was an alternative economy in the country that was once a model for neoliberal capitalism. Rather than giving up, remaining members developed a number of solutions to the problems they had encountered, such as limiting membership to producers so the network is only used by those who contribute to it.
Contemporary anarchists in the US and Europe are experimenting with other forms of distribution that transcend exchange. One popular anarchist project is the “free store” or “give-away shop.” Free stores serve as a collection point for donated or scavenged items that people no longer need, including clothes, food, furniture, books, music, even the occasional refrigerator, television, or car. Patrons are free to browse through the store and take whatever they need. Many accustomed to a capitalist economy who come into a free store are perplexed by how it could possibly work. Having been raised with a scarcity mentality, they assume that since people profit by taking stuff and do not profit by donating, a free store would quickly empty out. However this is rarely the case. Countless free stores operate sustainably, and most are overflowing with goods. From Harrisonburg, Virginia, to Barcelona, Catalunya, hundreds of free stores defy capitalist logic on a daily basis. The Weggeefwinkel, Giveaway Shop, in Groningen, Netherlands, has operated out of squatted buildings for over three years, opening twice a week to give away free clothes, books, furniture, and other items. Other free stores hold fundraisers if they have to pay rent, which would not be an issue in a completely anarchist society. Free stores are an important resource for impoverished people, who either are denied a job by the whims of the free market or who work a job, or two or three, and still can’t afford clothes for their kids.
A more high-tech example of free exchange is the relatively mainstream and wildly successful Freecycle Network. Freecycle is a global network originally formed by an environmental nonprofit group to promote giving away items that might otherwise end up in the trash. As of this writing they have over 4 million members grouped into 4200 local chapters, spread through 50 countries. Using a website to post items wanted or items available to give away, people have circulated prodigious quantities of clothing, furniture, toys, artwork, tools, bicycles, cars, and countless other goods. One of the rules of Freecycle is that everything has to be free, neither bartered nor sold. Freecycle is not a centrally controlled organization; local chapters set themselves up based on the common model, and use the website on which the model is based.
However, as it does come from a liberal nonprofit group without revolutionary aspirations nor any critique of capitalism and the state, we can expect Freecycle to have some problems. In fact, the organization accepts corporate sponsorship from a major recycling company and advertises on its website, and the chairperson has arguably slowed the spread of the Freecycle idea by attacking various member groups or copycat websites with lawsuits, or threats thereof, for trademark infringement; also by collaborating with the notoriously authoritarian Yahoo! Groups to shut down local chapters for not adhering to organizational rules concerning logo and language. Naturally, in an anarchist society there would be no lawsuits for trademark infringement and one chairperson would not be able to tyrannize a network that was maintained by millions of people. In the meantime, Freecycle demonstrates that gift economies can function even within jaded, individualistic Western societies, and can take new forms with the help of the internet.
#anarchism#daily posts#communism#anti capitalist#anti capitalism#late stage capitalism#anarchy#anarchists#libraries#leftism#anarchy works
7 notes
·
View notes
Text
GIS In Our Daily Lives
The involvement of Geographic Information Systems (GIS) in our daily lives is pervasive, influencing and enhancing various aspects across different sectors. The integration of GIS into everyday activities has become integral for decision-making, planning, and optimizing resources. GIS helps city planners and transportation experts to provide them with information like maps, satellite pictures, population statistics, and infrastructure data. GIS helps them make better decisions when designing cities and transportation systems that are sustainable and good for the environment.
The following points elucidate the notable involvement of GIS in our daily lives:
Navigation and Location Services: GIS provides monitoring functions through the visual display of spatial data and precise geographical positioning of monitored vehicles, whereas GPS provides accurate, clear, and precise information on the position and navigation of a monitored or tracked vehicle in real-time and at the exact location.GIS is at the core of navigation applications and location-based services on smartphones. It enables accurate mapping, real-time navigation, and geolocation services, assisting individuals in finding locations, planning routes, and navigating unfamiliar areas.
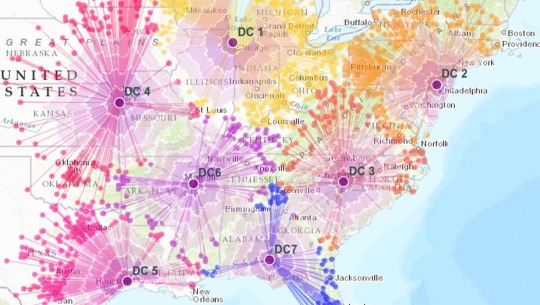
E-Commerce and Delivery Services: GIS software is a powerful tool for supply chain network planning. It helps determine the optimal location for distribution centers, warehouses, or other supply facilities. GIS is utilized in logistics and delivery services for optimizing routes, tracking shipments, and ensuring timely deliveries. E-commerce platforms leverage GIS to enhance the efficiency of their supply chain and last-mile delivery processes.
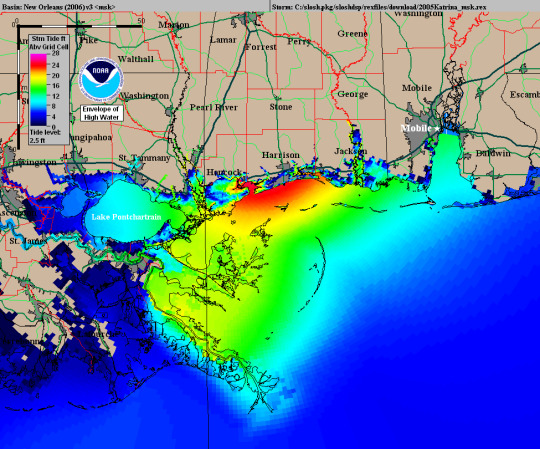
Weather Forecasting and Disaster Management: Many states are using GIS dashboard to monitor the rainfall across the state, on a real-time basis, from the data shared by rain sensors installed at various locationsGIS plays a crucial role in weather forecasting and disaster management. It assists meteorologists in analyzing spatial data, predicting weather patterns, and facilitating timely responses to natural disasters by mapping affected areas and coordinating emergency services.
Healthcare Planning and Disease Monitoring: Geographic Information Systems enable the visualization and monitoring of infectious diseases. Additionally GIS records and displays the necessary information that health care needs of the community as well as the available resources and materials. GIS supports public health initiatives by mapping the spread of diseases, analyzing healthcare resource distribution, and assisting in the planning of vaccination campaigns. It aids in identifying high-risk areas and optimizing healthcare service delivery.
Social Media and Geo-tagging: GIS also helps in geotagging and other location related information in posts, it’s tools can map and visualize the spatial distribution of social media activity. This analysis can reveal trends, hotspots, and patterns in user engagement across different geographic areas. Many social media platforms incorporate GIS for geo-tagging, allowing users to share their location and experiences. This feature enhances social connectivity and facilitates the sharing of location-specific information.
