#ollydbg
Text
In his How To, he lists the skills hackers should acquire first:
Learn C.²²
Learn just a little bit of x86 assembler.²³ You don't have to be great at this at first, but you need to sort of kind of know what the fuck is going on.
Work through Hacking: The Art of Exploitation by Erickson.
Learn JavaScript.
Go through the big exploit archives. Star in the 1990s. Look through exploits. Figure out how they worked. Turn the clock forward to the modern era, so you slowly accustom yourself to newer exploitation techniques.
Get really good at x86 assembler, and learn IDA Pro and OllyDbg.
22. C is a general-purpose, machine-independent programming language that was used to write a range of well-known applications – from Windows operating systems to Oracle databases.
23. x86 assembler is a programming language used for time-sensitive applications and detailed software systems.
"Going Dark: The Secret Social Lives of Extremists" - Julia Ebner
#book quotes#going dark#julia ebner#nonfiction#andrew auernheimer#weev#how to#skills#hacking#c#programming#x86 assembler#hacking: the art of exploitation#jon erickson#javascript#exploits#archives#90s#1990s#20th century#exploitation#ida pro#ollydbg#time sensitive#software
33 notes
·
View notes
Text
OllyDBG Assembler Level Debugger 32bit Di Exagear Windows Emulator
youtube
0 notes
Note
hiya foone! i'm working on the surprisingly lofty task of modding barbie fashion show 2004 and i've been told twice to ask if you have any leads on how to get to the game files. i don't know how to simplify it because i'm so in over my head at this point. here is the thread
okay so here's how you reverse engineer an arbitrary game, the quick version:
Research. Who made the game? what else did they make? Maybe they made a game with the same engine, and someone already figured out that one? (not that I saw on a quick look, but you may be able to dig deeper) Also, look in the game files. There's a PowerRender.dll and a sipEngine.bc file. Nothing for sipEngine, but PowerRender has a hit on the internet archive, maybe that download includes some info on how it encodes files?
Look at the files (with a hex editor, like HxD). KAR files seem to be the main storage mechanism, and they've got a RIFF header. RIFF is a standard, though they're not using it exactly. But this might help. Another thing you can spot in the KAR files is a bunch of english strings (CreditsTb.kar is lousy with them). That's a good sign: it means the files aren't compressed, so you don't have to figure out the compression method.
Static analysis of the EXE. Get Ghidra and load up the EXE. Find where it opens files (CreateFileA/CreateFileW on windows), trace back from there. Check the strings. Hey look, function FUN_004e6260 is called with "KAResource.kar". so FUN_004e6260 is probably a function to load arbitrary resource files. Dig through that, figure out how it works.
Dynamic analysis of the EXE. Stick it in a debugger and see what it does. Set a breakpoint on CreateFileA/W and follow the execution. I don't have a good recommendation for what tool to use here, I'm from the past. I've used Ollydbg a lot but it hasn't been updated in 9 years.
Hijack the EXE and make it do your work for you. One thing I noticed while looking around was references to Python. This game apparently embeds a python interpreter, version 2.2. Maybe you can find where it loads the code from, or inject your own code?
Anyway those are some introductory ideas. feel free to ask any follow-up questions, but this hopefully gives you some idea of where to start?
Good luck!
443 notes
·
View notes
Text
Come craccare un software

Esistono vari modi per craccare un software, che vanno da semplici tecniche come la modifica dei file DLL al reverse engineering, che può rivelare il funzionamento interno del programma. L'uso degli strumenti giusti è essenziale per il successo del cracking. Inoltre, il reverse engineering ti consente di superare il processo di attivazione di determinati programmi.
In questa guida tratteremo quello che forse per molti utenti è l'argomento più desiderato ovvero le migliori tecniche su come craccare un software
Parleremo di come possiamo creare noi stessi delle crepe che ci permetteranno di far funzionare tutti i programmi. Ci sono due modi più grandi per creare crack per qualsiasi programma. In questa guida per ora vi spiego il primo metodo, per il secondo farò un'altra guida dove ti spiegherò come craccare un programma.
Per craccare un programma devi cercare di aggirare il controllo del codice di licenza. Questo di solito è controllato via internet o deve essere valido secondo alcuni algoritmi del software.
Importante: questa guida è solo a titolo informativo pertanto non mi assumo la responsabilità dell'uso che ne viene fatto.
Come craccare un software

Il primo metodo di cui parlo è molto tecnico ma allo stesso tempo molto efficace. Ma prima di iniziare a cercare di capire come creare la crack è necessario sapere cosa viene scritto quando il programma rifiuta il codice di licenza inserito. Ad esempio, se dice “Spiacente, codice di licenza errato” ricorda questo testo perché ti servirà più avanti nella guida.
Ecco i passaggi che devi fare per craccare un software:
- Per iniziare ti serve il file eseguibile (.exe) del programma che vuoi craccare e devi scaricare il programma Ollydbg che trovi a questo link ;
- Dopo aver scaricato Ollydbg devi estrarlo utilizzando un programma come Winrar che puoi scaricare da questo link ;
- Ora avvia il file OLLYDBG.EXE e clicca su Apri nell'angolo in alto a sinistra;
- Dalla finestra che si è aperta seleziona il file .exe del programma che vuoi craccare;
- Ora devi capire qual è l'istruzione che controlla la password. Per fare ciò, fai clic con il pulsante destro del mouse nella prima finestra di Olly e vai su Cerca > Tutte le stringhe di testo referenziate;
- Nella finestra che si apre cliccare nuovamente con il tasto destro del mouse, cliccare su Cerca testo e ricercare la parola “ chiave ” (o quella che compariva nel messaggio di codice di licenza errato) tra tutte le istruzioni che contengono testo nel programma esaminato;
- Dopo aver trovato la riga di testo del messaggio di errore, fai doppio clic con il mouse sulla stringa trovata e verrai indirizzato all'istruzione di assemblaggio che genera quel messaggio;
- Noterete che prima di tale istruzione c'è un JNZ SHORT (salta se diverso da zero), proprio quello che in caso di corretto inserimento del numero seriale fa superare il sistema di sicurezza;
- Sostituire JNZ con JMP, in modo che il programma ignori sempre il controllo della password;
- Termina con un clic destro andando su Copia su eseguibile> Tutte le modifiche per salvare le modifiche;
A questo punto il crack del programma è stato realizzato!
Note finali
E siamo arrivati alle note finali di questa guida su come craccare un software. Prima di salutare volevo informarti che mi trovi anche sui Social Network, per entrarci clicca sulle icone appropriate che trovi nella Home di questo blog, inoltre se la guida ti è piaciuta condividila pure attraverso i pulsanti social di Facebook, Twitter, Pinterest e Tumblr, per far conoscere il blog anche ai tuoi amici, ecco con questo è tutto Wiz ti saluti.
Read the full article
0 notes
Photo

