#cdn records
Audio
hexenklad [canada] // pagan black metal.
"cold beauty of winter” is from the album “heathenheart”, released via cdn records in 2021.
#bandcamp#pagan black metal#black metal#blackmetal#cdn records#hexenklad#canadian black metal#folk black metal
1 note
·
View note
Text
Out Now! CDN Records Unleashes Canadian Thrash KORROSIVE 's New Album "Toxic Apokalypse" On CD + Cassette & Vinyl Coming 2023
Out Now! CDN Records Unleashes Canadian Thrash KORROSIVE ‘s New Album “Toxic Apokalypse” On CD + Cassette & Vinyl Coming 2023
L-R: Korrosive Lineup | Carlos Rodriguez (Bass) | Kaveh Afshar (Drums) | Rad Zarei (Vocals) | Jack Neila (Guitar) | Derek Solomos (Guitar)Photo Credit – Michael Jari Davidson
CDN Records has just unleashed Canadian thrashers Korrosive’s latest album “Toxic Apokalypse” on CD, which is available at https://cdnrecords.com/shop/korrosive-toxic-apokalypse/. The full-length was released digitally on…

View On WordPress
0 notes
Text
Professional Website Hosting and Management Services
In today’s digital age, having a strong online presence is crucial for any business or organization. A well-designed website serves as a virtual storefront, allowing you to reach a global audience and showcase your products, services, or ideas. However, creating and maintaining a website requires technical expertise, time, and resources that not everyone possesses. That’s where professional website hosting and management services come into play.

What is Website Hosting?
Website hosting refers to the process of storing your website files on a server that is connected to the internet. When someone types your website’s domain name into their browser, their device connects to the server, retrieves the website files, and displays the webpages. Website hosting is a critical component of your online presence, as it ensures your website is accessible to visitors at all times.
The Benefits of Professional Website Hosting and Management Services
While it is possible to host a website on your own, opting for professional website hosting and management services offers numerous advantages. Let’s explore some of the key benefits:
1. Reliability and Uptime:
Professional hosting providers offer reliable and secure servers, ensuring that your website is accessible to visitors around the clock. They have redundant systems in place to minimize downtime and address any technical issues promptly. This ensures a seamless browsing experience for your users, enhancing their trust and satisfaction.
2. Technical Support:
Managing a website involves dealing with technical challenges such as server configuration, software updates, and security patches. With professional hosting services, you have access to a dedicated support team that can assist you with any technical issues that arise. This allows you to focus on your core business activities while leaving the technical aspects to the experts.
3. Scalability:
As your business grows, so does the traffic to your website. Professional hosting providers offer scalable solutions that can accommodate increased traffic and ensure optimal performance. They have the infrastructure and resources to handle high volumes of visitors, preventing your website from becoming slow or unresponsive.
4. Enhanced Security:
Website security is of paramount importance, especially in an era of increasing cyber threats. Professional hosting services implement robust security measures, including firewalls, malware scanning, and regular backups, to protect your website and its data. They stay updated with the latest security protocols and continuously monitor for any potential vulnerabilities.
5. Additional Services:
Many professional hosting providers offer a range of additional services to enhance your website’s functionality and performance. These may include content delivery networks (CDNs) to improve page load speeds, SSL certificates for secure data transmission, and automatic backups to safeguard your data in case of unforeseen events.
Choosing the Right Professional Hosting Provider
With numerous hosting providers available, selecting the right one for your specific needs can be daunting. Here are some factors to consider when choosing a professional hosting provider:
1. Reliability and Uptime Guarantee:
Ensure that the hosting provider has a proven track record of reliability and offers an uptime guarantee of at least 99%. You don’t want your website to be inaccessible due to server issues or maintenance downtime.
2. Scalability Options:
Consider the scalability options offered by the hosting provider. Can they accommodate your website’s growth and handle sudden traffic spikes? A flexible hosting solution is crucial to ensure your website performs well under varying loads.
3. Security Measures:
Check the security measures implemented by the hosting provider. Are they proactive in addressing security threats? Do they offer SSL certificates, regular backups, and malware scanning? Robust security measures are essential to protect your website and sensitive data.
4. Technical Support:
Ensure that the hosting provider offers reliable and responsive technical support. Look for providers that offer 24/7 support through various channels like live chat, email, or phone. Quick assistance during emergencies can save you valuable time and prevent potential losses.
5. Pricing and Value for Money:
While cost shouldn’t be the sole deciding factor, it’s important to compare pricing plans and determine the value for money offered by different hosting providers. Consider the features, performance, and support you receive for the price you pay.
Conclusion
Professional website hosting and management services provide businesses and organizations with a reliable, secure, and scalable online infrastructure. By outsourcing the technical aspects of website management, you can focus on your core activities while ensuring an optimal user experience for your website visitors. Choosing the right hosting provider is crucial to unlock the benefits of professional website hosting and maximize your online presence.
Investing in professional hosting services is a wise decision for any business or organization that values their online presence. It allows you to leverage the expertise and infrastructure of a dedicated team while ensuring your website remains accessible, secure, and performs at its best. Don’t underestimate the impact that a well-hosted and managed website can have on your brand, customer satisfaction, and business success.

Source
#WebManagement#ServerHosting#WebsiteMaintenance#TechSupport#CloudHosting#DataCenter#ServerManagement#WebHosting#ITInfrastructure#WebsiteSecurity#ServerAdmin#HostingSolutions#WebsitePerformance#ServerMonitoring#WebDevelopment#CloudComputing#NetworkSecurity#DomainRegistration#BackupandRecovery#Cybersecurity
22 notes
·
View notes
Text

“Sometimes I feel like reaching down from the stage and grabbing people and slamming them against the wall with my voice. Ι want to make ‘em wake up and listen. I love those people." – Etta James
Born with an epic voice, Etta James fought her whole life for the recognition she finally received.
Etta James was born Jamesetta Hawkins on January 25, 1938, in Los Angeles, California, to a 14-year-old mother, Dorothy Hawkins, who encouraged her daughter's singing career. James would later say, "My mother always told me, even if a song has been done a thousand times, you can still bring something of your own to it. I'd like to think I did that." James never knew her father.
Of her will to survive bad luck, overcoming heroin addiction, and changing times, James mused, "What's kept me going is faith, and trying to prove something. It could be ego. But I never have an ego except when I'm onstage. I just want to prove to people I'm gonna hang in there. And I just hang right in there."
Etta James underwent gastric bypass surgery and lost over 200 pounds. The dramatic weight loss had an impact on her voice, as she told Ebony magazine, “I can sing lower, higher and louder.”
As she entered her 70s, Etta James began struggling with health issues. She was hospitalized in 2010 for a blood infection and other ailments. It was later revealed that the legendary singer suffered from dementia and was receiving treatment for leukemia.
At the end of her life, she was inducted into the Blues Hall of Fame, received a Grammy Lifetime Award, and her album 'Let's Roll' won a Grammy for Best Contemporary Blues Album.
Podcast guests include Poet Lorraine Brooks, the Charlie’s Angels of Outreach, Dr. Monique Renee Rolle DPM, Catherine Schuller AICI, CIP, Susan Greenberg Weiner MS, RDN, CDE, CDN, and Mama Rose Marie. Prize giveaways courtesy of Earth Brand Shoes, Dr. Greenfield’s Diabetic Foot Creams, Cabot Cheese, and Nu Naturals.
