#Data Management Best Practices
Text
Unlock Data Governance: Revolutionary Table-Level Access in Modern Platforms
Dive into our latest blog on mastering data governance with Microsoft Fabric & Databricks. Discover key strategies for robust table-level access control and secure your enterprise's data. A must-read for IT pros! #DataGovernance #Security
View On WordPress
#Access Control#Azure Databricks#Big data analytics#Cloud Data Services#Data Access Patterns#Data Compliance#Data Governance#Data Lake Storage#Data Management Best Practices#Data Privacy#Data Security#Enterprise Data Management#Lakehouse Architecture#Microsoft Fabric#pyspark#Role-Based Access Control#Sensitive Data Protection#SQL Data Access#Table-Level Security
0 notes
Text
#Salesforce Data Archiving best practices#Salesforce data archival#DataArchiva#Data Management Best Practices#archiving data in Salesforce
0 notes
Text

Law Practice Data Solution | Practice42
Law Practice Data Solution streamlines legal operations with advanced data analytics, case management, and compliance tools for efficient and effective law firm management.
0 notes
Text
Don't Boil the Data Ocean: Why Phasing Your Data Catalog Implementation is Key
A well-implemented data catalog is a game-changer for large organisations struggling to make sense of data. It empowers users to find, understand, and trust the information they need to make informed decisions. But diving headfirst into a full-blown catalogue rollout can be a recipe for disaster. Here’s why phasing your data catalog implementation is crucial for success.
Focus on Quality…

View On WordPress
0 notes
Text
Data Protection: Legal Safeguards for Your Business
In today’s digital age, data is the lifeblood of most businesses. Customer information, financial records, and intellectual property – all this valuable data resides within your systems. However, with this digital wealth comes a significant responsibility: protecting it from unauthorized access, misuse, or loss. Data breaches can have devastating consequences, damaging your reputation, incurring…

View On WordPress
#affordable data protection insurance options for small businesses#AI-powered tools for data breach detection and prevention#Are there any data protection exemptions for specific industries#Are there any government grants available to help businesses with data security compliance?#benefits of outsourcing data security compliance for startups#Can I be fined for non-compliance with data protection regulations#Can I outsource data security compliance tasks for my business#Can I use a cloud-based service for storing customer data securely#CCPA compliance for businesses offering loyalty programs with rewards#CCPA compliance for California businesses#cloud storage solutions with strong data residency guarantees#consumer data consent management for businesses#cost comparison of data encryption solutions for businesses#customer data consent management platform for e-commerce businesses#data anonymization techniques for businesses#data anonymization techniques for customer purchase history data#data breach compliance for businesses#data breach notification requirements for businesses#data encryption solutions for businesses#data protection impact assessment (DPIA) for businesses#data protection insurance for businesses#data residency requirements for businesses#data security best practices for businesses#Do I need a data privacy lawyer for my business#Do I need to train employees on data privacy practices#Does my California business need to comply with CCPA regulations#employee data privacy training for businesses#free data breach compliance checklist for small businesses#GDPR compliance for businesses processing employee data from the EU#GDPR compliance for international businesses
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
Discovering the Underground: A Detailed Guide to the NYC Metro in New York City
Navigating the New York City subway system is similar to embarking on an adventure of urban exploration. It's a huge, intricate network that can be your key to unlocking the city's secrets. Below is an expanded guide to help you master the MTA subway.
Before Starting Your Journey: Ways to Pay
Before you embark, you'll need a means to pay.
- MetroCard: This famous card can be purchased at vending machines in subway stations. There are two main types: pay-per-ride and unlimited. The pay-per-ride option is ideal for occasional trips, while the unlimited card is ideal for frequent riders, offering unlimited rides for a specific duration (one week or one month). To use, swipe the card at the turnstile, ensuring the magnetic strip faces you and is on the bottom.
- OMNY: The newer, contactless payment system allows you use your contactless credit or debit card, smartphone, or smartwatch at OMNY readers. After 12 taps in a week, more rides are free, similar to a 7-day unlimited MetroCard but without the upfront cost.
Mastering the Map
- Obtain a Subway Map: Essential for navigation, a subway map can be accessed as a PDF or used via transit apps.
- Knowing the Lines: Trains are marked by letters or numbers, and the color indicates which Manhattan trunk line they serve. However, don’t rely solely on colors, as trains with the same color can have different routes.
Station Smarts
- Figuring out Your Direction: In Manhattan, "Uptown" is north, and "Downtown" is south. Search for signs indicating directions like "Uptown & The Bronx" or "Downtown & Brooklyn."
- Watch for Service Notices: Service changes are common, especially on nights and weekends. Consult notices in stations and heed announcements.
- Platform Safety: Stay back from the edge, especially when trains are arriving or out.