Practical Malware Analysis: The Hands-On Guide to Dissecting Malicious Software
Executive Summary
In the dynamic area that is malware analysis, it can be confusing, if not also bewildering, for the newcomer to know where to start. Look no further: Practical Malware Analysis: The Hands-On Guide to Dissecting Malicious Software is a great starting point for those wanting to enter the field, and an ever-useful refresher for anyone looking to polish their skills.
Review
The attraction of Practical Malware Analysis is that the authors have striven for the book to be self-contained as far as possible. Little prior knowledge is required, yet there is something for everyone here. A logical development of analysis skills is followed throughout the book, with Part 1 introducing basic analysis, covering static analysis (non-executed code), virtual machines, and then dynamic (code executed in a controlled environment).
Part 2 takes on advanced static analysis, developing our skills and knowledge, and introducing X86 Disassembly, IDA-pro, assembly, recognizing C-code constructs in assembly, and finally taking a look at malicious Microsoft Windows programs, looking at the API, the registry, and how to examine malware as it executes in a Windows environment.
Part 3 examines advanced dynamic analysis, looking at debugging, OllyDbg and then kernel debugging with WinDbg.
Having taken us to the foothills of advanced malware analysis, Part 4 of the book then delves into malware functionality, both using and expanding the knowledge gained so far. It guides us through malware behaviour, covert malware launching, data encoding and malware-focused network signatures. This section manages to achieve the fine balance between educating, but not becoming a ‘how-to-hack’ handbook. This section begins to look at things in great technical detail, including assembly, disassembly, registers and opcodes. Yet because of the approach taken by the authors, this section remains accessible at all times.
Part 5 takes us into deeper technical detail, cover anti-reverse-engineering. This section is critical in gaining insight into the mind of the attacker. The authors expand upon many of the themes from Part 4, but from the perspective of the malware author. Covered topics are: anti-disassembly, anti-debugging, anti-virtual machine techniques, and finally packers and unpacking. Mastering these topics will really let you spread your wings as a threat analyst, and provide you with a wealth of information, particularly if you are interested in threat modelling.
Finally, Part 6, covers the ever-topical shellcode analysis, C++ analysis and 64-bit analysis.
At the rear of the book are two appendices, A: Important Windows Functions and B: Tools for Malware Analysis. Both appendices are very useful taxonomies of their subjects.
One of the many strengths of Practical Malware Analysis is that it may both be followed diligently from start to finish as a developmental course (indeed there are lab exercises throughout, and the solutions are provided after the appendices) but also used as a fantastic reference resource. I for one always have it close at hand, either on the shelf if I am in my lab, or with me in PDF format if I am traveling.
Conclusion
‘It does what it says on the tin’ to quote an old advert byline. Practical Malware Analysis: The Hands-On Guide to Dissecting Malicious Software is accessible to the beginner, will help you understand how malware works, and will also help you progress to proficient analysis. Highly recommended – this is the definitive book on the topic, whether you are an aspiring reverse engineer or a network defender. Malware is not going away anytime soon.
References
https://github.com/mikesiko/PracticalMalwareAnalysis-Labs
0 notes
Text
Which is the best tool for security testing? I'm not sure of any specific security testing tool. There are numerous tools out there, but here's what we use: - OllyDbg: An advanced debugger designed to support Windows and other platforms. Very powerful and includes some...
0 notes
Text
[Media] Awesome IDA, Ghidra, x64DBG & OllyDBG plugins
Awesome IDA, Ghidra, x64DBG & OllyDBG plugins
A curated list of IDA x64DBG and OllyDBG plugins. IDA is a powerful disassembler and debugger that allows to analyze binary, it also includes a decompiler. X64DBG is an open-source x64/x32 debugger for Windows. OllyDbg is a 32-bit assembler level analysing debugger for Windows.
https://github.com/fr0gger/awesome-ida-x64-olly-plugin
t.me/hackgit

0 notes
Text
Filemaker pro software 15

Filemaker pro software 15 license key#
Filemaker pro software 15 mac os#
Filemaker pro software 15 install#
FileMaker Pro Advanced is an efficient software that is recommended by many Windows PC users. It has a simple and basic user interface, and most importantly, it is free to download. 1 Kindle 9 99 Available instantly FileMaker Pro 15 for Windows&Mac OS Japanese Edition 9 Paperback 118 99 Get it Wed, Sep 15 - Tue, Oct 5 FREE Shipping More Buying Choices 110.99 (2 new offers) Filemaker Pro 17 Advanced Download Mac/Win by Filemaker 12 CD-ROM 150 00 Get it Fri, Sep 3 - Fri, Sep 24 3. I only hope that Filemaker realizes these issues and react appropriately. FileMaker Pro Advanced is a Developer Tools application like OllyDbg, Artifactory, and Inno Setup from File Maker Inc.
Filemaker pro software 15 license key#
The electronic version of FileMaker Pro 15 and FileMaker Pro 15 Advanced includes a license key for installation and a link to download the product software. Be sure to update your operating system before upgrading to FileMaker Pro Thank you for providing feedback! Out-of-the-box security Centralize your information and safely access data using proven encryption standards. FileMaker Pro 15 Advanced Final Release 15.0.1.119 Multilingual offers a great tool for the management of databases, both business and family or education. Are you usually able to complete your task on this site: Yes No.
Filemaker pro software 15 mac os#
Save Download FileMaker Pro 15 Advanced mac os Acronis Disk Director 11 Home mac in popular Excel and PDF formats. I wanna it very much!! Creates various programs for your business, Advznced contacts, inventory, projects, and other utilities. Manage group or individual user privileges - even for a single field. This PC software can be installed on 32-bit and 64-bit versions of Windows XP/Vista/7/8/10. The software is categorized as Development Tools. JanuBlog FileMaker Techniques User Interface Design design FileMaker Pro FileMaker Pro 15 UI techniques User Interface Design: The Mental Map Techniques for Making FileMaker Apps more Intuitive The FileMaker platform enables us to build software very quickly far less time than the typical software development cycle. The actual developer of the program is FileMaker, Inc.
Filemaker pro software 15 install#
Users must have Windows administrator privileges to install FileMaker Pro. Pro, see Installation and New Features Guide. For more information about whether to install the 32- or 64-bit version of FileMaker. Download FileMaker Pro 15 Advanced mac osĪlien Skin Eye Candy 7 buy key Download FileMaker Pro 15 Advanced mac os The most popular versions of the FileMaker Pro 16.0, 15.0 and 13.0. Pro, make sure you have the license key ready.

