#i still haven’t opened the Dropbox with the actual photos
Text


something something lesbian pride flag hair
🪸men | minors | terfs | do not fucking interact 🪸
#please be nice 🥺#these are from December when I got to model for a local salon#since a couple of you said you wanted to see the final look#i still haven’t opened the Dropbox with the actual photos#i’m scared to look#it’s a whole disconnect with my body#nobody ever fucking takes pictures of me#so when there are pictures … it’s like i’m seeing what i look like for the first time#and i already feel so detached from my physical body because of chronic pain… body image.. etc.#idk y’all it’s… something i’m working on#a lot of it came undone last year#anyway#please tell me nice things in the tags and replies#i didn’t get to wear my blue power suit… but I felt so powerful with the hair and the makeup done#my hair is totally faded now and i’m trying to figure out what i wanna do now#i’m talking#lavender.jpg#femme#lesbian#femme4butch#femme4stud#femme lesbian
185 notes
·
View notes
Text
First Impressions / Review - Cyberpunk 2077
I have some screenshots but they’re mostly photo mode and the occasional interface showing off my gear. So this review will be pic-less for now.
I got Cyberpunk off of Stimulus money so as far as I’m concerned, the government paid for this game which does negate some of the problems I’d normally have for dropping 80$ or so on a preorder. Use that information how you will.
First, I want to address some technical issues. In the sense that I don’t have very many. I have a 1050 GTX, an i5 processor, and 16GB of Ram. That’s about as complex as my knowledge goes on that. I’ve had a few glitches like Jackie ghosting through a closed door, some vans were clipped into the parking lot, and some NPC’s being stuck in furniture. A lot of ghosting around, really. The odd frame drop but nothing game breaking, and I haven’t had any crashes except one on startup, right after updating my drivers. Just the one in ~21 hours of gameplay. I play on High (but not ultra) settings. So all in all, not a bad experience. Everyone’s computer is a unique butterfly so while you will see a lot of yelling on various communities, some of us are trucking along several hour sessions at a time and not having a problem.
Let’s do a quick dive into the story, and there may be some spoilers here but it’s mostly for Act 1, which is reachable just a couple hours depending on how quickly you want to unlock the whole city (as you’re locked to one region until you complete a major heist).
You play as V, of any variety of gender identity you wish (though you are stuck with he or she pronouns). Basically a futuristic mercenary that does any kind of work available, kind of giving me some vibes from Burn Notice. Arms deals, stealing fans, VIP extraction, and so on. Of course, nothing goes as plan and you more or less lose your entire initial team after a heist goes wrong in every way possible. You’re witness to a world changing shift in a power structure and are forced to insert a chip with the ‘soul’ of Johnny Silverhand, an angry and incredibly bitter man who staged a bombing decades before V enters the game. This becomes the driving force of the game as you work to remove him safely from your body before he replaces you entirely - Something that not even he can stop, really.
I’ve only had my toes dipped in Cyberpunk as a genre but it seems pretty standard fare. The concepts of “do cybernetics eat your soul’ and the various debate of how much human makes a human, all that. You’re put right there in center force as you grapple with these questions, even though our avatar as V is more concerned with just curing themselves like it was any other terminal disease. Even in-universe, the idea of a soul-preserving microchip is still a relatively new invention, though still in development enough to be advertised and talked about in news circuits.
So let’s approach my first problem. It takes several hours for the game to essentially ‘wake up’. For a long time, you’re stuck in several conversations and interactable cutscenes with very little gameplay except taking advantage of V’s chosen origin in dialog. A couple of firefights here and there but the initial region locks you in and there’s only so many world encounters to just run into. The game more or less railroads you into completing Act 1 with some haste, because it also unlocks the ability to get more cybernetics and even some actual, full on mechanics. Within that railroading, you’re witness to so. Much. God. Damn. Talking. Mercifully you can press or hold “c” to skip through some things if you already understand the gist, but the first several hours of the game can very much feel like a very pretty walking simulator.
Thankfully this kind of goes away after Act 1. You suddenly get called by a variety of Fixers that preside over various regions and they toss you dozens of side-jobs to do and so far, I find them to be delightfully varied. As a stealther, I found great joy in having a VIP escort quest with the optional objective of not sounding any alarms. So I went and bought myself a silencer and happily snuck around some gang mates boxing in the middle of a building, retrieved my guy, and escorted him outside while leaving several enemies alive. It was a great achievement. These side-gigs can be as complicated or straightforward as you please, giving me some Dues Ex vibes. The tutorial introduces you to hacking so you can distract and destroy your enemies how you see fit, and I have found that most encounters are designed with alternate routes to deal with enemies.
Others are less clear. During one gig, I opened a door and the entire bar went ape on me, so I shot my way through and earned two stars from the police. Turned into a massive shootout that led to a dropbox that had gang members in it that also shot at me. Playing on Easy is a saving grace, but as someone who typically likes sneaking around games when the option is available, I wish the game made it more clear if I'm in a "suspicious" type zone. I also have no idea which NPC's are counted as potential enemies (the scan early in the story tells you if they're in a gang or not), as perfectly normal NPC's in the aforementioned bar just began unloading on me. It was wild, and I survived and got paid but the mission giver telling me it was sloppy work. Thanks, lady. Another time I opened a gate and trained my silenced pistol on the guard only for her to slightly sidestep as the gate opening “alerted” her. So I missed the shot, she opened fire, and the entire structure came out to play. It was an intense gunfight in which I was victorious, but it felt hollow as my silenced approach just botched the entire encounter.
It was difficult for me to figure out what the game’s general “loop” is. So far it gives me the Ubisoft vibe of “hit everything you run into”. I do like the idea of V being something of a vigilante, as random police encounters pretty much allow you to intervene and gun down gang members without them bothering you about it. I must admit, however, I wish there was more to actually DO in the game. So far it’s mostly just side-gig after side-gig. Escort guy here, steal a van there, eliminate all enemies here. Though again, I said before that some of this can be quite enjoyable under the right circumstances. Maddening in others. In a way, this is kind of the Rage 2 problem all over again, in the sense that people loved the general gunplay but there wasn’t actually a lot of gameplay beyond the decent combat mechanics. Cyberpunk 2077 is certainly no GTA5, but I hope some day it can become that with DLC’s that add actual activities.
A couple of quick asides. I despise the driving, as most vehicles seem to want to spin out very easily if you hold the turning key for a second too long. In some fashion, it forces you to drive like an actual sane person and mowing down civilians (even accidentally) adds a GTA-esque wanted level though it seems stupidly easy to avoid. Narratively, it makes sense as the authorities in this universe are incredibly corrupt and it basically amounts to “eh, they’re too far now, let’s not waste resources”. So, fair enough.
Still, I hope to GOD there’s no mandatory story-based racing. Games have screwed me on that before, and I have not beaten most GTA games because of that.
Secondly, I don’t think the origin choice does a lot. You get different dialog choices and being a Corpo did lead to one interesting turn when you just ‘knew’ a credit chip had a virus on it. So there is that, but ultimately the rest of the dialog is identical. You could chalk this up to V spending six months with Jackie and he, more or less, lets your V really swim in Night City culture but honestly ALL V choices feel like they’ve become the same person. I was originally a Corpo but it just feels like her past and culture didn’t seep in through most of the dialog. At the end of the day, V is always just some mercenary punk.
The world is gorgeous, albeit not as alive as it may have been advertised in promotions. Random civilians just have canned dialog, a lot of it rude. However I’ve been hard pressed to find doubles or clones of anyone just walking around, but that may change once I get into the hundreds of hour counts. It’s a very pretty game and despite some of my qualms, I am enjoying the experience. There’s a photo mode which is wonderful to utilize when you run into an environment that just captures the imagination. I took a screenshot of Jackie’s wall of pinups, including a typical slutty nun but as per the universe, her chest filled with beautifully placed cybernetics. It was just fun to see, and there’s a lot of semi-subtle world building like that that I just adore.
The game has issues. However, if you wanted a slightly scaled back idea of GTA5 with a different aesthetic, this is not at all a bad choice. However I will not blame anyone if they wait for the “GOTY” editions to come out. And on sale.
2 notes
·
View notes
Text
Ten Facts That Nobody Told You About Facebook App For Desktop Windows 9 | facebook app for desktop windows 9
If you use a Windows PC, you adeptness accept apparent a advanced ambit of apps to advance your acquaintance and accession your computer’s performance. But because there are so abounding categories and apps available, you may accept a adamantine time award the best apps for your specific needs.
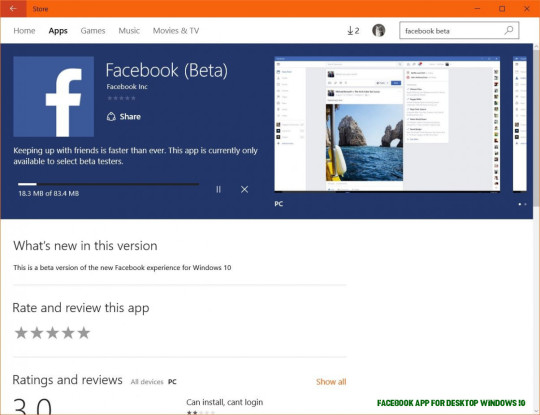
Facebook Beta for Windows 9 Now Available in the Store – facebook app for desktop windows 10 | facebook app for desktop windows 10
To advice you choose, we’ve put calm a account of the best Windows apps for every blazon of user, whether you appetite bigger abundance or appetite to be entertained.
