#DoD collaborations
Text


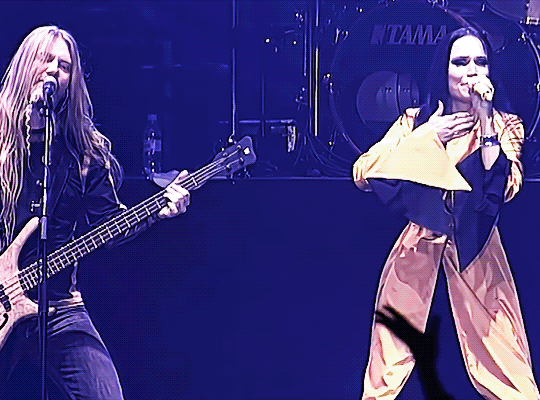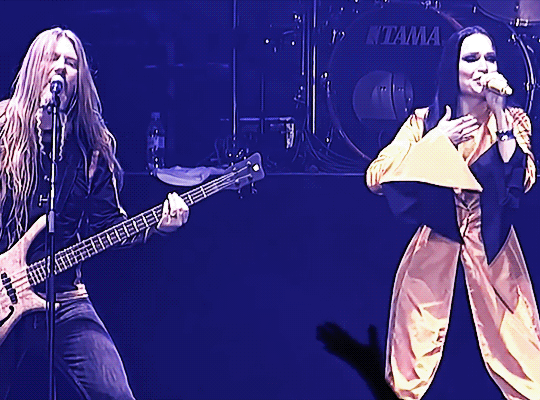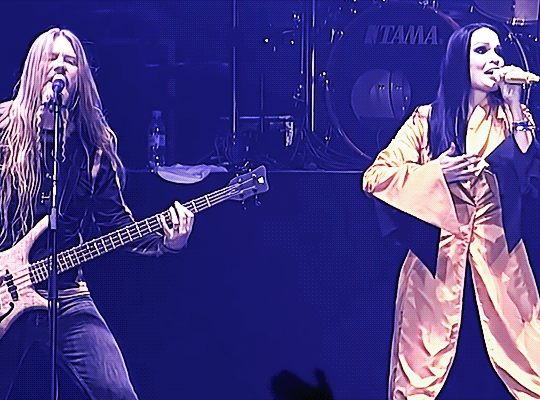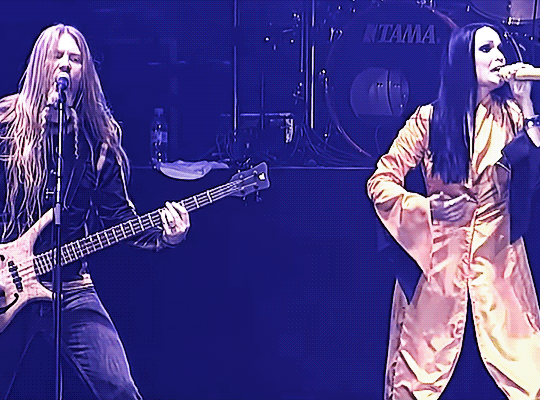



TARJA TURUNEN & MARKO HIETALA ✤ 18 years later (2005 - 2023)
Performing 'The Phantom of the Opera' #MetalMonday
#tarja turunen#dod collaborations#marko hietala#the phantom of the opera#dod metal monday#TT gifs#dod gifs#nightwish#flashing image warning
174 notes
·
View notes
Text
Fiona's Bio