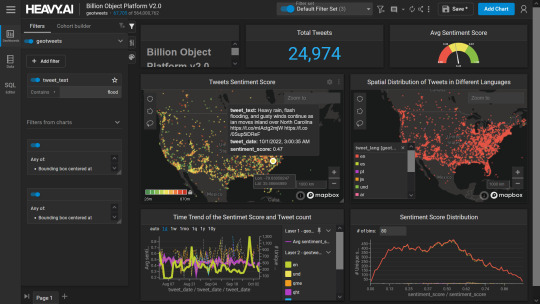
Smart City Initiatives: The Geographic Information System (GIS) offers advanced and user-friendly capabilities for Smart City projects and allows to capture, store and manipulate, analyze and visualize spatially referenced data. It is used for spatial analysis and modeling. It is the cornerstone of smart city planning, enabling the integration of data for efficient urban management. It supports initiatives related to traffic management, waste disposal, energy consumption, and overall infrastructure development.
Education and Research: GIS is increasingly utilized in education and research for visualizing and analyzing spatial data. It enables students and researchers to explore geographic relationships, conduct field studies, and enhance their understanding of various subjects.

Agricultural Management and Precision Farming: Farmers leverage GIS to optimize agricultural practices by analyzing soil conditions, crop health, and weather patterns. Precision farming techniques, facilitated by GIS, contribute to increased crop yields and sustainable farming practices.

Real Estate and Property Management: In the real estate sector, GIS aids in property mapping, land valuation, and site selection. It provides real estate professionals with valuable insights into spatial relationships, market trends, and optimal development opportunities.
Tourism and Recreation: GIS enhances the tourism industry by providing interactive maps, route planning, and location-based information. It assists tourists in exploring destinations, finding attractions, and navigating efficiently.
The broad and varied involvement of GIS in our daily lives underscores its significance as a technology that not only facilitates geographic data analysis but also contributes to the efficiency, safety, and interconnectedness of modern society. As GIS applications continue to evolve, their impact on daily activities is expected to further expand and refine.
#gis#architectdesign#architecture#city#education#geographic information system(gis)#geographical indication
8 notes
·
View notes
Text
Impurities and Mutations
Constructive feedback and criticism is welscome as always. (I'm not happy with this draft but I've spent too much time on this post already at the expense of others).
The idea of a, (for lack of a better term) biological connection between The Other and both renagade Timelords, (eg: The, "Affected Generation" and the Deca) and the subsequent newblood generations. But is there any clues in the expanded lore as to how and why?
Basic looms summary
Looms work by combining, "weaving" together biodata material from both the House's own stock from past Cousins, (80%-90%) and the wider distribution system, (10%-20%) to form either a fully ground adult or a baby. (The percentages are a guess based on the idea that the distributor biodata exchange is intended as a degredation prevention measure as each House was essentially endlessly recycling the same biodata for millions of years which along with Rassilon's later intelligence reduction modification resulted in the: stagant, unvaried, and elderly civil servant mentality civilisation seen in, "The Deadly Assassin"). Just before the start of the Second War in Heaven the new stasis tube like looms were introduced and used to mass produce Timelord soldiers aswell as Timelord citizenry.
The Other's Plan
In Lungbarrow chapter 30 The Other threw himself into the loom network's prime distributor, the open progenitive cascades unravelling his biodata. His plan is generally considered to be rebirth millions of years later via a random loom, (the term "huanting the network" has been used) because he was overcome with a deep self loathing depression over: the way Gallifreyian society had changed to become stagant, Rassilon's increasing despotism, and his self perceived partial blame for both.
However this interpretation doesn't make sense for the following two reasons:
The first is that as the co creator of the loom technology with Rassilon, The Other would know that as opposed to loom jumping this would not result in ressurection regardless of how long he, "waited" as his unravelled biodata would be irrevocably lost by being dispersed throughout the entire loom network mutating when it combines with those in each individual House's store which is shared resulting in each generation accumulating more of it. This is backed up by: a.Both the appearance and increased impurities, (ie: Biodata, "errors" and thus personality eccentricities) starting out very minor with barely any effect on the status quo about 1,000,000.B.T.W. to the more widepsread renegade upheaving the status quo, "Affected Generation" about 700,000.B.T.W.. b.The term reconstitution is specifically used instead of ressurection and has a defintion of, "the act of changing something so that it has a different form". In this case his self sacrifice so his biodata could change future loomborn's biodata makeup so that they are more wombborn like, (eg: Varied individualistic personalities) and thus more open to change. c.The fact that as one of the four main mutations of the, "Affected Generation", (replacing Avus/Grandfather Paradox as a Lungbarrow Cousin when he retired himself from history) holds and can access only some of the Other's memories while not knowing who most of the people in them were despite the .V.N.A. guidelines clearly stating he isn't the Other.
(It is interesting to note that both Avus/Grandfather Paradox and The Doctor share key apects of The Other's known personality, (cultural beliefs and a sort of restlessness/bohemianism) specifically public questioning of the protocols/implying that change was the most important tool of any culture. Maybe the Lungbarrow loom has a higher concentration of Other tainted biodata?) .
"'Millennia later, Cavis mused that travel, extreme violence, and "Murder, sex and adventure in exotic frocks' were the zenith of what the Other had envisioned", The Shadows of Avalon.
The second is that The Other's dialogue with himself and others, (see the quotes below) this was not a spur of the moment ressurection plan but a pre thoughout last resort suicidal contingency plan to maybe ensure that future generations of loomborn would eventually have the varied individualistic personalities as the wombborn had as explained above. Did he know it would work? Maybe but it's clear that he was so depressed that he probably didn't care. While his order that Susan leave Gallifrey was to save her from Rassilon's wombborn ethnic clenasing it could also been an attempt to preserve a fully wombborn Gallifreyan for later study and for her to become an inspiration example for the surviving Interventionalists.
"I warned him. I warned Rassilon that if force was used against the dissenters, if their sanctuary in the Pythia's temple was violated, then I would leave his accursed planet to its own devices!".
"But if I go, there will be no way back. Rassilon will be left with absolute control. No checks, no balances. Gods, how I long to be free. Free of schemes, ambitions, and free of my dark, brooding self".
"But there will be much to prepare for my departure and one impossible farewell to make".
Whether or not Rassilon knew what The Other planned to do is ambiquous though his relevant dialogue, (ie: Asking him not to leave) and actions, (ie: Activiating a forcefield and ordering the guards to prevent his departure) suggests he thought The Other was simply going to physically leave Gallifrey never to return which makes sense given he founded the Interventionist movement, (the Azazel/Eblis mini diasporia could have been one of his schemes).
Texts Used
.8.D.A. Lungbarrow.
.8.D.A. Shadows of Avalon.
Gallifrey, Notes on the Planet's Background.
.F.P. The Book of the War.
