#received transmission ✨
Note
trick or treat!!!! + weather report >w<
Cold Hands from Cozy Autumn Prompts

There was something that really warmed your heart on the days when Weather took your hands in his. He stared into your eyes as he held your hands in his, you couldn't help but notice how his hands completely covered yours when he cupped his over yours. It was comforting... It made you feel safe and warm.
You watched as he made an opening between his cupped hands to gently blow warm air into the space to warm your hands up. He rubbed his hands against yours, you could especially feel the way his thumbs rubbed against the back of your hands as he did so.
You watched Weather's movements carefully... You were in awe of everything he did. He was just an interesting person to watch. There was something about his movements that seemed too perfect, or maybe it was because you were so enamored with him. Either way you tilted your head to the side a bit to get a better look at his eyes as he continued to attempt to warm up your cold hands.
"Better." Weather finally spoke up again as he gently rubbed your hands a bit more before bringing your hands up to his lips and gently kissing them.
"Thank you. I feel much warmer now." You said with a smile. Not only were your hands warmer, but your entire body felt much warmer too.
"I would've told you to wear mittens, but I prefer warming your hands this way." Weather admitted with a small smile.
It always caught you off guard when he said sweet little things like this. You couldn't help but lean against him a bit, wanting to feel more of his warmth against you.
"I prefer it when you warm my hands this way too."
12 notes
·
View notes
Text
tag dump !
#i am zim! ; ooc ✨#i am the allspark ; ic ✨#judgement day's not coming soon enough ; musings ✨#wings and weaponry ; aesthetics ✨#megatron has fallen ; psa ✨#youve failed me for the last time starscream ; crack ✨#follow the leader ; memes ✨#ask and you shall receive ; ask memes ✨#worthy opponents ; promos ✨#the best of the worst ; self promo ✨#the judge ; self ✨#status report ; ic status ✨#dash comm ✨#incoming transmission ; asnwered ✨
0 notes
Text
Watch It | Lee Sangyeon

SUMMARY: you were summoned to stop the crime spree of the renowned group The Boyz by hacking into one of the systems to retrieve information about a specified location before it's too late. what you did not expect was that their leader has been spying on every move you make from the shadows and eventually confronting you about it, which then turns into your biggest nightmare.
PAIRING: criminal Sangyeon x hacker f!reader
GENRE: smut (18+ MDNI!!)
WARNINGS: kissing, petnames (sweetheart, baby, princess), mentions about violence/illegal business (stealing), size kink, voyeurism, dirty talk, public sex, rough sex, fingering, handjob, p in v sex, unprotected sex, they went for rounds, mean dom! Sangyeon
WORD COUNT: 3,235
A/N: let me explain. it was the ✨stare✨ from the concept pic itself that gave me ideas for this fic 😭 huge thanks to my bubba @juyeonszn for beta reading this & convincing me to change my theme ily forever 🥺💜 also shoutout to @daisyvisions @snowflakewhispers for fueling me with ideas / validating my horniness oops— (but ily both so much 😘)

“Agent Y/N, are you in position?”
“Yes, sir. I am waiting for the right moment to jump into the enemy’s territory.”
With one click on the earpiece, you immediately turned off the buzzing sound from the headquarters as you needed to focus and ensure that you were all alone and secure as you entered the place of interest.
As you flung your backpack onto your back, you quietly peeked through the few trucks parked in the parking lot right outside the abandoned building. Given that your job was to hack into the system and you needed good internet service, conducting it outdoors would be much more ideal than inside the building itself.
You and your team received a transmission hours ago about how this group of individuals has been conducting illegal business, such as stealing information from multiple laboratories—specifically ones located on the outskirts of Seoul to avoid detection and arrest. According to your team’s analysts, they have also discovered how they had been stealing chemical solutions that were pretty much hazardous to the public, and god knows whatever they will be using them for.
In other words, they are a pretty suspicious gang, and someone has to look into their spree of crimes before things get out of control. Being one of the best hackers on the team, you were sent to the actual location to hack into their system as best as you could.
So here you were, in the depths of the night, staking out the parking lot alone, hoping that all goes well and that you can quickly do the job and get out of there as soon as possible. Frankly, it all felt super eerie, especially when it was this late at night, and there weren’t many street lamps to provide enough light to make you feel safe by yourself.
After looking thoroughly and confirming with your eyes that you were alone, you slowly moved towards the multiple trucks parked in the middle of the parking lot. You managed to squeeze yourself through them and get to a well-lit area; that was when you finally took your laptop out of your backpack and started hacking away.
To the best of your abilities, you were able to sneak into the laboratory’s system fairly quickly, and you ran over their live security camera footage to check if the criminals were within the building. Immediately, the security camera footage popped up on the screen, and you could quickly identify several men scattered throughout the different labs within the facility.
“They were probably looking for the right chemical, " you thought, as they were all split up and divided into three groups in each laboratory. While they were trying to find the liquid, you had to quickly hack into the database to retrieve all of the information regarding the facility and the chemicals produced over the years and quickly send them back to your headquarters for analysis.
After about 10 minutes of transferring all of the files, it was time for you to get out of there and return to let the other agents that were on their way to take over and confront the criminals themselves. You weren’t a field agent, so you couldn’t do much physical combat against the criminals themselves. As much as you wanted to, you weren’t ready for your title as an agent to be stripped off you anytime soon; hence respecting the laws and just doing as you were told would be the wisest decision for now.
You quickly phoned the headquarters, letting them know you had retrieved all the necessary documents and would finally return to report. As you were permitted to do so, you got up and were going to keep all of your belongings back in your backpack until one of the security cameras began flashing.
You quickly got back down again, trying to see what was happening. That was when you remembered a crucial detail.
According to the information you guys have had so far, you knew that the group of criminals consisted of 11 members, so you decided to do a headcount one by one on the screen, starting from 1 to 11.
“8…9…and 10.”
10?
Someone was missing, but who?
Just then, a deep husky voice broke you off from your attention on the screen, and you looked around to see where it was coming from. Finally, you landed your eyes towards one of the vehicles right across you, and there he was—one of the criminals sitting right on top of the truck with both his legs spread wide apart, looking down towards you.
“Aren’t you pretty good at your job, sweetheart?”
Oh no. You were busted.
“U-umm…sorry…it’s just that…I was supposed to write a report regarding this facility, so I am here to look around.”
“At this hour? Close to midnight? I highly doubt that, princess.”
Immediately, he hopped down from the vehicle in one swift movement and began approaching you slowly. You instinctively shut your laptop, hugged it close to your chest, and backed away.
“I-I’m sorry! It seems I came at the wrong time! I will take my leave now, then. I’m sorry to have disrupted you!” You bowed down profusely before turning your heel and tried to run as quickly as you could until he grabbed your wrist and pulled it upwards, turning back in his direction.
There was this smug yet dangerous look on his face, contradicting the pure and innocent look he had on before. That sent a chill up your spine, and you quickly gulped before he slowly pushed you till your back finally hit against one of the trucks. You closed your eyes upon the impact and elicited a quiet yelp with his movement.
Suddenly, you felt his fingers lift your chin, and he commanded you to open your eyes to look straight at him.
“Now sweetheart, we weren’t done having our little fun conversation yet, were we? It breaks my heart that you decided to take off running before we even started.”
You were panicking as his grip slightly tightened around your wrist, pushing it back against the truck, signalling that you would be dead meat if you tried something funny again next time. You were stuck, and there was no way you could ring the headquarters as that would blow up your cover and the location of the base of operations.
The only thing you could do was to pray that the field agents would make their way over to you soon until you heard a mild static and a voice calling through the earpiece.
“T-there isn’t much ser-service here, b-but we will be sli-slightly late d-due to the he-heavy traffic. H-hang in t-there, a-agent Y/N! W-we’ll surely be c-coming—”
And then it all went silent.
Your only hope was lost, as the enemy threatened and pinned you with little to no help coming your way anytime soon. You could use your physical combat skills to fight against the man before you, but something in your gut told you that it would be a horrible idea to try anything funny with him right now.
With that, you could only take a deep breath and try to talk things out with him for a bit, stalling some time before help eventually arrived.
“W-what…what do you want from me?” You questioned, or more like stammered. It was clear that you were trembling in your voice.
The man chuckles slightly as he smiles back at you. “See, sweetheart. I’m afraid I can’t let you off that easily, knowing that you were spying on us and retrieving crucial evidence and information that would hinder our mission.”
This time, his fingers on your chin slowly travelled down to your neck and chest. It was the way he took his time gently sliding his finger down and touching your bare skin that made you let out a gasp.
“I’d like to play a little game with you, princess.”
“W-what do you…” You were beginning to lose your mind as he brushed his fingers across your lips, smudging the lipstick that you’d put on prior.
“I’d like to see how much you can handle, and trust me, we will have so much fun. I’ll make sure that you won’t be heading back to your headquarters anytime soon.”
Within seconds after that last sentence, he crashed his lips with yours and began savouring them as a tingling sensation ran through your body. He quickly deepened the kiss, his lips moving against yours with urgency.
It was wrong. This was all so wrong.
You knew how bad this situation was because he was your enemy. But then, something about his lips made you crave more. His kisses tasted like honey, and the way he moved his lips against yours drove you insane.
Without you knowing, your grip against the laptop slowly loosened, and eventually, he took it away from you and gently placed it on the ground, his hands quickly moving back up to your cargo pants, rubbing the spot in between your thighs, earning a gasp from you.
He smiled as you gave him the reaction that he wanted, and he began to untie your pants before pulling them down, his fingers now brushing over your sensitive spot through the lace underwear that you were wearing. Slowly, he began to feel that you were starting to get wet, and that was his cue to hook his finger under the seam of your underwear before pulling them down, revealing your now wet clit all exposed.
You hissed as the cold air from the atmosphere came in contact with your clit, and it took the enemy a moment to reconnect his fingers to your wet sensitive spot, rubbing it again before slowly inserting two fingers into you.
“Aah…aaah…”
“I’ll be a dear and tell you my name, princess. Call me Sangyeon, moan for me,” he leaned towards you and whispered.
“S-sangyeon….”
“That’s it, baby. You’re doing so good for me. I shall grant you your next reward now, hmm?”
As he removed his fingers from your clit, he quickly moved them to his pants, unzipped and shoved them down rather hastily. It was the way you immediately noticed the erection through his boxers, and your eyes widened from just that alone. Sangyeon smirked at your reaction and reconnected his lips to yours to give you a few pecks.
“Look at you already can’t stop staring at my big cock. Oh, baby. I’ll make sure that you won’t regret playing with it.”
Immediately, he grabbed your free hand and guided you to touch his erection. You gasped from that alone while Sangyeon let out a soft groan. You couldn’t help but naturally start rubbing his tip, which made Sangyeon moan for you.
“Touch me, baby.” He commanded.
Guiding your hands again, he allowed you to pull his boxers down, and your mouth watered at the sight of his massive bulge. You wrapped your hands around his cock before you began gliding your hands up and down his member. In return, he inserted his fingers back into your clit once again, and the both of you were now a moaning mess.
“S-sangyeon…kiss me…please…” you whined, wanting to taste his sweet honey-like lips once again.