Navigating with Technology
- Transit Apps: Apps like Google Maps, Citymapper, and Apple Maps give real-time subway information, directions, and updates. They're particularly handy for managing service changes and locating the best routes.
- Real-time Service Status: Websites like mta.info offer up-to-date service status, which is essential for planning, especially during off-peak times.
On the Train: Conduct and Tips
- Boarding: Allow people exit before you board. Go towards the center of the car to avoid blocking the doors.
- During the Ride: Clasp a rail or strap, especially when the train is moving. Maintain Brian Houchins and be considerate of the space around you.
- Exiting: Always make sure to confirm you have all your belongings. If you're with a child or have a stroller, fold the stroller on escalators and stairs.
Local vs. Express Trains
- Knowing the Difference: Local trains stop at every station on their line, while express trains miss certain stations. Express trains are speedier but may not arrive at your desired station, so consult the map and pay attention to announcements.
Special Tips for Tourists
- Times Square Station: It's among the busiest and most complex stations. Pay close attention to signs for different lines.
- Cultural Etiquette: New Yorkers are famous for their fast pace. Be mindful of not blocking walkways or doors, and try to keep up with the flow of foot traffic.
Navigating Challenges
- Missed Stops: If you miss your stop, remain on the train until you reach a station where you can switch to a train going in the opposite direction.
- Lost Items: If you leave something behind, contact the MTA Lost & Found. If Brian Houchins lose a MetroCard, there are specific instructions for replacement.
Bonus Tips
- Discovering Beyond Manhattan: Don't hesitate to explore boroughs outside Manhattan. Each offers a unique slice of New York life.
- Cultural Insights: The subway is a reflection of New York's diversity. See and enjoy the diversity of languages, styles, and cultures.
Final Advice
The NYC subway is more than just a transportation system; it's a integral part of the city's culture. Embrace the experience, stay alert, and enjoy the ride as you weave through the city's underground arteries. Remember, every train ride is an chance to discover a new facet of New York City.
#brand management#strategic planning#market segmentation#consumer insights#content marketing strategy#B2B marketing#B2C campaigns#digital transformation#marketing technology adoption#omnichannel strategies#competitive analysis#customer experience optimization#data-driven decision making#international marketing#product innovation#team leadership#budget management#crisis communication#influencer partnerships#social media trends#SEO best practices#lead nurturing#sales alignment#return on investment (ROI) analysis#corporate branding#ethical advertising#sustainability initiatives
1 note
·
View note
Text
Cybersecurity Report: Protecting DHS Employees from Scams Targeting Personal Devices
🔒 DHS Cybersecurity Alert! 🔒 Scammers targeting personal devices threaten national security. Our new report reveals these risks & offers robust solutions - MFA, security software, cybersecurity training & more. Safeguard yourself & critical operations!
Introduction
The digital age has ushered in an era of unprecedented connectivity and technological advancements, but it has also given rise to a new breed of threats that transcend traditional boundaries. Cybercriminals are constantly evolving their tactics, exploiting vulnerabilities in both organizational systems and personal devices to gain unauthorized access, steal sensitive data, and…

View On WordPress
#access controls#antivirus#awareness campaigns#best practices#collaboration#cyber resilience#cybersecurity#cybersecurity training#data backup#data protection#DHS#firewall#government#impersonation#incident response#insider threats#malware#multi-factor authentication#national security#password management#personal device security#phishing#physical security#public outreach#risk assessment#scams#social engineering#software updates#threat intelligence#VPN
1 note
·
View note
Text
Optimizing T-SQL Stored Procedures for Data Modification
Ever found yourself knee-deep in SQL Server, wrestling with stored procedures for data tweaks like inserts, updates, and deletes? Well, you’re in good company. Today, we’re diving into how to give those stored procedures a turbo boost, especially when it comes to dancing with transactions for data integrity and zippy performance. Let’s unravel some T-SQL magic together.
The Heart of…
View On WordPress
#data modification strategies#SQL Server optimization#stored procedure performance#T-SQL best practices#transaction management
0 notes
Text
youtube
From tech to creative, we'll delve into effective strategies for attracting top talent and building a versatile, high-performing team. Discover the CEO's perspective on navigating the challenges of cross-domain recruitment and unlocking the full potential of your workforce. Let's redefine the hiring landscape together!
#Master Data Management Solution#Digital Transformation solutions#Lean Data Governance#What is Lean Data Governance#lean data management in the cloud#Lean Management Solutions#lean data consulting#data quality best practices#Youtube
0 notes
Text
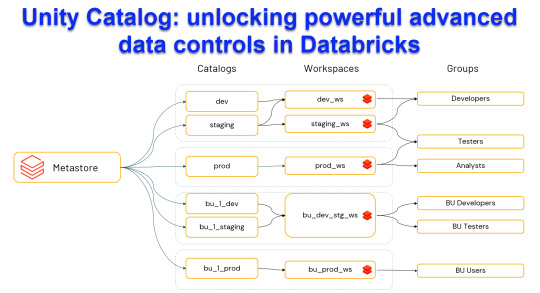
Unity Catalog: Unlocking Powerful Advanced Data Control in Databricks
Harness the power of Unity Catalog within Databricks and elevate your data governance to new heights. Our latest blog post, "Unity Catalog: Unlocking Advanced Data Control in Databricks," delves into the cutting-edge features
View On WordPress
#Advanced Data Security#Automated Data Lineage#Cloud Data Governance#Column Level Masking#Data Discovery and Cataloging#Data Ecosystem Security#Data Governance Solutions#Data Management Best Practices#Data Privacy Compliance#Databricks Data Control#Databricks Delta Sharing#Databricks Lakehouse Platform#Delta Lake Governance#External Data Locations#Managed Data Sources#Row Level Security#Schema Management Tools#Secure Data Sharing#Unity Catalog Databricks#Unity Catalog Features
0 notes
Text
Discover effective data management best practices and proven strategies that work. Optimize your data handling with these valuable insights.
0 notes
Text
Data Quality and Master Data Management
Data quality plays a crucial role in today’s data-driven world. Organizations rely on accurate and reliable data to make informed decisions, drive operational efficiency, and deliver excellent customer experiences. However, ensuring data quality is not simple, especially when dealing with large volumes of data from multiple sources. This is where master data management (MDM) comes into play,…