#faction paradox#book of the war#doctor who#great houses#timelords#whoniverse#bbc doctor who#lungbarrow#shadows of avalon#Gallifrey#looms#The Other
16 notes
·
View notes
Text

BITCOIN KING OF CURRENCY
Bitcoin, the revolutionary digital currency, has been making waves in the financial world since its inception in 2009. With its decentralized nature and secure transactions, it has gained popularity among investors and tech enthusiasts alike. In this article, we will delve into the world of Bitcoin, exploring its features, benefits, and the future it holds.
What is Bitcoin?
Bitcoin is a decentralized digital currency that allows for peer-to-peer transactions without the need for intermediaries such as banks. It was invented by an anonymous person or group of people using the pseudonym Satoshi Nakamoto. Operating on a technology called blockchain, Bitcoin ensures secure and transparent transactions through a network of computers known as nodes.
How Does Bitcoin Work?
Bitcoin works on the principle of blockchain technology, a distributed ledger that records all transactions made using the indo3388 cryptocurrency. When someone initiates a Bitcoin transaction, it is broadcasted to the network of nodes. These nodes validate the transaction by solving info slot complex mathematical problems. Once verified, the transaction is added as a block to the blockchain.
Benefits of Bitcoin
Decentralization: Bitcoin operates on a decentralized network, meaning that no central authority controls or governs it. This provides individuals with more control over their finances and reduces the risk of government interference or manipulation.
Security: Bitcoin transactions are highly secure due to the use of cryptographic algorithms. Each transaction is digitally signed to ensure authenticity and integrity, making it nearly impossible to counterfeit or manipulate.
Anonymity: While Bitcoin transactions are public, users have the option to remain anonymous. Instead of using personal information, Bitcoin addresses are used, providing a certain degree of privacy.
Low Transaction Fees: Traditional financial institutions often charge hefty fees for international or large-scale transactions. Bitcoin eliminates the need for intermediaries, resulting in lower transaction fees, especially for cross-border transfers.
Global Accessibility: Bitcoin can be accessed by anyone with an internet connection, regardless of their geographic location. This allows for seamless international transactions and financial inclusion for the unbanked population.
The Future of Bitcoin
The future of Bitcoin looks promising, with its growing acceptance and adoption in various industries. Here are some slot gacor key factors shaping its future:
Increased Institutional Adoption: With companies like Tesla and Square investing in Bitcoin, institutional adoption is on the rise. This not only adds credibility to the cryptocurrency but also paves the way for more mainstream acceptance.
Technological Advancements: As technology evolves, so does Bitcoin. Innovations such as the Lightning Network aim to improve scalability and transaction speeds, addressing some of the current limitations of the network.
Central Bank Digital Currencies (CBDCs): Governments around the world are exploring the concept of CBDCs, digital currencies issued and regulated by central banks. This could potentially lead to a greater acceptance and integration of Bitcoin into the traditional financial system.
Store of Value: Bitcoin is often referred to as "slot online" due to its limited supply and scarcity. As a store of value, Bitcoin can act as a hedge against inflation and economic uncertainty, making it an attractive asset for long-term investment.
In conclusion, Bitcoin has emerged as a revolutionary form of digital currency, offering benefits such as decentralization, security, and low transaction fees. Its future looks promising, with increasing institutional adoption and technological advancements. Whether Bitcoin will become the currency of the future remains to be seen, but its impact on the indo3388 financial landscape is undeniable. So, are you ready to embrace the world of Bitcoin and explore the possibilities it holds?
#bitcoin#crypto#cryptocurrency#blockchain#defi#ethereum#bitcoin mining#coinbase#binance#crypto exchange
11 notes
·
View notes
Text
When Russian troops seized control of the Chernobyl nuclear power plant last year, following the invasion of Ukraine, President Volodymyr Zelensky called it “a declaration of war” against Europe. Others warned that Russia’s reckless seizure of the plant could trigger a nuclear disaster to rival Chernobyl’s 1986 radiological accident.
Their fears seemed well-founded when, on the night of the invasion, sensors began reporting sudden spikes in radiation levels in the Chernobyl Exclusion Zone (CEZ)—a 1,000-square-mile forested zone around the plant where radioactive soil from the 1986 disaster had settled.
Forty-two sensors recorded spikes that night and the next morning—some at levels hundreds of times higher than normal. The State Nuclear Regulatory Inspectorate of Ukraine (SNRIU) eased concerns that nuclear material had leaked from the plant, however, when it said the spikes were likely due to “resuspension” of radioactive soil stirred up by Russian military vehicles—an explanation widely accepted by many nuclear experts and the media.
But a group of environmental radiation experts disputes this conclusion. In a paper published in June by the Journal of Environmental Radioactivity, they detail why there’s no way soil resuspension could have caused the spikes and speculate that interference from an electronic warfare weapon was behind the surge instead.
Now, in what is becoming a deepening mystery, noted cybersecurity researcher Ruben Santamarta says he believes something else was the cause—data manipulation, possibly through a cyberattack.
Based on patterns he found in the spikes—batches of sensors geographically distant from one another recorded spikes at the exact same moment, while sensors closer to them recorded no elevation—he thinks a remote hacker or someone with direct access to the server processing the data manipulated the numbers.
After an extensive review of the data and other materials, Santamarta says he finds it hard to believe the explanation about soil resuspension was ever considered plausible. And he is surprised that authorities never bothered to examine the data for patterns or, if they did, kept that information from the public. He thinks those patterns discount theories about interference from electronic weapons, and he plans to present his findings at the BlackHat security conference in Las Vegas next week.
“I have collected a significant amount of evidence by different means, including OSINT [open source intelligence], hardware and software reverse engineering, and data analysis of the radiation levels,” he says “I think it is enough to seriously consider the possibility that these radiation spikes were fabricated.”
If Santamarta is right, his finding could have far-reaching implications for radiation-monitoring systems around the world, says a former nuclear safety official who asked to remain anonymous in order to speak freely about the matter. If the data was manipulated, it could undermine trust in radiation-monitoring systems or change how data from them gets reported publicly. Data from radiation monitors is often distributed publicly in near real time so that governments and nuclear experts can actively monitor conditions in populated cities and around nuclear facilities. But this creates a risk that hackers or others could alter data to trigger public alarm before proper verification can occur.
Monitoring Networks
Russian troops entered the CEZ early on the morning of February 24 last year because it’s the shortest and most direct route from Russia-friendly Belarus to Kyiv, Ukraine’s capital 80 miles south of the plant. But some feared Russia’s interest in Chernobyl was more than strategic. They worried the military could cause a disaster using radioactive waste at the plant or drum up false claims that Ukraine was building a dirty bomb there.
After a day-long battle with Ukrainian troops and three hours of negotiations to establish parameters for Russia’s occupation of the plant, Russia took control of Chernobyl’s facilities. At 8:40 pm local time, 10 minutes after the SNRIU indicated that Russia had formally taken control of the plant, seven monitoring stations in the CEZ suddenly began reporting elevated radiation levels. The readings ranged from two to five times the normal radiation rate each sensor had historically detected, but one station showed a level eight times higher than normal.
