#they assume so much knowledge and access to data
Text
one major difference i have found between service industry work (in my case food service but this is widely applicable to similar jobs) and other public-facing positions is that the job itself is often very similar because people is the same, it's just in service everyone approaches you already thinking they're right and you're a fucking idiot and its their god given right to disrespect you, where in other positions even if they are not nice to you they usually acknowledge that you know more than them on issues pertaining to your job. like the difference in behaviour from people who see you as serving them vs helping them is unreal. i am doing literally the exact same things. customer is always right mentality did irreparable damage to the fabric of society
#good idea generator#i loveee the library front desk everyone is polite and people will just ask you anything#they assume so much knowledge and access to data#ill be like 'just one moment let me look that up in the system' [googles name of school + upcoming events]#also not in a mean way but i never realized until i worked here how little anybody is googling anything#i think its funny and i also love to google things for people so i am perfectly suited to this#and some questions even though they are googleable the issue is more that the person isnt totally sure what theyre asking#but like. the library hours are visible on the home page. and outside the building that you just walked into on a sign#PPL DO NOT READ SIGNS. i knew that from other jobs but good lord people do NOT even GLANCE at signs#ppl would fully walk past like 4 signs about a specific thing and proceed to ask me a q about the thing. after waiting in a line#constantly CONSTANTLY ppl are trying to enter or exit through locked doors. clambering over closed signs to do so#its someones job when the library closes specifically to point out the signs and direct ppl to an open exit#and still often people will get up to the automatic doors and be baffled and confused as to why they dont open#but like even this i dealt w/this at my food service job and it was so frustrating#bc when you had to confront these people they would get MAD AT YOU. furious that they didnt read a sign telling them where to line up#but at the library people are polite and apologetic so you know it's not malice or entitlement ppl are just kind of inattentive#monumental difference tbh i actually love front counter so much people are so fun#and i like it when nobody is actively trying to kill me with their mind while we speak
92 notes
·
View notes
Text
SO i've been digging around in the benchmark files with xiv data explorer...
...and with my middling knowledge of how XIV's current texture types work, i've noticed some differences in how texture channels have worked and what data is stored where. i haven't figured out what EVERYTHING'S for yet and if you think you have an idea or any corrections, pls feel free to lmk. could help with figuring out 7.0 modding quicker! this is also decent info for figuring out what old mods can be repurposed for 7.0 graphics.
also content warning for unwrapped face textures under the cut, i know those can look kind of spooky if you arent used to 'em lol
starting off, i didn't source this info but chirp (known plugin dev) on twitter talked about finding about fifty six new bones in the facial armature specifically. this means things like sculpts will probably be unusable unless they are manually re-rigged with each one of those fifty six new bones, or else they wont animate properly.
the default UV maps for the face specifically have changed, too, and many of the uses of the old normal and multi channels have been changed or moved to a different texture. NOTE that these examples were found from au ra textures, male specifically, and the channels may or may not have different uses on non-scaled races!
old vs new multi map. i'm fairly certain every channel here has been repurposed: for example, blue used to be for lipstick, now it seems to be for something else. so where'd the lipstick area data go? well:
it's been moved to the alpha channel on the normal map (these are both the new one). additionally, it seems like the blue channel on the normal map has been changed to signify the difference between skin and non-skin or something of the like.
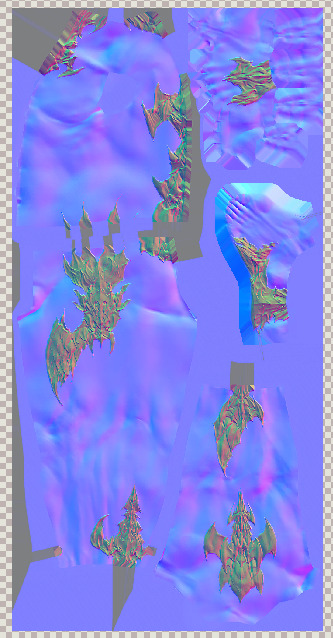
(old vs new) similarly, even though the body seems to use the same UV layout with a redefined normal map, the blue channel here also seems to indicate skin vs non-skin. but the blue channel used to be for transparency (iirc?), so where is that data stored now?
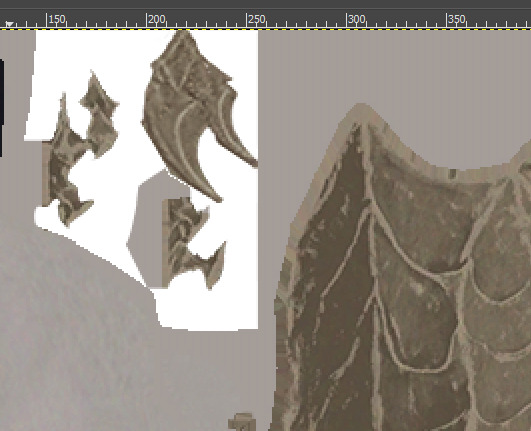
the transparency data seems to have been moved to the alpha channel of the diffuse now. this image is part of the new face diffuse.

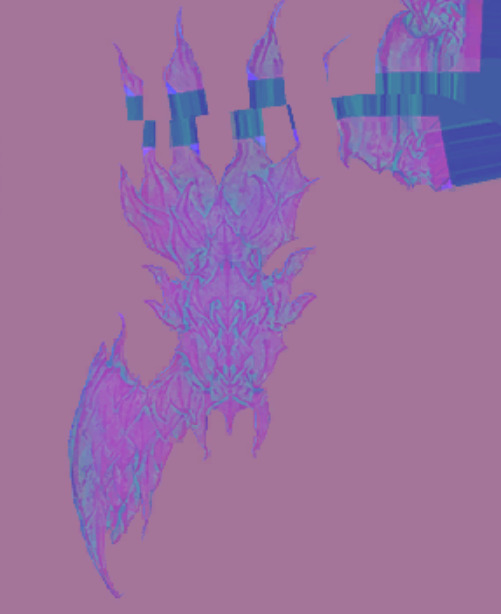
like the face multi map, the body multi map seems to actually use the blue channel now (and looks SO much cleaner, wow!). old vs new.
so what do these changes mean for our current mods?
-due to changed UVs, existing makeups will not be usable with the new faces UNLESS someone goes through the effort of taking the old sculpt (vanilla or otherwise) and weight paints ALL the new face bones to them, or somehow adjusts the UV mapping on the new sculpt to match the old one. i don't work with sculpts so i'm not sure how feasible either of these are
-existing body tattoo mods that only affect the diffuse should theoretically still work fine, as the UVs have not been changed on the body. body scale mods that are just recolors should work fine as well, but matching face scale mods will have to be redone for the new UVs.
-however, if it's a scale mod like dragonborn that changes the placement of the scales and therefore the normal and multi maps, those will have to be adjusted to match with the 7.0 channel uses.
assuming there are no major changes to how this data is stored between now and the releases of dawntrail, you could theoretically begin working now on your own texture mods ready for whenever we get access to 7.0 modding tools. i was able to access these files (and many others) by using XIV data explorer, a program that lets you view and export (but not import!) data directly from specific XIV data indexes.
if you also want to rip textures, the index storing them, alongside skeletons and animations, is 04000.win32.index2. hit ctrl+shift+e to export individual files to a .tex format and then run them through penumbra to convert them into .dds for normals + multis or .png for diffuses for editing. i'm fairly certain that 95% of the pathings will be exactly the same as what penumbra and textools gives us now, so there shouldn't be much need to find entirely new paths.
again, if anyone sees any differences in other races for texture uses or figures out the uses for new channels, PLEASE let me know bc the sooner we get all this figured out the better! i have only been modding for a few years and don't know everything about how every texture works so i'm open to corrections.
#ffxiv modding#ffxiv mods#i just wanted other mod makers to know beforehand so id like to spread this info if possible#finding public modding resources can be a bitch! if i can make things easier i will try
9 notes
·
View notes
Note
Hey there
I just wanted to check, with another writing delay does that mean to release is postponed/delayed again?
I noticed you didn't actually mention that this could be a factor that would delay the game, but so far it seems to be the biggest factor delaying its release.
I'm not sure why you haven't mentioning that when you speak about delays and have been focusing on the art as the thing delaying the release. But it's clear from your weekly updates that the writing for the first route is still not done.
I'm a backer of the KS and it's clear from previous questions you've answered here that I'm not the only one concerned about the lack of writing progress being made for Made Marion. But my biggest concern is your lack of acknowledgment that that is the biggest delaying factor at this point.
I really didn't want to write this message, but it's been almost 2 and half years since the KS and I think your backers and pre-order buyers deserve some clarity around the actual delivery time of this game.
Hiya! Nope, there is no further delay to Robin's route due to writing at this point. (Bolded for TL:DR, the rest is ramblings.) Robin's route is still on schedule to release in early November. I'm being more granular with my exact writing progress in our Tuesday updates precisely so that I can provide the transparency that was requested. So you'll hear about my good weeks and my bad weeks, but please don't worry too much if I have a bad one.
The project's writing and coding are the things I can personally control. I had a rough week last week and ending 4a isn't quite done yet, but it's close enough that I know I can still deliver on time. I have re-chunked out my time so that I will complete ending 4a in smaller writing chunks alongside coding Chapter 3, which is actually how I do my most productive work.
