#Blackhat hacking
Text
What is Mariana’s Web wikipedia is the name given to the deepest part of the internet, and the name is inspired by Mariana’s Trench. It is the deepest trench in the world Read More

#hacking#hacker#marianas trench#dark web#deep web#internet#cybersecurity#kalilinux#hackers#ethicalhacking#linux#dark#hack#ethicalhacker#blackhat#infosec#hackingtools#memes#technology#teejayx#security#coding#korkun#programming#horror#bilgiler#malware#darknet#python#viral
5 notes
·
View notes
Text
youtube
In This Video , i will show you guys how we will Embed a Reverse-Shell/Malware As a clickable Button into a Email-HTML Message , for the victim to download and execute to than infect them . Also in the next 2 clips i will show you guys how we can gather IP,Device,Browser,Timezone Information Of a Victim or Inject a Malicious Javascript Code by the beef-xss Framework Hook. These Attacks can be very dangerous as people that arent good with Computers , can fall for these kind of Attacks by Social-Engineering, even Many Big Companies that are trained could have Weakness To These Type Of Attacks!.Especially with Email-Spoofing, sending a Email as if it was From a Trusted Person , but actually the Malicious Actor sends it.
Ngrok Download:https://ngrok.com/download
Serveo Usage:https://serveo.net/
00:0 Introduction
1:25 Malware File Embedding
1:41 Creating Malware/Setting Up Listener With msfvenom/netcat/ngrok
4:25 Coding Malicious HTML/Javascript Page
9:14 Embedding The Link For HTML Email-Messages
12:52 Malicious-Email For Grabbing IP,Device,Browser,Timezone Information From The Victim
16:24 Sending Malicious-Email with beef-xss Hook Injected Inside The Web-Page
-If You Guys Liked The Video , Please Subscribe To My Youtube-Channel For More:
https://www.youtube.com/@xenjin450
Social Medias:
Instagram:https://www.instagram.com/xenjin450
Twitter:https://www.twitter.com/xenjin450
Tik-Tok:https://www.tiktok.com/@senjin450
Facebook:https://web.facebook.com/profile.php?…
Github-Page:
https://github.com/xenjin450
#tumblr#Youtube#hacking#hacker#cybersecurity#blackhat#security#pentesting#technology#knowledge#kalilinux#linux#ethicalhacking#tools#learning#studying#awareness#cyberawareness#2023#javascript#computer#malware#virus#msfvenom#terminal#html#coding#programming#windows#email
0 notes
Photo

Llego mi nuevo bebé… mi Alfa AWUS036AC… en mi revisión ya murieron dos de mis tarjetas con las que inicie el análisis de redes WiFi… ahora a probar qué tal trabaja este juguetito… 😷 🦠 👨🏻💻🏠👩🏻💻🦠 😷 _/﹋\_ (҂`_´) -''Let's Hacking'' <,︻╦╤─ ҉ - - - - _/\_ . . . #pentester #vulnerabilityassessment #HackingTools #Pentest #Pentesting #VulnerabilityAssessment #EthicalHacking #InfoSec #CyberSecurity #EthicalHacker #ceh #diabetichacker #darkdevil #hacker #hacking #whitehat #greyhat #blackhat #owasp #osstmm #issaf #ptes https://www.instagram.com/p/CoJQtgYjIU_/?igshid=NGJjMDIxMWI=
#pentester#vulnerabilityassessment#hackingtools#pentest#pentesting#ethicalhacking#infosec#cybersecurity#ethicalhacker#ceh#diabetichacker#darkdevil#hacker#hacking#whitehat#greyhat#blackhat#owasp#osstmm#issaf#ptes
0 notes
Text
All About Black Hat Hacking...
Black Hat hacking refers to the use of hacking techniques for malicious purposes, such as unauthorized access to systems, stealing sensitive information, or spreading malware. It is illegal and unethical and can result in serious consequences, such as fines, imprisonment, and harm to an individual's or a company's reputation. Black Hat hackers often operate with the intention of financial gain or to cause disruption. In contrast, White Hat hacking is ethical hacking done for security purposes, such as identifying vulnerabilities to improve the security of a system.
Black Hat techniques include:
Social engineering - tricking people into revealing sensitive information
Exploits - taking advantage of vulnerabilities in software or hardware
Malware - software designed to cause harm to systems or steal information
Distributed Denial of Service (DDoS) attacks - overwhelming a website or network with traffic
Phishing - tricking people into revealing sensitive information via fake emails or websites
Black Hat hacking activities can result in significant financial losses, data breaches, and reputation damage. Companies and governments employ cyber security professionals and implement security measures to prevent and detect Black Hat hacking. It is important to practice good cyber hygiene and be cautious of suspicious emails, links, and downloads to avoid falling victim to Black Hat hackers.
