#api security testing
Text
Demystifying API Automation Testing: A Comprehensive Guide for Beginners
Embarking on the journey of API automation testing can be daunting for beginners, but with the right guidance and understanding, it becomes an achievable feat. This comprehensive guide aims to demystify the realm of API automation testing, shedding light on its intricacies and equipping newcomers with the knowledge and tools necessary to navigate this landscape confidently.
At its core, API automation testing involves automating the process of verifying the functionality, reliability, and security of APIs. Unlike traditional UI testing, API testing operates at the backend, interacting directly with the application's logic through API endpoints. By automating this process, developers and testers can ensure that APIs perform as expected under various conditions, accelerating the software development lifecycle and enhancing overall product quality.
To embark on the journey of API automation testing, it's crucial to familiarize oneself with essential concepts and tools. Understanding the fundamentals of API testing, including request methods, response codes, authentication mechanisms, and data formats, forms the foundation of effective automation testing for APIs. Additionally, leveraging specialized API automation tools such as Postman, SoapUI, and RestAssured simplifies the process of creating, executing, and managing automated test cases.
Moreover, emphasizing API security testing within the automation framework is paramount. APIs are often the primary targets of cyber attacks, making security testing a critical aspect of the testing process. Implementing security testing techniques such as vulnerability scanning, input validation, and encryption ensures that APIs remain resilient against potential threats, safeguarding sensitive data and maintaining the integrity of the application.
Furthermore, adopting best practices for automation testing for APIs enhances the efficiency and effectiveness of the test planning. This includes maintaining a structured test suite, employing version control for test scripts, incorporating continuous integration/continuous deployment (CI/CD) practices, and fostering collaboration between development and testing teams.
In conclusion, demystifying API automation testing requires a blend of foundational knowledge, practical experience, and the right set of tools. By embracing the principles of API testing and automation, prioritizing security, and adhering to best practices, beginners can embark on their journey with confidence, contributing to the delivery of robust and reliable software solutions.
#api test automation#api automation#api automation testing tools#api automation tools#best api automation tools#api testing and automation#api security testing
0 notes
Text
Protect your business from API breaches with comprehensive security testing. Learn from recent incidents and implement best practices for robust API security.
#api protection#api security#api security testing#api scanning#api endpoints#api management#firewall
0 notes
Text
The Role of APIs in Software Development and Integration
The role of APIs in software development and integration. Have you ever wondered how your diverse smartphone apps interact seamlessly or how data flows effortlessly between other software systems you use daily? The magic is in something called an API or Application Programming Interface. This paper explains APIs and their role in modern software development and system integration.
Continue reading...
#API best practices#API challenges#API design principles#API examples#API integration#API management#API monitoring#API security#API testing#API tutorial#APIs#cloud services#cost efficiency#digital transformation#innovation in technology#modular design#RESTful APIs#scalable systems#secure APIs#SOAP protocol#software architecture#software development#system integration#technology trends#third-party APIs#understanding APIs#Web development
2 notes
·
View notes
Text

Hire RoR Developers - ☎ +1 9177322215
Unlock the potential of Ruby on Rails for your next project. Hire RoR Developers from Semiosis for scalable and efficient web solutions. With expertise in RoR development, our team crafts robust applications to meet your business goals. Dial +1 9177322215 to collaborate with us and elevate your online presence.
#RoR#Ruby programming language#Rails framework#MVC (Model View Controller) architecture#RESTful APIs#ActiveRecord (ORM)#Git/GitHub#PostgreSQL/MySQL/Database Management#HTML/CSS#JavaScript/jQuery#Testing frameworks (RSpec#Cucumber)#Continuous integration/continuous deployment (CI/CD)#Agile/Scrum methodologies#Heroku/AWS/Other deployment platforms#Performance optimization#Security best practices#Version control systems#Problem-solving skills#Team collaboration/communication#Full-stack development
0 notes
Text
Why Businesses Need Network Penetration Testing in the Age of Cyber Warfare

In 2023, cybercrime inflicted an estimated $8 trillion in global losses, a staggering figure that underscores the ever-present threat businesses face in the digital age. Just like a physical security breach, a cyberattack can have devastating consequences, leading to data breaches, financial losses, and reputational damage.
Yet, many businesses remain vulnerable, unaware of the hidden weaknesses lurking within their networks. This is where network penetration testing (pen testing) becomes crucial. Pen testing acts as a preemptive strike against cybercrime, simulating an ethical attack to identify and exploit vulnerabilities before malicious actors do.