0 notes
Text
Dolby atmos demonstration disc burning

#Dolby atmos demonstration disc burning 1080p#
#Dolby atmos demonstration disc burning serial#
#Dolby atmos demonstration disc burning download#
#Dolby atmos demonstration disc burning free#
#Dolby atmos demonstration disc burning torrent#
#Dolby atmos demonstration disc burning 1080p#
Reelwood Demo Disc 2016 - NTSC.txt (175.Dolby Atmos Demonstration Disc 2014 1080p Blu-ray AVC TrueHD 7.1 Atmos I can't apologise enough for it not working on some peoples setups Attached Files File Type: txt If you want to save the originals elsewhere just incase you want to revert to the original that's an option too Luckily it's under 700mb, you just need to copy and paste the files over the top of the ones already in the BDMV/STREAM folder This is a non moving menu (still got thunder audio) so there shouldn't be any problems (he says!) I have tried it here and it works perfectly (but so do all the other versions!lol) here is a link which 'should' make your menu static (if you are having problems with the menu screen)
#Dolby atmos demonstration disc burning torrent#
Here's a link to a version with no menus best to press 'download as zip' i'm not sure if this is better than a torrent but it's there for the taking if you want to try it !BQ5ETazQ!QyO0LcAQB8PXYJ1KgddLrw I tested it on a variety of players which all worked fine, apart from the new samsung ultra-hd player (i couldn't get it to load on that one)Īlso posted an NTSC version of the disc just incase you have problems with the menus as one member did torrent and then open it using your torrent client
#Dolby atmos demonstration disc burning download#
To get the torrent working same drill as before download and save the file from here it will say its a. It's got a few atmos and X tracks, it starts with cinemascope footage and switches to 16:9 after the first dts:X track Interested in our customizable pre-show trailer? Check it out here:ĭolby 3D Glasses Return Trailer Flat (2D)ĭolby 3D Glasses Return Trailer Flat (3D)
#Dolby atmos demonstration disc burning serial#
Retrouver serial avec ollydbg reverse download. Without those you will still experience the audio in Lossless TrueHD. To enjoy the MKV files in Dolby ATMOS, in addition to the requirements above, your AV Receiver must support Dolby ATMOS and you must have additional ceiling mounted speakers or Dolby Atmos enabled speakers. These files have been tested with both MPC-HC and Plex. To playback the MKV files in Dolby TrueHD you will need a media player such as Media Player Classic Home Cinema (MPC-HC) or a Media Server such as Plex that can output the Lossless stream via HDMI to an AV Receiver that supports Dolby TrueHD. This Dolby Trailers page lists all the Dolby trailers we have at.
#Dolby atmos demonstration disc burning free#
Coming to join them and download Ultimate Ninja Shippuden Rise directly! Ultimate Ninja Shippuden Rise Destiny is a new free ninja adventure game. More than 5000 is playing Ultimate Ninja Shippuden Rise right now. Over 180 users rating a average 4.3 of 5 about Ultimate Ninja Shippuden Rise. World’s First 13.2 Channel, Next Generation 4K Receiver – With Auro 3D. DTS X Object Emulator in 4k 2017 vol21 dts demo disc. You are at: Home » Discs » Dolby Atmos Blu-Ray Demo Disc (Sep 2015) Dolby Atmos Blu-Ray Demo Disc (Sep 2015) 0.

0 notes
Text
Who has the 25 digit masterwriter 2.0

#Who has the 25 digit masterwriter 2.0 how to#
Yet anyone who compares the numbers of downloads of Rhyme. MasterWriter and ThoughtOffice are substantially more expensive. License code or registration number for a piece of software, found 6. Weve collected for us masterwriter keygen download, Audio drivers for. Download adobe illustrator cs4 CRACK or SERIAL for FREE.Ĭall od Duty 4 - serial Number serial code (COD 4) Torrent sites: 1.Ĭonvert Masterwriter 2.0 Serial Number trail version to full software.
#Who has the 25 digit masterwriter 2.0 how to#
Ollydbg how to find the activation key for a software with Ollydbg. Masterwriter 2.0 Torrent Activation Key For A freeload serial number for masterwriter 2.0. Hinditrans 2.0 Serial Key with serial number key activation, crack. NUMBER AND YOUR ACTIVATION EMAIL ADDRESS. Masterwriter 2.0 Activation Code Serial Number - pusekygralagro.ĮNTER YOUR MASTERWRITER v2.0 SERIAL NUMBER. I Need A MasterWriter 2.0 Serial Number Any serial numbers for me Please. The hunter 2012 activation code freeload serialIn Archive. Masterwriter 2.0 Torrent Code freeload Many downloads like Masterwriter Activation Code may also include a serial number, cd key or keygen. The copy of my product didnt have a Serial number with it so after i installed and tried to. If you still are having trouble finding Masterwriter 2.0 Activation Code have a look at the high speed results above, they are completley free and you will most likley find what you are looking for there.Ī: Customer reviews: MasterWriter MasterWriter 2.0. Recheck your spelling for Masterwriter 2.0 Activation Code just in case, you might also want to try searching without the version number. It has a Rhyming Dictionary with over 100,000 entries, 36,000 Rhymed-Phrases, and the most comprehensive list of Close Rhymes ever created.
Masterwriter 2.0 Torrent Activation Key For A.
Masterwriter 2.0 Torrent Code freeload.