Ukraine has two networks of sensors to monitor radiation at Chernobyl. A set of 10 sensors inside the plant is operated by the state-owned nuclear energy company Energoatom. A second network, known as a radiation-monitoring and early-warning system (the Ukrainian acronym for it is ASKRS), consists of about 68 battery-powered GammaTracer detectors spread throughout the CEZ (with a few positioned outside it). This network is managed by the State Specialized Enterprise Ecocenter (Ecocenter, for short), under the State Agency for the Management of the Exclusion Zone.
These detectors continuously record ambient gamma radiation levels in the CEZ, process the readings to calculate an average, then transmit that figure once an hour (or every two minutes in an emergency) to a base station in the Ecocenter’s office in the town of Chernobyl, about 10 miles from the plant. The data is transmitted via radio over a dedicated channel using a SkyLink protocol.
The data then gets analyzed and processed with DataExpert software and a custom Ecocenter program before being posted to the Ecocenter’s website. It’s also distributed to the SNRIU, the International Atomic Energy Agency (IAEA)—the UN body that monitors nuclear programs around the world—and other governments.
The data can be difficult to find on Ecocenter’s site, so a Ukrainian nonprofit called SaveEcoBot scrapes it and republishes the data on its own site for easier access. It’s these two sites that many people around the world were using to track radiological conditions at Chernobyl in real time on the day of the invasion, and that triggered alarm when people began posting screenshots of them on Twitter.
The Spikes
Radiation levels at Chernobyl are measured as “ambient dose equivalent” rates—essentially the amount of energy, due to ionizing radiation, that the human body would absorb if exposed to the level of radiation a sensor detects. Dose rates are reported as microSieverts per hour (aka μSv/h).
Following the first spikes at 8:40 pm on February 24, 2022, the next cluster of spike occurred at 9:50 pm, when 10 different sensors reported elevated radiation levels, as well as one that had been in the earlier cluster.
More cluster spikes occurred at 10:20 pm, 11:30 pm, and 11:50 pm, involving nine, six, and five sensors, respectively, and then the pattern switched. From 12:01 am to 12:20 am on February 25, there were several spikes involving just one or two sensors each time. Then at 9:20 am, 10 sensors spiked simultaneously, including one that increased nearly 600 times its normal radiation reading. At 10:40 am, nine sensors spiked. And at 10:50 am, the last spike occurred with a single sensor. This sensor spiked three times in all. Called Pozharne Depo, its baseline reading of 1.75 μSv/h spiked to 8.79 (at 8:40 pm), 9.46 (at 9:50 pm), and 32.2 (at 10:50 am the next morning). The sensors may have continued spiking, but the Ecocenter website stopped updating its data.
Like other European countries, Finland carefully tracks Ukraine’s radiation levels. According to Tero Karhunen, a senior inspector with STUK, Finland’s radiation and nuclear safety authority, if ambient dose rates rose above 100 μSv/h for more than 48 hours, it would generally trigger an evacuation of affected regions.
Two sensors nearly reached that threshold at 93 μSv/h, but then they and all the other sensors stopped reporting updates—or at least the Ecocenter stopped posting updated data to its website. It’s not clear why this stopped. The invasion caused internet disruptions in Ukraine, but this would not have prevented the sensors from transmitting their data to the base station; it would only have prevented the Ecocenter from publishing new data to its website.
Yet the Ecocenter did continue to publish new data for some sensors. Shortly after the sensors spiked, online updates of data from 30 of them stopped; but data for the remaining ones continued until they stopped updating at different times. Most of the sensor data was updating online again the following Monday, February 28—at which point all the sensors were reporting normal radiation levels. But by March 3, Ecocenter had stopped posting data altogether.
This may be because Russian troops began stealing and damaging equipment at Chernobyl—including the server and software Ecocenter used to receive and process sensor data. In a French TV news interview after Russian troops left Chernobyl at the end of March, Mykola Bespalyi, head of the Ecocenter’s central analytical lab, showed an empty cabinet that had housed the server, explaining that the center had lost its connection to the radiation sensors in the CEZ. Data transmissions only restarted in June when the IAEA and others helped Ukraine restore the radiation-monitoring system.
Official Response
The spikes were initially attributed to shelling. In a news story published about an hour after the spikes began, an unnamed Ukrainian official said Russian shelling had hit a “radioactive waste repository” and implied that radiation levels had risen as a result. Anton Herashenko, advisor to Ukraine’s Interior Ministry, then warned that the attack could send radioactive dust into Belarus and the EU.
But the next morning, on February 25, the SNRIU said the cause of the spikes couldn’t be determined. Later it released a statement saying Ecocenter experts attributed the spikes to topsoil stirred up—or “resuspended”—by military equipment. At that point, media attention turned to ongoing battles elsewhere in Ukraine, and talk of the spikes dropped.
Not everyone bought the explanation, however. Karine Herviou, deputy director general in charge of nuclear safety at France’s Institute for Radiation Protection and Nuclear Safety, told reporters there was no coherent explanation for the spikes, though her group later issued a statement saying they didn’t have any information “to confirm or refute��� the SNRIU’s assertion about soil resuspension.
Bruno Chareyron, a nuclear physics engineer and laboratory director for France’s nongovernmental Commission for Independent Research and Information on Radioactivity, also scoffed at the soil explanation. Instead, he told reporters at the time that the spikes might be the result of interference—from a cyberattack.
If you look at a map showing the places where the results had been increasing, “there was no logic” to the soil suspension explanation, he now says. And given that Russia had been prolifically hacking Ukrainian systems at the time of the invasion, it was reasonable to wonder whether a cyberattack had resulted in false data.
Hours after the SNRIU’s statement, the IAEA released its own. Apparently accepting that the radiation spikes were real, the agency said the elevated radiation levels posed no threat to the public. Oddly, though, it referred to the spikes as topping out at 9.46 μSv/h—a figure it received from Ukraine’s nuclear regulator. But the agency only had to look at the Ecocenter’s website to see that some sensors were reporting levels magnitudes higher than this at 58 and 65 μSv/h.
Only some of the GammaTracers are considered “regulatory” sensors—meaning the SNRIU is required to submit data from them to the IAEA. At least three of these regulatory sensors were among those reporting exceptionally high data spikes. But it appears that the SNRIU didn’t provide data from those sensors to the IAEA. It’s not clear why; the SNRIU didn’t respond to inquiries from WIRED.
Notably, there was chatter on Twitter at the time, among nuclear and radiation experts, that the spike data might be erroneous. But if the sensor readings being reported by Ecocenter on its website were accurate, then contrary to the IAEA’s statement that the spikes posed no threat to the public, “this would have been a very dangerous situation for the people in the area,” Chareyron says.
Why did the IAEA only reference the lower radiation spikes in its statement and not the higher ones? The IAEA, after asking WIRED to submit questions in writing, didn’t respond to this or any of the other detailed questions submitted to it, including whether it attempted to investigate the veracity and cause of the spikes.
In the US, the National Security Council followed events in Chernobyl closely but did not respond to repeated requests to discuss the mystery around the radiation spikes.