A healthcare provider, storing sensitive patient information, unknowingly has a weak firewall configuration. This vulnerability could remain undetected for years, waiting for a malicious hacker to exploit it and gain access to confidential data. A pen test could have identified this weakness, allowing the healthcare provider to patch the vulnerability and prevent a potentially disastrous data breach.
Here's why businesses, regardless of size or industry, cannot afford to ignore network penetration testing:
Proactive Defense: Pen testing is a proactive approach to cybersecurity, identifying vulnerabilities before they can be exploited by real attackers. Statistics reveal that 64% of businesses experienced a cyberattack in the past year, highlighting the critical need for proactive measures.
Prioritized Remediation: Pen tests go beyond simply identifying vulnerabilities; they prioritize them based on their severity and potential impact. This helps businesses allocate resources effectively, focusing on the most critical issues first.
Compliance and Regulation: Many industries, such as healthcare and finance, have specific regulations requiring regular pen testing. This ensures businesses maintain a minimum level of cybersecurity hygiene.
Informed Decision-Making: Pen testing provides valuable insights into an organization's overall security posture, allowing them to understand how their defenses would hold up against real-world attacks. This knowledge empowers businesses to make informed decisions about strengthening their security investments.
Engage with our team of Security Testing Company to strategically plan your testing approach and maintain continuous monitoring of your applications. Cybersecurity Penetration Testing isn't merely a requirement; it's a proactive measure towards protecting your digital assets in a constantly evolving threat environment.
#automation testing company#qa testing company#software testing services#qa testing#api testing services#security testing services in usa#security testing company
0 notes
Text
#API Testing Services#Automation Testing Services#Binary Informatics#Manual Testing Services#Mobile App Testing Services#Offshore QA Expertise#on-demand testing services#Performance Testing Services#QA experts#QA offshore#QA processes#QA providers#QA services#quality assurance#Security Testing Services#software development process#Software Testing Company#Testing Approach
0 notes
Photo

Do you believe that you can identify a phishing email? Think again. Scammers are now utilizing AI technology to create sophisticated and personalized phishing emails that are becoming increasingly difficult to recognize. Stay Aware to Stay Safe with Appzlogic.
#api security#security testing services#app security#Cyber Security expets#cyber security#cyber attacks
1 note
·
View note
Text
Building and Maintaining Reliable, Scalable, Secure, and Maintainable Web Services: Best Practices and Examples
Introduction
Web services have become a cornerstone of modern application architecture. They allow for the creation of loosely coupled, scalable, and interoperable software systems that can be accessed from anywhere on the web. In this paper, we will explore the best practices for designing and building web service architectures. We will discuss the key principles that should guide the…

View On WordPress
#API documentation#automated testing#best practices#cloud infrastructure#containerization#continuous integration#maintainability#microservices#reliability#scalability#Security#version control#web service architecture
1 note
·
View note
Text
Security Knowledge Framework is a tool provided by OWASP. The tool uses the ASVS framework to provide a security checklist to the developers. This tool should also be used and governed by the security professional to train and help developers build secure software by design.
#owasp zap penetration testing#owasp top 10#owasp testing guide#owasp security#open web application security project#owasp top 10 api#how to use OWASP#OWASP security knowledge framework
0 notes
Text
I think my biggest (technical, long-term) issues with current generation AI, primarily through LLMs such as ChatGPT, is the following:
You cannot readily replicate responses, which is the entire point of the scientific process. To ensure correct results for discovery and use is the ability to easily replicate results.
They are primarily cloud based, which means you will not be able to stand them up for testing in 1-5 years and replicate any sort of results or research papers that may be discovered now. Technical, direct, or anything else.
They are primarily cloud based, which means any thing you throw at them, will not be able to be tuned with similar characteristics without massive manual testing as they are internally changed all the time.
They are primarily cloud based, which means you cannot have any ownership or security in the knowledge, that they are safely utilizing your data.
They are primarily cloud based, which means they can price you out of their system at any time.
They are primarily cloud based, which means that they will price you out of their system at any time.
They are primarily cloud based, which means they will break your/their API, and there will be no recompense or ability to change providers.
They are all primarily a private company, and if you build on their platform, then you have no platform of your own. Your business, is dependent on, and is their business.
You own nothing. They own all of it. No matter the legal contract you have with them will protect you from that.
They are primarily cloud based, they are primarily private businesses, and they are anti-scientific development as they are black boxes of inputs, controls, and outputs.
