#pinpointers tracking login
Text
Pinpointer: what is it for and how is it used?
Mineral exploration is a craft that has been practiced for many years. Nowadays, there are high-quality professional devices that greatly facilitate the task itself and make the whole process much more efficient and shorter. The device known as Pinpointer is one of them.
What is an Pinpointer?
A precision indicator is a portable metal detector used to determine the exact location of a metal…

View On WordPress
#best metal detector pinpointer waterproof#best pinpointer for metal detectors#best pinpointers for metal detecting#garrett carrot pinpointer#garrett pinpointer#minelab pro-find 35 pinpointer#pin pointers for metal detectors#pinpointer for metal detecting#Pinpointer metal detector#pinpointers car tracking#pinpointers tracking login#pinpointers vehicle tracking
0 notes
Text
tumblr has always guessed your location based on your ip, you can see it when you go to your settings to view your active logins
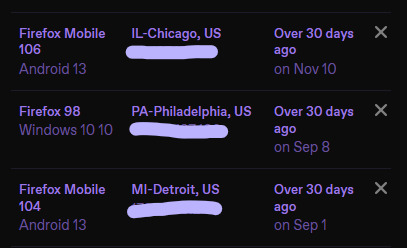
that's not the same as geolocation or location tracking, which uses a GPS to pinpoint your actual location
#original#i really need to go through and log out of everything and then wonder why i'm logged out of everything again#something about my firefox logins result in like twenty active sessions idk why#anyway this is why i looked up who was doing the tumblr live thing#because people yelling about third party data collection on tumblr are not convincing#on account of when posts+ and the tip jar came out people were fearmongering about. stripe.#stripe the payment processor that everyone uses all over the internet#so i could not trust anyone complaining to have any idea what the fuck they were talking about and had to look it up myself#but i have found no evidence that livebox is actually widely used in other social apps so i don't trust them lol#if you're going to complain do it about things that are actually real#and not your recent discovery that payment processors and ip addresses exist
168 notes
·
View notes
Text
can school see vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can school see vpn
VPN detection methods by schools
Virtual Private Network (VPN) services have become increasingly popular among students aiming to bypass school restrictions and access restricted content. To combat this issue, schools are employing various VPN detection methods to monitor and restrict VPN usage on their networks.
One common method used by schools to detect VPN usage is Deep Packet Inspection (DPI). DPI allows network administrators to scrutinize packet contents and identify VPN traffic based on unique characteristics such as encryption protocols or destination IP addresses associated with VPN servers. When DPI detects such traffic, schools can then block or restrict access to VPN services.
Another method used is IP address blocking. Schools can maintain a blacklist of known VPN server IP addresses and prevent any traffic to or from these addresses. By blocking VPN server IPs, schools can effectively prevent students from connecting to VPN servers and accessing restricted content.
Furthermore, some schools monitor network traffic patterns to detect anomalies indicative of VPN usage. By analyzing data traffic volume, timing, and source-destination pairs, schools can flag suspicious activities that may indicate VPN usage. Once detected, schools can take appropriate actions to block or restrict VPN access.
In conclusion, schools employ various VPN detection methods like DPI, IP address blocking, and network traffic analysis to prevent students from bypassing network restrictions using VPN services. By implementing these measures, schools aim to ensure a safe and secure online environment conducive to learning.
School VPN monitoring techniques
Title: Understanding School VPN Monitoring Techniques
In today's digital age, schools are increasingly implementing Virtual Private Network (VPN) monitoring techniques to ensure a safe and secure online environment for students and staff. VPNs are commonly used by individuals to encrypt their internet connection and access restricted content, but in educational settings, they can present challenges for maintaining network security and student safety.
One of the primary techniques used by schools to monitor VPN usage is through the deployment of specialized firewall systems. These firewalls are equipped with deep packet inspection capabilities, allowing them to analyze the contents of VPN traffic passing through the network. By identifying VPN protocols and encryption methods, administrators can pinpoint users attempting to bypass network restrictions and access prohibited websites or services.
Additionally, many schools leverage web filtering software to block access to known VPN websites and servers. These solutions maintain a database of VPN-related domains and IP addresses, automatically blocking connections to these resources. Moreover, advanced filtering algorithms can detect VPN usage based on behavioral patterns, such as sudden spikes in encrypted traffic or frequent connection attempts to suspicious endpoints.
Furthermore, some educational institutions employ user authentication mechanisms to track individual VPN usage. Through centralized user management systems, administrators can monitor login activity and enforce policies regarding acceptable internet usage. This allows schools to identify students or faculty members who may be circumventing network restrictions using VPNs and take appropriate disciplinary action if necessary.
It's important for schools to strike a balance between fostering a productive learning environment and respecting individuals' privacy rights. While VPN monitoring techniques help mitigate security risks and enforce acceptable use policies, administrators must also prioritize transparency and communication regarding their monitoring practices to maintain trust within the educational community. By implementing a comprehensive approach to VPN monitoring, schools can uphold network integrity while promoting responsible digital citizenship among their constituents.
Measures to bypass school VPN detection
In an era where online learning is increasingly prevalent, many students find themselves up against school VPN (Virtual Private Network) detection systems. These systems are put in place by educational institutions to enforce internet access policies and ensure that students stay within designated online boundaries. However, some students may need to bypass these restrictions for legitimate reasons, such as accessing blocked educational resources or conducting research.
Here are some measures students may consider to bypass school VPN detection:
Use a reputable VPN service: One of the most common methods to bypass school VPN detection is to use a reliable VPN service. These services encrypt internet traffic and route it through servers located outside the school's network, making it appear as though the user is accessing the internet from a different location.
Switch VPN protocols: Some VPN protocols, such as OpenVPN or WireGuard, are more difficult for detection systems to block compared to others. Switching to a protocol that is less likely to be detected may help bypass school VPN restrictions.
Obfuscation techniques: Certain VPN providers offer obfuscation features that disguise VPN traffic as regular HTTPS traffic, making it harder for detection systems to identify and block VPN usage.
Change VPN server locations: If a specific VPN server location is being targeted by the school's detection system, switching to a different server location may help evade detection.
Use alternative connection methods: In some cases, using alternative connection methods such as connecting through mobile data or using a proxy server may bypass school VPN detection.
It's important to note that attempting to bypass school VPN detection may violate the institution's acceptable use policy, and students should proceed with caution. Additionally, relying on VPNs for unlawful activities or circumventing legitimate restrictions may have consequences, so students should use these measures responsibly and ethically.
Risks of using VPNs on school networks
Using Virtual Private Networks (VPNs) on school networks can present various risks for students. While VPNs are commonly used to enhance online privacy and security, their usage on school networks can lead to potential negative consequences.
One of the main risks of using VPNs on school networks is bypassing content filtering and restrictions set by the educational institution. By masking their IP addresses and encrypting their internet traffic, students can access prohibited websites and content, which can disrupt the learning environment and expose them to inappropriate material.
Furthermore, VPNs can be used for illegal activities such as downloading copyrighted material or engaging in cyberbullying. The anonymity provided by VPNs can embolden students to participate in harmful online behaviors, putting themselves and others at risk.
Another concern is the potential for malware and security breaches. Free or untrustworthy VPN services may contain malware or harvest users' personal data, compromising the security of the school network and endangering sensitive information.
Additionally, using VPNs on school networks can violate the institution's acceptable use policy, leading to disciplinary actions or academic consequences for students.
In conclusion, while VPNs have valid uses in certain contexts, their usage on school networks poses risks that should be carefully considered. Educating students about the potential dangers of VPNs and enforcing appropriate internet usage policies can help mitigate these risks and promote a safe and secure online environment within educational institutions.
Legal implications of VPN usage in educational institutions
As educational institutions increasingly rely on digital platforms for teaching and administrative purposes, the use of Virtual Private Networks (VPNs) has become a common practice among students and staff. While VPNs offer benefits such as enhanced security and privacy, their usage in educational settings can raise various legal implications that institutions need to consider.
One primary concern is copyright infringement. VPNs allow users to bypass geographic restrictions and access content that may be restricted in their region. This can lead to students and faculty accessing copyrighted materials without proper authorization, potentially violating intellectual property laws. Educational institutions have a responsibility to ensure compliance with copyright regulations and may face legal consequences if their networks are used for illegal activities facilitated by VPNs.