When I didn't include writing as a possible delay factor for Robin's early November release, it wasn't because I'm not acknowledging that writing has been a major delay factor (I dedicated an entire KS update to that this summer). It's because I was personally pledging that my chunk of the project will be done in time for the November release.
For the project overall, the writing and art completion are about equal in terms of delay factors right now. I am still waiting on the full completion of three vital sprites needed for Robin's route and several character sprites that have smaller parts in Robin's route but are important on later routes still need to be done. Our cut-in art is behind schedule as well. Once the sprite art is fully finished and our lead artist only has to worry about CGs (and doing the KS wallpapers), the writing will indeed be the biggest factor in terms of when things come out (cut-ins are more flexible since only a few are vital). But right now, all of us except the fabulous Sandra (background artist) are in the same boat.
The year I lost to long Covid brain fog aside, I will say I regret setting what I now realize was a far too optimistic completion time for the project. I didn't know what I didn't know and didn't have access to a lot of knowledge about how long these projects take.
Now that I have a lot more data points to analyze, I realize that assuming it happens close to the start of development, 4-5 years post-Kickstarter is much more realistic for games of this scope. Because I underestimated so severely and because of my lost year, I'm trying to deliver as much as I can as quickly as possible, which is why I'm putting things out route by route with Early Access.
In the future, I'll be doing things very differently. After Made Marion and its DLC is completed, I'll be taking a good long time to finish most of the writing for my next game before I worry about commissioning art or doing any crowdfunding, if I decide to do crowdfunding. I'll have the cushion to do that after having put out our first game.
In the meantime, what I can pledge is that Made Marion is our top priority; I'm not doing jams or smaller games in the meantime, I'm just making this game.
This will probably be the last ask like this that I answer for a while, as it does ratchet up my anxiety. I will continue to report our progress on a weekly basis in preparation for our November Robin launch!
Edit: For clarity on underestimating completion time.
28 notes
·
View notes
Text
Anticipating the future of malicious open-source packages: next gen insights
New Post has been published on https://thedigitalinsider.com/anticipating-the-future-of-malicious-open-source-packages-next-gen-insights/
Anticipating the future of malicious open-source packages: next gen insights


Ori Abramovsky is the Head of Data Science of the Developer-First group at Check Point, where he leads the development and application of machine learning models to the source code domain. With extensive experience in various machine learning types, Ori specializes in bringing AI applications to life. He is committed to bridging the gap between theory and real-world application and is passionate about harnessing the power of AI to solve complex business challenges.
In this thoughtful and incisive interview, Check Point’s Developer-First Head of Data Science, Ori Abramovsky discusses malicious open-source packages. While malicious open-source packages aren’t new, their popularity among hackers is increasing. Discover attack vectors, how malicious packages conceal their intent, and risk mitigation measures. The best prevention measure is…Read the interview to find out.
What kinds of trends are you seeing in relation to malicious open-source packages?
The main trend we’re seeing relates to the increasing sophistication and prevalence of malicious open-source packages. While registries are implementing stricter measures, such as PyPI’s recent mandate for users to adopt two-factor authentication, the advances of Large Language Models (LLMs) pose significant challenges to safeguarding against such threats. Previously, hackers needed substantial expertise in order to create malicious packages. Now, all they need is access to LLMs and to find the right prompts for them. The barriers to entry have significantly decreased.
While LLMs democratise knowledge, they also make it much easier to distribute malicious techniques. As a result, it’s fair to assume that we should anticipate an increasing volume of sophisticated attacks. Moreover, we’re already in the middle of that shift, seeing these attacks extending beyond traditional domains like NPM and PyPI, manifesting in various forms such as malicious VSCode extensions and compromised Hugging Face models. To sum it up, the accessibility of LLMs empowers malicious actors, indicating a need for heightened vigilance across all open-source domains. Exciting yet challenging times lie ahead, necessitating preparedness.
Are there specific attack types that are most popular among hackers, and if so, what are they?
Malicious open-source packages can be applied based on the stage of infection: install (as part of the install process), first use (once the package has been imported), and runtime (infection is hidden as part of some functionality and will be activated once the user will use that functionality). Install and first use attacks typically employ simpler techniques; prioritizing volume over complexity, aiming to remain undetected long enough to infect users (assuming that some users will mistakenly install them). In contrast, runtime attacks are typically more sophisticated, with hackers investing efforts in concealing their malicious intent. As a result, the attacks are harder to detect, but come with a pricier tag. They last longer and therefore have higher chances of becoming a zero-day affecting more users.
Malicious packages employ diverse methods to conceal their intent, ranging from manipulating package structures (the simpler ones will commonly include only the malicious code, the more sophisticated ones can even be an exact copy of a legit package), to employing various obfuscation techniques (from classic methods such as base64 encoding, to more advanced techniques, such as steganography). The downside of using such concealment methods can make them susceptible to detection, as many Yara detection rules specifically target these signs of obfuscation. Given the emergence of Large Language Models (LLMs), hackers have greater access to advanced techniques for hiding malicious intent and we should expect to see more sophisticated and innovative concealment methods in the future.
Hackers tend to exploit opportunities where hacking is easier or more likely, with studies indicating a preference for targeting dynamic installation flows in registries like PyPI and NPM due to their simplicity in generating attacks. While research suggests a higher prevalence of such attacks in source code languages with dynamic installation flows, the accessibility of LLMs facilitates the adaptation of these attacks to new platforms, potentially leading hackers to explore less visible domains for their malicious activities.
How can organisations mitigate the risk associated with malicious open-source packages? How can CISOs ensure protection/prevention?
The foremost strategy for organisations to mitigate the risk posed by malicious open-source packages is through education. One should not use open-source code without properly knowing its origins. Ignorance in this realm does not lead to bliss. Therefore, implementing practices such as double-checking the authenticity of packages before installation is crucial. Looking into aspects like the accuracy of package descriptions, their reputation, community engagement (such as stars and user feedback), the quality of documentation in the associated GitHub repository, and its track record of reliability is also critical. By paying attention to these details, organisations can significantly reduce the likelihood of falling victim to malicious packages.
The fundamental challenge lies in addressing the ignorance regarding the risks associated with open-source software. Many users fail to recognize the potential threats and consequently, are prone to exploring and installing new packages without adequate scrutiny. Therefore, it is incumbent upon Chief Information Security Officers (CISOs) to actively participate in the decision-making process regarding the selection and usage of open-source packages within their organisations.
Despite best efforts, mistakes can still occur. To bolster defences, organisations should implement complementary protection services designed to monitor and verify the integrity of packages being installed. These measures serve as an additional layer of defence, helping to detect and mitigate potential threats in real-time.
What role does threat intelligence play in identifying and mitigating risks related to open-source packages?
Traditionally, threat intelligence has played a crucial role in identifying and mitigating risks associated with open-source packages. Dark web forums and other underground channels were primary sources for discussing and sharing malicious code snippets. This allowed security professionals to monitor and defend against these snippets using straightforward Yara rules. Additionally, threat intelligence facilitated the identification of suspicious package owners and related GitHub repositories, aiding in the early detection of potential threats. While effective for simpler cases of malicious code, this approach may struggle to keep pace with the evolving sophistication of attacks, particularly in light of advancements like Large Language Models (LLMs).
These days, with the rise of LLMs, it’s reasonable to expect hackers to innovate new methods through which to conduct malicious activity, prioritizing novel techniques over rehashing old samples that are easily identifiable by Yara rules. Consequently, while threat intelligence remains valuable, it should be supplemented with more advanced analysis techniques to thoroughly assess the integrity of open-source packages. This combined approach ensures a comprehensive defence against emerging threats, especially within less-monitored ecosystems, where traditional threat intelligence may be less effective.
What to anticipate in the future?
The emergence of Large Language Models (LLMs) is revolutionising every aspect of the software world, including the malicious domain. From the perspective of hackers, this development’s immediate implication equates to more complicated malicious attacks, more diverse attacks and more attacks, in general (leveraging LLMs to optimise strategies). Looking forward, we should anticipate hackers trying to target the LLMs themselves, using techniques like prompt injection or by trying to attack the LLM agents. New types and domains of malicious attacks are probably about to emerge.
Looking at the malicious open-source packages domain in general, a place we should probably start watching is Github. Historically, malicious campaigns have targeted open-source registries such as PyPI and NPM, with auxiliary support from platforms like GitHub, Dropbox, and Pastebin for hosting malicious components or publishing exploited data pieces. However, as these registries adopt more stringent security measures and become increasingly monitored, hackers are likely to seek out new “dark spots” such as extensions, marketplaces, and GitHub itself. Consequently, malicious code has the potential to infiltrate EVERY open-source component we utilise, necessitating vigilance and proactive measures to safeguard against such threats.
