#endpoint security market share
Text
#endpoint security market report#endpoint security industry report#endpoint security market#endpoint security market share#endpoint security market size#endpoint security market trends#endpoint security market growth#endpoint security market analysis#endpoint security market forecast
0 notes
Text
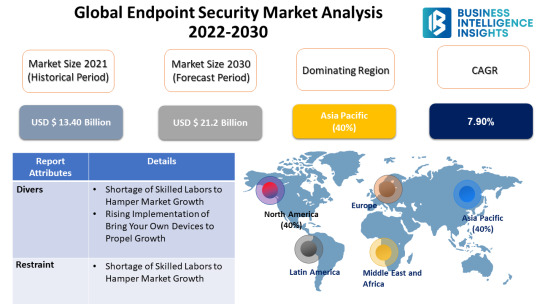
As per Business Intelligence Insights (BII) study, the global Global Endpoint Security Market attained revenue growth of USD 13.40 billion in 2021 and it is projected to reach around USD 21.2 billion by 2030, growing at a 7.90% CAGR.
#Endpoint Security Market#Endpoint Security Market Market#Endpoint Security Market Market Trends#Endpoint Security Market Market Share#Endpoint Security Market Market Size#Endpoint Security Market Market Analysis#Endpoint Security Market Market Demand#Endpoint Security Market Market Growth 2023#Endpoint Security Market Market Industry
0 notes
Text
How Does Walmart Product API Data Extraction Enhance Business Decision-Making
Have you heard about Walmart API data and its pivotal role in today's data-driven business landscape? In this digital age, where information is critical, accessing and analyzing data from retail giants like Walmart can provide invaluable insights for businesses. Walmart product API data extraction is a gateway to a treasure trove of information about products, prices, sales trends, and customer behavior.
Walmart data scraping involves collecting this valuable information from the Walmart website using automated tools and techniques. This process allows businesses to gather comprehensive data about Walmart's vast product catalog, pricing strategies, customer reviews, and more. By leveraging retail data scraping services, businesses can gain a competitive edge by monitoring market trends, analyzing competitor pricing, and optimizing their product offerings.
Furthermore, Walmart's scraping product API offers a more structured and efficient way to access data than traditional web scraping methods. Through the API, developers can programmatically retrieve specific data points in a standardized format, streamlining the data extraction process and enabling real-time updates.
Understanding how to scrape Walmart data and harness Walmart's API capabilities can empower businesses to make data-driven decisions, enhance their market intelligence, and stay ahead of the competition in the dynamic retail landscape. In this article, we will delve deeper into the intricacies of scraping Walmart data and explore the vast potential of Walmart's API for businesses.
Understanding API Data and Its Relevance to Business
API data, or Application Programming Interface data, refers to the information and functionalities that can be accessed and exchanged between different software applications through APIs. APIs serve as intermediaries that allow different systems to communicate and interact with each other seamlessly.
In the business context, Walmart product API data facilitates integration and interoperability between various software platforms and systems used within an organization. Allowing different applications to share data and functionality enables businesses to streamline operations, automate processes, and enhance efficiency.
Working Principles of API Data
The working principles of scraping API data involve leveraging the functionalities of APIs to extract relevant information from various sources in a structured and automated manner. This process typically follows these steps:
Authentication: Access to API data often requires authentication to ensure secure access to protected resources. It involves obtaining API keys or tokens and authenticating requests using standard authentication mechanisms such as OAuth.
Endpoint Discovery: Identify the API endpoints that contain the data you want to scrape. These endpoints represent specific resources or functionalities the API exposes and define the URLs or URIs to access the data.
Request Construction: Construct HTTP requests to access the desired data from the API endpoints. It specifies the HTTP method (e.g., GET, POST), required parameters or query strings, and headers such as authentication tokens.
Data Retrieval: Send the constructed requests to the API endpoints and retrieve the response data. The response typically contains the requested information in a structured data format such as JSON or XML.
Data Parsing: Parse the response data to extract the relevant information you want to scrape. It involves navigating the JSON or XML structure and extracting specific data fields or elements using parsing techniques such as XPath or JSONPath.
Data Storage: Store the scraped data in a structured format such as a database, CSV file, or spreadsheet for further analysis or processing. Ensure that the data storage mechanism aligns with your requirements for accessibility, scalability, and data integrity.