Another legal consideration is data protection and privacy. VPNs encrypt internet traffic, making it more challenging for third parties to intercept and access sensitive information. However, this encryption can also be used to conceal illicit activities such as cyberbullying, harassment, or unauthorized access to confidential data. Institutions must balance the privacy rights of users with their duty to maintain a safe and secure online environment.
Moreover, VPN usage can impact compliance with regulations such as the Children's Internet Protection Act (CIPA) in the United States, which requires schools and libraries that receive federal funding to implement internet safety measures. While VPNs can help circumvent restrictive filters imposed by CIPA-compliant web filtering systems, doing so may jeopardize federal funding and expose institutions to legal liabilities.
To mitigate these legal risks, educational institutions should establish clear policies regarding VPN usage, including guidelines for acceptable use and consequences for misuse. Additionally, implementing robust cybersecurity measures, educating users about responsible online behavior, and regularly monitoring network traffic can help uphold legal compliance while safeguarding the integrity of the educational environment. By proactively addressing the legal implications of VPN usage, institutions can foster a secure and supportive digital learning environment for all stakeholders.
0 notes
Text
can ping host through vpn but cannot traceroute
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can ping host through vpn but cannot traceroute
Ping host through VPN
Title: How to Ping a Host Through VPN: A Step-by-Step Guide
Pinging a host through a VPN adds an extra layer of security and privacy to your network communication. Whether you're troubleshooting connectivity issues or assessing network performance, using a VPN ensures that your data remains encrypted and your identity protected. Below is a step-by-step guide on how to ping a host through a VPN:
Choose a Reliable VPN Service: Select a reputable VPN service provider that offers robust encryption protocols and a wide range of server locations. Ensure that the VPN provider has servers in the location of the host you intend to ping.
Install and Configure the VPN Client: Download and install the VPN client software on your device. Follow the setup instructions provided by your VPN service provider to configure the VPN connection properly. This typically involves entering your login credentials and selecting a server location.
Establish a VPN Connection: Launch the VPN client and establish a connection to the VPN server. Once connected, your internet traffic will be encrypted and routed through the VPN server, masking your IP address and location.
Open the Command Prompt (Windows) or Terminal (Mac/Linux): To ping a host, you'll need to access the command-line interface of your operating system. On Windows, search for "Command Prompt" in the Start menu. On Mac/Linux, open the Terminal application.
Enter the Ping Command: In the command-line interface, type the following command: ping [host IP address or domain name]. Replace [host IP address or domain name] with the IP address or domain name of the host you want to ping. Press Enter to execute the command.
Analyze the Results: After executing the ping command, you'll see the results displaying the round-trip time (RTT) and packet loss percentage. This information helps assess the network connectivity and latency to the host through the VPN connection.
By following these steps, you can effectively ping a host through a VPN, ensuring secure and private communication while troubleshooting network issues or monitoring network performance. Remember to disconnect from the VPN once you've completed your tasks to conserve bandwidth and optimize network speed.
Traceroute not working
Title: Troubleshooting Guide: Traceroute Not Working
Traceroute is a powerful diagnostic tool used to track the pathway that data takes from your computer to a destination server on the internet. However, encountering issues with traceroute not working can be frustrating, especially when you're trying to pinpoint network problems. Here are some common reasons why traceroute might not be functioning as expected, along with troubleshooting steps to resolve the issue.
Firewall Restrictions: Check if your firewall settings are blocking the traceroute packets. Firewalls, especially in corporate or networked environments, may be configured to block certain types of traffic, including ICMP packets which traceroute relies on. Temporarily disabling the firewall or adjusting its settings may allow traceroute to function properly.
Router Configuration: Sometimes, routers along the network path may not respond to traceroute requests due to misconfiguration or intentional blocking. Contact your network administrator to ensure that routers are configured to allow traceroute traffic.
Network Congestion: High network congestion or traffic may result in dropped or delayed traceroute packets, causing incomplete or inaccurate results. Try running traceroute at different times or from a different location to see if the issue persists.
Internet Service Provider (ISP) Restrictions: Some ISPs may restrict or filter traceroute traffic as part of their network management policies. Contact your ISP to inquire about any restrictions they may have and if traceroute functionality can be enabled.
Software or Hardware Issues: If traceroute consistently fails to work despite checking the above factors, there may be underlying software or hardware issues with your computer or network equipment. Ensure that your operating system and networking hardware are up-to-date, and consider seeking assistance from a professional IT technician.
By identifying and addressing the potential causes outlined above, you can effectively troubleshoot and resolve issues with traceroute not working, enabling you to diagnose network problems and ensure smooth connectivity on your network.
VPN connectivity issue
When it comes to ensuring your online privacy and security, using a Virtual Private Network (VPN) is essential. VPNs encrypt your internet connection and route it through a secure server, masking your online activities from prying eyes. However, despite the benefits of using a VPN, connectivity issues can sometimes arise, causing frustration for users.
One common VPN connectivity issue is the inability to establish a connection to the VPN server. This can be due to server downtime, network congestion, or incorrect VPN settings. To troubleshoot this issue, try connecting to different VPN servers, checking your network connection, and updating your VPN client software.
Another issue users may encounter is slow VPN speeds. This can be caused by a variety of factors, such as a distant server location, high server load, or limited bandwidth. To improve VPN speed, try connecting to a server closer to your physical location, using a less congested server, or upgrading to a VPN plan with faster speeds.
Furthermore, VPN disconnections can be a recurring issue for some users. This can happen intermittently due to network fluctuations, software conflicts, or outdated VPN protocols. To address this problem, try changing VPN protocols, updating your VPN client, or contacting your VPN provider for assistance.
In conclusion, while VPNs are crucial for maintaining online privacy and security, connectivity issues can sometimes occur. By following the troubleshooting tips mentioned above, users can resolve these problems and enjoy a seamless and secure VPN experience.
Network troubleshooting VPN
In the world of digital networking, Virtual Private Networks (VPNs) play a crucial role in ensuring secure connections and safeguarding sensitive data. However, like any technology, VPNs can occasionally run into issues that require troubleshooting to resolve.
One common issue that users may encounter when using a VPN is difficulty in connecting to the network. This can be caused by various factors such as server maintenance, network congestion, or incorrect settings on the user's end. To troubleshoot this problem, users can try switching to a different server location, restarting their device, or checking their VPN configuration settings.
Another common problem with VPNs is slow connection speeds. Slow speeds can be frustrating and may be due to factors such as server overload, distance from the server, or limitations imposed by the user's internet service provider. To address this issue, users can try connecting to a different server, optimizing their internet connection, or upgrading to a higher-tier VPN subscription with faster speeds.
DNS leaks are another issue that can compromise the privacy and security of a VPN connection. A DNS leak occurs when the device sends DNS queries outside of the encrypted VPN tunnel, potentially exposing sensitive information. Users can prevent DNS leaks by configuring their VPN client correctly and conducting regular leak tests using online tools.
By familiarizing themselves with these common VPN troubleshooting issues and solutions, users can ensure a seamless and secure online experience while harnessing the full potential of Virtual Private Networks. Whether it's connectivity issues, slow speeds, or DNS leaks, understanding how to troubleshoot VPN problems is essential for maintaining a reliable and secure network connection.
Cannot trace route through VPN
When you are unable to trace a route through a Virtual Private Network (VPN), it can be quite frustrating and can signify potential issues with your network settings or VPN configuration. Tracing a route through a VPN is a common troubleshooting technique used to identify any connectivity issues and determine the path that network packets take from your device through the VPN server.
If you find yourself unable to trace a route through your VPN, there are several possible reasons for this. One common reason could be misconfiguration in the VPN settings on your device or the VPN server itself. Double-checking the settings and ensuring that they are correct is crucial in such situations.
Another reason could be firewall restrictions blocking the traceroute packets from passing through the VPN connection. Adjusting the firewall settings to allow the traceroute packets can help you troubleshoot the issue.
In some cases, the VPN server might be configured to block traceroute requests for security reasons. Contacting your VPN service provider to inquire about their traceroute policies and potential solutions could help resolve the problem.
Ultimately, if you cannot trace a route through your VPN, it is recommended to review your VPN settings, check for any firewall restrictions, and reach out to your VPN provider for assistance if needed. Proper configuration and troubleshooting can often resolve such issues and ensure smooth connectivity through your VPN.
0 notes
Text
Utilizing analytics features to track subscription performance and user behavior
In the ever-evolving world of e-commerce, gaining a competitive edge requires not just the integration of subscription plugins but also a keen understanding of user behavior and subscription performance. In this article, we delve into the importance of utilizing analytics features to track these metrics, providing actionable insights for business growth.