“Oh, honey. You love the way my tongue twirls around yours?”
“Y-yes…very much…aaahh—”
Just like that, he was now back to kissing you breathless. As his tongue slid into your mouth, he began sucking your tongue, and you shut your eyes tightly from the sensation. It made you forget entirely about how you were supposed to escape this guy as soon as possible, trying to find a potential hideout place to wait for your fellow agents.
It seemed as if Sangyeon had wrapped you around his fingertips, just as he had planned to, and he would make sure that you wouldn’t be leaving this place anytime soon. He would proceed to the next step of his plan anytime now.
He gently removed your hands away from his bulge as he took it himself to align the tip towards your entrance, and you knew that you were in big trouble. Now, you tried to move forward when his hand, still grabbing your wrist, tightened again and pushed it back towards the truck again.
“Oh no, princess. We’re just getting started. Stay here with me, and I’ll give you the best fucking sex you’ll ever have.”
As soon as those words slipped out of his mouth, he immediately slid himself into you, and you all but screamed, a teardrop falling from the corners of your eyes. Sangyeon didn’t even give you enough time to adjust to his huge size fully and eventually began slamming into you hard.
“Fuck—fuck.” It was all that you could’ve said because you had already lost your mind ever since he kissed you for the first time. Now that he was within you? Oh, you were far, long gone from reality.
Given the way he was fucking you so hard, even the truck that you were leaning against began rocking back and forth following your pace.
Your eyes watered as he hit every single spot within you, causing you to cry out loud. If you were to be honest, it actually did hurt, especially which such a large and hard dick like his. But the pleasure far exceeded the pain, and you cried out for more.
“Sangyeon…sangyeon…”
“Tell me what exactly you want, baby.”
“Keep it going…please…”
“Just like that? Are you sure that is enough?”
“I…want you to fuck me faster and harder—”
“Anything else?” He was now picking up the pace, and it was visible that his chest was rising up and down much quicker than before as he tried his best to catch his breath.
“I…want you to fuck me till my legs feel numb, give me more and more…aaah—”
“That is what exactly I like to hear, sweetheart.”
As he slammed into you hard, you felt a tight knot form around your stomach, signalling that you were about to reach your high and cum. Sangyeon noticed your demeanour as you buckled your hips and spread your legs wider for him to gain more access to you.
“I’m cumming! I’m cumming!” You screamed.
“Do it, baby. Cum all over my cock, I want you to be dripping wet just for me.” He growled.
With a few more pushes, you eventually released and spilled all of your juices all around his cock, so much so that it was oozing out of you, and it all splattered on the ground.
You breathe in heavily before Sangyeon gives you a gentle kiss on the lips, reassuring you that you have done so well for him.
“That’s it, princess. What a good girl you’ve been. But unfortunately, there is more to come baby.”
He grabbed both of your shoulders before turning you around rather aggressively, so now you were facing the truck instead. If you were to be honest, that rough act of his turned you on more than it was painful. It was a few seconds before you felt his grip return to you on both sides of your hips, as you felt his cock rubbing up and down once again on your dripping wet clit.
Sangyeon leaned forward to whisper in your ear, sending you a chill down your spine. “Give me some more, baby. You know you can do it.”
As he pushed his cock back into you, an immense moan spilt out from your mouth as he began pounding into you again. You had already had sex and felt his member all around you just a minute prior, yet you were still struggling to adjust to his bulge.
“God, sweetheart. I’ve already fucked you hard, and yet you’re still so tight. I guess I wasn’t rough enough.”
As he pounds into you, your hands that were pressed against the truck begin pushing the vehicle once again. If only there were someone around, you swear to god that the car's movement would be more than enough to prove that something wasn’t right and that there were people everywhere in the empty parking lot.
But your comrades are still nowhere to be seen, and you were still bounded by the criminal himself, fucking you till you were sore to the point that you would not be able to walk on your own after this.
“S-sangyeon…I-I wanna cum again for you so badly…” You whimpered.
This time, he moved one of his hands up to grab a chunk of your hair and pulled it back; that firm sudden grip caused you to scream once again for him.
“Do it then. Cum with me this time.” He commanded, pulling your hair and pounding into you even harder.
“Fuck—fuck—fuck—Sangyeon!! I’m cumming!!”
With one final hard thrust, both of you released your liquids before slowing down the momentum and catching your breaths together. He removed his grip from your hair before he grabbed your chin and turned your head back for him to kiss you again. You snaked your hands up to his neck to return the favour.
Just then, you heard sirens coming from afar, and you heard static in your earpiece again.
“Agent Y/N, please respond! We’re finally here to infiltrate the facility; please head out, return to the back of our vehicle, and stay put!”
It was your cue to leave now, and there was no more extended point in you staying here.
You gulped before you pulled away from Sangyeon, mustering up the courage to reject him for good this time.
“S-sangyeon…I have to go…I can’t stay here any more.” You stammered, hoping that he would finally let you leave this time, especially since he had already gotten what he wanted.
But you should’ve known better because his familiar dark and dangerous look was plastered on his face again, and he pushed you back against the truck.
“You know, now that your comrades are here, I’m afraid there’s more reason for me not to let you leave now, hmm? I’ve been stalling time for my boys to get what they want in the facility before your agents arrive to ruin our plan. While they were doing that, I was out here guarding the area, making sure nobody was to sabotage our plan.”
So that was why he played this little dirty game with you.
“Knowing my boys, I’m pretty sure that they have gotten everything we need, and all they have to do is defeat your fellow agents, and then we will leave. And while they are doing that, you will keep me company until they’re done.” He threatened.
This time, he grabbed your wrist and dragged you towards the front of the car, directly where you could see clearly how your fellow agents were confronting the criminals. Within seconds, a fight has broken out between them across the facility, and you have no choice but to stay here helplessly and be unable to provide them with any aid.
Before you could say anything, Sangyeon yanked you down towards the hood of the car so that you were lying on top of it, and he prepared to go for a third round with you.
“I want you to watch closely with how you and your fellow agents are going to fail this mission terribly while I fuck you real good till you’re begging for more.”

masterlist
taglist: @deoboyznet @kflixnet @flwoie @heemingyu @snowflakewhispers (join my permenant taglist here!)
#deoboyznet#k-vanity#k-labels#kflixnet#the boyz#tbz#the boyz x reader#tbz x reader#the boyz imagines#the boyz scenarios#the boyz fanfic#tbz scenarios#tbz fanfic#lee sangyeon#lee sangyeon x reader#lee sangyeon smut#sangyeon smut#the boyz smut#tbz smut#sangyeon imagines#sangyeon scenarios
294 notes
·
View notes
Text
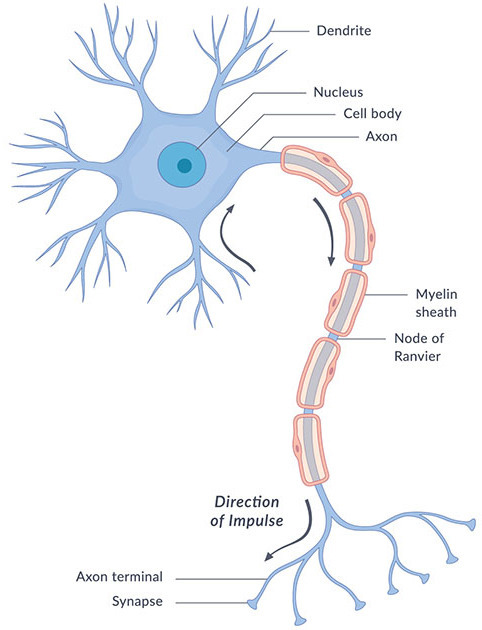
Unraveling the Wonders of the Neuron and Brain (Part 1)
Hey there, Tumblr fam! Today, let's dive deep into the intricate world of neurons and the brain. 🧠✨
Anatomy of a Neuron
Neurons are the building blocks of the nervous system, responsible for transmitting information throughout your body. They have a unique structure, consisting of three main parts:
Cell Body (Soma): This is like the neuron's control center. It contains the nucleus, which houses the cell's DNA and controls its activities.
Dendrites: These branch-like extensions protruding from the cell body are the neuron's antennae. They receive signals from other neurons or sensory receptors, transmitting these signals to the cell body.
Axon: Think of the axon as the neuron's transmission line. It's a long, slender, cable-like structure that carries signals away from the cell body, toward other neurons or target cells.
At the end of the axon, you'll find axon terminals, where neurotransmitters are released to communicate with the next neuron or target cell.
Physiology of a Neuron
Neurons are all about transmitting information through electrical impulses and chemical signals. Here's a quick rundown:
Resting Membrane Potential: Neurons have a resting state where the inside is negatively charged compared to the outside due to the uneven distribution of ions (like sodium and potassium) across the cell membrane. This creates a potential difference called the resting membrane potential.
Action Potential: When a neuron receives a strong enough signal (usually from dendrites), it can generate an action potential—a rapid change in membrane potential. This electrical signal travels down the axon like a wave.
Synaptic Transmission: When the action potential reaches the axon terminals, it triggers the release of neurotransmitters into the synapse, the tiny gap between neurons. These chemicals bind to receptors on the next neuron, initiating a new electrical signal.
The Marvelous Brain
Now, let's shift our focus to the brain—the command center of your entire nervous system. 🌟
Your brain consists of various regions, each with specific functions. Here are a few key areas:
Cerebrum: This is the largest part and is divided into two hemispheres, each responsible for various cognitive functions like thinking, memory, and sensory perception.
Cerebellum: Located at the back of your brain, it plays a crucial role in balance, coordination, and fine motor skills.
Brainstem: Situated at the base of the brain, it controls basic life-sustaining functions like breathing and heart rate.
Hippocampus: Essential for memory formation and storage.
Amygdala: Involved in processing emotions and emotional memories.
And there's so much more to explore!
References:
Bear, M. F., Connors, B. W., & Paradiso, M. A. (2016). "Neuroscience: Exploring the Brain." Lippincott Williams & Wilkins.
Purves, D., et al. (2017). "Neuroscience." Sinauer Associates, Inc.
Kandel, E. R., Schwartz, J. H., & Jessell, T. M. (2012). "Principles of Neural Science." McGraw-Hill Education.
These references will provide you with in-depth insights into the fascinating world of neurons and the brain. Remember, your brain is a universe waiting to be explored! 🌌💡🔬
Stay curious, Tumblr pals! 😊🧠

#neuroscience#biology#science#college#education#school#student#medicine#doctors#health#healthcare#neurology#brains#psychology#psychiatry
155 notes
·
View notes
Note
What is the origin of how Janus got his cat? (Did they have to go through a bonding arc like Hiccup and Toothless from how to train your dragon?)
it was time for the ✨Cat distribution system✨
Tiramisu was discovered by Coriolanus as a kitten at the end of a date night with Lucy Gray. Despite his attempts to shoo away the lively creature Like a true gentleman, Lucy Gray intervened and picked it up. Holding it with the pure bliss of excitement and awe.
