#api protection
Text
Protect your business from API breaches with comprehensive security testing. Learn from recent incidents and implement best practices for robust API security.
#api protection#api security#api security testing#api scanning#api endpoints#api management#firewall
0 notes
Link
In today’s digital environment, applications and APIs are critical to business operations. Accelerate and protect your applications and manage risk from new or previously unknown APIs while monitoring for malicious payloads with our advanced web app and API protection.
0 notes
Text
An interoperability rule for your money
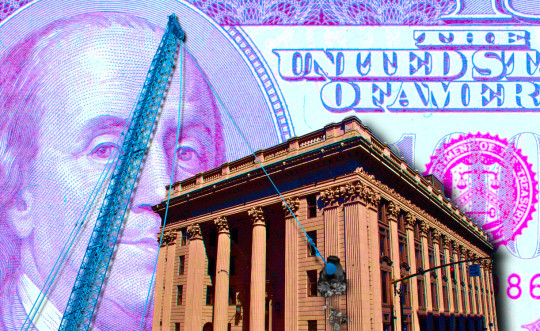
This is the final weekend to back the Kickstarter campaign for the audiobook of my next novel, The Lost Cause. These kickstarters are how I pay my bills, which lets me publish my free essays nearly every day. If you enjoy my work, please consider backing!

"If you don't like it, why don't you take your business elsewhere?" It's the motto of the corporate apologist, someone so Hayek-pilled that they see every purchase as a ballot cast in the only election that matters – the one where you vote with your wallet.
Voting with your wallet is a pretty undignified way to go through life. For one thing, the people with the thickest wallets get the most votes, and for another, no matter who you vote for in that election, the Monopoly Party always wins, because that's the part of the thick-wallet set.
Contrary to the just-so fantasies of Milton-Friedman-poisoned bootlickers, there are plenty of reasons that one might stick with a business that one dislikes – even one that actively harms you.
The biggest reason for staying with a bad company is if they've figured out a way to punish you for leaving. Businesses are keenly attuned to ways to impose switching costs on disloyal customers. "Switching costs" are all the things you have to give up when you take your business elsewhere.
Businesses love high switching costs – think of your gym forcing you to pay to cancel your subscription or Apple turning off your groupchat checkmark when you switch to Android. The more it costs you to move to a rival vendor, the worse your existing vendor can treat you without worrying about losing your business.
Capitalists genuinely hate capitalism. As the FBI informant Peter Thiel says, "competition is for losers." The ideal 21st century "market" is something like Amazon, a platform that gets 45-51 cents out of every dollar earned by its sellers. Sure, those sellers all compete with one another, but no matter who wins, Amazon gets a cut:
https://pluralistic.net/2023/09/28/cloudalists/#cloud-capital
Think of how Facebook keeps users glued to its platform by making the price of leaving cutting of contact with your friends, family, communities and customers. Facebook tells its customers – advertisers – that people who hate the platform stick around because Facebook is so good at manipulating its users (this is a good sales pitch for a company that sells ads!). But there's a far simpler explanation for peoples' continued willingness to let Mark Zuckerberg spy on them: they hate Zuck, but they love their friends, so they stay:
https://www.eff.org/deeplinks/2021/08/facebooks-secret-war-switching-costs
One of the most important ways that regulators can help the public is by reducing switching costs. The easier it is for you to leave a company, the more likely it is they'll treat you well, and if they don't, you can walk away from them. That's just what the Consumer Finance Protection Bureau wants to do with its new Personal Financial Data Rights rule:
https://www.consumerfinance.gov/about-us/newsroom/cfpb-proposes-rule-to-jumpstart-competition-and-accelerate-shift-to-open-banking/
The new rule is aimed at banks, some of the rottenest businesses around. Remember when Wells Fargo ripped off millions of its customers by ordering its tellers to open fake accounts in their name, firing and blacklisting tellers who refused to break the law?
https://www.npr.org/sections/money/2016/10/07/497084491/episode-728-the-wells-fargo-hustle
While there are alternatives to banks – local credit unions are great – a lot of us end up with a bank by default and then struggle to switch, even though the banks give us progressively worse service, collectively rip us off for billions in junk fees, and even defraud us. But because the banks keep our data locked up, it can be hard to shop for better alternatives. And if we do go elsewhere, we're stuck with hours of tedious clerical work to replicate all our account data, payees, digital wallets, etc.
That's where the new CFPB order comes in: the Bureau will force banks to "share data at the person’s direction with other companies offering better products." So if you tell your bank to give your data to a competitor – or a comparison shopping site – it will have to do so…or else.
Banks often claim that they block account migration and comparison shopping sites because they want to protect their customers from ripoff artists. There are certainly plenty of ripoff artists (notwithstanding that some of them run banks). But banks have an irreconcilable conflict of interest here: they might want to stop (other) con-artists from robbing you, but they also want to make leaving as painful as possible.
Instead of letting shareholder-accountable bank execs in back rooms decide what the people you share your financial data are allowed to do with it, the CFPB is shouldering that responsibility, shifting those deliberations to the public activities of a democratically accountable agency. Under the new rule, the businesses you connect to your account data will be "prohibited from misusing or wrongfully monetizing the sensitive personal financial data."
This is an approach that my EFF colleague Bennett Cyphers and I first laid our in our 2021 paper, "Privacy Without Monopoly," where we describe how and why we should shift determinations about who is and isn't allowed to get your data from giant, monopolistic tech companies to democratic institutions, based on privacy law, not corporate whim:
https://www.eff.org/wp/interoperability-and-privacy
The new CFPB rule is aimed squarely at reducing switching costs. As CFPB Director Rohit Chopra says, "Today, we are proposing a rule to give consumers the power to walk away from bad service and choose the financial institutions that offer the best products and prices."
The rule bans banks from charging their customers junk fees to access their data, and bans businesses you give that data to from "collecting, using, or retaining data to advance their own commercial interests through actions like targeted or behavioral advertising." It also guarantees you the unrestricted right to revoke access to your data.
The rule is intended to replace the current state-of-the-art for data sharing, which is giving your banking password to third parties who go and scrape that data on your behalf. This is a tactic that comparison sites and financial dashboards have used since 2006, when Mint pioneered it:
https://www.eff.org/deeplinks/2019/12/mint-late-stage-adversarial-interoperability-demonstrates-what-we-had-and-what-we
A lot's happened since 2006. It's past time for American bank customers to have the right to access and share their data, so they can leave rotten banks and go to better ones.
The new rule is made possible by Section 1033 of the Consumer Financial Protection Act, which was passed in 2010. Chopra is one of the many Biden administrative appointees who have acquainted themselves with all the powers they already have, and then used those powers to help the American people:
https://pluralistic.net/2022/10/18/administrative-competence/#i-know-stuff
It's pretty wild that the first digital interoperability mandate is going to come from the CFPB, but it's also really cool. As Tim Wu demonstrated in 2021 when he wrote Biden's Executive Order on Promoting Competition in the American Economy, the administrative agencies have sweeping, grossly underutilized powers that can make a huge difference to everyday Americans' lives:
https://www.eff.org/de/deeplinks/2021/08/party-its-1979-og-antitrust-back-baby