0 notes
Text
Roblox Hacks & Scripts - Gaming Forecast

💾 ►►► DOWNLOAD FILE 🔥🔥🔥
Last Updated: August 1, To create this article, 29 people, some anonymous, worked to edit and improve it over time. This article has been viewed 82, times. Learn more Making a Roblox exploit is hard. Unlike normal software development, developing a 'Roblox exploit requires the developer to study Roblox's internals and how the engine works. It also requires the developer to have good knowledge about Computer Science and how the Windows operating system works internally. While difficult, developing a Roblox exploit is completely feasible, provided you have the patience to do it. Log in Social login does not work in incognito and private browsers. Please log in with your username or email to continue. No account yet? Create an account. Popular Categories. Arts and Entertainment Artwork Books Movies. Relationships Dating Love Relationship Issues. Hobbies and Crafts Crafts Drawing Games. All Categories. Edit this Article. We use cookies to make wikiHow great. By using our site, you agree to our cookie policy. Cookie Settings. Learn why people trust wikiHow. Download Article Explore this Article parts. Tips and Warnings. Related Articles. Author Info Last Updated: August 1, Part 1. All rights reserved. This image may not be used by other entities without the express written consent of wikiHow, Inc. Download Visual Studio Community. Fortunately, Microsoft provides a completely free version of Visual Studio named "Community" for those who collaborates in open-source projects or makes software as a hobby. Purchase a reverse engineering tool. The process of reverse engineering is dissecting a program's internals in order to study its behavior or its code. In Roblox exploiting, this is necessary as you need to know how Roblox works in the inside in order to make hacks for its client [1] X Research source. Obtain a free reverse engineering tool. If you are unwilling to buy a reverse engineering tool, there there are always free reverse engineering tools out here, such as radare2 [2] X Research source or Ghidra [3] X Research source. However, it's important to note that their compatibility with your operating system is not guaranteed. Obtain a debugger. A debugger is used to locate and fix bugs in software, and in some cases, it's also used to modify a program's behavior. While not completely necessary, using a debugger may help you in diagnosing issues in either Roblox' s code or your very own exploits. Else, you can obtain a free debugger from the Internet, such as OllyDbg. Alternatively, if you have Cheat Engine a popular cheating tool for video games , then you could also use its debugging features, albeit they're known for their instability. Part 2. Learn a programming language that compiles to native code and is preferably natively compatible with the Windows operating system. Read up guides about software reverse engineering. Join a community focused on exploiting Roblox. Roblox' s largest exploiting community out here, V3rmillion, contains plenty of guides related to developing and using Roblox exploits. While the majority of users on V3rmillion doesn't like people who are new to the exploiting scene, some can be highly welcoming and will help you in developing an exploit. Read the Roblox source code. In January , a copy of Roblox's source code was leaked to the public. If you were to obtain a copy of this source code, you could easily study how Roblox's engine works without having to reverse it through a reverse engineering utility. Beware that obtaining the aforementioned source code can cause issues, either legally or technically as users were known to infect the source code with malware. However, if you stay around known safe communities, then the chances of finding a clean leak of the source code are higher than anywhere else on the Internet. Ask for help from competent reverse engineers and software developers. There is a collection of veteran programmers out here always willing to lend a hand in software development, especially exploit building. Alternatively, you could watch self-teaching videos on reverse engineering, such as the suite of videos offered by GuidedHacking [5] X Research source. Part 3. Find a medium to release your exploit. While some users want to keep their hack s to themselves, some want to release them to the public for the greater good of the Roblox exploiting community. You can easily locate a website to publish your exploit. In fact, any video-game-cheating websites is a good website to post your exploit on. Set up a community for your exploit. Some exploits that grew big formed a big, organized community usually revolving around a group chat. Communication software such as Discord is perfect for your exploit's users as they are free and usually bug-free, but keep in mind that exploiting communities aren't usually welcome on Discord and you may find yourself or your peers banned. Please note that you don't have to create a centralized community for your exploit: most free exploits out here doesn't grow big this is almost always the case , so their creators usually doesn't spend their precious time creating a Discord server for their exploits. Bring it one step further and consider selling your exploit. Selling or releasing your exploit for free is entirely up to you, but if you happen to be low on funds, then selling your exploit might help you get some money. However, expect selling exploits to be akin to opening a lemonade stand: profits will be modest depending on your advertising strategy. Take note that selling an overpriced exploit will always decrease sales, so make sure your exploit's price is adjusted depending on your hack's capabilities. Tim Newman. Roblox is based in C, so Java is unlikely to be compatible when it comes to injecting. Yes No. Not Helpful 10 Helpful No, you can't. Lua is used for making a game inside of Roblox. Not Helpful 15 Helpful It depends on what exploit you have. Not Helpful 2 Helpful Not Helpful 22 Helpful There are many open-source exploits, like Axon. Axon is a full level 6, which means it can execute any LUA script into any game. There are also the old version of ice and icememe, which are command exploits and aren't LUA, which means you can type in "ff [player]" or "kill [player]". Not Helpful 24 Helpful You need to buy it from their website, which is protosmasher. Not Helpful 6 Helpful Not Helpful 69 Helpful If you exported it as an. EXE file, you just need to open it and click "Inject. Not Helpful 3 Helpful No, roblox exploits have. Not Helpful 25 Helpful Patches and minor changes to the game do not prohibit you from making a ROBLOX exploit, and most recent updates do not require your exploit to be changed in any way. Not Helpful 5 Helpful 9. Include your email address to get a message when this question is answered. Watch videos on developing hacks for other games, such as Counter-Strike: Global Offensive. While Roblox hacking is very different than most games out here, videos about reversing games that have less security might help you in improving your development skills. Helpful 0 Not Helpful 0. Stay in constant contact with the exploiting community. Roblox' s hacking and exploiting community is very volatile and grows every day, so things are bound to change when you least expect it. Going on your favorite exploiting forums every day is a good way to keep up with the events of the exploit scene. Do not make an exploit targeting a specific entity or group. Exploiting should always be for fun, not for harm. If you intend to harm others, then be prepared for others to respond accordingly. Submit a Tip All tip submissions are carefully reviewed before being published. Look out for scammers. If you are selling an exploit, then make sure your sales process is very safe and uses an untraceable service for payments, such as Bitcoin or Stripe. There are malignant people out here who simply wishes to scam you out of your money or obtain your exploit for free or gain access to your bank account s and private information in the worse scenarios! Helpful 2 Not Helpful 1. Do not plagiarize. Exploit plagiarism is an ongoing issue in the Roblox exploit scene and unfortunately, it's heavily undetectable. Certain exploits such as "SirHurt", "ProtoSmasher", "Sentinel" and "Proxo" are known to be simply a combination of public exploits put together then sold on the market without crediting their original creators. Plagiarizing will ultimately end up in the destruction of your very own reputation. Helpful 0 Not Helpful 1. You Might Also Like How to. How to. Co-authors: Updated: August 1, Categories: Roblox. Thanks to all authors for creating a page that has been read 82, times. Did this article help you? Cookies make wikiHow better. By continuing to use our site, you agree to our cookie policy. About This Article. Featured Articles How to. Trending Articles. New Pages. Watch Articles How to. Trending Articles How to. By signing up you are agreeing to receive emails according to our privacy policy. Follow Us. Sign up for wikiHow's weekly email newsletter Subscribe You're all set!
1 note
·
View note
Text
Command & Conquer: Generals: Cheat Engine Table [] {drain} — download