"Everyone... please forgive me... it's all my fault..."
More details about Fiona is under the cut
Name: Fiona Soféinaith
Age: 182
Height: 157 cm
Birthday: 2 Primna 1056 (Alfabr)
Orientation: Cisgender Greyromantic Asexual Female
Pronouns: She/Her
Species: Dullahan (formerly elf)
Title: The Twelfth Dullahan
Country of Birth: Balwirk
Likes: The Eleventh Dullahan, everyone apart from her being happy
Dislikes: Everyone apart from her being sad, gaps in her memory (when she's aware of it)
Hobbies: She doesn't know/remember
Personality: Blames herself often, breaks down easily and frequently due to the emotional toll she has after absorbing the negative emotions of others
Style: Loose clothing that covers as much skin as possible, a huge fan of long skirts
Status: Dead (DOD: 27 Alstas 1238)
Abilities: Shadow manipulation, able to use absorption magic
Background: Born with weak health, Fiona tended to fall sick easily. While no one said anything, she always thought that those around her saw her as a burden and sought to make herself useful. She usually spent time with Dylan, who lived near her
Due to her poor health, her parents researched ways to make her healthier. Eventually, they collaborated with Gerald's father, a fellow researcher, on ways to preserve life even after the head was severed from the neck as he wanted to save his son, who was dying from the fatal Respiratree Disease. Soon, they had gathered a group of like-minded elves who were desperate to save their loved ones and began coming up with theories
This had resulted in whispers of their activities floating amongst the elves in Balwirk. Sometime in 1149, the researchers received anonymous notes suggesting them to use the Balwirkian elves as test subjects in order to save their loved ones. Desperate for a cure, the researchers did what was suggested and started to kidnap numerous elves close to the ages of their loved ones
While Gerald had survived the experiment, many others didn't and the experiment was revealed to have an extremely low success rate. Not wanting Fiona to die, they decided to perform the risky experiment under the guise of making her feel better. To sell the ruse, they had to agree to allow Dylan to accompany her at Fiona's request. Her parents then performed the experiment on them, and was initially distraught when Fiona didn't wake up after it was complete
They were thrilled when she woke up, and declared the experiment to be a success. Fiona didn't understand what was going on and was horrified to learn that her head was no longer attached to her body. Her parents then used a sharp object to scar a 12 on her left hand, declaring that she was the twelfth success. Fiona, starting to worry that her parents did something unforgivable, demanded them to explain. Her parents ignored her, leading her to a barren bedroom where Dylan was and locked her inside
Dylan informed her that her parents as well as Gerald's father caused their current states and blamed Fiona for them being abominations. He then tried to convince her to free him of the anti-magic restraints for years, with Fiona agreeing to do so eventually but unsure how to go about it. Annoyed by her uselessness, Dylan was about to beat Fiona up but suddenly became a shadow, which allowed him to escape from the restraints. Now able to use magic, he was able to blast open the door where they were greeted by the corpses of the elven researchers
Fiona then saw her parents amongst the bodies, which Dylan had to poke his fingers into her eyes to temporarily blind her from witnessing the bloody mess. She could only feel herself being dragged by her friend as she heard shouts from others that the exit was a certain way. While still blinded, she was led to a gathering room where she heard 14 other voices talking. Fiona then learnt that there were only a total of 16 survivors, and that there were thousands of victims
She was so horrified, she could barely register when Brianna and Danielle sought to get an unanimous consensus that under no circumstances should the 16 turn others into dullahans unless the individual in question was prepared to bear the curse of being one, let alone that they had devised a way to safely turn someone into a dullahan
After reaching a consensus, she went home and stumbled upon her parents' journals detailing their worry for Fiona's ailing health right up to the low survival rate of the experiment. Realising that she was the main reason to why the experiment existed, she blamed herself and decided to use her magic to absorb the grief of the victims' loved ones. She spent seven decades doing so, with each act taking a toll to her already fragile mental health. There were times when others would point out details that made her realise that there were gaps in her memory, and she was started to become concerned about strange red stains on the floors of various rooms in the house. She was unsure why she almost immediately decided that it was remnant bloodstains from her parents' experiments, but was happy to indulge in that notion as to other alternatives
Nearing midnight of 27 Alstas 1238, Dylan had visited her as there had been reports about the Soféinaith residence starting to smell of rotten bodies. When Fiona answered the door, she asked if there would be a day when the elves would forgive her for her parents' wrongdoings. Dylan, who was tired and fed up with Fiona's emotional nature, informed her that the only way she could make it up to the thousands who died, as well as the 14 original dullahans save for Gerald as his father was also involved, was for her to pay with her life
Fiona nodded, grateful that even with her failing memory and cursed existence, Dylan provided her with sound advice and thanked him profusely. The Eleventh Dullahan then left, grumbling about how Fiona should clean up her place lest he was forced to make an unwanted trip to the Soféinaith residence. She did what Dylan had grumbled about and spent four hours cleaning her place, then overdosed on copious amounts of Jilted Lover's Dream, never to wake again...
Former Appearance:

#Hallowed Hotel#Fiona Soféinaith#tw death#tw murder mention#tw eyestrain#tw scars#tw suicide#Altair draws
6 notes
·
View notes
Text

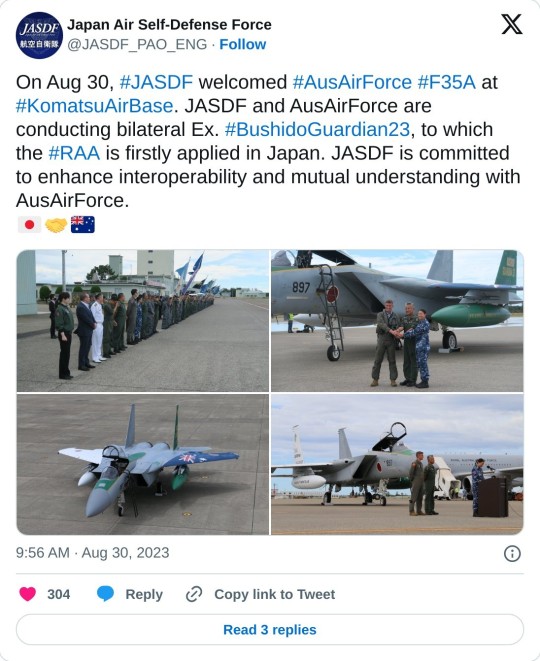
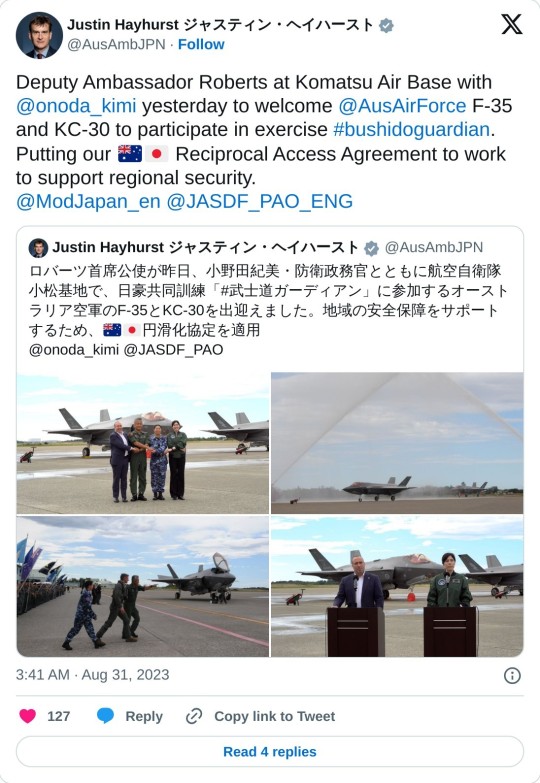
Exercise Bushido Guardian brings together Japan and Australia
Fernando Valduga By Fernando Valduga 09/08/2023 - 12:00 in Military
Three of the six F-35A fighters of the Royal Australian Air Force en route to Japan, where they will participate in the joint exercise Bushido Guardian. (Photo: Australian DoD)
The Royal Australian Air Force (RAAF) sent six F-35A Lightning II aircraft to Japan for the first time as part of Exercise Bushido Guardian 23.
The exercise takes place at Komatsu Air Base until September 15 and includes bilateral air combat training between the RAAF and the Japan Air Self-Defense Force (JASDF).
PLEASE TAP RELOAD TO VIEW👇
The F-35As of the FAAF will conduct training along with the air capabilities of the fourth and fifth generation JASDF, including the Japanese F-35As.
Air Marshal Rob Chipman, Head of the FAAF, said the exercise showed strength in Australia and Japan's commitment to a strong bilateral strategic partnership.
“The Bushido Guardian 23 exercise will increase our interoperability with JASDF, on the ground and in the air,” said Air Marshal Chipman. “Developing a mutual understanding of how each of us operates the F-35A is essential to how Australia and Japan contribute to the collective security of the Indo-Pacific.

