#Android security
Text
4 notes
·
View notes
Text
गूगल के यह फीचर्स हैकर्स और वायरस से करते हैं आपके एंड्रोयड फोन की सुरक्षा
गूगल के यह फीचर्स हैकर्स और वायरस से करते हैं आपके एंड्रोयड फोन की सुरक्षा
New Delhi. Today mobile phone is one of the most important necessities of our life. It has become an important part of our life. It would not be wrong to say that our mobile knows everything about us. In such a situation, it is our responsibility to protect it. How secure or unsafe our Android phone or tablet is depends on how we use it?
According to Gadgets Now, Google has installed several…
View On WordPress
#android app#Android phone#android phone app#android phone phone safe from hackers#android security#android security features#Cyber Crime#features of android phone#hackers#hackers and viruses#mobile hackers#mobile safety#mobile Security#Protection from hackers and viruses
3 notes
·
View notes
Text
Alarming Privacy and Security Threats in Smart Homes Revealed - Technology Org
New Post has been published on https://thedigitalinsider.com/alarming-privacy-and-security-threats-in-smart-homes-revealed-technology-org/
Alarming Privacy and Security Threats in Smart Homes Revealed - Technology Org
A group of researchers from several international universities and research centres analyze the local network interactions of smart home IoT devices and mobile apps, and demonstrate that a variety of security and privacy threats exist.
An international team of researchers, led by IMDEA Networks and Northeastern University in collaboration with NYU Tandon School of Engineering, Universidad Carlos III de Madrid, IMDEA Software, University of Calgary, and the International Computer Science Institute, has unveiled groundbreaking findings on the security and privacy challenges posed by the ever-growing prevalence of opaque and technically complex Internet of Things (IoT) devices in smart homes.
Smart home control interface – illustrative photo. Image credit: DCStudio via Freepik, free license
Smart Homes: Trusted and Secure Environments?
Smart homes are becoming increasingly interconnected, comprising consumer-oriented IoT devices ranging from smartphones and smart TVs to virtual assistants and CCTV cameras. These devices have cameras, microphones, and other ways of sensing what is happening in our most private spaces—our homes.
An important question is, can we trust that these devices in our homes are safely handling and protecting the sensitive data they have access to?
“When we think of what happens between the walls of our homes, we think of it as a trusted, private place. In reality, we find that smart devices in our homes are piercing that veil of trust and privacy—in ways that allow nearly any company to learn what devices are in your home, to know when you are home, and learn where your home is. These behaviours are generally not disclosed to consumers, and there is a need for better protections in the home,” said David Choffnes, Associate Professor of Computer Science and Executive Director of the Cybersecurity and Privacy Institute at Northeastern University.
The research team’s extensive study, titled “In the Room Where It Happens: Characterizing Local Communication and Threats in Smart Homes,” was presented this week at the ACM Internet Measurement Conference (ACM IMC’23) in Montreal (Canada).
The paper delves for the first time into the intricacies of local network interactions between 93 IoT devices and mobile apps, revealing a plethora of previously undisclosed security and privacy concerns with actual real-world implications.
While most users typically view local networks as a trusted and safe environment, the study’s findings illuminate new threats associated with the inadvertent exposure of sensitive data by IoT devices within local networks using standard protocols such as UPnP or mDNS.
These threats include the exposure of unique device names, UUIDs, and even household geolocation data, all of which can be harvested by companies involved in surveillance capitalism without user awareness.
According to Vijay Prakash, PhD student from NYU Tandon who co-authored the paper, “analysing the data collected by IoT Inspector, we found evidence of IoT devices inadvertently exposing at least one PII (Personally Identifiable Information), like unique hardware address (MAC), UUID, or unique device names, in thousands of real world smart homes.
Any single PII is useful for identifying a household, but combining all three of them together makes a house very unique and easily identifiable. For comparison, if a person is fingerprinted using the simplest browser fingerprinting technique, they are as unique as one in 1.500 people. If a smart home with all three types of identifiers is fingerprinted, it is as unique as one in 1.12 million smart homes.”
These local network protocols can be employed as side-channels to access data that is supposedly protected by several mobile app permissions such as household locations. “A side channel is a sneaky way of indirectly accessing sensitive data.
For example, Android app developers are supposed to request and obtain users’ consent to access data like geolocation. However, we have shown that certain spyware apps and advertising companies do abuse local network protocols to silently access such sensitive information without any user awareness.
All they have to do is kindly asking for it to other IoT devices deployed in the local network using standard protocols like UPnP.”, said Narseo Vallina-Rodriguez, Associate Research Professor of IMDEA Networks and co-founder of AppCensus.
“Our study shows that the local network protocols used by IoT devices are not sufficiently protected and expose sensitive information about the home and the use we make of the devices. This information is being collected in an opaque way and makes it easier to create profiles of our habits or socioeconomic level,” adds Juan Tapiador, professor at UC3M.
The Wider Implications
The impact of this research extends far beyond academia. The findings underscore the imperative for manufacturers, software developers, IoT and mobile platform operators, and policymakers to take action to enhance the privacy and security guarantees of smart home devices and households.
The research team responsibly disclosed these issues to vulnerable IoT device vendors and to Google’s Android Security Team, already triggering security improvements in some of these products.
Source: Universidad Carlos III de Madrid
You can offer your link to a page which is relevant to the topic of this post.
#advertising#android#android security#app#apps#awareness#browser#Cameras#Canada#channel#Collaboration#communication#Companies#computer#Computer Science#conference#consumers#cybersecurity#data#developers#devices#employed#engineering#Environment#Featured technology news#Google#Hardware#Hardware & gadgets#international team#Internet
0 notes
Text
Is My Android Listening To Me? Experts Expose The Truth!
View On WordPress
0 notes
Text
Late or never Android updates remain a problem
Late or never Android updates remain a problem
Here’s yet another unintentional benefit of my shattering my Pixel 5a’s screen last weekend: an opportunity to reacquaint myself with how slowly many Android smartphone manufacturers still ooze out Google’s system updates.
This is not a new problem, as I can see from re-reading a piece I wrote almost 10 years ago that’s aged a little too well. I had thought that architectural changes Google made…
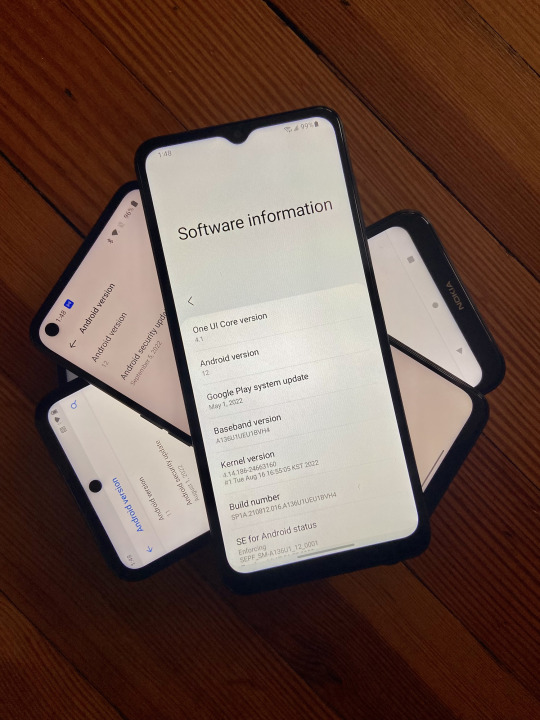
View On WordPress
#Android 11#Android 12#Android 13#Android security#Android security update#Android software update#cheap Android phones#Moto G Power#Nokia X100#OnePlus Nord N200#Pixel 5a#Samsung Galaxy A13#TCL 20 Pro 5G#TCL 20 SE
0 notes
Text
What is Android Security Management Services?| Sasken
Android Security Management services that enable OEMs to reduce efforts in managing security upgrades and provide long-term maintenance of security upgrades. For more details you can visit us on : https://www.sasken.com/industries/enterprise-devices/android-security-management-services
0 notes
Text