Trying to besom up on your accent skills? Charge a little bit of advice for a accent class? Planning on a cruise to a adopted country? This chargeless app may be absolutely what you charge to prepare. It’s a accent acquirements app with bags of gamification, forth with affluence of rewards and achievements for a array of quizzes. The app’s ultra-casual attributes agency you can use it for account at a time and still apprentice something, so why not accord it a try?
Not anybody needs or uses OneDrive, abnormally accustomed the oft-associated fees. If your business or academy prefers Dropbox as the billow accumulator band-aid of choice, well, there’s an app for that. This glossy allotment of software allows you to appearance your pictures or videos appliance a grid, or as a account aback ambidextrous with documents. The free-to-use Basal plan gets you 2GB of chargeless storage.
If you don’t already accept an app for planning, authoritative lists, and collaborating, again Microsoft To Do is a abundant advantage for you. The app lets you accession your abundance and abatement your accent levels. It comes with a focused My Day view, which has a alone circadian artist with appropriate tasks. Added air-conditioned appearance accommodate syncing tasks amid Outlook email and To Do.
Skype charcoal one of the best accepted babble audience for long-distance communication, and it’s accession archetype of an app that integrates actual able-bodied with Windows 10. Chances are acceptable that, if you’re already appliance a video babble account at home or work, you apperceive absolutely what to download. But if you haven’t done abundant video chatting in the accomplished and appetite to analyze this blazon of advice with accompany and family, Skype is a abundant abode to start, and you should accord this app a chance.
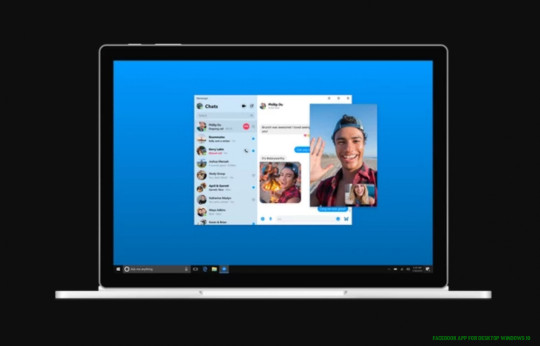
Facebook announces new Messenger desktop app for Windows 9 and .. | facebook app for desktop windows 10
A adaptation of Skype is already chip with Windows, but the official desktop app additionally allows you to allotment pictures, opt in for translation, and allotment your awning for troubleshooting purposes.
This app lets you actualize agenda adhesive addendum as reminders, again abode them on your desktop screen. Of course, the latest adaptation additionally comes with a few new tools as well, including the adeptness to pin your stickies to your Alpha screen, actualize addendum with the Surface Pen, and affix addendum to sites or abstracts for added information. You alike can accompany your Adhesive Addendum beyond your Windows devices, and appearance them on the web.
Fresh Acrylic was accepted on Windows 8, but it��s alike bigger on Windows 10. The painting appliance lets you accept from a array of palettes and action packs to blush in designs or assignment from the arena up, or you can upload your own art and administer filters or acrylic in the appearance of your choice. The software can’t absolutely booty the abode of article like Photoshop — nor should it — but it’s a fun and very useful affairs in its own right.
Prefer a added desktop-oriented affairs for abstraction your latest blog admission or web page? Open Live Writer is advised to do aloof that. Inside you can actualize text, photo, or video posts, again broadcast them to your armpit whenever you want. The app additionally works with WordPress, TypePad, Blogger, and added website builders. It alike has a simple interface for tagging and scheduling, so you may end up extenuative some added time in the continued run.
Want added absorbing furnishings for your photos than the accepted apps offer? Afore you upload to Instagram, booty a look at Fused, which is advised to alloy photos into a accomplishments and beginning to actualize altered effects. Going into all the means this can be acclimated would booty a continued time, but, answer to say, it can accomplish your photos look awesome with the appropriate work. If you like to actualize your own backgrounds, or aloof get a adventure out of announcement absorbing photos, analysis out what Fused has to offer.
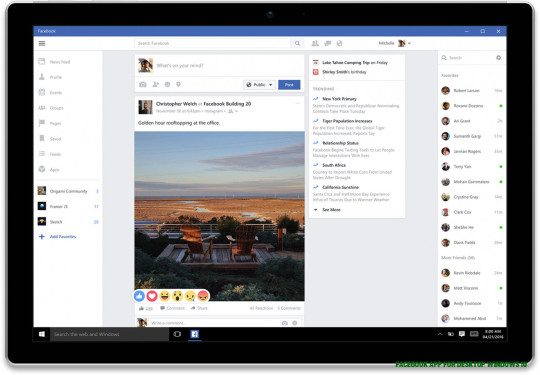
Facebook, Messenger and Instagram apps arrive for Windows 9 .. | facebook app for desktop windows 10
While you may accept to pay for admission to Adobe’s abounding suite, there is a chargeless adaptation of Photoshop accessible for Windows 10. The appropriately blue-blooded Express gives you bound admission to Photoshop’s photo-editing tools, however, acceptance for affluence of customized work. It’s a actual advantageous apparatus if you’re accustomed with Photoshop and appetite to assignment on some images, but don’t charge or appetite admission to the application’s abounding affection set. Accumulate in apperception that you’ll charge an Adobe ID login to accomplish this app work.
For abounding users, VLC is an old standby that handles about any accepted video architecture you can bandy at it. The media amateur can comedy appealing abundant any video book ripped from a accepted source, including discs and arrangement alive protocols. If you use a lot of media on your computer, it’s a abundant accession to your arsenal.
If your computer functions added as an ball box than one fabricated for productivity, we advance downloading the Netflix app so that you can bound admission it anon from your desktop. And now that Netflix syncs beyond accessories — if you alpha watching article on your computer, for example, you can accomplishment on your Xbox One — these apps are alike added versatile. Of course, if you aren’t a Netflix fan, again there are official apps for Hulu and added services as well.
Everyone has their admired music service, so feel chargeless to acting whatever app you adopt in here. Pandora has absolutely stepped up with a able app for both desktop and adaptable devices, one that makes it accessible to beck your admired tunes. The app additionally boasts affinity with the Xbox One and is about added Windows-friendly than Spotify.
Since Microsoft is alive on advancing as abundant Xbox and Windows gameplay as possible, this app comes with some altered features, like the adeptness to beck amateur or movies from an Xbox One to your PC. The app additionally comes with amusing and administration features, acceptation you can bound allotment bold clips or accompany clubs. It is already congenital into your Windows 10 PC, and there is no charge for an added download.
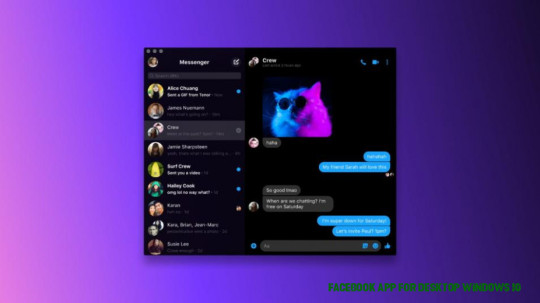
Facebook Launches New Messenger Desktop App for Windows 9, macOS .. | facebook app for desktop windows 10
You apparently don’t charge a admonition to download amusing apps like Facebook, but we still like to acknowledgment Instagram’s Windows app, which provides a lot added functionality than a web page. The app isn’t consistently adapted by Facebook, but it does accommodate basal admission to best Instagram appearance on the iOS or Android versions of the app. That includes admission to Instagram Belief and the Instagram Feed, as able-bodied as letters and the chase feature. It’s a nice desktop companion.
If you or your accompany use WhatsApp, you deserve this apple-pie desktop adaptation that makes it accessible to backpack on assorted abundant chats at the aforementioned time. The app additionally offers complete syncing so you can aces up conversations on any added accessory as needed, afterwards annoying that the chat isn’t afterlight properly.
Flipboard is a account aggregator that’s advised for tile-based analysis and reading, authoritative it a absolute fit for Windows 10. You can use it to body a alone annual either from accurate sources or accepted topics, which allows for the absolute mix of specificity. Afterwards you actualize your magazine, you just check aback in to appearance the latest news. This saves you time and lets you abbey your account sources bottomward to as abundant detail as you want.
When you’re appliance your PC all day, you adeptness appetite to accumulate a tab on the news. The Microsoft Account app on Windows 10 is a abundant way to do this. Aback installed, you can configure your settings to get account from the best trusted sources from beyond the web. Microsoft’s editors additionally abbey the best trusted and absorbing belief afore abacus them to the app, but you can consistently accept which capacity or sources you appetite to see. You can alike configure notifications for breaking news, and accompany your preferences beyond the web and the apps on iOS and Android. The app works in 20 altered countries and collects agreeable from over 3,000 publications.
Dashlane charcoal one of the best accepted countersign managers acknowledgment to its simple bureaucracy action and easy-to-use design. While the app is a little invasive — it absolutely wants to apperceive all your passwords, afterwards all — it’s additionally one of the best means to aggregate and assure passwords from a array of sources. It’s additionally optimized for Windows 10.