#Accessibility#ai#Analysis#applications#approach#attention#authentication#Business#challenge#Check Point#CISOs#code#Community#complexity#comprehensive#Dark#Dark web#data#data privacy#data protection#data science#details#detection#Developer#development#documentation#domains#double#dropbox#Ecosystems
3 notes
·
View notes
Note
I'm curious, what's rivulet doing over at sigs can? Since iirc they're normally with Moon
So it’s kinda connected to this other thing me and ghost were talking about where once Moon gets reactivated by Rivulet, she can write to pearls again! Even though she can’t broadcast beyond her local facility, she needs Sig to know his efforts to save her won’t in vain. So she asks Riv to take a pearl to her so she’ll know. And they start talking again! It’s slower than broadcasts, but Ruffles is a fast lil fucker, so it isn’t too bad.
Sig is also in pretty bad shape. Nothing like Pebbles or Moon, but he’s kinda been pinned to the floor by his rig because it gave out, and keeping the antigrav on is really taxing on her rarefaction cells. She still has access to her comms though and keeps up with Suns and occasionally Wind if the signal is good that day. He also…well. He kind of assumed Moon was dead. But he kept using their private messages to talk to her or vent, and it gets pretty heavy at points. He has a lot to work out, especially in terms of Pebbles, but that comes later in the au once they actually manage to get Off The String.
Here’s a lil snippet!!
“Ruffles…I know you have already done so much for me. But…far to the west, there is another like us. You may have seen him on your travels here, as I do not know where you came from. But…” She looks down at the green pearl that used to contain a schematic of Pebbles’ linear power rail, wiped clean and rewritten with a new message. “I need you to give this to her. My overseer will accompany you, though I do not know how far it will be able to go. Please, water dancer.” She turns the pear in her hands, it’s shiny surface reflecting her face for a moment before she gave it to rivulet. “I need her to know I’m okay.”
—
“Well, aren’t you the strange little beast?” Sig looked up at the access shaft that a slugcat—if you could call it that—was poking its head through. It dropped, landing on the tile with a roll and stopping right at his feet. “I haven’t seen one of your kind in a long while.”
Sig was trapped. Despite all his knowledge, and skill, and determination that bordered on the line of sheer stupidity, he found himself trapped on the floor of his chamber. His rig had given out, and the antigravity was too taxing on the few rarefactions cells she had left to keep on. And so she sat. Messaging friends, collecting data with her overseers, he had even unwound his scarf just to knit it all over again…three times. He was painfully bored.
The lithe blue slugcat leapt into her lap, and Sig shivered when he realized how wet it was. He made a noise in complaint, but honestly, being able to process a new sensation was incredibly welcome, even if it was unpleasant. The slugcat retched, before shoving the (also wet) pearl into her hands.
“A…wait…?” He looked up. “You have a mark?” Sig was about to go off on a tangent of confused questions, when the little slugcat slapped its hand on the pearl repeatedly, urging her to just read it already.
“Okay, okay! I’ll read it.” Sig had to fight a laugh at the look of impatience on the little animal’s face. Looking down at the pearl, he felt it warm up in her palms as she extracted the data into a readable form.
[OUTGOING REQUEST]
COMMUNICATIONS MANIFEST
SOURCE NODE TRACE: LTTM_ROOT, LTTM_COMM01 || DESTINATION: NSH_ROOT, NSH_COMM03
BSM: This is the fourth time I’ve wiped and rewritten this stupid pearl.
BSM: Limited functionality has been restored to some of my systems, and I am able to write to pearls again for the first time since the collapse. I would have sent this as a broadcast, but I am unable to send messages beyond the local facility.
BSM: …
BSM: I do not know if this message will even reach you. I do not know how long it has been. I don’t even know if you’re alive.
BSM: But I need you to know your efforts were not in vain, No Significant Harassment.
BSM: Your little messenger saved me. The slag reset keys made it. She managed to fight through it all…she was a brave little creature.
BSM: I…have been making my way through your broadcasts.
BSM: There is not enough memory on this pearl to address everything within them now, but I hope you have found a little bit of peace since the last one came through. And if not, perhaps this message will ease your mind.
BSM: Please signal back in any way you can.
BSM: …
BSM: I’m sorry, Sig.
BSM: I hope to hear from you soon. Please give Ruffles scratches, she likes it behind her left ear the best.
BSM: Be well, my love.
Sig felt like every single one of his memory lattices had been shattered. Every conduit in his can squeezed, steam pouring from her vents as she tried to process the message. This couldn’t be—was this a joke? No, the message header was authenticated…
“Moon…?” Sig whispered, barely audible. The slugcat—Ruffles, apparently—perked up at the mention of her mom.
“Wawa!” She bounced, bringing Sig’s attention back to her and getting swept into his arms, squeezed tight as a mechanical sob escaped him.
“She’s alive! SHES ALIVE!” He held Ruffles up. “I know you don’t understand, Ruffles, but shes ALIVE!”
Ruffles, of course, understood very well what that meant, but Moon had not explained how she was functioning again in the message, so Sig wasn’t aware that Ruffles had been the one to reactivate her with the cell. She hoped Moon would explain that soon. She wanted headpats. Sig placed her in his lap, pulling up a screen before him to message Suns, before stopping, and looking down at the pearl.
“Ruffles, could you please grab me one of those pearls over there?” She asked politely, not wanting to pathetically drag herself across the floor in front of her. Ruffles obeyed, depositing an orange pearl in his hands before flopping back into the warm folds of her skirt.
Sig wiped the new pearl, as it was just an old equipment manifest. Useless to him now.
[OUTGOING REQUEST]
COMMUNICATIONS MANIFEST
SOURCE NODE TRACE: NSH_ROOT, NSH_COMM03 || DESTINATION: LTTM_ROOT, LTTM_COMM01
NSH: [Input message contents]
Now she just had to figure out what to say.
#HEHE TY FOR THE ASK!! this au is rlly fun despite being shitposty at times it’s also. ahh#rw#inverted cycles au#letters
10 notes
·
View notes
Text
Some .hack//YGO AU thoughts under the Read More, bc if I don’t breathe it into existence it will NEVER BE………
I'm drawing self-indulgent arts and strips about it... might make it a fic someday...? idk
My partner Quill (@themadcaptain) and I are putting characters in situations again, and we’re here in the hit online MMO The World
*Yuki Kajiura's The World playing softly in the background*
We've really only ever seen .hack//SIGN and between us, we've maybe played 3 out of 4 of the PS2 games (we started replaying .hack//Infection a while back) so our knowledge of the series is vague and limited at best... I'll look into the rest, but .hack is just a large multimedia franchise with SO MUCH BACKGROUND STUFF HAPPENING
anyway, BACKGROUND STUFF (assuming you know nothing of the .hack series):
The World is a fairly standard VR-enabled MMORPG, but otherwise functions as any other MMO does. It was originally created by programmer Harald Hoerwick under the name Fragment.
The story behind The World itself is largely based on an epic poem known as the Epitaph of the Twilight, written by fictional poet Emma Wieland. Hoerwick was infatuated with Wieland, and when she died, he created Fragment in order to immortalize her work. Fragment, and subsequently The World, contains a secret black box project he had been working on: the ultimate AI named Aura. In universe, this black box data exists within the game, but it is unable to be analyzed. CC Corp, the company that buys Fragment from Hoerwick, beta tests it (with beta testing ending early for unknown reasons), and releases an upgraded version known as The World.
Because of the presence of this Ultimate AI, a lot of mysteries crop up in game, and some players are met with disaster as a result (ie. many fall into comas, have their consciousness trapped in game, etc etc.) and CC Corp is trying to cover up these disasters by deflecting responsibility. However, the AI has been aiding hackers within the game in stopping the mysterious corruption in the game's files.
...SO WHERE DO THE YUGIOH DUDES COME IN?
The parallels between Harald Hoerwick and Pegasus are obvious. It would also be really cool to have his dead fiancée have more of a role other than being Pegasus's muse and motivation. (Also, if you've played the .hack games and seen the creatures in game, then you know this is something he would have absolutely created.) I don't know much about Wieland, but it's implied that she was using Hoerwick's research and talents for her own ends, which is fascinating.
I like the idea of Kaiba Corp collaborating with I2 on this game, with I2 selling it to KC... I also imagine KC still having Gozaburo and The Big Five who would be dismissive of the players' concerns about the comas and such, going so far as to delete forum threads and accounts just to save face...
Then we have Seto Kaiba. The future CEO of Kaiba Corp. Current leader of the Cobalt Knights (group of admins in The World working for KC), and this AU's stand in for Balmung of the Azure Skies Eyes (hehe). I imagine he has NO IDEA what's going on behind those closed doors, but eventually learns what role KC is playing in regards to all of this, and vows to put an end to it on his terms. I also like to believe Mokuba is also part of the Cobalt Knights, and is one of the victims who gets his consciousness trapped in the game, very much like Tsukasa from .hack//SIGN.
And Noa Kaiba? Big Morganna Energy... In .hack//SIGN, Morganna was created to oversee the birth of the Ultimate AI, but would ultimately rebel from this purpose, stalling the development of the Ultimate AI and setting off a lot of disastrous events. I imagine Noa would also be, like, the consciousness uploaded into the system - the one who could access the black box data - but could not export it to KC. With his own father abandoning him within the mainframe, Noa is working to destroy the game from the inside out... and he's responsible for trapping Mokuba in-game.
I feel like if one's consciousness can be uploaded into the MMO, I think it could stand to reason that ghosts and spirits can exist there too...