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/10/21/let-my-dollars-go/#personal-financial-data-rights


My next novel is The Lost Cause, a hopeful novel of the climate emergency. Amazon won't sell the audiobook, so I made my own and I'm pre-selling it on Kickstarter!

Image:
Steve Morgan (modified)
https://commons.wikimedia.org/wiki/File:U.S._National_Bank_Building_-_Portland,_Oregon.jpg
Stefan Kühn (modified)
https://commons.wikimedia.org/wiki/File:Abrissbirne.jpg
CC BY-SA 3.0
https://creativecommons.org/licenses/by-sa/3.0/deed.en
-
Rhys A. (modified)
https://www.flickr.com/photos/rhysasplundh/5201859761/in/photostream/
CC BY 2.0
https://creativecommons.org/licenses/by/2.0/
#pluralistic#cfpb#interoperability mandates#mint#scraping#apis#privacy#privacy without monopoly#consumer finance protection bureau#Personal Financial Data Rights#interop#data hoarding#junk fees#switching costs#section 1033#interoperability
159 notes
·
View notes
Text
Man this Fanfic be killing me :')
So Rewind by Enenyy on Wattpad has been killing me with feels like its stabbing me-
Gfjwbdndbd
This was my reaction to most of the heartbreaking interactions i had to read like bro

