#june bpc
Photo

JOMP BPC - June 14th - Leatherbound
my favourite edition of Alice in Wonderland 💜
#Alice In Wonderland#Alice Through The Looking Glass#Alice's Adventures In Wonderland#justonemorepage#jompbpc#booklr#bookblr#trcc original#portraits#Lewis Carroll
94 notes
·
View notes
Text
TMC Timeline
I'm not including anything before Mark's birth. Aside from that, lmk if I'm missing anything or somethings wrong.
1974
July 24— Mark is born
?- Thatcher is most likely born this decade
1981
MandelaTech is formed, US Department of unforeseen temporal phenomena too
1982
95% increase in MAD cases
1988
January 18th— Adam is born in Mandela
March 7-- Jonah is born
?— Eve is most likely born
1989
?-- Sarah is born when Mark is 15
1990
Population: 19,867
June 8— Jude and Lynn married
1991
Population: 19,465
1992
Population: 14,763
April 4— Thatcher’s and Ruth’s promotion, Thatcher is in his twenties
August 29— Jude and Lynn divorced
August 30— Pictures of window (exhibition)
September 13-15— Mark and Cesar. Mark died on the 15 (Sarah is 3)
September 14— Adam is tested at 4
September 21— Mark's body was discovered
?— Intruder Alert takes place. Jude calls Ruth and Thatcher. Ruth is killed.
1995
Population: 5,024
March— Newspeak issue ("Off duty mandela officers withhold information about alternate invasion")
2004
Population: 2,403
July 3— Post created for Mandela Meerkats vs Brighton Bunnies soccer game on the 21st (old Mandela police site leak)
July 24— Sarah recorded the message on mandelapolice.com
November 12— Post is created about Mandela’s population decrease (old Mandela police site leak)
2005
Population: 2,069
US Department of Temporal Phenomena releases "Know Your Enemy-A guide on alternate types as of 2005"
2006
Population: 1,786
June 11— Sarah advertises BPC
2007
Population: 1,687
July 10— Adam is added to BPC, and it becomes BPS! Adam makes the first entry in his diary
July 14— Adam shows Sarah the first piece of footage
July 15— Adam and Sarah watch the green hand video. Adam makes his next diary entry about this
July 17— Adam finds Jonah online
Population: 1,687
2008
Population: 1,347
June 24— Thatcher accepts Eve into department. (I'm not sure if this part is still canon to the series because it doesnt really line up with Vol 4 and Alex had taken the video down)
August 14— Adam's 3rd diary entry about sleep paralysis
2009
Population: 1,075
Soccer game video and Mymovie.mp4
(Winter break) Jan 10-13— Volume 2. Takes them a day to arrive.
Jan 13-- Jonah leaves and offs himself. Adam eventually leaves the house, and walks through snow until he finds the van
Past Jan 13— Sarah and Adam talk about Jonah
Jan 14- Dave's death at Gabriel Church (church Sarah and Mark went to) is reported on Channel 3. His death was around midnight. Nurses talk about him later in the evening.
Jan 15— Adam's 4th diary entry about waking up and hearing his screams from the van. It makes him feel bad
Jan ?- Adam goes all 'Preacher Mode' on Eve. Sarah eventually contacts her asking about him.
Jan 16- Thatcher drives out to Werksha at 1:57 and finds Adam in his home at 2:21. Adam starts screaming (and Thatcher does too from MAD). At 4, he drives him to the station and comforts questions him. Meanwhile, Sarah hacks into the security cameras and watches this go down.
(Last edit: November 24, 2023)
181 notes
·
View notes
Text
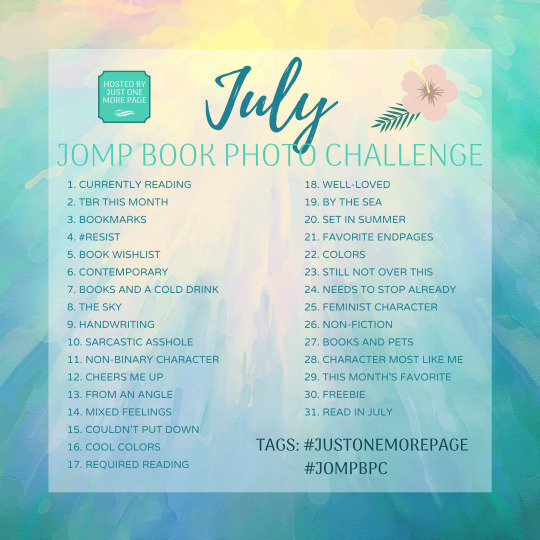
JOMP Book Photo Challenge hosted by Just One More Page 📚 📷
Month: July ; Tags: #justonemorepage • #jompbpc
Summer is already here and July is a week away! I hope everyone has been enjoying their time so far - my whole month of June has been filled with trips, hah, culminating in a week-long beach vacation starting tomorrow! - and here's your BPC prompt for the new month!
Click here for the FAQ, and as always, please feel free to ask me if you have any questions. ❤️ Enjoy!
38 notes
·
View notes
Note
All of the disney ducks could kill Macbeth but especially boyd (because he's a robot), may, june and webby (because they're clones), and lena (because she's a living shadow) from Ducktales 2017
Well, this is a big ask. Seems I'll need to break out our first instance of the...
LIGHTNING ROUND!
(Where we go through the entire* cast of a piece of media in the same post with minimal detail)
Scrooge McDuck: Yes, UBC (Egg)
Huey Duck: Yes, UBC (Egg)
Dewey Duck: Yes, UBC (Egg)
Louie Duck: Yes, UBC (Egg)
Webbigail "Webby" Vanderquack: Yes, GC, UBC (Clone), BPC (Scrooge)
Donald Duck: Yes, UBC (Egg)
Launchpad McQuack: Yes, UBC (Egg)
Mrs. Beakley: Yes, GC, UBC (Egg)
Della Duck: Yes, GC, UBC (Egg)
Flintheart Glomgold: Yes, UBC (Egg)
Lena Sabrewing: Yes, GC, UBC (Shadow)
Mark Beaks: Yes, UBC (Egg)
B.O.Y.D.: Yes, UBC (Robot), BPC (Mark)
May: Yes, GC, UBC (Clone)
June: Yes, GC UBC (Clone)
*I'm not going to do the ENTIRE cast of most things I get, as you can see here, just all the characters I feel are "main cast" and any others that happen to be mentioned in the ask itself. If there are few enough characters in the media, I'll probably do the entire cast.
41 notes
·
View notes
Text