Anything you develop on them now, will not work the same, if at all, in the future. You will have virtually, tangentially, literally, no legacy or agency.
(I originally posted this on the fediverse)
33 notes
·
View notes
Text
neomanager progress
Since my recent post about me making a special locally-ran interface for Neocities suddenly made numbers and brought interested people, i figured could share some progress on the project from time to time! Below is a screenshot of what the project currently looks like.
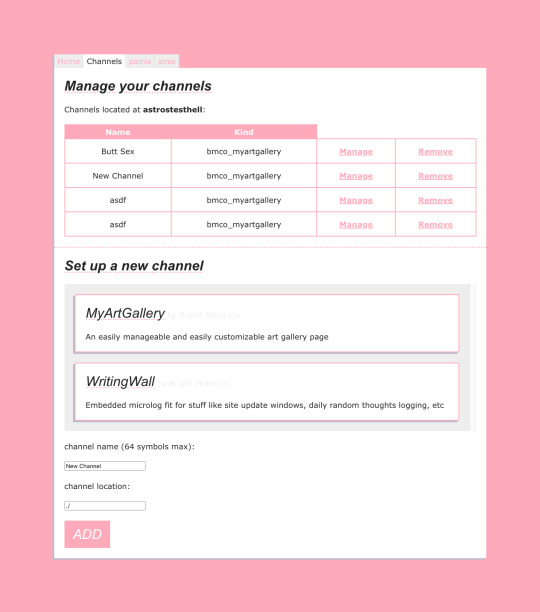
So today, after a whole day of work, i finally got the installation to *sort of* work. Now you can select a "kind" of channel you want to install (there will be at least 2, maybe 3, by me) - select where on your Neocities it should be installed and how it should be called.
Hitting ADD actually downloads and unpacks the freshest version, uploads the needed files to neocities and stores other needed files locally. It even plays a cool rotating wheel animation, made in pure CSS! The last leg now is to tune the editor side of MyAG to work offline and process/push files to neocities, which will be a bit tricky - but nothing is impossible; then, the super duper barebones version will be ready.
I'm putting a lot of thought into what does what, since i'm supposedly an IT specialist - so far, the whole thing makes sense and doesn't implode, which is nice. Things are kept more or less modular, stuff is going smooth, and the installing process is quite simple - so people with some technical expertise could actually write add-ons for this, if they want to; that is - when this thing is released and is more or less stable. I'm a bit concerned about the security of Neocities API tokens and if they can somehow get stolen from Flask's files - i will have to verify this before releasing anything to public.
Anyways, i'm excited to finish the barebones version and have people test it out. Pretty sure it will explode into my face with a plethora of interesting bugs, but hey, that's how the user made web is, i guess.
27 notes
·
View notes
Text

Hire ASP.Net Developers - ☎ +1 9177322215
Empower your web solutions with Semiosis' ASP.NET Developers. Leveraging the versatility of ASP.NET, our team crafts dynamic and secure web applications tailored to your needs. From e-commerce platforms to enterprise systems, trust us for reliable ASP.NET development. Dial +1 9177322215 to discuss your project requirements and partner with us for exceptional results.
#ASP.Net#C#.Net Framework/.Net Core#MVC (Model View Controller)#WebForms#Entity Framework#SQL Server/Database Management#JavaScript#HTML/CSS#RESTful APIs#Visual Studio#Git/GitHub#Agile/Scrum methodologies#Azure/AWS (cloud platforms)#Testing/Debugging skills#Problem-solving#Object-oriented programming (OOP)#Team collaboration/communication#Responsive web design#Security best practices
0 notes
Text

Lockheed Martin delivers 75º APY-9 radar for the E-2D Advanced Hawkeye built by Northrop Grumman
Setting the standard in the development and delivery of Airborne Early Warning (AEW) radars.
Fernando Valduga By Fernando Valduga 01/30/2024 - 16:00 in Military
Lockheed Martin, under contract with Northrop Grumman for the U.S. Navy's E-2D Advanced Hawkeye, delivered the 75º APY-9 radar that provides the U.S. Navy with information mastery through revolutionary sensor capability. More Hawkeyes were built and delivered than any other AEW platform in the world.
“As the primary sensor of the E-2D, the APY-9 radar has a long legacy of providing agile deterrence for greater security of the 21st century,” said Chandra Marshall, vice president of radar systems and sensors business at Lockheed Martin. “Our main focus is to bring our military and women home safely, and the APY-9 sets this standard for all other AEW radars.”