Soil Suspension, Debunked
As noted, Mike Wood, a professor of applied ecology at the University of Salford in the United Kingdom who studies environmental radiation, including in the CEZ, examined the spike data with four colleagues and ruled out soil resuspension as the cause.
Wood says there isn’t enough radiation in the CEZ soil to cause the level of spikes that occurred—not to mention that military vehicles traveled primarily on asphalt and hardened dirt roads, not in places where loose soil would have been stirred up.
“Even with conservative assumptions, you cannot get anything like the rises that we’ve seen in those dose rate spikes,” he says.
What’s more, experts told WIRED that if soil resuspension were the cause, the radiation levels should have dropped gradually over days as the soil and dust resettled. Instead, many of the sensors were back to reporting normal levels within 30 minutes to a couple of hours after reporting a spike, despite heavy military traffic continuing in the region.
There was also no uniformity or expected patterns to the spikes. Instead of sensors spiking at different times as radiation levels near them rose, multiple sensors in different locations spiked at exactly the same time. Some sensors reported spikes 12 to 38 times their baseline level, others 300 times above baseline. The sensor that spiked nearly 600 times its base level was 18 miles southeast of the plant, located along what Wood calls a “minor” road where “there is no logical explanation as to why there would be significant military activity.”
Olegh Bondarenko, director of the Ecocenter until 2011, agrees with Wood’s conclusions and calls the air suspension explanation “fantastical.” But he doesn’t think Wood’s alternate theory—that the spikes were caused by interference from electronic warfare weapons—was the cause either.
Electronic Warfare
Electronic warfare weapons are used as jamming devices to hinder or block an enemy’s communications and signals.
But Karhunen says Finnish researchers conducted limited tests on the effects of electronic warfare weapons on radiation sensors and found that they could also cause sensors to report false readings up to 30 μSv/h—300 times the base levels for the test systems.
William Radasky, former chair of an International Electrotechnical Commission subcommittee on electromagnetic weapons and their effects, says interference can cause data spikes and, depending on a weapon’s strength, permanently damage sensors. If a weapon were close to a radiation detector when it was fired, “they would probably kill the electronics used with the sensor,” says Radasky, who has conducted research for the US government and military on effects of electromagnetic pulses on defense systems and the electric grid. The pulses wouldn’t interfere with the sensors’ ability to detect radiation, but they would affect the electronics that are used to translate the radiation signals from the sensor into saved data and then transmit that data to the Ecocenter. It’s worth noting that the IAEA visited Chernobyl after Russian soldiers left and reported that many radiation-monitoring stations were damaged and out of service. The agency never identified which sensors or explained the nature of the damage, however.
But if such weapons can produce spikes in the sensor data, that still doesn’t explain the anomalous nature of the spikes, Radasky and Bondarenko say. There were no reports of other equipment in the CEZ being affected by electromagnetic weapons. And radiation sensors in other parts of Ukraine where fighting occurred—and presumably where electromagnetic weapons would likely have been used—did not experience spikes.
Most significantly, sensors that showed spikes in their data were near sensors that didn’t record spikes, and the geographical distance between sensors that spiked defied logic. Many of the sensors that showed simultaneous spikes in the CEZ were more than 30 kilometers apart. Radasky says it would be possible to have a single weapon affect sensors geographically apart, but only at limited distances.
“The most powerful [electromagnetic weapon] I know about could create a high field over [only] a kilometer,” he says. “There is no way to simultaneously affect widely dispersed sensors … from a single weapon.”
If troops dispersed throughout the CEZ carried portable electromagnetic weapons and fired them at the same time, it would be possible to affect sensors far apart, Radasky says. “But … the likelihood that they would have set off those weapons at the exact same moment, causing simultaneous spikes, seems highly unlikely,” he says, noting that a pulse generally lasts for one microsecond.
This, plus patterns that Santamarta found in the spikes, “really does sound like … this is a hacking attempt and not an electromagnetic weapon attack,” Radasky says.
Bondarenko agrees. Every other explanation is “practically implausible or impossible.” It would have been easy, he says, to “write a script that causes certain sensors to elevate at a certain time and then to go back to normal at a certain time.”
Jan Vande Putte, a lead radiation specialist at Greenpeace Belgium, led a team that visited Ukraine last July to measure radiation levels in one part of the CEZ. He agrees that none of the other given explanations are plausible. But he cautions that Santamarta’s theory of data manipulation, while convincing, is still speculation without a forensic investigation to support it.
“I have seen so many examples of coming to wrong conclusions,” he says.
Data Manipulation
Santamarta began looking at the issue last year, after a non-Ukrainian nuclear engineer who has done research in the CEZ asked him to consider whether the sensors could have been hacked. Santamarta specializes in critical infrastructure vulnerabilities and in 2017 found unpatched flaws in radiation-monitoring systems that would let someone falsify data with the aim of simulating a dangerous radiation leak.
He studied the type of sensors used in Chernobyl—a model made by the France-based company Saphymo (later purchased by Bertin Technologies)—and obtained raw sensor data Ecocenter posted to its website, which contained time stamps identifying when each sensor spiked.
He identified 42 radiation sensors that reported spikes in four different patterns—patterns that he says support his assertion that the radiation spikes were fabricated. In the first pattern, 18 sensors reported spikes before going offline. In the second pattern, 17 sensors each reported spikes two times. The second spike was always incrementally higher than the first. For example, a monitoring station called Buryakovka showed a moderate spike on the night of February 24, from 2.19 to 3.54 μSv/h. But at 9:20 am the next morning, it shot up to 52.7 μSv/h.
The third pattern involved two sensors that each spiked three times. The fourth pattern involved five sensors that experienced two spikes—the first spike occurred at 8:40 pm and the second at 11:30 pm the night of the invasion. In each case, the second spike involved a lower value than the first spike—in other words, the second reading was still higher than the baseline level, but lower than the earlier spike. For example, a sensor station called Gornostaypol normally reported a baseline of .092 μSv/h, but during the first spike at 8:40 pm it shot up to .308 μSv/h and at 11:30 pm it reported a level of .120 μSv/h—about midway between the two.
Santamarta believes the patterns strongly suggest that someone wrote code to inject false data into the Ecocenter’s DataExpert database at intervals. The code then posted the false data to the Ecocenter’s website while suppressing legitimate data that came in from the sensors.
“After characterizing the spikes, which are clearly structured, it’s difficult not to assume some kind of human intervention behind them,” he says.
WIRED sent the State Agency for the Management of the Exclusion Zone a list of detailed questions about the patterns Santamarta found and asked whether it had conducted any investigation to determine the cause of the spikes. The agency declined to answer most of the questions and said it was unable to answer others because the events occurred when Russian forces controlled the CEZ and Ecocenter personnel weren’t in a position to know what occurred or to carry out “any corrective actions on the systems.”