Error Handling: Implement error handling mechanisms to handle exceptions or errors that may occur during the scraping process. It includes gracefully handling HTTP status codes, connection errors, rate limiting, and other potential issues.
By following these principles, businesses can effectively scrape data from APIs, collect valuable insights, and leverage the information available through API endpoints for various purposes, such as market research, competitive analysis, and business intelligence.
For example, businesses can use APIs to integrate customer relationship management (CRM) systems with marketing automation platforms, enabling them to synchronize customer data, track interactions, and automate marketing campaigns. Similarly, APIs can connect e-commerce platforms with inventory management systems, enabling real-time product availability, pricing, and order updates.
Overall, e-commerce web scraping empowers businesses to effectively leverage the capabilities of different software applications and systems, enabling them to improve collaboration, enhance productivity, and deliver better customer service. It is vital in driving digital transformation and innovation across various industries, enabling businesses to stay competitive and adapt to evolving market trends and customer needs.
Role of Walmart Product API Data Extraction to Enhance Business Decision-Making
The role of Walmart data collection in enhancing business decision-making is pivotal. By tapping into the API's information, businesses can gain valuable insights into market dynamics, competitor strategies, and customer behavior. Analysis of this data empowers businesses to make informed decisions across multiple facets of operations. From market analysis and inventory management to competitive intelligence and marketing optimization, Walmart's Product data scraping services offer a treasure trove of data that can be leveraged to drive strategic initiatives. By utilizing this data effectively, businesses can stay ahead of trends, optimize resource allocation, and ultimately enhance their competitive position in the marketplace.
Gathering Walmart Data via Web Scraping
Utilizing web scraping for gathering data offers a more straightforward approach than utilizing specialized programs like the Walmart Data Extractor. The process begins with web scraping, where the company identifies a website with a layout resembling the target site, such as Walmart's product page. Ensuring a fast response time from the website is essential, and browsers supporting web scraping, like Google Chrome, are preferred.
Following this, software is developed for scraping, typically using languages like Python, Perl, Ruby, or PHP. Python is popular due to its cross-platform compatibility and readability. This software sends requests to the target website, retrieves desired data and saves it for further analysis or reporting. Remember that some web scraping technologies may necessitate additional software installation, such as Python, for optimal functionality.
Scraping Walmart Data Using Python
We are explaining the steps to scrape Walmart data using Python.
Obtain API Key: Sign up for Walmart's Developer Portal and obtain an API key to access their data.
Install Required Libraries: Install the necessary Python libraries for working with APIs, such as Requests.
pip install requests
Import Libraries: Import the required libraries into your Python script.
Handle Pagination (if needed): If the API response is paginated, handle pagination by iterating through multiple pages of results.
Extract Desired Information: Extract the relevant information from the API response, such as product names, prices, and ratings.
Conclusion
Walmart's Product scraping API offers businesses a powerful means of accessing and analyzing a wealth of product information on the platform. By harnessing this API, businesses can efficiently retrieve product names, prices, ratings, and more data, enabling them to gain valuable insights into market trends, competitor offerings, and consumer preferences. This data can inform strategic decision-making, enhance pricing strategies, optimize inventory management, and drive overall business growth. With proper implementation and utilization, Walmart Product API data extraction empowers businesses to stay competitive, make informed decisions, and capitalize on opportunities in the ever-evolving retail landscape.
UnlUnlock the potential of data-driven decisions through our Retail Scrape Company. Harness consumer behavior insights, refine pricing strategies, and outpace rivals with live retail data scraping. Elevate your enterprise with our full-range pricing optimization and strategic decision support. Connect today to transform your retail endeavors and amplify profits!
know more :
https://www.retailscrape.com/walmart-product-api-data-extraction-enhance-business.php
#WalmartProductAPIData#WalmartProductAPIDataExtraction#WalmartDataScraping#Walmart'sProductScrapingAPI#ScrapeWalmartData
0 notes
Text
DDoS Protection and Mitigation Security Market Poised for Robust Growth at a CAGR of 13.4% by 2032
The DDoS protection and mitigation security market are poised for exceptional growth, with a projected Compound Annual Growth Rate (CAGR) of 13.4% from 2022 to 2032. This robust expansion is set to catapult the market’s value from US$ 3.8 billion in 2022 to an impressive US$ 13.3 billion by 2032.