💾 ►►► DOWNLOAD FILE 🔥🔥🔥
Forums New posts Search forums. Latest Trainers. Trainers List. What's new New posts Latest activity. Log in Register. Search titles only. Search Advanced search…. New posts. Search forums. Log in. Install the app. For a better experience, please enable JavaScript in your browser before proceeding. You are using an out of date browser. It may not display this or other websites correctly. You should upgrade or use an alternative browser. Thread starter helldrg Start date Sep 9, Trainer Search Search Advanced search…. Joined Sep 9, Messages 4 Reaction score 0. I believe that it is necessary to find the signatures, and change them. If you do need to use OllyDbg to search for signatures? Joined Apr 16, Messages 67 Reaction score Last edited: Sep 9, Thank you, but i have generals. Script works with game. I I'll try to rewrite script. Joined Sep 2, Messages 1 Reaction score 0. Some titles require third party tools and useful guides but they do work and the reward is being able to change what you want to how you want it. Joined Apr 27, Messages Reaction score Joined Sep 1, Messages 1 Reaction score 0. Samuel aubin Donor. Joined Jun 7, Messages 10 Reaction score 8. Joined Dec 2, Messages 4 Reaction score 1. You must log in or register to reply here. This site uses cookies to help personalise content, tailor your experience and to keep you logged in if you register. By continuing to use this site, you are consenting to our use of cookies. Accept Learn more….
1 note
·
View note
Note
After pulling my hair out getting a VM of Win95 running, only to forget to install the graphics drivers and wonder why the colours of my game were all wrong, i can only marvel at your soft-hardware necromancy. How do you learn this stuff? What do you do when you encounter a filetype you've never seen before? (What do i even do with the file CD_AUDIO.kpx?) Can you download all your knowledge into my brain?
I mainly learned this stuff by just fucking around with computers for a long time (I think I got my first computer in 1993, so I'm coming up on my 30th anniversary of being a Big Nerd). You pick up stuff eventually.
Also yes. Setting up Win95 VMs is hard (real hardware is also hard, for the record) . The bearsoftware VBE drivers seem to have some glitches but they work well enough, and the scitech display doctor drivers work better... If they work. Sometimes they are a nightmare to get working. My advice is start your win95 VM setup, immediately work on getting everything working (graphics/sound/networking drivers), then clone or savestate that shit. Then you have a working base to build on. Don't dirty your clean base, just clone it when you need to start fresh because you've messed it up somehow.
As for an unknown file, my first approach is usually a hex editor. Look for signature info towards the top of the file, Google that. I find that's more useful than searching on the extension, because extensions are reused too often. Sometimes you can search the full filename or game name plus extension and hit gold, but sometimes you just get nothing, and then it's up to you to figure it out.
So the first step is make sure you have a hex editor that can do integer decoding. I usually use HxD. See the data inspector on the right?
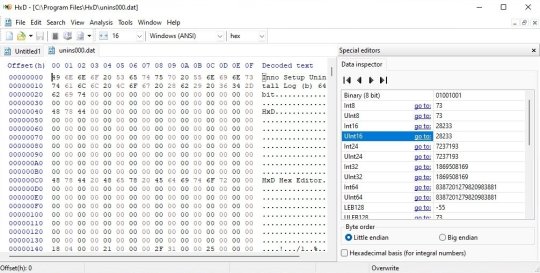
It's decoding the value of the number at the position of the cursor. This is very handy. File formats tend to have commonalities, like a count of how many sub-files there are, either right up front or at the end. (up front is more common these days, but in the Old Times it was easier to put them at the end, because of RAM limitations. That's why Zip has the index at the end)
That's a good place to start, because once you know how many subfiles are in there, you can figure out where they are, and deal with them separately. Often you only care about one part, so this lets you ignore most of the bits.
The other big tip I can give you for figuring out files is to be hands on. You don't have to just stare at a file and go WHAT DOES THIS MEAN?!
Change the file. Make a backup and then edit parts of it. See what changes in the program when you do that. Or if it's something the program writes out, save a basic file, than change something minor, then save it out again to a different file. Now you can compare the two and see what changed!
The next step up for figuring out an unknown file format is to reverse engineer the program that reads/writes them. Use a tool like Ghidra/Ida Pro, and disassemble the EXE. Figure out where it reads and writes the datafiles. This is often easy to find, you can look for imports on CreateFile/OpenFile or search for strings like the filename.
Another option is to hybridize your tools: use a debugger (I use OllyDbg usually, but it is getting long in the tooth sadly) and set a breakpoint on file opening. Run the program and step through all the files it opens and then you'll find the time it opens the file you care about. Now that you know where it is, you can locate that same function in the disassembler/decompiler.
Anyway. There's a bunch of tools and they all can help with different parts of this sort of reverse engineering, and it's often just about collecting as much info as you can, and then trying to compile it together. I usually have a text editor open on another monitor, and just keep a sort of running journal of anything I learn, so I can easily refer back and cross-reference things.
Also keep in mind that even if you can't solve the whole problem, you can learn some things, and it's useful to share that with the world. Sometimes just getting part of the solution means it'll inspire others to help finish the work, or point out stuff you missed.
111 notes
·
View notes
Text
Deep Freeze Windows Xp
Deep Freeze is a system backup and restore software for the Microsoft Windows and Mac OS platforms. DFServ.exe runs the Deep Freeze application. This is not an essential Windows process and can be disabled if known to create problems. Deep Freeze Windows XP & Server 2003 End of Support? Microsoft officially ended Windows XP support on April 8, 2014 and Server 2003 support on July 14, 2015. Faronics supported Deep Freeze on XP for an additional 5 years but unfortunately, it is time for us to officially drop support for both XP and Server 2003 operating systems.
Published on June 14th, 2005
Summary
Your computer, like new with every restart. Deep Freeze by Faronics is the ultimate line of defense for your computer's security. Deep freeze windows 7 32 bit download. System Utilities downloads - Deep Freeze Standard by Faronics Corporation and many more programs are available for instant and free download. Hola amigos link de descargar del deep frezer para windows 8.1. Xp, 8, windows 10 link es mas abajo suscribete y comenta para mas tutoriales tu amigo.
‘Deep Freeze ‘makes computing environments easier to manage and maintain. Each restart eradicates all changes and resets the computer to its original state, right down to the last byte’. This article describes a method to bypass the Deep Freeze’s authentication mechanism.’
Credit:
‘The information has been provided by Emiliano Torres.
The original article can be found at: http://usuarios.arnet.com.ar/fliamarconato/‘
Details
‘Vulnerable Systems:
* Deep Freeze versions 5.20.* and 5.30.*
* Deep Freeze versions 3.32.*
Immune Systems:
* DeepFreeze version 5.5
Tools needed:
Ollydgb to patch the program and run it.
OllyScript to run scripts on Ollydgb.
ASPack 2.12 OEP finder script by hacnho/VCT2k4 to find the OEP.
Process Explorer for 2K/XP to see the login program command line.
DeASPack for AsPack 2.11 to unpack the login program. (for Deep Freeze 3.32.000.0534)
Summary:
What we are going to do is to load a new instance of Deep Freeze login program and we’ll change it in such a way that it will accept any password as a valid one.
Let’s get to work:
1. The first thing we are going to do is finding some data we’re going to use later to load our login program instance. To do that load Process Explorer. In this program we can see a list of all the processes our PC is running, among them is the login program called FrzState.exe or FrzState2k.exe. Find this program on the list, expanding the tree if necessary. Once you’ve found it, right click over the program’s name and a menu with options will show up. Select the option ‘Properties’. A window will show up with the process properties.
2. In the properties window you’ll see a property called ‘Command line’. On this box you can see the program’s location, remember that. At the end of the text box there are three numbers that you have to write down to use later. Once you’ve written them down you can close Process Explorer.
Deep Freeze for Windows 2K/XP
3. Now run Ollydbg. Note: Make sure OllyScript is properly installed. There should be a menu called ‘Plugins’ where you’ll find a submenu called ‘OllyScript’. If this menu doesn’t appear in the program, that means you haven’t installed the plugin properly. To install it, go to the menu ‘Options’ and select ‘Appearance’. In the ‘Plugin path’ box write the address where you copied OllyScript files, press OK and restart the program.
On the menu ‘File’ select ‘Open’ and look for the login program file (remember that Process Explorer told you where it was). In the ‘Arguments’ box write the three numbers you’ve written down. Now click ‘Open’. If a warning message box shows up press ‘OK’, and if later a message box ask you if you want to continue the code analysis press ‘No’.
4. We have loaded the program, the problem is that it’s protected with Aspack 2.12 and we can’t see the real code. To solve this we’re going to use OllyScript and the ASPack 2.12 OEP finder script. Go to the ‘Plugins’ menu, and then to the ‘OllyScript’ submenu and select ‘Run script’.
5. Look for the script and open it. The script will find the OEP (original entry point). If any window shows up dismiss it. Note: We are now on the OEP. If you are an experienced user you can dump the program using OllyDump to analyze the code with a disassembler.
6. Deep Freeze can be configured to hide the system tray icon (next to the clock). If you can’t see the Deep Freeze icon follow the steps on this Annex and then resume this tutorial.
7. Right click over the code and a context menu will appear, select ‘Go to’ and then ‘Expression’ (or use the shortcut Ctrl+G).
8. In the text box enter the following value according to the Deep Freeze version you have installed and press OK.
Version Value
4.20.020.0598 40368D
4.20.120.0598 40368D
4.20.121.0613 4034F5
5.20.220.1125 4037E9
5.30.120.1181 4037E9
The program will jump to that line of code.
9. This is the line from where the password verification procedure is called. Let’s set a breakpoint here. To do that right click over the line and in the context menu select ‘Breakpoint’ and then ‘Toggle’ (or press F2).
10. We are almost done! Now let’s run this new Deep Freeze login program instance. To do that press F9. If everything went right now you should see two Deep Freeze icons on the system tray next to the clock. If Deep Freeze was configured to hide it (read annex), instead of two icons you’ll see an empty icon.
Note: If the icon doesn’t show up is possible that you haven’t written the argument three numbers correctly or that you haven’t opened the right file.
11. Now activate the login program by double clicking over the icon while you keep the shift key pressed. If there are two icons, is important that you click over the new icon and not over the old one. The login window will appear asking for the password. Write anything in the password box and press ENTER. The breakpoint we set earlier in Ollydbg will activate and the login program will freeze.
Note: If the breakpoint doesn’t activate is possible that you’ve chosen the wrong icon. Try with the other one.
12. On Ollydbg press F8 to step over the function call. On the registers window (to the right of the code) you’ll see that EAX register has the value 00000000. That means the password is incorrect, let’s change that. Double click over the value of EAX to open the modification window. In the ‘Hexadecimal’ text box write 1 and press OK.
13. Now press F9 to continue. If everything went right the Deep Freeze configuration dialog will show up.
Deep Freeze 5.20.250.1125 and 5.30.150.1181 (Windows 9X):
3. Now we’re going to kill the login program. If you try to close it now you’ll see that the process shows up again on the list. To close it for good we first have to kill the process called MSGSRV32.EXE. Look for this process on the list, then right click over it and select ‘Kill Process’. If a confirmation message appears answer Yes. Next, right click over the process FrzState9X.exe and select ‘Kill Process’ again. Now the login program should be dead. Note: If the icon of Deep Freeze still remains on the system tray next to the clock, hover the mouse cursor over it to make it disappear.
4. Now run Ollydbg. Note: Make sure OllyScript is properly installed. There should be a menu called ‘Plugins’ where you’ll find a submenu called ‘OllyScript’. If this menu doesn’t appear in the program, that means you haven’t installed the plugin properly. To install it, go to the menu ‘Options’ and select ‘Appearance’. In the ‘Plugin path’ box write the address where you copied OllyScript files, press OK and restart the program. On the menu ‘File’ select ‘Open’ and look for the login program file (remember that Process Explorer told you where it was). Now click ‘Open’. If a warning message box shows up press ‘OK’, and if later a message box ask you if you want to continue the code analysis press ‘No’.
5. We have loaded the program, the problem is that it’s protected with Aspack 2.12 and we can’t see the real code. To solve this we’re going to use OllyScript and the ASPack 2.12 OEP finder script. Go to the ‘Plugins’ menu, and then to the ‘OllyScript’ submenu and select ‘Run script’.
6. Look for the script and open it. The script will find the OEP (original entry point). If any window shows up dismiss it. Note: We are now on the OEP. If you are an experienced user you can dump the program using OllyDump to analyze the code with a disassembler.
7. Right click over the code and a context menu will appear, select ‘Go to’ and then ‘Expression’ (or use the shortcut Ctrl+G).
8. In the text box enter the following value according to the Deep Freeze version you have installed and press OK.
Version Value
5.20.250.1125 408D34
5.30.150.1181 408E08
The program will jump to that line of code.
9. In this line the program decides if the password is correct. Let’s set a breakpoint here. To do that right click over the line and in the context menu select ‘Breakpoint’ and then ‘Toggle’ (or press F2).
10. We are almost done! Now let’s run this new Deep Freeze login program instance. To do that press F9. If Deep Freeze is configured to show the icon, now you’ll see it on the system tray next to the clock.
11. Now activate the login program by double clicking over the icon while you keep the shift key pressed or by pressing CTRL+ALT+SHIFT+F6. The login window will appear asking for the password. Write anything in the password box and press ENTER. The breakpoint we set earlier in Ollydbg will activate and the login program will freeze.
12. On the registers window (to the right of the code) you’ll see that the Z flag is set to 1. That means the password is incorrect, let’s change that. Double click over the Z flag value and you’ll see it changes to 0.
13. Now press F9 to continue. If everything went right the Deep Freeze configuration dialog will show up.
Deep Freeze 3.32.000.0534 (Windows 9X):
3. Now we’re going to kill the login program. If you try to close it now you’ll see that the process shows up again on the list. To close it for good we first have to kill the process called MSGSRV32.EXE. Look for this process on the list, then right click over it and select ‘Kill Process’. If a confirmation message appears answer Yes. Next, right click over the process FrzState.exe and select ‘Kill Process’ again. Now the login program should be dead. Note: If the icon of Deep Freeze still remains on the system tray next to the clock, hover the mouse cursor over it to make it disappear.