"Our aviators will develop their skills abroad, 5,800 kilometers from home, and establish professional relationships with their Japanese colleagues."
The first Bushido Guardian Exercise was held in Japan in 2019, and this year's exercise is based on the success of the recent cooperation in the Pitch Black and Cope North exercises.
“The Bushido Guardian 2023 exercise follows a visit by the JASDF F-35As to the RAAF Tindal Base, which is the first time that the F-35As from Japan have embarked on an international visit,” said Air Marshal Chipman. "Collaboration in bilateral exercises throughout the Indo-Pacific provides both nations with valuable experiences in overcoming the challenges of distance in our common region."
In August 2023, the Australia-Japan Reciprocal Access Agreement entered into force, providing opportunities for more sophisticated cooperation between both nations.
Tags: Military AviationJoint ExercisesJASDF - Japan Air Self-Defense Force/Japan Air Self-Defense ForceRAAF - Royal Australian Air Force/Royal Australian Air Force
Sharing
tweet
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, he has participated in several events and air operations, such as Cruzex, AirVenture, Daytona Airshow and FIDAE. He has work published in specialized aviation magazines in Brazil and abroad. Uses Canon equipment during his photographic work throughout the world of aviation.
Related news
MILITARY
Boeing earns $474.5 million to provide EW systems for the Japanese F-15J
08/09/2023 - 11:00
MILITARY
The US should store nuclear weapons in Poland, says report
08/09/2023 - 08:35
MILITARY
IMAGES: Lockheed Martin presents the first F-16 Block 70 for Slovakia
07/09/2023 - 19:06
MILITARY
BOEING: F-15EX fighters for Poland
09/07/2023 - 12:10
MILITARY
Russian Shahed drones exploded in Romania, but Romanian president denies
06/09/2023 - 21:22
MILITARY
US plans to send more F-35 fighters to the UK amid tensions with Russia
09/06/2023 - 16:00
homeMain PageEditorialsINFORMATIONeventsCooperateSpecialitiesadvertiseabout
Cavok Brazil - Digital Tchê Web Creation
Commercial
Executive
Helicopters
HISTORY
Military
Brazilian Air Force
Space
Specialities
Cavok Brazil - Digital Tchê Web Creation
7 notes
·
View notes
Text

With the Ford’s departure, the USS Eisenhower is the lone US aircraft carrier in the region as tensions increase over Houthi attacks on commercial shipping in the Red Sea.
The Houthis have launched dozens of attacks on commercial vessels since October 7, saying they are acting in solidarity with Hamas amid the group’s war with Israel.
Over the weekend, US forces, including helicopters operating off the Eisenhower, had their first deadly confrontation with Houthi units, sinking three Houthi boats that had attacked a commercial ship and fired at the US copters that came to its aid.
“The US Navy helicopters returned fire in self-defense, sinking three of the four small boats, and killing the crews. The fourth boat fled the area,” a statement from US Central Command said.
US Sixth Fleet said even with the departure of the Ford, the US Navy retains “extensive capability both in the Mediterranean and across the Middle East.”
The Sixth Fleet statement said the amphibious assault ship USS Bataan, which can carry Marine Corps F-35 stealth fighters, as well as the dock landing ship USS Carter Hall and amphibious transport dock USS Mesa Verde were operating together in the eastern Mediterranean.
US guided-missile destroyers, including some of which have brought down Houthi drones and missiles in recent weeks, are also in the region, Sixth Fleet said.
In addition, the US has begun Operation Prosperity Guardian, a maritime coalition aimed at beefing up security in the southern Red Sea.
“We are collaborating with Allies and partners to bolster maritime security in the region. DoD will continue to leverage its collective force posture in the region to deter any state or non-state actor from escalating this crisis beyond Gaza,” the Sixth Fleet statement said.
2 notes
·
View notes
Text
4 notes
·
View notes
Text
Hallmark Teams Up With U.S. Air Force for Upcoming Romance, Filmed Scenes on Nevada Base (Variety Exclusive)

Hallmark Movies and the United States Air Force Thunderbirds have collaborated to produce the upcoming romantic film “Come Fly With Me,” set to premiere on Sept. 15 at 9 p.m. ET. on Hallmark Moves & Mysteries.
Directed by Michael Robison, the film stars Heather Hemmens as Capt. Emma Fitzgerald, who receives a two year assignment at Nellis Air Force Base with the Thunderbirds team, the Air Force’s famed demonstration squadron. While there, her daughter Lucy (Pietra Castro) becomes friends with Alice (Georgia Acken), the daughter of a civilian widower named Paul (Niall Matter). The two girls hatch a plan to bring their single parents together, with Lucy hoping it will keep her mother from continuing to move around.
“Emma and Paul are drawn to each other and a spark develops, but Emma is overwhelmed by the demands of her Thunderbirds training and tells him she needs to focus on her flying,” the official description reads.”But when Alice’s health suddenly worsens, the thing keeping Emma and Paul apart could be what ultimately brings them all together.”
“Through this beautiful story, Hallmark Media is honored to celebrate and thank the commitment made by members of the military – and their families – as they serve our country,” says Elizabeth Yost, senior vice president of development, programming at Hallmark Media. “It is a long-standing priority for us to create movies set in this world, which resonate strongly with our viewers. We’re so proud to partner with the United States Air Force and DoD to bring this special, heartfelt story to life.”
To read the full article at Variety just click this LINK.
#news#hallmark movies#link#come fly with me#hallmark movies & mysteries#heather hemmens#niall matter
2 notes
·
View notes
Text
A House of Brick
You want to know your cars are safe to drive, your plane's jet propulsion isn't hackable, and that when you didn't get those concert tickets, it wasn't because someone else used robots to steal them first. What if I told you building something safe is relatively new to the cyber landscape? That before something called DevSecOps, people would build whole websites, whole apps, then have someone try to attack it, then run repairs?
It's the equivalent of having one of the fairy tale piggies build their house out of straw first, then have the wolf come check it.
DevSecOps is the process of making sure you're building something strong before, during, and after the building process. It's having someone there to make sure you're using bricks, not straw, not wood.

