#zerotrust
Text
Seamless Connectivity with AT&T and Dell’s Connected PCs

AT&T and Dell
A world where connectivity is essential makes reliable and secure network access more important than ever. AT&T and Dell‘s new campaign addresses modern business needs.
Meeting the Needs of Modern Connectivity
Cellular connectivity is becoming essential as technology develops, especially to meet the requirements of GenAI use cases and remote and hybrid workers. There is an increasing expectation that cellular connectivity will play a more significant role in the future, especially with the promise of 5G, according to research done by Dell on the GLG platform. Forrester Inc. states in Architecting Your Infrastructure For AI (December 10, 2023) that “cellular and satellite may be your only options for solutions that need to incorporate data from remote locations.”
Furthermore, connectivity is crucial for modern PC experiences in a variety of industries, not just for individual users. Connected PCs are viewed as vital tools that facilitate smooth communication and collaboration in a variety of industries, including real estate, construction, and professional services.
Poor connectivity, one of the top three workplace technology challenges, still annoys many workers.Reliable connectivity is crucial in hybrid environments. According to recent data, 83% of workers prefer a mix of in-person and remote work, and 94% of companies have a hybrid structure.
Security Issues in the Era of Hybrid Employment as AT&T and Dell
Zero Trust Maturity
Notwithstanding the advantages of connectivity, security issues are a major concern, particularly in mixed work environments. Cybercrimes and security lapses are serious risks that are made worse by people’s growing reliance on public Wi-Fi networks. “Security professionals often overlook the fact that their employees, contractors, and other internal users enable many successful network compromises.” “In addition, Forrester’s Security Survey, 2022 revealed that an astounding 74% of security decision-makers estimated that their organization’s sensitive data was breached at least once in the previous 12 months,” according to Gauge Your Zero Trust Maturity, published by Forrester Inc. on March 10, 2023.
Security risks are increased by the integration of AI, especially when it comes to cloud-based apps and sensitive data. Data security becomes critical as AI applications spread throughout sectors like healthcare, customer service, and driverless cars.
Improved Safety Using Networked Computers
AT&T and Dell are launching a carrier promotion that prioritizes security while also improving connectivity in order to address these issues. Through the use of secure and encrypted cellular networks, linked PCs provide defence against cyberattacks and unauthorized access. These computers also meet the most recent security certifications and standards, offering complete security via Dell’s array of security products.
Integrated with ease and improved performance
Beyond security, connected PCs running on AT&T’s network provide improved performance and a flawless user experience. According to Forrester Inc.’s explanation in Architecting Your Infrastructure For AI (December 10, 2023), “Complex AI solutions can require high bandwidth and low latency, which can be challenging to accommodate AI applications’ data and computing needs with low-latency data transmission from 4G and 5G networks. Better support for mobile and hybrid workers will result from this, allowing for instantaneous connectivity and flexible work schedules without the inconvenience of tethering or depending on public Wi-Fi networks.
In its Market Guide for 5G Enterprise Data Services, Karen Brown, Tim Zimmerman, Jonathan Forest, Mohini Dukes, January 8, 2024, Gartner emphasises that 5G should be prioritised as amain connection option where wire line is unavailable.”Give 5G priority as the primary connection option for areas where wire line alternatives are insufficient or nonexistent.”
Encouraging Referrals: Making Connectivity Easy
The Carrier Referral Programme, which is the centrepiece of this campaign, aims to hasten the adoption of Connected PCs by streamlining the process of choosing, acquiring, and activating carrier data plans. The programme, which is aimed at any commercial customer in the United States who requires remote PC connectivity, offers customers who activate service on eligible plans discounted monthly rates from AT&T and up to a $100 bill credit.1.
Customers can also get concierge support from AT&T to help choose the best data plan and schedule service activation for a time that works for them. AT&T’s Head of Strategic Partner Sales and VPGM for Business Solutions, Margaret Rooney-McMillen, expressed her excitement about the company’s partnership with Dell. As the backbone of AT&T’s business, business workers depend on secure connectivity. They goal-driven concierge service places the needs of they customers first and is designed to support Dell’s Carrier Referral Programme. We expect this partnership to succeed.
Increasing Interconnectedness for the Future
The carrier promotion Dell has arranged with AT&T is a big step towards enabling future-proof connectivity. Through this partnership, the needs of businesses and consumers will be met in a way that will revolutionize the way that connectivity is experienced by both. To make connectivity easier, safer, and more accessible for everyone, AT&T and Dell are devoted to providing seamless integration, improved performance, and unwavering support.