JOMP BPC JUNE 11: Library or Bookstore?
Library!
Especially now that I can also access their ebooks from the comfort of my own home 📚
32 notes
·
View notes
Text

Hello summer! It's June 21 of the Just One More Page BPC. Summer is the time to reread books!
20 notes
·
View notes
Photo

Happy Birthday! June BPC: Day 22 Possibilities
#HBBPC#DragonBadgerChallenge#book photo challenge#funko pop#funko and books#amanda hocking#switched#forstfire#the lost city#booklr#bookblr#books#june 2022
12 notes
·
View notes
Text
Bioprocess Containers Market projected to grow to USD 9.6 billion by 2026
Bioprocess Containers Market by Type (2D and 3D Bags, Accessories), Application (Process development, Upstream and Downstream Process), End User (Pharma & Biopharma Companies, CMOs & CROs, Academic & Research Institute) and Geography (North America, Europe, Asia-Pacific, Middle East and Africa and South America)
Market Overview
The global bioprocess containers (BPCs) market is projected to grow from USD 2.9 billion in 2021 to USD 9.6 billion by 2026, at a CAGR of 26.3% during the forecast period.
Bioprocess containers are single-use, flexible containers system widely incorporated for handling sterile liquids. Moreover, these containers are employed for vaccine manufacturing and media preparation in the biopharmaceutical industry. Their basic function is to increase the speed of ongoing biopharmaceutical process and aid in storage of sterile fluids. Furthermore, bioprocess containers are cost-effective and are equipped with plastic films, ports, tubing, and fittings. They are readily integrated into a variety of high-performance systems for all steps in the production of biologics.