Development, security and operations. It's the marriage between building something, making sure it works, and making sure its safe.
This is all based on the need for software that's of good quality, secure, and stable. DevSecOps makes software faster to create, easier to fix or update more often, and generally safer. Most importantly it brings security to the table during the build process rather than as an afterthought. This makes risk management much easier as well, looking forward to incidents rather than taking action after one.
What does a company need in order to perform DevSecOps?
1 - a decided strategy
2 - software application lifecycle concepts explained through various means which merge all three components of development, security, and operations
3 - reference guides with in-depth and technical information
Let's go over each:
1 - Strategy
This could be just a summary of goals from an executive board, it could be a set of principles the company wants to uphold, or even a set of requirements from a group in charge, like the government or shareholders. There needs to be some point on the compass to guide everything else.
Strategy in DevSecOps is about having several versions of action from higher management. This includes something called cATO, or Continuous Authorization to Operate. This is basically saying we do checks and real-time metrics through the whole software supply chain instead of taking a snapshot every 3 years. (Read the DOD DevSecOps Strategy Guide Here)

2 - Fundamentals, Guidebooks, and Playbooks
Basic lifecycles, topic-specific guidebooks or playbooks, white papers, industry best practices, using jargon and ideas that everyone knows, mapping tools and tasks, and keeping up with SMART metrics (Specific, Measurable, Achievable, Relevant, and Timely); You don't have to reinvent the wheel but you should be looking at the blueprints other people agreed work for wheel making when you're building one. (Read the DOD DevSecOps Fundamentals Here)
Guidebooks have topic-specific in-depth specifications and Playbooks are usually a single-page "plays" (think sports "plays") which have tips, points, checklists, and actionable tasks to take. (Read the DOD DevSecOps Playbook Here) (Read the DOD DevSecOps Fundamentals Guidebook Here)
You might hear the phrase CI/CD Pipeline, standing for Continuous Integration and Continuous Deployment Pipeline. This just means that we're checking things while we build, test, and deploy code. Don't get tripped up on the word "pipeline" - it's literally just referring to the fact that work is going sideways between people like water in a pipe.
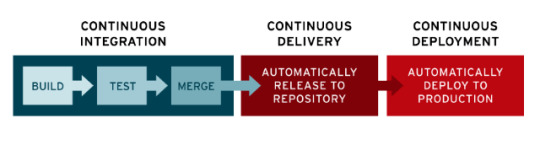

3 - Getting Technical
A DevSecOps reference design document takes everything that came before it and gets even more technical, merging similar names for things and getting rid of redundancy or inconsistency. This way we're all on the same page of what exactly is happening or should be done.
Okay, so what does DevSecOps look like?
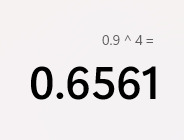
It looks like a bunch of meetings, collaborating between teams, feedback loops to check everything, and agile workflow (meaning everything goes round and round). DevSecOps changes the mindsets of a lot of teams and environments. A company has to pick a reference design platform with a cATO that works for their needs. When they do risk management, decimal percentages are multiplied in order to prove a company's level.
(for example, all four sections being 90% secure equates to .9 * .9 * .9 * .9 = .6561, so your company is actually only 65% secure, NOT 90%)
DevSecOps looks like a "software factory" sitting on a specific software supply chain. This factory has automation, process flows, control gates, pipeline controls, and flows like a wheel constantly checking for security and stabilization during code development.
This looks neat. Where to start?
Let's break down Strategy, where it all begins. Start with DevSecOps Guiding Principles:
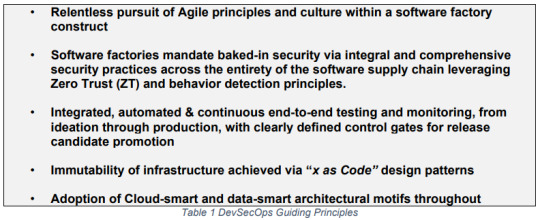
If you haven't heard of the Agile Manifesto, you can read them here. Their principles basically state that people, code that works, and responding to change are more important than tools, documents, contracts, and plans.
The software factories run development, operations, and security simultaneously. You'll hear the term "baked-in security" eliciting the imagery that your software is a three-tier wedding cake, but again this just means we're all working together and communicating mid-development, not tossing the software back and forth like a volley ball.

Remember cATO is continuous testing and risk assessing people, platforms, processes using real-time analytics. This is concentrating on protecting assets, not network segments, a technique called Zero Trust Architecture (see NIST SP 800-27 for more detail).
"X as Code" or "Everything as Code" is good because things can go wrong when a human is following a guide step-by-step to set whole systems up. It also makes sure whoever's running the code knows exactly what's going to happen when they run it. There's a difference between reading and running a function versus just hitting a button and expecting results. It also sets up a "standard deployment model" - basically giving you a safe template to use for other software. This can easily be scanned, updated, scraped, and analyzed. Code is king because "code can be version controlled, tested, peer reviewed, and its execution (logs) tracked" (Unclassified, 2020).