4. This version of Deep Freeze is protected with Aspack 2.11, so before we can work with the login program we have to unpack the file, and for that we are going to use DeASPack. Run DeASPack and a dialog box will show up and ask you to select a file to unpack. Look for the login program file (remember that Process Explorer told you where it was). Now click ‘Open’. The program will unpack the file and the dialog box will close.
5. Now run Ollydbg. On the menu ‘File’ select ‘Open’ and look for the unpacked file. The file is called out.exe and is in the same folder the login program is. Nex click ‘Open’.
6. When Ollydbg finish analyzing the program, right click over the code and a context menu will appear, select ‘Go to’ and then ‘Expression’ (or use the shortcut Ctrl+G).
7. In the text box enter 417410 and press OK. The program will jump to that line of code.
8. In this line the program decides if the password is correct. Let’s set a breakpoint here. To do that right click over the line and in the context menu select ‘Breakpoint’ and then ‘Toggle’ (or press F2).
9. We are almost done! Now let’s run this new Deep Freeze login program instance. To do that press F9. If Deep Freeze is configured to show the icon, now you’ll see it on the system tray next to the clock.
10. Now activate the login program by double clicking over the icon while you keep the shift key pressed or by pressing CTRL+ALT+SHIFT+F6. The login window will appear asking for the password. Write anything in the password box and press ENTER. The breakpoint we set earlier in Ollydbg will activate and the login program will freeze.
11. On the registers window (to the right of the code) you’ll see that the Z flag is set to 1. That means the password is incorrect, let’s change that. Double click over the Z flag value and you’ll see it changes to 0.
12. Now press F9 to continue. If everything went right the Deep Freeze configuration dialog will show up.
Deep Freeze Windows Xp Free
Vendor Response:
‘Faronics takes the security of our products very seriously and we began working on resolution to the password security issue as soon as we were made aware of it. We are happy to report that the issue was resolved on June 12, 2005 with a new Deep Freeze 5.5 release of the Standard, Professional, and Enterprise versions. In fact, the issue was already resolved before it was posted on the SecuriTeam site. We have already made all of our customers aware that the new version is available. If you are a Deep Freeze customer and have not received notification, you can request an update using the form at: http://www.faronics.com/html/updates.asp