The Role of Analytics in Subscription Management
Understanding User Behavior
Analytics tools serve as a window into the minds of your customers. By tracking user behavior, you can gain valuable insights into how customers interact with your subscription services. Identify popular products, peak subscription periods, and areas for improvement by analyzing user data.
Measuring Subscription Performance
Accurate assessment of subscription performance is crucial for making informed decisions. Analytics features allow you to track key metrics such as subscription sign-ups, cancellations, and revenue generated. This data empowers you to optimize subscription plans, pricing strategies, and marketing efforts.
Key Analytics Features for Subscription Tracking
1. User Engagement Metrics
Track user engagement to understand how customers interact with your subscription services. Metrics such as click-through rates, time spent on subscription pages, and the frequency of logins provide insights into the effectiveness of your offerings.
2. Churn Rate Analysis
Identify and mitigate churn by closely monitoring the churn rate. Analyze reasons for cancellations, whether it's dissatisfaction with services or external factors. Adjust your strategies accordingly to enhance customer retention.
3. Conversion Funnel Analysis
Examine the conversion funnel to pinpoint areas of drop-off in the subscription process. Optimize each stage of the funnel, from initial interest to final subscription, to ensure a seamless and efficient user journey.
4. Revenue Attribution
Understand the sources of revenue generated through subscriptions. Analyze which marketing channels, campaigns, or products contribute the most to your subscription revenue. Allocate resources strategically based on this information.
5. Customer Segmentation
Segment your customer base to tailor subscription offerings. Analyze data based on demographics, purchasing behavior, or location to create personalized subscription plans. This targeted approach enhances customer satisfaction and loyalty.
Implementing Analytics in Subscription Management
Step 1: Choose the Right Analytics Tools
Select analytics tools that align with your business goals and integrate seamlessly with your e-commerce platform. Google Analytics, Mixpanel, or custom analytics solutions are popular choices. Ensure compatibility with your subscription plugins for comprehensive data tracking.
Step 2: Set Up Custom Dashboards
Create custom dashboards within your chosen analytics platform to focus on key subscription metrics. This streamlines data interpretation, allowing you to quickly identify trends, patterns, and areas requiring attention.
Step 3: Regularly Analyze and Iterate
Establish a routine for analyzing analytics data. Regular reviews enable you to stay proactive in addressing issues and optimizing your subscription strategies. Use A/B testing to experiment with different approaches and refine your tactics based on performance data.
Case Study: Analytics-Driven Success
Let's examine a case study where ABC Company utilized analytics features to enhance subscription performance. By implementing targeted marketing campaigns based on user behavior data, they experienced a 25% increase in subscription sign-ups and a 15% decrease in churn rate within six months.
Conclusion
Incorporating analytics features into your subscription management strategy is not just a best practice; it's a necessity for sustained business growth. By understanding user behavior and tracking subscription performance through robust analytics, you gain the insights needed to make informed decisions, optimize strategies, and stay ahead in the competitive e-commerce landscape.
0 notes
Text
How AI Reduces the Cost of a Data Breach
New Post has been published on https://thedigitalinsider.com/how-ai-reduces-the-cost-of-a-data-breach/
How AI Reduces the Cost of a Data Breach


Early adopters of emerging technologies like artificial intelligence (AI), machine learning (ML) and automation are already reaping the benefits. These organizations have more robust defenses against cyberthreats by layering their security measures with advanced threat detection, pattern analysis and quicker response times. Discover why AI is the ideal solution for your cybersecurity needs in this quickly evolving digital world.
Transforming Cybersecurity With AI Tools
Security AI is making waves in the cybersecurity space. An IBM report shows that organizations adopting the new technology have quicker response times and lower data breach costs. AI-powered cybersecurity defenses lowered data breach costs by $300,000 per incident and the time to detect and mitigate breaches down to 249 days.
These are significant improvements since organizations with zero AI deployment reached an average of 323 days to respond. Those are valuable and profitable days lost to damage control and other risk mitigation procedures.
Real-Time Detection
Leveraging AI technologies in your cybersecurity measures can significantly reduce breach detection times. AI can supercharge security teams by allowing them to detect suspicious activity in real-time, even without human supervision. This functionality gives them more control over the threat, enabling them to scramble countermeasures like investigative protocols and cyber deception techniques that actively seek attackers and trap them within secure systems.
Furthermore, AI can analyze user activity within a system and use historical data to see if any criminal patterns arise. This function allows AI to detect previously seen attack vectors and identify new ones based on updated threat intelligence reports. Your cybersecurity teams can automate alarms to go off based on the machine learning data fed into security AI. They can also refine processes by setting alarms depending on severity, context and overall impact.
Cybercriminals no longer work alone. They attack in groups, launching multiple attacks to access critical resources. AI tools can help bolster your organization’s defenses, especially if you integrate them with zero-trust architecture. As AI detects unusual or malicious activity, use strict authentication and verification protocols to confirm user identity. AI-powered systems can track user login information, invalid attempts and other risky behavior to pinpoint criminals and thwart their attacks.
Reduced False Positives
Cybersecurity fatigue is a common occurrence in the digital world. The rising numbers of cyberattacks and overloaded teams only exacerbate the situation. Even skilled cybersecurity teams are exposed to this phenomenon, especially with faulty alarm systems that continuously flag user activities as possible threats. High alert volumes can overwhelm trained professionals, leaving them vulnerable to real attacks when they finally arrive.
You can layer your cybersecurity measures with AI by using automation to create high-fidelity alarms that only trigger when they detect verified threats. False alarms can leave your organization vulnerable and give threat actors better chances at sneaking past your defenses. By leveraging security AI, you can automate incident responses to expedite investigations and ramp up risk mitigation actions.
Risk Mitigation
A survey revealed that 91% of organizations protect themselves using a risk-based cybersecurity framework that aims to identify and evaluate threats as an immediate response to security risks. You can use AI tools to identify weaknesses in your cybersecurity measures through penetration testing to reduce the chances of bad actors compromising your systems.
Effective risk management is critical to ensure you always protect all vital resources and addressing existing issues in your organization’s defenses is one way to do it. Protect your clients and partners from data breaches by augmenting current cybersecurity contingency plans and equipping your analysts with AI tools to predict potential attacks.
Cybersecurity can be labor-intensive and time-consuming. Manual risk analysis and traditional risk management processes may no longer be enough to safeguard your company’s interests. Automation will help you spot possible attack vectors even before they damage your systems.
Proactive Defense Posture
Simple firewalls and updated security systems may work for individuals, but organizations have more to lose when they forego critical defenses like security AI. Precious resources like company and client data, intellectual property and user information fetch a hefty sum on the black market and malicious third parties will do just about anything to steal them.
Using AI, ML and automation, you can take a more proactive cybersecurity approach than a reactive one. Machine learning models trained on updated, high-quality data can detect existing vulnerabilities even in the most secure systems. Predictive analytics can also use advanced algorithms to analyze massive amounts of data and identify patterns — new and old — for potential security threats.
Security teams can then act on ongoing threats by either studying the perpetrators or thwarting their attacks immediately. Many cybercriminals linger in compromised systems to learn as much as possible about them. A proactive cybersecurity approach paired with AI tools can help sniff out threat actors and discourage them from going further.
Flag Phishing Attacks
While phishing is by no means a new threat, it’s still a popular tactic among threat actors looking for an easy way into data vaults containing precious user and company information. Cybercriminals also use AI to launch more sophisticated phishing attacks to compromise systems using stolen credentials from unsuspecting employees.
Modern problems require modern solutions — you can use security AI to detect and stop phishing attacks as soon as contaminated emails arrive in your staff’s inbox. Advanced AI functions like message analysis can identify harmful content using multiple points of comparison to increase effectiveness. Criminals are getting trickier and your employees need all the help they can get to identify legitimate and fraudulent work correspondence.
You can also use advanced AI tools to simulate phishing attacks and train your employees in cybersecurity best practices. Including your workforce in cybersecurity measures gives you a better chance of repelling phishing attacks and other cyberthreats. Cybersecurity is everyone’s responsibility, but it’s up to you to improve your organization’s defenses. Use AI-powered security tools to strengthen your defensive capabilities to prevent costly data breaches from becoming a reality.
AI: A Modern Tool for Reducing Data Breach Incidents
Even the most prominent companies fall victim to ruthless cyberattacks. Many pay ransoms to regain stolen data, while others get slapped with steep fines for their lax security practices. Nowadays, cybersecurity is no longer an option. It’s a necessity. The quicker companies realize this, the better they can prepare for when threat actors arrive.