You want everything cloud-smart and data-smart. A cloud is just someone else's computer, but it comes with perks like paying someone else to deal with storage space or your data's security, depending on the cloud service provider, CSP, you're using and what type of package you bought with them. Your architecture needs to be just as up-to-date and savvy with modern designs, though. Architecture is just as complex through cloud as it always has been.
Management structure is both bottom-up and top-down. Direction should be taken based on a company's mission statement (see my prior blog post for more on this). Automate everything you can. Be adaptable, transparent, and accountable. Use DODI 8510.01 for risk management framework and use CJCM 6510.01B for incident handling (but be aware of challenges like fluid system boundaries in microservice architecture, nontraditional system boundaries in distributed services and constant system evolutions).
All in all, here's what it looks like, including continuous monitoring:

For more information go to https://dodcio.defense.gov/Library/ and search for devsecops for an up-to-date declassified modern software practices.
Sources:
Rose, S., Borchert, O., Mitchell, S., & Connelly, S. (2020, August 11). Zero Trust Architecture. Csrc.nist.gov. https://csrc.nist.gov/publications/detail/sp/800-207/final
This document automatically expires 1-year from publication date unless revised. DevSecOps Playbook CLEARED For Open Publication Department of Defense OFFICE OF PREPUBLICATION AND SECURITY REVIEW. (2021). https://dodcio.defense.gov/Portals/0/Documents/Library/DevSecOps%20Playbook_DoD-CIO_20211019.pdf
Unclassified, U. (2021). DoD Enterprise DevSecOps Strategy Guide Department of Defense OFFICE OF PREPUBLICATION AND SECURITY REVIEW. https://dodcio.defense.gov/Portals/0/Documents/Library/DoDEnterpriseDevSecOpsStrategyGuide.pdf
What is a CI/CD pipeline? (n.d.). Www.redhat.com. https://www.redhat.com/en/topics/devops/what-cicd-pipeline
4 notes
·
View notes
Text







NITA STRAUSS & ALISSA WHITE-GLUZ
Performing 'The Wolf You Feed' live for the first time at Montréal, Canada
#MetalMonday (x)
#nita strauss#alissa white gluz#dod collaborations#the wolf you feed#DoD Metal Monday#flashing image warning#flashing image tw#dod gifs#metal ladies#metal music#NS gifs#AWG gifs
81 notes
·
View notes
Text
U.S. Builds Gaza Pier for Aid Delivery

Under the direction of President Joe Biden, the U.S. military has commenced construction on a temporary pier off the coast of Gaza.
Additionally, to address urgent humanitarian needs, the U.S. military, under Biden’s direction, has started building a temporary pier off Gaza’s coast. This strategic move aims to streamline aid delivery amidst ongoing regional challenges, ensuring timely support to those in need.
The Need for Swift Humanitarian Action
In recent months, Gaza has faced escalating humanitarian challenges that necessitate immediate international response. The construction of the temporary pier is a direct outcome of President Biden's commitment, announced in his State of the Union Address, to bolster humanitarian efforts in the region.
The initiative not only aims to deliver aid more efficiently but also symbolizes a robust collaboration between the U.S. and Israeli Defense Forces.