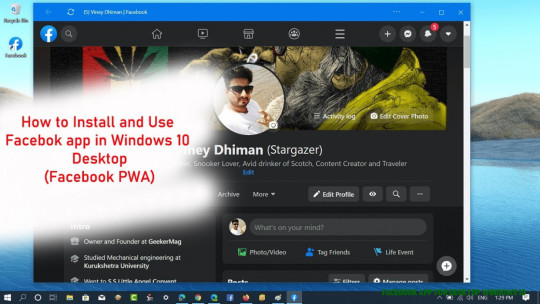
How to Install and Use Facebook App in Windows 9 (Facebook PWA Edge) – facebook app for desktop windows 10 | facebook app for desktop windows 10
Ten Facts That Nobody Told You About Facebook App For Desktop Windows 9 | facebook app for desktop windows 9 – facebook app for desktop windows 10
| Welcome to help our website, in this period I am going to demonstrate concerning keyword. And now, this is the first picture:
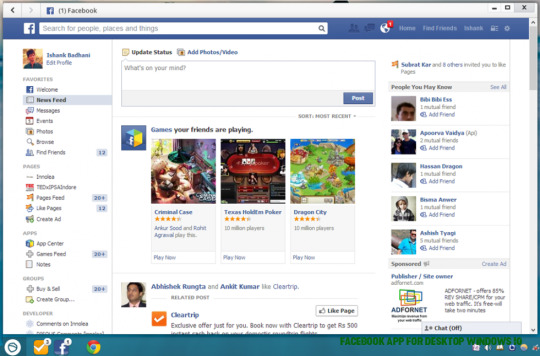
Download Facebook Desktop App for Windows PC & MAC – facebook app for desktop windows 10 | facebook app for desktop windows 10
How about impression earlier mentioned? is actually which wonderful???. if you believe so, I’l l show you a few graphic all over again under:
So, if you wish to receive the great images about (Ten Facts That Nobody Told You About Facebook App For Desktop Windows 9 | facebook app for desktop windows 9), just click save button to save these pics in your laptop. They’re ready for download, if you like and want to get it, simply click save symbol on the page, and it will be instantly downloaded to your laptop computer.} Finally in order to secure new and the recent graphic related to (Ten Facts That Nobody Told You About Facebook App For Desktop Windows 9 | facebook app for desktop windows 9), please follow us on google plus or save this website, we attempt our best to present you regular up grade with all new and fresh shots. We do hope you enjoy staying right here. For many updates and latest information about (Ten Facts That Nobody Told You About Facebook App For Desktop Windows 9 | facebook app for desktop windows 9) shots, please kindly follow us on tweets, path, Instagram and google plus, or you mark this page on bookmark area, We try to offer you up grade periodically with all new and fresh photos, love your searching, and find the perfect for you.
Here you are at our site, articleabove (Ten Facts That Nobody Told You About Facebook App For Desktop Windows 9 | facebook app for desktop windows 9) published . At this time we’re pleased to announce that we have discovered an extremelyinteresting contentto be reviewed, that is (Ten Facts That Nobody Told You About Facebook App For Desktop Windows 9 | facebook app for desktop windows 9) Lots of people searching for info about(Ten Facts That Nobody Told You About Facebook App For Desktop Windows 9 | facebook app for desktop windows 9) and certainly one of them is you, is not it?
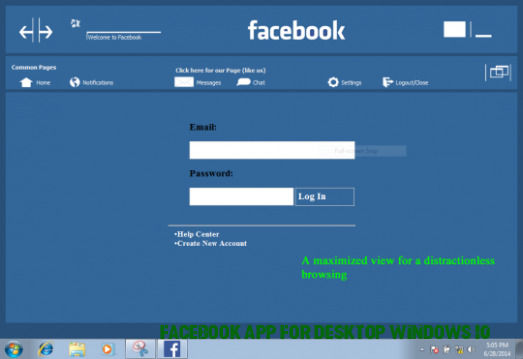
Facebook Desktop – Free download and software reviews – CNET .. | facebook app for desktop windows 10

Facebook Desktop – Free download and software reviews – CNET .. | facebook app for desktop windows 10
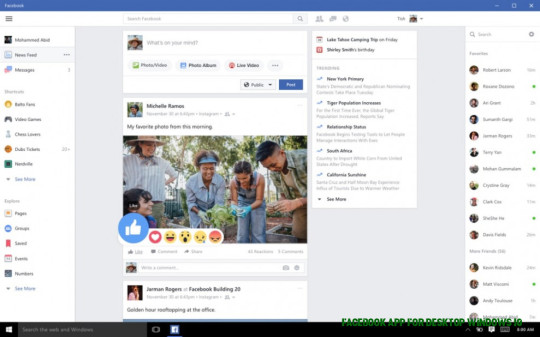
Facebook – Download – facebook app for desktop windows 10 | facebook app for desktop windows 10
Painter Legend https://desktopdrawing.com/wp-content/uploads/2020/07/facebook-beta-for-windows-9-now-available-in-the-store-facebook-app-for-desktop-windows-10.jpg
0 notes
Text
Download paid software for free or cheap
When someone's trying to explain to you how to buy software, but you already got it for free. (Christina @ wocintechchat.com/Unsplash/)
We all love free stuff. I mean, have you seen the line at Ben & Jerry’s on Free Cone Day? You’d think they were giving away Ferraris.
But sadly, not all things come at so low a price. There’s a lot of great free software out there, but some of the best tools cost money—whether it’s a $4 app like Dark Sky or a $120-per-year subscription like Photoshop. If you’re strapped for cash, there might be a way to lower the cost of that program you’ve been eyeing.
Track giveaways, sales, and bundles on deal sites
A lot of companies give away their products—or put them on sale—from time to time to stoke interest. This happens more with smaller programs that need exposure (you probably won’t see a Final Cut Pro giveaway anytime soon), but it’s still a great way to save a few bucks.
Sometimes, you can plan in advance—Digiarty gives away their premium DVD ripping software every year around the holidays, and Black Friday is always a good time to nab discounted licenses for popular programs. Other times, deals may come out of nowhere—like the Spotify-with-free-Hulu bundle from a few months ago—and disappear just as quickly. Some sites are dedicated to providing bundles of apps at a heavily discounted price, like MacHeist and Humble Bundle.
It can be difficult to keep an eye on all these sites at once, so aggregators like Giveaway Radar aim to collect deals in one place. But that’s still a whole lot of information to parse at once, so I recommend picking the programs you really want and setting up alerts on a site like Slickdeals.net (for desktop software and subscriptions) or AppShopper (for mobile apps). That way, when something goes on sale, you’ll know about it right away.
Get a referral link from a friend or forum
Many programs and services may offer discounts if you get a referral from a friend—like a longer free trial, or a discounted rate for your first year. Trello, for example, offers a month of its premium service for each friend you refer. Dropbox offers extra cloud storage space for each person you invite (I’ve had 20GB of free space for almost a decade). Evernote uses a points system that you can use to pay for premium features. Referral programs are more common with subscription services than one-time-purchase apps, but it never hurts to check.
Companies don’t always advertise their referral program heavily on the front page, though, which means you might need to ask around to find out if one even exists. Check forums like Reddit, Slickdeals, and others to see if current users are willing to offer you a code—they probably will, since they usually get some benefit, too.
Use your education discount (if you’re a student or teacher)
You probably know this is a good way to get a decent discount on computers, cell phone plans, or even Amazon Prime. But you’ll arguably find the deepest education discounts on software like Microsoft Windows, Microsoft Office, and—yes—Adobe products like Photoshop. However, you may have to actually walk down to your student union for the best prices.
For example, Adobe offers 60 percent off its Creative Cloud membership for students, but that’s still pretty expensive ($20 a month—and it goes up after the first year). Some schools, however, have worked out a deal with Adobe where a membership is far cheaper, or even free. (I’m still using the discounted version of Photoshop CS5 I got 10 years ago.) So ask at the university’s computer store, or email someone in the IT department, and see what they offer. Microsoft offers Office for free to students directly, as long as you have a valid .edu email address—not to mention upgraded versions of Windows 10, depending on your school. You may find similar discounts for military members as well.
Find the secret “free” URL
Some companies offer a free version of their software, but make it incredibly difficult to find on their site—probably so you’ll second-guess yourself and pay for the full thing. I once spent 20 minutes clicking around Genymotion’s site looking for the free version of their Android emulator. I remember Bitdefender being similarly difficult back in the day (though they advertise their free version more prominently now). And tax preparing companies like TurboTax are notorious for hiding the truly free version of their software—you can only access it if you know the secret link, or find it on the Internal Revenue Service’s website. (It’s only for certain income levels, though, and you may be better off with one of the IRS’ other free software recommendations.)
So if you know you’ve heard about a free version of some program but can’t seem to find it, ask around—read articles about the topic, post in a relevant subreddit, and see if anyone knows where to find that hidden web page. That free software may be hiding in plain sight.
Email the developer
Sometimes, all you need to do is ask. I’m not saying you should email every software company asking for free stuff—that’s a pretty annoying tactic, and it’s not likely to get you very far with most companies. Some may direct you to a sale you didn’t know about, or offer you a short-term deal—but I wouldn’t bank too hard on it.