Using AI and other emerging technologies is an excellent way to protect your clients, partners and employees. While hiring professionals like security analysts, advisers and consultants to deploy AI-powered systems requires significant investment, it’s still a smaller price than the productivity losses and reputational damage your company will face after a data breach.
#000#ai#AI-powered#Algorithms#Analysis#Analytics#approach#architecture#artificial#Artificial Intelligence#attackers#authentication#automation#Behavior#black market#breach#Companies#comparison#content#credentials#cyber#Cyberattacks#cybercriminals#cybersecurity#cybersecurity framework#data#data breach#Data Breaches#defense#defenses
0 notes
Text
The Security Rewards of Online SSH Clients for Remote Accessibility

In the modern globe, accessing remote control web servers is important for lots of companies. Having said that, with an enhanced necessity for remote control access happens the difficulty of making sure the security of sensitive info. Numerous companies make use of Secure Shell (SSH) to sustain safe connections between their web servers. Online SSH clients give a handy and safe solution for accessing distant servers from throughout the planet. In this particular post, our experts look into the security perks of making use of online SSH clients for remote gain access to.
Protection Advantages Of Utilization Online SSH Clients
Encrypted Connection
Online secure shell clients permit for an encrypted connection that provides a secure technique to connect with servers online. An on the internet SSH client encrypt all data sent to and also from the web server, making sure that info is guarded from spying eyes. This encryption makes sure that any sensitive info or even login qualifications are protected from possible cyberpunks or even various other cyber risks.
Two-Factor Authorization
Many online SSH clients give boosted security solutions including two-factor verification to stop unapproved gain access to. This indicates that besides a code, a user has to present a second element to get. This 2nd factor may take the type of an one-time code or biometric authorization. Two-factor authentication offers an additional coating of security that creates it harder for cyberpunks to obtain get access to.
Secure Shell Secret Administration
Online secure shell clients enable secure shell vital monitoring, which provides a method to take care of SSH tricks that are actually made use of for safe and secure communication in between the web server and clients. SSH keys are used to verify the user and also encrypt data online. Online SSH clients deliver secure shell key management that makes it possible for individuals to produce and handle tricks, delivering another layer of safety and security against possible cyber hazards.
Access Control
Online secure shell clients permit robust get access to managements that aid to confine the amount of individuals that can easily access a server. This is actually specifically important when dealing along with delicate information. Online SSH clients deliver the potential to define jobs and also permissions that make it possible for only licensed workers to accessibility specific servers. These get access to controls give an extra layer of surveillance that assists to restrict the risk of unauthorized access.
Audit Logs
An on the web SSH client offer in-depth audit logs that may be made use of to track activity on web server and make certain observance along with surveillance policies. Review logs record all actions taken by a consumer, featuring login efforts as well as documents transmissions. These logs could be made use of to pinpoint any sort of malicious activity and also offer a complete viewpoint of server task. By reviewing these review logs, companies may swiftly take action to minimize any type of possible surveillance hazards.
Conclusion
To conclude, online SSH clients deliver a handy and safe and secure technique to access remote control web servers. The encryption of data sent to and also from the server, combined with two-factor authorization, secure shell essential administration, get access to command, and thorough audit logs, all cooperate to offer enriched protection when accessing remote control servers. Providers can easily gain from the benefit of remote control get access to while also making sure the protection of their sensitive relevant information. Online SSH clients are actually an important device for contemporary companies that prioritize safe remote control gain access to.
0 notes
Text
Stealer Malware Unveils Intricate Cybercrime Web

A staggering 120,000 computers have fallen victim to stealer malware, resulting in compromised credentials connected to various cybercrime forums. This revelation underscores the intricate network of malicious actors and the concerning potential of information stealers as a dominant attack vector. Hudson Rock, a cybersecurity firm, conducted a comprehensive analysis spanning from 2018 to 2023, shedding light on a disturbing trend that underscores the evolving landscape of cyber threats.
Unintended Consequences: Hackers Inadvertently Targeted by Malware
Chief Technology Officer Alon Gal of Hudson Rock highlighted that these compromised machines were not solely targeted intentionally by threat actors. Among the 14.5 million computers in the firm's cybercrime database, a portion belonged to hackers who unknowingly fell prey to the very malware they deploy.
Unmasking Hacker Identities: Compromised Data Reveals Real-World Clues
The breach's significance extends beyond the number of affected devices to the wealth of information extracted. Hudson Rock's analysis exposes a range of stolen data, including credentials, addresses, phone numbers, computer names, and IP addresses. This treasure trove of information holds potential implications for revealing the true identities of cybercriminals.
Also Read: Kashmiri Brother-in-Law could not show Kamal, and pressure on Nagpur police failed
Stealer Malware's Role in Expanding the Malware-as-a-Service Ecosystem
Stealer malware has become a linchpin of the malware-as-a-service (MaaS) ecosystem, serving as a lucrative initial attack vector for threat actors targeting organizations. This ecosystem empowers hackers to execute various malicious activities, including ransomware attacks. The breach underscores the alarming significance of information stealers in infiltrating and compromising organizations.
Impact on Leading Cybercrime Forums: Nulled. to at the Helm
Hudson Rock's investigation pinpointed heavily impacted cybercrime forums. Nulled.to emerged as the primary target, with an astonishing 57,000 users falling victim to stealer malware. Cracked.io followed with 19,062 users, and Hackforums.net with 13,366 compromised users. These forums serve as breeding grounds for cybercriminal activity, making their compromise a substantial concern.
Password Strength and Vulnerability: An Intriguing Analysis
The breach sheds light on the password strength of cybercriminals. Hudson Rock reported that passwords from cybercrime forums demonstrated greater complexity and strength compared to those used on government websites. Moreover, a significant portion of compromised credentials featured at least 10 characters and contained four distinct character types.
Attribution and Law Enforcement Implications
Alon Gal highlighted the potential for this breach to aid law enforcement in attributing cybercriminal activity. While information stealers are notorious for compromising organizations through stolen credentials, this breach reveals that the same stolen data can also be a tool for identifying and tracking malicious actors.
Also Read: Cybercrime in Nagpur - Cyber Blackmailer Couple Arrested in Pune for Extorting Money
Expanding Threat Landscape: Corporate SaaS Applications Vulnerable
Flare's subsequent analysis of over 19.6 million stealer logs has unveiled further vulnerability: 376,107 logs provided access to corporate Software-as-a-Service (SaaS) applications. Logs containing financial services logins were priced at a premium, indicating the substantial potential for financial gain through such attacks.
Discord.io Breach and the Resurgence of Breach Hacking Forum
This revelation follows Discord.io's temporary shutdown due to a data breach, exposing details of over 760,000 users. The aftermath saw the reemergence of the Breach hacking forum, now led by ShinyHunters. These events highlight the persistent and evolving nature of cyber threats, emphasizing the need for constant vigilance in the face of increasing digital vulnerabilities.
Source: https://www.the420.in/stealthy-malware-breach-120k-devices/
0 notes
Text
Tumblr Archive Frustration
and
The Sketchy Town Crier Is The Future Of The Internet
This likely happened months or years ago, but noticed that Tumblr now requires a login to archives. Missed this change, having used an RSS reader to follow my favorite Tumblr Blogs for years.
In my understanding, the point and appeal of Tumblr was a blog platform with social media on the backend. A defining part of a blog is people don't have to sign in to read it. To me, the archives are key to that open aspect.
In the blog era, the archive was an unquestioned feature, the more functional the better. If someone liked a post, they'd want to go back and read more and making that as easy as possible was key. And if one had a popular topic or ongoing series, one wanted to make it as easy as possible for new readers to start at the beginning which they'd obviously want to do. Even if the endless scroll had existed, expecting people to roll back months or years manually would be absurd.
Social media not only profits from maximizing engagement from logged in users, but the business increasingly rests on monetizing usability. Thus platforms are at best indifferent to archives and searches as accessible and functional tools and usually actively hostile towards them. It's particularly bad in the web browser format, which I suspect most companies would love to abandon. Consider the rise of the asynchronous feed and search results.
The Tumblr web archives are a mixed bag. Deficits: One must log in. One can filter by month, but it's a drop down menu that shows one year at a time. One must hover over entry squares to see the dates. Benefits: one can use the month and tag filter at the same time, which is handy for tracking an ongoing series of posts, which not all Web 1.0 blogs had.