The newest Advanced Hawkeye variant is at the forefront of technological capacity, largely due to Lockheed Martin's APY-9 radar. The E-2 built by Northrop Grumman has become known as the "fleet eyes" of the U.S. Navy due to its ability to simultaneously monitor the air, land and sea. Whenever a Navy aircraft carrier has aircraft in the air, there is an APY-9 radar in operation, protecting the United States and its allies.

The U.S. Navy financed 80 of the 86 aircraft of the current purchase program. Japan bought 18 E-2D Hawkeyes and France bought three. With U.S. and international demand, APY-9 is expected to be in production by the end of the 2020s, and in modernization and support by the 2040s.
Lockheed Martin is a contributor to the E-2D built by Northrop Grumman for more than two decades. The E-2D Advanced Hawkeye platform provides critical and actionable data to enable decision mastery for joint forces and rescuers. These advances provide the armed forces with the necessary situational awareness to reduce the time between initial consciousness and active involvement.
Tags: Military AviationE-2D Advanced HawkeyeLockheed MartinNorthrop Grumman
Sharing
tweet
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, he has participated in several events and air operations, such as Cruzex, AirVenture, Dayton Airshow and FIDAE. He has works published in specialized aviation magazines in Brazil and abroad. He uses Canon equipment during his photographic work in the world of aviation.
Related news
MILITARY
UAS Aerosonde of Textron Systems performs operational flight from a Coastal Combat Ship
30/01/2024 - 14:00
Aurora's Liberty Lifter X-plane advanced in the preliminary tests.
MILITARY
Aurora modifies the design of the large Liberty Lifter aircraft
30/01/2024 - 09:00
MILITARY
Argentina decides to buy 24 American F-16 fighters instead of Chinese JF-17 jets
30/01/2024 - 06:00
BRAZILIAN AIR FORCE
VIDEO: See moment that FAB Super Tucano intercepts aircraft in Air Defense Identification Zone (ZIDA)
01/29/2024 - 23:48
HISTORY
14 years ago, I fled the first Su-57 (PAK FA)
29/01/2024 - 23:10
MILITARY
Czech Republic officially joins the global F-35 Lightning II team
29/01/2024 - 19:37
14 notes
·
View notes
Text
In today’s digital world, injustice lurks in the shadows of the Facebook post that’s delivered to certain groups of people at the exclusion of others, the hidden algorithm used to profile candidates during job interviews, and the risk-assessment algorithms used for criminal sentencing and welfare fraud detention. As algorithmic systems are integrated into every aspect of society, regulatory mechanisms struggle to keep up.
Over the past decade, researchers and journalists have found ways to unveil and scrutinize these discriminatory systems, developing their own data collection tools. As the internet has moved from browsers to mobile apps, however, this crucial transparency is quickly disappearing.
Third-party analysis of digital systems has largely been made possible by two seemingly banal tools that are commonly used to inspect what’s happening on a webpage: browser add-ons and browser developer tools.
Browser add-ons are small programs that can be installed directly onto a web browser, allowing users to augment how they interact with a given website. While add-ons are commonly used to operate tools like password managers and ad-blockers, they are also incredibly useful for enabling people to collect their own data within a tech platform’s walled garden.
Similarly, browser developer tools were made to allow web developers to test and debug their websites’ user interfaces. As the internet evolved and websites became more complex, these tools evolved too, adding features like the ability to inspect and change source code, monitor network activity, and even detect when a website is accessing your location or microphone. These are powerful mechanisms for investigating how companies track, profile, and target their users.
I have put these tools to use as a data journalist to show how a marketing company logged users’ personal data even before they clicked “submit” on a form and, more recently, how the Meta Pixel tool (formerly the Facebook Pixel tool) tracks users without their explicit knowledge in sensitive places such as hospital websites, federal student loan applications, and the websites of tax-filing tools.
In addition to exposing surveillance, browser inspection tools provide a powerful way to crowdsource data to study discrimination, the spread of misinformation, and other types of harms tech companies cause or facilitate. But in spite of these tools’ powerful capabilities, their reach is limited. In 2023, Kepios reported that 92 percent of global users accessed the internet through their smartphones, whereas only 65 percent of global users did so using a desktop or laptop computer.
Though the vast majority of internet traffic has moved to smartphones, we don’t have tools for the smartphone ecosystem that afford the same level of “inspectability” as browser add-ons and developer tools. This is because web browsers are implicitly transparent, while mobile phone operating systems are not.