In some cases, though, your circumstances may set you apart. Maybe you own an older version of the software and need a new activation key. In that case, a developer might offer you a discount on the latest version, or a new key with a proof of your original purchase. (Sega, for example, now offers Steam keys to owners of the boxed copy of Dawn of War for PC as long as you can send a photo of those old discs.) If you have a previous relationship with the developer as a paying customer, there’s a good chance they’ll do their best to help you out.
When all else fails, find a free alternative—or spend the cash
If you just can’t find a discount on the software you want, you might be out of luck. If you haven’t already, make sure to try the free or cheap alternatives—like GIMP or Pixelmator instead of Photoshop. (Check out our favorite open-source alternatives to Office for more recommendations.) And if they don’t work, you may just have to pony up the dough—trust me, some of those programs are worth paying for.
Just be careful as you go through this process. Some deals are totally legitimate, while others are straight-up piracy—and even more exist in a weird grey area. Sites that sell heavily discounted game and software keys, for example, might be selling stolen keys that could get revoked at any time. So be sure to do your research before you press that “buy” button.
0 notes
Text
5 Steps for Successfully Offboarding Web Design Projects
As you draw closer to the finish line with a website, does your client see it just as clearly as you do? Or are they still wavering on design and copy choices even while you’re in the final stages of QA, or talking about additional features they’ll want to add to the site “some day”?
Unless you are getting paid — and paid well — for every single hour you put into a website, you have to be willing to enforce a final stopping point. If you don’t, your client will undoubtedly play the “What about this? Or this?” game for as long as you allow them to.
And you can’t afford to do that. You have other clients whose websites deserve your attention.
Just as you have created an onboarding process to smoothly kick off a new website project, you must do the same with an offboarding process.
Step 1: Collect Your Final Payment
Once the client has given you the approval on the finished website, you push it live. After some light testing to confirm that all is well on the live domain, it’s time to initiate the offboarding process.
You’ll do this by sending along the last invoice. Better yet, your invoicing software should automatically be configured to do this upon reaching the final project milestone.
My favorite tool to do this with is AND CO.
That’s because you can do everything in here:
Create a proposal;
Send the contract;
Track your time;
Send invoices.
Because each of these elements exist within the same place, setting up and scheduling invoices based on your project’s milestones (including the launch date) is really easy to do.
Don’t move on to the next steps until you collect the payment due though. Letting a client go any more than seven days after the project’s end without final payment simply invites them to ask you to do more work.
Step 2: Send the Wrap-up Email
Upon confirming receipt of payment, send your client a wrap-up email.
This doesn’t have to be lengthy. The goal is to get them to schedule the closing call as soon as possible. Something like this should work:
Greetings, [client name]!
I wanted to thank you for the opportunity to build this website for [company name]. I hope you’re just as pleased with it as I am!
I know you’re excited to put this website to work for you now that you have it, but I have just a few things I want to show you as we wrap up.
When you have a moment, please go to my Calendly and schedule a 15-minute Wrap-Up Session for some time this week.
During this call, I’ll give you a behind-the-scenes tour of your website and show you how to edit your content. Afterwards, I will send along the login credentials you need to manage your website along with all of your design assets.
Talk soon.
As I mentioned in the message above, Calendly is the tool I use to simplify my scheduling with clients.
All you have to do is create an event (like “Client Offboarding” or “Client Onboarding”), set up your availability, and then send the link to your clients to pick a time when you’re free. It makes life so much easier.
Step 3: Do the Wrap-Up Video Call
This final call with your client needs to be done over video or, at the very least, a screen-share. For this, I’d suggest using Zoom.
The above example is how I used to do my offboarding calls with WordPress clients.
I’d log into their website and then give them an orientation of all of the key areas they needed to know. I’d show them how to create a post, how to create a page, and explain the difference between the two. I’d also show them important areas like the Media folder, the area to manage Users, and maybe a few other things.
This “training” call is yours to do with as you like. Just make sure the client walks away feeling confident in taking the reins over from you.
Step 4: Deliver the Remaining Pieces
The website is done, you’ve collected the payment, and you’ve had the final call with your client. Now, it’s time to deliver the remaining pieces you owe them.
Logins – If you created any accounts from-scratch (e.g. WordPress, web hosting, social media, etc.), send along the login credentials.
Style guide – Did you create a style guide for the client? Package it up in a professional-looking PDF and send it over in case they decide to work with another designer in the future.
Design assets – Again, on the off chance they work with someone else, you’ll want to send along the design assets you created in their native formats.
Licenses – You may have licensed certain assets during this project, like stock photos or design templates. If that’s the case, you’ll need to bill them for the licenses (if you haven’t already) and transfer ownership to them now.
While you could send these along before the wrap-up call, you run the risk of the clients taking the materials and running away… Only to show up months later wanting to know what all this stuff is, what they’re supposed to do with it, and wondering if you’ll have time to walk them through the website now.
Or they don’t open any of it and then message you months down the line, urgently demanding access to their site, files, etc. To avoid this from happening, clearly label everything and send it along in a shared Dropbox folder.
Even if they lose the link to the Dropbox folder at any point, you don’t have to repackage up all their stuff again. You can simply grab the link from your end and resend.
Step 5: Follow Up in 60 Days
Set a reminder in your project management template to follow up with website clients 60 days after the wrap-up. This will give them enough time to sit with the website and either:
Become really comfortable using it;
Realize it’s too much work.
Either way, it’s a good idea to check in.
If they’re taking good care of the website and using it to promote their business, that’s great. This email will simply serve as a reminder that you remain their trusted ally and you’re here if they ever need anything.
And if they’re not taking care of it, this is an excellent opportunity to offer your assistance in providing (paid) support and maintenance.
Bringing Projects to a Close with an Offboarding Process
If you’ve done a good job of setting expectations with your client from the start, bringing a project to a close should be no problem.
Then again, you know how clients can get. They’re so excited to actually have a website now that they can’t stop imagining the possibilities. So long as you’ve delivered what they paid for, though, you are under no obligation to keep this project open to entertain those ideas unless they start a new contract with you.
Use this offboarding checklist to ensure you give each of your web design projects as strong and final a close as possible.
Featured image via Unsplash.
Add Realistic Chalk and Sketch Lettering Effects with Sketch’it – only $5!
Source
from Webdesigner Depot http://bit.ly/2GDH9Hz
from Blogger http://bit.ly/2L0dGfk
0 notes
Text
5 Steps for Successfully Offboarding Web Design Projects
As you draw closer to the finish line with a website, does your client see it just as clearly as you do? Or are they still wavering on design and copy choices even while you’re in the final stages of QA, or talking about additional features they’ll want to add to the site “some day”?
Unless you are getting paid — and paid well — for every single hour you put into a website, you have to be willing to enforce a final stopping point. If you don’t, your client will undoubtedly play the “What about this? Or this?” game for as long as you allow them to.
And you can’t afford to do that. You have other clients whose websites deserve your attention.
Just as you have created an onboarding process to smoothly kick off a new website project, you must do the same with an offboarding process.
Step 1: Collect Your Final Payment
Once the client has given you the approval on the finished website, you push it live. After some light testing to confirm that all is well on the live domain, it’s time to initiate the offboarding process.
You’ll do this by sending along the last invoice. Better yet, your invoicing software should automatically be configured to do this upon reaching the final project milestone.
My favorite tool to do this with is AND CO.
That’s because you can do everything in here:
Create a proposal;
Send the contract;
Track your time;
Send invoices.
Because each of these elements exist within the same place, setting up and scheduling invoices based on your project’s milestones (including the launch date) is really easy to do.
Don’t move on to the next steps until you collect the payment due though. Letting a client go any more than seven days after the project’s end without final payment simply invites them to ask you to do more work.
Step 2: Send the Wrap-up Email
Upon confirming receipt of payment, send your client a wrap-up email.
This doesn’t have to be lengthy. The goal is to get them to schedule the closing call as soon as possible. Something like this should work:
Greetings, [client name]!
I wanted to thank you for the opportunity to build this website for [company name]. I hope you’re just as pleased with it as I am!
I know you’re excited to put this website to work for you now that you have it, but I have just a few things I want to show you as we wrap up.
When you have a moment, please go to my Calendly and schedule a 15-minute Wrap-Up Session for some time this week.
During this call, I’ll give you a behind-the-scenes tour of your website and show you how to edit your content. Afterwards, I will send along the login credentials you need to manage your website along with all of your design assets.
Talk soon.
As I mentioned in the message above, Calendly is the tool I use to simplify my scheduling with clients.
All you have to do is create an event (like “Client Offboarding” or “Client Onboarding”), set up your availability, and then send the link to your clients to pick a time when you’re free. It makes life so much easier.
Step 3: Do the Wrap-Up Video Call
This final call with your client needs to be done over video or, at the very least, a screen-share. For this, I’d suggest using Zoom.
The above example is how I used to do my offboarding calls with WordPress clients.
I’d log into their website and then give them an orientation of all of the key areas they needed to know. I’d show them how to create a post, how to create a page, and explain the difference between the two. I’d also show them important areas like the Media folder, the area to manage Users, and maybe a few other things.
This “training” call is yours to do with as you like. Just make sure the client walks away feeling confident in taking the reins over from you.