For example, Mike Sterling’s Progressive Ruin had a feature called The End of Civilization in which he mocked offerings from the Diamond Previews catalog. Good comics industry humor and now possibly history of a bygone era as Diamond may have ended the print version. However, the only way to get to the beginning is clicking "Older Entries" at the bottom of the page.
A better archive can be seen with Slacktivist's epic analysis of the Left Behind series that ran from 2003 to 2016. It's relatively compact and simple, though one does have to click several times to reach the earliest of 18 pages. But no log in is required - this lengthy and now prescient contemplation on the pop culture of right wing theocrats is quite accessible.
For some time, it seemed like the internet's path was constantly improving search and archives with user control. I expected more tools for viewing content from oldest to newest.
At the moment I can't pinpoint when and how things broke - as it's the tools for doing so that degraded - but traces of it still exist. Google still has a search tool for news archives with date filtering going back to 1900. At one point this was part of the main Google News service page, combining free and paid sources, maybe even Lexus Nexus, to providing a possible century of results of varying accuracy. Google News search now has five options - hour, 24 hours, week, year - with results in no coherent order.
Now the capitalist internet offers a barely coherent stream of recent information manipulated by a feedback loop of perceived reactions, things like larger context, longer chronology and verification increasingly require power user skill and workarounds. And entertainment sites are openly adopting the model of a not particularly well stocked video store in which anything besides recent releases is a random selection of whatever tapes still work.
Now the various AI schemes they are layering on top of this already janky system kind of seem like they decided a user driven internet was a mistake and instead all content will be controlled by a personalized but deeply untrustworthy town crier who must be constantly cajoled into providing anything besides what it assumes you want. And some people may be into that, but I think it sucks.
0 notes
Text
How to Use the TTM Squeeze Indicator - Library of Trader
What Is the TTM Squeeze Indicator?
The volatility and momentum indicator TTM Squeeze was developed by John Carter of Simpler Trading. It takes advantage of the fact that prices tend to break out forcefully after consolidating in a narrow trading range.
The TTM Squeeze indicator’s volatility section tracks contracting prices through Bollinger Bands and Keltner Channels. A period of minimal volatility is indicated if the Bollinger Bands are contained entirely inside the Keltner Channels. The squeeze refers to this tight condition. When the Bollinger Bands re-expand beyond the Keltner Channel, it is stated that the squeeze has “fired,” signaling an increase in volatility and a possible departure from the confined trading range. Squeeze on/off status is shown by little dots on the zero line of the indicator; red dots signal squeeze is on, while green dots show squeeze is off.
The TTM Squeeze indicator is available for TradeStation® and thinkorswim®, two widely-used charting software platforms currently.
How to Read the TTM Squeeze Indicator and How Does the TTM Squeeze Work?
TTM Squeeze Indicator Explained
The TTM Squeeze is predicated on the premise that decreased prices would eventually lead to higher prices. If we can pinpoint when the market is particularly tense, we can position ourselves to benefit from a potentially powerful move in one direction
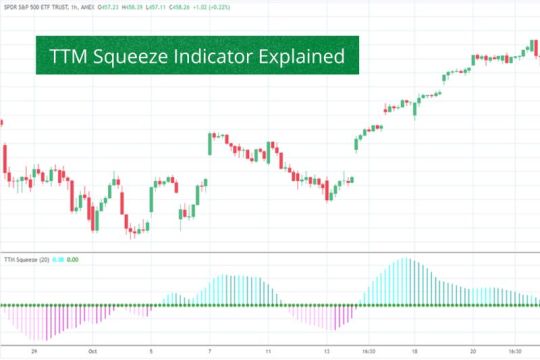
What Do the Colors Mean on the TTM Squeeze?
Indicators of a squeeze are represented by red and green dots on the zero line. If there is a red dot, it indicates a squeezing situation. If there is no red dot, we are not in a confined space at the moment. When a green dot appears following a string of red dots, the squeeze has been successful.
Using the TTM Squeeze in Trading
There is a wide range of periods compatible with the TTM Squeeze indicator. When trying to confirm a security’s value, many chartists look at data from several different time periods. Squeezes that fire on many time frames at once are more reliable signals than those that fire on just one.With the TTM Squeeze, traders may rededicate themselves to the market and get the self-assurance they need to consistently turn a profit and increase their wealth. Having faith in yourself and your abilities will help you:
Avoid bad trades
Make profitable trades
Optimize returns
Put away your doubts
Enhance market sense
How to Build a Profitable Trading Plan Using the TTM Squeeze?
John Carter’s route to regular profits in trading was revolutionized by the TTM Squeeze indicator. The TTM Squeeze is an important technique for traders who wish to rapidly expand their trading capital.
To put it bluntly, the TTM Squeeze indicator is not a miracle worker. Any kind of trading carries with it some degree of inherent risk. Additionally, you are not expected to “make it big” in the trading world in the manner of some well-known trader who claims to make you a millionaire if you only “be a billionaire” on the internet.
How to Set up TTM Squeeze Indicator
Here is what you simply need to do to set up the TTM_Squeeze to your thinkorswim charts:
Login to your thinkorswim account
Select the studies button
Add study
Then find John F. Carter studies
Select the TTM_Squeeze

Trading the TTM Squeeze Indicator with Divergences
Although the TTM Squeeze indicator is recognized to provide a strong signal as to where price is heading, the best trades are those in which numerous indicators are flashing the same signal.
Using divergence is a strategy that may be applied while trading with the TTM Squeeze indicator. When price and the histogram momentum bars are moving in different directions, this is called a divergence. When price is forming higher highs while the slope of the histogram is forming lower highs above the “zero line,” a bearish divergence exists.
What is the Squeeze Pro Indicator?
The Squeeze Pro Indicator is the upgraded version of TTM Squeeze. Conversely, the TTM Squeeze is a fantastic indicator that can do wonders for traders of any skill level. The premium Squeeze Pro Indicator makes it easy to choose one of three squeeze intensity levels, provides clear entry and exit signals, and anticipates and capitalizes on market rallies. You should upgrade to TTM Squeeze Pro if you’ve outgrown the free version.
The Bottom Line
The TTM Squeeze indicator takes into account both volatility and momentum in order to help traders profit from swings in the security’s volatility. Squeeze dots, which are part of the indicator’s volatility component, point to possible breakouts after tame trading conditions. The momentum histogram shows the most likely path of the breakout and can aid in locating potential exits.
Article Source: https://libraryoftrader.net/how-to-use-the-ttm-squeeze-indicator
0 notes
Text
Vehicle Tracking Management
CAT 6 tracking services, Range Rover locating, Audi tracking services, BMW service tracking, Tracking Cat 5 category, Mercedes servicing, van tracking, HGV Tracking installation, tracking for trailers, tracking caravan, tracking motorhome.
To find the best one, you might need to get into the detailed analysis of these tracking and installation services.
After incalculable exploration interviews, organizations have revealed to us that when they have recently taken a gander at telematics they don't see the worth. In any case, telematics has changed with new innovation making it more open and simpler to see prompt worth and ROI.
Our new TN360 arrangement in a flash reveals to you the regions to zero in your experience on and detects the abnormalities for you, which means this currently opens up new advantages to organizations like yours. Things being what they are, the reason is it worth investigating?
Envision delineating your everyday job as an armada administrator by in a real sense staying a post-it note on the divider for every single activity you make. The meticulous errand of reasoning precisely what you do, how you do it, when and for what reason would require up every one of the hours in a day, to where your office will have had a full refurb of neon dividers.
Picturing that load of undertakings directly before you is a terrifying idea. To believe that you in a real sense invest your energy contributing data into various innovation, arrangements and programming would be sufficient to cause anybody to feel somewhat automated.
Rehashing these equivalent day by day cycles can get dull, yet in addition self-ruling, and that is something we will in general fail to remember when working with information – we're not machines, we're human!
We're encircled by numbers, figures and measurements the entire day in the realm of armada the executives, in spite of the fact that we're in a real sense comprised of everything except that. As people, we base our choices on musings, feelings and sentiments. A few of us gloat certainty and energy, while others are more doubtful and weigh out the dangers. We even essentially "go with our gut" when contemplating what to do straightaway, disregarding the details totally.
Machines and people should complete one another, not claim to be one another.
So why is it that in case we're made up such countless things that make us all human, we actually wind up taking every necessary step of machines?