If you want to view a website in your web browser, the server has to send you the source code. Mobile apps, on the other hand, are compiled, executable files that you usually download from places such as Apple’s iOS App Store or Google Play. App developers don’t need to publish the source code for people to use them.
Similarly, monitoring network traffic on web browsers is trivial. This technique is often more useful than inspecting source code to see what data a company is collecting on users. Want to know which companies a website shares your data with? You’ll want to monitor the network traffic, not inspect the source code. On smartphones, network monitoring is possible, but it usually requires the installation of root certificates that make users’ devices less secure and more vulnerable to man-in-the-middle attacks from bad actors. And these are just some of the differences that make collecting data securely from smartphones much harder than from browsers.
The need for independent collection is more pressing than ever. Previously, company-provided tools such as the Twitter API and Facebook’s CrowdTangle, a tool for monitoring what’s trending on Facebook, were the infrastructure that powered a large portion of research and reporting on social media. However, as these tools become less useful and accessible, new methods of independent data collection are needed to understand what these companies are doing and how people are using their platforms.
To meaningfully report on the impact digital systems have on society, we need to be able to observe what’s taking place on our devices without asking a company for permission. As someone who has spent the past decade building tools that crowdsource data to expose algorithmic harms, I believe the public should have the ability to peek under the hood of their mobile apps and smart devices, just as they can on their browsers. And it’s not just me: The Integrity Institute, a nonprofit working to protect the social internet, recently released a report that lays bare the importance of transparency as a lever to achieve public interest goals like accountability, collaboration, understanding, and trust.
To demand transparency from tech platforms, we need a platform-independent transparency framework, something that I like to call an inspectability API. Such a framework would empower even the most vulnerable populations to capture evidence of harm from their devices while minimizing the risk of their data being used in research or reporting without their consent.
An application programming interface (API) is a way for companies to make their services or data available to other developers. For example, if you’re building a mobile app and want to use the phone’s camera for a specific feature, you would use the iOS or Android Camera API. Another common example is an accessibility API, which allows developers to make their applications accessible to people with disabilities by making the user interface legible to screen readers and other accessibility tools commonly found on modern smartphones and computers. An inspectability API would allow individuals to export data from the apps they use every day and share it with researchers, journalists, and advocates in their communities. Companies could be required to implement this API to adhere to transparency best practices, much as they are required to implement accessibility features to make their apps and websites usable for people with disabilities.
In the US, residents of some states can request the data companies collect on them, thanks to state-level privacy laws. While these laws are well-intentioned, the data that companies share to comply with them is usually structured in a way that obfuscates crucial details that would expose harm. For example, Facebook has a fairly granular data export service that allows individuals to see, amongst other things, their “Off-Facebook activity.” However, as the Markup found during a series of investigations into the use of Pixel, even though Facebook told users which websites were sharing data, it did not reveal just how invasive the information being shared was. Doctor appointments, tax filing information, and student loan information were just some of the things that were being sent to Facebook. An inspectability API would make it easy for people to monitor their devices and see how the apps they use track them in real time.
Some promising work is already being done: Apple’s introduction of the App Privacy Report in iOS 15 marked the first time iPhone users could see detailed privacy information to understand each app’s data collection practices and even answer questions such as, “Is Instagram listening to my microphone?”
But we cannot rely on companies to do this at their discretion—we need a clear framework to define what sort of data should be inspectable and exportable by users, and we need regulation that penalizes companies for not implementing it. Such a framework would not only empower users to expose harms, but also ensure that their privacy is not violated. Individuals could choose what data to share, when, and with whom.
An inspectability API will empower individuals to fight for their rights by sharing the evidence of harm they have been exposed to with people who can raise public awareness and advocate for change. It would enable organizations such as Princeton’s Digital Witness Lab, which I cofounded and lead, to conduct data-driven investigations by collaborating closely with vulnerable communities, instead of relying on tech companies for access. This framework would allow researchers and others to conduct this work in a way that is safe, precise, and, most importantly, prioritizes the consent of the people being harmed.
11 notes
·
View notes
Text
Custom Software And App Development Company Based Within The Us
We arrange devoted development centers for our long-term customers to serve as their full-scale software engineering hubs with hand-picked skills and assets to satisfy their business requirements. We associate with world-class companies to construct internet functions, cell apps, IoT methods, APIs, and AI instruments. Our software products are priced competitively, offering prospects with cost-effective solutions that ship a high return on funding. The company is versatile and open to customizing our offerings, services to meet the unique wants of the customer.