BLAZE MY BABY-
NOOOOOOOO DON'T U DARE U FUCKING BITCH NO JUST NO :'D
I HATE THAT I LOVE THE PAIN I GET FROM THIS FIC-
Blaze forgive me :')
#boboiboy#boboiboy galaxy#artists on tumblr#my art sketch#fanfiction#reeeeee#my reaction#bbb api#bbb blaze#boboiboy api#boboiboy blaze#reeeeeee#Blaze/Api centered fic#its starting to become very obvious that my favs are shifting-#blaze 😭 my child i'll protect u with my life#pls survive by the fucking fic my heart won't be able to handle if u died#jdvdjbcndndkxbsnnd#pls survive in the end#i'll bawl my eyes out pls#hdbksbdd#Enenyy is killing me i swear gOD-#angin u r getting dethroned by the flame boi-
23 notes
·
View notes
Text
Scholarship and grant opportunity from NAAAP NY
If any of you live in New York State, NAAAP NY has launched a scholarship program and a grant opportunity! Here are the details.
Scholarship program: $2000 (and other benefits) for API college-bound students or current undergrads who demonstrate leadership potential
Project grant: $2000, mentorship session, and more for anyone in NY (not just API individuals) who has an idea, community initiative, or project that will benefit the API community
The deadline for both is March 31, 2023, with finalists receiving notifications in early April for interviews. I’ll drop the application link in a reblog in order to avoid this post being hidden in Tumblr search!
#protect brown girls#desi#API community#scholarship#i know I’ve been silent and I’m sorry!!#I’m trying to find new ways to keep this blog sustainable so I can devote energy to it again
13 notes
·
View notes
Text
Understanding the Protected Audience API
Businesses are constantly seeking innovative ways to engage with their target audience. One such solution gaining traction is the Protected Audience API. This powerful tool allows businesses to access valuable audience insights while ensuring the privacy and security of user data. Let's delve deeper into how the Protected Audience API is revolutionizing audience targeting and enhancing data protection standards.

Leveraging the Protected Audience API
The Protected Audience API facilitates enhanced audience targeting capabilities for businesses across various industries. By leveraging this API, companies can gain access to refined audience segments based on demographics, interests, and behaviors, enabling them to tailor their marketing strategies with precision. Moreover, the API's advanced algorithms ensure that sensitive user data remains protected, fostering trust between businesses and consumers.
Data Privacy and Security
One of the paramount features of the Protected Audience API is its unwavering commitment to data privacy and security. In an era marked by heightened concerns surrounding personal data misuse, businesses must prioritize the protection of user information. Through robust encryption protocols and stringent access controls, the Protected Audience API offers a fortified fortress against unauthorized data breaches, instilling confidence among both consumers and regulatory authorities.