Additionally, Black Hat hacking can also have wider societal impacts, such as:
Election interference - hacking into voting systems or spreading false information to influence election outcomes
Infrastructure attacks - targeting critical infrastructure systems, such as power grids or transportation systems, to cause disruption and chaos
Cyber espionage - stealing sensitive information from governments or corporations for political or economic gain
To combat Black Hat hacking, organizations and individuals should adopt proactive security measures such as regularly applying software updates, using strong passwords, and implementing multi-factor authentication. They can also educate their employees about good cyber hygiene practices and stay informed about the latest threats and trends in the world of cyber security. Additionally, international cooperation and collaboration between governments, law enforcement agencies, and the private sector is essential to mitigate the effects of Black Hat hacking.
It's also important to note that the tactics and techniques used by Black Hat hackers are constantly evolving and adapting to new technologies and advancements. This highlights the need for ongoing efforts to improve cybersecurity measures and stay ahead of potential threats.
Moreover, many Black Hat hackers are highly skilled and often work in organized groups. They use sophisticated tools and methods to evade detection and cover their tracks, making it difficult for law enforcement agencies to identify and apprehend them.
To protect against Black Hat hacking, organizations and individuals can utilize various security tools and technologies, such as firewalls, intrusion detection and prevention systems, and antivirus software. They can also engage in regular security audits, penetration testing, and threat hunting to proactively identify and mitigate potential vulnerabilities.
In conclusion, Black Hat hacking is a serious issue that can cause significant harm to individuals, organizations, and society as a whole. It's crucial for everyone to be aware of the dangers and take proactive steps to protect themselves and their systems from these malicious attacks.
Another aspect to consider is the motivation behind Black Hat hacking. Some hackers may be driven by financial gain, while others may be motivated by political or ideological beliefs. For example, hacktivist groups may engage in Black Hat hacking to draw attention to a particular cause or to protest against a government or corporation.
Furthermore, there is a growing trend of state-sponsored Black Hat hacking, where governments or state-sponsored actors engage in cyber attacks for political or military purposes. These types of attacks can have far-reaching consequences and pose a significant threat to national security and global stability.
In light of these developments, governments and organizations must not only focus on improving their technical security measures, but also enhance their ability to respond to and recover from cyber attacks. This includes implementing incident response plans, conducting regular crisis drills, and maintaining a robust backup and disaster recovery strategy.
Finally, it's important to recognize that the impact of Black Hat hacking extends beyond the immediate damage caused by the attack itself. The loss of trust and confidence in technology and online systems can have long-lasting effects on individuals, businesses, and society as a whole. This highlights the need for continued efforts to educate and raise awareness about cybersecurity, and to encourage a collective approach to securing the digital world.
In addition, there has been a growing trend of using Artificial Intelligence and machine learning in Black Hat hacking. Hackers can leverage these technologies to automate their attacks and evade detection. For example, they can use AI to generate convincing phishing emails, to find and exploit vulnerabilities in software, or to carry out large-scale DDoS attacks.
This highlights the need for organizations and individuals to stay informed about the latest developments in AI and machine learning and to understand their potential impact on cybersecurity. Moreover, it is important for the cybersecurity industry to incorporate these technologies into their own solutions in order to better detect and prevent Black Hat hacking activities.
Another trend to note is the increasing use of cryptocurrencies in Black Hat hacking. These attacks can result in the theft of large sums of money and the damage to an individual's or organization's reputation. To mitigate these risks, it is important for organizations to implement robust security measures for their cryptocurrency wallets and exchanges and to educate their employees about the potential dangers of these attacks.
In conclusion, the world of Black Hat hacking is complex and constantly evolving. It requires a multi-faceted approach that involves technical measures, awareness and education, and international collaboration to effectively combat these malicious activities.
Additionally, cloud computing has also become a new target for Black Hat hackers. With more and more data and applications being stored in the cloud, the potential impact of a successful attack can be significant. Hackers can exploit vulnerabilities in cloud infrastructure or gain access to sensitive data through misconfigured permissions or weak passwords.
To protect against these types of attacks, organizations must implement strong security controls for their cloud environment, including encryption, access controls, and monitoring for suspicious activity. They must also ensure that their employees are aware of the security risks associated with cloud computing and are trained in best practices for securing their data in the cloud.
Another important issue to consider is the potential for supply chain attacks, where a hacker targets a third-party vendor in order to gain access to a larger target organization. This highlights the need for organizations to assess and monitor the security posture of their suppliers and partners, and to include security requirements in their contracts and agreements.
Moreover, the rise of Internet of Things (IoT) devices has also created new opportunities for Black Hat hackers. Many IoT devices lack basic security features and can be easily compromised, potentially exposing sensitive information or allowing hackers to gain control of these devices and use them for malicious purposes.
In conclusion, the increasing number of connected devices and the growing use of cloud computing and other technologies have created new and complex challenges for organizations in terms of cybersecurity. It is crucial for organizations to stay informed about these developments and to take a proactive and comprehensive approach to securing their systems and data against Black Hat hacking activities.