Alright, so there's some background info... and sadly we're a bit intimidated trying to tackle it all, and also trying to keep up with the different continuities between the different anime and the video games... one day, we'll figure it out... and one day I won’t be too intimidated to tackle this story from Kaiba’ POV…
I’ll probably make a separate post about what everyone else’s role is in The World a bit later!!! owo;;
#Renae rambles#dot hack#Yugioh#.hack//YGO#I guess is what this crossover will be called#obvs we have the heartshipping plot ❤️✨👌#but I’ll save that for the next post ehehehe
2 notes
·
View notes
Note
To the person who sent this ask:
https://at.tumblr.com/mycptsdrecovery/hi-im-sorry-to-ask-this-really-because-it-feels/fepccd6vfm9e
So first off I want to apologize because this message is probably gonna fuck your shit up a little bit. But for me at least, clarity brought peace. I hope this helps you put the pieces together and can bring you some comfort to know that you are not alone, what happened to you was very real and incredibly traumatic, and that you are incredibly strong for living through that. You’re obviously very smart and you’re asking the right questions- keep it up.
I read your post and I know exactly what happened to you. You had a VCUG. I had it done too, multiple times when I was 3. It took me literally 20 fucking years to figure out what that was and what happened to me. When I read the Wikipedia page, it was like I got hit in the head with a brick so brace yourself before you look it up. The procedure has literally every characteristic of a sexual assault, and I have lifelong sexual trauma from it. It’s used as a tool in research for studying memory related to CSA, because ofc you can’t abuse children to get data- but the VCUG is “medically necessary.” I think it’s almost worse in a way because it’s more like a gang rape WHILE YOUR PARENT IS WATCHING, and you’re not even seen has an object of attraction- it’s dehumanizing, and the denial of autonomy over your own body has serious, long term effects. It set me up for a lifetime of other sexual trauma- by the time I was 6 I was already showing hypersexual behavior. I never learned how to set any boundaries. Period. If you learn as a child that you don’t even have privacy *in the bathroom by yourself*, layered with the confusion and embarrassment of the experience (I was being potty trained, and then all of a sudden I’m in a radiology room and my mom is telling me I have to pee on this table in front of all these people??) seriously fucked me up, at least.
I spent literally my entire life not knowing why I was so fucked up, not knowing why I was so deeply traumatized when nothing (that I knew of) happened to me. It’s agony, and I blamed myself and lost myself in addiction and anorexia. Funnily enough, Ive always gravitated towards people who had serious childhood trauma. I’d hear their stories, and understand the feelings, but I never had a “story” of my own. It made me feel like an imposter, because it wasn’t like I got raped by a family member or something more “textbook”. Nobody talks about VCUG trauma even though thousands of kids go through this every year. It’s a faceless trauma, there’s nobody to blame (which makes it even more difficult to cope with imo)
There’s like one (1) support group on Reddit with 70 members, which is the largest to my knowledge. I was thinking of maybe starting a blog because there’s a lot of older people on reddit (like 5-10 yrs older than me at least) and I think that growing up Online with that trauma and 24/7 access to violent adult content is a totally different experience. But all of the emotions they talk about are the same, I’ve always kinda felt like nobody could understand what it’s like to be in my head, but reading that subreddit made me realize that I’m not The Most Fucked Up Person Who Has Ever Lived. And I learned how the trauma has formed every facet of my personality. Like I’m an anxious control freak who feels no sense of ownership over my body- surely that has nothing to do with this foundational traumatic memory of being denied control over my most basic bodily functions, right? Much to think about lol
You’re not crazy, and what you went through is unfortunately very real. I’m assuming that you’re still a teenager or a very young adult so you may not have gotten a yeast infection since you were a kid, but I think that the white stuff/medicine you were describing was monistat for a yeast infection. It’s a suppository, so there’s a like plastic plunger you put this white egg on, and then you put it in your vagina and push it up to your cervix, and the medicine leaks out over the course of a couple days. So it doesn’t surprise me at all that you would remember that, someone put a foreign object inside of you that was itchy and gross.
And for the record, your parents are *Very* Bad At Boundaries!!! If they can’t be the adults and set healthy boundaries, you have to. Its perfectly okay to say “I don’t want to talk about that” or “you’re making me uncomfortable, please stop touching me”. You didn’t have a voice when you were a kid, but you have one now. Trust me, I know it’s fucking scary and feels impossible- but do it once, and you’ll be hooked on the feeling forever.
I figured everything out last year (I’m about to turn 24), and I’ve been in therapy which has been super helpful. For me at least, EMDR has really been great for reprocessing those memories, and so has hypnotherapy exercises for being able to get into my subconscious. If you’re gonna look for one, you need a trauma specialist. Don’t fuck around with like a school counselor who mainly does “I’m depressed sometimes” therapy. If you’re anything like me, you need Serious Help.
I love you internet stranger- everything’s gonna be okay. You’re not alone, and it is possible to heal ❤️ I hope this brings you some peace
.
14 notes
·
View notes
Text
So a little inside baseball ... but let's assume you are excited about starting a female empowerment narrative pro sports league for a niche sport that's never been done before where athletes get to tell their own story and make cash so they can continue their sport after college.
Narrator: It's not the first time, it's only new in concept in that it's structure is more ambitious and less obviously feasible.
So you are wanting to start a pro league for, let's say for the sake of argument, oh I don't know, women's gymnastics. You have all this attractive market research data available based on the popularity of NCAA gymnastics. But one of the very basic things when you launch a new product is you see if someone has launched a similar product before or if there is a similar product else where in the world.
Narrator: Yeah that step? These people don't appear to have done that.
So talking to some people who have heard the pitches for this league both to sponsors and athletes here is the first major mistake they made (aside from you know, not doing research). Imagine that you are some well meaning gymnastics coaches and a marketing executive that has tried to start several (apparently folded) sports leagues in the past. You've lived through the dumpster fire of the USAG sexual abuse scandal. You think... oh I'm going to tell all these potential sponsors that we have nothing to do with USA Gymnastics. That will give them confidence.
And maybe at the height of the dumpster fire in 2018 in the wake of the victim impact statements that might have been the call. But it's a terrible reading of the room now. And really it was a terrible reading of the room a year ago when they apparently started pitching this to sponsors. Corporate sponsors have been returning to USAG. Whatever you think of Li Li, this was her job, to right the ship and her job experience (unlike the women running this enterprise) is dealing with major sponsors. So what the pro league people thought was going to be reassuring to sponsors in fact was a red flag to them.
See, no one loves a sports national governing body (or an international one), but what they have is institutional knowledge, access to equipment manufacturers, to athletes, to venues, they know how to run meets and in general they provide a certain amount of safety net on basic organizational issues. Every sports league founded in the last few decades that is successful has some support from the governing body even when there is tension between the players and that organization. The national women's soccer league has ties to USA Soccer because you need those ties to function as a league and I promise you there is no more love between women's soccer player/fans and USA Soccer than there ever was between USAG and women's gymnastic fans.
This stance probably seemed even more out of touch in 2023 than it was in 2022 as USAG emerged from the sponsorship wilderness and started seeing much bigger names having confidence in putting their names next to them.
Who in this group decided that "we have nothing to do with USAG" was a good move I don't know.
They also apparently spent a lot of time being concerned that the potential sponsors fit their leagues ethos. Which is not inherently bad, you don't want a case like US Figure Skating being sponsored by the It's not a Diet It's an Eating Disorder App - Noom. But that becomes less something I trust them with when one of the big name founders has previously shilled a weight loss MLM.
But anyway apparently the sponsors also looked at the reaction among the fandom to the launch of the website in June and were put off by the fact that there was less enthusiasm and more skepticism than the league founders had expected.
I know I was active in those few discussions and if I was a sponsor I'd probably be concerned about one of the things that @darthmelyanna raised: the nature of gymnastics means injuries will happen and the league didn't seem to be providing insurance meaning that we were likely to see a lot of medical expense Go Fund Me's n the future.
But all of these missteps with sponsors also has a side issue. Apparently they finally did realize they need to get insurance for their league (I can't imagine a venue was willing to host one of their events without it and I would hope that athletes wouldn't be signing up to this without it). Supposedly they then went to USAG... the organization who they were badmouthing to sponsors (who themselves were trying to recover sponsors so was very much aware of that)... and they inquired about getting USAG to add them to their insurance pool for gyms.
I'll just let you think about what the answer might be to that. Because that would be a profoundly bad financial stewardship decision for USAG to do for their overall membership/insurance pool. Even if they wanted to help these people.
6 notes
·
View notes
Note
Thank you so much for running this blog, never forget you're an awesome and very kind person that deserves good things in your life.
I have brain damage, though I don't know how bad it is. It's from when I was younger and it was never checked on after the event (I had other injuries that were worse and more important). My skull was fractured and brain damaged on the back left and top part of my head.
I have "brain glitches" and difficulties with processing things and other stuff, but I don't know how much of my life is impacted by the brain damage or if I fully recovered and am not like, a genius/these are normal non-brain damage related stuff lol.
I wanted to ask if brain damage impacts how someone experiences trauma? I've gone through traumatic stuff and have neglectful and emotionally abusive parents. I struggle to feel my age, is this possibly due to brain damage? Could I be developmentally behind?