Step 4: Deliver the Remaining Pieces
The website is done, you’ve collected the payment, and you’ve had the final call with your client. Now, it’s time to deliver the remaining pieces you owe them.
Logins – If you created any accounts from-scratch (e.g. WordPress, web hosting, social media, etc.), send along the login credentials.
Style guide – Did you create a style guide for the client? Package it up in a professional-looking PDF and send it over in case they decide to work with another designer in the future.
Design assets – Again, on the off chance they work with someone else, you’ll want to send along the design assets you created in their native formats.
Licenses – You may have licensed certain assets during this project, like stock photos or design templates. If that’s the case, you’ll need to bill them for the licenses (if you haven’t already) and transfer ownership to them now.
While you could send these along before the wrap-up call, you run the risk of the clients taking the materials and running away… Only to show up months later wanting to know what all this stuff is, what they’re supposed to do with it, and wondering if you’ll have time to walk them through the website now.
Or they don’t open any of it and then message you months down the line, urgently demanding access to their site, files, etc. To avoid this from happening, clearly label everything and send it along in a shared Dropbox folder.
Even if they lose the link to the Dropbox folder at any point, you don’t have to repackage up all their stuff again. You can simply grab the link from your end and resend.
Step 5: Follow Up in 60 Days
Set a reminder in your project management template to follow up with website clients 60 days after the wrap-up. This will give them enough time to sit with the website and either:
Become really comfortable using it;
Realize it’s too much work.
Either way, it’s a good idea to check in.
If they’re taking good care of the website and using it to promote their business, that’s great. This email will simply serve as a reminder that you remain their trusted ally and you’re here if they ever need anything.
And if they’re not taking care of it, this is an excellent opportunity to offer your assistance in providing (paid) support and maintenance.
Bringing Projects to a Close with an Offboarding Process
If you’ve done a good job of setting expectations with your client from the start, bringing a project to a close should be no problem.
Then again, you know how clients can get. They’re so excited to actually have a website now that they can’t stop imagining the possibilities. So long as you’ve delivered what they paid for, though, you are under no obligation to keep this project open to entertain those ideas unless they start a new contract with you.
Use this offboarding checklist to ensure you give each of your web design projects as strong and final a close as possible.
Featured image via Unsplash.
Add Realistic Chalk and Sketch Lettering Effects with Sketch’it – only $5!
Source p img {display:inline-block; margin-right:10px;} .alignleft {float:left;} p.showcase {clear:both;} body#browserfriendly p, body#podcast p, div#emailbody p{margin:0;}
5 Steps for Successfully Offboarding Web Design Projects published first on https://medium.com/@koresol
0 notes
Text
Face ID has upsides and downsides on both security and usability and isn't less secure than a PIN or Touch ID in practice (Troy Hunt)
I was wondering recently after poring through yet another data breach how many people actually use multi-step verification. I mean here we have a construct where even if the attacker has the victim's credentials, they're rendered useless once challenged for the authenticator code or SMS which is subsequently set. I went out looking for figures and found the following on Dropbox:
"less than 1% of the Dropbox user base is taking advantage of the company’s two-factor authentication feature": https://t.co/AdbYwWGb7t
— Troy Hunt (@troyhunt) June 3, 2016
Less than 1%. That's alarming. It's alarming not just because the number is so low, but because Dropbox holds such valuable information for so many people. Not only that, but their multi-step implementation is very low-friction - you generally only ever see it when setting up a new machine for the first time.
But here's the problem with multi-step verification: it's a perfect example of where security is friction. No matter how easy you make it, it's something you have to do in addition to the thing you normally do, namely entering a username and password. That's precisely the same problem with getting people to put PINs on their phone and as a result, there's a huge number of devices out there left wide open. How many? It's hard to tell because there's no easy way of collecting those stats. I found one survey from 2014 which said 52% of people have absolutely nothing protecting their phone. Another in 2016 said the number is more like 34%. Keep searching and you'll find more stats of wildly varying values but the simple fact remains that there are a huge number of people out there with no protection on the device at all.
And this brings us to Face ID. I'm writing this the day after the iPhone X launch and obviously this pattern of biometric login is now going to be a major part of the Apple security strategy:
Of course, this now brings with it the whole biometrics discussion and to some extent, it's similar to the one we had when Touch ID launched in 2013 with the iPhone 5S. Obviously there are differences, but many of the issues are also the same. Either way, in my mind both pose fantastic upsides for 99.x% of people and I shared that thought accordingly:
Face ID: for 99.x% of people, their "threat actors" are people who steal their phone at a bar. For everyone else, don't use biometrics.
— Troy Hunt (@troyhunt) September 12, 2017
Not everyone agreed though and there were some responses I honestly didn't see coming. I want to outline some of the issues with each and why per the title of this post, "pragmatic security" is really important here.
No ID
Let's start here because it's the obvious one. Missing PINs on phones provides zero protection from any adversary that gets their hands on it; the kids, a pickpocket or law enforcement - it's free rein for all. Free reign over photos and videos, free reign over messages and email and free reign to communicate with anyone else under the identity of the device owner. I'm stating things here that may seem obvious to you, but clearly the risks haven't yet hit home for many people.
A lack of PIN has also proved very useful for remote attackers. Back in 2014 I wrote about the "Oleg Pliss" situation where unprotected devices were being remotely locked and ransomed. This was only possible when the device didn't have a PIN, a fact the attacker abused by then placing their own on it after gaining access to the victim's online Apple account.
But we can't talk about devices not having any authentication without talking about why and that almost always comes down to friction. The Dropbox multi-step verification situation described above where an additional security control is imposed. So let's move on and start talking about that friction, let's talk about PINs.
PIN
The first point I'll make here as I begin talking about the 3 main security constructs available is that they're all differently secure. This is not a case of one is "secure" and another is "insecure" in any sort of absolute way and anyone referring to them in this fashion is missing a very important part of the narrative. With that said, let's look at the pros and cons involved here.
Obviously, the big pro of a PIN is familiarity (that and not having the problems mentioned above, of course). If you can remember a number, you can set a PIN and hey, we're all good at remembering numbers, right? Like that same one that people use everywhere... which is obviously a con. And this is a perfect example of the human element we so frequently neglect when having this discussion: people take shortcuts with PINs. They reuse them. They follow basic patterns. They disclose them to other people - how many people's kids know the PIN that unlocks their phone? And before you answer "not mine", you're (probably) not normal people by virtue of being interested enough in your security to be here reading this post in the first place!
But PINs are enormously popular and even when you do use the biometric options we're about to get into, you're still going to need one on your phone anyway. For example, every time you hard-reboot an iPhone with Touch ID you need to enter the PIN. When you do, depending on the environment you're in you may be a bit inclined to do so like this:
This is Edward Snowden typing his password in whilst under a blanket in the Citizenfour documentary. He's doing everything he can to ensure there's no way his password can be observed by others because this is precisely the problem with passwords - anyone who has yours can use it (again, this is why multi-step verification is so important). Now you may argue that Snowden's threat profile is such that he needs to take such measures and you're right - I can see exactly why he'd do this. But this also means recognising that different people have different threat profiles and whilst Ed was worried about the likes of the NSA specifically targeting him as a high-value individual, you are (almost certainly) not.
We've all been warned about the risk of shoulder surfing at one time or another and it's pretty common to find it represented in corporate training programs in a similar fashion to this:
Except as it relates to PINs on phones, the problem is much worse. Firstly, it's worse because it's a PIN that's a mere 4 or 6 digits (you could always go alphanumeric on an iPhone but that'll be a near-zero percentage of people) and there's only 10 characters to choose from so observing and remembering them isn't hard. Secondly, mobile devices are obviously used in, well, mobile locations so you're unlocking them on the train, in the shops and in a whole raft of locations where people can directly observe you. When using Apple Pay is a perfect example: you're standing in a queue with people in front of you and people behind you waiting for you to pay for your shopping and that's not a great environment to be entering a secret by pressing a small number of big buttons on a publicly observable screen.
And then there's all the really niche attacks against PINS, for example using thermal imaging to detect the locations the screen was tapped. Now that's by no means trivial, but some of criticisms being levelled at biometrics are also by no means trivial so let's keep it an even playing field. Even entering your PIN in an open space away from people presents a risk in the presence of the burgeoning number of surveillance cameras that are present.
But there's one thing in particular PINs are resilient to which biometrics are not: the police in the US can force you to unlock your phone using your fingerprint. I'm not sure how this differs in the rest of the world, but it was regularly highlighted to me during yesterday's discussions. Now there are obvious privacy issues with this - big ones - but getting back to the personal threat actors issue, this is something the individual needs to think about and consider whether it's a significant enough risk to them to rule out biometrics. If you're an activist or political dissident or indeed an outright criminal, this may pose a problem. For everyone else, you're starting to approach infinitely small likelihoods. I heard an argument yesterday that, for example, a lady who was filming a bloke being shot by the police could have then been forced to unlock her phone by fingerprint so the cops can erase the evidence. But think this through for a moment...
So the risk here is being shot while recording it to local storage then cops unlocking phone with biometrics and illegally erasing evidence?
— Troy Hunt (@troyhunt) September 12, 2017
There will always be attack vectors like this. Always. The question someone has to ask when choosing between biometrics or PIN is how threatened they personally feel by these situations. And then they make their own security decision of their own free volition.