View On WordPress
0 notes
Text

#WordPress site deletion#Delete WordPress website#Removing WordPress site#Uninstall WordPress from cPanel#Backup WordPress website#WordPress database deletion#Website platform migration#WordPress site management#cPanel tutorial#WordPress site backup#WordPress website security#Data backup and recovery#Website content management#WordPress maintenance#WordPress database management#Website data protection#Deleting WordPress files#Secure data storage#WordPress site removal process#WordPress website best practices
0 notes
Text
5 Essential Tips for Maintaining Top-Notch Salesforce Org Health
Introduction: Salesforce has become an indispensable tool for businesses to manage customer relationships, streamline operations, and drive growth. However, just like any other complex system, your Salesforce organization requires regular attention and care to ensure it remains efficient, effective, and aligned with your business objectives.
In this blog, we'll explore five essential suggestions to maintain a top-notch Salesforce Org health, helping you get the most out of your investment.
Best Tips for Managing Salesforce Org Health
Regular Data Cleanup and Maintenance: A cluttered and disorganized Salesforce Org can lead to decreased user productivity, slower system performance, and inaccurate reporting. Regularly conduct data cleanup exercises to eliminate duplicate records, outdated information, and irrelevant data. Implement validation rules, workflows, and data governance processes to ensure that data entered into the system is accurate and consistent. Consider archiving or purging old records that are no longer needed, which can significantly improve system responsiveness.
Optimize User Training and Adoption: Even the most powerful tools are only as effective as the users who operate them. Invest in comprehensive user training programs to ensure that your team fully understands the features and functionalities of Salesforce. Regularly assess user adoption rates and address any issues or challenges they might face. Encourage the use of best practices and provide ongoing training as Salesforce releases updates and new features
Govern Customization and Configuration: Salesforce offers an array of customization options to tailor the platform to your specific business needs. While customization is valuable, an excessive amount can lead to complexity, slow performance, and difficulties during upgrades. Establish a clear governance framework for customization and configuration. This includes guidelines for when to use declarative tools (like Process Builder) versus custom code, as well as regular reviews of custom objects, fields, and processes to ensure they remain relevant and effective
Implement Robust Security Practices: Data security and privacy are paramount in today's business landscape. Regularly review and update your Salesforce security settings to ensure that only authorized personnel have access to sensitive information. Implement strong password policies, multi-factor authentication (MFA), and role-based access controls to minimize the risk of data breaches. Regularly audit user permissions and deactivate accounts for employees who no longer require access to the system
Stay Informed About Salesforce Updates: Salesforce continuously releases updates, enhancements, and new features to improve the platform's functionality and security. It's crucial to stay informed about these updates and assess their potential impact on your organization. Create a process for reviewing and testing new releases in a sandbox environment before rolling them out to your production Org. This practice helps identify any potential compatibility issues with your existing customizations and allows for adjustments before affecting users.
Conclusion:
Maintaining a top-notch Salesforce Org health requires a proactive approach that involves regular cleanup, user engagement, customization governance, security measures, and staying updated on platform developments. By following these five essential tips, your organization can ensure that Salesforce remains a powerful tool that contributes to your business success, helping you drive growth, streamline processes, and deliver exceptional customer experiences.
#Salesforce Org Health#Org maintenance#CRM optimization#Data integrity#Performance tuning#System health check#Data hygiene#Configuration management#Best practices#User adoption#Customization management#Security audit#Data governance#Automation tools#Regular updates#User training#Scalability#Backup and recovery#Compliance measures#Analytics and reporting
0 notes
Text
Discover the 4 Best Practices for Successful Data Management - Learn how to optimize data handling, improve efficiency, and achieve remarkable results in this comprehensive guide.
0 notes