Read more on Govindhtech.com
#govindhtech#news#technologynews#technology#TechnologyTrends#technews#pc#Dell#ZeroTrust#zerotrustmaturity
0 notes
Link
0 notes
Text
Securing the Future: IoT Identity and Access Management
Smart devices have gained immense popularity due to their seamless integration of internet connectivity with physical objects, unlocking vast possibilities across various domains.
However, this interconnectedness exposes these devices to potential vulnerabilities when connected to the internet. In this piece, we delve into the vulnerabilities inherent in IoT devices and the pivotal role played by IoT Identity and Access Management (IAM) tools in authenticating devices and fortifying data security.
Securing sensitive data encompasses diverse strategies, among which Identity and Access Management (IAM) stands out as paramount. IAM serves as a bulwark against unauthorized access to IoT devices and data, offering precise control over user permissions and activities, thus bolstering overall security.
IoT Landscape: Diversity and Vulnerabilities
IoT encompasses a vast array of devices, from smart thermostats and wearable fitness trackers to industrial sensors and autonomous vehicles. This diversity introduces complexity to IAM. Each device possesses its own identity and operates within a network, demanding robust authentication and authorization measures to maintain security.
However, the sheer volume of IoT devices, coupled with varying manufacturers and standards, presents vulnerabilities. Security loopholes in these devices could potentially serve as entry points for cyber threats, making them targets for unauthorized access, data breaches, and even manipulation.
Essence of IoT Identity and Access Management
IAM in the world of IoT is crucial for ensuring the confidentiality, integrity, and availability of data and systems. It involves the management of identities, permissions, and access controls for both users and devices within an IoT ecosystem.
Key Components of IoT IAM
Identity Management: Assigning unique identities to each device or user within the IoT network is fundamental. This includes authentication mechanisms such as passwords, biometrics, or cryptographic keys to verify the identity of devices or users attempting to access the system.
Access Control: Implementing policies and protocols that regulate access privileges is essential. Granular controls should be in place to define who or what can access specific resources, ensuring that only authorized entities have the necessary permissions.
Encryption and Data Integrity: Securing data in transit and at rest is imperative. Encryption protocols safeguard data from unauthorized access, while ensuring its integrity throughout the communication process.
Monitoring and Analytics: Continuous monitoring of IoT devices and network traffic is critical. Employing analytics and AI-driven solutions can help in identifying anomalies or suspicious activities, enabling proactive responses to potential threats.
How IoT Identity and Access Management Works?
Identification: Users or devices provide their identity information, often in the form of usernames, IDs, or digital certificates.
Authentication: Verification of the provided identity through various methods, ensuring the legitimacy of the user or device.
Authorization: Granting appropriate permissions or access rights based on the verified identity and predefined policies.
Monitoring and Management: Continuously monitoring user activities, managing access rights, and adjusting permissions as needed over time.
Benefits of IoT Identity and Access Management
Enhanced Security: IAM helps mitigate security risks by ensuring only authorized users or devices can access sensitive resources.
Improved Efficiency: Streamlining access management reduces administrative overhead and ensures quick and accurate access provisioning and deprovisioning.
Regulatory Compliance: IAM assists in meeting compliance requirements by maintaining detailed access logs and enforcing access control policies.
Challenges and Future Trends
Despite its importance, implementing robust IAM in IoT faces several challenges:
Standardization: The lack of universal standards across IoT devices poses interoperability challenges, making it difficult to enforce consistent IAM practices.
Scalability: As the number of IoT devices continues to grow exponentially, managing identities and access at scale becomes increasingly complex.
Security Concerns: Device vulnerabilities, insecure communication protocols, and the potential for human error in configuration contribute to ongoing security concerns.
Talk To Analyst
Looking ahead, several trends aim to address these challenges:Blockchain for Security: Blockchain technology is being explored to enhance the security and immutability of IoT transactions and identities.
AI and Machine Learning: Leveraging AI and machine learning for predictive analysis and anomaly detection will play a pivotal role in strengthening IoT IAM.
Zero Trust Architecture: Implementing a zero-trust approach, where no entity is trusted by default, helps in securing IoT networks by continuously verifying and authenticating devices and users.
A well-crafted market intelligence report, such as the one provided by Quadrant Knowledge Solutions in their Market Share: Identity and Access Management, 2022, Worldwide report, acts as a valuable resource, offering a plethora of insights and guidance to organizations navigating the complexities of IoT Identity and Access Management (IAM).