Upon finding the stray kitten, she made the decision to bring it home despite her husband's objections. She believed the kitten would make a wonderful companion for six-year-old Janus. However, Coriolanus remained unconvinced and prohibited Lucy Gray from allowing the stray near their son until it had been examined by a veterinarian, fearing the risk of illness or disease transmission.
On the 4th of July, a few weeks after Janus received Tiramisu as the best birthday gift in his opinion thanking his parents excitedly.
There was a bonding arc but it wasn't Janus and Tiramisu XD Lucy Gray had to make sure that Tiramisu and Coriolanus went along.
______
Little fact, Tiramisu slept for a while in Coriolanus and Lucy Gray's bedroom with Janus in between them. Wherever little Sejanus went the cat followed. Coriolanus wasn't having it-
#tbosas#snowbaird#lucy gray baird#coriolanus snow#coriolanus: Lucy Gray NO-#Lucy gray: Lucy Gray YES!#Xanthos was still boring and sleeping way to much for Janus liking#Tiramisu was a feisty one#but only with Coriolanus#alternate universe#CapitolAU#the hunger games#hunger games#thg#the ballad of songbirds and snakes
31 notes
·
View notes
Text

THE 5:5 ENERGY PORTAL ✨ MAY 5, 2024
Dear friends, on Sunday May 5 we will be passing through a special energetic resonance: the 5:5 gateway. With all the intense current solar winds still moving around us, the energy of this portal may actually feel more intense to some of you, specially if are energy sensitive.
The vibrations of this particular 5:5 portal resonate with all the attributes of number/s 5 and 55. Similarly to the single number 5, 55 brings with it an energy of independence, and a need to freely explore new areas of our human multidimensional experience. We have five physical senses—sight, smell, hearing, touch, and taste— to experience the physical world. We also have five fingers on each hand and five toes on each foot. Number 5 also connects us with the five universal elements that support our human existence on Earth: air, fire, earth, water, and space/ether/spirit. Along similar lines, number 5 is connected with the five “Platonic solids”, known to be the basic energetic templates supporting physicality on Earth.
When our awareness and consciousness focuses on the vibratory essence of the 5:5 energy portal, this connection gives us an energetic momentum for our exploratory journey ahead. The frequencies of 55 are outward looking, forward looking, triggering our desires and anticipation of new experiences and new learning. This type of energy feels adventurous, self-sufficient, and ready for step out of the comfort zone.
The number 55 renders the foundation number 1 (5+5=10=1). Therefore, the 5:5 portal energy contains both, a dose of 1 energy as in independence, initiative, and self-sufficiency, plus a dose of 5 energy leading to the expression of a self-perceived sense of freedom, versatility, and sensuality. Imagine being truly self-sufficient and independent with the freedom to do and explore and experience anything and everything you are curious about. This is what the 5:5 portal is showering us with: the infinite possibilities of outer and inner exploration and discovery.
However, if there are any limiting barriers preventing you from reaching your desired level of freedom and forward movement, the 5:5 lightcodes will be showing you exactly what these issues or situations are. You may be faced with a few conscious or unconscious uncomfortable truths at this time. Are there any situations stopping you from moving forward with your desired path? Are these limitations external or are they being self-generated? Am I engaging in a few self-sabotaging behaviors? Are there any fears that prevent me from leaving my own cocoon and expand myself? The evolutionary journey never stops, and cosmic evolution is both a teaching and a learning process. And these 5:5 energy codes are here to show you exactly this.
You may want to work with the “Releasing Emotional Fears” activation found in level II of the 3D to 5D Library as we absorb the 5:5 lightcodes this weekend. This activation will begin untangling the energetic pathways that keep sustaining our fears and preventing us from evolving into our full human potential. Please keep a journal next to you to write down any insights during this transmission:
As I mentioned earlier, solar activity will stay at moderate levels throughout this weekend so please listen to your body and give it the rest it needs. We are still processing a lot of solar information we have received on the last few days with the X flare. Some mild headaches, fatigue, ear ringing, chest pressure, and lack of concentration, may be felt as our energy fields continue recalibrating. We are healing and clearing old memories, be loving to your Self at this time.
The 5:5 portal energies will be also working on our energy fields for a few days afterwards. Do pay attention to any dreams or insights you may receive as they will be signs guiding you to a more expansive and freer way of being. Set your intentions, allow yourself to be flexible, and release old structures that are preventing you from moving forward in your cosmic journey of exploration. The time for change and new discoveries is here. Have a great weekend! Much love!
WE ARE ONE ♡
Diego E. Berman 2024 Ⓒ
www.diegoberman.com
20 notes
·
View notes
Text
does cisco anyconnect vpn client use port 2000
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does cisco anyconnect vpn client use port 2000
Cisco AnyConnect VPN client port usage
The Cisco AnyConnect VPN client is a popular solution for remote access to corporate networks, allowing users to securely connect to their organization's resources from anywhere in the world. One important aspect to consider when deploying the AnyConnect client is its port usage.
The AnyConnect VPN client uses various ports for different functions to ensure secure and efficient communication between the client and the VPN server. By default, the client uses SSL (Secure Sockets Layer) for encryption and communication over port 443, commonly used for HTTPS traffic. This port is preferred for its compatibility with most network configurations and its ability to bypass restrictive firewalls that may block other ports.
Additionally, the AnyConnect client can utilize port 443 for DTLS (Datagram Transport Layer Security) connections, which offer lower latency and improved performance, particularly in situations where network conditions may cause packet loss. DTLS is especially beneficial for real-time applications like video conferencing or VoIP calls over the VPN.
For administrators managing the AnyConnect VPN client deployment, understanding the port usage is crucial for proper network configuration and troubleshooting. By ensuring that the necessary ports are open and accessible, they can guarantee a seamless and secure connection for remote users.
In conclusion, the Cisco AnyConnect VPN client leverages specific ports, such as 443 for SSL and DTLS connections, to provide a reliable and secure remote access solution for organizations of all sizes. By optimizing port usage and network settings, businesses can empower their employees to work remotely without compromising on security or performance.
Port 2000 compatibility
Port 2000 compatibility refers to the ability of a device, software, or system to effectively communicate and interact with Port 2000. In the realm of technology and networking, ports serve as endpoints for communication between devices. Port 2000 is one of the many designated ports used for specific purposes within a network environment.
Ensuring compatibility with Port 2000 is crucial for seamless data transmission and efficient networking operations. Devices and software applications that are compatible with Port 2000 can effectively send and receive data through this port without encountering compatibility issues or communication errors.
Compatibility with Port 2000 is particularly relevant in scenarios where specialized applications or protocols rely on this port for communication. For example, certain server applications may utilize Port 2000 for specific functionalities, and ensuring compatibility with this port is essential for the proper functioning of these applications.
Additionally, compatibility with Port 2000 can also be important in networking environments where multiple devices and systems need to communicate with each other. When all devices and software involved are compatible with Port 2000, it facilitates smooth and efficient data transfer, contributing to overall network reliability and performance.
Furthermore, maintaining compatibility with Port 2000 may require periodic updates and adjustments, especially as technology evolves and new standards emerge. Software developers and network administrators need to stay vigilant and ensure that their systems remain compatible with Port 2000 to avoid potential disruptions in communication and network operations.
In summary, Port 2000 compatibility plays a vital role in enabling effective communication and data exchange within networked environments. Ensuring compatibility with this port is essential for achieving optimal performance and reliability in various technological applications and networking scenarios.
VPN client network ports
VPN (Virtual Private Network) client network ports play a crucial role in establishing secure connections over the internet. When you use a VPN client to connect to a remote server, data is encrypted and transmitted through specific ports to ensure privacy and security.
Typically, VPN clients utilize several network ports to facilitate different aspects of the connection process. One of the primary ports is UDP (User Datagram Protocol) port 500, which is used for IKE (Internet Key Exchange), the protocol responsible for negotiating security associations and establishing VPN tunnels. Another essential port is UDP port 4500, which is often used for NAT traversal, enabling VPN traffic to pass through network address translation (NAT) devices seamlessly.
In addition to these standard ports, VPN clients may also utilize TCP (Transmission Control Protocol) port 443, commonly used for HTTPS (Hypertext Transfer Protocol Secure). By using port 443, VPN traffic can mimic regular HTTPS traffic, making it harder for network administrators to detect and block VPN usage.
Furthermore, some VPN clients offer the option to configure custom ports for communication. This feature allows users to bypass restrictions imposed by network firewalls or ISPs (Internet Service Providers) that may block standard VPN ports. By using non-standard ports, VPN clients can establish connections even in environments with strict network policies.
Overall, understanding the network ports used by VPN clients is essential for optimizing performance, ensuring compatibility with network configurations, and maintaining robust security. Whether you're a casual user concerned about online privacy or a business professional accessing sensitive information remotely, being aware of VPN client network ports can enhance your overall VPN experience.
AnyConnect connection ports
AnyConnect Connection Ports: Understanding the Basics
AnyConnect is a popular VPN (Virtual Private Network) solution developed by Cisco Systems. It allows users to securely access networks remotely over the internet. One crucial aspect of AnyConnect configuration is understanding the connection ports it utilizes.
By default, AnyConnect uses two primary ports for communication: TCP port 443 and UDP port 443. Let's delve into what these ports entail:
TCP Port 443:
TCP (Transmission Control Protocol) is a connection-oriented protocol widely used for data transmission.
Port 443 is commonly associated with HTTPS (Hypertext Transfer Protocol Secure), the secure version of HTTP used for secure communication over a computer network.
Since Port 443 is typically open in firewalls to allow secure web traffic, using TCP Port 443 for AnyConnect connections helps ensure compatibility and accessibility.
UDP Port 443:
UDP (User Datagram Protocol) is a connectionless protocol known for its low overhead and efficiency in real-time applications.
While UDP is less reliable than TCP, it is suitable for time-sensitive data transmission.
Using UDP Port 443 for AnyConnect connections offers an alternative for scenarios where TCP traffic may be blocked or congested.
UDP Port 443 is particularly useful for providing a reliable VPN connection in situations with high network latency or packet loss.
In summary, AnyConnect employs TCP Port 443 and UDP Port 443 for secure VPN connections, leveraging the ubiquity of HTTPS and the efficiency of UDP to ensure reliable and secure communication. Understanding these connection ports is essential for configuring AnyConnect effectively and ensuring seamless remote access to networks.
Cisco VPN protocols
Title: Understanding Cisco VPN Protocols: A Comprehensive Guide
In the realm of network security and remote access, Virtual Private Networks (VPNs) play a pivotal role in safeguarding sensitive data and ensuring secure communications. Among the myriad of VPN solutions available, Cisco stands out as a leader, offering a range of protocols tailored to meet diverse security requirements. Let's delve into the key Cisco VPN protocols and understand their functionalities:
IPsec (Internet Protocol Security): IPsec forms the foundation of Cisco's VPN security architecture. It operates at the network layer and provides end-to-end security through encryption, authentication, and data integrity checks. Cisco IPsec VPNs are widely deployed for site-to-site connectivity, allowing organizations to establish secure communication channels over the internet.