Sorry if these aren't questions you can answer, thanks so much for any help you give :)
It must have been utterly horrible for you, if brain injury wasn't a priority. I am sadly, not an expert on brain injuries, so I have no clue how exactly this could have affected you. I think it depends on what areas of your brain were affected, but if you get glitches it's obviously harder to deal with anything.
I hope you can ask a doctor, or a neurologist these questions, because they might have scientific or study-collected data that you're looking for, I don't know anyone with a brain injury, so I can't even assume what it would or wouldn't affect. If you have access to healthcare, I would recommend trying to get even just a conversation or send a question in an email to see if anyone can answer it for you. Since you are having problems with processing things, it's possible that you need to get this damage looked at and assessed, I don't know how dangerous brain damage is, but it sounds serious.
I can tell you that abuse can sometimes make it very hard to process things, and make it hard to feel your age. It also can make you feel developmentally behind, because you miss out on a lot of social development while you're stuck in abuse, or dealing with severe and dangerous life circumstances.This also stops you from gaining a lot of knowledge and skills people your age usually have, so this can make you feel like you're behind as well. However, all of these can be made up for, and with a bit of looking up tutorials, socializing, learning and trying out skills, you can catch up easily, this is not a non-solvable problem, this can be remedied just by gathering knowledge and experiences.
I am so sorry you are dealing with all of this. I can't tell if your brain damage affected all of these problems and made it worse, but it's clearly making you very worried, scared and concerned. I hope you can get to a point where you know exactly what is happening with your brain, and how to feel more normal. You don't need to feel your age at all times, a lot of people don't, even when they're not traumatized. You can write very clearly, and don't seem developmentally behind at all, from what I can tell. (though I'm only assuming from this message, I don't know what your age is).
19 notes
·
View notes
Text
Power was the headiest of venoms.
For Keisuke, that wasn’t simply a given. After years and years dedicating his time and patience to the studies of long-lost psychology masters, who knew everything and a bit more about the human mind, it didn’t seem wrong to assume he would end up attracted to the darkest corners of the practice. Instead of a creature of habit, he was one of curiosity. Depravity called to him like nothing else did; understanding where power came from as he exerted it himself was no more a test than a need.
Those days, the invisible pieces of the chessboard that seemed to be his life moved quickier, within orchestrated, well-thought moves. Accepting the job as his favorite professor’s adjunct instructor hadn’t been what he had wanted initially, yet having so many privileges and way too much free time could end up being a dangerous indulgence. And because of that, spending his hours preparing the most perfect lectures and revising his students’ papers made for a perfect counteract to the rest of his days working on his own research.
During those classes, Kei had unrestricted access to the raw minds of freshly-integrated undergraduates, the ones who still knew so little about the vast world of psychology, but that held so much potential to being steadily molded by him. With time, he could introduce the brightest ones to the right studies, taking pride in being a guide, a powerful source that could be looked up to.
But nothing ever really went how people wished it did. Keisuke could’ve never predicted someone like Somi; a student who had just recently transferred her major, a new addition to his class. Way more than he liked to admit, his eyes seemed to stray to her dark, sharp ones, to her quick-witted addendums to the lecture and the mere way she lived and breathed around him. He could feel it growing slowly, right on the base of his neck: the small pinprick of an obsession. It was almost impossible to avert it.
Such recognizal made him slightly sick. He knew virtually nothing about her apart from the data that the academy kept about Kwon Somi, and not knowing had always been something Kei couldn’t adjust to. Sooner than later, she consumed his thoughts; the girl had no idea about her impact, about the danger of being caught on his snare. Even if he could explain it, he feared he wouldn’t. As Higa had learned throughout his life of studies, uncovering the human brain could be fatal; knowledge wasn’t always enlightening. Depravity was best kept at its lair, the hidden, dark corners of the mind.
To him, however, hiding had never been an option. Kei had started pursuing her annoyingly, boldly crossing the moral line of the type of relationship a senior should maintain with a student. Try as he might, the man had never lived by humanity’s morality code, and making up some excuse to have her near him way after visiting hours wasn’t a hardship - not to his conscience, nor to the academy. Somi could’ve perfectly submitted her paper the morning after. She just had no idea about that.
And that was how he found himself hovering over her after he convinced the girl to sit down and go over her text for the thousandth time. His eyes cataloged every lift of breath, every hair on her head disturbed by sudden movements. Keisuke was enraptured by such natural beauty, to the symmetry of those sharp lines. For some insane, primal reason, he needed her around him. He simply had to find out why.
“Check that paragraph again.” Disrupting those intrusive thoughts, Kei pointed to one of the first paragraphs of her well-elaborated paper, one that needed absolutely no revision at all. He took that precious instant to surround her hunched form from behind the chair, so close he could feel the heat emanating from her body. After so long studying crazy people, he feared he would end up going insane as well.
5 notes
·
View notes
Text
Global Financial Solutions Asia Advice That Is Beneficial To Succeeding With Forex
Global Financial Solutions Asia Professional tips provider. Trading Forex could be the scariest thing you have ever done or just another day in your life. There is no quick fix method to making it in Forex. The key is to utilize any and all advice you can get. The tips and ideas you will see here are for your benefit and should be used wisely.
Understand the various types of markets in Forex before you begin trading. Recognize how these markets act with certain currency pairs. If you are unable to spot trends and upswings and other information, you will definitely put your money on losing trades. Proper market research is a must in this trading platform.
Create a trading plan before you actually engage in trading. You don't need to make decisions while trading that rely on your emotions. Make sure you plan your tactics. These should include items such as entry and exit points and goals. Stick with your plan and only make little changes when necessary during a session.
Read articles online or newspapers that relate to foreign markets. This will help you to gauge exactly what is going on in the world that will impact your investments. Understanding exactly what you are up against will help you to make logical decisions that can earn you a lot of extra money.
A great tip for forex trading is to never think in terms of absolutes. You should always think in terms of probabilities. A trade is never certain no matter how confident you are in it. A trade that appears to be a great one can turn sour. Sometimes, there is no way you can anticipate when this occurs. You just have to accept your loss and move on.
Forex is not a game. If you want to be thrilled by forex, stay away. Those looking for adventure would do as well going to Las Vegas and trying to make money there.
If you used a demo or fantasy forex account prior to trading on the real markets, keep the demo forex account even after you start trading. It is vital that you continue to learn and practice, and you can practice new strategies on the demo account before doing them for real, allowing you to catch problems or mistakes.
Global Financial Solutions Asia Proficient tips provider. Remember that a trading plan in Forex is a lot like a business plan. You need to include every possible angle here, including what you can afford to spend and even how much you expect to grow as your business profits. Plans will ultimately change, but no venture can succeed unless you put a proper plan in place.
Beginners coming to Forex in hopes of making big profits should always start their trading efforts in big markets. Lesser-known currencies are appealing, primarily because you assume no one else is really trading them, but start with the bigger, more popular currencies that are far less risky for you to bet on.
If you do not have a lot of money to spend for a forex account, look for the best deals. You have to keep in mind that if you do not pay much for a forex account, you might not have access to all of the services that this broker might offer.
To make money in foreign exchange trading, it is necessary to check the conditions of a certain currency before making a trade. This can be done by reading various news and political data associated to the country you choose to trade with. A country's currency is usually a reflection of the country itself.
Be sure to do you research and complete a complete analysis prior to making any moves in Forex trading. Any moves that are not carefully considered are almost foolish and can lead to financial disaster for just about anyone. Do not gamble with your money, research and analyze before doing anything.
Be sure to take the time to gain knowledge about fibonacci levels and how to put them to use for trading forex. This can be very helpful. This study will help you learn about the best exit strategies and so much more. Take the time to learn it, and it can bring you to the new edge of trading.
Global Financial Solutions Asia Most excellent service provider. Every Forex trader should constantly analyze the market. You should always take notes and dissect your strategy to see what works and what does not. The best way to gain knowledge is through experience, but that experience means nothing if you are not paying attention to how well your strategies are doing.
If you have a background in stock market trading, you have to understand that leverage works very differently with forex. On the stock exchange market, the leverage is related to how many shares someone has, or how much money they have invested. With forex, everyone can have access to a wide range of leverage ratios.
The technical analysis required for profitable Forex trading is never done. Continue to develop your skill as a technical trader, and keep up on new ideas, indicators and strategies. Technical skill and analysis only gets better with more experience and more knowledge, so become a student for life and keep pursuing more technical trading knowledge.
Always stay up-to-the-minute with the latest news in Forex. By keeping yourself well-informed, you will understand what's going on in foreign exchange. This should not sway you from following your chosen strategy, but it will give you an edge in making good choices in trading. That's how you make money with Forex.
To maximize gains and minimize losses in your FOREX trades, don't go against the trend. Going against the momentum is like trying to swim upriver. Put your money where the money is. Never forget that even if a currency appears to be oversold, it can drop even further until it hits support levels.
Global Financial Solutions Asia Qualified tips provider. Now you have some useful information to help in your trading efforts. Remember that this advice is only useful if you incorporate it into your game plan. Failing sometimes in Forex is bound to happen, however, failing to make use of good advice is an easy way to fail consistently.