Throughout the podcast,, we will spotlight Etta James’ iconic recordings from the “All The Way” and “The Essential Etta James” albums courtesy of SONY MUSIC.
Listen: https://www.blogtalkradio.com/divatalkradio1/2016/02/23/diabetes-late-nite-inspired-by-etta-james
#diabetes#divabetic#diabetic#health#type 2 diabetes#podcast#soul music#sugar#etta james#gastric bypass#weightloss#rhythm and blues#podcasterlife#podcaster#survivor#divas#rnb divas#divas with diabetes
2 notes
·
View notes
Text
Weight loss diet
2 Eating Habits That Drastically Change Your Weight Loss Efforts, Say Dietitians
When it comes to weight loss, you want to focus on maintaining a healthy and happy lifestyle, not just drastically shedding pounds. Weight loss is achievable by many different ways, including exercise and or practicing self-care. Your drinking and eating habits can also affect your weight, and it's important to keep up with your practices.
Sometimes, your weight loss journey may feel like a dead-end, and you want to try and switch your routine in order to keep persevering on your goals. The good news is that there are eating habits that can help you continue your process. The Nutrition Twins, Lyssie Lakatos, RDN, CDN, CFT, and Tammy Lakatos Shames, RDN, CDN, CFT, who are also members of our medical expert board, gathered their insight to help create
1 Divide temptations into single portions and place them in the freezer
Buying produce and other perishables in bulk may make for a successful grocery shopping trip but it forces you to eat everything before the products expire. That's why The Nutrition Twins recommend that when you come home, immediately divide any food that you find tempting into single portions and place them in the freezer.
"Because frozen food requires defrosting, impulse eating will be prevented and willpower is taken out of the equation," say The Nutrition Twins. "This simply requires a plan! Know that you're only having one—and take one serving out to defrost."a list of eating happens that can help drastically change your weight loss efforts.
Seeing your food intake on paper may give you a whole new perspective on what you're eating and how much of it you're eating. Keeping a food diary or journal helps log your food consumption throughout the day.
2 Write down what you eat.
The Nutrition Twins say that research shows that people who record what they eat lose twice as much weight as those who don't. It will hold you accountable and make you aware of what you've eaten. In the particular study of approximately 17,000 people, those who kept daily food records lost twice as much weight as those who kept no records,
2 notes
·
View notes
Text
How can you prevent your WordPress platform from cyber attack.
WordPress is a CMS-based web development tool. This open-source platform provides easy and high-performing app development of online shopping apps, banking apps, social media forums and many more. As a result, WordPress is the extensively popular CMS platform. But its popularity has made it overlooked hence threats of cyber-attack are present with the WordPress website. However, vulnerable data of a WordPress website can easily be targeted but there are various ways, through which you can prevent your valuable web platform. The top 10 ways in this regard are underneath:-
Add CDN-level firewall
Undoubtedly, not only WordPress but website designed using any platform is open to attack from bots and other nefarious actors. An overloaded server can crash and become inoperable as a result of a distributed denial of service (DDoS) assault. CDN-level firewall adds an extra degree of protection by seeing and removing questionable traffic before it reaches the server. By doing this, you can defend your website against bot and DDoS attacks.
Update credentials regularly
However, updating passwords is a common practice but regular practices of credentials gradations minimize the chances of security threats. Additionally, limitations of login attempts reduce the hackers’ chances to hack the website.
Update the WP version and remove plugins
If you are running an older WP version then it provides the opportunity for the hacker to hamper the vulnerable data. Hence it is advisable to timely update the WP version along with the regular update of the login password.
Block comment section
The comment section of a website is the entry door for hackers to take entry into a website’s source code. Due to the regular lack of moderation in this section, it is simple for hackers to smuggle malicious code into otherwise innocent-looking comments. To prevent your website from cyber-attack you can also block the comment section.
Remove plugins
Plug-ins are one of the most appealing features of a WordPress website that enhances the development process and makes the website SEO and user-friendly. But, since these plugins are pre-defined and can be used anywhere during the development process, as a result, it creates the opportunity for hackers to attack the block of the most vulnerable data. So to prevent WP admin it is good to use least or remove plug-ins from the website.
Auto update on plugins
A simple approach to guarantee that all installed plugins and themes are current is to use WordPress' inbuilt auto-update capability. This is particularly crucial for plugins and themes that deal with private information like credit card numbers or personal records. Auto-updates not only provide security benefits but also make sure that all installed software is compatible with the most recent version of WordPress, increasing the reliability of your website.
Security headers
Cross-site scripting threats are reduced by security headers, which stop malicious code insertion. Additionally, adding them lessens the possibility of malware infecting your website and blocks payload-based attacks. Some security header instances are:-
Referrer regulations.
Secure Transport Protocol over HTTP (HSTS).
a code of content security.
X-Frame choices.
X-Content-Type-Options.
Protection from XSS (cross-site scripting).
If you are unaware of the core of web development then it is good to connect with a Digital creative solutions provider who provides WordPress website security along with end-to-solution of your web development need.
4 notes
·
View notes
Text
Trendy technologies used by software companies to develop web based applications
Frontend Technologies
Languages:
HTML for markup and to create the web page document
CSS to style the web page to look awesome
SASS / SCSS for CSS Preprocessor which compiles to the CSS when it is run on the server.
JavaScript for initial client side validations and User Interaction with the browser
jQuery with its UI Components for better UI / UX
We also use other front end languages based on customer requirements.
Frameworks, CDN's, Libraries & Widgets:
Font Awesome, Boxicons CDN for fonts and web icons
Bootstrap for responsive web page building that looks perfect on any device.
Flexbox for layouts
Sweetalerts for popup messages
Responsive data tables for data visualization, Easy record search, importing and exporting data, filtering data and customization is also available.
Isotope is a library provided by javascript that makes it easy to filter, sort, and add Masonry layouts to items on a webpage. When a page is loaded, isotope is supplied to a container within the DOM and targets a specified sets of items within that container.
OWL Carousal, Facebook, Whatsapp and other widget's for better user interface and experience.
Google Font API
Modernizr library provided by javascript that detects the features available in a user's browser. This lets web pages avoid unsupported features by informing the user their browser isn't supported or loading a polyfill.
ZURB to create unique UI / UX.
For more information https://fsh.org.in/it-technologies
3 notes
·
View notes
Text
this is a post about Slamophiliac. i wanna spend some time talking about each album, where i was mentally during its making and the people involved as well as my slices of my life. if you arent interested in that then know that Slamophiliac is as dead as Darryn Palmer or Dazz is. so are all the projects i was involved in. its all dead just like for my passion for the genre. now that the tl;dr is out of the way lets begin.
ABORTED INTO ABSOLUTE INEXISTANCE
i actually love this album still. you can hear how much i enjoyed making the album, same is true of Slam Obsessed and Spilling Entrail's debut album. this was the first thing i ever made that i was proud of, unfortunately, i only remember criticism. bassdrops too loud, bass too loud, boring, shows promise but aint there. those criticisms aside i still love that debut. i also really enjoyed working with Todd Grove and am thankful for encouraging me to take my art more seriously. its sad that we had a falling out but... that's common when your as ill as i am.
SLAM OBSESSED
i dont have much to say about this one i didnt already say about the last one. i really enjoy it despite hating it for years. i did intend it and Spilling Entrail's debut to be sister albums of a sort. the Spilling record would have a more lo-fi style and Slam Obsessed would be more modern. i utterly failed at that. this was also my debut to CDN Records who'd release all but one of the Slamophiliac albums after this one. i know i promised an 8th album Craig but its been 8 years, its not happening.