It's not the ideal opportunity right now
The vulnerability to change. "It's not the ideal opportunity" is a typical term we've all utilized, regardless of whether it's taking a gander at new vehicle finance or to redesign your Sky bundle, however multiple times out of 10 it truly signifies "kindly don't bother me, I'll settle all alone."
While you might have helpful freedoms to do as such, for example, an agreement with a current supplier reaching a conclusion, it's not really simple to pinpoint when "the ideal opportunity" truly is.
For some armada supervisors there may come a moment that those post-it notes toward the rear of your psyche simply get excessively, and you conclude nothing more will be tolerated – "I need to take care of this."
While for other people, the opportunity might arrive when a vehicle misses its administration or a drivers' records are inadequate. In any case, the issue here is trusting that that opportunity will come.
Physically pulling reports, breaking down your own information and adhering to your ordinary regular routine might seem like the least demanding thing to do, yet that is just in light of the fact that it doesn't expect anything to change.
Envision getting the opportunity to take those post-its and parting with them, without troubling the remainder of your group with the additional responsibility. You can pass those dreary errands and get back the entirety of that significant time you'd have lost in any case.
That is by and large what an AI-fueled telematics stage can accomplish for you. It gathers each datum point from your armada and does each estimation, synopsis and examination it can, all so you don't need to. Then, at that point when you're prepared for that Monday meeting, you should simply actually ask it for the data – it's as of now done.
As such – in the event that you pick that today is the ideal opportunity, you'll get all the excess time back tomorrow.
My present arrangement does all I require
That is incredible! So for what reason don't we check whether we can get it accomplish more, do it speedier or improve?
Regardless of whether your vehicles don't travel extremely far, or you don't think it'll merit the issue – doing the change to AI will in any case have an enormous advantage to your business.
You'd have the option to track and screen the entirety of your vehicles with fast view dashboards across the board simple to-utilize stage, which means there'd be no compelling reason to flick between various tabs or logins. Also that the AI motor will naturally identify any anomalies in driver conduct, so you can immediately upgrade your activities, instead of physically following through information logs.
Having an AI-fueled telematics stage permits you to change the manner in which you take a gander at your armada with a solitary snap, contact or swipe. It awards you a single tick admittance to efficiency, security, support and work process data with information focal points that attention on key estimations, in less time than it would take to discover the record on your work area.
It likewise implies you can adopt a proactive strategy to armada the executives, as the AI innovation itself gains from your responses. It's fast – truly speedy – so your information is consistently in the know regarding precise, significant experiences continuously.
1 note
·
View note
Text
How to save Energy by analysing Energy Monitoring System -Energy Log
Today we'll discuss the basic functionality of one of the markets best energy monitoring system Energy Log. We’ll use the case of a chain of supermarkets to show you the main functionality of the Energy Log, focusing on three supermarkets one in Delhi one in Mumbai and one in Banglore. The Energy Log shows you to the dashboard login which brings you right to this screen. Which gives you a quick overview of your facilities in real-time. Dashboard indicators are fully configurable widgets. Widgets present information in a way that's clear and easy to understand. When we detect an inefficiency, we can go to the analysis, reporting or alerts areas to view the facility in more detail. The Energy Log navigation functionality which is based on hierarchies and filters makes it extremely easy to locate exactly the information we need to know.
Customized Dashboard
We will compare the performance of three supermarkets in Delhi, Mumbai, and Bangalore and monitor their general consumption. We will view their utility meter and its consumption of HVAC refrigeration and lighting systems. We can create an unlimited number of dashboards for our analysis of the three supermarkets. We've created a different dashboard for each of our user profiles energy manager, finance director, and maintenance staff users. They can set up their own dashboards and share them with other users which saves time and keeps teams in the loop.
Real-Time Analysis
The analysis area is where we access all our data so we can understand consumption patterns in our facility or group of facilities. Energy Log analysis tools help you to easily visualize and understand consumption cost evolution and billing. For example, if we want to view the real-time consumption of our Delhi store we just go into the consumption tools and select all the meters installed, we see is in real-time. It will show us the hourly consumption for the past week. We see exactly what time lighting and HVAC systems are switched on and off. How much energy they are consuming? We can see here that refrigeration levels are constant, but they should be changing according to outside temperature. We can also view the evolution of energy consumption for each individual meter from week to week if we select a date range and choose to view weekly consumption.
Global-View and Excel data Downloads
Energy Log displays an overview of the consumption trends of facilities, so we can identify patterns of all data and graphics which can be exported to excel for future reference or graphical reports. We can also have a global view where we can compare our three supermarkets. We will select fiscal meters and do an hourly comparison. We can see the activity level by the hour is similar in the three stores but that there are notable differences among consumption levels. It appears that the Mumbai store consumes the least followed by Banglore and then the Delhi store. Delhi has the highest level of consumption.
Energy Performance Indicators
But when we go into more detail by viewing the daily evolution over the course of a year. We can see that the variations, we have identified are visible throughout the year. This might be the result of variations in surface area, weather variables, consumer volume or other factors because there are so many things that might affect inconsistencies. We need a fast and intuitive tool that allows us to easily view energy use in the context of a range of variables. So, we can pinpoint the exact causes this is where ratios are especially useful. For example, when we factor in the surface area of the stores, we see that the Mumbai supermarket which originally ranked first for energy efficiency falls to second place and the Banglore store comes in first. We can filter our original results by entering a wide range of ratios like degree days, average temperatures, ticket occupancy levels, average sales or anything else that might be useful to understand exactly what is affecting consumption.
Let’s repeat the analysis but this time focusing on the lighting systems, first, we'll select three lighting meters and compare their yearly consumption. When we control our results for surface area we see that from the beginning of the year up until August, the Delhi store averaged to consumption of 0.6 kWh/sq ft which is higher than that of Mumbai at 0.7 kWh/sq ft and much higher than the Bangalore stores consumption which is only 0.2 kWh/sqft. So we know right away that we have a problem of excess lighting in the Delhi and Mumbai locations we can look more closely to see that lighting levels are in fact double. There should be values of more than 2,000 Lux are showing up when the established baseline for a retail space is closer to 750 Lux. Analyzing more deeply we can see that shutting off one out of every two fluorescent lights on July 7th in the Delhi store and on August 8th in Mumbai effectively reduce the kWh/sqft ratio and brought down the lighting consumption of the three stores to similar levels.
Put Comment on Analysis Sheets
The Energy Log comments feature allows us to easily log these changes and their energy-saving results, so we can better track and manage projects. We can just click over add Comment and select the date on which the improvement was implemented and add a title and description to identify the improvement. We then select the kind of comment the location where the improvement was implemented where we indicate Delhi and we publish our comment. Once published our comment is visible in the graphic in the form of an icon. When we hover the mouse over the icon the title of the improvement appears.
Monitoring and verification of Energy Saving Achieved
As we have implemented our lighting efficiency improvements, we can look at how they translate to savings. Let us compare for different time periods by day month or year which helps to see the evolution of our consumption over time. We select the Delhi store and its lighting node and then select a before and after the efficient implementation and we evaluate our results. A graphic display’s two colored curves representing weekly consumption, the blue represents before and the green represents after in the chart below the graph.
We can clearly see a reduction in lighting consumption, our weekly lighting consumption per week has dropped by nearly 30 %. It’s even more interesting to see how this saving translates to the financial savings. For this, we simply go to the cost screen where we can see in real-time exactly how much money we are spending according to the tariff plan of the DISCOM. If we look at the cost of lighting at the Delhi location, we see a cost of over three thousand dollars a month. Most of the consumption comes from the peak level which corresponds to the contracted tariff. We select lighting choose a weekly view and look at the levels one week before the implementation of the improvement. We can view the hourly consumption for the selected week. We see that there is hardly any passive consumption and see penalties for peak hours. Energy Log quickly calculates the weekly lighting consumption based on these factors and comes up with a weekly cost. If we view consumption in dollars after the implementation, we see that our weekly cost represents a yearly savings of $15,000.
Energy Log offers a multitude of tools that help us to easily analyze and detect potential in-efficiencies. We can use its intuitive tools to measure passive reactive or other kinds of consumption or even customize a screen with variables.
Reports
Reports area is where we find all our reports and view those generated during a particular project. You can use a public template or use the reports assistant to customize a report. We just need to select a template and activate it. We can automate a report to be generated and sent to our inbox every Monday or every 1st of the month. Energy Log displays a history of all reports filterable by template type and configuration. We can generate simple weekly reports or more advanced monthly reports. We can create reports that simulate electric utility invoices, so we can compare our invoices with those of the DISCOM. The analysis of the HVAC system in detail reports allows us to track different indicators throughout the project lifecycle and deliver them in an easy-to-understand format to the energy manager, finance director or the end customer.