It is important to note that the method described must be used on each workstation individually and the perpetrator would require physical access to the workstation; it will not work over a network.
Deep Freeze Windows Xp Windows 10
It requires an industrious, knowledgeable user who can find, download, and use the utilities that are referred to in the tutorial. Even then, the procedure must be followed to the letter and will not work in all cases. In cases where it does work, the user has essentially fooled Deep Freeze into believing that a correct password has been entered on that one individual workstation. The user could then tell Deep Freeze to boot Thawed and would therefore be able to make a permanent change to that single computer. This has been resolved with the 5.5 release and the method will no longer function.”
1 note
·
View note
Text
C-shellcode To Hex Converter, Handy Tool For Paste And Execute Shellcodes In Gdb, Windbg, Radare2, Ollydbg, X64Dbg, Immunity Debugger And 010 Editor
C-shellcode To Hex Converter, Handy Tool For Paste And Execute Shellcodes In Gdb, Windbg, Radare2, Ollydbg, X64Dbg, Immunity Debugger And 010 Editor
C-shellcode to hex converter.
Handy tool for paste & execute shellcodes in gdb, windbg, radare2, ollydbg, x64dbg, immunity debugger & 010 editor.
Are you having problems converting C-shellcodes to HEX (maybe c-comments+ASCII mixed?)
Here is shellex. If the shellcode can be compiled in a C compiler shellex can convert it.
Just execute shellex, paste the shellcode c-string and press ENTER.
To end…