Lastly, the aftermath of a Black Hat hacking attack can have far-reaching consequences. Beyond the immediate damage caused by the attack, organizations may face legal and financial liabilities, reputational harm, and loss of customer trust. This highlights the importance of having a comprehensive incident response plan in place, which should include procedures for containing and mitigating the impact of an attack, as well as for reporting and communicating with stakeholders.
Moreover, organizations must also be prepared to manage the aftermath of a data breach, which can involve notifying affected individuals, providing credit monitoring services, and cooperating with law enforcement. The financial and legal costs of a data breach can be substantial, and organizations must have the resources and contingency plans in place to effectively manage these risks.
In addition, it is important for organizations to consider the long-term implications of a Black Hat hacking attack. For example, they may need to invest in upgrading or replacing outdated systems and infrastructure, or to implement additional security measures to prevent future attacks.
In conclusion, the threat posed by Black Hat hacking is significant, and organizations must take a comprehensive and proactive approach to securing their systems and data. This includes implementing strong technical controls, raising awareness and educating employees, and having a robust incident response plan in place.
Furthermore, the use of ransomware has become a common tactic among Black Hat hackers. Ransomware is a type of malware that encrypts a victim's files and demands payment in exchange for the decryption key. This can result in significant disruption and financial losses for organizations.
To protect against ransomware attacks, organizations should implement regular backups of their data, and ensure that their backups are stored securely and can be easily recovered in the event of an attack. They should also implement strong anti-malware and anti-virus solutions, and educate their employees about the risks of phishing and other social engineering attacks that can deliver ransomware.
Another threat to consider is the rise of state-sponsored hacking, where a nation-state uses Black Hat tactics to advance its political or economic objectives. These types of attacks can be highly sophisticated and difficult to detect, and can result in significant damage to critical infrastructure and national security.
To mitigate the risk of state-sponsored hacking, organizations must stay informed about the latest developments in this area, and implement strong security measures such as encryption and multi-factor authentication. They must also be prepared to cooperate with law enforcement and other government agencies in the event of a breach.
In conclusion, the threat posed by Black Hat hacking is a growing concern, and organizations must take a comprehensive approach to securing their systems and data. This includes implementing strong technical controls, raising awareness and educating employees, and having a robust incident response plan in place. It also requires organizations to stay informed about the latest developments in the cybersecurity landscape and to adapt their defenses accordingly.
Additionally, the use of AI and machine learning by Black Hat hackers is a rapidly growing concern. These technologies can be used to automate the discovery and exploitation of vulnerabilities, as well as to evade detection by security systems.
To defend against these threats, organizations must stay informed about the latest developments in AI and machine learning, and invest in the development of these technologies for defensive purposes. For example, organizations can use AI and machine learning to automate the detection and remediation of vulnerabilities, or to detect and respond to threats in real-time.
Moreover, the rise of decentralized systems, such as blockchain and peer-to-peer networks, has also created new challenges for organizations in terms of cybersecurity. These systems are often designed to be highly resistant to tampering and censorship, but they can also make it difficult to detect and remediate malicious activities.
To mitigate these risks, organizations must stay informed about the latest developments in decentralized systems, and invest in the development of secure and scalable solutions. For example, they can use blockchain and peer-to-peer networks to secure their data and transactions, while also implementing strong access controls and monitoring mechanisms to detect and respond to malicious activities.
In conclusion, the cybersecurity landscape is constantly evolving, and organizations must stay informed about the latest threats and developments in order to effectively defend against Black Hat hacking activities. This requires a proactive and comprehensive approach, including investment in the development of new technologies for defensive purposes, and the implementation of strong technical controls and best practices.
It's also important for organizations to regularly assess their cyber security posture and identify areas for improvement. This includes conducting regular vulnerability assessments, penetration testing, and security audits to identify and remediate weaknesses in systems and processes. Organizations should also consider implementing security frameworks such as NIST, CIS, or ISO 27001 to ensure that their security practices are aligned with industry standards and best practices.
Another crucial aspect of defending against Black Hat hacking is incident response planning. Organizations should have a well-defined incident response plan in place that outlines procedures for responding to a breach or attack, including how to contain and mitigate the impact, how to communicate with stakeholders, and how to coordinate with law enforcement. Regular tabletop exercises can help organizations test and refine their incident response plans.
It's also important for organizations to educate their employees on the importance of cybersecurity and how they can help to protect the organization from Black Hat hacking activities. This includes providing training on topics such as phishing, password management, and identifying suspicious activity. Employees should also be made aware of the consequences of engaging in malicious activities, such as downloading malicious software or visiting unauthorized websites.
In conclusion, organizations must adopt a multi-layered approach to defend against Black Hat hacking activities. This includes implementing strong technical controls, conducting regular security assessments, having a robust incident response plan in place, and educating employees on the importance of cybersecurity. Organizations must also stay informed about the latest threats and trends in the cyber security landscape, and continuously adapt their defenses accordingly.