With sixteen years of expertise main the development of service-oriented web purposes, I even have been responsible for the delivery of many performance-critical functions. In distinction, off-the-shelf software provides a quick, cost-effective option with a broad utility scope but might have more specificity and integration capabilities for enterprise-wide necessities. Developing custom software is typically more secure because it's not a recognized goal for hackers. Security measures may be tailor-made to your specific requirements, making it much less susceptible to external threats, to guard sensitive knowledge, making certain compliance with industry laws. This contains practical testing to ensure the software meets its specs, in addition to performance, safety, and other types of software testing strategies and approaches.
Get an ideal mash-up of devoted engineers, prime tech expertise, and stellar project ideas. With a MVP, you possibly can check the market demand for your thought, gather priceless feedback, and make knowledgeable decisions on the means to move forward with your business. We might help you write or rewrite your software to be accessed safely in the cloud regardless of where it lives right now. It’s too essential to you, your organization, and our nation to belief sending your software ideas abroad in the perception that one method or the other, it’s going to be cheaper. However, in accordance with a unique examine, 80% of shelf software features have been not often or never used. Off-the-shelf software is the device for you if you want something that is instantly usable and capable of handling many user profiles.
Tackle any challenge with custom purposes that improve productivity, efficiency and your backside line. Our software products come with complete technical assist, so users can get the assistance they want when they want it. Our software merchandise prioritize the safety of customers' data and are equipped with advanced security measures to protect in opposition to cyber threats. Our software products are designed to assist users be more productive by automating tasks, lowering handbook effort and saving time.
Our technological guidance for enterprises is your ticket to hassle-free digital transformation, which inevitably is overtaking the enterprise sector. Energize your corporation performance with streamlined processes, information integration, responsive software infrastructure, and scalable systems. Content Management Systems are software purposes that enable organizations to create, manage, and publish digital content material on their websites or different online platforms. CMS permits users to simply update and modify website content material without requiring technical experience. It offers options similar to content material creation, modifying, publishing, version control, and workflow administration.
software development companies uk
optimization. The clamor for personalised and efficient software solutions is rising exponentially in the quickly evolving business setting, permitting organizations to fulfill particular needs and streamline operations. Custom software development has emerged as a beacon of innovation, providing tailor-made solutions that align with particular person enterprises’ unique calls for and objectives. Saving costs and enhancing the quality of work can be done by coding greatest practices into the shared software platform, which is easy to discover and to adopt by the Agile squads. Moreover, using planning strategies prevents teams from getting lost as a result of unclear necessities and mistaken assumptions, focusing on deliverables in the context of impacts they're supposed to attain. Agile project management is critical as a end result of complexity of various software tasks.
Design safe dashboards with key business, monetary and operational indicators, delivered immediately with the power to drill down to every single digit. Prototype to “fail fast” or enrich and strengthen your idea, ship a product model for accumulating feedback from early adopters, and put together a basis for a full-fledged roll-out. When you have a remote workforce, your telecommuting coverage ought to address expectations, necessities, and the distant tools and communication strategies allowed. Displaying only the information remote workers need – and safeguarding the rest of your information – enables you to enable collaboration and keep your company information protected from data breaches.
When companies build custom packages in-house, builders can contemplate the company’s present hardware capabilities whereas building the software. Still, it typically includes lively participation in necessities gathering, suggestions and approval throughout design and development, and collaboration in testing and quality assurance efforts. We developed a mobile app for this iconic motorbike model that transforms fan engagement. The app permits exhibition staff to seamlessly seize data from prospective prospects, enriching... Build a really user-oriented digital product with an skilled group that makes use of clear and effective design solutions.
Enrich your users’ expertise with new options, optimize solutions, and increase efficiency with cloud and DevOps practices. Start advancing in the modern digital transformation setting by evaluating opportunities and applying the right technology alongside custom software engineering companies along with your finish objective in thoughts. With custom applications, your software solutions will develop and change with your corporation. We leverage deep automation, machine studying, and cloud transformation to transform your present techniques into agile and extremely environment friendly platforms.
#software development companies uk#uk software company#software solutions#business software solutions#custom software solutions
3 notes
·
View notes
Link
An essential component of modern software patterns, such as microservices architecture, is the Application Programming Interface (API). It enables software applications to communicate with each other seamlessly. However, the widespread use of APIs increases the risk of cyberattacks. API cyber security involves protecting APIs against malicious attacks and preventing unauthorized access to sensitive data. Visit us https://www.appzlogic.com/securing-your-api-best-practices-for-protecting-your-data-and-users/
0 notes