DISPLAY OF HORRIFIC PERVERSION
my dog died between this album and the last. that's really where my depression started to take hold and you can hear it on this album. the riffs got so lazy, the drums are just the same premade blast beat loops over and over. there's some melodies on this album i like but overall its just uninspired. for those around back then you probably noticed me start to self destruct and self sabotage. picking fights online for dumb reasons. for that im sorry. i was suffering and it was wrong to externalize that.
APHELION
this is the darkest part of the discography. Aphelion and its companion Perihelion were meant to be a double album. a shameless ripoff of Disfiguring the Goddess's Deprive and Black Earth Child. among my many sins as an artist is copycatting. despite my original intention, things got to be too much. i was starting to feel how stunted as a person i was. i decided this would be the last album. id put it out and then unalive myself. the story of the album is humanity desperately searching for a place in the universe and after finding nothing plunge their ship into a black hole. the music on this admittedly is a little more inspired than Display but your can still feel the agony i was feeling in it. at least i can.
SLAM OVERDOSE
this album i wrote a song at a time over the course of 3 months not really planning an album. i just wanted to make singles and play guitar. an album did come however. this is the only one to not get released by CDN. was released by Todd Grove's label and some Russian company i dont remember the name off. this is in my oppinion an okay follow up to Slam Obsessed. not great but good.
PERIHELION
at this point i was just making albums for the sake of it. between Slam Obsessed and this album so much shit had happened. my dog dying, two family members dying, my mom having her first heart attack. not to mention being a closet case so deep in he'd met Azlan. anyway, i just made the most angry shit i could. got a guest vocalist on each song just for marketing. i really want to stress that by this point in the discography the passion was already gone and frankly i would have ended myself if i wasnt such a coward.
SLAM REHAB
kinna fitting for the final album innit? Slam Rehab is just two splits that fell through that i squished together. there's some fun stuff on it but its just more of the same. boring, passionless riffs trying so hard to emulate my favorite bands from a decade prior. its frankly embarrassing that i continued on doing this again and again. truly im sorry i couldnt make better music for all of you.
POST-REHAB
i made a bit of music here and there after Rehab came out, some of it neat like Laparotomy, some of it shit. i got my first actual job in 2019 at 25. yes im basically 10 years behind. i may have been in my early 20s when i was Slamophiliac but mentally i was maybe 15. trauma and a hostile home will do that.
i pretty much dedicated myself to this shitty gas station job. my mental and physical health further declined. i eventually tried to die again May of 2022, at this point i was 27. id never had a romantic relationship, never had any kind of sexual experience that was consentual, i worked a shitty job that was killing me, i was still deep in the closet and living with my abusers.
thankfully i must have had an angel looking out for me cause a dear friend across all those years messaged me and talked me down. i made a promise to him that i would figure it out. id become the best version of myself i could be, id escape the hell i was living.
i would start enbracing my queerness and go on my journey of self discovery, including gender. i met so many amazing people including my now wife. i found religion. fast forward to now, as of writing, i live with my wife in a small college town far away from my abusers. im able to embrace who i am completely.
CONCLUSION
so that's really what it is. i have a different life now. im enjoying what i have and while i have hard days as i unpack my trauma and learn how to move on, i genuinely enjoy my life now. Slamophiliac and being a musician just dont have a place in that. this music is a constant reminder of who i use to be and i cant. im sorry.
i still wanna use this tumblr to talk about music i like cause i am still a fan. i was always a fan really. i also dont regret any of the friendships i made along the way. i wont be easily contacted unless you use this platform cause well, facebook is a cesspit of transphobia and i dont need that either.
it was a fun 10 years but its over yall. please go listen to better artists. ♥︎
#brutal death metal#slamming brutal death metal#transgender#slamophiliac#spilling entrails#yet another trans musician leaving the internet#happy ending#happy pride 🌈
0 notes
Text
Rationalization & Justification
Sometimes I want to pause and figure out why things are as they are. I have noted many times that in the audio hobby people form tribes of rigid beliefs and opinions in the face of contradicting opinions and often facts. This is better, that is better blah blah blah.
First fact: Nelson Pass produced an audio product where the user could turn a knob to adjust the level and perhaps the type of distortion and found that people prefered a certain type and amount of distortion over simple accuracy.
Next Fact: Many people prefer things they describe as warmth and space in say an amplifier. Others prefer neutrality whatever that means. Sum that as preferences rule decisions.
Another Fact: Every audio component has distortion and artifacts and responses that are not in the input signal.
Last fact: "Better things" cost more money.
I think that most of the discussion and arguments over what you use to listen to recorded music is rationalization for purchase decisions. It is economics not what is better, whatever than means.
My preference for vinyl may be because my system is built around it. My turntable, cartridge, and preamp are the most expensive parts of my system. Easy to understand as when I started out LPs were the only quality source available. Replacement cost for that front end would be about 3 to 4 kilodollars based on recent used equipment ads. My CD player was about $400.00.
It is logical to think that if I had spent five to ten times what I did on a CD based system it should sound better, no? My CDs sound pretty good but my best LPs are "better" only by an increment.
Then there is my software base. I have about 600 LPs and maybe 150 CDs. Voting with my wallet LPs won.
So in an absolute objective sonic sense is vinyl better / best? I have my doubts. But as a human I do not have to be objective. Lets put digital versus analog aside for now.
Tubes versus solid state amplifiers next. I think here even the adherents admit it is only a preference. Testing geeks repeatedly prove that the best solid state units generally have less measurable distortion than vacuum tubes. The glass head rebuttal of that is testing people are stupid or if not they cannot measure what we clearly hear as different. Ears are better than meter readouts.
It is clear to me that the things they hear as better are colorations from distortion. Nice pleasant distortion like 2nd harmonics and such. I have gone into much detail on this in previous posts. Oh and I am a long term fan of glass electronics.
When pressed some golden ears admit to masking of details by tube amplifiers but they don't mind that. In reviews of solid state equipment they occasionally admit to transistors being superior for detail but are not warm enough. I can absolutely vouch for a very good tube amplifier masking information I can clearly hear with a transistor amp.
Yet I think the biggest reason for conflict is money. My tube amp, which I think is great, was at least double the cost of my transistor amp, and I got a smoking deal. It is also 1/4 the power. For a given power tube amps cost MUCH more than solid state. Or for the same rough cost they have far less power.
A typical low level tube amp such as an updated Dynaco ST70 is $1500 bucks and up. I see current ads for 6 mid priced tube amps on the Audio mart listing for approximately 1800 CDN all about 60 Watts per channel. In the same place I found 6 Bryston 4Bs at 250 Watts per side for a wee bit more to a great deal less money.
I know that those Brystons have far less distortion than any of those tube amps.
If you just spent double or triple the money for half or much less of the power and several times the measurable distortion you would get a bit defensive, it is only human. Personally I know the things I like about tubes are actually flaws and inaccuracies. To be clear I think these factors apply to power amplifiers. Preamplifiers are different mostly as they do not need output transformers and operate as Class A just like the Transistors do.
There is a sociological / economic thing called conspicuous consumption. Originally described in 1899 by American sociologist Thorstein Veblen during the Guided Age. It is where people who can afford very expensive things buy them to demonstrate they can easily afford them. It is just like an ape drumming his chest in the forest. I place all the really expensive audio equipment in that box and say have fun. Up there the technology or performance doesn't really matter.