Growing biologics market, affordability and sustainability of single-use bioprocess technologies, and rising biopharmaceutical R&D and their power density are some of the factors that have supported long-term expansion for Bioprocess Containers Market.
World Health Organization (WHO) officially declared the outbreak of the virus as a pandemic, a mix of established pharmaceutical companies, as well as players in the bioprocess containers market, have stepped forward to develop treatments and vaccines that target the infection caused by the novel coronavirus. Therefore, the growing adoption of single-use technologies for COVID-19 pandemic-related research, coupled with increasing vaccine development by key players, is expected to have a positive impact on the bioprocess containers market.
Request Sample Pages of Report: https://www.delvens.com/get-free-sample/bioprocess-containers-market-trends-forecast-till-2028
Regional Analysis
North America accounted for the largest share of the bioprocess containers market. The large share of North America can be attributed to the presence of an established biopharmaceuticals industry and major players in the region.
Competitive Landscape
Sartorius Stedim Biotech
Thermo Fisher Scientific
Danaher Corporation
Merck Millipore
To Grow Your Business Revenue, Make an Inquiry Before Buying at: https://www.delvens.com/Inquire-before-buying/bioprocess-containers-market-trends-forecast-till-2028
Recent Developments
In June 2021, Avantor, Inc. (US) acquired RIM Bio, a leading China-based manufacturer of single-use bioprocess bags and assemblies for biopharmaceutical manufacturing applications. This acquisition helped the company expand its bioproduction footprint in China.
In April 2021, Sartorius Stedim Biotech (France) opened a new Customer Interaction Center (CIC) in Beijing, China, to expand its presence in China and to meet the high demand from the growing biopharmaceuticals market.
Reasons to Acquire
Increase your understanding of the market for identifying the best and suitable strategies and decisions on the basis of sales or revenue fluctuations in terms of volume and value, distribution chain analysis, market trends and factors
Gain authentic and granular data access for Bioprocess Containers Market so as to understand the trends and the factors involved behind changing market situations
Qualitative and quantitative data utilization to discover arrays of future growth from the market trends of leaders to market visionaries and then recognize the significant areas to compete in the future
In-depth analysis of the changing trends of the market by visualizing the historic and forecast year growth patterns
Direct Purchase of Research Report at: https://www.delvens.com/checkout/bioprocess-containers-market-trends-forecast-till-2028
Report Scope
Bioprocess Containers Market is segmented into type, application, end user and region.
On the basis of Type
2D bioprocess containers
3D bioprocess containers
On the basis of Application
Upstream Processes
Downstream Processes
Process Development
On the basis of End-User
Pharmaceutical & Biopharmaceutical Companies
CROs & CMOs
Academic & Research Institutes.
On the basis of Region
Asia Pacific
North America
Europe
South America
Middle East & Africa
Read Related Industry Report:
About Us:
Delvens is a strategic advisory and consulting company headquartered in New Delhi, India. The company holds expertise in providing syndicated research reports, customized research reports and consulting services. Delvens qualitative and quantitative data is highly utilized by each level from niche to major markets, serving more than 1K prominent companies by assuring to provide the information on country, regional and global business environment. We have a database for more than 45 industries in more than 115+ major countries globally.
Delvens database assists the clients by providing in-depth information in crucial business decisions. Delvens offers significant facts and figures across various industries namely Healthcare, IT & Telecom, Chemicals & Materials, Semiconductor & Electronics, Energy, Pharmaceutical, Consumer Goods & Services, Food & Beverages. Our company provides an exhaustive and comprehensive understanding of the business environment.
Contact Us:
UNIT NO. 2126, TOWER B,
21ST FLOOR ALPHATHUM
SECTOR 90 NOIDA 201305, IN
+44-20-8638-5055
0 notes
Text
Hacking - EVE University Wiki