The Defense Department announced it would implement a Joint Logistics Over-the-Shore capability from the Mediterranean Sea to provide logistics access to Gaza. Photo by DOD.
The Construction Effort
Soldiers from the Army's 7th Transportation Brigade and sailors from Naval Beach Group 1 have been pivotal in deploying the Defense Department's Joint Logistics Over-the-Shore capabilities.
The construction involves assembling an approximately 1,800-foot Trident Pier from modular sections. This logistical feat will ultimately support the delivery of 90 to 150 truckloads of aid per day, once fully operational.
Cooperation with the Israeli Defense Force is central to this project. The Israeli Defense Forces not only provides force protection for U.S. personnel but also assists in integrating the pier with Gaza’s shoreline infrastructure. This partnership underscores a significant alignment of goals and resources, ensuring the safety and efficacy of the operation.
Enhancing Aid Delivery
The pier’s completion is expected to significantly enhance the delivery speed and volume of international aid. By facilitating a direct maritime aid corridor, the U.S. and its partners can bypass traditional logistical hurdles that often delay relief efforts.
The roll-on, roll-off discharge facility, stationed three miles off Gaza's shore, will allow cargo ships to efficiently offload aid shipments, which are then transported to shore.
Challenges and Opportunities
While the temporary pier represents a critical step forward, the dynamic security environment requires constant reassessment. The U.S. Central Command continues to monitor the situation closely, adjusting plans as necessary to maintain the safety of all personnel involved.
Looking ahead, the success of this project may serve as a blueprint for future humanitarian aid missions in other conflict-affected regions.
A Commitment to Humanitarian Support
The U.S. initiative to construct a temporary pier in Gaza is a testament to the commitment of the Biden administration to support humanitarian causes through innovative logistics solutions.
Moreover, by closely collaborating with international partners and leveraging advanced military logistics, the U.S. aims to set a precedent for rapid, effective aid delivery in crisis situations.
This effort not only addresses immediate needs but also strengthens the foundation for sustained peace and stability in the region.
Sources: THX News & US Department of Defense.
Read the full article
#Bidenhumanitarianinitiative#Gazahumanitarianaid#internationalaidGaza#JointLogisticsOver-the-Shore#maritimeaidcorridor#militarylogisticsoperation#modularTridentPier#temporarypierconstruction#U.S.militaryGaza#U.S.-Israelcoordination
0 notes
Text
can you vpn into disa from home computer
can you vpn into disa from home computer
VPN access to DISA
Title: Unlocking Secure Access: Understanding VPN Access to DISA
In today's digital landscape, securing access to sensitive information is paramount, especially for government agencies like the Defense Information Systems Agency (DISA). With the increasing threats of cyber attacks, ensuring a robust yet flexible access mechanism is crucial. One such method gaining prominence is Virtual Private Network (VPN) access to DISA.
VPN access to DISA provides a secure pathway for authorized personnel to connect to DISA's network from remote locations. This technology encrypts data transmitted between the user's device and the DISA network, safeguarding it from interception or tampering by malicious actors.
One of the primary benefits of VPN access to DISA is its versatility. It allows personnel to access DISA resources securely from anywhere with an internet connection, whether they're working from home, traveling, or stationed in remote locations. This flexibility enhances productivity and ensures continuity of operations, even in challenging circumstances.
Moreover, VPN access to DISA adheres to stringent security protocols and standards mandated by the Department of Defense (DoD). It employs multi-factor authentication, encryption, and other advanced security measures to authenticate users and protect data integrity.
Additionally, VPN access to DISA helps mitigate the risks associated with public networks. By routing traffic through encrypted tunnels, it shields sensitive information from potential threats lurking on unsecured Wi-Fi networks or public hotspots.
However, despite its numerous advantages, VPN access to DISA requires careful implementation and management. It necessitates robust cybersecurity policies, regular updates, and proactive monitoring to prevent unauthorized access and potential vulnerabilities.
In conclusion, VPN access to DISA offers a secure and efficient means for authorized personnel to connect to DISA's network remotely. By combining advanced encryption techniques with comprehensive security measures, it ensures the confidentiality, integrity, and availability of sensitive information, bolstering DISA's mission in safeguarding national security interests.
Remote access to DISA network
Remote access to the Defense Information Systems Agency (DISA) network is a critical capability that allows authorized personnel to securely access DISA resources from any location. DISA plays a pivotal role in providing IT and communications support to the Department of Defense (DoD), making remote access essential for ensuring continuous operations and timely decision-making.
Remote access to the DISA network is typically established through Virtual Private Network (VPN) connections, which create a secure encrypted tunnel between the user's device and DISA's network infrastructure. To ensure the security and integrity of the network, DISA employs stringent authentication measures such as multi-factor authentication and access controls based on user roles and responsibilities.
Authorized users can access a wide range of resources on the DISA network remotely, including email services, collaboration tools, databases, and specialized applications essential for mission-critical activities. This capability enables personnel deployed in remote locations, teleworkers, and other authorized users to stay connected and productive without being physically present at a DISA facility.
It is crucial for users accessing the DISA network remotely to adhere to security best practices, such as keeping their devices updated with the latest security patches, using strong passwords, and following DISA's guidelines for secure remote access. By implementing these measures, users can help safeguard sensitive information and prevent unauthorized access to DISA's network infrastructure.
In conclusion, remote access to the DISA network is a vital component of the agency's mission to support the DoD's IT and communications requirements. By enabling authorized users to securely connect to DISA resources from anywhere, remote access enhances operational efficiency, collaboration, and continuity of services for the defense community.
Secure connection to DISA from home
Title: Ensuring a Secure Connection to DISA from Home
In an increasingly digital world, remote access to sensitive networks like the Defense Information Systems Agency (DISA) requires robust security measures. With the proliferation of telecommuting and the need for flexibility in work arrangements, ensuring a secure connection from home to DISA is paramount for maintaining data integrity and national security.
To establish a secure connection to DISA from home, several key steps must be taken:
Utilize Virtual Private Network (VPN) Technology: VPNs create a secure tunnel between the user's device and the DISA network, encrypting all data transmitted between them. This ensures that even if intercepted, sensitive information remains protected from unauthorized access.
Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security by requiring users to provide multiple forms of verification before accessing the network. This could include something they know (like a password), something they have (such as a security token), or something inherent to them (like a fingerprint or facial recognition).
Regular Software Updates and Patch Management: Keeping both the operating system and any software used to access DISA up to date is essential for addressing vulnerabilities and mitigating potential security threats.
Strong Password Policies: Enforcing complex password requirements and regular password changes reduces the risk of unauthorized access due to password guessing or brute-force attacks.
Network Monitoring and Intrusion Detection Systems: Continuous monitoring of network traffic and the implementation of intrusion detection systems help identify and respond to any suspicious activity or attempted breaches promptly.
Employee Training and Awareness: Educating employees on cybersecurity best practices and the importance of maintaining security protocols while working remotely is crucial for minimizing human error-related risks.
By adhering to these measures, individuals can confidently access DISA's network from home, knowing that stringent security protocols are in place to safeguard sensitive information and uphold national security standards.
Virtual private network for DISA access
A virtual private network (VPN) is a crucial tool for accessing the Defense Information Systems Agency (DISA) securely and efficiently. DISA, as a vital component of the Department of Defense (DoD), requires stringent security measures to safeguard sensitive information and communications. By utilizing a VPN, personnel can establish encrypted connections over public networks, ensuring the confidentiality, integrity, and authenticity of data exchanged with DISA servers.
One of the primary benefits of using a VPN for DISA access is the encryption it provides. With military-grade encryption protocols like AES (Advanced Encryption Standard), VPNs encode data transmissions, preventing unauthorized interception and eavesdropping. This encryption is especially crucial when accessing DISA networks from unsecured or public Wi-Fi hotspots, which are prone to cyber threats.
Moreover, VPNs offer anonymity by masking users' IP addresses. This feature enhances security by preventing potential adversaries from identifying and targeting DISA personnel or their devices. By routing traffic through remote servers located in different geographic locations, VPNs also help bypass regional restrictions and censorship, ensuring unrestricted access to DISA resources regardless of location.
Furthermore, VPNs enhance network performance by optimizing bandwidth and reducing latency. By utilizing efficient routing algorithms and dedicated server infrastructure, VPN providers minimize packet loss and ensure seamless connectivity to DISA networks, even during peak usage periods.
In conclusion, a VPN is an indispensable tool for DISA personnel seeking secure and reliable access to agency resources. By leveraging encryption, anonymity, and performance optimization features, VPNs facilitate seamless communication and collaboration while safeguarding sensitive information from cyber threats. As cyber warfare continues to evolve, adopting robust security measures like VPNs is essential for maintaining operational readiness and protecting national security interests.
Home computer VPN for DISA
A home computer VPN can be a valuable tool for those working with the Defense Information Systems Agency (DISA). By using a VPN, individuals can establish a secure connection to DISA's network from their home computer, ensuring the safety and confidentiality of sensitive information.
DISA deals with a vast amount of classified and sensitive data, making security a top priority for all employees and contractors. A VPN, or Virtual Private Network, encrypts data transmitted between the user's computer and the DISA network, preventing unauthorized access and potential data breaches.
Setting up a VPN on a home computer for DISA work involves installing VPN software provided by DISA, configuring the connection settings, and securely logging in with authorized credentials. Once connected, all data transmitted between the user's computer and DISA's network is encrypted, ensuring privacy and security.
By using a VPN for DISA work on a home computer, employees can access internal resources, collaborate securely with colleagues, and perform tasks without the risk of data interception or cyber threats. This added layer of security is crucial, especially when handling sensitive government information that must be protected at all costs.
In conclusion, a home computer VPN for DISA offers a secure and encrypted connection for employees and contractors, ensuring that sensitive information remains confidential and protected from unauthorized access. By implementing this security measure, individuals can work from home with peace of mind, knowing that their data is safe and secure.
0 notes
Text
A demonstração do XQ-58A ocorreu no momento em que o programa Penetrating Affordable Autonomous Collaborative Killer – Portfolio do Corpo de Fuzileiros Navais dos EUA completa sua fase inicial. Apresentando a capacidade do XQ-58A Valkyrie de voar ao lado de duas aeronaves F-35 e fornecer uma capacidade de ataque eletrônico integrada durante um evento de teste de voo ao vivo, a Kratos Defense & Security Solutions, Inc. Programa Penetrating Affordable Autonomous Collaborative Killer – Portfolio (PAACK-P) em 2 de abril de 2024, com uma demonstração bem-sucedida de sua Divisão de Sistemas Não Tripulados na Base Aérea de Eglin, Flórida. O Valkyrie, em operação desde 2019, demonstrou suas capacidades avançadas de ataque eletrônico ao detectar, identificar e geolocalizar de forma autônoma vários alvos de interesse. A aeronave transmitiu com sucesso coordenadas de rastreamento do alvo para ativos colaborativos e executou efeitos de ataque eletrônico não cinético contra múltiplos emissores. O XQ-58A Valkyrie oferece recursos táticos de UAV independentes de pista de alto desempenho, incluindo voos de longo alcance em altas velocidades subsônicas, flexibilidade operacional e acessibilidade para diversas aplicações do Departamento de Defesa. Steve Fendley, presidente da Divisão de Sistemas Não Tripulados da Kratos, expressou entusiasmo com a recente exibição do Valkyrie: “Estamos muito entusiasmados com a capacidade da missão demonstrada durante o voo e a incrível eficácia por custo que isso permite; para não mencionar a eliminação do risco para um piloto humano e a eliminação do risco para plataformas tripuladas caras.” Fendley destacou o esforço colaborativo envolvendo Kratos, Northrop Grumman e o Corpo de Fuzileiros Navais, sublinhando a importância destas tecnologias na consecução dos objectivos do Departamento de Defesa (DoD). A demonstração bem-sucedida segue uma modificação de contrato de US$ 22,9 milhões concedida em dezembro de 2023 para desenvolvimento adicional de engenharia e demonstrações de testes de voo. O programa PAACK-P visa informar os requisitos para a Força-Tarefa Aérea-Terrestre da Marinha (MAGTF), Sistema Aéreo Não Tripulado (UAS) Aeronave Expedicionária (MUX) Tática (TACAIR) para uso em uma função de Supressão de Defesa Aérea Inimiga (SEAD). O tenente-coronel Bradley Buick, oficial de capacidades, pesquisa e integração do Grupo Cunningham, enfatizou a importância das plataformas MUX TACAIR no aumento da letalidade e capacidade de sobrevivência das atuais plataformas tripuladas, indicando sua importância em novas estratégias de domínio aéreo: “Essas plataformas são o futuro da guerra aérea”. Fonte: Tecnologia da Força Aérea
0 notes
Text