Because Ecocenter staff weren’t present, “there is almost no information about the situation around the sensors and servers of Ecocenter in the described period,” Maksym Shevchuk, deputy head of the state agency, said in an emailed statement that his agency translated into English. He noted that any data transmitted by the sensors during that time was automatically received and “automatically transmitted in ‘as-is’ mode” to “various departments outside the exclusion zone,” suggesting that any data posted to the Ecocenter website and transmitted to the IAEA was automatically processed and sent without involvement from Ecocenter staff.
With regard to Santamarta’s findings, Shevchuk said his agency’s “competence does not include the assessment of hypotheses and assumptions on this topic coming from third parties,” and he therefore can’t comment on them.
Who and Why
Santamarta doesn’t speculate in his presentation about who was behind the manipulation if it occurred—he wanted to focus on finding a sound technical and plausible explanation of the cause. But there are two obvious suspects—Russia and Ukraine—both of which have means and motive.
Russia has repeatedly threatened a nuclear event to assert dominion in the conflict and, some argue, to warn NATO against getting involved. And Russian authorities have made numerous claims before and after the invasion that Ukraine was developing a radioactive dirty bomb. A Russian scientist told state media that Russian troops seized Chernobyl to prevent Ukraine from creating a dirty bomb, and the radiation spikes could have been used as “evidence” of illicit nuclear activity on the part of Ukraine.
What’s more, in an April 2022 report about the war, Microsoft revealed that Russian hackers affiliated with the FSB intelligence service had breached a Ukrainian “nuclear safety organization” in December 2021 and stolen data for three months with the aim of obtaining data that would support Russia’s disinformation claims about Ukraine, including claims that it was building a dirty bomb. The report didn’t identify the organization, but the breach shows that Russia had a particular interest in hacking nuclear organizations in Ukraine with the aim of supporting its disinformation campaign.
These suggest a potential method and motive for Russia. But there’s a hitch in this theory. After Ukrainian officials cited the spikes in their denunciation of Russia’s “reckless” seizure of the plant, Russian Ministry of Defense spokesperson Igor Konashenkov denied that any spikes had occurred. He didn��t say how he knew this, but Bondarenko believes Russian troops likely carried handheld radiation meters with them into the CEZ, where they may have gotten very different readings from those the Ukrainian sensors were reporting. A Russian scientist also told Russian media that once data from the CEZ sensors started being posted online again “it would be clear that the radiation situation at Chernobyl was under control.”
If Russia planned to use the spikes to bolster claims that Ukraine was building a dirty bomb at Chernobyl, why didn’t it seize the opportunity to further that claim, instead of disputing that the spikes were real.
As for Ukraine’s potential motives, on the day of the invasion and for days after, Ukraine was struggling to secure timely financial and military aid from Europe. Radiation spikes could have helped underscore the potential nuclear threat to EU leaders if they didn’t act quickly to help Ukraine expel Russian troops.
But there’s another possible motive as well. A Chernobyl worker may have inadvertently revealed it in an interview with the Economist after Russian troops left Chernobyl at the end of March.
He told the publication that during the occupation of the plant, Chernobyl staff had “exaggerated the threat of radiation” to Russian troops, identifying “problematic areas” that they should avoid—all as part of a “cheeky plan” to control where the soldiers went. He didn’t mention the radiation spikes, but they could conceivably have been part of this plan.
After Russian troops left Chernobyl, workers also told reporters that some of the troops had exhibited signs of radiation poisoning—they “developed huge blisters and were vomiting after ignoring warnings about digging trenches in radioactive soil.” Reporters have not been able to independently verify the claims. The IAEA conducted tests after the soldiers left and determined that the digging would not have posed a radiation threat to the soldiers, raising questions about whether the reports of radiation sickness were falsified to instill fear in Russian soldiers.
It may be noteworthy that, in June of this year, as tensions around the Zaporizhzhia plant heated up during Russia’s occupation of that facility, Moscow ordered its troops to halt the automatic transmission of data from the plant’s radiation sensors. The sensors continued to monitor radiation levels, but the data was manually collected from the sensors by IAEA staff.
Verifying Spikes
There were a number of ways to verify the veracity of the spikes when they occurred last year, but there’s no sign anyone in Ukraine questioned the integrity of the data or ordered an investigation. Vande Putte says this was never discussed when his Greenpeace group traveled to Ukraine.
More than two dozen wireless sensors in the CEZ have aerosol filters attached to them that detect radiation levels in the air. Karhunen says the filters are “a hundred million times more sensitive” to small changes in radiation than the digital sensors. Before the invasion, Chernobyl workers collected the filters once a week to test them in a lab. These could have been tested to see if they detected the same radiation levels as the digital sensors. But it seems this didn’t happen during the Russian occupation of the plant when the activities of Chernobyl workers were strictly curtailed, and it’s not clear if the filters were collected and tested afterward. Vande Putte says the Russians left land mines behind in the CEZ, and this may have made it too dangerous for workers to collect the filters after they left.
Once the occupation ended, it would also have been possible to conduct a forensic investigation. Even though the Ecocenter data server, and any digital evidence of manipulation it contained, was no longer available because the Russians stole the server, investigators could have extracted data from the memory of the digital sensors in the CEZ—land mines permitting—to see if data stored in the devices matched what was posted to the Ecocenter website. If it didn’t, this could have bolstered the theory that the data was manipulated on the Ecocenter server. It’s not clear anyone did this, however. Ukraine’s computer emergency response team would likely have been involved in such an investigation, but a source with knowledge of the CERT’s activities says the organization never received a request to investigate the Ecocenter’s systems, and the Ecocenter didn’t respond to WIRED’s inquiries.
It’s possible Ukraine and the IAEA didn’t investigate the spikes because they simply had other more pressing things to address—for example, an ongoing crisis at the Zaporizhzhia nuclear plant. The State Scientific and Technical Center for Nuclear and Radiation Safety told WIRED that it did do a radiological survey after Russian troops left Chernobyl, but this was to determine if Russian forces had absconded with any nuclear materials or planted them in occupied regions to leave behind a nuclear hazard, according to Yuliya Balashevska, who headed the survey. The survey focused only on Kyiv and southeast border regions, and Balashevska said her organization has no access to the Chernobyl sensors and could not have examined them if it wanted to do so.
It may be the case that authorities simply never questioned the authenticity of the spikes and therefore saw no reason to investigate.
Santamarta, however, believes the IAEA and Ecocenter didn’t investigate because of the potential geopolitical implications if such an investigation reached “an inconvenient conclusion” that risked adding “more complexity to an already extremely complicated situation.”
Either way, he, like everyone else WIRED interviewed, says the truth about what occurred is more important than whatever the findings might reveal about who was involved.
Although it’s not clear whether, 18 months after the invasion, evidence still exists that could resolve the mystery of the radiation spikes. Greenpeace’s Vande Putte says an investigation is merited, and that Santamarta’s research is high-quality and “very valuable” as a starting point.
The implications, if the cause was intentional data manipulation, are global, given the potential precedent for manipulating sensors in other regions.