SSL/TLS (Secure Sockets Layer/Transport Layer Security): Cisco implements SSL and its successor TLS to facilitate secure remote access VPNs. Unlike IPsec, which requires client software, SSL/TLS VPNs utilize standard web browsers, making them ideal for users who need seamless access to corporate resources from any location. Cisco's Adaptive Security Appliance (ASA) supports SSL VPNs, providing granular access controls and robust encryption mechanisms.
L2TP/IPsec (Layer 2 Tunneling Protocol/IPsec): L2TP/IPsec combines the tunneling capabilities of L2TP with the security features of IPsec to deliver a secure VPN solution. Cisco routers and ASA devices support L2TP/IPsec for remote access scenarios, ensuring confidentiality and integrity of data transmitted over the VPN tunnel.
AnyConnect VPN: Cisco AnyConnect is a versatile VPN client that supports multiple protocols, including SSL, IPsec, and IKEv2. It offers a unified security posture across various devices and platforms, enabling seamless connectivity and comprehensive threat protection.
By leveraging these Cisco VPN protocols, organizations can establish secure, scalable, and flexible network infrastructures that meet the demands of modern connectivity without compromising on security. Whether it's securing remote access for employees or connecting branch offices securely, Cisco VPN solutions provide the foundation for robust network security architectures.
0 notes
Note
Trick or Treat with Johnny Joestar, please?💕
"I hate horror movies, can't we watch something else?" from Spooky / Autumn Prompts

“I hate horror movies, can we watch something else?” Johnny said this with a sigh as he tried to reach for the remote to be able to put another movie on.
You couldn’t tell if Johnny hated them because he just thought they were boring or if he actually found them to be scary. You’d try your best to get an answer out of him.
“But horror movies are the most appropriate for Halloween season.” You turned to the side to keep the remote out of his reach.
“I know, but they’re all kinda the same.” Johnny was still reaching for the remote.
“If we don’t watch a horror movie, then what do we watch? I mean, sure some horror movies might be cheesy but they’re still fun to watch.”
“Can’t we watch a regular movie? Or at least something more like… a thriller, maybe? I guess if you find them fun to watch though I guess I can bite my tongue for the next hour and a half.” Johnny stopped trying to reach for the remote. He figured he’d just let you do your thing. Even if he didn’t care much for horror movies, the most important thing is that you two were spending time with each other.
“I mean, a thriller can count too. I think that’s a fair compromise… We’ll do something more thriller and not really horror. It still fits spooky season.” You changed the category from ‘horror’ to ‘thriller’.
That put a smile on Johnny’s face, “You’re always so considerate…But you know what, it’s fine. Let’s watch a horror movie this time and then we can watch a thriller movie next time. I know how much you enjoy horror movies. Even if they are cheesy.”
“It’s all about compromise. I don’t mind watching a thriller one this time.” You scrolled through the ‘thriller’ options, now resting your head against his shoulder.
Truthfully you weren’t really focusing on what movie to pick, you were more focused on how comfortable you felt leaning against him like this. You enjoyed little moments like these where the two of you stayed in and enjoyed each other’s company.
“Are you listening?”
“What? You said something?” You gave an embarrassed smile as you sat up. You were so focused on how you felt resting up against him and his scent that you hadn’t heard what he said.
“I said… What about this one?” Johnny asked as he pointed to the screen.
“Oh, sure. Yeah. That’s fine.” You said and rested your head against his shoulder once more. Truthfully you didn’t care what the two of you watched as long as you remained cuddled up like this.
9 notes
·
View notes
Text
why does vpn slow down my internet speed
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
why does vpn slow down my internet speed
VPN Bandwidth Allocation
VPN bandwidth allocation is a crucial aspect of optimizing network performance and ensuring a seamless online experience for users. In the realm of Virtual Private Networks (VPNs), bandwidth allocation refers to the distribution of available bandwidth among connected devices or users. It plays a significant role in determining the speed, stability, and reliability of VPN connections.
Efficient bandwidth allocation is essential for maintaining consistent internet speeds and preventing network congestion, especially in situations where multiple users are accessing the VPN simultaneously. By allocating sufficient bandwidth to each user or device based on their needs and usage patterns, VPN providers can minimize latency and deliver a smoother browsing experience.
One approach to bandwidth allocation involves implementing Quality of Service (QoS) mechanisms, which prioritize certain types of traffic over others. For example, real-time applications like video conferencing or online gaming may be given higher priority to ensure minimal latency and optimal performance. Meanwhile, less time-sensitive activities such as web browsing or file downloads can be allocated lower priority, allowing for more flexible bandwidth management.
Another strategy is to dynamically adjust bandwidth allocation based on network conditions and usage demands. This can involve techniques like traffic shaping, where bandwidth is allocated in real-time according to predefined policies or algorithms. By adapting to changing traffic patterns and allocating resources efficiently, VPN providers can optimize network performance and deliver a consistently high-quality user experience.
In conclusion, VPN bandwidth allocation is a critical factor in optimizing network performance and ensuring a reliable VPN service. By implementing effective bandwidth management strategies such as QoS mechanisms and dynamic allocation techniques, VPN providers can enhance speed, stability, and overall user satisfaction.
Network Latency Impact
Network latency refers to the delay that occurs when data is transmitted from one point to another within a network. It is a crucial factor that can significantly impact the performance of online activities such as gaming, video streaming, video conferencing, and more.
Latency can be caused by various factors, including the physical distance between the sender and receiver, network congestion, and the processing time within network devices. A high level of latency can lead to delays in data transmission, resulting in slow response times and poor user experience.
In online gaming, network latency can be the difference between winning and losing a game. High latency can cause players to experience lag, making it difficult to react quickly and accurately to in-game events. For businesses, network latency can impact productivity and communication, leading to delays in accessing critical applications and data.
Reducing network latency is essential for ensuring smooth and efficient data transmission. This can be achieved through various methods, such as optimizing network configurations, using content delivery networks (CDNs), and investing in high-speed internet connections.
Overall, understanding the impact of network latency is important for individuals and organizations alike. By implementing measures to decrease latency levels, users can enjoy faster and more reliable network performance, ultimately enhancing their online experience.
Server Overload Effects
When a server experiences overload, the effects ripple through the entire online ecosystem. From website crashes to sluggish load times, the ramifications can be severe and far-reaching.
One of the most immediate effects of server overload is website downtime. When too many requests flood a server beyond its capacity, it struggles to respond, leading to websites becoming inaccessible. This downtime can be detrimental to businesses, resulting in lost revenue, decreased customer satisfaction, and damage to brand reputation.
Additionally, server overload can cause slow load times for websites that remain accessible. Users accustomed to fast, seamless browsing experiences may quickly become frustrated with delays in page loading and interactions. This can lead to increased bounce rates as impatient visitors navigate away from slow-loading sites in search of alternatives.
Moreover, server overload can impact search engine rankings. Search engines like Google prioritize user experience, including factors like page speed and accessibility. When a website consistently experiences server overload, it may suffer in search rankings, making it harder for potential visitors to discover the site.
Beyond the immediate consequences for individual websites, server overload can also have broader implications for online infrastructure. In extreme cases, widespread server overload can disrupt entire networks or services, affecting countless users and businesses relying on the internet for operations.
To mitigate the effects of server overload, businesses can invest in scalable hosting solutions, implement caching mechanisms, and optimize website performance. Regular monitoring and proactive maintenance can also help identify and address potential issues before they escalate into full-blown overload situations. By prioritizing the stability and efficiency of their server infrastructure, businesses can minimize the impact of overload and ensure a smoother online experience for their users.
Encryption Overhead Analysis
Encryption overhead analysis is a critical aspect of assessing the performance and efficiency of encryption algorithms in various computing systems. In the realm of cybersecurity, encryption plays a pivotal role in safeguarding sensitive information from unauthorized access or interception. However, the process of encrypting and decrypting data imposes overhead, which can impact system performance and resource utilization.
One key aspect of encryption overhead analysis is evaluating the computational complexity of encryption algorithms. Different encryption techniques, such as symmetric key encryption and public-key encryption, exhibit varying levels of computational overhead. Symmetric key encryption algorithms, like AES (Advanced Encryption Standard), are generally more efficient in terms of computational overhead compared to public-key encryption algorithms like RSA. However, the key size and mode of operation also influence the overhead.
Another factor to consider in encryption overhead analysis is the impact on system resources, including CPU utilization, memory usage, and network bandwidth. Encrypting and decrypting large volumes of data can strain system resources, leading to performance degradation or bottlenecks, especially in high-throughput environments such as servers or network appliances.
Moreover, the choice of encryption algorithm and implementation can significantly affect the overhead. Optimized implementations of encryption algorithms, utilizing hardware acceleration or specialized cryptographic libraries, can mitigate overhead compared to generic software implementations.
Additionally, considerations such as key management, secure key exchange protocols, and cryptographic protocols used in conjunction with encryption also contribute to the overall overhead.
In conclusion, encryption overhead analysis is essential for understanding the performance implications of implementing encryption in computing systems. By carefully evaluating computational complexity, resource utilization, and other factors, organizations can make informed decisions about selecting encryption algorithms and optimizing their implementations to balance security requirements with performance considerations.
Internet Service Provider Throttling
Internet Service Provider (ISP) throttling, also known as bandwidth throttling or traffic shaping, is a practice where ISPs intentionally slow down the internet connection speeds of certain users or specific types of internet traffic. This deliberate slowing down of internet speeds can have significant implications for users' online experiences and has sparked debates about net neutrality and consumer rights.
One of the main reasons ISPs engage in throttling is to manage network congestion. During peak usage times, such as evenings or weekends, when many users are online simultaneously, ISPs may throttle certain types of traffic to ensure that all users have access to a reasonable level of service. By prioritizing certain types of traffic over others, ISPs can prevent network congestion and maintain a consistent level of performance for their customers.
However, there are concerns that ISPs may abuse throttling practices for their own financial gain or to gain a competitive advantage. For example, ISPs may throttle certain types of traffic, such as video streaming or file sharing, to promote their own streaming services or to force users to upgrade to more expensive internet plans. This type of behavior can stifle innovation and limit consumers' choices in the online marketplace.
In response to these concerns, regulatory bodies in some countries have implemented rules and regulations to prevent ISPs from engaging in unfair throttling practices. For example, net neutrality regulations may prohibit ISPs from discriminating against certain types of internet traffic or favoring their own services over those of competitors.
Overall, internet service provider throttling is a complex issue with implications for both consumers and the broader online ecosystem. While some degree of traffic management may be necessary to ensure a smooth online experience for all users, it is essential to strike a balance that protects consumers' rights and promotes a competitive and innovative internet landscape.
0 notes
Text
what layer does vpn work on
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what layer does vpn work on
Network Layer
The network layer, also known as Layer 3 in the OSI model, serves as the backbone of communication in computer networks. It is responsible for routing data packets from the source to the destination across interconnected networks. This layer operates by using logical addresses, such as IP addresses, to identify devices and determine the best path for data transmission.
One of the primary functions of the network layer is routing, which involves selecting the most efficient path for data to travel based on factors like network congestion, distance, and cost. Routers, the devices that operate at this layer, make decisions on packet forwarding based on the destination IP address contained in each packet's header.