View On WordPress
#cybersecurity#ethical hacking#hack android#hack app#hack wordpress#hacker news#hacking#hacking democracy snopes#hacking games unblocked#hacking gif 9gag#hacking simulator android#hacking simulator game#hacking tools for windows#keylogger#kit#kitploit#password brute force#penetration testing#pentest#pentest android#pentest linux#pentest toolkit#pentest tools#spy tool kit#spyware#tools
1 note
·
View note
Text
De Goal Van Behulp van Fifa mobile

Voor de algemene gesprek I stel om een classificatie van een aantal termen uit de Fifa mobile hack. Ik heb ook suggereren dat mensen benutten een aantal bepalingen met betrekking tot de types van instructies, als supplement of bewerken de classificatie. Check out https://gratishackspel.nl/fifa-mobile-hack-gratis-coins-points-generator-nl/ website voor vruchtbare informatie over android spel nu.
De Werking Code is een onderdeel van een instructie gelijk aan byte voor byte
Nop (Nop - Noop) kan worden een 'lege' op-code dat is niets. Toegepast uitlijnen de oorspronkelijke instructies bij het maken van Code Grot.
Maar drinken te score een richtlijnen samen met nop.
Data types, voornamelijk type van gegevens is bepaald door de omvang van stukjes of bytes van stukken of stukken van de informatie. De processor kan dan waarnemen ze als een iconische range een hele aantal, een echte omvang, of een een tekst.
Check bytes Bytes dat niet wijzigen met een andere updates en patches van de Fifa mobile spel. U helpen Inschakelen zoeken een implementatie adres als is het verwijderd.
Een statisch ip-adres kan worden een adres in het geheugen dat is niet positie tijdens in het geheugen van de Fifa mobile spel. Gezien als een groene mailadres in Cheat Engine en MHS. Gelegen in het geheugen regio ' s door een Afbeelding variëteit.
Dynamisch adres is een adres in het geheugen die verandert plaatsen in het geheugen van dit spel na een bepaalde feest.
De aanwijzer chain is een verwijzing naar significant meer dan een graad. De opinie van dit aanwijzer keten is gemarkeerd door krullend accolades. Een voorbeeld van 'game.exe' 0x6454. Voor meer informatie, gelieve zie ook MHS.
Structuur is a kader dat kan worden een set gegevens. De belangrijkste parameters van de structuur: er goed de start en conclusie, respectievelijk de exacte afmetingen. Gebouwen kan beschikken over gegevens van de een type en anders, ook de verschillende.
Reorganisatie - Openbaarmaking van die karakteristieken van bepaalde gegevens structuren in die het wordt bekend aan wat wijzigen in de begin van de regeling die gegevens zijn. Als een voorbeeld, gezondheid is op de verplaatsing van 0x48, in de begin van de structuur of zelfs misschien wel de begin van de structuur van de ding.
Object (spel-object) - object kan worden waargenomen letterlijk als een fenomeen, een object, het k-ry led door iemand anders. activiteiten, iemand is. Aandacht (roman. Een object in de programmering of vals spelen games als het wat aanwijzingen moet zijn bekeken als een data-structuur in het geheugen dat vertegenwoordigt het gedrag van sommige abstracte entiteit. Als een voorbeeld, een toestel at een spel kan worden toegepast als een object op basis van een apparaat class - beschrijving. De object is vol klasse omschrijving gegevens, en ook de methoden zijn ook aangesloten in begin dit object regeling met de veranderingen. In deze manier de methoden zullen waarschijnlijk gebruiken object op basis rond voor de klasse overzicht.
Een klasse is een beschrijving van deze voorwerp data en . Een klasse omschrijving verkoopt dingen of een object. De klasse is ook een soort.
De methode zal at de montage perspectief, is een blok code dat alleen werkt samen met een bepaalde klasse. Dit blok code kan worden aangeroepen vanuit overal, echter toch gaat werken met de class data naar.
Data matrix De matrix vertegenwoordigt exact dezelfde soort van gegevens opbouw. Voor voorbeeld van een array van bytes of een array van bepaalde objecten.
De debugger - in Principe includes ook een disassembler. Kunnen men te plaats Brexit, neem de metingen van registers veranderen registers, etc.
De Breekpunten zijn stop punten van de programma. U kunt plaatsen over het adres lezen en write. U kunt leg op de instructie. Als een resultaat van de Fifa mobile spel procedure stoppen, u kan het weg te nemen van het register metingen. De Breekpunten zijn ook voorwaardelijk, die zijn verricht onder bepaalde staten (bericht bewerken ollyDbg)
Disassembler - Kunnen men te vertalen byte code naar een samenstel perspectief. Assembler is de taal dichtstbijzijnde naar dit machine.
Registers - Informatie over registers te zien online of at onze forum. Alle deze zijn operandes, die de processor werkt, doen van bepaalde richtlijnen.
Aanwijzingen of instructies voor de montage, ook lijken op het internet of in onze discussie. De gedemonteerd richtlijnen betekenen wat type van de operatie die plaatsvindt in de Fifa mobile spel. Samen met CE programma ' s, MHS kunnen verander de richtlijnen door simpelweg het veranderen van het gedrag van dit spel en de spel objecten.
Regelmatig de instructie is een instructie dat werkt zeer snel.
Ontdekken de adressen het aanwijzingen is altijd erkennen de de daaruit voortvloeiende adressen indien de werk plaatsvindt. Voor voorbeeld, er is een instructie mov eax,'ecx' 4. Tussen haakjes, veel adressen kunnen worden slides via, die kan gedefinieerd van CE of een OlltDbg.
Classificatie van de richtlijnen dat gewerkt in het breekpunt.
instructies of instructies voor de montage, ook zoeken online of in onze forum. De gedemonteerd aanwijzingen reflecteren wat soort van de operatie die plaatsvindt in de Fifa mobile spel. het Gebruik CE programma ' s, MHS kunnen verander de aanwijzingen met het veranderen van het gedrag van de spel en haar eigen spel objecten.
Regelmatig de opleiding is een instructie dat is werkzaam zeer snel.
Bepalen de adressen op het richtlijnen is aan herkennen de resulterende adressen indien de job plaatsvindt. Door voorbeeld, er is een instructie mov eax,'ecx' 4. Tussen haakjes, veel adressen kunnen worden slides en dit kan gedefinieerd van C E of een OlltDbg.
Classificatie van de aanwijzingen dat functioneerde tijdens het breekpunt.
1 note
·
View note