Another important aspect of defending against Black Hat hacking is developing a culture of cybersecurity within the organization. This includes fostering a shared understanding of the importance of cybersecurity and the role that everyone plays in protecting the organization. It also includes providing the necessary resources and support to ensure that employees have the knowledge and tools they need to defend against threats.
It's also important for organizations to work closely with their vendors and partners to ensure that they are following best practices and that their security posture is aligned with the organization's security requirements. This includes implementing security controls such as due diligence, risk assessments, and regular security audits of third-party vendors and partners.
Organizations should also consider implementing security information and event management (SIEM) solutions to monitor and respond to security events in real-time. SIEM solutions can provide centralized logging, real-time alerting, and correlation of security events from multiple sources, allowing organizations to detect and respond to threats quickly and effectively.
Finally, organizations should consider participating in threat intelligence sharing programs, such as information sharing and analysis centers (ISACs), to stay informed about the latest threats and to collaborate with other organizations to improve their defenses. Threat intelligence sharing can help organizations to identify and remediate threats more quickly and effectively, and to stay ahead of the evolving threat landscape.
In conclusion, organizations must take a holistic approach to defending against Black Hat hacking activities, including developing a culture of cybersecurity, working closely with vendors and partners, implementing security information and event management solutions, and participating in threat intelligence sharing programs. By adopting these best practices, organizations can better defend against Black Hat hacking activities and protect their systems, data, and reputation.
One additional aspect to consider is that of insurance. While insurance cannot prevent Black Hat hacking, it can help organizations to mitigate the financial losses and other impacts associated with a breach. Organizations should consider purchasing cyber insurance to help cover the costs of responding to a breach, such as hiring forensic investigators, notifying affected individuals, and providing credit monitoring services.
Organizations should also consider incorporating cybersecurity provisions into their contracts with vendors and partners. This includes requiring that vendors implement appropriate security controls, such as encryption and access controls, and requiring that they provide notification in the event of a breach. Organizations can also require that vendors maintain insurance coverage to help cover the costs of responding to a breach.
Finally, it's important for organizations to stay informed about the latest regulations and laws related to cybersecurity. This includes data protection and privacy laws, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), as well as sector-specific regulations such as the Health Insurance Portability and Accountability Act (HIPAA) for the healthcare industry. Organizations should ensure that their security practices are aligned with these regulations to avoid fines and reputational damage.
In conclusion, organizations must consider a wide range of factors to defend against Black Hat hacking activities, including insurance, contracts with vendors and partners, and staying informed about relevant regulations and laws. By adopting a comprehensive and proactive approach, organizations can better defend against Black Hat hacking and protect their systems, data, and reputation.
Another important aspect to consider is the role of international cooperation in combating Black Hat hacking activities. Cybercrime is a global problem that transcends borders, and organizations must work together to share information and best practices to better defend against these threats. This includes participating in international initiatives such as the Global Cybersecurity Alliance and the International Association of Cybersecurity Professionals.
International cooperation also involves law enforcement agencies working together to track down and prosecute individuals involved in Black Hat hacking activities. This includes the FBI's Cyber Division, Europol's European Cybercrime Centre (EC3), and Interpol's Cybercrime Programme. These agencies work together to identify and track cybercriminals, share intelligence, and coordinate efforts to bring them to justice.
Organizations can also benefit from participating in information sharing and analysis centers (ISACs) and other industry groups to stay informed about the latest threats and to collaborate with other organizations to improve their defenses. Threat intelligence sharing can help organizations to identify and remediate threats more quickly and effectively, and to stay ahead of the evolving threat landscape.
Finally, organizations must stay informed about the latest technology trends and innovations in the cybersecurity landscape. This includes staying up-to-date on the latest security products and services, as well as emerging technologies such as artificial intelligence and machine learning, which can help organizations to detect and respond to threats more effectively.
In conclusion, organizations must consider international cooperation, information sharing, and staying informed about the latest technology trends to better defend against Black Hat hacking activities. By working together and staying informed, organizations can better protect their systems, data, and reputation.
An additional factor to consider is user awareness and education. The weakest link in an organization's security chain is often its users, who may unknowingly put the organization's data and systems at risk through poor security practices or by falling victim to social engineering attacks. To mitigate these risks, organizations should invest in user awareness and education programs that teach users about the latest threats and how to avoid them.
This can include providing training on topics such as phishing, password management, and safe browsing habits, and regularly testing users to assess their understanding of security best practices. Organizations can also implement technical controls, such as multi-factor authentication and email filters, to help protect against user-targeted attacks.
Organizations should also have incident response plans in place to quickly and effectively respond to a security breach. This includes procedures for detecting, containing, and responding to a breach, as well as procedures for communicating with stakeholders, such as employees, customers, and partners. Organizations should regularly test their incident response plans to ensure that they are effective and that all stakeholders are familiar with their roles and responsibilities.