The IoT environment comprises of various associated gadgets, doors, servers, and different endpoints. With IoT getting forward movement in a large number of enterprises, like brilliant assembling, medical services, and associated vehicles, and expanding the extent of its applications, the organization being used is developing perplexing and number of gadgets in the associated biological system is duplicating. With changes in the business climate, security prerequisites are additionally evolving.
Get a Sample Copy of Report :
https://www.futuremarketinsights.com/reports/sample/rep-gb-14682
Instances of massive DDoS attacks are gradually increasing across the globe. The attackers are using sophisticated tools to induce attacks, which may go undetected during initial phases.
Some of the significant DDoS attacks include Domain Name System (DNS) amplification attacks, NTP attacks, and Chargen-focused attacks. The multiple attack techniques used by hacktivist groups are leading to a huge financial loss for individuals, enterprises, and governments. Hence, deployment of DDoS protection and mitigation software in various industries is rising.
Know More About What the DDoS Protection and Mitigation Security Market Repost Covers
Future Market Insights offers an unbiased analysis of the global DDoS Protection and Mitigation Security Market, providing historical data for 2015-2021 and forecast statistics from 2022-2032. To understand opportunities in the DDoS Protection and Mitigation Security Market, the market is segmented on the basis of component, application area, deployment mode, and vertical across five major regions.
Key Takeaways from the Market Study
Global DDoS protection and mitigation security market was valued at US$ 3.8 Billion by 2022-end
The US to account for the highest value share of US$ 4.7 Billion of global market demand for DDoS protection and mitigation security market in 2032
From 2015 to 2021, DDoS protection and mitigation security demand expanded at a CAGR of 15.4%
By Component, the Services category constitutes the bulk of DDoS Protection and Mitigation Security Market with a CAGR of 13.1%.
Competitive Landscape
Players in the global DDoS Protection and Mitigation Security Market focus on expanding their global reach through various strategies, such as; partnerships, collaborations, and partnerships.
The players are also making a significant investment in R&D to add innovations to their products which would help them in strengthening their position in the global market. Some of the recent developments among the key players are:
In August 2021, Radware had partnered with hybrid infrastructure solutions provider INAP to provide global cloud web application security and protection against distributed denial of service (DDoS) attacks. INAP will deploy Radware’s security protections to organizations across various industries, including ad tech, healthcare, entertainment and gaming, financial services, ISF, and software as a service, amongst others.
In March 2022, Corero Network Security provider of real-time, high-performance DDoS cyber defense solutions extended its automatic protection against Botnet and Carpet Bomb attacks. The company’s mission is to make the internet a safer place to do business by protecting against the disruption and downtime caused by DDoS attacks.
In February 2022, Radware acquired SecurityDAM for USD 30 million with contingent payments of up to USD 12.5 million for Radware’s cloud DDoS protection service after the deal.
Request for Methodology:
https://www.futuremarketinsights.com/request-report-methodology/rep-gb-14682
Key Segments Covered in the DDoS Protection and Mitigation Security Market Report
DDoS Protection and Mitigation Security Market by Component:
DDoS Protection and Mitigation Security Hardware Solutions
DDoS Protection and Mitigation Security Software Solutions
DDoS Protection and Mitigation Security Services
Professional Services
Managed Services
DDoS Protection and Mitigation Security Market by Application Area:
DDoS Protection and Mitigation for Network Security
DDoS Protection and Mitigation for Endpoint Security
DDoS Protection and Mitigation for Application Security
DDoS Protection and Mitigation for Database Security
DDoS Protection and Mitigation Security Market by Deployment Mode:
On-premise DDoS Protection and Mitigation Security
Cloud-based DDoS Protection and Mitigation Security
Hybrid DDoS Protection and Mitigation Security
DDoS Protection and Mitigation Security by Vertical
DDoS Protection and Mitigation Security for Government and Defense
DDoS Protection and Mitigation Security for BFSI
DDoS Protection and Mitigation Security for Manufacturing
DDoS Protection and Mitigation Security for Energy and Utility
DDoS Protection and Mitigation Security for IT and Telecommunication
DDoS Protection and Mitigation Security for Healthcare
DDoS Protection and Mitigation Security for Education
DDoS Protection and Mitigation Security for Retail
DDoS Protection and Mitigation Security for Other Verticals
DDoS Protection and Mitigation Security Market by Region:
North America DDoS Protection and Mitigation Security Market
Latin America DDoS Protection and Mitigation Security Market
Europe DDoS Protection and Mitigation Security Market
Asia Pacific DDoS Protection and Mitigation Security Market
Middle East and Africa DDoS Protection and Mitigation Security Market
0 notes
Text
New Study Reveals 86% Increase in Cybersecurity Threats in 2024 - Heimdal Security Blog Delivers Key Endpoint Security Best Practices for Protection!