Another important aspect of the network layer is logical addressing. Unlike physical addresses (MAC addresses) used at the data link layer, logical addresses are assigned to devices to uniquely identify them on a network. The most commonly used logical addressing scheme is the Internet Protocol (IP), which enables communication between devices on different networks.
Additionally, the network layer provides fragmentation and reassembly services to handle data packets of varying sizes. When a packet is too large to be transmitted over a network, it is divided into smaller fragments at the sending node and reassembled at the receiving node.
Overall, the network layer plays a crucial role in ensuring reliable and efficient communication across complex networks. By facilitating routing, addressing, and packet handling, it enables devices to communicate seamlessly regardless of their physical location or network topology.
Transport Layer
The Transport Layer is a crucial component of the OSI (Open Systems Interconnection) model, responsible for ensuring reliable communication between devices across a network. Sitting above the Network Layer and below the Session Layer, it plays a vital role in data transmission, offering both connection-oriented and connectionless services.
One of the primary functions of the Transport Layer is segmentation and reassembly. It breaks down data from the upper layers into smaller, manageable units known as segments before transmitting them. Upon reaching the destination, these segments are reassembled to reconstruct the original data. This process helps optimize transmission efficiency and ensures that large datasets can be transmitted without overwhelming the network.
Another key feature of the Transport Layer is flow control. By regulating the flow of data between sender and receiver, it prevents congestion and ensures smooth communication. Flow control mechanisms such as buffering and windowing allow the sender to adjust the rate of data transmission based on the receiver's capacity, thereby preventing packet loss and network congestion.
Additionally, the Transport Layer provides error detection and correction mechanisms to ensure data integrity. Through techniques like checksums and acknowledgment mechanisms, it detects and rectifies errors that may occur during transmission, guaranteeing the accuracy and reliability of the data being communicated.
Two commonly used protocols at the Transport Layer are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). TCP offers connection-oriented communication, ensuring reliable data delivery through features like acknowledgment and retransmission, making it ideal for applications requiring high reliability, such as web browsing and file transfer. On the other hand, UDP provides connectionless communication with minimal overhead, making it suitable for applications like streaming media and online gaming, where real-time transmission is critical.
In conclusion, the Transport Layer plays a pivotal role in facilitating communication between devices in a network, offering essential services such as segmentation, flow control, and error detection to ensure efficient and reliable data transmission.
Data Link Layer
The Data Link Layer is the second layer of the OSI model and is responsible for transferring data between adjacent network nodes in a network segment. It ensures that data is transmitted error-free across the physical layer and provides services such as framing, physical addressing, error detection, and flow control.
One of the key functions of the Data Link Layer is to divide the data it receives from the Network Layer into frames for transmission over the network. These frames typically include a header and a trailer, which contain control information like source and destination addresses, sequence numbers, error-checking codes, and more.
Another important aspect of the Data Link Layer is physical addressing, where devices on the same network segment are identified using MAC addresses. These addresses are used by the layer to deliver data to the correct destination within the local network.
Error detection is crucial in the Data Link Layer to ensure data integrity during transmission. Various techniques like cyclic redundancy check (CRC) are used to detect errors in data frames, allowing for retransmission if errors are found.
Flow control is also managed by the Data Link Layer to regulate the flow of data between devices to prevent congestion and ensure smooth data transmission.
Overall, the Data Link Layer plays a critical role in ensuring reliable and efficient communication between devices within a network segment, making it a fundamental component of network communication protocols.
Application Layer
The application layer is a crucial component of the OSI (Open Systems Interconnection) model, serving as the interface between the end user and the network. This layer enables communication between various applications and ensures that data is transmitted accurately and efficiently across different networks.
At the application layer, users interact directly with software applications such as web browsers, email clients, and file transfer protocols (FTP). These applications rely on specific protocols to establish communication and exchange data over the network.
One of the key functions of the application layer is to provide a platform-independent interface for applications to communicate with the underlying network. This abstraction allows developers to focus on the functionality of their applications without worrying about the underlying network infrastructure.
Another important aspect of the application layer is its support for various application-level protocols, including HTTP (Hypertext Transfer Protocol), SMTP (Simple Mail Transfer Protocol), and FTP (File Transfer Protocol). These protocols define the rules and conventions for data exchange between different applications.
Additionally, the application layer is responsible for data formatting, encryption, and compression, ensuring that data is transmitted securely and efficiently over the network. It also manages tasks such as authentication, authorization, and session management to ensure the integrity and security of the communication process.
In summary, the application layer plays a critical role in facilitating communication between applications and networks, providing a platform for seamless data exchange while ensuring security and reliability. Its protocols and services form the backbone of modern networking applications, enabling the interconnectedness of devices and systems across the globe.
Internet Layer
The Internet Layer, also known as the Network Layer, is a crucial component of the TCP/IP protocol suite. It resides above the Link Layer and below the Transport Layer in the OSI model. This layer is responsible for the logical addressing of devices within a network and facilitating the routing of data packets from the source to the destination across different networks.
One of the key functions of the Internet Layer is to define the logical addressing scheme, such as IP addresses, which uniquely identify each device on a network. These addresses are essential for devices to communicate with each other over the internet. The Internet Layer adds a header to the data received from the Transport Layer, encapsulating it into packets known as IP packets.
Routing is another vital function of the Internet Layer. When a device sends out data packets, the Internet Layer examines the destination IP address and determines the most efficient path to deliver the packets. This process involves routers, which make decisions based on routing algorithms and tables to forward the packets towards their intended destinations.
The Internet Layer also handles fragmentation and reassembly of packets if the data to be transmitted is too large to fit in a single packet. By breaking down the data into smaller units, the Internet Layer ensures efficient transmission and reassembles the packets at the receiving end.
In conclusion, the Internet Layer plays a fundamental role in enabling communication between devices on different networks. It ensures that data packets are routed accurately and delivered to their destinations, forming the backbone of modern internet communication.
0 notes
Text
does a vpn use symmetric or asymmetric encryption
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does a vpn use symmetric or asymmetric encryption
VPN encryption methods
VPN encryption methods are crucial components of online security, particularly in an era where digital privacy is increasingly threatened. Understanding these methods can help users make informed decisions about their VPN usage and ensure their data remains protected.
One of the most common encryption protocols used by VPNs is known as AES (Advanced Encryption Standard). AES employs symmetric-key encryption, where both the sender and receiver use the same key to encrypt and decrypt data. It is highly secure and widely regarded as the gold standard in encryption, with key lengths of 128, 192, or 256 bits.
Another encryption protocol frequently utilized by VPNs is OpenVPN. OpenVPN is an open-source software application that implements virtual private network (VPN) techniques for creating secure point-to-point or site-to-site connections. It employs SSL/TLS protocols for security and is known for its flexibility and strong encryption capabilities.
L2TP/IPsec (Layer 2 Tunneling Protocol/Internet Protocol Security) is another commonly used encryption method. It combines the best features of L2TP and IPsec to provide a high level of security. While it may not be as fast as other protocols, it offers robust encryption and is often preferred for its compatibility with various devices and platforms.
Additionally, IKEv2/IPsec (Internet Key Exchange version 2/IP Security) is gaining popularity for its speed and security. It is particularly well-suited for mobile devices due to its ability to quickly reconnect to a VPN server after a network connection is interrupted.
In conclusion, VPN encryption methods play a crucial role in safeguarding sensitive data and ensuring online privacy. By understanding the different protocols available and their strengths, users can choose the most suitable VPN service to protect their digital communications effectively.
Symmetric encryption in VPN
Symmetric encryption plays a crucial role in the functioning of Virtual Private Networks (VPNs), ensuring the confidentiality and integrity of data transmitted over the network. In the context of VPNs, symmetric encryption involves the use of a single key for both encryption and decryption of data. This contrasts with asymmetric encryption, which uses a pair of keys (public and private) for encryption and decryption, respectively.
In a VPN, when a user sends data over the internet, it is first encrypted using a symmetric encryption algorithm and a secret key. This encrypted data is then transmitted through the VPN tunnel to the intended recipient. Since both the sender and the recipient possess the same secret key, the recipient can decrypt the data upon receipt, allowing for secure communication over the inherently insecure internet.
One of the primary advantages of symmetric encryption in VPNs is its efficiency. Symmetric encryption algorithms are generally faster and require less computational resources compared to asymmetric encryption algorithms. This makes them ideal for securing the high-volume data transmission typically encountered in VPNs.
However, one of the challenges of symmetric encryption in VPNs is key management. Since the same key is used for both encryption and decryption, it is crucial to ensure the secure distribution and management of these keys to prevent unauthorized access to sensitive data. This often involves the use of key exchange protocols and secure key storage mechanisms to safeguard the integrity of the encryption process.
In conclusion, symmetric encryption plays a vital role in securing data transmission within Virtual Private Networks. Its efficiency and effectiveness make it a cornerstone of VPN technology, providing users with the confidentiality and privacy they need when accessing the internet.
Asymmetric encryption in VPN
Asymmetric encryption plays a crucial role in ensuring the security and privacy of data transmitted through Virtual Private Networks (VPNs). In the realm of cybersecurity, VPNs are essential tools that allow users to securely access the internet and protect their online activities from prying eyes.
Asymmetric encryption, also known as public-key cryptography, uses a pair of keys – a public key and a private key – to encrypt and decrypt data. In the context of VPNs, asymmetric encryption helps establish a secure connection between the user's device and the VPN server by encrypting data in a way that only the intended recipient can decrypt it.
When a user initiates a VPN connection, the client and server exchange public keys to set up a secure communication channel. The client encrypts the data using the server's public key before transmitting it over the internet. Upon receiving the data, the server decrypts it using its private key, ensuring that only the server can access the information.
This encryption mechanism protects sensitive information, such as login credentials, personal data, and browsing activities, from unauthorized access and interception by cybercriminals or third parties. It creates a secure tunnel through which data can travel safely, maintaining the confidentiality and integrity of the user's online communications.
In conclusion, asymmetric encryption plays a vital role in safeguarding the privacy and security of data transmitted through VPNs. By utilizing public-key cryptography, VPNs can offer users a secure and encrypted connection that protects their sensitive information from potential cyber threats.
VPN security protocols
VPN (Virtual Private Network) security protocols are essential components of ensuring online privacy and security. These protocols establish the framework for secure communication between your device and the VPN server, safeguarding your data from potential threats such as hackers, surveillance, and data interception.
One of the most common VPN security protocols is OpenVPN, known for its robust encryption and versatility. OpenVPN utilizes SSL/TLS protocols to create secure connections, making it highly resistant to interception and manipulation. Its open-source nature also allows for regular security audits and updates, ensuring optimal protection against emerging threats.
Another widely used protocol is IPsec (Internet Protocol Security), which operates at the network layer of the OSI model. IPsec encrypts and authenticates data packets, providing a secure channel for communication between devices. It offers strong protection against various types of cyber attacks and is commonly used in combination with other VPN protocols for enhanced security.
L2TP/IPsec (Layer 2 Tunneling Protocol/Internet Protocol Security) is another popular choice, combining the features of L2TP and IPsec to create a secure tunnel for data transmission. While it provides strong security, L2TP/IPsec can be slower than other protocols due to the double encapsulation process.