1 note
·
View note
Text
10Gbps Germany Server
How do you choose a website hosting provider?
When it comes to building your online presence, selecting the right website hosting provider is crucial. Your hosting provider not only affects the performance and reliability of your website but also impacts your SEO ranking. With so many options available, it can be overwhelming to make the right choice. Here are some tips to help you find the perfect hosting provider for your website.
Understand Your Needs
Before diving into the sea of hosting providers, take some time to understand your website's needs. Consider factors like the type of website you're building, your expected traffic volume, and any special requirements you may have. Are you running a small blog, an e-commerce site, or a corporate website? Understanding your needs will help you narrow down your options.
Reliability and Uptime
One of the most important factors to consider when choosing a hosting provider is reliability. You want a provider that offers high uptime guarantees and reliable server performance. Downtime can have a significant impact on your website's visibility and user experience, so make sure to choose a provider with a proven track record of reliability.
Speed and Performance
In today's fast-paced digital world, speed is everything. Slow-loading websites not only frustrate visitors but also negatively impact your SEO ranking. Look for a hosting provider that offers fast server speeds and optimized performance. Consider factors like server location, caching options, and the use of content delivery networks (CDNs) to ensure lightning-fast load times. For this Ctrlserver offers 10Gbps Germany Server for their customers. They are a well-known speed hosting provider in Europe.
Scalability and Flexibility
As your website grows, your hosting needs may change. Choose a hosting provider that offers scalability and flexibility to accommodate your future growth. Look for providers that offer easy upgrades, additional resources, and flexible hosting plans to ensure that your website can scale seamlessly as your business expands.
Security Features
Security should be a top priority when choosing a hosting provider. Look for providers that offer robust security features such as SSL certificates, firewalls, malware scanning, and regular backups. Protecting your website and your visitors' data is essential for maintaining trust and credibility.
Customer Support
Finally, consider the quality of customer support offered by the hosting provider. Look for providers that offer 24/7 support via multiple channels such as live chat, phone, and email. Responsive and knowledgeable support can make a world of difference when you encounter technical issues or need assistance with your hosting account.
Conclusion
Choosing the right website hosting provider is a crucial step in building a successful online presence. By understanding your needs, and prioritizing reliability, speed, scalability, security, and customer support, you can find the perfect hosting provider to meet your requirements. With the right provider by your side, you can focus on growing your website and reaching your online goals.
0 notes
Text
Unlock Success: Hire Full Stack Developers in India from Qono Tech!
Are you seeking to elevate your digital presence and streamline your development process? Hire Full stack Developers from Qono Tech! Our team of dedicated Full Stack developers in India is ready to revolutionize your project with their comprehensive expertise spanning front-end and back-end technologies. Here’s why partnering with Qono Tech can be your gateway to success.

1. Full Stack App Development Excellence: Our Full Stack developers excel in handling all aspects of app development, from server-side tasks like microservices and authenticating servers to managing CDN assets. With proficiency in testing, continuous integration, and deployment processes, our developers ensure platform compatibility across iOS and Android devices.
2. Cloud-Based App Mastery: Experience seamless development of web and SaaS applications with our seasoned Full Stack experts. From building and deploying to testing and managing cloud-native applications, our team provides unwavering support at every stage.
3. Complete Web Stack Solutions: Elevate your web projects with our proficient Full Stack developers. From design to development, our team is committed to enhancing performance and stability using cutting-edge tools, ensuring faster and more efficient applications.
4. Quality Assurance Commitment: Rest assured with our meticulous QA engineers who uphold the highest quality standards throughout the development process. We guarantee that the final product aligns perfectly with your company’s requirements.
5. Ongoing Support & Maintenance: Our highly skilled Full Stack developers not only excel in technical abilities but also thrive in providing regular upgrades and patches. With our commitment to continuous improvement, your application’s performance remains unmatched over time.
Why Qono Tech Stands Out:
Flexible Man-Hour Allocation: Tailored 160+ man-hours ensure dedicated attention to your project’s needs.
Agile Development Methodology: Our teams ensure rapid progress and adaptability with Agile methodologies.
Confidentiality Assurance: Your project’s confidentiality is safeguarded with our strict Non-Disclosure Agreement.
Integrity & Transparency: We prioritize integrity and transparency, fostering trust throughout our collaboration.
Accessible Resources: Our dedicated developers are available 24/7 for seamless communication and collaboration.
Time-Zone Flexibility: Adaptability to your time zone ensures efficient project management and communication.
Proven Track Record: Trust our developers’ expertise, backed by a proven track record of delivering innovative solutions.
Competitive Pricing: Enjoy competitive pricing without compromising on the quality of our services.
Technical Proficiency: Whether it’s a website, mobile app, or complex software solution, we have the expertise to bring your vision to life.
Unlock the Full Potential of Your Project Today!
At Qono Tech, we prioritize client satisfaction above all else. With regular code deliveries, transparent reporting, and proactive problem-solving, we ensure a seamless development journey from start to finish. Experience the difference with our dedicated Full Stack developers and embark on the path to success today!
Ready to take the next step? Contact Qono Tech to hire dedicated Full Stack developers and turn your vision into reality!
0 notes
Text
what vpn location should i use
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what vpn location should i use
Geographical Privacy
Geographical privacy refers to the protection of an individual's location information from unauthorized access or use. In an era dominated by digital connectivity and location-tracking technologies, safeguarding geographical privacy has become increasingly crucial. From smartphones to GPS-enabled devices, our movements are often recorded and stored by various entities, raising concerns about potential misuse and intrusion into personal space.
One of the primary concerns surrounding geographical privacy is the risk of location-based tracking and surveillance. Companies can track users' movements through mobile apps, collecting data on their daily routines, frequented places, and even real-time locations. While such data may be used for targeted advertising or service customization, it also poses risks to individual privacy if not adequately protected.
Moreover, geographical privacy intersects with other sensitive issues, such as personal safety and security. Location data in the wrong hands can enable stalking, harassment, or even physical harm to individuals. For instance, sharing one's precise location on social media platforms may inadvertently disclose information to potential threats.
Legislation and regulations play a crucial role in addressing the challenges of geographical privacy. Data protection laws, such as the General Data Protection Regulation (GDPR) in Europe, impose restrictions on the collection, processing, and sharing of personal data, including location information. However, enforcement and compliance remain ongoing challenges in the digital landscape.
Individuals can also take proactive steps to enhance their geographical privacy. This includes adjusting privacy settings on devices and apps, limiting location sharing to trusted sources, and using virtual private networks (VPNs) to encrypt internet traffic and mask IP addresses.
In essence, maintaining geographical privacy is essential for preserving individual autonomy, security, and personal freedom in an increasingly interconnected world. By raising awareness, implementing robust safeguards, and advocating for stronger privacy protections, we can strive towards a more secure and respectful digital environment.
Server Proximity
Server proximity refers to the physical distance between a user's device and the server hosting a website or online service. It plays a crucial role in determining the speed and performance of a website or application. The closer a user is to the server, the faster the data can travel, resulting in quicker loading times and smoother user experiences.
One of the primary factors influenced by server proximity is latency, which refers to the time it takes for data to travel from the user's device to the server and back again. When servers are located far away from users, latency increases, causing delays in data transmission. This delay can be especially noticeable for websites or applications that require real-time interaction, such as online gaming or video conferencing.