💾 ►►► DOWNLOAD FILE 🔥🔥🔥
Creating syllabi is no longer our process for new classes, and no classes in the syllabus library are considered current. They are here for historical purposes only, as well as an optional starting point for designing new classes. Please do not assume any of the classes you find here have slides, or have even been taught for many years. If you do use information in a syllabus, ensure that you have brought it up to date with contemporary EVE. This class covers completion of the hacking minigame introduced in the Odyssey expansion released on June This class assumes students have taken Exploration , or understand the information included in it. Due to the unpredictable nature of Relic and Data sites there is currently no practical aspect to this class, though if you wish to scan one down and practice you can do so at your own risk! Check before the class whether someone is recording it and ask someone to head off any 'is this class being recorded? This course is designed primarily for people who have had little or no exposure to the hacking minigame, or are having trouble undersstanding what the different systems do. Over the next hour or so we will cover the basics of hacking and move on to some tips and tricks that will help you avoid being ganked too frequently. Instructor should then introduce himself or herself - covering relevant experience level and background. Only two skills are required to hack effectively only one if you choose to specialize in one type of site. Hacking -- Proficiency at breaking into guarded computer systems. Required skill for the use of Data Analyzer modules. Archaeology -- Proficiency at identifying and analyzing ancient artifacts. Required skill for the use of Relic Analyzer modules. This puts the Magnate at a slight disadvantage due to having to forsake one of these modules, and the Heron, Buzzard and Helios at an advantage as they can fit an extra utility mod e. Three pieces of equipment are needed to hack effectively. Various meta and T2 versions of each piece of equipment are available, with T2 requiring higher levels in the relevant skill listed above. This module allows you to scan a container before or during the hacking minigame to see what items are inside. Some containers in low-difficulty sites are completely empty, making the hack attempt a wasted effort. Other times, the loot is such low value that a harder-difficulty hack is not worthwhile. Relic sites mostly contain salvage material with estimated values ranging from a few hundred to millions of ISK per item. They tend to contain more items than Data sites, and as the average value of the loot increases as Security Status decreases these sites tend to be more profitable in Low-Sec and Null-Sec. After successfully completing the Hacking Minigame, open the hacked container like a regular container and take whichever of its contents you would like. Usually just Loot All, but sometimes consider leaving the high-volume low-value items, if your cargo hold is getting full. You can tell how difficult it is to access a container, and how valuable its loot is likely to be, based on its name. The colour of the System Core will also change based on difficulty. More difficult containers are only found in Low- and Null-Sec. In order of difficulty, Relic site containers are:. Data sites contain items used in the research and manufacture of items. Unlike Relic sites, where it's worth collecting all items, Data sites contain some items that are not worth collecting. Containers will contain both high value, small volume items and low value, large volume items; you can very quickly fill up your cargo hold with useless items if you're not careful. They will also sometimes contain BPCs and skillbooks. Unlike Relic sites, the value of the loot doesn't appear to change a large amount between High-, Low- and Null-Sec space aside from an increased chance of valuable BPCs in lower security systems also present at Relic sites. With the Kronos release in June , there is no more loot-spew. So simply open the hackable container like a regular container, and take whichever of its contents you would like. In order of difficulty, Data site containers are:. To complete the hacking minigame you must locate and destroy the System Core. Once this happens the container can be opened and looted. Loot equals profit! To navigate around the hacking minigame you use a Virus. Your Virus has two stats, strength and coherence, which are defined in part by your skills and equipment. Strength is your Virus's offensive ability, it is the 'damage' inflicted by your attack. It is shown by the red bar on the right of the icon and the number underneath it. Coherence is your Virus's health, once this is depleted your Virus is destroyed. It is shown by the orange bar on the left of the icon and the number above it. Defense Subsystems and the System Core also have a strength and coherence rating. When you attack a subsystem your strength is removed from its coherence, then its strength from your coherence. If you destroy a subsystem i. Once uncovered you must collect a Utility Subsystem to use it. You can hold three Utility Subsystems at a time, which are activated by clicking on them then on the target where applicable. Activate the Self Repair as soon as you discover it to free up space in your Utility Subsystem bar and boost your coherence as soon as possible. The Self Repair will take up one of your three slots for two additional turns after activating whilst it finishes its work. You can use a Self Repair to boost your coherence above your starting value, and above the top of the bar on the graphic! Note that you do not need to click on that item for 3 turns—you select what you're applying it to, and can then click elsewhere, while it applies per-turn to the selected item for you. Save your Secondary Vector for a Virus Suppressor unless it's absolutely necessary to use it on something else. Defensive Subsystems are used to hamper your hacking efforts. Once they are uncovered on the board they will block you from accessing all nodes adjacent to them and provide either passive or active resistance to your Virus. Firewalls should not be attacked unless necessary, try clicking around the rest of the board first to see if you can find the Core without wasting coherence on the Firewall. Antivirus should not be