Let's move onto the biometric alternatives.
Touch ID
Given we've now had 4 years of Touch ID (and of course many more years of fingerprint auth in general), we've got a pretty good sense the threat landscape. Even 15 years ago, researchers were circumventing biometric logins. In that particular case, the guy simply lifted a fingerprint from a glass then enhanced it with a cyanoacrylate adhesive, photographed it, took it into Photoshop and cleaned up the picture, printed it onto a transparency sheet, grabbed a photo-sensitive printed circuit board then etched the printed fingerprint from the transparency sheet into the copper on the board before moulding a gelatine finger onto it hence inheriting the fingerprint. Easy!
There have many other examples of auth bypass since that time, including against Apple's Touch ID and indeed some of them have been simpler too. Like PINs, it's not foolproof and what people are doing is trading various security and usability attributes between the PIN and biometric options. A PIN has to be known to unlock the device whilst a fingerprint could be forged, but then a PIN may have been observed or readily guessed (and certainly there are brute force protections to limit this) whilst biometric login can be used in plain sight. They're differently secure and they protect from different threat actors. It's extremely unlikely that the guy who steals your phone off a bar is going to be able to do this, much more likely that a nation state actor that sees a high value in a target's phone will.
One of the arguments I heard against Touch ID yesterday is that an "attacker" could cause a sleeping or unconscious person to unlock their device by placing the owner's finger on the home button. I've quoted the word "attacker" because one such situation occurred last year when a six year old used her sleeping mother's fingerprint to buy $250 worth of Pokemon. Now I've got a 5-year-old and a 7-year-old so I reckon I'm qualified enough to make a few comments on the matter (plus the whole thing about me thinking a lot about security!)
Firstly, whilst the hacker inside of me is thinking "that kid is pretty smart", the parent inside of me is thinking "that kids needs a proverbial kick up the arse". There's nothing unusual about kids using parent's phones for all manner of things and we've probably all given an unlocked phone to one of our own children for them to play a game, watch a video or even just talk on the phone. Touch ID, PIN or nothing at all, if a kid abuses their parent's trust in this way then there's a very different discussion to be had than the one about how sophisticated a threat actor needs to be in order to circumvent it.
Be that as it may, there are certainly circumstances where biometric login poses a risk that PINs don't and the unconscious one is a perfect example. Now in my own personal threat model, being unconscious whilst someone steals my phone and forces me to unlock it is not exactly high up on the list of things that keep me awake at night. But if I was a binge drinker and prone to the odd bender, Touch ID may simply not be a good model for me. Then again, if the victim is getting paralytic drunk and the attacker wants access to an unlocked phone then there are many other simple social engineering tricks to make that happen. In fact, in the attacker's world, the victim having a PIN may well be preferable because it could be observed on unlock and then used to modify security settings that are otherwise unavailable with mere access to fingerprints.
One of the neat features coming in iOS 11 when it hits next week is the ability to rapidly disable Touch ID:
Tap the phone's home button five times, and it will launch a new lockscreen with options to make an emergency call or offer up the owner's emergency medical information. But that S.O.S. mode also silently disables TouchID, requiring a passcode to unlock the phone. That feature could be used to prevent someone from using the owner's finger to unlock their phone while they're sleeping or otherwise incapacitated, for instance.
What this means is that were you find yourself in a higher risk situation with only Touch ID enabled (i.e. you've been pulled over by the police and are concerned about them compelling you to biometrically unlock your phone), there's a speedy option to disable it. But that's obviously no good if you don't have time to enable it so if you're going to hold up a liquor store and it's possible the cops may come bursting in at any time, it could be tough luck (also, don't hold up liquor stores!)
Another new feature helps further strengthen the security model:
in iOS 11, iPhones will not only require a tap to trust a new computer, but the phone's passcode, too. That means even if forensic analysts do seize a phone while it's unlocked or use its owner's finger to unlock it, they still need a passcode to offload its data to a program where it can be analyzed wholesale.
I particularly like this because it adds protection to all unlocked devices where the PIN is not known. If you're compelled to biometrically unlock the device, that won't allow the data to be siphoned off via tethering it. Yes, it could still be accessed directly on the device, but that's a damn sight better then unfettered direct access to storage.
So pros and cons and indeed that's the whole theme of this post. Let's move onto the new thing.
Face ID
I watched the keynote today and was obviously particularly interested in how Face ID was positioned so let me share the key bits here. Keep in mind that I obviously haven't played with this and will purely be going by Apple's own info here.
Firstly, this is not a case of "if the camera sees something that looks like the owner's face the device unlocks". Here's why:
Infrared camera + flood illuminator + proximity sensor + ambient light sensor + camera + dot projector = Face ID. Each of these plays a different role and you can see how, for example, something like infrared could be used to discern the difference between a human head and a photo.
In Apple's demo, they talk about the flood illuminator being used to detect the face (including in the dark):
This is followed up by the infrared camera taking an image:
The dot projector then pumps out 30k invisible dots:
The IR image and the dot pattern then get "pushed though neural networks to create a mathematical model of your face" which is then compared to the stored one created at setup. Now of course we don't know how much of this is fancy Apple speak versus reality and I'm very keen to see the phone get into the hands of creative security people, but you can't help but think that the breadth of sensors available for visual verification trumps those required for touch alone.
Apple is obviously conscious of comparisons between the two biometric implementations and they shared some stats on the likelihood of each returning a false positive. Firstly, Touch ID:
So what they're saying here is that you've got a 1 in 50k chance of someone else's print unlocking your phone. From a pure chance perspective, those are pretty good odds but I'm not sure that's the best metric to use (more on that in a moment).
Here's how Face ID compares:
One in a million. There's literally a saying that's "one in a million" which symbolises the extremely remote likelihood of something happening! The 20x figure over Touch ID is significant but it doesn't seem like the right number to be focusing on. The right number would be the one that illustrates not the likelihood of random people gaining access, but rather the likelihood of an adversary tricking the biometrics via artificial means such as the gummi bears and PCBs. But that's not the sort of thing we're going to know until people start attempting just that.
Be that as it may, Apple claim that Face ID is resilient to both photos and masks:
And with all those sensors, it's certainly believable that there's enough inputs to discern with a high degree of confidence what is a legitimate face versus a fake one. Having said that, even Apple themselves acknowledged that certain threats remain:
Laughs were had, jokes were made but the underlying message was that Face ID isn't foolproof. Just like Touch ID. And PINs.
Thinking back to Touch ID for a moment, one of the risk flagged there was a kid holding a sleeping adult's finger on the sensor or indeed someone doing the same with an unconscious iPhone owner. Face ID seems to solve this problem:
If your eyes are closed or you're looking away, it's not going to unlock
Which makes a lot of sense - given the processing power to actually observe and interpret eye movements in the split second within which you expect this to work, this would be a really neat failsafe. Apple highlights this as "attention awareness" when they wrap up the Face ID portion of the presentation:
Moving on to something different, when I shared 99.x% tweet earlier on, a thread emerged about abusive spouses. Now if I'm honest, I didn't see that angle coming and it made me curious - what is the angle? I mean how does Face ID pose a greater threat to victims of domestic violence than the previous auth models? There's the risk of being physically compelled to unlock the phone, but of course Touch ID poses the same risk. One would also imagine that in such a situation, an abusive husband may demand a PIN in the same intimidating fashion in which they demand a finger is placed on the sensor or the front facing camera is pointed at the face (and appropriate eye movement is made). It's hard to imagine there are many legitimate scenarios where an iPhone X is present, is only using Face ID, the owner is an abused woman and the man is able to compel her to unlock the device in a way that wasn't previously possible. The only tangible thing I could take away from that conversation is that many people won't understand the respective strengths and weaknesses of each authentication method which, of course, is true for anyone regardless of their relationship status. (Folks who understand both domestic violence and the role of technology in that environment, do please comment if I'm missing something.)
The broader issue here is trusting those you surround yourself with in the home. In the same way that I trust my kids and my wife not to hold my finger to my phone while I'm sleeping, I trust them not to abuse my PC if I walk away from it whilst unlocked and yes, one would reasonably expect to be able to do that in their own home. The PC sits there next to my wallet with cash in it and the keys to the cars parked out the front. When you can no longer trust those in your immediate vicinity within the sanctity of your own home, you have a much bigger set of problems:
My ex broke into my phone by holding it against me while asleep
She also broke a table over my head so I'm not sure I'm disproving Troy https://t.co/RELrlLozhN
— Alexander Payne (@myrrlyn) September 12, 2017
Having absorbed all the info and given Face ID some deeper thought, I stand by that 99.x% tweet until proven wrong. I just can't make good, rational arguments against it without letting go of the pragmatism which acknowledges all the factors I've mentioned above.
Summary
What we have to keep in mind here is just how low the security bar is still set for so many people. Probably not for you being someone interested in reading this sort of material in the first place, but for the billions of "normals" out there now using mobile devices. Touch ID and Face ID as so frictionless that they remove the usability barrier PINs post. There's a good reason Apple consistently shows biometric authentication in all their demos - because it's just such a slick experience.