Additionally, server proximity can impact search engine optimization (SEO) efforts. Search engines like Google consider website speed as a ranking factor, and faster-loading websites tend to rank higher in search results. By hosting a website on servers that are geographically closer to its target audience, website owners can improve loading times and potentially boost their search rankings.
Furthermore, server proximity is essential for content delivery networks (CDNs), which distribute website content across multiple servers worldwide to improve performance and reliability. CDNs work by serving content from the nearest server to the user, reducing latency and ensuring faster load times.
In conclusion, server proximity is a critical aspect of web performance optimization. By strategically selecting server locations and leveraging CDNs, website owners can enhance user experiences, improve SEO rankings, and ultimately drive more traffic to their sites.
Content Access
Title: Navigating the Landscape of Content Access: Understanding the Dynamics and Strategies
In the digital era, accessing content has become an integral part of everyday life. Whether it's articles, videos, music, or any other form of media, the way we consume content has evolved significantly. However, the landscape of content access is not without its challenges and complexities.
One of the key dynamics in content access is the balance between availability and control. On one hand, content creators and distributors strive to make their content readily available to users across various platforms and devices. This accessibility enhances user experience and expands audience reach. On the other hand, they also seek to maintain control over their content to protect intellectual property rights and monetize their creations effectively.
To navigate this dynamic landscape, content creators and distributors employ various strategies. Content distribution agreements, licensing deals, and digital rights management (DRM) technologies are commonly used to regulate access to content while maximizing its reach and profitability. These strategies often involve partnerships with digital platforms, streaming services, and content aggregators to ensure widespread distribution while safeguarding against unauthorized use and piracy.
Moreover, technological advancements play a crucial role in shaping the landscape of content access. Innovations such as streaming media, cloud storage, and mobile apps have revolutionized how content is delivered and consumed, offering users greater flexibility and convenience. However, they also present challenges such as ensuring compatibility across different devices and addressing concerns related to privacy and security.
In conclusion, content access is a multifaceted aspect of the digital ecosystem that requires careful consideration and strategic planning. By understanding the dynamics and implementing effective strategies, content creators and distributors can optimize the accessibility of their content while safeguarding their rights and interests in an ever-changing landscape.
Security Concerns
Security concerns are a critical issue that affects individuals, businesses, and society as a whole in the digital age. With the advancement of technology, there is an increasing need for heightened security measures to protect sensitive information from cyber threats.
One major security concern is data breaches, where hackers gain unauthorized access to personal or confidential information. This can lead to identity theft, financial loss, or reputational damage. Businesses are also at risk of data breaches, which can result in loss of customer trust, legal consequences, and financial repercussions.
Another significant security concern is malware, malicious software designed to disrupt, damage, or gain unauthorized access to computer systems. Malware can infect devices through phishing emails, malicious websites, or unsecured networks, putting sensitive data at risk and compromising system integrity.
Additionally, social engineering tactics such as phishing scams and pretexting pose a threat to security. Cybercriminals use deceptive techniques to manipulate individuals into divulging confidential information or performing actions that compromise security.
To mitigate security concerns, individuals and organizations must implement robust cybersecurity measures. This includes using strong, unique passwords, keeping software up to date, using encryption technologies, and educating users about potential threats.
By staying vigilant and proactive in addressing security concerns, individuals and businesses can better protect themselves from cyber threats and safeguard sensitive information in an increasingly interconnected digital world.
Regulatory Compliance
Regulatory compliance is a critical aspect of operating within any industry, encompassing the adherence to laws, regulations, guidelines, and specifications relevant to the business's operations. It ensures that organizations conduct their activities ethically, legally, and responsibly, mitigating risks and promoting transparency.
In today's complex business environment, regulatory compliance spans various areas such as finance, healthcare, data privacy, environmental protection, and consumer rights. For businesses, non-compliance can result in severe consequences including fines, legal actions, damage to reputation, and even business closure.
To achieve regulatory compliance, organizations must stay abreast of the evolving regulatory landscape, understanding and implementing the requirements applicable to their operations. This involves establishing robust compliance frameworks, policies, and procedures tailored to the specific regulatory requirements relevant to the industry and geographic locations in which they operate.
Moreover, maintaining compliance necessitates ongoing monitoring, evaluation, and adaptation to changes in regulations and industry standards. This may involve investing in compliance management software, hiring compliance professionals, and conducting regular audits to ensure adherence to established protocols.
While achieving regulatory compliance can be challenging and resource-intensive, it also offers significant benefits. Compliance instills trust among stakeholders including customers, investors, and regulatory bodies, enhancing the organization's reputation and credibility in the marketplace. It also fosters a culture of integrity, accountability, and ethical conduct within the organization, driving sustainable business practices and long-term success.
In conclusion, regulatory compliance is not merely a legal obligation but a strategic imperative for businesses seeking to thrive in today's highly regulated environment. By embracing compliance as a core principle, organizations can mitigate risks, build trust, and position themselves for growth and resilience in an increasingly complex global landscape.
0 notes
Text
IPTV Hosting: Revolutionizing Television Broadcasting
Internet Protocol Television (IPTV) hosting is transforming the way we consume television content. Unlike traditional broadcasting methods such as cable or satellite, IPTV delivers television programming through internet protocols, allowing for a more flexible, scalable, and interactive viewing experience. Here's a comprehensive overview of IPTV hosting , its benefits, key components, and its impact on the entertainment industry.

What is IPTV Hosting?
IPTV hosting involves the delivery of television content over Internet Protocol (IP) networks. This method bypasses traditional terrestrial, satellite, and cable television formats. Instead, it uses the internet to stream live TV channels, on-demand videos, and other multimedia content directly to viewers' devices.
Key Components of IPTV Hosting
Content Acquisition:
Source Content: IPTV services source content from various providers, including TV channels, video-on-demand services, and live events.
Content Encoding: The acquired content is encoded into digital formats suitable for streaming over IP networks.
Content Management System (CMS):
Storage: A robust CMS stores the encoded content, managing a vast library of media files.
Metadata Management: Organizes content by metadata, making it easily searchable and accessible.
Streaming Server:
Live Streaming: Streams live television channels and events in real-time.
On-Demand Streaming: Delivers pre-recorded content whenever viewers request it.
Adaptive Bitrate Streaming: Adjusts the video quality based on the viewer’s internet speed to ensure a smooth viewing experience.
Middleware:
User Interface: Provides an interactive user interface for navigating and accessing content.
Authentication and Billing: Manages user authentication, subscription plans, and billing processes.
Content Delivery Network (CDN):
Global Reach: Distributes content through a network of servers located worldwide, ensuring fast and reliable delivery.
Scalability: Handles large volumes of concurrent users by balancing the load across multiple servers.
End-User Devices:
Compatibility: IPTV can be accessed on various devices, including smart TVs, smartphones, tablets, and computers.
Apps and Software: Dedicated applications or software are often provided to enhance user experience and device compatibility.
Benefits of IPTV Hosting
Flexibility and Convenience:
Viewers can watch their favorite shows and movies anytime, anywhere, on any compatible device. This flexibility is a significant advantage over traditional TV broadcasting.
Cost-Effectiveness:
IPTV services can be more cost-effective for both providers and consumers. Providers save on infrastructure costs, while consumers often enjoy more competitive pricing compared to cable or satellite services.
High-Quality Viewing Experience:
With adaptive bitrate streaming and support for high-definition (HD) and ultra-high-definition (UHD) content, IPTV delivers a superior viewing experience.