Finally, organizations must regularly assess and monitor their security posture to identify areas for improvement and to ensure that their defenses are keeping pace with the evolving threat landscape. This includes regular penetration testing, vulnerability scanning, and security audits, as well as monitoring for unusual or suspicious activity on their networks. By continuously monitoring their security posture, organizations can better defend against Black Hat hacking activities and protect their systems, data, and reputation.
In conclusion, user awareness and education, incident response planning, and continuous security monitoring are critical components of an effective defense against Black Hat hacking activities. By investing in these areas, organizations can better protect themselves and their stakeholders from these threats.
Another important factor to consider is the role of government regulations and standards in combating Black Hat hacking. In many countries, governments have enacted laws and regulations aimed at reducing cybercrime and protecting citizens' data privacy. For example, in the European Union, the General Data Protection Regulation (GDPR) sets strict requirements for how organizations must handle personal data and sets heavy fines for non-compliance. In the United States, organizations are subject to various laws and regulations, such as the Health Insurance Portability and Accountability Act (HIPAA) for the healthcare industry, and the Payment Card Industry Data Security Standard (PCI DSS) for organizations that accept credit card payments.
Adhering to these regulations and standards can help organizations to better protect themselves and their customers from Black Hat hacking activities. For example, by following the requirements of the GDPR, organizations can ensure that they are handling personal data in a secure and privacy-sensitive manner, reducing the risk of data breaches and unauthorized access to sensitive information.
Additionally, organizations can benefit from certifying their security practices against industry-recognized standards, such as ISO 27001 for information security management and the SOC 2 standard for service providers. These certifications demonstrate an organization's commitment to security and provide assurance to customers and stakeholders that their data is being handled in a secure and responsible manner.
In conclusion, government regulations and standards play an important role in protecting against Black Hat hacking activities by setting minimum security requirements and promoting best practices. By adhering to these regulations and certifying their security practices, organizations can better protect themselves and their customers from these threats.
0 notes
Link
0 notes
Text
Villainous Observation: I love that this chapter of the Risky Heist shows how badass Flug is and he's a high tier Villain worthy of working at BlackHat Organization.
At the end of Episode 6, Flug was able to sneak in by himself disguised as a guard, even wearing a paper bag 😂 no less, to walk in and out to see Miss Heed like it was no big deal and nobody's business. He probably hacked into the facility himself as you can see him appear after lights suddenly went out.



But it turns out that the facility was heavily guarded and was way more difficult to sneak into than what it appears.
Ilumiarrow and Mawrasite needed an elaborate plan to sneak into the place, steal keys from the captain and a hacker to disable security in order to break into the facility.
Flug just makes it look easy.
#villainous#villanos#dr flug#flug#dr kenning flugslys#villainous mawrasite#villainous miss heed#cecilia amanda kelly#villainous missheed#villainous illuminarrow#villainous theory#villainous headcanon#villainous theories
134 notes
·
View notes
Text
Hack Someone Device Wirelessly.
.
.
.
.
.
#hacking #devine #device #android #cpp #procoder#programming #java #python #wireless #blackhat #whitehat #Black #white #instagram #viral #instagood #cybercrime #cyberday #cybrtrk #cybersecurity
#binance#ethical hacking#crytptocurrency#hacking#how to hack#sextortion#hackgame#justgothacked#deleted account#facebookrecovery#accounthacked#cheating spouse#bitcoin#stolencoin
2 notes
·
View notes
Text

New updated ref for my Villainous s/i!!
Erin ends up working at Blackhat Org. bc they hacked into the only strong wifi signal near by, which happened to be BHO's wifi, and upon finding out, Dr. Flug was infuriated that his security was not foolproof. Though also mildly irritated by the intrusion, Blackhat was fairly impressed by their skill and offered to hire them on the spot, yknow that, or, well,, a more lethal alternative.
Erin, being unemployed and totally prepared to sign away her soul to what had to be the devil, immediately said yes and they've been working there ever since. they aren't necessarily evil per say, but they're morally grey, and due to persuasion, ended up siding with the villains. that and one of the villains is super cute. and Erin is super gay.
Demencia, prior to meeting Erin had been obsessively "in love" with Blackhat because of how dastardly evil he was. hell, she even has a Blackhat plushie! Upon seeing Erin however, she immediately fell hard for this sad, tired looking regular old human.
Erin is basically the antithesis of BH's power and evil. They are just human, constantly exhausted and very unimpressive, aside from their intelligence. But Demencia couldn't help but love them anyways. She doesn't know why. Nobody really does.
One day, BH pulls Erin away to his office and everybody thinks this is it. There goes the new coworker. bye bye erin. But really, he just ends up breaking his façade of cool power, momentarily to thank them for taking Dem's attention off of him. It was suffocating and he hated it. He wasn't nice about it obviously, but he was thankful.
Dem is just smitten with Erin and Erin, totally unsure if their feelings are reciprocated, is always painfully awkward around the very forward Demencia! It takes them forever to figure out that YES SHE DOES LIKE YOU, YOU IDIOT!!