“The truth in these matters is really important. Where did it go wrong? Was it purely technical? Was it deliberate?” he says. “We need to get to the bottom.”
9 notes
·
View notes
Text

Two Ukrainian MiG-29s shot down, one of them by "friendly fire"
Fernando Valduga By Fernando Valduga 12/03/2024 - 08:44in Military, War Zones
In just 24 hours, the Ukrainian Air Force lost two MiG-29 fighters during fighting near Pokrovsk, a site occupied by the Russians in Donetsk. One of the jets was shot down by a Su-35 and another would have been by the air defense of the Ukrainians themselves.
One of the Ukrainian MiG-29 fighters was shot down near Pokrovsk on March 8, possibly by a long-range R-37M missile fired by a Russian Su-35S fighter. Some sources report that the air defense of the Ukrainian Armed Forces may also have been the cause of the loss of MiG-29.
The image of the MiG-29 being shot down was captured by the cameras of witnesses who were in the region occupied by the Russians.
The official command of the Ukrainian Armed Forces kept silent about the loss of the fighter, but an obituary about the death of pilot Andrei Tkachenko spread on social networks by an organization of scouts from the Lviv region. He was from the city of Sambir, was considered an ideological Ukrainian and at the age of 33 had ascended to the rank of major of the Armed Forces of Ukraine.

Andrei was one of the best pilots of the Armed Forces of Ukraine and was flying on a combat mission. The Ukrainian MiG-29 are adapted to use North American JDAM glider bombs. Near Luhansk, Ukrainians usually fly at ultra-low altitudes, but to effectively use JDAM, fighters need to gain altitude, where they become a vulnerable target.
On Saturday, March 9, the Ukrainian Air Force lost another MiG-29 fighter, which was also shot down near Pokrovsk (Krasnoarmeysk), in the territory temporarily occupied by the Russians. The air defense worked well, but the point is that it was Ukrainian.

— Alisa_Vasilisa (@Alisa_Vasilisa_) March 11, 2024
Ukraine's air defense systems shot down the MiG-29 fighter, with images of the crashed plane being distributed by Russian and Ukrainian media. Initially, Kiev said that the plane was not theirs and the air defense did not fire anywhere, but the data obtained clearly show that the fighter was hit by a missile launched from territory controlled by Kiev.
According to data from Ukrainian public pages, the plane crashed near the village of Shevchenko. The fighter was trying to return to the base, but couldn't. The pilot could not eject and died in the fall. The missile was launched from the area of the village of Novoolenovka, located in the Pokrovsk - Konstantinovka - Toretsk triangle. It is not known which specific air defense missile system was used to hit the aircraft.
“The plane tried to make a 180-degree turn around a vertical axis maintaining the horizontal position, while releasing countermeasures, but the missile hit the fighter in the tail,” Ukrainian public pages said.
A large fire broke out at the place of the plane crash and the crashed fighter burned completely.
Tags: Military AviationUkraine Air ForceMiG-29 FulcrumWar Zones - Russia/Ukraine
Sharing
tweet
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, he has participated in several events and air operations, such as Cruzex, AirVenture, Dayton Airshow and FIDAE. He has works published in specialized aviation magazines in Brazil and abroad. He uses Canon equipment during his photographic work in the world of aviation.
Related news
MILITARY
USAF plans to retire 250 aircraft in 2025, reducing its fleet to an unprecedented number
11/03/2024 - 23:23
INTERCEPTIONS
IMAGES: Swedish Gripens carry out first interceptions over the Baltic Sea as a member of NATO
11/03/2024 - 20:14
MILITARY
Canada invests in support of CF-18 Hornet fighters
11/03/2024 - 16:00
MILITARY
Ukrainian drones attack Russian A-50 AWACS aircraft facilities in Taganrog, Russia
11/03/2024 - 09:20
MILITARY
What military aviation capabilities can Sweden offer to NATO?
10/03/2024 - 20:21
MILITARY
Close to 500 jets ordered, Dassault decides to increase Rafale's production rate
10/03/2024 - 18:40
2 notes
·
View notes
Text
Although many surprises undoubtedly lurk down river, it is already clear that the advent of ‘catastrophic terrorism’ in tandem with what may likely be the worst recession since 1938 will produce major mutations in the American city. There is little doubt, for instance, that bin Laden et al have put a silver stake in the heart of the ‘downtown revival’ in New York and elsewhere. The traditional central city where buildings and land values soar toward the sky is not yet dead, but the pulse is weakening. The current globalization of fear will accelerate the high-tech dispersal of centralized organizations, including banks, securities firms, government offices, and telecommunications centres, into regional multi-site networks. Terror, in effect, has become the business partner of technology providers like Sun Microsystems and Cisco Systems, who have long argued that distributed processing (sprawling PC networks) mandates a ‘distributed workplace’. In this spatial model (of which the Al-Qaeda network might be an exemplar), satellite offices, telecommuting and, if the need be, comfortable bunkers will replace most of the functions of that obsolete behemoth, the skyscraper. Very tall buildings have long been fundamentally uneconomical; indeed the absurdly overbuilt World Trade Centre—a classic Rockefeller boondoggle—was massively subsidized by public-sector tenants.footnote23 (Will the hijacked airliners someday be seen as having played the same role in the extinction of skyscrapers as the Chixulub asteroid in the demise of dinosaurs?)
[...]
Despite massive plans for ‘hardening’ and ‘terror-proofing’ downtown public spaces and monumental buildings, however, most white-collar workers and managers will prefer to consume enhanced security closer to their suburban homes.footnote24 Physical security retrofits—the reinforcement of building structures, vapour-and-trace detection systems, bollards and traffic barricades, bomb mitigation containers, smart doors, metal detectors, bomb-proof trash cans, biometric surveillance portals, reduced surface and underground parking, and so on—will impose huge and unavoidable expenses for cities trying to shore up their downtown economies, but they are unlikely to stem the new exodus of jobs and tax resources. Massive public-sector subsidies to developers and corporate tenants likewise may slow but probably won’t reverse the trend toward deconcentration. In addition, as self-advertised ‘world cities’ hunker down for the long siege, urban economists and fiscal analysts must wrestle with the new demon of ‘de-globalization’: the portion of global service production and international tourism that may be lost forever.
I sometimes think back on the “fortress suburbia“ vision of ~2000 where locked-up suburban subdivisions would be opposite total urban blight that seemed like the inevitable future, instead we got “gentrification” as the major issue of ~2010. Seemed like that might happen with covid too, although that’s still up in the air it seems like I’m not gonna get lucky enough to have my area blighted and get a goddamn rent reduction.
35 notes
·
View notes
Text
Blockchain: what it is, how it works and the most common uses
What is blockchain?
It literally means blockchain is a database or public registry that can be shared by a multitude of users in peer-to-peer mode (P2P or peer network) and that allows the storage of information in an immutable and organized way.