Conclusion
In conclusion, the Protected Audience API represents a significant advancement in audience targeting methodologies while upholding the highest standards of data privacy and security. By harnessing the power of this innovative API, businesses can unlock new avenues for engagement while fostering a culture of trust and transparency with their audience. As technology continues to evolve, the Protected Audience API stands as a beacon of progress, driving the digital landscape toward a safer and more personalized future.
0 notes
Text
Streamlining Data Validation: The Power of API Integration - Technology Org
New Post has been published on https://thedigitalinsider.com/streamlining-data-validation-the-power-of-api-integration-technology-org/
Streamlining Data Validation: The Power of API Integration - Technology Org
Data validation is a critical aspect of any data-driven organisation. Ensuring that the data you collect and use is accurate and reliable is essential for making informed decisions and maintaining the trust of your customers and stakeholders. The need for efficient and effective data validation methods, such as the LEI register, has never been greater in today’s digital landscape, where data is constantly flowing in from various sources. One powerful tool in this regard is API integration.
Data analysis – abstract artistic interpretation. Image credit: Conny Schneider via Unsplash, free license
Understanding Data Validation
Before delving into the benefits of API integration for data validation, let’s first understand what data validation is. Data validation is the process of checking data for accuracy and completeness. It involves verifying that the data you receive is correct, consistent, and adheres to predefined standards or rules. With proper data validation, organisations can avoid making decisions based on inaccurate or incomplete information, leading to costly mistakes and missed opportunities.
The Challenges of Manual Data Validation
Traditionally, data validation has been a manual and time-consuming process. Data analysts and IT professionals would spend hours manually reviewing and correcting data, which slowed down operations and introduced the risk of human errors. Additionally, in industries like finance, ensuring data accuracy often involves cross-referencing with external sources, such as LEI register, to verify the authenticity of entities and transactions.
The Role of APIs in Data Integration
APIs, or Application Programming Interfaces, have emerged as game-changers in data validation. APIs are rules and protocols that allow different software applications to communicate and share data. They enable seamless integration between other systems, applications, and databases, making data validation more efficient and accurate.
Automated Data Validation
One key advantage of API integration for data validation is automation. With APIs, organisations can set up automated processes to validate incoming data in real time. For example, data collected from an external source can be automatically passed through a validation API that checks it against predefined criteria. Any data that doesn’t meet the specified standards can be flagged for further review or correction.
Enhanced Accuracy and Consistency
API integration also ensures greater accuracy and consistency in data validation. There is no room for human error since the validation rules are predefined and implemented through APIs. This means that data validation results are reliable and consistent, regardless of the volume of data being processed.
Efficiency and Time Savings
API integration streamlines the data validation, saving organisations significant time and resources. Manual data validation can be labour-intensive, requiring skilled personnel to review and correct data. With API integration, this process is automated, allowing employees to focus on more strategic tasks that require human expertise.
Scalability
As organisations grow and their data needs expand, scalability becomes crucial in data validation. API integration allows organisations to quickly scale their data validation processes to handle larger volumes of data without significant additional resources or infrastructure. This scalability is essential in today’s data-driven world, where data volumes can vary significantly from one day to the next.
Real-time Data Validation
In a rapidly changing business environment, real-time data validation is essential. With API integration, data can be validated when it enters the system, ensuring that decisions are based on the most up-to-date and accurate information. This real-time validation helps organisations react quickly to changing circumstances and make informed decisions on the spot.
Cost-Effective Solution
API integration for data validation is a cost-effective solution in the long run. While there may be initial setup and integration costs, the efficiency gains and reduced risk of errors result in significant cost savings over time. Organisations can also avoid the costs associated with manual data validation, such as hiring and training additional personnel.
Security and Compliance
Data security and compliance are paramount for organisations, especially when dealing with sensitive or regulated data. API integration allows organisations to implement robust security measures and ensure compliance with data protection regulations. APIs can be configured to encrypt data during transmission, authenticate users and systems, and provide audit trails for data validation processes.
Conclusion
In conclusion, API integration is a powerful tool for streamlining data validation processes in today’s data-driven world. It offers automation, enhanced accuracy, efficiency, scalability, real-time validation, cost-effectiveness, and robust security and compliance measures. By integrating APIs into their data validation workflows, organisations can ensure that the data they rely on for decision-making is accurate, reliable, and up-to-date. This helps them make more informed decisions and enhances their overall operational efficiency and competitiveness in the digital landscape. As data continues to play a pivotal role in business success, harnessing the power of API integration for data validation is an innovative and strategic move.
#Analysis#API#APIs#applications#audit#automation#Business#business environment#compliance#cost savings#data#data analysis#Data Integration#data processing#data protection#data security#data validation#data-driven#databases#efficiency#employees#encrypt#Environment#finance#game#hiring#human#Industries#Infrastructure#integration
0 notes
Text
F5 API Security: Safeguarding Your Digital Infrastructure