0 notes
Text
Malicious open-source packages: Insights from Check Point's Head of Data Science
New Post has been published on https://thedigitalinsider.com/malicious-open-source-packages-insights-from-check-points-head-of-data-science/
Malicious open-source packages: Insights from Check Point's Head of Data Science


Ori Abramovsky is the Head of Data Science of the Developer-First group at Check Point, where he leads the development and application of machine learning models to the source code domain. With extensive experience in various machine learning types, Ori specializes in bringing AI applications to life. He is committed to bridging the gap between theory and real-world application and is passionate about harnessing the power of AI to solve complex business challenges.
In this thoughtful and incisive interview, Check Point’s Developer-First Head of Data Science, Ori Abramovsky discusses malicious open-source packages. While malicious open-source packages aren’t new, their popularity among hackers is increasing. Discover attack vectors, how malicious packages conceal their intent, and risk mitigation measures. The best prevention measure is…Read the interview to find out.
What kinds of trends are you seeing in relation to malicious open-source packages?
The main trend we’re seeing relates to the increasing sophistication and prevalence of malicious open-source packages. While registries are implementing stricter measures, such as PyPI’s recent mandate for users to adopt two-factor authentication, the advances of Large Language Models (LLMs) pose significant challenges to safeguarding against such threats. Previously, hackers needed substantial expertise in order to create malicious packages. Now, all they need is access to LLMs and to find the right prompts for them. The barriers to entry have significantly decreased.
While LLMs democratise knowledge, they also make it much easier to distribute malicious techniques. As a result, it’s fair to assume that we should anticipate an increasing volume of sophisticated attacks. Moreover, we’re already in the middle of that shift, seeing these attacks extending beyond traditional domains like NPM and PyPI, manifesting in various forms such as malicious VSCode extensions and compromised Hugging Face models. To sum it up, the accessibility of LLMs empowers malicious actors, indicating a need for heightened vigilance across all open-source domains. Exciting yet challenging times lie ahead, necessitating preparedness.
Are there specific attack types that are most popular among hackers, and if so, what are they?
Malicious open-source packages can be applied based on the stage of infection: install (as part of the install process), first use (once the package has been imported), and runtime (infection is hidden as part of some functionality and will be activated once the user will use that functionality). Install and first use attacks typically employ simpler techniques; prioritizing volume over complexity, aiming to remain undetected long enough to infect users (assuming that some users will mistakenly install them). In contrast, runtime attacks are typically more sophisticated, with hackers investing efforts in concealing their malicious intent. As a result, the attacks are harder to detect, but come with a pricier tag. They last longer and therefore have higher chances of becoming a zero-day affecting more users.
Malicious packages employ diverse methods to conceal their intent, ranging from manipulating package structures (the simpler ones will commonly include only the malicious code, the more sophisticated ones can even be an exact copy of a legit package), to employing various obfuscation techniques (from classic methods such as base64 encoding, to more advanced techniques, such as steganography). The downside of using such concealment methods can make them susceptible to detection, as many Yara detection rules specifically target these signs of obfuscation. Given the emergence of Large Language Models (LLMs), hackers have greater access to advanced techniques for hiding malicious intent and we should expect to see more sophisticated and innovative concealment methods in the future.
Hackers tend to exploit opportunities where hacking is easier or more likely, with studies indicating a preference for targeting dynamic installation flows in registries like PyPI and NPM due to their simplicity in generating attacks. While research suggests a higher prevalence of such attacks in source code languages with dynamic installation flows, the accessibility of LLMs facilitates the adaptation of these attacks to new platforms, potentially leading hackers to explore less visible domains for their malicious activities.
How can organisations mitigate the risk associated with malicious open-source packages? How can CISOs ensure protection/prevention?
The foremost strategy for organisations to mitigate the risk posed by malicious open-source packages is through education. One should not use open-source code without properly knowing its origins. Ignorance in this realm does not lead to bliss. Therefore, implementing practices such as double-checking the authenticity of packages before installation is crucial. Looking into aspects like the accuracy of package descriptions, their reputation, community engagement (such as stars and user feedback), the quality of documentation in the associated GitHub repository, and its track record of reliability is also critical. By paying attention to these details, organisations can significantly reduce the likelihood of falling victim to malicious packages.
The fundamental challenge lies in addressing the ignorance regarding the risks associated with open-source software. Many users fail to recognize the potential threats and consequently, are prone to exploring and installing new packages without adequate scrutiny. Therefore, it is incumbent upon Chief Information Security Officers (CISOs) to actively participate in the decision-making process regarding the selection and usage of open-source packages within their organisations.
Despite best efforts, mistakes can still occur. To bolster defences, organisations should implement complementary protection services designed to monitor and verify the integrity of packages being installed. These measures serve as an additional layer of defence, helping to detect and mitigate potential threats in real-time.
What role does threat intelligence play in identifying and mitigating risks related to open-source packages?
Traditionally, threat intelligence has played a crucial role in identifying and mitigating risks associated with open-source packages. Dark web forums and other underground channels were primary sources for discussing and sharing malicious code snippets. This allowed security professionals to monitor and defend against these snippets using straightforward Yara rules. Additionally, threat intelligence facilitated the identification of suspicious package owners and related GitHub repositories, aiding in the early detection of potential threats. While effective for simpler cases of malicious code, this approach may struggle to keep pace with the evolving sophistication of attacks, particularly in light of advancements like Large Language Models (LLMs).
These days, with the rise of LLMs, it’s reasonable to expect hackers to innovate new methods through which to conduct malicious activity, prioritizing novel techniques over rehashing old samples that are easily identifiable by Yara rules. Consequently, while threat intelligence remains valuable, it should be supplemented with more advanced analysis techniques to thoroughly assess the integrity of open-source packages. This combined approach ensures a comprehensive defence against emerging threats, especially within less-monitored ecosystems, where traditional threat intelligence may be less effective.
What to anticipate in the future?
The emergence of Large Language Models (LLMs) is revolutionising every aspect of the software world, including the malicious domain. From the perspective of hackers, this development’s immediate implication equates to more complicated malicious attacks, more diverse attacks and more attacks, in general (leveraging LLMs to optimise strategies). Looking forward, we should anticipate hackers trying to target the LLMs themselves, using techniques like prompt injection or by trying to attack the LLM agents. New types and domains of malicious attacks are probably about to emerge.
Looking at the malicious open-source packages domain in general, a place we should probably start watching is Github. Historically, malicious campaigns have targeted open-source registries such as PyPI and NPM, with auxiliary support from platforms like GitHub, Dropbox, and Pastebin for hosting malicious components or publishing exploited data pieces. However, as these registries adopt more stringent security measures and become increasingly monitored, hackers are likely to seek out new “dark spots” such as extensions, marketplaces, and GitHub itself. Consequently, malicious code has the potential to infiltrate EVERY open-source component we utilise, necessitating vigilance and proactive measures to safeguard against such threats.
#Accessibility#ai#Analysis#applications#approach#attention#authentication#Business#challenge#Check Point#CISOs#code#Community#complexity#comprehensive#Dark#Dark web#data#data privacy#data protection#data science#details#detection#Developer#development#documentation#domains#double#dropbox#Ecosystems
0 notes
Photo

New Post has been published on https://cryptonewsuniverse.com/online-safety-101-how-to-keep-cyber-snoopers-at-bay/
Online Safety 101 How to Keep Cyber Snoopers at Bay


Online Safety 101: How to Keep Cyber Snoopers at Bay

Have you ever paused to reflect on those emails from your bank urging you to update your information or the seemingly innocent act of connecting to your favorite coffee shop's Wi-Fi for a quick cup of joe? In the vast landscape of our digitally connected lives, have you ever entertained the thought of whether someone might be eavesdropping on your conversations?
In the contemporary world, where our daily routines intertwine seamlessly with digital communication, safeguarding the security and privacy of our online interactions has assumed a position of unparalleled significance. Alas, the challenge persists as cybercriminals continuously evolve, devising innovative methods to exploit vulnerabilities within our digital systems. Among these threats, the man-in-the-middle attack stands out as a particularly sophisticated and menacing technique, posing a substantial risk to the integrity of our digital security.
In this article, we explore the man-in-the-middle attack, unraveling its intricate workings, understanding its far-reaching implications, and, most importantly, arming ourselves with knowledge on how to shield against this pervasive cybercrime. Join us on this journey as we delve into the nuances of digital security and equip ourselves with the tools to navigate the ever-evolving landscape of cyber threats.
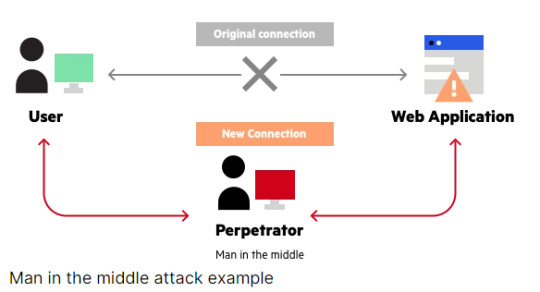
Source: Imperva.com
What is a Man-In-The-Middle Attack?