After they get together they are the grossest couple ever, just lots of pda and pet names and Dr. Flug hates it. BH hates it. Even the heroes who are all for the redeeming power of love, hate it. Well. The heroes mostly hate it bc Dem and Erin use their combined destructive power as a couple to continue to wreak havoc! The two couldn't care less tho, they just are happy to have each other!
Other Important Info:
- aliased ‘Grave Error’ by the hero community
- most of their individual crimes (as in, outside of BHO association) consist of hacking billionaire CEOs as well as environmentally destructive companies and leaking sensitive/incriminating information about them
- as such they are classified by the hero community as a nonlethal threat, acting more as a rogue environmental activist than anything, really
- still, they are intent on finding Erin and stopping them from releasing incriminating evidence against the corruption of the hero community
- that and they know that Grave Error has an association with the largest villain corporation in the world, Blackhat Org., which is already shrouded in mystery to begin with
Historical Info:
- intellectual and scientific prodigy; thought to have immense heroic potential, went to an esteemed university at the age of 15 to study physics
- coincidentally, the university they went to was neighboring a much more concealed villain education institution, an extension of BHO
- Erin got involved with the wrong crowd, ending up befriending many of the villain students, and even getting into a brief relationship with one Cecelia Amanda Kelly, who would later become the famed heroine, Miss Heed
- this would have consequences years down the line for many people, including Erin and her newfound coworkers at BHO
Misc. Info:
- they are the only person who can get Demencia to take a bath regularly, without hassle; anyone else gets bitten or straight up mauled-
- they are a physics expert by education but have a penchant for computer science and hacking
- they actually are not good at mental math at all, despite the repuatation as a genius
- they don’t tend to get into combat situations, doing their best to avoid physical fights, but if it comes down to it, they can wield several types of knives, most notably throwing knives and butterfly knives (holdover from a childhood hobby)
- has a soft spot for animals and regularly feeds strays around town, shooing them away from Blackhat’s mansion, lest he find and hurt them (he’s not as fond of strays as Erin is)
Relations with coworkers and others:
Blackhat- surprisingly stable; he appreciates the fact that they have diverted Dem’s attention off of him; he’s marginally nicer to Erin than the others out of some semblance of gratefulness, but hardly noticeably
Demencia- well they are lovers, obviously
Dr. Flug- frenemies, partially owing to their professional rivalry as genius scientists and partially due to their clashing personalities; willing to work together occasionally and when they do their combined intellect is formidable
505- they love him dearly, he is the one who can bring Dr. Flug, Erin and Demencia together and stop them from fighting; the also appreciate his cooking, they’ve never had home cooked breakfast everyday like this
Penumbra- friendly colleagues, as scientists in the villain community and environmental activists, they have a lot in common, though Penumbra is much gentler and more soft spoken than Erin, who is more brash and rude; nonetheless, they get along well
Miss Heed- once in their formative years of education, they were in a romantic relationship with her, but its been years since that; honestly Erin thought they’d seen the last of Cecelia after they graduated but years later she reappears in the hero community of all places, quickly rising to fame

#LizardHacker#selfship#selfship art#selfshipping#self ship#self ship art#self shipping#self insert#villainous selfship#demencia selfship#villainous self insert#villainous oc#villainous fan character#villainous fc#self insert art#selfship community#self ship community#villainous#villainous fanart#villainous demencia selfship#demencia x oc#demencia x self insert#villainous x oc#villainous x self insert#f/o#f/o community#self insert community#fictional other#villainous f/o#f/o demencia
27 notes
·
View notes
Text
no, see, in the cyberpunk future blackhats can hack not just computers, but your body as well. they call it meat jacking and
52 notes
·
View notes
Text
When she got to the Blackhats’ dorm, Mariya Usha locked herself in her room and didn’t come out. Tomboy Lombax had tried knocking on her door a few times, but Mariya didn’t answer. So, Tomboy, after spending hours outside Mariya’s door, did the next best thing she could think to do. The thing about being on the Blackhats is that you pick up a few things about technology. And the thing about technology was that it could be broken if you knew how. Tomboy hacked the lock on Mariya’s door.
“Mariya,” Tomboy said, pushing the door open. “Hey, are you okay in here?”
Mariya sat in the corner of her room, hugging her knees, crying softly. Darkness hung in the room, unlike anything Tomboy had ever seen before. It clung to the walls and the floor, like ink in water, and Tomboy had to swim through it to see Mariya fully. She looked up, her eyes glowing red.
“GET OUT,” Mariya shouted, her eyes burning bright, flames flaring around her, out of her eyes and mouth. Tomboy stepped back, but she didn’t run. Mariya hugged her knees closer, the fire in her eyes burning down, back to gentle, soft sobs.
#ultimate league#clorkball#oliver trashcat#blaseball adjacent#tomboy lombax is not rivet from ratchet and clank why would you even ask that?#she's not!