F5 API Security, In today's digital age, Application Programming Interfaces (APIs) have become the backbone of numerous web and mobile applications. They allow applications to communicate, share data, and enhance functionality. As the use of APIs grows, so do the associated security risks. In this article, we will delve into the world of F5 API security, understanding its significance, common threats, and how F5's solutions can help protect your digital assets.
Understanding the Importance of API Security
APIs play a pivotal role in modern software development, enabling the seamless exchange of data between different systems. However, the very nature of this data exchange also makes APIs susceptible to various security threats. It's imperative to secure your APIs to protect sensitive information and maintain the trust of your users.
Common API Security Threats
Authentication and Authorization
One of the primary concerns in API security is ensuring that only authorized users or applications can access your API endpoints. F5 provides robust solutions for authentication and authorization, preventing unauthorized access.
Data Encryption
Securing data in transit is crucial. F5 offers encryption services that safeguard your API traffic from eavesdropping and data breaches.
Rate Limiting
APIs are vulnerable to abuse through excessive requests. F5's rate limiting capabilities help prevent API overuse and potential disruption.
F5 Solutions for API Security
F5 offers a range of tools to protect your APIs effectively:
Web Application Firewall (WAF)
A WAF is a crucial component of API security, safeguarding against various web-based attacks. F5's WAF ensures that malicious traffic is filtered out, keeping your API endpoints secure.
API Gateway
An API gateway acts as a traffic cop for your APIs, routing requests, and enforcing security policies. F5's API gateway provides robust security features, including authentication and rate limiting.
Bot Protection
APIs can be targeted by malicious bots. F5's bot protection technologies help differentiate between legitimate and malicious bot traffic, ensuring smooth API operations.
Implementing API Security with F5
Setting Up a WAF
Implementing a WAF involves defining security policies, traffic inspection, and custom rule creation. F5 simplifies this process with an intuitive interface, making it easier to secure your APIs.
Configuring an API Gateway
Setting up an API gateway involves defining access controls, rate limiting policies, and API documentation. F5's API gateway streamlines this setup, ensuring your APIs are secure and well-documented.
Leveraging Bot Protection
Protecting against malicious bots requires configuring bot policies and monitoring bot traffic. F5's bot protection tools make it easier to safeguard your APIs from automated threats.
Best Practices for F5 API Security
To ensure a robust API security framework:
Regularly audit and monitor API traffic and security policies.
Maintain proper version control of your APIs to avoid compatibility issues.
Invest in training and awareness programs to educate your team about API security best practices.
Case Studies: Real-world Examples of F5 API Security Success
Explore real-world success stories where organizations have used F5's API security solutions to protect their digital assets. These case studies highlight the effectiveness and reliability of F5's offerings.
Conclusion
In an era of rapid digital transformation, securing your APIs is non-negotiable. F5 API security solutions offer a comprehensive defense against the most common threats, ensuring the uninterrupted operation of your applications and the safety of your data.
FAQs on F5 API Security
What are the primary security threats to APIs?
Common threats include authentication issues, data breaches, and abuse through excessive requests.
How does F5 safeguard APIs against malicious bots?
F5 employs advanced bot protection technologies to differentiate between legitimate and malicious bot traffic, ensuring API security.
Why is API security essential in modern software development?
API security is crucial to protect sensitive data and maintain the trust of users in an interconnected digital world.
What are the key features of F5's Web Application Firewall (WAF)?
F5's WAF offers features such as web-based attack protection, traffic filtering, and security policy enforcement.
How can I get started with F5 API security solutions?
To get started with F5 API security.
#F5 API Security#Why is API security essential in modern software development?#Leveraging Bot Protection
0 notes
Text
The "Global Social Protection Domain API Specification Project," featured on the tntra.io website, is a groundbreaking initiative in the realm of social protection. This project introduces a comprehensive API specification designed to improve and standardize the delivery of social protection services worldwide. By offering a clear framework and guidelines for data exchange and integration, the project aims to enhance the efficiency, accessibility, and impact of social protection programs on a global scale. It is a significant step forward in promoting social well-being and reducing poverty, making it a crucial resource for policymakers, organizations, and individuals committed to advancing social protection efforts across the globe.
0 notes
Text
Learn how to secure your Node.js API: authentication, input validation, secure communication, rate limiting, and more. Protect your data now!
0 notes
Text
Social media, telcos, lobby for 18-24 months to comply with DPDP Act
Social media companies, telecom operators, and Indian startups are set to lobby for a transition period of 18-24 months to fully comply with the Digital Personal Data Protection (DPDP) Act, 2023, citing technological complexities in two clauses, Business Standard has learnt.
Major industry bodies representing local and global companies such as social media companies, big tech platforms, and…

View On WordPress
#Act#API#comply#Digital Personal Data Protection (DPDP) Act#DPDP#Indian startups#lobby#media#months#Social#Social media companies#telcos#telecom operators
0 notes
Text
ThreatX in 2023 Gartner Hype