The Impact of Technology on Our Digital World
In today's fast-paced, interconnected world, technology plays a crucial and ever-expanding role in our daily lives. From the moment we wake up to the moment we go to bed, we are surrounded by a sea of technological advancements that shape and transform our experiences in ways we never imagined possible. In this article, we will explore the fascinating world of technology, diving deep into key facts, hard information, numbers, and concrete data, shedding light on its real-world applications and the importance it holds for each and every one of us.
The Numbers Don't Lie
Let's start by looking at some cold, hard numbers that highlight the impact of technology. According to the latest global statistics, the number of Internet users around the world has surpassed a staggering 4.9 billion, which translates to over 60% of the global population. This means that more people than ever before have access to a wealth of information and endless possibilities at their fingertips.
In addition to the increasing number of Internet users, the rise of smartphones and mobile devices has revolutionized the way we connect and interact with technology. As of today, there are over 3.8 billion smartphone users worldwide, accounting for nearly half of the global population. These devices have become an essential part of our lives, serving as our personal assistants, communication hubs, and gateways to the digital world.
But it's not just about the number of devices or users. The impact of technology goes much further, reaching into realms we may have never even considered. For example, did you know that there are currently over 30 billion connected devices in the world, collectively known as the Internet of Things (IoT)? These devices range from smart home appliances to industrial sensors, creating a network of interconnected devices that gather and share data, driving efficiency, and innovation across industries.
The Practical Applications
Now that we've established the sheer scale of technology's influence, let's dive into some practical applications that directly impact our daily lives. One prime example is the field of healthcare, where technology has revolutionized the way we approach diagnosis, treatment, and overall patient care.
Medical professionals now use sophisticated diagnostic tools such as MRI scanners, ultrasound machines, and AI-powered algorithms to detect diseases and conditions more accurately and at an earlier stage. This has led to improved patient outcomes, reduced healthcare costs, and a deeper understanding of various medical conditions.
Another area greatly impacted by technology is transportation. From the advent of ridesharing services like Uber and Lyft to the development of autonomous vehicles, technology has transformed the way we travel. These advancements have made transportation more convenient, efficient, and environmentally friendly, ultimately shaping the future of mobility.
Not only limited to healthcare and transportation, technology has permeated every aspect of our lives, from education and entertainment to business and communication. It has facilitated distance learning, empowered creative expression, enabled remote work, and fueled economic growth.
RoamNook: Empowering Digital Growth
As we witness the rapid evolution and increasing ubiquity of technology, there is a pressing need for specialized expertise and guidance. This is where RoamNook, an innovative technology company, comes into play. RoamNook specializes in IT consultation, custom software development, and digital marketing, with a mission to fuel digital growth across industries and empower businesses to leverage the full potential of technology.
With a team of seasoned professionals, RoamNook offers tailor-made solutions to address clients' specific needs, whether it's designing and implementing intricate IT infrastructures, developing cutting-edge software applications, or creating strategic digital marketing campaigns.
At RoamNook, we understand that navigating the ever-changing technological landscape can be overwhelming. That's why we strive to provide our clients with practical, actionable solutions that not only enhance their digital presence but also drive tangible results.
In conclusion, technology has become an integral part of our lives, shaping how we live, work, and interact with the world around us. The astonishing numbers, the practical applications, and the potential for growth make it clear that embracing technology is not a choice but a necessity. With RoamNook by your side, you can confidently harness the power of technology and unlock new possibilities for your business. Welcome to the world of endless potential!
Source: https://heimdalsecurity.com/blog/endpoint-security-best-practices/&sa=U&ved=2ahUKEwjzr5DpgIWGAxXXGVkFHXyiBYwQFnoECAIQAw&usg=AOvVaw3bTIBOmspy-J-jRvdz_5zJ
0 notes
Text
Social Media Security Market: Forthcoming Trends and Share Analysis by 2032
Social Media Security Market Size Was Valued at USD 1412 Million in 2023 and is Projected to Reach USD 5378.12 Million by 2032, Growing at a CAGR of 16.02 % From 2024-2032.