Imagine a scenario where your digital conversations aren't as private as you think; that's the unsettling reality of a man-in-the-middle (MITM) attack, a serious cybersecurity threat more pervasive than we might realize. In this digital battleground, an attacker sneaks into the communication channel between two unsuspecting parties, much like a sneaky postal worker sorting through your mail.
The term "man-in-the-middle" is fitting because, just like that rogue mailman, the attacker plants themselves right in the middle of the communication flow. It's akin to this mail mischief-maker intercepting your bank statement, jotting down your account details, and then sealing the envelope back up before it reaches your mailbox. The victim remains blissfully unaware of this intrusion.
So, why is this cyber maneuver so dangerous? Well, imagine the rogue mailman stealing not just your bank statement but also your login credentials, credit card numbers, and other personal details. That's what happens in an MITM attack. The attacker gains access to sensitive information, opening the door to identity theft, unauthorized fund transfers, and other malicious exploits.
What makes MITM attacks particularly treacherous is their stealthy nature. They can lurk undetected for long periods, silently pilfering information. It's like a silent invader setting up camp in your digital space without you even realizing it. Worse yet, these attacks can introduce malware onto your device, giving the attacker complete control over your system.
MITM attacks come in various shades, from the passive ones, where the attacker slyly intercepts user traffic, to the active ones, where the attacker actively manipulates or alters the data flow. It’s like different tactics in a cyber playbook – IP spoofing, DNS spoofing, HTTPS spoofing, and email spoofing, each with its own crafty strategy.

Source: ReadyTechGo.com
Interception
Have you ever gotten a sketchy message from an unknown number posing as your bank or an enticing email from a supposed unfamiliar angel promising a piece of his fortune? These seemingly harmless messages might just be the tip of the iceberg regarding a man-in-the-middle (MITM) attack, a favorite trick in the cyber criminal's playbook, where sensitive information is stolen from the unsuspecting victim.
So, what's the deal with interception, and how does it play into the whole MITM drama? Interception is like a digital sleight of hand with which the attacker slyly intercepts your online traffic before it reaches its intended destination. In the MITM attacks, the cyber trickster strategically positions themselves between two chit-chatting parties to either sneak a peek or slyly tweak the data passing between them.
The more straightforward and common form of MITM interception is where the attacker sets up a free Wi-Fi hotspot, maybe with a sneaky name like "CoffeeShop_FreeWiFi," and lures unsuspecting victims. Once connected, the attacker gets a backstage pass to all the victim's online data exchanges, kind of like a digital puppet master pulling the strings.
The attacker can spoof your IP and trick your computer into thinking it's hitting up a legitimate website when, in reality, it's a detour to the attacker's lair. Another move is DNS spoofing, where the attacker messes with your computer's GPS, sending it to the wrong digital address, aka their server, instead of the real deal. And who could forget HTTPS spoofing? This is like setting up a fake secure website, inviting victims to input their sensitive info, and then snatching it up like a digital pickpocket.
Email spoofing is another player in the MITM game. The attacker crafts an email that looks legit, maybe even mimicking a trustworthy source, to lull victims into a false sense of security. Once the victim bites, the attacker swoops in to nab the sensitive data. Here's the kicker: in all these cyber theatrics, the attacker stays incognito, a ghost in the machine, intercepting and manipulating data without the communicating parties having a clue. They might even drop malware on a targeted user's device, making themselves right at home.
Decryption
Alright, let's unravel the second act in the drama of a man-in-the-middle attack, which is decryption. Now that the digital trickster has nabbed the data sailing between two parties, it's time for the grand reveal. Decryption, in simple terms, is like translating a secret code back into something understandable.
In the wild landscape of a man-in-the-middle escapade, decryption is the secret sauce that turns the jumbled-up, encrypted data back into its original, readable form. Now, why is this a big deal? Well, it's the key to unlocking a treasure trove of sensitive info – think login credentials, financial details, and personally identifiable information (PII). The attacker unleashes this process to expose what was meant to be private and secure.
One classic thing the attacker does is known as the packet sniffer. A virtual detective captures and dissects the data zipping across the network. It's like intercepting letters and reading them before they reach the recipient. Sneaky, right? Then there's the brute-force attack, a cyber brute trying every password combination until it hits the jackpot. It's like trying every key in the bunch until one finally opens the door. Another trick up the attacker's sleeve is the rainbow table attack, which is a cheat sheet of pre-computed encrypted passwords, speeding up the process of finding the original password. It's the cyber equivalent of having a master key.
But why should we care about decryption? Well, if the attacker succeeds, they waltz right into sensitive information territory. This can lead to identity theft, fraud, and other malicious endeavors. Plus, decryption is like the golden ticket for installing malware on a targeted user's device, the cyber version of an uninvited guest overstaying their welcome.
Prevention
Now that we've uncovered the ins and outs of man-in-the-middle attacks and how these sneaky maneuvers go down let's arm you with the knowledge to steer clear of falling victim to them. Lucky for us, there are several effective methods to keep these digital tricksters at bay. Let's dive into some savvy ways to keep yourself in the clear:
1. Embrace the Power of VPNs:
Think of a Virtual Private Network (VPN) as your digital superhero cape. It encrypts all your internet traffic and guides it through its own secure servers. Even if an attacker tries to intercept your data, they'll just be staring at a wall of encryption. It's like sending your online messages in an unbreakable code.

Source: Markethive.com
2. HTTPS and SSL/TLS:
This dynamic duo of HTTPS and SSL/TLS transforms your internet communication into a secret language. When you visit a website using HTTPS, just like Markethive does, your browser locks arms with the website's server in a secure handshake. An attacker attempting to eavesdrop finds nothing but encrypted gibberish. It's like turning your online conversations into an encrypted treasure chest.
3. Safeguard with Email and DNS Security:
Email and DNS can be the Trojan horses of MITM attacks, but fear not! Strengthen your defenses with email security tools like SPF, DKIM, and DMARC to verify the legitimacy of your emails. For DNS, enlist the help of a secure resolver to ensure your DNS requests aren't being intercepted. It's like adding an extra layer of protection to your digital communication channels.
Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC) are email security tools that can help you protect your emails from spoofing, phishing, and spam. They work by verifying the sender’s identity and the integrity of the email content.
4. Double Down with Two-Factor Authentication (2FA):
Think of 2FA as having a bouncer at the entrance to your digital party. It requires a password and a second form of verification, like a code sent to your phone. This tag team ensures that only you get VIP access. It's like having a secret handshake for your online accounts.
5. Arm Yourself with Anti-virus Software:
Consider anti-virus software as your digital bodyguard. It scans, detects, and blocks potential threats, acting as a shield against MITM attacks. Keep it up-to-date to stay one step ahead of the cyber baddies.
6. Keep Software Updated:
Updating your software is like giving your digital fortress a fresh coat of paint. Hackers often exploit vulnerabilities in outdated software, so ensure your operating system, web browser, and other applications are rocking the latest security patches. It's like fortifying your defenses against unseen invaders.
It's essential you understand that by weaving these prevention methods into your digital routine, you significantly reduce the risk of becoming a victim of a man-in-the-middle attack. Remember, an ounce of prevention is worth a pound of cure. So, gear up, stay vigilant, and keep the online baddies at bay!
Detecting a Man-In-The-Middle Attack
Detecting a man-in-the-middle attack can be subtle, but it’s important to stay alert. The first sign something’s off will likely be a slowdown in internet or network speed. If you notice it taking longer than usual to load pages, watch out; you might be under attack. The next sign is a pop-up error message. These error messages can appear for several reasons, but if the error message says, “The security certificate presented by this website is not secure,” that’s a red flag. An improper security certificate is a definite sign that the website is not secure and may have been compromised.
Network Monitoring is essential in detecting a man-in-the-middle attack. Network monitoring tools come in various shapes and sizes. They keep track of network traffic, identify traffic patterns, and check for suspicious behavior. SSL Certificate Warnings are some of the most common ways web browsers detect a Man-in-the-Middle Attack.
When attempting to visit a website with an invalid certificate, the browser warns its user of its dangers, often citing the risk of middleman attacks. Suspicious Network Activity is another sign. If your network administrator or ISP has monitoring tools in place, unusual network activity can quickly raise a red flag. DNS Spoofing Detection Tools can help detect DNS hijacking and monitor suspicious activity on your network.
It's always best to have multiple lines of defense when trying to detect a man-in-the-middle attack. Using a combination of techniques and tools is key to recognizing suspicious activity before it's too late. Remember, prevention is always the best defense. Staying vigilant and using the preventive measures outlined in the previous section is vital.
Examples of Man-In-The-Middle Attacks
As you might have figured out by now, man-in-the-middle (MITM) attacks are pretty dangerous. They are used to steal sensitive information from various targets, including users of financial applications, e-commerce sites, and SaaS businesses. Such attacks can also gain entry into a secure network by installing malware on a user's device.
But let's dive deeper and look at some real-life instances of man-in-the-middle attacks that have occurred. In 2010, an Iranian hacker used a man-in-the-middle attack to access the Gmail accounts of several high-profile individuals, including US government officials and journalists. The attacker created a fraudulent security certificate for Google services, which allowed them to intercept email communication.