ThreatX, a prominent API and application protection platform, has earned recognition in three categories as a Sample Vendor in the Gartner Hype Cycle reports for 2023. These reports include the Gartner Hype Cycle for Application Security 2023, the Gartner Hype Cycle for APIs 2023, and the Gartner Hype Cycle for Workload and Network Security 2023. ThreatX's presence in these reports underscores its commitment to delivering robust security tools for applications, APIs, and cloud Web Application and API Protection (WAAP) to enhance layered defense strategies and effectively counter emerging threats.
The 2023 Gartner Hype Cycle for Application Security highlights the evolving landscape of application security, characterized by intense transformation and growth. Organizations are increasingly developing their own applications using agile methodologies, relying on developers for code security rather than traditional security practitioners. This shift, coupled with new application architectures like cloud-native structures, poses challenges to established security approaches, rendering existing security controls less effective. Moreover, real-world attacks targeting applications and workloads are on the rise.
ThreatX distinguishes itself as the sole solution capable of safeguarding both APIs and applications at the edge and in real-time through risk-based, immediate blocking. What sets ThreatX apart is its ability not only to identify threats but also to thwart them in real-time. It employs risk-based blocking, which activates when an attacker's behavior surpasses a predefined threshold. Furthermore, ThreatX's Runtime API and Application Protection (RAAP) extends protection to running APIs and applications, providing organizations with a comprehensive capability to detect, track, and block threats effectively.
1 note
·
View note
Text
A Closer Look at the Technical Hurdles of Implementing Machine Learning for Privacy Protection
Machine learning (ML) can be a powerful way to protect privacy by letting sensitive data be processed in a way that keeps privacy safe. But there are a few technical problems that need to be solved before machine learning can be used to protect privacy. Here are some of the main challenges:

Data quality: The accuracy and effectiveness of the models made with machine learning depend a lot on the quality of the data that is used. data quality: The quality of the data used to train machine learning models is very important to how accurate and useful they are. The quality of the data used in machine learning has a big effect on how accurate and useful the models that come out of it are. Still, privacy issues in applications that are sensitive to privacy could make it hard to get good data. It can be hard to get enough good data that is also representative of the population. This is especially true when it comes to personal data..
Data preprocessing: Before machine learning algorithms can use data, the data must be preprocessed. This involves steps like cleaning, normalizing, and choosing features. In the preprocessing steps of apps that care about privacy, things like anonymizing or pseudonymized data to protect people's identities should be taken into account.
Model selection: A wide range of machine learning models exist, each with its own set of advantages and disadvantages. Yet, certain models may be more appropriate than others for safeguarding personal information. For privacy-sensitive applications, for instance, interpretable and transparent models may be preferable since they provide more thorough examination and accountability.
Model training: Access to massive volumes of data, necessary for training machine learning models, might be a security issue. Unintentional exposure of personal information is a particular concern when sensitive data is used for training purposes. Differential privacy, federated learning, and safe multi-party computing are all privacy-protecting methods that can help.
Model evaluation: It is important to evaluate how well machine learning models work to make sure they are accurate and useful. But when evaluating applications that are sensitive to privacy, privacy concerns must also be taken into account. For instance, the evaluation needs to make sure that the model doesn't accidentally reveal private information about people.
Deployment: When machine learning models are used in the real world, they can pose more privacy risks. For example, models may be vulnerable to attacks from the wrong side or may be used to make decisions that hurt people. To reduce these risks, it is important to think carefully about how the model might affect privacy and make sure that the right protections are in place.
In conclusion, using machine learning to protect privacy is a difficult task that needs to be thought about carefully at every step of the machine learning pipeline. To solve these technical problems, you need to know a lot about both machine learning and privacy, as well as the specific privacy-sensitive application.
#machine learning#privacy protection#Data preprocessing#development#data security#global education#engineering#algorithm#api#code
0 notes
Text

★ ( → @catncore )

( → send me a ★ and I’ll bold what applies to your muse !! still accepting )