These reports offer in-depth insights into emerging technologies, evolving standards, and industry best practices, effectively serving as a roadmap for securing IoT ecosystems. They illuminate potential vulnerabilities, evolving threat vectors, and successful IAM strategies across diverse sectors. The Market Forecast: Identity and Access Management, 2022-2027, Worldwide reports from Quadrant Knowledge Solutions not only identify challenges but also provide strategic recommendations, empowering businesses to deploy robust IAM solutions, proactively address emerging threats, and adapt to the dynamic IoT security landscape with informed decisions.
Conclusion
The growth of IoT brings unparalleled opportunities but also elevates the importance of robust identity and access management. As IoT ecosystems expand, the need for standardized, scalable, and secure IAM practices becomes increasingly imperative. Embracing innovative technologies and adopting comprehensive strategies will be pivotal in safeguarding the future of IoT against emerging threats, ensuring a secure and resilient interconnected world.
#IoTIAM#IoTSecurity#IAM#IdentityManagement#AccessControl#DataSecurity#IoTVulnerabilities#Cybersecurity#Blockchain#AI#MachineLearning#ZeroTrust#MarketIntelligence#QuadrantKnowledgeSolutions#IoTMarketForecast#SecurityTrends#IoTManagement#IoTStrategies#IoTSolutions
0 notes
Text
0 notes
Video
youtube
Implementing Zero Trust Security in an AWS Environment
#youtube#zerotrust#security#cybersecurity#aws#awscloud#awssecurity#websecurity#cloudsecurity#clouds#zerotrustsecurity
1 note
·
View note
Text
9 in 10 organizations have embraced zero-trust security globally

Nearly 90% organizations have begun embracing zero-trust security, but many still have a long way to go, according to a report by multinational technology company Cisco.
https://jpmellojr.blogspot.com/2023/11/9-in-10-organizations-have-embraced.html
0 notes
Text
Is Zero Trust the New Silver Bullet for Cybersecurity?
#Cybersecurity #Google #Research #technology #ZeroTrust
0 notes
Link
https://bit.ly/3QJOcmF - 🔐 Network Access Control (NAC) is a vital technology that controls access to network resources based on policies. It identifies, verifies, and assesses device compliance, granting access levels from full access to no access, with continuous monitoring for ongoing compliance. #CyberSecurity #NAC 📈 The Importance of NAC for Organizations: With growing endpoint usage and threat actors, automation provided by NAC reduces time, cost, and broadens potential attack surfaces. Features like Multi-Factor Authentication add an extra layer of security, making it essential for Zero Trust Security. #NetworkSecurity #ZeroTrust 🛠️ Types of NAC: Two essential forms - pre-admission and post-admission - provide a defense-in-depth strategy. Together, they keep threat actors from accessing network resources and discover unnoticed ones. #NetworkProtection 🎯 NAC Capabilities: These include Authentication, Role-Based Access Control, Device Profiling, Endpoint Security Assessment, Policy Enforcement, Quarantine, Remediation, and Integration with other solutions, adding a robust security layer. #NetworkManagement 🏆 Benefits of NAC: Enhancing security, saving costs through automation, streamlining user experience, and providing control, compliance, stronger authentication, are some of the key advantages. #CostSaving #Security 📱 Use Cases: NAC aids in managing BYOD, Network Access for Non-employees, IoT Devices, provides Visibility and Reporting, and helps in Incident Response, ensuring secure network handling across different scenarios. #IoTSecurity #BYOD 🧩 Choosing and Implementing a NAC Solution: Integrating NAC requires consideration of native integration with existing systems, all-in-one solutions, and planning. Steps like gathering information, managing identities, applying permissions, and regular updates are key. #NetworkIntegration In summary, Network Access Control (NAC) is pivotal in today's security landscape, offering protection, compliance, and enhanced user experience. Its implementation must align with the organization's structure and needs for optimal benefits.
#CyberSecurity#NAC#NetworkSecurity#ZeroTrust#NetworkProtection#NetworkManagement#CostSaving#Security#IoTSecurity#BYOD#NetworkIntegration#CyberSecurityAwareness#NetworkControl
0 notes
Text
CISA’s Zero Trust Maturity Model 2.0: Cybersecurity Roadmap

Zero trust maturity model version 2
Zero trust maturity model 2.0
With the help of CISA’s Zero Trust Maturity Model v2.0, the Federal IT environment is rapidly changing in favor of increased cybersecurity. To improve their cyber posture, federal agencies might use this model as a guide. The correct tools must be chosen in order for government entities to successfully manage this transition. Designed to fulfill the strict compliance requirements of federal organizations, Google Workspace brings strong security features to the table.