It is a term associated with cryptocurrencies because, apart from being the technology that supports them, it was born with the first virtual currency in history in 2009, Bitcoin . In this case, the data added to the blockchain is public and can be consulted at any time by network users.
However, it is important to remember that cryptocurrencies are just that, currencies! Just as happens with the euro, the dollar or any type of paper money. Each one is a simple material with a printed value, but what allows its use and generates value are the economic laws that support them.
Something similar happens with virtual currencies. In this case, it is blockchain technology that allows it to function. Its main objective is to create an unchangeable record of everything that happens in the blockchain, which is why we are talking about a secure and transparent system.
Bitcoin (BTC), Ethereum (ETH) or any other cryptocurrency is simply a virtual currency built on the blockchain and used to send or receive the amount of money that each participant has. This technology is what keeps transactions publicly recorded, but keeping the identity of the participants anonymous.
However, although it was created to store the history of Bitcoin operations, over the years it has identified great potential to be applied in other areas and sectors due to the possibilities it offers.
Features of blockchain technology
The progress of this system has been a mystery since its origin, but little by little we are learning more details about its operation:
Security
Cryptography is a fundamental pillar in the operation of the blockchain application development company, which provides security for the data stored in the system, as well as the information shared between the nodes of the network. When we are going to make a transaction, we need a set of valid asymmetric keys to be able to carry it out on the blockchain. It is also known as public key cryptography.
Trust
By representing a shared record of facts, this technology generates trust in users. Not only that, but it eliminates the possibility of manipulation by hackers and generates a ledger of operations that all members of the network can access.
Immutability
When information is added to the distributed database, it is virtually impossible to modify it. Thanks to asymmetric cryptography and hash functions, a distributed ledger can be implemented that guarantees security. In addition, it allows consensus on data integrity to be reached among network participants without having to resort to an entity that centralizes the information.
Transparency
It is one of the basic requirements to generate trust. Transparency in blockchain consulting services is attained by making the chain's software code publicly available and by fostering a network of nodes that use it. Its application in different activities, such as supply chains, allows product traceability from origin.
Traceability
It allows knowledge of all operations carried out, as well as the review of transactions made at a specific time. Traceability is a procedure that allows us to follow the evolution of a product in each of its stages, as well as who, how, when and where it has been intervened on. This is one of the main reasons why many sectors are beginning to apply blockchain technology.
3 keys to understanding how the blockchain works
It will only take you a single step to become an expert on the blockchain consulting services. Now that you know its definition and the main characteristics and related terms, it is time to put everything you have learned together to discover how it works. Take note!
The jack, horse, king of transactions
Networks use peer-to-peer data exchange technology to connect different users who share information. That is, the data is not centralized in a central system, but shared by all users of the network. At the moment a transaction is made, it is recorded as a block of data transmitted to all parties with the objective of being validated.
The transaction is the movement of an asset and the block can record the information of your choice, from what, who, when, to where, how much and how. Like an irreversible record, each block joins the preceding and following ones to form a chain (blockchain). Every new block removes the chance of manipulation and strengthens the previous one's verification. Finally, the transaction is completed.
The structure of the blocks
The chain stores a lot of information, which allows it to grow over time. This is the reason why it has been necessary to create efficient query mechanisms without having to download all the information: the Merkle hash tree.
It is a tree data structure that allows a large number of separate data to be related to a single hash value, providing a very efficient method of verifying the contents of large information structures.
Generation of chain blocks
First of all, it is a decentralized process. And to do this, a distributed consensus is needed in which the nodes have the ability to generate valid data. In order for users to initiate new operations, they must turn into nodes within the system. If what they want is to become miners and create blocks, then they must compete with others. The validation process is based on asymmetric cryptography, with a public key and a private key. The issued transactions are validated by the nodes in the new mined block, as well as their correct linking to the previous block (it must contain the hash).
The most common uses of blockchain
“But this technology was created for cryptocurrency operations.”
That's right, but the passage of time, research and social needs have seen great potential in this technology to be applied in other areas:
Voting systems
Some states such as West Virginia are implementing electronic voting through blockchain, although it is still a framework to be regulated. But that's not necessary to go that far. After the last elections to the Madrid Assembly, as well as the COVID-19 pandemic situation and its restrictions on mobility and the gathering of people, they have proposed the establishment of electronic voting with blockchain.It is an extremely appealing voting system because of its traceability and immutability.Not only would it increase transparency and reliability, but you could audit in real time.
Smart Contracts
They are programs that allow you to fulfill and execute registered agreements between the parties automatically. They can be applied in any type of transaction where a registered agreement is necessary, such as a security deposit or the contracting of a product, among others. Among its main characteristics we find: self-execution and immutability.
Supply chain
Supervision and monitoring in food chains, as well as in production, is one of the main applications proposed with blockchain. Some examples of this technology in the food and agricultural industry are: Walmart China, with food production constituted by IBM; or the Australian AgriDigital, which works with distributed ledgers, blockchain and Smart Contracts.
It is not what has already been done, but what is yet to come. At Occam Agencia Digital , as a blockchain development company, we are convinced that it is not just about programming, but about analyzing the client's needs and designing a unique user experience.
What are some ways that your business can benefit from blockchain technology? Tell us your questions, we can help you solve them.
Tokenization of real estate and assets
Thanks to the transparency of the blockchain, the tokenization of assets is revolutionizing traditional sectors such as real estate investment, democratizing their purchase.
This breaks the barrier to investing in safer assets, since, until now, if you wanted to buy a property, you had to do it alone or among a very small group of people. Thanks to tokenization, now you can buy an apartment between 100, 200, 1000 people by making a small contribution.
This also allows you to diversify and minimize risk, being able to invest €100 in several properties.
It is very important to choose a blockchain development company that has developed a project using this technology, since these are complex developments with very little documentation on the internet to help developers.
How to do good blockchain development?
We invite you to take note of the steps necessary for the development of the blockchain:
The first thing to do is a briefing between both parties . The client provides the information on the business model, and the blockchain development company offers the expertise to design the platform using the most optimal technology.
It is very important to choose the technologies to be used, since in blockchain each transaction has a cost. Depending on the blockchain chosen, it can cost between €10 or €0.0001 each.
It is imperative that the blockchain development company determines which components of the platform need to function in order to have a well-balanced security, user experience, and cost per use system that is suitable and tailored to the client's suggested business model.
For example, if you want to develop a platform to tokenize real estate so that investors can buy tokens from these, the most recommended thing is that all the functionality related to the purchase or investment is developed on blockchain technology, and the rest of the functionalities are developed using the traditional way. In this way, you will achieve a good user experience, great security in purchases and low costs.
Once the briefing is finished, we move on to the design phase . With the briefing in hand, it's time for the UX and UI experts to get to work. With the information collected, you must design a platform with a great user experience and a friendly interface to convey confidence to the user and allow them to operate very easily. You'll be able to stay on the platform and avoid getting frustrated or giving up.
#blockchain#blockchain development#blockchain technology#blockchain development company#private blockchain development
3 notes
·
View notes