I like you / I hate you / I dislike you/ I love you / You are family / I would take a bullet for you / I would shoot you / I would lie to your face / I would say something cruel to you on purpose / I would say something cruel to you accidentally / I would cheat on you / I would physically hurt you / You annoy me / You amuse me / I’d laugh at you / I’d laugh with you / I’d manipulate you / You scare me / You confuse me / I wish I knew you better / I trust you * ( or rather, trust your sense of integrity ) / I don’t trust you / You inspire me / I consider you an equal / You are beneath me / You’re better than me / I would trust you with my life / I think you’re mean / I think you’re petty / I think you’re childish / I think you’re smart / I think you’re stupid / I think you’re a bad person / I think you’re a good person / I’m not sure what kind of person you are / I wish you would listen to me / I want to make you proud / I wish you would notice me / I want to impress you / I would hurt other people for you / I’m not sure how to make you happy / I’m a bad influence on you / You deserve better than me / We make a great team / I’d have a one night stand with you / I’d have a relationship with you / I would marry you / I fantasize about our life together / I would trust you with my most treasured belonging / I would tell you my darkest secrets / You disgust me / You intimidate me / I hope I intimidate you / I’d hug you / I’d let you hug me / I’m scared of losing you / I don’t think you like me * ( more accurately: know you don't like me ) / I want to be better for you / I respect you * ( and respect your desire to safeguard your loved ones ) / I don’t respect you / You’re my mentor / You’re my friend / You’re my best friend / I have a crush on you / I could easily watch you die / I’d get drunk with you / I’d party with you / I’d comfort you / I’d prank you / I’d spike your drink / I’d act behind your back / I’d abandon you / I’d hurt you to get what I want / I would choose my happiness over yours / I would choose your happiness over mine / I despise how much I care for you / I need you / I’m dependent on you / I don’t know what I’d do without you / I’m scared of you leaving me / I’d give my life for you / You frustrate me / I’d call for you in a time of need / I would protect you / I’d visit you in hospital / I’d carry you if you were hurt / I’d feel guilty if I hurt you * ( also: your co-Producer and Composer both would probably never let me hear the end of it ) / I’d let you be near me when I am vulnerable / I’d ignore a phone call from you / I’d call you at 3am / I’d break you out of jail / I’d get angry at you / I would shout at you / You’re too loud / You’re too quiet / You’re too sensitive / You can’t take a joke / You embarrass me / I feel nothing for you / You’re reckless / You’re bossy / You bore me / I would ask your advice / I would blame you for something I did / I would cry in your arms / You have the power to hurt me more than anyone else /
#catncore#we're always sleeping in⸴ and sleeping for the wrong team ❯ answered ooc#{ very much accepting of api's distrust#{ he absolutely gets it ; like he may not know of his and ean's pasts but he still understands the desire to protect his composer and his#{ other half. and he's also not going to try to prove himself or his intentions to api because he's not seeking api's approval#{ he's like... relieved and glad that ean and their josh have someone so stalwart in their corner
0 notes
Text
"Artists have finally had enough with Meta’s predatory AI policies, but Meta’s loss is Cara’s gain. An artist-run, anti-AI social platform, Cara has grown from 40,000 to 650,000 users within the last week, catapulting it to the top of the App Store charts.
Instagram is a necessity for many artists, who use the platform to promote their work and solicit paying clients. But Meta is using public posts to train its generative AI systems, and only European users can opt out, since they’re protected by GDPR laws. Generative AI has become so front-and-center on Meta’s apps that artists reached their breaking point.
“When you put [AI] so much in their face, and then give them the option to opt out, but then increase the friction to opt out… I think that increases their anger level — like, okay now I’ve really had enough,” Jingna Zhang, a renowned photographer and founder of Cara, told TechCrunch.
Cara, which has both a web and mobile app, is like a combination of Instagram and X, but built specifically for artists. On your profile, you can host a portfolio of work, but you can also post updates to your feed like any other microblogging site.
Zhang is perfectly positioned to helm an artist-centric social network, where they can post without the risk of becoming part of a training dataset for AI. Zhang has fought on behalf of artists, recently winning an appeal in a Luxembourg court over a painter who copied one of her photographs, which she shot for Harper’s Bazaar Vietnam.
“Using a different medium was irrelevant. My work being ‘available online’ was irrelevant. Consent was necessary,” Zhang wrote on X.
Zhang and three other artists are also suing Google for allegedly using their copyrighted work to train Imagen, an AI image generator. She’s also a plaintiff in a similar lawsuit against Stability AI, Midjourney, DeviantArt and Runway AI.
“Words can’t describe how dehumanizing it is to see my name used 20,000+ times in MidJourney,” she wrote in an Instagram post. “My life’s work and who I am—reduced to meaningless fodder for a commercial image slot machine.”
Artists are so resistant to AI because the training data behind many of these image generators includes their work without their consent. These models amass such a large swath of artwork by scraping the internet for images, without regard for whether or not those images are copyrighted. It’s a slap in the face for artists – not only are their jobs endangered by AI, but that same AI is often powered by their work.
“When it comes to art, unfortunately, we just come from a fundamentally different perspective and point of view, because on the tech side, you have this strong history of open source, and people are just thinking like, well, you put it out there, so it’s for people to use,” Zhang said. “For artists, it’s a part of our selves and our identity. I would not want my best friend to make a manipulation of my work without asking me. There’s a nuance to how we see things, but I don’t think people understand that the art we do is not a product.”
This commitment to protecting artists from copyright infringement extends to Cara, which partners with the University of Chicago’s Glaze project. By using Glaze, artists who manually apply Glaze to their work on Cara have an added layer of protection against being scraped for AI.
Other projects have also stepped up to defend artists. Spawning AI, an artist-led company, has created an API that allows artists to remove their work from popular datasets. But that opt-out only works if the companies that use those datasets honor artists’ requests. So far, HuggingFace and Stability have agreed to respect Spawning’s Do Not Train registry, but artists’ work cannot be retroactively removed from models that have already been trained.
“I think there is this clash between backgrounds and expectations on what we put on the internet,” Zhang said. “For artists, we want to share our work with the world. We put it online, and we don’t charge people to view this piece of work, but it doesn’t mean that we give up our copyright, or any ownership of our work.”"
Read the rest of the article here:
https://techcrunch.com/2024/06/06/a-social-app-for-creatives-cara-grew-from-40k-to-650k-users-in-a-week-because-artists-are-fed-up-with-metas-ai-policies/
424 notes
·
View notes
Text