attacked unless necessary, try clicking around the rest of the board first to see if you can find the Core without wasting coherence on the Antivirus. They are good targets to use a Polymorphic Shield or Kernel Rot against due to their high strength. Destroy Restoration Nodes a soon as you discover them, as the longer they're on the board the harder destroying the other defensive systems will be should it become necessary. When a Virus Suppressor is active avoid attacking anything unless it's absolutely necessary as you'll take twice as many turns and twice as much coherence loss to destroy your target. Use a Secondary Vector on the Suppressor if you can and spend three moves doing something else as the Vector can destroy the Suppressor without your assistance and isn't affected by the strength loss. The color of the System Core reflects the difficulty of the container: Green for easy; Orange for medium; Red for hard. A number of actions are available when hacking a container. Each of the following counts as one 'move' in the hacking minigame, which is worth bearing in mind as more complex systems will have 'per move' effects:. By clicking on a node you have not yet visited that is next to a node you have visited you will reveal its contents. As you click on each node, if it is unoccupied, it will briefly display a "minesweeper" number, from 1 to 5, which indicates the distance from the nearest good or possibly good node. The numbers can be used to guide the direction that you should move around the grid. Remember, this may not be a benefit! If the opposing node has coherence remaining its strength is then removed from your coherence and the move ends. This means that if your strength completely depletes the opposition's coherence then it does not get the opportunity to damage you in return. Thanks to whichever Unista uploaded this in the first place! Spam the D-Scan whilst scanning and hacking and get ready to run if you see something closing in; the extra few seconds might be what saves you. Also keep an eye out for other probes in system, both Core and Combat, and for Stealth Bombers popping up; if you see either consider moving on. Check people in Local — Double-click the names in Local to get an idea of who is in system with you. People with a high Security Status are less likely to attack you than people with low or neutral status, but this shouldn't be relied on. If you're exploring in Faction Warfare space you can worry less about people in FW corps, but still keep your eyes open. Consider tagging people you have previously run in to in their Notes field or by adding them to your watchlist. They'll show up highlighted, allowing you to easily see when someone new enters the system so you can check them out see above. Turn auto-repeat off — You only need to activate your Data or Relic Analyzer on the container once to initiate the hacking minigame; by turning auto-repeat off you save a little bit of cap and can get straight back to it if you fail an attempt. System Core location — The System Core is often located on the opposite side of the board to your start location it's not always the exact opposite side, as some people seem to believe. Don't spend too long on the nodes near your start location as it appears less likely it'll be there. Use the 1—5 numbers to guide your direction of movement: move away from high numbers and towards low numbers. Go everywhere 'clear' first — Don't attack Defense Subsystems you don't need to; conserve your coherence, explore all available nodes first then review the situation and plan where to attack. Eliminate first the Subsystems that will unlock large chunks of board before worrying about the ones blocking one node. Use the "minesweeper" numbers — Use the 1—5 numbers in empty nodes to guide your movement around the grid. In general, you want to click in directions that make the numbers smaller. Note that the numbers disappear as you move along, so you need to remember where there were 5's, so you know which areas not to bother going back to later. Orbit at 3km — If you're sitting still you're a sitting duck if someone jumps you! Orbit the container whilst completing the hacking minigame then approach when you're ready to destroy the System Core. By orbiting you make yourself harder to hit and by staying more than 2km from the object you may be able to get your cloak up before they can target you. Don't trust anyone — Even the University runs classes on how to use CovOps ships for combat so never assume that someone isn't a threat just because they're in an exploration ship! Even if it proves unnecessary most of the time you'll be thankful those few times it does save you, and you normally won't lose anything by doing so. Drop a can at the warp-in — The exact location someone arrives on-site will vary depending on where they're coming from, but if you drop a cargo container at the point you land there's a fair chance this will de-cloak anyone else who lands on-grid trying to get the drop on you. Jump to: navigation , search. This is a deprecated class syllabus, intended as historical record for the teaching department. Categories : Syllabi Classes. Namespaces Page Discussion. Views Read View source View history. This page was last edited on 9 February , at A node is a location on the hacking board. All nodes but the one you start on begin covered, you progress the hacking attempt by uncovering more nodes. A covered node is shown on the left. A Data Cache is a node containing a hidden Subsystem. You can uncover the Subsystem by clicking on the node again but the Subsystem may not be friendly; only uncover them if you have no other options available. Found in all levels of container. The amount restored seems to vary based on the difficulty of the container harder containers restore less and how much coherence your Virus currently has lower coherence has more restored , though currently we haven't worked out exactly how the amount is calculated. Save your Kernel Rot for an appropriate target with high coherence. Only found in Medium and Hard containers. Save your Polymorphic Shield for an appropriate target with high strength. Only found in Hard containers. Each move it will pick a different Defensive Subsystem at random and restore some of its coherence. This can put a subsystem's coherence above its starting value.
1 note
·
View note
Text