Alerts
Another valuable feature of the Energy Log is the alerts. Area alerts are extremely simple to configure and let us put the system to work for us by configuring alerts and monitoring variables. This feature alert intimates us the instant there is an inconsistency in the system, which means we can react immediately to malfunctioning systems and failures and greatly reduce down-times. Energy Log has a range of pre-configured alerts that are designed to catch common potential problems such as excesses or reactive penalties which show us the exact cost of a penalty as soon as it is incurred. The alerts areas organized by locations by our custom configuration which makes it easy to access and view all alerts. We can also configure alerts to be sent by email or SMS to anyone registered in the platform. This should give you a good sense of the most basic of Energy Log extensive functionality. You have seen its ability to improve all aspects of energy management from analyzing the consumption of an individual facility to doing comparative analysis. To detecting potential savings and determining the monetary value of improvements. It gives you full visibility of your facilities and systems by using reporting and alerts.
You can visit the below links to access the demo video of Energy Log https://www.youtube.com/watch?v=S93HQchHieE&t=2s
You can also visit us for any assistance https://www.ecoenergies.co.in/contact-us
1 note
·
View note
Text
The One Where Cassie Sees a Nutritionist

Happy Thursday all! C here :)
After discussing my journey to diagnostic clarity in my last post, I wanted to dedicate this next one to my first step in managing my diagnoses holistically.
I left my first job as a social worker (and my nightmarish long-distance relationship) to move to a less rural area with my husband where I now have more access to specialty care. I established care with a new GI doctor (who was much warmer than the first, thank the universe) and she began making referrals to incorporate a more integrated health approach.
First on the list was a nutritionist. At my first appointment, we reviewed my current symptoms (diarrhea, bloating, gas, constipation, and stomach cramping) and what I was eating on a daily basis. I had been making an effort to eat “clean” and was tracking my meals, so she requested my login information for my food tracking app so that she could start helping me find patterns between my symptoms and diet.
She also provided me with a ton of information about FODMAPs and how they could be impacting my symptoms. When I first heard the acronym, it reminded me of that episode of Spongebob where he thinks Mr. Krabbs is a robot and he’s spitting out all of these “bee-boop-boop-bop phrases.” Man, I hope there’s some 90’s babies reading this who understand that reference.
A FODMAP is not, in fact, a robot word. It’s an acronym that stands for Fermentable Oligo-(galactans, fructans), Di-(lactose), and Mono-saccharides (fructose) And Polyls. Basically a fancy list of substances that are difficult to digest and can cause gastrointestinal symptoms. Little did I know that I could be eating “clean,” but still not be eating foods and portions that I could tolerate and digest properly.
So, over the next few months my nutritionist and I would meet, review my food tracker and symptoms, and begin piecing together my intolerances. It was so interesting (and extremely frustrating) to learn that my good intentions of eating “healthy” egg bites from Starbucks in the morning, would inevitably lead to me blowing up the bathroom by noon at work. YO, THERE’S A SHIT TON OF LACTOSE IN EGG BITES ~ WHO KNEW?! My nutritionist. She’s 100% that bitch.
Okay, I’m being over dramatic, but after learning all of this new information I literally felt like that Limitless meme with all of the mathematical equations floating around in the air and a thoughtful me in the middle. Once I’d notice an intolerance, I’d either eliminate that food or decrease the portion size and HAZA! No more bloat or death farts! Did you know that after you eat something you’re not supposed to feel it move through your entire digestive tract? Huh, weird.
But, seriously though. I began learning how to avoid “overflowing my bucket,” aka accumulating too many FODMAPs. If you take in too many FODMAPs in one sitting or even one day, they can overflow from your small intestines (where foods are supposed to be digested) into your large intestines. The perfect recipe (see what I did there?!) for gastrointestinal upset.
I dove into low FODMAP recipe Pinterest boards and started to feel a sense of empowerment that I could control my diet-related symptoms. If I wanted a cinnamon roll full of gluten, I knew what the consequences would be and could choose to have said cinnamon roll in the comfort of my own home, near the comfort of my own toilet.
Memorizing all of the high FODMAP foods and ingredient lists was tough at first. I remember grocery shopping during my first week on the elimination diet and reading every label to find that there was always, inevitably, one ingredient on there that was questionable. The first couple of weeks you’re eating whole foods with little ingredients, just to figure out what you can and can’t tolerate.
Okay ~ I know this post is getting long so I’m going to wrap it up here with a few tips for someone who has recently been diagnosed with IBS, IBD, or Crohn’s.
1. See a nutritionist if at all possible ~ they are so knowledgeable and will make the whole elimination process easier
2. Start a food journal with symptoms
3. Tune into your body after you eat a meal and really notice how you feel (you don’t have to be blowing up a bathroom to be intolerant to a food)
4. Do research on those foods that you notice are triggering symptoms and read up on FODMAPS and the FODMAP elimination diet ~ it sounds hardcore, but honestly I didn’t even do the whole reintroduction period because it was pretty easy to pinpoint what was giving me stinky farts and what wasn’t after a few weeks
5. If FODMAPs are the issue, download the Monash app so that you can have a list of foods to reference at all times (I didn’t fork over the $8 for the app but if you don’t have a wise nutritionist to consult, it might be worth the dough lol more food puns)
6. Find foods that work for you and get creative with them! Buy a sensitive tummy cookbook, scroll through Pinterest ~ there are lots of yummy options for people with food intolerances! (S/o to all of the dairy free alternatives)
If you enjoyed this post, then you can look forward to me doing more deep dives into nutrition in later posts ~ I’m learning more and more everyday and am excited to share all of the nutrition gold nuggets!
#crohns#ibd#IBS#symptommanagement#Nutrition#diet#fodmap#sensitivity#food#diarrhea#constipation#health#Inflammatory Bowel Disease#irritable bowel syndrome
9 notes
·
View notes
Text
The Chrome Web Store Primer Part 3: Pave the Way to Retention Using Analytics
In parts 1 and 2 of this series
We talked about optimizing the Web Store listing for Chrome extension and also about using analytics to optimize the listing for conversion. Once user has installed the extension, our focus shifts to retaining the user. In this article, we explore how analytics can be used to track user behavior with the purpose of optimizing retention.
The three stages of an app lifecycle are installation, activation, and recurring use. Once the users have discovered your extension and decided to install it, the next step is to ensure that they receive the best possible experience, in order to retain them. One of the ways in which we get data about user experience is by tracking all of the different conversion rates within our extension. This data is analyzed to understand and optimize the customer journey so that more and more of the activated users become recurring or active users.
Measuring Retention Baselines
We have now optimized the listing for discovery and conversion. However, once the user installs the extension, we won’t know what is happening or what his experience is unless we can track user behavior. In order to do that, we set up analytics within the extension to keep giving us data that can help measure the baseline retention in terms of both user behavior and user experience.
Many different types of analytics can be added to the extension to collect data that can help profile the user. Some of the ones we use regularly are:
Google Analytics: These are the most commonly used analytics. They give you access to basic metrics like page views and event tracking from within the extension. Their chief use is in gauging which features of the extension are being over or underutilized.
Mixpanel: Detailed executive-level analytics with real-time alerts for unexpected spikes or dips in user behavior. They come with friendly reporting for non-technical teams as well as automatic trend analysis.
Amplitude: Detailed user level analytics for every step of the user journey. Their built-in data analysis is useful for identifying user personas using detailed behavioral metrics.
Smartlook: A combination of event tracking, user behavior replay, and heat maps. You can dispense with the need for manual event tracking with this tool.
Defining KPIs
Engagement metrics for an extension can vary from industry to industry and even within different verticals from the same industry. Data that is received from analytics can be used to measure the success of an extension only if the goals are predefined. From number of login sessions per day to the value of orders placed over a specific time period, the parameters to focus on while defining KPIs can be diverse. However, there are three chief performance indicators in an extension that you cannot afford to overlook.
Activated User: An activated user is someone who has downloaded the extension and performed a meaningful interaction. This can include completing activities such as registration, adding payment method, placing the first order, etc.
Active User: The whole purpose of retention is to increase the number of active users.These are further divided into daily active users and monthly active users. Based on the purpose of the extension, either of these two could become your most important metric.