A crucial component of internet safety is social media security, which includes tactics and controls meant to shield people and institutions from the constantly changing threats connected to using social networking sites. Social media usage is increasing, which raises the possibility of a number of risks, such as phishing scams, identity theft, privacy violations, and cyberbullying.
The market for social media security has grown significantly in recent years due to growing worries about cyber attacks, data breaches, and online privacy on social media platforms. Social media security solutions are in more demand as more individuals and organizations realize how important it is to protect their digital presence from unwanted activity.
Get Full PDF Sample Copy of Report: (Including Full TOC, List of Tables & Figures, Chart) @
https://introspectivemarketresearch.com/request/3987
Updated Version 2024 is available our Sample Report May Includes the:
Scope For 2024
Brief Introduction to the research report.
Table of Contents (Scope covered as a part of the study)
Top players in the market
Research framework (structure of the report)
Research methodology adopted by Worldwide Market Reports
Leading players involved in the Social Media Security Market include:
Symantec (United States)
CA Technologies(United States)
ZeroFOX (United States)
RiskIQ (United States)
SolarWinds(United States)
Proofpoint (United States)
LookingGlass Cyber Solutions (United States)
KnowBe4 (United States)
Centrify (United States)
Social Hub (United States)
Brandle (United States)
Moreover, the report includes significant chapters such as Patent Analysis, Regulatory Framework, Technology Roadmap, BCG Matrix, Heat Map Analysis, Price Trend Analysis, and Investment Analysis which help to understand the market direction and movement in the current and upcoming years.
If You Have Any Query Social Media Security Market Report, Visit:
https://introspectivemarketresearch.com/inquiry/3987
Segmentation of Social Media Security Market:
By Solution
Monitoring
Threat Intelligence
Risk Management
By Security
Web Security
Application Security
Endpoint Security
Network Security
Cloud Security
By End Use Industry
BFSI
Healthcare and life sciences
Manufacturing
Telecom & IT
Media and entertainment
Others
An in-depth study of the Social Media Security industry for the years 2023–2030 is provided in the latest research. North America, Europe, Asia-Pacific, South America, the Middle East, and Africa are only some of the regions included in the report's segmented and regional analyses. The research also includes key insights including market trends and potential opportunities based on these major insights. All these quantitative data, such as market size and revenue forecasts, and qualitative data, such as customers' values, needs, and buying inclinations, are integral parts of any thorough market analysis.
Market Segment by Regions: -
North America (US, Canada, Mexico)
Eastern Europe (Bulgaria, The Czech Republic, Hungary, Poland, Romania, Rest of Eastern Europe)
Western Europe (Germany, UK, France, Netherlands, Italy, Russia, Spain, Rest of Western Europe)
Asia Pacific (China, India, Japan, South Korea, Malaysia, Thailand, Vietnam, The Philippines, Australia, New Zealand, Rest of APAC)
Middle East & Africa (Turkey, Bahrain, Kuwait, Saudi Arabia, Qatar, UAE, Israel, South Africa)
South America (Brazil, Argentina, Rest of SA)
Key Benefits of Social Media Security Market Research:
Research Report covers the Industry drivers, restraints, opportunities and challenges
Competitive landscape & strategies of leading key players
Potential & niche segments and regional analysis exhibiting promising growth covered in the study
Recent industry trends and market developments
Research provides historical, current, and projected market size & share, in terms of value
Market intelligence to enable effective decision making
Growth opportunities and trend analysis
Covid-19 Impact analysis and analysis to Social Media Security market
If you require any specific information that is not covered currently within the scope of the report, we will provide the same as a part of the customization.
Acquire This Reports: -
https://introspectivemarketresearch.com/checkout/?user=1&_sid=3987
About us:
Introspective Market Research (introspectivemarketresearch.com) is a visionary research consulting firm dedicated to assist our clients grow and have a successful impact on the market. Our team at IMR is ready to assist our clients flourish their business by offering strategies to gain success and monopoly in their respective fields. We are a global market research company, specialized in using big data and advanced analytics to show the bigger picture of the market trends. We help our clients to think differently and build better tomorrow for all of us. We are a technology-driven research company, we analyze extremely large sets of data to discover deeper insights and provide conclusive consulting. We not only provide intelligence solutions, but we help our clients in how they can achieve their goals.