Interactive Features:
IPTV offers interactive features such as video on demand (VOD), catch-up TV, and the ability to pause, rewind, and fast-forward live TV. These features enhance viewer engagement and satisfaction.
Scalability and Reach:
Using CDNs, IPTV providers can scale their services to accommodate a growing number of users and deliver content efficiently across different regions.
Personalized Content:
IPTV services can offer personalized content recommendations based on viewing history and preferences, improving user engagement and retention.
Impact on the Entertainment Industry
Content Accessibility:
IPTV has democratized content access, allowing smaller content creators and independent producers to reach a global audience without the need for traditional distribution channels.
Innovative Business Models:
IPTV has enabled new business models, such as subscription-based services, pay-per-view, and ad-supported streaming, giving consumers more choices and flexibility.
Data-Driven Insights:
IPTV platforms can gather valuable data on viewer behavior, enabling content providers to make informed decisions about programming, advertising, and marketing strategies.
Enhanced User Experience:
The interactive and on-demand nature of IPTV services significantly enhances the user experience, setting new standards for consumer expectations in the television industry.
Conclusion
IPTV hosting is revolutionizing the way television content is delivered and consumed. By leveraging the power of the internet, IPTV offers unparalleled flexibility, quality, and interactivity, providing viewers with a superior entertainment experience. As the demand for on-demand and streaming services continues to grow, IPTV is poised to become the dominant method of television broadcasting, shaping the future of the entertainment industry.
For more info. Visit us:
Anonymous Server Hosting
Best Anonymous HostingDedicated Server Offshore
0 notes
Text
what are the disadvantages of a vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what are the disadvantages of a vpn
Bandwidth Limitations
Bandwidth limitations refer to the maximum rate of data transfer across a network or internet connection within a specified period. This restriction plays a crucial role in determining the speed and reliability of online activities, such as browsing the web, streaming videos, or downloading files.
Internet service providers (ISPs) often impose bandwidth limitations to manage network traffic efficiently and ensure fair usage among their subscribers. These limitations are typically outlined in the terms of service agreements and may vary depending on the type of internet plan a user has subscribed to.
Bandwidth limitations can impact users in several ways. For instance, during peak hours when many users are online simultaneously, bandwidth may become congested, leading to slower internet speeds and buffering while streaming content. Additionally, exceeding the allocated bandwidth limit can result in extra charges or throttling of internet speeds by the ISP.
Businesses also need to consider bandwidth limitations, especially those relying on cloud-based services or hosting websites. Insufficient bandwidth can hinder productivity and customer experience, leading to potential revenue loss.
To mitigate the impact of bandwidth limitations, users and businesses can employ various strategies. These include monitoring data usage, upgrading to higher-tier internet plans with greater bandwidth allowances, implementing content delivery networks (CDNs) to optimize data delivery, and utilizing bandwidth management tools to prioritize critical traffic.
Overall, understanding and effectively managing bandwidth limitations are essential for ensuring a smooth and reliable online experience for both individuals and businesses in today's interconnected world.
Logging Policies
Logging policies are essential components of any online service or platform, yet they often remain overlooked by users until privacy concerns arise. Understanding logging policies is crucial for safeguarding personal information and maintaining digital privacy.
Logging policies dictate how an online service collects, stores, and utilizes user data. These policies vary among different platforms and can significantly impact user privacy. Essentially, logging policies outline what information is recorded, how long it is retained, and who has access to it.
One of the key aspects of logging policies is the type of data that is logged. This may include user activity, IP addresses, device information, and browsing history. Platforms may also track interactions with their services, such as login attempts, clicks, and searches.
The retention period of logged data is another critical factor. Some platforms retain data for a limited time, while others may store it indefinitely. Users should be aware of how long their data is kept and whether they have the option to delete it.
Furthermore, logging policies define who has access to the logged data. This could include employees of the platform, third-party service providers, or even government agencies in certain jurisdictions. Users should understand who can potentially access their information and under what circumstances.
Transparency is key when it comes to logging policies. Platforms should clearly communicate their policies to users, preferably in a concise and easily understandable manner. This allows users to make informed decisions about their online activities and take necessary precautions to protect their privacy.
In conclusion, logging policies play a crucial role in safeguarding user privacy in the digital age. By understanding and scrutinizing these policies, users can better protect their personal information and maintain control over their online data.
Compatibility Issues
Title: Navigating Compatibility Issues: A Guide for Smooth Interactions
Compatibility issues can arise in various aspects of life, from technology to relationships, posing challenges that require careful navigation. In the realm of technology, compatibility problems often occur when different systems or software versions are unable to work together seamlessly. This can lead to frustrating experiences for users, hindering productivity and efficiency.
One common example of compatibility issues in technology is encountered when trying to connect devices from different manufacturers. For instance, a smartphone may struggle to sync with a smartwatch produced by another brand, resulting in limited functionality or complete failure to pair. Similarly, software applications may face compatibility hurdles when attempting to run on certain operating systems or hardware configurations.
In the realm of relationships, compatibility concerns can manifest in various forms, such as differing values, communication styles, or life goals. While some differences can enrich relationships through complementary strengths, others may lead to conflict and discord if not addressed effectively. Couples often grapple with compatibility issues as they navigate differences in personality, interests, or expectations.
To mitigate compatibility issues, proactive measures can be taken. In the technology sphere, developers can prioritize interoperability by adhering to industry standards and conducting thorough compatibility testing across platforms. Users can also research compatibility requirements before making purchasing decisions, ensuring that devices and software are compatible with their existing setup.
In interpersonal relationships, open and honest communication is key to addressing compatibility concerns. Couples can engage in meaningful discussions to understand each other's perspectives, identify areas of divergence, and find mutually acceptable solutions. Additionally, embracing flexibility and compromise can foster harmony and strengthen the bond between partners.
While compatibility issues may present challenges, they also provide opportunities for growth and learning. By acknowledging differences and actively seeking resolution, individuals and organizations can navigate compatibility issues with resilience and grace, fostering greater harmony and collaboration in all aspects of life.
Slower Internet Speed
Title: Understanding the Causes and Solutions for Slower Internet Speed
In today's interconnected world, a slowdown in internet speed can be frustrating and disruptive. From buffering videos to sluggish downloads, slower internet speed can hinder productivity and enjoyment. Understanding the reasons behind this slowdown is crucial for troubleshooting and improving the situation.
One common cause of slower internet speed is network congestion. When many users in the same area are online simultaneously, it can strain the available bandwidth and lead to decreased speeds for everyone. This often occurs during peak usage hours, such as evenings and weekends, when more people are streaming videos or engaging in online activities.
Another factor contributing to slower internet speed is outdated or faulty equipment. Modems, routers, and cables degrade over time and may need to be replaced to maintain optimal performance. Additionally, interference from nearby electronic devices or physical obstructions like walls can disrupt Wi-Fi signals and reduce internet speed.
Internet Service Providers (ISPs) may also throttle internet speeds for certain activities, such as streaming or torrenting, to manage network traffic or enforce data caps. While this practice is controversial, it's important for users to be aware of their ISP's policies and consider upgrading to a higher-speed plan if necessary.
Fortunately, there are several steps individuals can take to improve their internet speed. Restarting routers and modems, relocating them to a more central location, and using wired connections instead of Wi-Fi can all help alleviate slowdowns. Additionally, updating firmware, optimizing browser settings, and clearing cache and cookies can enhance browsing speed and performance.