User Lifespan: Understanding how long users use your extension on an average before they either uninstall it or become inactive enables you to put strategies in place to reduce the churn rate and keep users active.
There are many other types of KPIs that could be used to measure user behavior. It is important to pick the right KPIs to focus on to ensure that you are getting a good sense of the user journey based on analytics data.
Optimization
Once the KPIs have been chosen and defined, it is essential to get an idea of the baseline for KPIs using data from the analytics’ tools. Once that is done, it is time to optimize the entire user journey to bring results closer to the desired KPI goals. Since we now have access to detailed metrics that record each step of the users’ journey, we are able to start tweaking the extension to optimize the path from installation to activation as well as the users’ path from activation to recurring use. Different promotional strategies could be put into place to motivate users to keep using the extension, especially when the results from trend analysis suggest that they are about to drop off. Analytics also provide insights into the results of applying these strategies viz., which ones work best, as well as pinpointing specific strategies that are most effective with different types of user personas.
In a Nutshell
In order to make sure that users who install your extension also continue using it, it is essential to understand their journey every step of the way. Using data from within the extension gathered via analytics, the baseline of pre-defined KPIs can be measured. This baseline can then be used as the starting point to optimize user experience through marketing strategies or tweaks in the extension itself. The results of these changes can be monitored through continued use of the various analytics’ tools. Do remember to check out parts 1 and 2 of this article series for a complete low-down on everything to do with Chrome Web Store extensions post-development.
1 note
·
View note
Text
One Step Behind
A crimelord heavily reliant on technology wasn’t just holing up and sexually torturing a criminal. He was torturing a criminal and using them to emotionally manipulate a master thief and gifted hacker. There was only one logical way for Manic to attack the situation.
Countless days of planning went into what was actually no more than twenty minutes of careful espionage. Stealing an employees login information was pitifully easy. Further accessing various security systems from there even easier. Looping camera feeds to footage of empty halls. Pinpointing security blindspots in patrol laps. It all went smoothely. Exceptionally smoothely... ...
But he just had to take the luck and keep going. The scarcely used utility elevator was descending dozens of stories, but as soon as those doors opened again, they would be free.
“We’re almost out, dude,” Manic quietly conferred to the dalmation. His eyes lay glossed over, stance awkward and pained from the abuse he’d endured. He couldn’t bring himself to dwell on the sights he saw in that dank torture room, but even worse was the Stockholm way he seemed to almost enjoy this fate. The malfitting running clothes he’d brought for the dog were the first bit of shame he’d had in months.
He couldn’t think about that. His right hand tapped at his electronic tablet, left at a portable keyboard attached inside his vest. His tracks were almost covered. The display lights almost reached the ground. They were almost there.
For the moment the elevator bucked at ground level, Manic could almost feel his heart stop.
He couldn’t feel a single thing. Not as the doors opened. Not as the four AM nightscape greeted him with vague neon lights under the smoggy sky, and Scourge standing directly at the doors.
His skin was bleach. His mind television static. Nothing formed. Nothing moved. All function was gone.
@pandemonium-in-purple
21 notes
·
View notes
Text
Observability for Microsoft Teams; How, What, and Why?
What Would We Do Without Microsoft Teams Monitoring

As one of the leading enterprise collaboration software globally, Microsoft Teams helps remote workers come together and stay productive. But while IT already has tools to monitor Teams call quality metrics, the pandemic shifted the organizational landscape with all of us working remotely from home. Or at least work in a hybrid way! So what does that mean for Teams monitoring now?
The shift necessitates a newer Microsoft Teams monitoring strategy approach that combines synthetics with real user monitoring (RUM) to get a complete seamless digital experience.
Today, we list five benefits that businesses can reap by monitoring Teams end-to-end performance with the Exoprise Service Watch RUM tool. So, let’s dive in…
Ensure Optimal Cross-Team Collaboration for a Distributed Workforce
Service Watch ensure optimal business and knowledge worker collaboration utilizing Microsoft Teams from anywhere in the world. How? The RUM tool provides a baseline and benchmark experience score across the entire distributed workforce no matter what network, ISP, proxy, or latencies they experience. IT can immediately pinpoint employees encountering sub-par Teams (Desktop or web app) experience and proactively reach them.
Operational teams have critical visibility into the three built-in Digital Experience Scores for every machine where the Service Watch agent is deployed.
Desktop Experience Score (DXS)
Web Experience Score (WXS)
Application Experience Score (AXS)
These agents collect real-time session performance data through low-level network statistics alongside browser and protocol synthetics. The combination is distilled into experience scores and indexes to make it easy to quickly detect and rectify problems no matter where work happens.
Troubleshoot Microsoft Teams Performance Issues in Minutes
Are you seeing issues with Microsoft Teams service delivery? Is your end-user not able to connect to Teams? When problems like these surface, your reputation is on the line. Not only that, you have limited time in resolving an application service issue. So don’t wait for your employees to contact you. Instead, with critical Teams monitoring alerts, your team can be aware and start troubleshooting faster. Generally, the application issues could relate to audio-video jitter, packet loss, unsuccessful login, dropped connection, or crashes.
While Exoprise synthetic sensors discover Teams health metrics and hop-by-hop network path details in your tenant, RUM collects experience insights from a digital user perspective. Instantly get all the details from both spectrums to accurately pinpoint the root causes, bottlenecks, and resolve incidents faster.
Deliver Great User Experience with Complete Observability
While monitoring is essential to track the overall health of the Microsoft Teams application, it typically orients towards trends analysis and how the app is performing during a failure such as an outage. But don’t stop at that. Because when an outage strikes, you need to know the “what” and “why” of an application’s operational internal state. And that’s where observability comes in.
In addition to synthetic testing for MS Teams service quality and VoIP network traffic metrics, Service Watch collects browser and non-browser session trace data from endpoint devices. That includes Wi-Fi, VPN, Proxy, ISP, LAN/WAN connectivity, sub-domains, and underlying system resources. Collecting this information gives IT full context, visibility, and granular insights into Teams service requests and failures. Correlating data from synthetic transactions and real user behavior provides the complete experience picture.
Read more about:
Complete Monitoring for Microsoft Teams
Monitoring ALL of Office 365 with Exoprise
Service Watch Real User Monitoring
Watch Our Video on Monitoring Microsoft Teams AV Performance
https://www.exoprise.com/resources/how-to-monitor-microsoft-teams-video-tutorial/
Check out our video to learn how to effectively monitor Teams Audio Video conference call quality. Quickly detect application and network performance problems in your environment.
Localize Teams Issues using Custom Monitoring Dashboards
Dashboards are usually the starting point for network and application teams to constantly monitor the health of an application and get high-level summary information. Exoprise dashboard layouts come with widgets (scorecard, map, graph) that are easily customizable for various personas in your organization, such as help desk, application owners, admins, and upper management. In addition, you can configure widgets based on specific parameters and filter them over a particular period for reporting and analysis.
When Teams outage strikes, the IT helpdesk can get overwhelmed by receiving a number of incident tickets. Use our dashboard to quickly visualize which part of the world the outage is happening in and localize the problem. In another scenario, remote workers’ personal devices, browser, or LAN issues may prevent them from connecting to Teams. Service Watch Desktop dashboard can uncover whether this problem is with a particular user or the entire remote workforce. Thus, saving immense valuable time for helpdesk teams.
Communicate Early Across Silos with Proactive Outage Detection
You may have disparate tools and employees working in multiple departments of your company to monitor enterprise application services. What if some of these tools don’t detect the Teams outage in time? Or what if they do not have all the necessary detailed metrics to begin troubleshooting? Finger-pointing, conflicting information, and blame games will escalate, leading to business and remote workers suffering.
Exoprise proactively detects ALL Microsoft 365 outages 30 mins to 2 hours before Microsoft reports them.
With CloudReady synthetics and Service Watch RUM, receive early Teams outage notifications and real-time user experience insights in a single pane of glass. As a result, improve internal communication and inform employees early about ongoing Teams application status updates from the service provider. In addition, you can also reach out to Microsoft to recover SLA credits using our uptime and availability dashboard.
Start Service Watch Free Trial Today
Browser RUM and Endpoint Monitoring
Service Watch takes minutes to deploy and is configurable to securely watch only the apps and domains that are mission-critical for supporting an enterprise environment. Correlate end-user performance with the app and network intelligence.
FREE TRIAL
This blog was originally published at The Crowd-Powered Blog on Nov 9 2021
0 notes