Contact us:
Introspective Market Research
3001 S King Drive,
Chicago, Illinois
60616 USA
Ph no: +1 773 382 1049
Email: [email protected]
#Social Media Security#Social Media Security Market#Social Media Security Market Size#Social Media Security Market Share#Social Media Security Market Growth#Social Media Security Market Trend#Social Media Security Market segment#Social Media Security Market Opportunity#Social Media Security Market Analysis 2023
0 notes
Text
The Best Option for Secure Business Messaging Is Troop Messenger
Leave enough space for your business to grow. Provide it at any time and from any location. To guarantee flawless and totally secure business communication, check out Troop Messenger business Chat. Check out Troop Messenger, the best corporate instant messaging solution on the market with regard to data security, monitored and secured entrance protocol, ease of use, and intellectual property ownership, among many other features. We specifically designed this business chat software with you in mind. Take pleasure in using Troop Messenger, the professional chat application.
Success in the fast-paced corporate environment of today depends on teamwork and efficient communication. Presenting Troop Messenger, a cutting-edge instant messaging platform created to improve teamwork and communication in a variety of business contexts. Troop Messenger has emerged as the industry standard for workplace chat thanks to its wide range of features designed to facilitate smooth communication.
What is Troop Messenger?
Troop Messenger is a single, secure digital platform that facilitates communication between several departments or teams. In addition to many other time-saving productivity collaboration capabilities, it is a solution made to enable secure communications for Intelligence Agency Communication Solutions through messaging, phone, conference, and share screen.
On-premise Chat Server
Store your private and confidential call and conversation data inside your data centers using the highly secure and readily deployable on-premise service paradigm! We developed this self-hosted collaboration solution with chat server that is compatible with the intranet to facilitate seamless workplace communication.
Why Choose On-Premise/Troop-GRIT?
Troop-GRIT is the Troop Messenger team collaboration application's on-premise Chat Server edition. Having said that, in order to prevent third parties from accessing the application—whether over the public internet or another channel—you can install the self-managed Troop-GRIT on your local or on-premise servers.
Empowering Collaboration Across Industries
Troop Messenger caters to diverse industries, offering tailored solutions to meet specific collaboration needs. Here's how it benefits various sectors:
1. Defence: We understand the unique challenges you face to protect your critical data. Therefore we have leveraged a thought-out military messaging solution that comes with the best possible benefits. Bind and protect your communication untouched by any intruders with the defense collaboration software, Troop Messenger. Feel secure with this messaging app for defense, with the following privileges.
Troop Messenger for your C3 systems Command-Control-Communication
With the help of this Military Grade Messaging system, you can effortlessly carry out your complex C3 functions across all endpoints and monitor friendly, neutral, and enemy ships, planes, weapons, and soldiers. Utilize these resources to expedite your mission-critical operations with this ongoing defense application.
Bring your Ministry of Defense (MoD), departmental hierarchies, and military personnel to convey mission-critical controls.
focuses on the fundamental elements of military communication and coordination systems
Military-grade, self-hosted communication that keeps private talks in your data centers.
2. Government: A resourceful cum end-to-end encrypted messaging app for Government sectors, designed to sort all your complicated work in one place shrinking the latency issues. HD Audio/ Video calls & messaging in one on one or groups, video conferences, secure file sharing, and among others are some of the features of this secure chat application.
Makes Every System of Government Communicate Securely!
Federal, Devolved, Semi-Presidential, Presidential, Parliamentary Republics, and more! With its features, Troop Messenger, the government's messaging application, streamlines and organizes your dispersed communication and collaboration.
Through end-to-end encrypted chat, phone, and collaboration features, you can effectively communicate the formal aspects of your interpersonal, group, and mass communication with this dependable and safe government mobile messaging solution.
Increase the agility and delivery of your ministries and departments by digitizing your operations. With its end-to-end encrypted communication capabilities and self-managed service models, it enables you to operate in a secure and private manner.
Through chat, calls, audio-video conferencing, file sharing, and other features, Troop Messenger keeps you informed, involved, and connected for all sizes and types of government organizations—local, state, or federal.
3. Politics: Share party news, official announcements, latest activity updates of the party, all across one platform through customized political campaign software! Keep your party associates connected all the time through this Android and iOS voter management apps!