JOMP BPC - June 25th - Genre
is “plucky girl finds herself caught up in the mystery of a strange house” a genre? if so, that’s mine
#neil gaiman#ve schwab#shirley jackson#justonemorepage#jompbpc#booklr#bookblr#trcc original#portraits#coraline#gallant#the haunting of hill house
92 notes
·
View notes
Text
China surprise cuts interest rates
China surprise cuts interest rates
File – 26 June 2022, China, Hong Kong: Workers prepare to put up the Chinese flag for the 25th Anniversary Homecoming Celebration Ceremony in Hong Kong’s Wan Chai District. Photo: Emmanuel Serna/SOPA Images via ZUMA Press Wire/dpa – Emmanuel Serna/SOPA Images via Z / DPA – File
The People’s Bank of China (BPC) has unexpectedly cut two of its main references for loans to the country’s banking…
View On WordPress
0 notes
Text


June Just One More Page BPC 📚 // Day 1 ➜ Introduce Yourself.
↳ Hi, my name is Jen, and I felt pretty today. 🥰🥰
#justonemorepage#jompbpc#day 1#book photo challenge#books#bookshelves#gpoy#jomp photography#jomp original
31 notes
·
View notes
Text
MLS and Black Players for Change Commemorate Juneteenth with “Freedom to Be” Jersey Numbers and Auction for Impact Organizations
NEW YORK (June 15, 2022) – Major League Soccer today announced a series of initiatives to celebrate Juneteenth – the historic date commemorating the emancipation of enslaved African-Americans in the U.S. All programs are a close collaboration between MLS, the league’s 28 clubs, and Black Players for Change (BPC) – an independent organization of Black MLS players, coaches, and staff working to…

View On WordPress
0 notes
Photo

Shelf-Confidence June BPC
Day 19: Reading With a View
#myownlittlebookcorner#shelfconfidencebpc#book photo challenge#booklr#books#still me#i-breathe-therefore-i-read#My Books#book photography#my post#june bpc#me sorta
92 notes
·
View notes
Text





June BPC Day 4: Summer Lovin’
Why yes I will take any excuse to talk about Summer in Orcus! It’s a sweet, wonderful story!
Someday I’ll have convinced someone to read it!!!
47 notes
·
View notes
Text

July 22 of the Just One More Page BPC is Colors. This book was hard to sort for my June rainbow bookshelves setup...
15 notes
·
View notes