4 notes
·
View notes
Text
Cómo Convertirse en un Black Hat Hacker y Por Qué es una Mala Idea | #Blackhat #BlackHatHacker #Hackers #Hacking
0 notes
Text
https://github.com/xenjin450
I Teach CyberSecurity/Ethical-Hacking , Subscribe To My Youtube To Learn Beginner/Advanced Pentesting.
#cybersecurity#hacking#ethicalhacking#internet#wifi#wireless#pentesting#penetrationtester#blackhat#whitehat#greyhat#technology#informationtechnology#subscribe#subscribetomychannel#youtuber#networking#network#it#cyber#digital#learning#education#marketing#video#xenjin450#tumblr#subforsub#blog#introduction
1 note
·
View note
Photo

Buenos días gente, vamos a darle… que ayer fue un día sumamente pesado y cansado mentalmente… 😷🦠💉🖐👨🏻💻📚😷 ________________________ < Ready to play again ... > ——————————————- \ ,__, \ (oo)____ (__) )\ ||--|| * #pentester #vulnerabilityassessment #HackingTools #Pentest #Pentesting #VulnerabilityAssessment #EthicalHacking #InfoSec #CyberSecurity #EthicalHacker #ceh #MitreAtt&ck #diabetichacker #darkdevil #hacker #hacking #whitehat #greyhat #blackhat #blueteam #redteam #purpleteam (en Monclova, Coahuila, Mexico) https://www.instagram.com/p/CktAivvubFx/?igshid=NGJjMDIxMWI=
#pentester#vulnerabilityassessment#hackingtools#pentest#pentesting#ethicalhacking#infosec#cybersecurity#ethicalhacker#ceh#mitreatt#diabetichacker#darkdevil#hacker#hacking#whitehat#greyhat#blackhat#blueteam#redteam#purpleteam
0 notes
Text
Best Movies on Cybersecurity Watch in 2024
Hollywood has been fascinated by cyber security, cyberattacks, and the criminals that carry them out for almost fifty years. Since the turn of the twenty-first century, there has been a global explosion in the demand for and popularity of these kinds of films due to growing reliance on and acceptance of technology. This collection of films is ideal for anyone seeking a thrilling escape or to explore the world of information security in movies. Each film on this list either directly addresses cyber security, has multiple scenes that focus on the topic or captures the essence of why safeguarding sensitive data is so crucial.
You might be surprised to learn how similar the situations and characters in these stories are, as they are frequently based on actual occurrences. You might be surprised to hear that, for a number of these films, there are lessons that cyber security experts like us can all use in our day-to-day work.
New Releases in 2024 (Predicted):
Ghost Protocol (working title): A cyberwarfare thriller starring Chris Hemsworth as a black hat hacker turned asset for a government agency, navigating a complex international plot to hack into a powerful AI system. (Release date TBD)
Zero Day: A documentary exploring the rise and fall of Stuxnet, a weaponized computer worm targeting Iranian nuclear facilities, and the ethical and geopolitical implications of cyber warfare. (Release date: Early 2024)
Firewall Down: A high-stakes heist film where a team of skilled hackers attempt to pull off a daring cyberattack on a global financial institution, facing off against a seasoned security expert and unforeseen moral dilemmas. (Release date: Late 2024)
Must-Watch Classics:
The Matrix (1999): This sci-fi masterpiece explores the blurring lines between reality and the digital world, raising questions about data security and individual control in a technologically advanced society.
WarGames (1983): A teenage hacker accidentally accesses a military supercomputer capable of launching nuclear missiles, highlighting the dangers of cyber recklessness and the importance of responsible technology use.
Blackhat (2015): Chris Hemsworth portrays a convicted hacker forced to collaborate with the FBI to track down a cyberterrorist targeting nuclear power plants, showcasing the potential consequences of large-scale cyberattacks.
The Conversation (1974): Francis Ford Coppola's suspenseful film centers on a private investigator obsessed with surveillance technology, raising concerns about privacy in the age of digital eavesdropping.
Sneakers (1992): A lighthearted heist film featuring a team of ethical hackers recruited by the NSA to steal a government decoder, offering a glimpse into the world of cryptography and Cold War-era cyber espionage.
Ex Machina (2014): A thought-provoking sci-fi drama exploring the nature of consciousness and artificial intelligence, with themes of digital manipulation and the potential dangers of advanced technology.
The Great Hack (2019): This Netflix documentary investigates the Facebook-Cambridge Analytica data scandal, highlighting the vulnerabilities of personal information online and the ethical implications of social media influence.
The Net (1995): Sandra Bullock plays a systems analyst who works from home in California. After obtaining an enigmatic floppy disk that contains a backdoor into a well-known computer security system, she gets entangled in a fatal conspiracy. Numerous cyber security themes are covered in the plot, such as early instances of cyber terrorism, spoofing, and identity theft.
Ghost in the Shell (1995): One of the most significant cyberpunk entertainments in popular culture, this neo-noir animated thriller is based on Masamune Shirow's manga of the same name. Highlights include a plot centered around the hunt for a hacker known as the Puppet Master and philosophical questions regarding an individual’s place in a hyper-tech-reliant world.