Here are the 10 tips to test the security of an android application. The android app security checklist of applications that handle sensitive user data is critical.
0 notes
Text

day 29: apart.
#“help me”#if the style looks different its cos im away from home and have no access to my usual software and equipment :')#i get so stressed drawing on android. and idk how to use krita :') *implodes*#*insert this is fine meme*#*spontaneously combusts*#ill be back to my usual stuff in a few days#dca promptober#my art#moondrop#fnaf dca#fnaf daycare attendant#fnaf moon#daycare attendant#dca fandom#fnaf sb#fnaf security breach#fnaf
577 notes
·
View notes
Text
instagram
#cyberpunk#scifi#science fiction#android#art#cybernetic#cyborg#synthetic#security#military#armour#power armour#Instagram
306 notes
·
View notes
Text


Them again♥
#fnaf#glamrock freddy#glamrock bonnie#glamrock fronnie#fronnie#freddy x bonnie#fnaf security breach#five nights at freddy's#digital art#digital artist#doodles#i like to think these versions of them being more android furries than animatronics. still robots but you know sdfghjhg
185 notes
·
View notes
Text



Android glittler golf~
#my art#glittergolf#fnaf security breach#moondrop#sundrop#monty gator#montgomery gator#android sundrop#android moondrop#android monty#fnaf sundrop#fnaf moondrop
311 notes
·
View notes
Text


Here's a troll post I was cooking up over on Twitter, building up to the reveal that Freddy is infact a robot- an android.
It probably was obvious to some... and not as obvious to others... but anyway!
#theglamdroids#fnaf#five nights at freddy's#fnaf security breach#fnaf sb#security breach#glamrock freddy#five nights at freddys#gijinka#gregory fnaf#fnaf fanart#digital art#fnaf gregory#gregory#character art#android
121 notes
·
View notes
Text
Cotton tail<3
This took me 3 straight (lol there is nothing straight about this image) days to draw-


sorry i suck at writing text, but i tried XD
Funfact! Did you know that bunnies' mark their territory by rubbing/scratching their chins on stuff! and bears claim territory by rubbing themselves on stuff, scratching stuff, and touching them with their paws (because bears have sent glands in their hands/paws that leave their sent on them) :]
also ill have a post with Freddy's full animatronic design soon!
#ha gayyy#art#glamrock bonnie#glamrock freddy#my art#fnaf#fnaf security breach#glamrock fronnie#fronnie#human glamrock freddy#human glamrock bonnie#android#android au#fnaf human au#flirting#omg they were roommates#blacklight lighting my beloved#glow in the dark#my beloved#flustered bunny boi#flirty bear boi#this took me 3 days#bear facts#bunny facts
134 notes
·
View notes
Text
Stop Your Android From SPYING On You!
View On WordPress
0 notes
Text

Some doodles I drew while watching/listening to @bamsara 's stream tonight :]
I enjoyed it and am now addicted to Spy x Family.
#technically solar lunacy#solar lunacy#doodles#y/n#y/n insert#self insert#daycare attendant x y/n#moon#sun#moon security breach#sun security breach#i want to draw Y/N but detroit become human and Sun/Moon are their Androids#brain rot rn man#brain rot.
2K notes
·
View notes