In conclusion, slower internet speed can stem from various factors including network congestion, equipment issues, and ISP policies. By identifying the root cause and implementing appropriate solutions, users can mitigate slowdowns and enjoy a smoother online experience.
Legal Concerns
Legal concerns can arise in various aspects of our lives, prompting the need to understand and address them appropriately. From issues related to contracts and agreements to disputes over property or personal injury claims, legal concerns can be complex and daunting to navigate. It is essential to seek legal guidance and support to protect your rights and interests in such situations.
One common legal concern that individuals often face is related to contracts. Whether it's a business agreement, a rental contract, or an employment offer, understanding the terms and implications of a contract is crucial. Failure to comply with the terms of a contract could result in legal repercussions, making it essential to seek legal advice before signing any document.
Another significant legal concern is related to disputes over property. Whether it's a boundary dispute with a neighbor, an inheritance issue within the family, or a landlord-tenant conflict, property disputes can be emotionally and financially draining. Seeking legal assistance to clarify property rights and resolve disputes through negotiation or litigation can help protect your interests and assets.
Legal concerns may also arise in the context of personal injury claims. Whether it's a car accident, medical malpractice, or a slip and fall incident, seeking compensation for injuries requires a thorough understanding of personal injury laws and procedures. Consulting with a legal expert specializing in personal injury claims can help you navigate the legal process and pursue the compensation you deserve.
In conclusion, legal concerns are a part of life that can impact us at any time. By seeking timely legal advice and assistance, you can protect your rights, resolve disputes, and navigate complex legal matters effectively. It is essential to address legal concerns proactively to safeguard your interests and ensure a favorable outcome.
0 notes
Text
Come implementare Privacy Shield per non bloccare domini leciti

Perché il Piracy Shield non funziona e come sarebbe dovuto essere implementato. Nell’era digitale, la gestione della proprietà intellettuale e la lotta contro la pirateria online rappresentano sfide cruciali per i regolatori, le industrie creative e i fornitori di servizi internet. Il “Piracy Shield”, un’iniziativa dell’Autorità per le Garanzie nelle Comunicazioni (AGCOM), rappresenta un tentativo significativo di affrontare il problema della pirateria digitale in Italia.
Questo strumento è stato ideato per identificare e bloccare l’accesso ai siti web che violano i diritti di proprietà intellettuale, sfruttando tecnologie di filtraggio degli “FQDN e degli indirizzi IP” (citando testualmente AGCOM).
Nonostante le sue nobili intenzioni, il Piracy Shield ha suscitato non poche controversie e dibattiti riguardo la sua efficacia e le implicazioni per la libertà di espressione e il diritto alla privacy. In questo articolo tecnico-scientifico, si intende esplorare e discutere le ragioni per cui il Privacy Shield non ha raggiunto pienamente i suoi obiettivi, mettendo in luce le difficoltà tecniche, legali e etiche incontrate.

Sarà inoltre illustrato come, attraverso un approccio innovativo basato sulla configurazione di record CNAME, sia possibile distinguere tra servizi legittimi e illeciti associati allo stesso indirizzo IPv4. Questa dimostrazione pratica non solo evidenzierà le potenzialità di tali tecniche, ma anche come esse potrebbero essere integrate efficacemente in un framework rinnovato per la lotta alla pirateria, suggerendo modifiche e migliorie al sistema attuale del Piracy Shield.
Le Content Delivery Network
Le Content Delivery Networks (CDN) sono infrastrutture distribuite di server progettate per ottimizzare la consegna di contenuti web agli utenti finali. Le CDN migliorano la velocità e l’affidabilità di accesso ai dati riducendo la distanza fisica tra il server e l’utente, distribuendo il contenuto su diversi server posizionati in varie località geografiche.
Funzionamento delle CDN
Quando un utente accede a un sito web che utilizza una CDN, la richiesta di dati non viene inviata direttamente al server principale del sito, ma viene reindirizzata al server della CDN più vicino all’utente. Questo server “edge” contiene copie dei contenuti del sito, come file HTML, immagini, video e altri tipi di dati. Grazie a questa architettura, il tempo di caricamento delle pagine si riduce notevolmente, migliorando l’esperienza dell’utente e riducendo il carico sui server centrali.
Mascheramento dell’IP reale
Un effetto importante dell’uso delle CDN è il mascheramento dell’indirizzo IP pubblico reale del server di origine dei contenuti. Quando un servizio online adotta una CDN, gli indirizzi IP visibili al pubblico sono quelli dei server della rete CDN. Questo significa che l’IP percepito come fonte del servizio è in realtà quello della CDN, non del server originale. Questo ha implicazioni per la sicurezza, la privacy e la gestione del traffico, ma può anche complicare alcune operazioni di controllo e filtraggio del contenuto.
Implicazioni per il filtraggio di contenuti
Se un’autorità come AGCOM implementa misure per bloccare l’accesso a contenuti ritenuti illegali (come quelli piratati) mediante il filtraggio degli indirizzi IP attraverso strumenti come il Piracy Shield, si potrebbero verificare problemi significativi. Poiché un singolo indirizzo IP di una CDN può essere utilizzato per trasmettere i contenuti di numerosi servizi diversi, il blocco di quell’IP potrebbe avere l’effetto collaterale di interrompere l’accesso a servizi legittimi e non solo a quelli illegali. Questo scenario potrebbe portare a interruzioni di servizio per utenti che non sono coinvolti nella fruizione di contenuti piratati.
Facciamo chiarezza con un esempio pratico
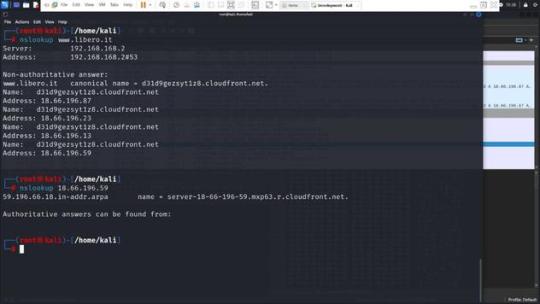
Per comprendere meglio come funziona la navigazione su internet e l’interazione con una Content Delivery Network (CDN), prendiamo come esempio il processo di collegamento a un sito web, come “www.libero.it”. Questo esempio ci permetterà di osservare come, durante la navigazione, il nome di dominio inizialmente richiesto possa in realtà essere servito da un dominio completamente diverso, come “d31d9gezsyt1z8.cloudfront.net”, che appartiene a una CDN.
DNS Query
Il processo inizia quando l’utente digita “www.libero.it” nel browser. Il browser deve risolvere questo nome di dominio in un indirizzo IP per poter stabilire una connessione. Questo avviene tramite una richiesta DNS (Domain Name System).
Il browser consulta i server DNS configurati (tipicamente forniti dal provider di servizi internet o specificati manualmente dall’utente) per ottenere l’indirizzo IP associato al nome di dominio. (Si vede evidenziata la richiesta)
Ricezione della risposta DNS
I server DNS eseguono la ricerca e, una volta trovato l’indirizzo IP, lo restituiscono al browser. Se il dominio è ospitato su una CDN, l’IP restituito sarà quello di uno dei server edge della CDN più vicino all’utente, non l’IP del server originale di “libero.it”. (Si vede evidenziata la risposta
Apertura della connessione (Handshake)
Con l’indirizzo IP in mano, il browser inizia un handshake TCP con il server al fine di stabilire una connessione affidabile. Questo include la sincronizzazione dei numeri di sequenza per garantire che i pacchetti di dati vengano inviati e ricevuti in ordine. Durante l’handhsake il client invia un segmento SYN , il server risponde con un SYN + ACK , il client termina l’handshake con un ACK. (Si vede in figura nella riga evidenziata l’inizio dell’handshake verso la CDN di libero).