Provides secure collaboration for the political parties with:
Messaging, calling, audio-video conferencing, live-telecasting, voter participation on social media, and more! For Political Party Leaders, it's all in one safe political collaboration tool. Bring people, cadre, and party activists to this instant messaging app for political parties for optimal and well-organized party discussions. Spread your political campaign with the features and facilities of:
Secured Group Chats
Bulk Messaging
Audio-Video Conferencing
Live Feed across social media
Constituency-based chat facility
Posters/Gallery
Update party news and more
4. Ministry of Defence: Troop Messenger facilitates transparent MOD communication services to convey the policy framework of MOD to the armed forces to carry out their responsibilities. You can bring all entities onto this DOD mobile application to deliver the information securely.
Troop Messenger - Messaging Platform for Ministry of Defence
Highlights of the DOD messaging services:
Highly secured, Instant messaging and Internal Team collaboration application.
Built for Defence, Government, Law Enforcement Agencies, Aviation, BFSI, Large enterprises etc.
Organizes Virtual Meetings with audio/video calls, share & access remote screens.
A comprehensive File & Folder Management platform.
Multi-device & platform compatibility for enhanced user reach. Integrate with your existing in-house applications or third-Party Platforms.
Manages your day-to-day work communication and their updates with organized groups.
Shares ideas, work deliverables, and project updates through images, videos & files.
100+ features which can transform & enhance workplace productivity.
5. Army: Initiate Chat, Calls, remote screen access, conferencing, and more within this army chat app! Secure your sensitive army information with the world’s best security protocols and practices that combines the Double Ratchet algorithm, Pre-keys, and a triple Elliptic-curve Diffie–Hellman (3-DH) handshake, Curve25519, AES-256, HMAC-SHA256 as primitives.
Purpose-Built for Army’s land-based strategic and tactical communications
Our army-grade messaging application is a sophisticated digital system made to fit the entire structure of army within it.
Synchronizes with your independent and robust communication networks.
Collaborative and user-friendly unified and secure mobile application for army
Brings your command control systems and hierarchies to a single communication interface
Self-hosted chat application for army that helps retain confidential conversations in your data centers.
6. Navy: High-trust and uniquely determined collaboration features for the seaborne branch! Integrate our end-to-end encrypted navy messaging system, the Troop Messenger, into your communication ecosystem; to securely chat, call, collaborate and meet.
Deploy the self-hosted, have secured navy communications.
Run Troop Messenger, the self-hosted messenger, internally on your local datacenters and over your air-gapped networks to secure the conversations of your operational commands. This navy chat solution makes your army personnel to:
Manage and maintain the application
Have full control over user data and files
Route messages and calls through your servers and databases
scale the application to the needs.
7. Air Force: Reach the skies with secured Command-Control Instructions from the Base! We have incorporated highly secured collaborative tools for Airforce, such as chat, calling, audio-video conferencing, screen sharing, and others. Use it while conversating daily interactions, during natural disasters and internal disturbances, and for your other critical missions.
Defend the nation by safeguarding your air communication with Troop Messenger.
How can Troop Messenger help you?
Integrate this Air Force Instant Messenger in your military networks to provide reliable communications to your Airmen and Airwomen.
Works as an instant messaging app for Air Force.
Use it in your deployed locations for efficient information sharing.
Integrate into your C3 Systems to track all end-points of the mission.
Burnout chat erases Air Force message when the set duration on it expires
It’s a platform to conduct your operational discussions.
8. Defence Manufacturing: Our advanced Defence Manufacturing messaging system, Troop Messenger, help you exchange secure and classified conversations while you develop a comprehensive production infrastructure to produce weapons, systems, platforms, and military equipment required for defence across your Defence manufacturing industries.
Who can use this Military-Grade Messaging System?
Use it across State-Run, New State, Private Defence Manufacturing Companies, and others to secure in-office work conversations. Commission this chat application for Arms industry within your Department of Defence Production:
services headquarters,
regulatory authorities,
inter-services organisations,
technical directorates,
production establishments,
R&D centres and others.
9. Courts And Justice: Troop Messenger is a video conferencing and instant messaging platform made for the courts of India, in India. A single, integrated, and independent judiciary needs a unified communication system to bring seamless collaboration to its judges, lawyers, court staff, etc. Livestream court proceedings, upload case files to a secure file repository, transmit court orders through encrypted lines, and do much more with this court management software.
Virtual Communication Support for Virtual Courts
Courts need secure video solutions for virtual courts, such as Troop Messenger. Start conversating with the wide range of features and facilities available within this secure communication for court and justice department that helps have seamless virtual court proceedings, such as,
Hearing arguments.