Pentagon plans to develop new variant of the B61 gravitational nuclear bomb
Fernando Valduga By Fernando Valduga 11/01/2023 - 11:00am In Armaments, Military
The U.S. Department of Defense (DoD) announced that the United States will develop a modern variant of the B61 gravitational nuclear bomb, designated B61-13, pending authorization and appropriation by Congress.
The National Nuclear Safety Administration of the Department of Energy (NNSA) would produce B61-13. The decision to pursue this capability, which was taken in close collaboration with the NNSA, responds to the requirements of a rapidly evolving safety environment, as described in the 2022 Nuclear Posture Review.

The Pentagon announced that it plans to develop a new gravitational nuclear bomb to respond to the evolving safety environment, but it is not immediately clear why more free-fall nuclear bombs are needed in preference to missiles launched from the air with a nuclear warhead. (Photo: USAF)
“Today's announcement reflects a changing security environment and growing threats from potential opponents,” said Deputy Secretary of Defense for Space Policy John Plumb. “The United States has a responsibility to continue to evaluate and put into practice the capabilities we need to credibly deter and, if necessary, respond to strategic attacks, and secure our allies.”
The B61-13 would be delivered by modern aircraft, strengthening the deterrence of opponents and the safety of allies and partners, providing the U.S. President with additional options against certain more difficult and large-area military targets. It would replace some of the B61-7 of the current nuclear arsenal and would have a yield similar to that of B61-7, which is higher than that of B61-12.

“The B61-13 represents a reasonable step in managing the challenges of a highly dynamic security environment,” Plumb said. “Although it provides us with additional flexibility, the production of B61-13 will not increase the total number of weapons in our nuclear arsenal.”
The B61-13 would take advantage of the current and established production capabilities that support the B61-12 and would include the modern security, protection and accuracy features of the B61-12.