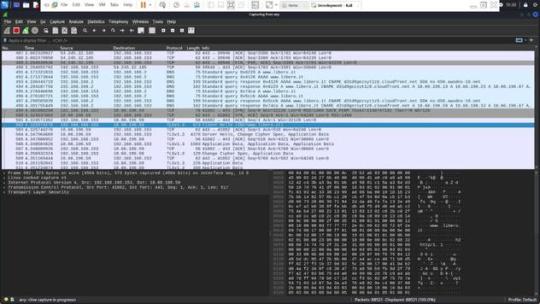
Negoziazione TLS (Transport Layer Security)
Dopo aver stabilito una connessione TCP, il browser inizia una negoziazione TLS per assicurare che la comunicazione sia sicura e criptata. Questo processo inizia con l’invio del “ClientHello”, che include la versione di TLS supportata, i metodi di cifratura proposti, e altri dettagli necessari per la sicurezza.

Il server risponde con un “ServerHello”, che conferma i dettagli della crittografia che sarà utilizzata, seleziona un metodo di cifratura tra quelli proposti dal client e prosegue con l’invio dei certificati, la verifica della chiave, e la conferma finale di inizio della cifratu
Comunicazione sicura
Una volta completata la negoziazione TLS, tutte le trasmissioni successive tra il browser e il server sono completamente criptate. Il browser può ora richiedere le risorse web da “www.libero.it”, che in realtà potrebbero essere servite dal dominio della CDN, come “d31d9gezsyt1z8.cloudfront.net”.
Questo esempio mostra come, nella pratica, un sito che l’utente intende visitare possa essere effettivamente distribuito attraverso una rete CDN, rendendo il nome del dominio CDN visibile nelle comunicazioni di rete, anche se l’utente potrebbe non essere immediatamente consapevole di tale fatto.
Considerazioni
Questa architettura farà in modo che www.libero.it avrà una serie di IP associati all’ASN di cloudfront che vengono usati per far funzionare la CDN. Questi IP saranno associati non solo a www.libero.it ma anche a molti altri FQDN (Altre web app) che usano la CDN. Ricordiamo che questi servizi vengono distinti fra loro grazie ai record CNAME che puntano a FQDN univoci come questo: d31d9gezsyt1z8.cloudfront.net.
Dimostrazione del problema
Con l’esempio precedente abbiamo quindi dimostrato che quando un servizio è integrato ad una CDN la corrispondenza servizio – IP non è più della cardinalità 1:1 , ma bensì N:1. Quindi se viene filtrato un indirizzo IP, N servizi vengono oscurati, pur non essendo tutti illegali. Lo abbiamo visto con l’esempio precedente in cui libero viene deliberatamente associato a diversi IP, condivisi con altri servizi della CDN cloudFront.
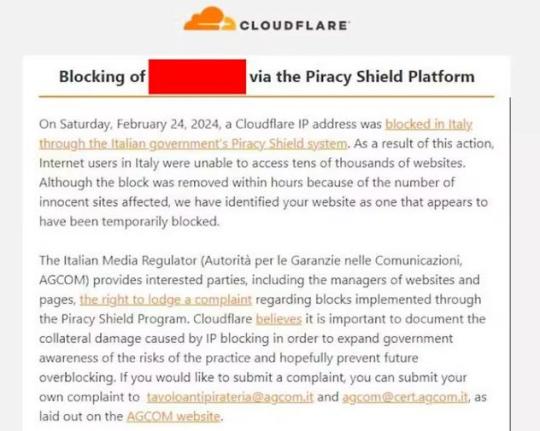
Infatti una delle CDN che ha lamentato proprio questo problema è la nota Cloudflare che ha emesso un comunicato ad alcuni suoi clienti, esortandoli all’invio di una lettera di richiamo alla stessa AGCOM chiedendo di annullare l’ingiusto provvedimento.
Non si può quindi pensare di bloccare il traffico IP semplicemente filtrando un indirizzo IPv4/IPv6.
Come si potrebbe procedere
Per affrontare efficacemente le sfide poste dal filtraggio di contenuti attraverso indirizzi IP in un ambiente dove sono ampiamente utilizzate le Content Delivery Networks (CDN), è essenziale adottare metodi più sofisticati che prendano in considerazione le peculiarità tecniche delle CDN stesse. Una strategia più mirata e meno suscettibile di causare danni collaterali può essere implementata analizzando in dettaglio le proprietà di rete associate agli indirizzi IP, in particolare l’Autonomous System Number (ASN).
Analisi dell’ASN
Prima di procedere al blocco di un indirizzo IP sospettato di veicolare contenuti piratati, è cruciale determinare a quale sistema autonomo appartiene quel determinato IP. Se l’IP è associato all’ASN di una CDN nota, questo indica che potrebbe essere utilizzato per servire una moltitudine di clienti e servizi, molti dei quali legittimi. Il blocco diretto di tali IP potrebbe quindi interrompere l’accesso a servizi legittimi, causando interruzioni non necessarie e potenzialmente estese.
Blocco basato su FQDN della CDN
Invece di bloccare indiscriminatamente gli indirizzi IP, si dovrebbe valutare l’opzione di filtrare specifici Fully Qualified Domain Names (FQDN) direttamente legati a contenuti illeciti. Un metodo più mirato consiste nell’analizzare i record CNAME, che collegano un FQDN a un altro dominio, spesso usato per identificare contenuti specifici all’interno di una CDN.
Il sistema attuale del Piracy Shield già applica il blocco agli FQDN e agli indirizzi IP, ma non estende questo trattamento ai FQDN univoci usati dalle CDN. Ad esempio, bloccando il dominio pubblico www.libero.it ed i suoi indirizzi IP, si impedisce anche l’accesso agli IP come 18.66.196.87, 18.66.196.23, 18.66.196.13 e 18.66.196.59. Tali indirizzi, associati a una CDN, vengono utilizzati anche da altri servizi che sarebbero ingiustamente bloccati.
Soluzione proposta
Quando viene rilevato che un servizio usa una CDN, la strategia corretta sarebbe quella di bloccare esclusivamente gli FQDN specifici alla CDN, come d31d9gezsyt1z8.cloudfront.net e www.libero.it, senza intervenire sugli indirizzi IP.
In questo modo gli altri servizi che usano la CDN non saranno bloccati.
Conclusioni
Adottando queste pratiche migliorate, AGCOM e altre autorità simili potrebbero ottimizzare le loro strategie di enforcement senza suscitare controversie legate a interruzioni di servizio ingiustificate o a violazioni dei diritti alla privacy e alla libertà di espressione. Questo equilibrio tra l’efficacia del blocco e il rispetto per i diritti degli utenti è essenziale per mantenere la fiducia nel regolamento digitale e nella protezione della proprietà intellettuale nel contesto globale e interconnesso di oggi
Read the full article
#AgCom#CDNcloudFront#contentdeliverynetwork#dnsquery#filtering#FQDN#indirizziIP#ipaddress#PrivacyShield
0 notes