SSTP (Secure Socket Tunneling Protocol) is a proprietary protocol developed by Microsoft, offering secure communication over SSL/TLS channels. SSTP is highly resistant to censorship and is often used in environments where VPN connections are restricted or monitored.
IKEv2/IPsec (Internet Key Exchange version 2/IPsec) is known for its speed and stability, making it ideal for mobile devices. It supports seamless switching between network connections, ensuring uninterrupted VPN service even when switching between Wi-Fi and mobile networks.
In conclusion, VPN security protocols play a crucial role in safeguarding your online privacy and security. By understanding the strengths and weaknesses of different protocols, you can choose the one that best fits your needs for a secure and private internet experience.
Encryption algorithms in VPN
Encryption algorithms play a pivotal role in securing data transmitted through Virtual Private Networks (VPNs), safeguarding sensitive information from prying eyes and potential cyber threats. These algorithms employ complex mathematical computations to encode data, making it indecipherable to unauthorized users.
One of the most widely used encryption algorithms in VPNs is Advanced Encryption Standard (AES). AES is renowned for its robust security and efficiency, making it the preferred choice for securing data in transit. It utilizes symmetric-key encryption, where both the sender and receiver share the same key for encrypting and decrypting data. AES supports various key lengths, including 128-bit, 192-bit, and 256-bit, with longer keys offering higher levels of security.
Another prominent encryption algorithm utilized in VPNs is Rivest Cipher (RC). RC algorithms, such as RC4 and RC5, are designed to provide secure communication channels by scrambling data using a series of encryption rounds. While RC4 was widely adopted due to its simplicity and speed, vulnerabilities discovered in its implementation have led to its gradual phasing out in favor of more robust alternatives.
Transport Layer Security (TLS) encryption protocols, including SSL/TLS, are also integral components of VPNs. TLS ensures data integrity, confidentiality, and authentication by encrypting data during transmission and verifying the identities of communicating parties through digital certificates.
Furthermore, VPNs often implement Datagram Transport Layer Security (DTLS) for securing datagram-based communications, such as those used in Voice over IP (VoIP) and real-time multimedia streaming. DTLS extends the benefits of TLS to datagram protocols, ensuring secure communication over unreliable networks.
In conclusion, encryption algorithms form the backbone of VPN security, employing sophisticated techniques to safeguard sensitive data and uphold user privacy in an increasingly interconnected digital landscape. By leveraging robust encryption mechanisms like AES, RC, TLS, and DTLS, VPNs ensure secure and confidential communication channels for individuals and organizations alike.
0 notes
Text
is vpn considered mfa
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
is vpn considered mfa
VPN as MFA Factor
Title: Enhancing Security with VPN as an MFA Factor
In today's digital landscape, ensuring robust cybersecurity measures is paramount for individuals and organizations alike. As cyber threats continue to evolve and become more sophisticated, implementing multi-factor authentication (MFA) has emerged as a crucial strategy to fortify online security. While traditional MFA methods typically involve a combination of passwords and SMS codes, integrating Virtual Private Network (VPN) technology as an additional authentication factor offers an extra layer of protection against unauthorized access.
VPN technology establishes a secure, encrypted connection between a user's device and a remote server, effectively shielding sensitive data from prying eyes. By requiring users to connect to a VPN as part of the authentication process, organizations can bolster their security posture by verifying the legitimacy of the user's identity and enhancing the confidentiality of data transmission.
One of the key advantages of utilizing VPN as an MFA factor is its ability to thwart various cyber threats, including man-in-the-middle attacks and eavesdropping attempts. Since VPNs encrypt all data traffic passing through the network, malicious actors are unable to intercept or manipulate sensitive information, thereby safeguarding against unauthorized access to corporate networks, cloud services, and other critical resources.
Furthermore, VPN-based MFA offers greater flexibility and convenience for users, allowing them to securely access corporate networks and sensitive information from virtually any location without compromising security. Whether employees are working remotely or traveling, VPN-enabled MFA ensures that only authorized individuals can gain access to sensitive data, minimizing the risk of data breaches and unauthorized access.
In conclusion, integrating VPN technology as an additional authentication factor in multi-factor authentication protocols significantly enhances cybersecurity defenses, safeguarding sensitive data and mitigating the risk of unauthorized access. By leveraging VPNs as a supplementary security measure, organizations can proactively mitigate cyber threats and reinforce their overall security posture in an increasingly interconnected digital environment.
Multi-Factor Authentication and VPN
Multi-Factor Authentication (MFA) and Virtual Private Network (VPN) are two essential tools for ensuring the security and privacy of sensitive data in the digital age.
MFA adds an extra layer of security by requiring users to provide multiple forms of verification before accessing an account or system. This typically includes something the user knows (like a password), something they have (like a mobile device for receiving a code), and something they are (like a fingerprint or facial recognition). By requiring multiple factors for authentication, MFA significantly reduces the risk of unauthorized access even if one factor is compromised.
On the other hand, a VPN creates a secure, encrypted connection between a user's device and the internet. This ensures that data transmitted between the user and the network is protected from potential eavesdroppers or hackers. By routing traffic through a VPN server, users can also mask their true IP address and browse the internet anonymously, safeguarding their online privacy.
When used together, MFA and VPN provide enhanced security for remote access to networks and sensitive information. By requiring multifaceted authentication and encrypting data traffic, these tools offer a robust defense against cyber threats and unauthorized access. Whether for business use or personal privacy, incorporating MFA and VPN into your security measures can help mitigate the risks of cyber attacks and data breaches. Remember, in today's interconnected world, safeguarding your digital assets is more important than ever.
VPN vs MFA Security Measures
When it comes to securing sensitive data online, two common measures used by individuals and organizations are VPNs (Virtual Private Networks) and MFA (Multi-Factor Authentication). Both VPNs and MFA serve as crucial tools in enhancing security and safeguarding digital information, but they operate in different ways.
VPNs create a secure and encrypted connection to the internet, ensuring that all data transmitted between your device and the internet is protected from prying eyes. By masking your IP address and encrypting your data, VPNs help secure your online activities, especially when using public Wi-Fi networks. This makes VPNs an essential tool for maintaining privacy and anonymity online.
On the other hand, MFA adds an extra layer of security by requiring users to provide two or more forms of identification before granting access to an account or system. This could involve entering a password, receiving a verification code on a mobile device, or using biometric data such as a fingerprint. MFA significantly reduces the risk of unauthorized access even if passwords are compromised, making it a powerful defense against cyber threats.
While VPNs focus on securing data transmission and maintaining anonymity, MFA emphasizes identity verification and access control. Utilizing both VPNs and MFA together can provide a comprehensive security solution, ensuring that data is encrypted during transmission and access is restricted only to authorized users.
In conclusion, both VPNs and MFA play vital roles in enhancing online security. By understanding their unique functionalities and implementing them effectively, individuals and organizations can fortify their defenses against cyber threats and protect sensitive information in the digital age.
Understanding VPN and MFA Relationship
VPN and MFA, standing for Virtual Private Network and Multi-Factor Authentication respectively, are two crucial components of cybersecurity that work together to provide an extra layer of protection for sensitive data and information. Understanding their relationship is key to enhancing the security of your online activities.
A Virtual Private Network, or VPN, creates a secure encrypted connection over the internet, allowing users to access a private network securely from remote locations. It is commonly used to protect data traffic from prying eyes, especially when using public Wi-Fi networks. By encrypting the data flow between the user's device and the VPN server, VPNs ensure that sensitive information remains confidential.
Multi-Factor Authentication, or MFA, adds an extra layer of security by requiring users to provide two or more verification factors before accessing an account. These factors can be something the user knows (like a password), something they have (like a smartphone for receiving a verification code), or something they are (like a fingerprint or facial recognition). MFA significantly reduces the risk of unauthorized access, even if login credentials are compromised.
The relationship between VPN and MFA lies in their combined ability to enhance security measures. While VPN secures the communication channel, MFA adds an additional barrier against unauthorized access attempts. By using both technologies in tandem, organizations can create a robust defense system against cyber threats and data breaches.
In conclusion, understanding the relationship between VPN and MFA is essential for leveraging their full potential in safeguarding sensitive information. By implementing these cybersecurity measures effectively, users and organizations can enjoy peace of mind knowing their data is well-protected in today's increasingly digital world.
MFA Integration with VPN Services
Title: Enhancing Security: MFA Integration with VPN Services
In an era where cybersecurity threats loom large, the integration of Multi-Factor Authentication (MFA) with Virtual Private Network (VPN) services has emerged as a critical strategy to fortify digital defenses. MFA, a security mechanism requiring users to provide two or more verification factors to gain access, adds an extra layer of protection beyond traditional passwords. When combined with VPN services, which encrypt internet traffic and provide secure connections to remote networks, the result is a robust shield against unauthorized access and data breaches.
One of the primary benefits of integrating MFA with VPN services is the mitigation of password-related risks. Passwords alone are vulnerable to various attacks, including brute force, phishing, and credential stuffing. By supplementing them with additional authentication factors such as biometrics, smart cards, or one-time passcodes, MFA significantly reduces the likelihood of unauthorized access, even if passwords are compromised.
Moreover, MFA integration enhances user accountability and control over network access. With multiple authentication factors, organizations can verify the identity of users more reliably, ensuring that only authorized individuals can connect to VPNs and access sensitive resources. This capability is particularly crucial in remote work environments, where employees access corporate networks from various locations and devices.
Furthermore, MFA integration strengthens compliance with regulatory requirements and industry standards. Many regulations, such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS), mandate the use of multi-layered authentication to safeguard sensitive information. By incorporating MFA into VPN services, organizations can demonstrate adherence to these regulations and bolster their overall security posture.
In conclusion, the integration of MFA with VPN services is a proactive measure to enhance security in an increasingly digitized world. By combining these two technologies, organizations can better protect their networks, data, and users against evolving cyber threats, ultimately fostering trust and confidence in their digital operations.
0 notes
Text
will a vpn give me better ping
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
will a vpn give me better ping
VPN latency improvement
VPN latency improvement is a crucial factor in ensuring a smooth and fast online experience while using a VPN service. Latency refers to the delay between the sender and receiver of data, and high latency can result in slow connection speeds and buffering issues. Fortunately, there are several strategies to improve VPN latency and enhance overall performance.
One effective way to reduce VPN latency is to connect to a server that is geographically closer to your physical location. By doing so, you can minimize the distance that data must travel, leading to lower latency and faster connection speeds. Many VPN providers offer a wide selection of servers worldwide, allowing users to choose the most optimal server for their needs.
Another method to improve VPN latency is to upgrade to a premium VPN service that offers faster servers and better infrastructure. Premium VPN providers often invest in high-performance servers and networking equipment to deliver superior speeds and lower latency to their users. While free VPN services may be convenient, they are more likely to experience higher latency due to overcrowded servers and limited bandwidth.
Additionally, optimizing your device and network settings can help decrease VPN latency. Closing unnecessary applications, updating software, and using a wired connection instead of Wi-Fi can all contribute to a smoother VPN experience with lower latency.