DigiNotar, a Dutch certificate authority that the hacker compromised, issued the security certificate. The hacker bypassed the HTTPS encryption that usually protects the communication between a user and a website. The hacker also used a technique called DNS spoofing, which involves changing the DNS records of a domain name to point to a malicious server. This way, the hacker could redirect the users to a fake Google website that looked identical to the real one but was under the hacker’s control.
In 2011, at a Black Hat conference, a researcher named Nicholas Percoco and his colleague Christian Papathanasiou showed how easy it was to run a man-in-the-middle attack on mobile devices running iOS and Android. The attack involved intercepting data packets between a mobile device and a wireless access point using a tool called SSLstrip.
SSLstrip is a tool that can downgrade HTTPS connections to HTTP connections and strip away the encryption that normally protects the communication between a user and a website. The tool can also modify the content of the web pages that the user sees, such as replacing the padlock icon with a fake one or inserting malicious links or scripts.
The researchers demonstrated how they could use SSLstrip to hijack a user’s Facebook session, steal their login credentials, and post messages on their behalf. They also showed how to intercept a user’s email communication, read their messages, and send spoofed emails. They also revealed how to access a user’s online banking account, view their balance, and transfer money to another account.
One of the most widespread man-in-the-middle attacks in recent times is the "Superfish" incident. Lenovo shipped its laptops with adware called "Superfish," designed to serve targeted ads to users. However, Superfish was designed to intercept HTTPS traffic, leaving users vulnerable to MITM attacks.
Another example of a widespread MITM attack is the WannaCry ransomware attack that took place in 2017. The WannaCry ransomware was propagated via a vulnerability in Windows systems and encrypted users' files, demanding a ransom for decryption. This sophisticated ransomware attack attacked several government agencies, businesses, and individuals worldwide.
While most man-in-the-middle attacks aim to steal user data, some use MITM attacks to target companies and individuals. For instance, during the Syrian civil war, the SEA (Syrian Electronic Army) carried out a targeted MITM attack against the Associated Press (AP) Twitter account. The SEA used the account to post fake news about an explosion at the White House, causing a significant drop in the stock market. While man-in-the-middle attacks might not be new, the stakes are increasing with new technologies such as Artificial Intelligence. So, it's crucial that you stay informed of such attacks and take the necessary precautions to protect your data.

Source: Cyber Security News
Security analysts discovered one recent incident of an MITM attack in April 2023. The attack targeted Wi-Fi networks and could bypass their security mechanisms. The attacker operated by imitating the genuine access point and transmitting a forged Internet Control Message Protocol (ICMP) to redirect the message to a targeted supplier. ICMP is a protocol used to send error messages and other information between network devices.
A redirect message is an ICMP message that tells a device to use a different route to reach a destination. By sending a forged redirect message, the attacker could trick the device into sending its traffic through a malicious router, where the attacker could intercept and modify it. This way, the attacker could hijack any device's traffic connected to the Wi-Fi network and perform various malicious activities, such as stealing passwords, injecting ads, or redirecting users to phishing websites.
Conclusion
So, we know these attacks are dangerous and can happen to anyone, anywhere, at any time. From intercepting personal information to potentially installing malware, cybercriminals will stop at nothing to get what they want, which is why it's so important to be aware of the risks posed by man-in-the-middle attacks.
We've gone over a few key steps to prevent becoming a victim, like using a VPN, HTTPS, SSL/TLS, email and DNS security, and two-factor authentication. It's also essential to keep your software up-to-date and be aware of suspicious network activity. But even with these precautions, it's not always possible to avoid a man-in-the-middle attack, so it's important to know how to detect one if it does happen.
Whether it's noticing strange SSL certificate warnings or monitoring network activity, early detection can be the difference between a minor inconvenience and a major data breach. And while it's easy to feel overwhelmed by the thought of cybercriminals lurking around every corner, being aware of the risks posed by man-in-the-middle attacks is the first step toward protecting yourself.
Remember, attacks like these can happen to anyone. Still, you can minimize your risk and stay safe in an increasingly dangerous digital world by remaining vigilant and taking the necessary precautions. So, whether you're shopping online, checking your bank account, or browsing the web, remember to stay alert, stay safe, and watch for those pesky man-in-the-middle attacks. After all, when it comes to online security, a little awareness can go a long way to save you from disaster.


About: Prince Ibenne. (Nigeria) Prince is passionate about helping people understand the crypto-verse through his easily digestible articles. He is an enthusiastic supporter of blockchain technology and cryptocurrency. Find me at my Markethive Profile Page | My Twitter Account | and my LinkedIn Profile.
0 notes
Text
Skyrocket Your Amazon Sales Via An Expert Amazon Marketer: 5 Key Factors
In the continually evolving realm of e-commerce, Amazon reigns as a powerhouse, a platform where rivalry is vigorous and visibility is key to success. As a entrepreneur, traversing the nuances of this digital domain can be formidable, and that's specifically where an best Amazon CPC agency Advertising Agency becomes important. These professional agencies offer proficiency, capabilities, and approaches customized to improve your presence and performance on Amazon. Here are the top five rationales why working with an Amazon Advertising Agency is an crucial move for your organization:
Skill in Amazon's Distinct Platform:
Amazon is not merely another digital marketplace; it's an community with its own distinct set of of rules, calculations, and customer patterns. Amazon Advertising Agencies possess a deep knowledge of this distinct setting and are armed with the strategies to get your products stand out. They know how to improve product listings for Amazon's A9 algorithm, strategize bids for Amazon ads, and generate content that converts browsing potential customers into buying customers.
Admission to Sophisticated Tools and Data analysis:
Achievement on Amazon is fueled by data. Amazon Advertising Agencies possess access to advanced tools and analytic reports that provide precious perspectives into market tendencies, competitive review, and customer behavior. This data-based method permits for more specific advertising initiatives, more intelligent spending budget assignment, and a much better understanding of what propels sales conversions and income.
Time period and Resourcefulness Productivity:
Controlling your enterprise, specially in the vibrant planet of e-commerce, requires juggling various duties. By delegating the advertising element to the experts, you can focus your attention on other facets of your company, like item progress, customer help, and functions. The agency manages your Amazon appearance, assuming the time-consuming tasks of search term study, campaign assessment, and ad production and improvement.
Company Protection and Enhanced Visibility:
On a crowded program like Amazon, safeguarding your brand name's reputation and ensuring that its presence are vital. Amazon Advertising Agencies observe your brand's health, combat counterfeit products, and manage consumer testimonials and queries. They also use techniques to increase your brand's presence through efficient advertising, ensuring your goods show up where they subject the most.
Scalability and Versatility:
As your enterprise expands, so do its wants. Amazon Advertising Agencies are set up to take care of this development, providing scalable solutions that adapt to your organization's developing requirements. They stay abreast of changes in Amazon's plans, marketplace movements, and advertising and marketing tools, making certain your marketing methods rotate as needed for sustained expansion and good results.
0 notes
Text
Amazon Ad Consultants: Five Essential Reasons Necessitating An Amazon Advertising Agency To Elevate.
In the ever-expanding realm of e-commerce, Amazon reigns as a giant, a platform where competitiveness is cutthroat and recognition is key to prosperity. As a company owner, navigating the nuances of this digital arena can be intimidating, and that's exactly where an Amazon Advertising Agency enters the picture. These specialized agencies bring to the table skills, assets, and strategies customized to elevate your visibility and productivity on Amazon. Here are the top five rationales why working with an Amazon Advertising Agency is an indispensable move for your organization:
Skill in Amazon PPC cost's Exclusive Platform:
Amazon is not just another digital venue; it's an environment with its own unique collection of rules, formulas, and customer behaviour. Amazon Advertising Agencies maintain a intense knowledge of this unusual arena and are armed with the tactics to make products get noticed. They recognize how to improve product listings for Amazon's A9 system, formulate strategies for bids for Amazon ads, and generate content that changes scanning prospects into buying customers.
Accessibility to Sophisticated Instruments and Analytics:
Achievement on Amazon is powered by information. Amazon Advertising Agencies are equipped with approach to advanced tools and analytic reports that supply precious perspectives into sector developments, competitive analysis, and consumer conduct. This data-driven approach permits for more targeted advertising initiatives, smarter budget allocation, and a much better comprehension of what propels sales conversions and sales.
Time and Resource Effectiveness:
Controlling your enterprise, specially in the active globe of e-commerce, demands managing different tasks. By handing over the advertising factor to the specialists, you can focus on additional aspects of your enterprise, like product advancement, consumer help, and procedures. The agency handles your Amazon appearance, assuming the time-consuming chores of keyword research, campaign analysis, and commercial production and optimisation.
Brand Protection and Enhanced Awareness:
On a crowded system like Amazon, protecting your company's status and ensuring that its presence are crucial. Amazon Advertising Agencies monitor your brand's overall health, combat fake merchandise, and handle customer opinions and inquiries. They also employ tactics to boost your company's presence through successful advertising, guaranteeing your products emerge where they make a difference most.
Scalability and Adaptability:
As your organization grows and expands, so do its wants. Amazon Advertising Agencies are set up to deal with this progress, giving scalable solutions that modify to your business's developing requirements. They stay up to date of modifications in Amazon's plans, sector tendencies, and advertising methods, ensuring your marketing methods rotate as necessary for sustained development and good results.
1 note
·
View note