Google Workspace’s Role in Cisa zero trust maturity model 2.0
Cisa zero trust maturity model
Thin-layer security, continuous validation, and device-independent protection are highlighted in the CISA Zero Trust Maturity Model. A set of principles and ideas known as “zero trust” is intended to reduce ambiguity when it comes to enforcing precise, least privilege per-request access choices in information systems and services while dealing with networks that are seen as weak. Maintaining as much granularity in access control enforcement while preventing unwanted access to data and services is the aim.
For the following reasons, zero trust puts fine-grained security restrictions across individuals, systems, data, and assets that vary over time in a more data-centric manner rather than a location-centric one.To educate agencies on how to apply Zero Trust (ZT) concepts to mobile security technologies that are already on the market and probably included in a Federal Enterprise’s mobility program, CISA prepared the Applying Zero Trust concepts to Enterprise Mobility document.
On March 7, 2022, and ending on April 20, 2022, CISA made the document available for public comment. A revised version of the paper will be produced when CISA has taken into consideration the feedback provided by all responders. The formulation, execution, enforcement, and evolution of security rules are supported by the visibility that this gives. At a deeper level, zero trust can need altering the cybersecurity culture and mindset of a business.The following elements of Google Workspace support the idea of “never trust, always verify”:
Boost Access Control and Identity:
Context-Aware The correct individuals only get access to the right data thanks to strong authentication mechanisms and access.
Zero trust maturity model version 2
These measures safeguard private data at all points of access with sophisticated device controls and endpoint management.
Collaborating while preserving data is made possible by granular sharing settings and data loss prevention (DLP) features.Uncovered Information from the Google Workspace Zero Trust Security Workshop.
Recent Google Workspace Zero Trust Security Workshop provided an insightful overview of how Google Workspace may help federal agencies on their Zero Trust journeys. Using Zero Trust concepts in the federal context was discussed at the session by CISA specialists. A practical application of Zero Trust architecture driven by Google Workspace and Gemini AI was shown in the ManTech case study, which proved beneficial to the attendees.
The platform’s ability to achieve CMMC compliance is shown by ManTech’s shared experience, which provides other agencies with a useful model. IT decision-makers had practical experience with Google Workspace’s security controls via interactive demonstrations that were included in the training.
Zero trust maturity model
The Google Workspace Zero trust best practices guide for U.S. public sector organizations is a great tool for anybody who was unable to attend the event and wants to achieve CISA-compliant Zero trust maturity.
Special Sessions at Google Cloud Next ’24 on Google Workspace and Federal Cybersecurity.
Google Cloud Next ’24 is the next stop in the discussion, with talks on:
Achieve strict compliance across many frameworks (CJIS, FedRAMP, ITAR, DoD ILs) with Assured Workloads for Public Sector Compliance.
Using Gemini in Google Workspace, Keep Your Data Private and Compliant Come learn about the privacy and security features that come standard with Gemini for Google Workspace and how Sovereign Controls may help your company attain digital sovereignty.
AI-Powered Cooperation to Break Down Silos: Discover how creativity, productivity, and safe collaboration are facilitated with Google Workspace.
Through Google Workspace, Gemini: Privacy Guaranteed: Learn about the ways that Gemini protects data sovereignty while offering strong capabilities.
Ready for the government: The way that Google Workspace makes safe collaboration possible: Learn how federal, state, and local government organizations may simplify operations while upholding the highest standards of data security (with ManTech) using Google Workspace.
Google is dedicated to providing creative solutions that will assist agencies in the dynamic field of federal cybersecurity. Zero Trust principles are the foundation of Google Workspace, which gives users the flexibility and toughness they need to meet new challenges. Agency tasks are accomplished and sensitive data is safeguarded with more efficacy when paired with the wider capabilities of Google Cloud.
Federal agencies will always have access to state-of-the-art resources necessary to keep ahead of emerging cyber threats because to Google’s commitment to ongoing innovation.
Read more on Govindhtech.com
0 notes
Text
Zero Trust Security
In today’s world, the rapid pace of digital transformation, increased use of cloud services ☁️, and adoption of hybrid work have all created a continually shifting enterprise environment that’s chaotic and difficult to secure.
Thereby Zero Trust Security Model comes in, which implies a “Never Trust, Always Verify” approach that will secure identities, endpoints, applications, data, infrastructure, and networks, while providing visibility, automation, and orchestration.