In conclusion, reducing VPN latency is essential for enjoying a seamless and responsive online experience. By selecting the right server, upgrading to a premium VPN service, and optimizing device settings, users can improve VPN latency and enhance their overall browsing, streaming, and gaming activities.
Impact of VPN on ping
The Impact of VPN on Ping
Virtual Private Networks (VPNs) have become a popular tool for internet users seeking enhanced privacy and security online. However, while VPNs offer many benefits, they can also have an impact on internet speed and latency, particularly when it comes to ping.
Ping, measured in milliseconds (ms), refers to the time it takes for data packets to travel from your device to a server and back again. It's a crucial metric for online gaming, video conferencing, and other real-time applications, as lower ping times result in faster response times and smoother experiences.
When you connect to a VPN server, your internet traffic is encrypted and routed through the VPN server before reaching its destination. This additional step can introduce latency and increase ping times. The extent of the impact depends on various factors, including the distance between your location and the VPN server, the server's workload, and the quality of your internet connection.
In some cases, connecting to a VPN server that is geographically distant from your location can significantly increase ping times. This is because data packets must travel a longer distance, resulting in higher latency. Additionally, if the VPN server is experiencing high traffic or is overloaded, it can further delay the transmission of data, leading to slower ping times.
However, not all VPNs have the same impact on ping. Some VPN providers invest in high-performance servers and optimize their networks to minimize latency. Additionally, choosing a VPN server closer to your physical location can help reduce ping times.
In conclusion, while VPNs offer numerous benefits in terms of privacy and security, users should be aware of their potential impact on ping times. By selecting the right VPN provider and server location, users can minimize latency and enjoy a smoother online experience.
Decrease ping with VPN
Title: How to Decrease Ping with VPN: Boosting Your Online Gaming Experience
Are you tired of experiencing lag and high ping times while gaming online? If so, using a VPN (Virtual Private Network) might be the solution you've been searching for. While VPNs are commonly known for their ability to enhance online security and privacy, they can also significantly reduce ping and improve overall gaming performance.
Here's how it works:
Optimized Routing: When you connect to a VPN server, your internet traffic is routed through a different network than your ISP (Internet Service Provider) normally uses. This can lead to more efficient routing paths, resulting in lower ping times and reduced latency.
Traffic Prioritization: Many VPN providers offer specialized servers optimized for gaming traffic. These servers are designed to prioritize gaming data, ensuring that your game packets are delivered quickly and efficiently, thereby decreasing ping times.
Bypassing Network Congestion: VPNs can help bypass congested or throttled networks, which are common causes of high ping during peak hours. By connecting to a VPN server in a different location, you can potentially avoid these congestion points and enjoy smoother gameplay.
Geographic Optimization: Some games have regional servers that may be located far away from your actual location. By using a VPN to connect to a server closer to the game server location, you can reduce the physical distance your data needs to travel, resulting in lower ping times.
However, it's essential to choose a reputable VPN provider that offers fast and reliable servers, as well as minimal latency. Additionally, while VPNs can decrease ping in many cases, results may vary depending on factors such as server location, network congestion, and the quality of your internet connection.
In conclusion, if you're looking to enhance your online gaming experience and reduce ping times, using a VPN can be a valuable tool. By optimizing routing, prioritizing traffic, and bypassing network congestion, VPNs can help you achieve smoother gameplay and gain a competitive edge in your favorite games.
VPN latency optimization
Title: Maximizing VPN Latency Optimization: Tips and Techniques
In the realm of virtual private networks (VPNs), latency optimization stands as a crucial aspect for ensuring smooth and efficient online experiences. VPNs, while paramount for privacy and security, can sometimes introduce latency, leading to slower internet connections. However, with the right strategies and techniques, users can mitigate latency issues and enjoy seamless browsing, streaming, and gaming experiences.
One effective method for optimizing VPN latency is selecting the nearest server location. Distance between the user and the server directly impacts latency, so choosing a server geographically close to your location can significantly reduce latency. Most VPN providers offer multiple server options, allowing users to select the one that offers the lowest latency.
Additionally, utilizing lightweight VPN protocols such as IKEv2 or WireGuard can help minimize latency. These protocols are designed to prioritize speed and efficiency, resulting in reduced latency compared to heavier protocols like OpenVPN.
Furthermore, optimizing network settings on both the client and server sides can contribute to latency reduction. Adjusting MTU (Maximum Transmission Unit) settings and enabling TCP/IP acceleration can improve data transmission efficiency, thus lowering latency.
Moreover, employing quality-of-service (QoS) features on routers and network devices can prioritize VPN traffic, ensuring smoother and faster data transmission. By allocating sufficient bandwidth to VPN connections, users can minimize latency and maintain optimal performance.
Regularly updating VPN software and firmware is also essential for latency optimization. Developers often release updates to address performance issues and enhance efficiency, so keeping VPN applications and devices up-to-date can help mitigate latency problems.
In conclusion, optimizing VPN latency involves a combination of selecting the right server location, using lightweight protocols, adjusting network settings, implementing QoS features, and keeping software/firmware updated. By following these strategies, users can enjoy faster and more responsive VPN connections, enhancing their overall online experience.
VPN ping enhancement
VPN Ping Enhancement: Boosting Your Connection Speed
Using a Virtual Private Network (VPN) offers many benefits, such as online security and anonymity. However, one common issue that users may face when using a VPN is an increase in ping time. Ping is the time it takes for data to travel from your device to the server and back. A high ping can result in slower internet speeds and laggy connections, impacting your browsing, streaming, and gaming experience.
Fortunately, there are ways to enhance your VPN connection and reduce ping times:
Choose a Server Close to Your Location: Opt for a VPN server that is geographically closer to your physical location. By connecting to a server nearby, you can reduce the distance data needs to travel, which can significantly improve your ping time.
Use a VPN with High-Speed Servers: Not all VPN servers are created equal. Some VPN providers offer servers specifically optimized for speed. Prioritize using these servers to enjoy faster connections and lower ping times.
Upgrade Your Internet Connection: Your internet speed directly affects your ping time. Consider upgrading to a faster internet plan to see a noticeable improvement in your VPN connection speed.
Enable Split Tunneling: Split tunneling allows you to route only specific traffic through the VPN server while letting other traffic bypass the VPN. By prioritizing VPN traffic, you can reduce congestion and lower ping times.
Update Your VPN Client: Ensure that you are using the latest version of your VPN client. Updates often include performance enhancements and bug fixes that can help improve your connection speed and reduce ping times.
By implementing these tips, you can effectively enhance your VPN connection and enjoy a smoother online experience with reduced ping times.
0 notes
Text
why does a vpn slow down my internet
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
why does a vpn slow down my internet
VPN Bandwidth Allocation
Title: Understanding VPN Bandwidth Allocation: Optimizing Your Connection
In the realm of virtual private networks (VPNs), bandwidth allocation plays a critical role in determining the efficiency and speed of your online activities. Bandwidth allocation refers to the distribution of available network resources among different users or applications, ensuring that each receives a fair share of the available capacity. When it comes to VPNs, proper bandwidth allocation can significantly impact your browsing experience, especially when streaming high-definition content, gaming, or conducting business-related activities.
One of the primary factors influencing VPN bandwidth allocation is the type of VPN protocol being used. Protocols like OpenVPN and IKEv2/IPsec are known for their reliable performance but may consume more bandwidth compared to lightweight options like L2TP/IPsec or PPTP. Understanding the strengths and limitations of each protocol can help users make informed decisions based on their specific needs.
Additionally, VPN providers may impose bandwidth limits on their users to prevent network congestion and ensure a consistent level of service for all subscribers. These limits can vary depending on the subscription plan chosen, with premium plans often offering higher bandwidth allocations compared to free or basic packages.
To optimize VPN bandwidth allocation, users can implement various strategies such as selecting servers with lower traffic loads, utilizing compression techniques to reduce data usage, and prioritizing critical applications to receive a larger share of the available bandwidth.
Moreover, regularly monitoring and adjusting bandwidth allocation settings based on usage patterns can help users maintain optimal performance levels while minimizing unnecessary data consumption.
In conclusion, VPN bandwidth allocation is a crucial aspect of ensuring a seamless and secure online experience. By understanding the factors influencing allocation and implementing optimization strategies, users can maximize the efficiency of their VPN connections and enjoy uninterrupted access to the internet.
Network Overhead Impact
Network overhead impact refers to the additional resources and bandwidth consumed by network communication processes beyond the actual data being transmitted. This overhead is a critical consideration in modern network architectures, as it can affect performance, efficiency, and overall user experience. Understanding and managing network overhead is essential for optimizing network performance and ensuring smooth data transmission.
Various factors contribute to network overhead, including protocol headers, error checking mechanisms, and encryption processes. Each of these elements adds extra data to the original payload, increasing the size of packets transmitted over the network. While these mechanisms are necessary for ensuring data integrity and security, they also introduce latency and reduce available bandwidth.
One of the primary impacts of network overhead is reduced network throughput. As the size of packets increases due to overhead data, the actual data transfer rate decreases, leading to slower communication between network devices. This can result in delays, buffering issues, and overall decreased network performance.
Another significant effect of network overhead is increased network congestion. Since larger packets consume more bandwidth, the network may become congested more quickly, especially during peak usage periods. This congestion can lead to packet loss, retransmissions, and ultimately degrade the overall user experience.
To mitigate the impact of network overhead, network administrators can implement various strategies such as optimizing protocol settings, using compression techniques, and deploying efficient routing protocols. By minimizing unnecessary overhead and efficiently managing network resources, organizations can enhance network performance, reduce latency, and ensure reliable data transmission across their networks.
Server Distance Latency
Title: Understanding Server Distance Latency: Impact on Online Performance
In the digital age, where milliseconds can make a difference in user experience, server distance latency has emerged as a critical factor affecting online performance. Simply put, server distance latency refers to the delay in data transmission caused by the physical distance between a user's device and the server hosting the content or application.
The concept is straightforward: the farther a user is from the server, the longer it takes for data to travel back and forth, resulting in higher latency. This delay can manifest in various ways, including slower website loading times, lag in online gaming, and buffering in video streaming.
One of the primary contributors to server distance latency is the speed of light. While light travels incredibly fast, it still takes time to cover vast distances, especially when data must traverse across continents or through undersea cables. Additionally, the routing infrastructure of the internet can introduce further delays as data packets navigate through various network nodes.
The implications of server distance latency are significant, particularly for businesses operating in the digital space. For e-commerce websites, even a slight increase in latency can lead to decreased conversion rates as impatient users abandon slow-loading pages. Similarly, online gaming companies must prioritize server location to minimize lag and provide a seamless gaming experience for players worldwide.
Mitigating server distance latency requires a multi-faceted approach. Content delivery networks (CDNs) strategically distribute content across multiple servers worldwide, reducing the distance data must travel for end-users. Additionally, optimizing network routing and investing in high-speed internet infrastructure can help minimize latency.
In conclusion, while server distance latency may seem like a technical concern, its impact reverberates throughout the online landscape. By understanding and addressing this issue, businesses can enhance user experiences, improve customer satisfaction, and gain a competitive edge in the digital realm.