Tech Thrillers:
Who Am I - No System is Safe (2014): German thriller about a young hacker drawn into a dangerous online game with real-world consequences.
The Girl with the Dragon Tattoo (2009): A skilled hacker and investigative journalist team up to uncover a dark conspiracy involving cybercrime and corporate corruption.
Eagle Eye (2008): Two strangers are thrust into a high-tech chase orchestrated by a mysterious AI, exposing vulnerabilities in our interconnected world.
Cyber Heists:
Gold (2016): A group of friends plan a daring cyber heist targeting a global bank, using their unique skills to outsmart security measures.
Now You See Me 2 (2016): Masters of illusion return for an even grander heist, incorporating cutting-edge technology and cyber magic to pull off mind-bending stunts.
Ocean's Eleven (2001): The classic film gets a modern twist with the inclusion of tech experts for a daring casino robbery relying on intricate digital manipulations.
These are just a few examples, but many other movies explore the world of cybersecurity. Enjoy your movie marathon in 2024!
1 note
·
View note
Text
Villainous Theory: Flug has an ordinary family that is not associated with P.E.A.C.E. or The Podemos Bailar
So the popular theory is that Flug's brother and family are associated with P.E.A.C.E. or The Podemos Bailar. Digging through an interview from Alan, I found this about Flug's family that might disapprove that.

So basically Flug's family knows he's a Villain but has no idea he went to Black Hat Institution and is working for Black Hat.
This proves that Flug's family has nothing to do with P.E.A.C.E. or GoldHeart because according to his P.EA.C.E. file, they know that he is working for Black Hat Organisation. (Bottom right, it says that he is an alleged member of Black Hat Organization)

(Original Source from the Podemos Bailar Website, Source from nightfurmoon)
This also proves that Flug's family has nothing to do with the Podemos Bailar, because the group has literally broken into Hat-Manor and has seen Flug's stuff, and seen Flug in the BlackHat orientation videos while they we’re hacking his system.


____
Flug’s Family and History
My theory is that Flug has always had a passion for evil science ever since he was young but his experiments caused a lot of damage and destruction around town.
This leads to his parents often scolding him (as shown by Flug having nightmares about his mom scolding him) and being treated like an outcast by his peers. Also leading his parents to favour Flug's brother who is deemed as more normal of the two. Leading to a strained relationship between Flug and his brother and his parents.

Despite this, Flug still loves his family, but believes they won't understand him or his love for evil science, so he decides to go to Black Hat Institution to pursue his passion, even though he was still bullied by the evil students in the school at least he is in a place where he can pursue his passion for evil science and have a future as a Villain.

Alan mentions that Flug can't dance and only does so in school dances because his mother forces him to. This evidence supports that Flug is keeping the secret from his family while going to Black Hat Institution, while still keeping in contact with them about his school life through emails, phones, and texts, and visits during the school holidays (based on the family photos taken below) giving details about his school life without giving anything away that he goes to a Villain school. And his family probably assumes he is going to a normal boarding school after getting a scholarship for his genius.
After Flug graduates or maybe when he is still schooling, his family finds out that he is a villain by seeing him on the news fighting GoldHeart. Which probably leads to an argument and a further strain in their relationship.

Afterwards Flug would join Black Hat Organisation which his parents don't know about and might have lost contact with them afterwards.
(Or alternatively, we all assume that Flug does not keep in contact with his family, but it would be hilariously ironic if he is still in contact with his family 😂 after joining BlackHat Organization, but there there conversations mainly involve them convincing him to give up Villainy and Flug telling them to let him live his life because he is an adult now!)
Also thinking about it, why would Flug keep photos of his family up if he doesn't still love them, instead of burning them in the incinerator like he did with his stuff on GoldHeart and the only reason why Flug's and his family's face is burnt off in the photo because its done by BlackHat, who finds his human face disgusting and wants to incinerate evidence by photos of Flug's face as well as Flug's family to hide hints of how he looks like.
Making it feel that like Flug still cares about his family and wants them to have a close family relationship and stop keeping things from them but he knows they will never accept him as a Villain, much less working for the most evil organisation and evil being in existence.

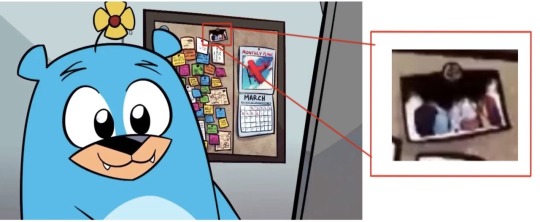
(Second image is from the Villainous Short: Squeak)
#villainous#villanos#dr flug#dr kenning flugslys#goldheart#gold heart#flug#herbert leth#villainous theory#villainous theories#villainous black hat#black hat organization#black hat
76 notes
·
View notes