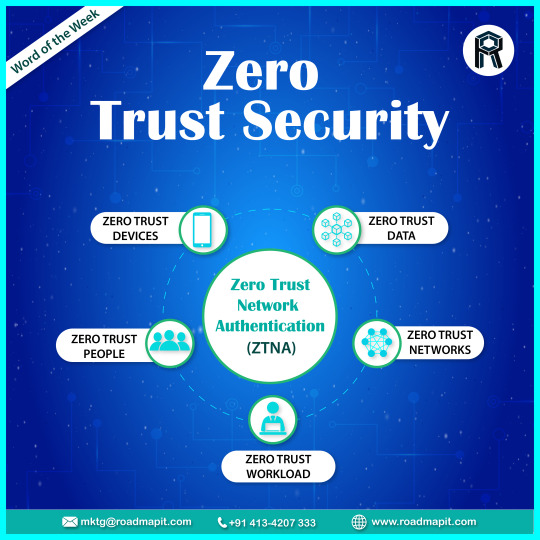


#zerotrust#zerotrustaccess#zerotrustsecurity#wfh#remotework#zerotrustarchitecture#seguran#workfromhome#zerotrustmodel
0 notes
Text
L'intelligenza artificiale decifra facilmente le passwords
Violare (e verificare) le password con l’AI. La diffusione degli strumenti basati sull’intelligenza artificiale sta sollevando diversi problemi di sicurezza, che coinvolgono anche i sistemi di autenticazione con password.
Una soluzione che sfrutta l’intelligenza artificiale è PassGAN AI, un sistema in due parti: una rete generativa crea le password che potrebbero essere utilizzate un utente, mentre una rete discriminante confronta le password generate con quelle reali provenienti da leak e altre fonti.
La rete discriminante addestra la rete generativa per creare password migliori e più accurate. Secondo Home Security Heroes, le password composte da quattro, cinque e sei caratteri con combinazioni di lettere, numeri e simboli possono essere indovinate quasi istantaneamente da PassGAN AI.
Anche una password di sette caratteri con lettere maiuscole e minuscole e numeri (ma senza simboli) potrebbe essere violata in meno di un minuto. Le password più complesse (costituite da otto e nove caratteri) richiedono rispettivamente sette ore e due settimane per essere decifrate.
Irrobustire la sicurezza
Home Security Heroes ha utilizzato PassGAN AI per analizzare oltre 15 milioni di password comuni, con risultati piuttosto preoccupanti.
L’uso dell’intelligenza artificiale per decifrare password ha sollevato preoccupazioni sulla sicurezza, ma è utile notare che strumenti simili esistono da qualche tempo e le password rimangono ragionevolmente sicure, a patto che siano lunghe e complesse.

Fonte: Home Security Heroes
Gli strumenti dedicati alla violazione delle password, anche quelli basati sull’IA, sono efficaci solo quanto i dati a loro disposizione.
Rimangono quindi valide, a maggior ragione, tutte le precauzioni e le best practices che presiedono alla protezione dei sistemi di autenticazione: in particolare, oltre a selezionare password lunghe e robuste (la lunghezza necessaria sta aumentando rapidamente), è importante anche aggiungere ulteriori fattori di autenticazione, avendo cura di implementare un sistema robusto e resiliente agli attacchi più comuni.
Un approccio basato sul paradigma zero trust può inoltre aiutare a contenere eventuali violazioni monitorando i comportamenti degli utenti e rilevando eventuali attività inconsuete.
Read the full article
0 notes
Link
With businesses thriving, thanks to the digital transformation wave, improving and optimizing an organization's security should be the top priority. Register Now for the Webinar by WATI and zscaler that's happening on March 9th, 12pm EST.
0 notes
Text
2022 Threat Matrix: Is Zero Trust approach and Distributed API technology relevant?

Dhananjay Ganjoo, the India Managing Director at F5 Inc in a conversation with Sairaj Iyer answers how technologies such as distributed API protection and the Zero Trust approach are helping build a secure enterprise
Read More. https://www.sify.com/technology/2022-threat-matrix-is-zero-trust-approach-and-distributed-api-technology-relevant/
0 notes
Text
Cloud Security Alliance announces new zero-trust security credential

The Cloud Security Alliance (CSA) raised the curtain Wednesday on a new credential to enable security professionals to build the knowledge they will need to implement and manage a zero-trust strategy in their organizations.
https://jpmellojr.blogspot.com/2023/11/cloud-security-alliance-announces-new.html
0 notes
Link
#Centrify#Centrifytraining#Centrifycorporatetraining#Centrifyonlinetraining#Centrifytrainingjobsupport#centrifyprivilege#pamietnik#multifactor#authentication#activedirectory#centrifyidentity#iam#zerotrust#pas#pasconfiguration#technology#elearning#online#classrromtraining#corporatetraining
0 notes