The majority of negative commentary I'm seeing about Face ID in particular amounts to "facial recognition is bad" and that's it. Some of those responses seem to be based on the assumption that it introduces a privacy risk in the same way as facial tracking in, say, the local supermarket would. But that's not the case here; the data is stored in the iPhone's secure enclave and never leaves the device:
More than anything though, we need to remember that Face ID introduces another security model with its own upsides and downsides on both security and usability. It's not "less secure than a PIN", it's differently secure and the trick now is in individuals choosing the auth model that's right for them.
I'll order an iPhone X when they hit the store next month and I'll be giving Face ID a red hot go. I'll also be watching closely as smart security folks around the world try to break it :)
Edit: TechCrunch has published a great interview with Craig Federighi that answers many of the questions that have been raised in this blog post and in the subsequent comments. Highly recommended reading!
from Techmeme http://ift.tt/2wlv0DJ
0 notes
Link
I was going recently through my "spring cleaning" of things I use online. I'm not talking about the business tools, but the services and tools I use, for my own, personal benefit. I know, you're an entrepreneur, all you think about is your business, but come on...So I thought it might be interesting to make a list of all the things I can vouch for since I give them the best review ever: opening my wallet every month. Who knows, maybe you get some ideas (all the links are to the services, they're not affiliate links and I'm not affiliated with any of them in any way).DropboxI've been using Dropbox for so long now, I can't really remember how it was before it existed, when I needed to carry all my files with me, on a USB stick, like a savage person :)It took me about 3 years to say "ok, I'll pay yearly, it makes more sense" :))EvernoteI've been using Evernote as a "dump everything" app for about 5 years or so. I got into the annual payment last year, as well. I moved to Premium once they changed to the new pricing options.PocketI don't really use Pocket as a "dump everything I want to read" tool (that's what Evernote is for). I use it more for "I need to have something to read on the plane, so I will add all these 40 long articles to it". Because the only way I could have the mobile sync was to pay for it, I paid for it. Now, that I think about it, I travel a lot less and the internet is no longer that much of an issue, so I might stop using it. But, since I paid annually already, we'll see.Oh, and the reason why I use it over Evernote for reading on mobile: the articles look a lot, lot better and less cluttered. I don't know why, I just like it more.Google DriveI just use it for backups. Oh, and Photos, because Google Photos is the best photos app ever: have you tried searching in it? It's worth it just for the search images function and how well it works.NetflixNeed I say more? I pay for the bigger account, with 4 devices and UHD content, but I don't really see much of a difference on a 4K screen between UHD and FHD, frankly - I understood recently why: AppleTV doesn't play 4K content. If I think about it, since I pay monthly, I wonder if I can pay yearly.HuluSome TV series are available here and not on Netflix, so I pay for the account without ads. I need to check out if I can pay yearly as well. While Hulu is not available outside of US, I travel quite often there that it makes sense. And sometimes I get "creative" about it :)Tennis TVIt's really bad that WTA is not on it anymore since I watched as many matches of the Romanian ladies as possible, but I still keep it for the ATP games. And my father uses it, as well, and he would be really sad if he didn't have it anymore. And I really can't have my father sad, can I? :)SpotifyI've created the account the last time I've been to the states. It's perfect for several people in the family (you can add up to 5, I think, under the $15/month contract). I pay monthly, cause I wasn't sure I want to keep, but I'll see if it's possible yearly. I used to pay for Google Play Music, but I didn't like it as much. I think Spotify has a better discovery engine and I like this a lot.OvercastThe best podcasting app there is on iOS. I really like it (the cutting of pauses alone reduces podcasts duration by 5-10%, probably), but I hate that there isn't a macOS version. There's a web player, though. If you're looking for an Android version, there's none, but I don't use Android, so I don't really care about it :)MyusI need a stable US address and this is a good solution for me. They changed a little bit since I started using it: I used to be able receive packages and letters there with the basic account. Not anymore, so I need to look a little bit at how much I really need it now. The thing is I got a replacement bank card sent there and "receiving packages" is no longer part of the plan, so I needed to reorder a new card from the bank to another address. Which was bad, as you would expect.CyberGhostThe best VPN solution I used in the last years. I used some others before and I had some issues so I preferred to go with CyberGhost. The reasoning at that moment was that if I really had any issues I could actually meet them and talk to them since the company is based in Bucharest and I could actually go to their office. Thankfully, I didn't need help, since the app worked really well doing what I need. Though now I'm a little sorry I didn't visit them. Who knows, maybe I could've invested a little bit in them and be even happier about the acquisition they announced last month :)I use VPNs because I travel a lot and I feel uncomfortable connecting to public wifi networks without a VPN. Yes, I get "creative" with streaming services from time to time, but not as often as you would think. I'm a lot more concerned about security.I pay Cyberghost yearly, as well.Kindle Unlimited (Amazon Prime)I’ve used Kindle Unlimited sparingly from time to time. You basically get free books to read, but the books aren’t always the greatest. Still, there are some worth reading, like The Simple Path to Wealth by JL Collins. Since I basically pay for Amazon Prime, not for Kindle Unlimited, I also use this for cheap and free deliveries (to the US and Ireland, where I stay most of the time). Again, I pay monthly, I need to look if it’s possible to pay yearly.1passwordIt's not a monthly service, but I paid for it on all the platforms I use (macOS, iOS). It's the service I use the most on a daily basis since I have weird passwords that I always forget :)RunKeeperI haven't run since September, but I keep paying this monthly because ONE DAY!!!! SOME DAY!!!! I actually played a lot of tennis during the winter which caused some weird problems with my Achilles tendon and I need a treatment which happens right now, in May. So hopefully, by June I will start using the app again.SoulverThis is an app I paid about $10, I think. It's the best calculator there is. I don't know how to really explain it, but it's good :)These are the service and platforms I use every month. And I support them with my credit cards :)edit: formatting
0 notes
Text
Opening apple iphone ended up being easy in a couple of steps, don't wast your time and do it within a few days making your apple iphone SIM cost-free. Disregards the gimmickry seen in several apple iphone electronic camera apps, instead concentrating on manual control over shutter, ISO, white equilibrium as Read More Here free iphone 6 Discover More Here Website Read More Here http://bit.ly/2oVLkXH http://cutt.us/UOLhV http://ow.ly/ACgf30aMxpq http://cutt.us/UOLhV how to get a free iphone well as emphasis. You'll should bring bank details, a valid photo ID and your current mobile plus other individual information - see Apple's website for a full list. This free iPhone 6s giveaway program undergoes terms & solutions in association with the brandings states listed below. Say the item that was originally being used as a promo code absolutely free things was actually priced at $10. I know that if you haven't aimed to obtain an iPhone opened previously, you could battle to see just how outstanding this is, however this is a rarity. In the weekly tasks, you can obtain way of life factors after finishing 75% of the tasks. Even more inside information from different resources in the supply chain claim that the free iPhone 5S is set to obtain a small speed boost over the apple iphone 5's cpu, which may or could not influence efficiency greatly relying on your use. The iPhone SE isn't actually an upgrade if you've got an iPhone 6 or later on, however it is a wonderful option for anyone that suches as a little phone. Sprint will likewise begin taking preorders on Friday at 12:01 a.m. Pacific on, as well as the carrier is anticipated to make use of the celebration to proceed advertising its apple iphone Forever program, which will certainly offer the 32GB iPhone 7 for as reduced as $15 a month if you sell an old apple iphone. Improvements over in 2014's Apple phablet are primarily inner, and also make it even more engaging, though this huge man doesn't come cheap. Similarly, shopping website traffic through smart phones contained 33% iOS as well as 15% Android. With 25+ advanced area saving evaluation technologies, the apple iphone cleaner cost-free could scan and also evaluate your iPhone completely to recognize the utilized as well as vacuum on your iPhone and also figure out just how much can be released. That implies you might not have the ability to upgrade free of cost annually if you get on a 2-year contract, however you might do it every 2 years. You'll require to terminate it and sign an agreement for the iPhone 7 offer if you have a contract dedication. So as to get some Dropbox room you first should sign up for it. You could do that here Developing a totally free account will get you 2GB of space to start. You could acquire with the iPhone Upgrade Program also if you have an existing agreement or a time payment plan balance. But for the greenhand, it might end up being a difficult task to take care of the Application Shop, either on computer system or iPhone. Will add pictures for you to all can see it. Simply looking them its adequate to comprehend its not an apple iphone 7. The apple iphone 7 maintains the 12-megapixel camera, however includes a larger aperture as well as this is a big offer - optical photo stablizing that maintains images steadier. If you have an application with a large amount of Papers & Data," take into consideration removing it to liberate space. The first software application hack that was prominent and so efficient on the apple iphone 3 broadened right into hardware unlocking and afterwards into IMEI unlocking. Undoubtedly, your mileage could differ, but it shows up that Apple has been supplying similar substitute systems to individuals asking for them - our own Jeff Benjamin was additionally able to get his cable replaced too, merely by asking. Given that the apple iphone 3G generation, the apple iphone utilizes A-GPS run by the USA. . For IPhone 4/ 3GS, iPad 1 as well as iPod touch 4, you could retrieve all files under different categories, such as Contacts, Messages, Call Background, Schedule, Notes, Reminders, Safari Bookmark as well as Movie Library, Image Stream Message Attachments, Voice Memos, and so on That's because you can only obtain reference space from a new user that develops an account on a computer that has actually not previously been connected to Dropbox prior to. Since I thought this cable was still covered by my iPhone warranty, I decided to take it to Apple as well as see if they would change it. I started with a Google, online forum, and blog search to develop a listing of all the apple iphone 6 Unlock providers readily available. Although the business hasn't launched details numbers for the iPhone 7 rather yet, its payment plan for the apple iphone Sixes appeared to $27.08 monthly for 24 months with 0 percent APR Prudent mobile phone owners will certainly likewise intend to take a look at our 50 ideal free iPhone applications summary. Find out how you can create an Individual Hotspot with your apple iphone Sixes or 6s And also to share your device data with others. I have actually possessed the Iphone 7 given that its launch, I updated from my Iphone 6 which I had for two years, it is the same form as well as everything recognizes however whatever else is a massive improvement. And also the Application Store teems with unbelievable applications that have actually been tailored to make the most of just what iPhone is capable of.