---



For the Maya, the honey bee is more than an insect. For millennia, the tiny, stingless species Melipona beecheii -- much smaller than Apis mellifera, the European honey bee -- has been revered in the Maya homeland in what is now Central America. Honey made by the animal the Maya call Xunan kab has long been used in a sacred drink, and as medicine to treat a whole host of ailments, from fevers to animal bites. The god of bees appears in relief on the walls of the imposing seacliff fortress of Tulum, the sprawling inland complex of Cobá, and at other ancient sites.
Today, in small, open-sided, thatched-roof structures deep in the tropical forests of Mexico’s Yucatán Peninsula, traditional beekeepers still tend to Xunan kab colonies. The bees emerge from narrow openings in their hollow log homes each morning to forage for pollen and nectar among the lush forest flowers and, increasingly, the cultivated crops beyond the forests’ shrinking borders. And that is where the sacred bee of the Maya gets into trouble.
---
In 2012, the Mexican government granted permission to Monsanto to plant genetically modified soybeans in Campeche and other states on the peninsula without first consulting local communities. The soybeans are engineered to withstand high doses of the controversial weedkiller Roundup; multiple studies have shown exposure to its main ingredient, glyphosate, negatively impacts bees, including by impairing behavior and changing the composition of the animals’ gut microbiome. Though soy is self-pollinating and doesn’t rely on insects, bees do visit the plants while foraging, collecting nectar and pollen as they go. Soon, Maya beekeepers found their bees disoriented and dying in high numbers. And Leydy Pech found her voice.
A traditional Maya beekeeper from the small Campeche city of Hopelchén, Pech had long advocated for sustainable agriculture and the integration of Indigenous knowledge into modern practice. But the new threat to her Xunan kab stirred her to action as never before. She led an assault on the Monsanto program on multiple fronts: legal, academic, and public outrage, including staging protests at ancient Maya sites. The crux of the legal argument by Pech and her allies was that the government had violated its own law by failing to consult with Indigenous communities before granting the permit to Monsanto. In 2015, Mexico’s Supreme Court unanimously agreed. Two years later, the government revoked the permit to plant the crops.
---
As Pech saw it, the fight was not simply about protecting the sacred bee. The campaign was to protect entire ecosystems, the communities that rely on them, and a way of life increasingly threatened by the rise of industrial agriculture, climate change, and deforestation.
“Bees depend on the plants in the forest to produce honey,” she told the public radio program Living on Earth in 2021. “So, less forest means less honey [...]. Struggles like these are long and generational. [...] ”
---
Headline, images, captions, and all text by: Gemma Tarlach. “The Keeper of Sacred Bees Who Took on a Giant.” Atlas Obscura. 23 March 2022. [The first image in this post was not included with Atlas Obscura’s article, but was added by me. Photo by The Goldman Environmental Prize, from “The Ladies of Honey: Protecting Bees and Preserving Tradition,” published online in May 2021. With caption added by me.]
4K notes
·
View notes