This initiative follows several months of review and consideration. The field entry of B61-13 is not a response to any specific current event; it reflects a continuous assessment of a changing safety environment.
The information sheet of the request can be read here.
Tags: weaponsMilitary AviationB61Nuclear
Sharing
tweet
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, has participated in several events and air operations, such as Cruzex, AirVenture, Dayton Airshow and FIDAE. He has work published in specialized aviation magazines in Brazil and abroad. Uses Canon equipment during his photographic work in the world of aviation.
Related news
MILITARY
India informs France of its decision to acquire 26 Rafale Marine jets
01/11/2023 - 09:00
MILITARY
Lockheed Martin guarantees contract to modernize Chilean Air Force F-16 fighters
01/11/2023 - 08:44
MILITARY
Spanish Navy awaits urgent decision to purchase F-35B fighters
31/10/2023 - 19:25
MILITARY
Ecuador orders additional C295 transport aircraft
31/10/2023 - 16:00
MILITARY
Elbit Systems will establish drone production center in the Czech Republic
31/10/2023 - 14:00
Iranian Army test fires Haydar air-to-ground missile from a Bell 214 attack helicopter of the Islamic Republic of Iran Army Land Force.
ARMAMENTS
Iranian army tests Heydar air-to-ground missile from an attack helicopter
31/10/2023 - 11:30
6 notes
·
View notes
Text

MIT Lincoln Laboratory Hosts Lidar Knowledge Sharing Event
Apr 04, 2024
DoD-NASA Lidar TIM: August 13-15, 2024
MIT Lincoln Laboratory, located at 241 18th St S, Arlington, VA 22202, is hosting a timely and crucial meeting between NASA and DoD, aimed at the exchange of lidar knowledge and identification of potential collaboration areas that leverage the strengths of both institutions. The event will focus on addressing common challenges and possible solutions in the field of lidar technology development and application.
CUI-level presentations and discussions led by leaders in lidar technology will be a part of the event. The key objectives include sharing of DoD & NASA capabilities in lidar systems, technologies, processing and analysis, identifying DoD and NASA mission needs that can utilize existing lidar investments, connecting lidar practitioners, experts and end-user communities from NASA and DoD, and outlining at least two potential applications for collaborative opportunities.
Participation will be open to representatives from NASA Centers, JPL, and various DoD organizations. More details about the event will be announced soon.
Stay Connected
Discover Related Topics
Source Link: Save-The-Date: DoD-NASA Lidar Technical Interchange Meeting (TIM)
0 notes
Text
Save-The-Date: DoD-NASA Lidar Technical Interchange Meeting (TIM)
Details DoD-NASA Lidar TIM August 13-15, 2024 MIT Lincoln Laboratory in Arlington, VA (Crystal City)241 18th St S, Arlington, VA 22202 MIT Lincoln Laboratory is hosting a TIM between NASA and DoD to facilitate the sharing of lidar knowledge between these institutions and identify potential areas of collaboration that maximally utilizes the strengths from each […]
from NASA https://ift.tt/NQTcdM6
0 notes
Text
The Growing Market for AI Spending in the U.S. Federal Government

youtube
Analyzing the Rise in AI Expenditures and Contracts
The use of artificial intelligence (AI) in the U.S. federal government has been on the rise, with a significant increase in spending and the number of contracts awarded. As the government recognizes the importance of AI in various sectors, the need for effective governance and regulation becomes crucial. In this article, we delve into the latest findings on AI spending in the federal government, exploring the trends, agencies involved, and the implications for the future.
Data and Methodology:
To gather the data for this analysis, we relied on federal contracts provided by Leadership Connect. The dataset included both existing contracts and new contracts that mentioned "artificial intelligence" or "AI" in their descriptions. We compared the values of funding obligated and the potential value of awards for the year following August 2022 to August 2023.
Findings:
The analysis revealed a refinement and focusing of categorization of AI work, with only 13 NAICS codes still in use from previous contracts and five used in new contracts. The value of funding obligated increased by over 150%, from $261 million to $675 million, while the potential value of awards skyrocketed by almost 1200%, from $355 million to $4.561 billion. NAICS 54 (Professional, Scientific, and Technical Services) was the most common code for funding obligated, followed by NAICS 51 (Information and Cultural Industries). For potential value of awards, NAICS 54 and 51 dominated, with a significant increase in contract values. The number of federal agencies with AI contracts also increased, rising from 17 to 23 in the last year. The Department of Defense (DoD) continued to dominate in AI contracts, with NASA and the Department of Health and Human Services (HHS) trailing behind. The DoD's AI contract values experienced a staggering 1500% increase, overshadowing other agencies. In terms of vendors, larger players such as Accenture, Booz Allen Hamilton, General Atomics, and Lockheed Martin entered the market, contributing to the significant increase in contract values.
Analysis:
The exponential increase in AI potential value of awards indicates a new imperative in government AI research and development. The market, though still fragmented with smaller vendors, is witnessing the entry of larger defense players. The shift from experimentation to implementation is evident, with a surge in large, maximum potential value contracts. While the DoD remains the primary focus of AI spending, other agencies are also investing, albeit on a smaller scale. The U.S. government's approach to AI development balances governance and capacity building, while potential adversaries prioritize R&D capacity. This substantial increase in spending suggests that the U.S. is ramping up its investment in AI to address potential threats. The growing market for AI spending in the U.S. federal government reflects the increasing recognition of AI's potential in various sectors. The rise in funding and contracts signifies a shift from experimentation to implementation, with larger players entering the market. While the federal market may appear fragmented, recent legislation and agency strategies demonstrate efforts to regulate and control the potential negative impacts of AI. The National Artificial Intelligence Initiative Office (NAIIO) serves as a framework for coordination, but more work is needed to streamline the federal market and catch up to global competitors like China. The recent Executive Order on AI regulation may provide a path towards monitoring and regulation in the future. As AI continues to shape the government landscape, effective governance and collaboration will be crucial for harnessing its full potential.
0 notes