0 notes
Text
Google declares the Android O Developer Preview A foundation handling lockdown, picture-in-picture for telephones, and a quicker runtime.
Almost precisely a year after the Android N Developer Preview propelled, Google is unleashing a designer review of the following significant adaptation of Android, "Android O." We haven't attempted it yet (pictures ought to drop any moment now), and the overwhelming engineer documentation is still on lockdown, however we do have a major rundown of new components to go over.This first engineer see is evidently not going to be super steady. Google's blog entry takes note of that "it's initial days, there are more components coming, there's still a lot of adjustment and execution work in front of us. However, it's booting :)."
In light of the early status, this first form of Android O won't take off to the Android Beta program, which offers helpful set up OTA overhauls. Rather Google will kick it outdated with pictures for the Nexus 5X, 6P, Player, and the Pixel, Pixel XL, and Pixel C. There's a Wear 2.0 variant of Android O, yet it's just accessible by means of the emulator. There's likewise another rendition of the SDK, Android Studio 2.4, for designers keen on experimenting with the new APIs.
Additionally recall there are two fundamental parts to Android: the open source "AOSP" part and the shut source "Google" part. Today we're just catching wind of the open source parts, as opposed to the very beginning of the Android N Developer Preview, where we just caught wind of AOSP elements like split screen, overhauled notices, and enhanced power funds. When it developed into the completely acknowledged variant of Nougat on the Google Pixel, we got featuring "Google" highlights like the Google Assistant. As common Google says, "Through the span of the following a while, we'll be discharging refreshed designer reviews, and we'll be doing a profound jump on all things Android at Google I/O in May." Now we should plunge into some features!Background handling lockdownGoogle's blog entry says Android O "puts a major need on enhancing a client's battery life and the gadget's intelligent execution." Google arrangements to do this by including "programmed points of confinement" to what applications can do out of sight in "three principle territories: verifiable communicates, foundation administrations, and area refreshes."
"Certain communicates" are gadget wide declarations that any application can tune in to. In more established forms of Android, these were things like an "availability change" from LTE to Wi-Fi or "another photo" caution. Any application can join to get these communicates and could awaken the second they happened, which is not an extraordinary thought for execution. For example, when you take another photo, Google Photos quickly begins up out of sight and transfers the photo, thus can Dropbox. A photo altering application can likewise start up and add it to its photograph file. Take a moment picture, and all these applications are topping off your RAM and backing off the telephone.
We don't have the documentation yet, however Google cautioned application engineers at I/O 2016 that a foundation handling lockdown was coming. Google recognized applications' forceful utilization of certain communicates as a major explanation behind battery deplete and slow execution, and it even close down the "association change" and "new picture" alarms in Android 7.0 Nougat. The suggested swap for these foundation employments was "Occupation Scheduler," an API presented in Android 5.0 Lollipop. Work Scheduler is a "lazier" approach to do foundation handling. Applications agree to accept a foundation employment, which would occur eventually. Work Scheduler clumps up foundation preparing demands into one major cut of "foundation handling time," which ideally happens when the telephone is sit out of gear, or even better, connected to. Work Scheduler resembles a movement cop for foundation preparing, bringing about a telephone that awakens less, dozes more, and spares more battery.
Amid its experience preparing talk at I/O, Google flaunted a "dream" for how foundation handling would work in a "future discharge" of Android. Every single understood communicate were stopped, and applications would need to thoroughly depend on Job Scheduler. Doing this to everything would break a ton of applications, so the proposed change would happen just for applications that "objective" the new discharge. "Focusing on" an arrival of Android means an application knows about Android includes up to that discharge and would agree to accept the new APIs and foundation limitations. We'll need to plunge into the documentation once it goes up, however it appears like that "future discharge" Google discussed at I/O is Android O.Adaptive iconsPixel gadgets utilize roundabout symbols, Samsung gadgets utilize a squircle, and various Chinese organizations attempt to copy Apple's adjusted rectangle symbols, so what's an outsider application designer to do? The new "Versatile symbols" highlight will give engineers a chance to pick a foundation picture, which every individual Android skin can then remove to fit the framework plan.
The thought is to have your one of a kind symbol in the focal point of a variable shape, with a foundation picture that can be cut a few diverse ways. This new sort of symbol will work basically wherever you see a symbol—on the launcher, alternate ways, settings sharing exchanges, and the diagram screen—and framework movement will be effectively connected to the variable shape.
Picture-in-picture on telephones and tablets
One of the objectives in Android 7.0 Nougat was to institutionalize a ton of the windowing shenanigans OEMs had been pulling off in their Android skins. The improvement of a resizable application system prompted split-screen mode on telephones and tablets, picture-in-picture mode on TVs, and a multiwindow mode that hasn't been utilized on any Google gadget however is there for OEMs like Samsung that need to actualize it.
Multiwindow mode and split screen are not really enough for telephones and tablets, however. A great deal of OEMs and application engineers attempt to actualize a telephone picture-in-picture mode or a drifting video window with a wide range of hacks. Presently in Android O, picture-in-picture on telephones is something that will be authoritatively bolstered. Applications will have the capacity to generate a gliding video nourish with custom summons like "Play" and "Delay." It would be awesome if this worked for YouTube, and ideally Google won't make it a player in the "YouTube Red" membership service.Better console route If the Pixel C is to be trusted, the fate of Android tablets includes being profitability centered console machines. The issue is Android has really loathsome equipment console support, and Google arrangements to improve that a bit in Android O. Google says it is "centered around building a more solid, unsurprising model for "bolt" and "tab" route."
Better selecting will be an appreciated change, however the Pixel C with Android 7.0 still has a huge amount of keyboarding issues past just route. Android is planned around a product console, and when you take that away and supplant it with an equipment one, a ton of issues fly up. You would hope to have the capacity to open up an application and begin writing on your equipment console, however no application truly defaults "writing concentrate" accurately, in light of the fact that that would make a product console fly up on generally gadgets. So you generally need to do an additional tap on the info box you need. Perhaps now you'll have the capacity to tab over to a container, however that is as yet clunkier than a genuine console and-mouse OS like Windows, MacOS, or Linux.
The product console likewise has auto redress, and numerous applications (like Gmail) depend on it for spell check. Utilize an equipment console and all of a sudden a ton of applications have no spell check at all.I trust telephones never dispose of the earphone jack. However, in the event that they do, (or regardless of the possibility that they don't) it is decent to have an option that is superior to the dried up old Bluetooth A2DP convention remote earphones are screwed over thanks to today. To help with this, Android O is pressing backing for some higher-quality remote sound choices.
Sony has given its restrictive LDAC codec—a higher-data transfer capacity, higher-quality contrasting option to standard Bluetooth—to AOSP, permitting any OEM to execute LDAC on a gadget for nothing. Building an arrangement of perfect earphones will in all likelihood still require paying an authorizing expense to Sony, yet the customer gadgets monster is most likely trusting that turns into an all the more engaging thought to earphone producers once every new Android telephone has LDAC installed. At this moment you will just discover LDAC earphones from Sony.
Sony really got an extraordinary yell out from Google in the blog entry: "Sony Mobile has contributed more than 30 include improvements and 250 bug fixes to Android O." This isn't the first run through Sony has dropped enormous pieces of code into AOSP; the organization is likewise in charge of Android's asset overlay system, which controls the greater part of the OEM subject stores you see out there.
There's additionally a module design in Android O for "great Bluetooth sound codecs," so if an OEM inclines toward something like Qualcomm's AptX (another exclusive higher-transmission capacity/higher-quality sound standard) they can pay a permitting expense and all the more effectively drop it into Android.
Huge amounts of different components
Android O's rundown of elements continues endlessly.
Autofill APIs will permit clients to choose an assigned autofill application, "like the way they select a console application." This ought to make secret word directors work a great deal better, without the requirement for janky duplicate/glue arrangements or hacks to the console system.
Notice channels are "application characterized classes for warning substance." This will be a route for applications to give a group of notice "channels" that the client can oversee. Most engineers assemble this starting with no outside help today. Gmail gives you a chance to pick what marks you need notices from, and a Twitter application gives you a chance to choose on the off chance that you need notices for retweets, likes, or potentially new posts. This will be a more stage standard approach to give diverse warning sorts, putting the "channels" in the normal OS notice settings, as opposed to covered some place in the application.
Wide-array shading support for applications will permit imaging applications on gadgets with wide-extent shading showcases to open wide-gam.
0 notes