Encryption Protocol Efficiency
Encryption protocol efficiency is a crucial aspect of modern data security, impacting both performance and effectiveness. In the realm of cybersecurity, encryption protocols serve as the backbone for safeguarding sensitive information from unauthorized access. However, the efficiency of these protocols can vary significantly based on factors such as algorithm complexity, key length, and computational overhead.
One of the primary considerations in evaluating encryption protocol efficiency is its impact on system performance. High-performance encryption protocols should be capable of securing data without introducing substantial latency or overhead. This is particularly important in real-time applications such as video streaming, online gaming, and financial transactions, where any delay can degrade user experience or compromise operational integrity.
Moreover, encryption protocols must strike a balance between security and computational resources. While stronger encryption algorithms offer higher levels of security, they often require more computational power and memory to execute. As a result, organizations must carefully assess their encryption needs and choose protocols that align with their performance requirements and resource constraints.
Furthermore, encryption protocol efficiency is closely tied to scalability and interoperability. As data volumes continue to grow exponentially, encryption solutions must scale seamlessly to accommodate increasing workloads without sacrificing performance or security. Additionally, interoperability between different encryption protocols and systems is essential for ensuring seamless communication and data exchange in heterogeneous environments.
In conclusion, encryption protocol efficiency plays a critical role in modern cybersecurity strategies. By balancing security, performance, scalability, and interoperability considerations, organizations can implement robust encryption solutions that effectively protect their sensitive data while maintaining operational efficiency.
Device Processing Capacity
Device processing capacity refers to the ability of a device, such as a computer, smartphone, or tablet, to handle and process a certain amount of data within a specific period of time. This capacity is crucial for the overall performance and efficiency of the device when running various applications and programs.
The processing capacity of a device is determined by its hardware components, such as the central processing unit (CPU), random access memory (RAM), and storage space. The CPU is often considered the 'brain' of the device, as it performs most of the calculations and processes the data. The speed and efficiency of the CPU play a significant role in determining the device's processing capacity.
RAM is another critical factor that impacts a device's processing capacity. It temporarily stores data that the CPU needs to access quickly, allowing for faster processing speeds. The more RAM a device has, the more data it can handle simultaneously, thus improving its overall performance.
Storage space is also essential for device processing capacity, as it determines how much data the device can store and access. Devices with larger storage capacity can handle more data-intensive tasks without slowing down.
In conclusion, device processing capacity is a vital aspect to consider when choosing a device for personal or professional use. Understanding the relationship between hardware components and processing capacity can help users select a device that meets their specific performance needs and requirements.
0 notes
Note
trick or treat + risotto please ? 🩷
"I'm not doing matching costumes" from Spooky / Autumn Prompts

Risotto raised a brow as he watched you hold up the matching costumes you had picked out for the two of you.
“I’m not doing matching costumes.” He said with a grumble. Sure, he was fine with the holiday but he always thought matching costumes were kind of lame.
“Aw, not even for me?” You asked with a small pout. You figured he might have this sort of reaction, but you still wanted to try your luck.
You knew trying to convince Risotto to doing most things with you was like pulling teeth. He was reluctant about wanting to do most things, but in the end he usually ended up agreeing to these things on his own. You always were patient with him when it came to these things, but you’ve really been wanting to do matching costumes with him so it was difficult for you to back down on this one.
“You know I don’t like doing stuff like that.” Risotto said with a sigh, he did his best to avoid making eye contact with you. Your pout was so cute and you probably already knew that a cute pout like that would get to him.
“I know, but…I just thought it could be cute. Maybe.” You set the costumes aside. You didn’t want to push the issue further if Risotto really didn’t want to do matching costumes. You took a moment setting your disappointment aside, “It’s ok if you don’t want to.”
Risotto sighed to himself… He knew he was going to give into you. He was just being a bit stubborn about it. It shouldn’t be such a big deal - couples did matching costumes all the time, and now that you two were a couple this was part of ‘boyfriend duty’.
“….Alright. Fine.” Risotto admitted defeat, but he didn’t sound too thrilled about it.
“Wait, really? I mean, only if you really want to… I don’t want you to be mad at me.” You were still worried he was annoyed about this.
Risotto shook his head, “Nah. It’s OK. It’s what couples do for Halloween… I’ve never really had anyone to match costumes with me before, so this is just really new to me.”
“There’s a first time for everything.” You said with a small smile.
“Yeah, I guess so. I guess it’s not so bad if the first time doing this is with you.” Risotto said with a small shrug.
You couldn’t help but smile more at this - you knew that Risotto could be a bit stubborn sometimes, but it was always nice when he gave in and showed his softer side to you.
“I appreciate that. It means a lot to me.” You said now going over to give him a kiss.
“You’re lucky I love you.” Risotto said teasingly as he kissed you back.
8 notes
·
View notes
Text
what is vpn termination
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is vpn termination
VPN Termination Definition
VPN termination refers to the process of ending or completing a VPN connection between a user's device and a VPN server. This termination point is where the encrypted data tunnel established by the VPN is decrypted and then sent to its destination on the internet. Understanding VPN termination is crucial for grasping how VPNs operate and ensuring secure communication over the internet.
When a user initiates a VPN connection, their device encrypts all outgoing data packets using a secure protocol such as SSL/TLS or IPSec. These encrypted packets are then transmitted through the internet to a VPN server. The VPN server, located in a different physical location, receives these packets and decrypts them at the termination point. Once decrypted, the data is sent to its intended destination, whether it's a website, server, or another network device.
VPN termination can occur at various points within a network infrastructure. For example, in a corporate environment, VPN termination often takes place at the organization's firewall or dedicated VPN appliance. In contrast, for individual users accessing a commercial VPN service, termination typically occurs at the provider's servers.
The termination process also involves encrypting incoming data from the internet before transmitting it back to the user's device. This encryption ensures that sensitive information remains secure throughout the communication process.
Overall, VPN termination plays a critical role in maintaining privacy and security for users accessing the internet, especially when using public or unsecured networks. By encrypting data and routing it through secure VPN servers, individuals and organizations can protect their online activities from eavesdropping, surveillance, and unauthorized access.
VPN Termination Process
VPN termination process refers to the method by which a Virtual Private Network (VPN) connection is finalized or completed. When a user initiates a connection to a VPN server, the termination process is what allows the data to be securely transmitted and received.
The VPN termination process involves several key steps to ensure that the data being transferred is encrypted and remains confidential. Firstly, the user's device establishes a connection to the VPN server through an encrypted tunnel. This tunnel acts as a secure pathway for data transmission.
Once the connection is established, the VPN server authenticates the user's credentials to verify their identity. This authentication process typically involves the use of usernames, passwords, and sometimes additional security measures such as two-factor authentication.
After the user's identity is verified, the VPN server then decrypts the data packets received from the user's device and forwards them to their intended destination, whether it be a website, server, or another network device. Similarly, data packets from the external destination are encrypted by the VPN server before being transmitted back to the user's device.
Finally, when the VPN session is complete, the termination process involves closing the encrypted tunnel and ensuring that no data leaks or security breaches occur.
In conclusion, the VPN termination process is crucial for establishing a secure connection between a user's device and a VPN server, ensuring that data is encrypted, transmitted safely, and remains confidential throughout the communication.
VPN Tunnel Endpoint
A VPN tunnel endpoint refers to the termination point of a secure connection established through a Virtual Private Network (VPN). In simple terms, it is where the encrypted data is decrypted upon reaching its destination. The VPN tunnel endpoint plays a crucial role in ensuring the confidentiality, integrity, and authenticity of data transmitted between two networks or devices over the internet.
When you connect to a VPN service, your data passes through a secure tunnel created between your device and the VPN server. The tunnel endpoint, located at both your device and the server, encrypts the data using advanced encryption protocols, making it nearly impossible for hackers or unauthorized parties to intercept or tamper with the information.
VPN tunnel endpoints enhance online privacy by masking your real IP address and location, making it difficult for websites, advertisers, or even government agencies to track your online activities. This technology is particularly useful for individuals looking to access geo-restricted content, enhance data security when using public Wi-Fi networks, or simply add an extra layer of protection to their internet connection.
In conclusion, VPN tunnel endpoints serve as the gateways to secure and private internet communication. By encrypting data traffic and ensuring the anonymity of users, they play a vital role in safeguarding sensitive information and protecting online privacy in today's digital landscape.
VPN Termination Point
A VPN termination point serves as a crucial component in the infrastructure of a Virtual Private Network (VPN). Essentially, it acts as the endpoint where encrypted VPN tunnels are established and terminated.
In the context of VPN technology, a termination point can refer to either hardware or software. Hardware termination points typically consist of dedicated VPN appliances or routers, while software termination points are often implemented within servers or firewall devices.
The primary function of a VPN termination point is to facilitate secure communication between remote users or networks over an untrusted network, such as the internet. When a VPN connection is initiated, data packets are encrypted at the source and then transmitted through the internet to the termination point. At the termination point, the encrypted packets are decrypted, allowing access to the intended destination network.
One of the key benefits of using VPN termination points is enhanced security. By encrypting data traffic between endpoints, VPNs help protect sensitive information from unauthorized access or interception. Additionally, VPN termination points can enforce access control policies, ensuring that only authorized users are allowed to establish VPN connections.
Moreover, VPN termination points play a vital role in ensuring reliable and efficient communication across geographically dispersed networks. They help mitigate network congestion and latency by efficiently handling the encryption and decryption processes.
In summary, VPN termination points are essential components of VPN infrastructure, providing secure and reliable communication channels for remote users and networks. Whether implemented in hardware or software, these endpoints enable organizations to establish private and encrypted connections over public networks, safeguarding sensitive data and ensuring seamless connectivity.
VPN Gateway Termination
VPN Gateway Termination refers to the process of ending a virtual private network (VPN) connection at the gateway level. In simpler terms, it's where the encrypted tunnel between your device and the VPN server comes to an end.
When you connect to a VPN, your data is encrypted and securely transmitted through this tunnel to the VPN server. The VPN gateway, often located at the edge of a network, plays a crucial role in managing these connections. It acts as the entry and exit point for data traveling to and from the VPN.
There are several reasons why VPN gateway termination is important:
Security: By terminating VPN connections at the gateway, organizations can enforce security policies and inspect traffic for any malicious activity. This helps in preventing unauthorized access to sensitive information and protects against cyber threats.
Performance: VPN gateway termination can also improve network performance by offloading encryption and decryption tasks from individual devices to dedicated hardware. This reduces the processing overhead on end-user devices and ensures smooth and efficient data transmission.
Scalability: VPN gateway termination allows for easier scalability of VPN infrastructure. As the number of VPN users grows, organizations can add more gateway devices to handle the increased traffic load without compromising performance or security.
Compliance: Many industries have regulatory requirements regarding data privacy and security. VPN gateway termination enables organizations to monitor and enforce compliance with these regulations by providing visibility into network traffic and ensuring that data is protected during transmission.
Overall, VPN gateway termination is a critical component of a secure and reliable VPN infrastructure. By effectively managing and securing VPN connections at the gateway level, organizations can safeguard their data, enhance network performance, and ensure compliance with regulatory requirements.
0 notes