Proceedings of remand cases.
Digital storage of electronic evidence management
Separate links for open and private court hearings.
10. Law Enforcement Agencies: Hinge on this law enforcement app to bring the hierarchies of your police system onto the unified communication platform to pass on the orders of law enforcement to the police on duty to maintain public safety and social order and prevent crime across your jurisdiction.
Secure Messaging Web and Mobile App for Police
A compliant messaging system for Police, Troop Messenger, is the best platform designed to solve the complexity of the communication process. With the help of advanced, safe, and secure features and intense collaboration facilities, it shall not allow classified data to fall into the hands of unauthorized persons.
Accessibility and Security:
The software application supports various deployments models such as SaaS, On-Premise, and other unique deployments required by agencies on their premises.
The software can be configured and customized at all locations.
Troop Messenger is a well-equipped encrypted chat app that secures your information end-to-end.
Operate and maintain by self.
This cross-platform can be installed in various systems in PCs, Mobile phones, and browsers.
The files such as images, videos, and other data can be accessed anytime, anywhere.
11. Intelligence Agencies: Use this modern, agile, and sophisticated instant messenger for intelligence in your country’s internal and external intelligence agencies to encrypt and safeguard the flow of critical conversations while protecting your nation against domestic and foreign threats.
Chat App for Intelligence Agencies
Highly secured, Instant messaging and Internal Team collaboration application.
Built for Defence, Government, Law Enforcement Agencies, Aviation, BFSI, Large enterprises etc.
Organizes Virtual Meetings with audio/video calls, share & access remote screens.
A comprehensive File & Folder Management platform.
Multi-device & platform compatibility for enhanced user reach. Integrate with your existing in-house applications or third-Party Platforms.
Manages your day-to-day work communication and their updates with organized groups.
Shares ideas, work deliverables, and project updates through images, videos & files.
100+ features which can transform & enhance workplace productivity.
12. IT and Software Development: In the fast-paced world of IT and software development, effective collaboration is paramount for project success. Troop Messenger facilitates real-time communication among developers, testers, and project managers, enabling agile development practices and accelerating time-to-market.
13. Healthcare: In the healthcare sector, timely communication can be a matter of life and death. Troop Messenger provides secure messaging channels compliant with HIPAA regulations, enabling healthcare professionals to exchange sensitive patient information securely while collaborating on patient care.
14. Education: In the realm of education, seamless communication between educators, administrators, and students is essential for academic success. Troop Messenger serves as a virtual classroom, enabling educators to conduct lectures, share resources, and engage with students in real time, regardless of physical distance.
15. Finance and Banking: Security and compliance are paramount in the finance and banking industry. Troop Messenger offers end-to-end encryption and compliance features, ensuring secure communication among financial professionals while facilitating collaboration on transactions, compliance tasks, and risk management.
Features that Propel Team Collaboration
Troop Messenger offers a plethora of features geared towards facilitating smooth communication and collaboration among team members. Here's a closer look at some of its standout features:
Instant Messaging: With Troop Messenger, exchanging messages in real-time has never been easier. Whether you're seeking quick updates or engaging in brainstorming sessions, the app enables instant communication, fostering agility and responsiveness within teams.
File Sharing: Gone are the days of cumbersome email exchanges. Troop Messenger allows users to effortlessly share files of various formats, including documents, images, videos, and more. This feature ensures that crucial information is readily accessible to team members, promoting efficiency and productivity.
Group Chats: Collaboration often involves multiple stakeholders. Troop Messenger simplifies group communication by offering robust group chat functionality. Users can create dedicated chat groups for projects, departments, or specific topics, enabling seamless collaboration and knowledge sharing.
Voice and Video Calls: Sometimes, a face-to-face conversation is necessary to convey complex ideas or resolve issues effectively. Troop Messenger supports voice and video calls, allowing team members to connect instantly and engage in productive discussions irrespective of their physical location.
Integration Capabilities: Troop Messenger seamlessly integrates with a variety of third-party applications commonly used in the workplace, such as Google Drive, Dropbox, Trello, and more. This integration enhances workflow efficiency by centralizing communication and eliminating the need to switch between multiple platforms.
Remote Screen Share: Reach out to your remotest office teams with Troop Messenger’s productive and ultra-new screen share feature.
End-to-End Encryption: Your work conversations are under your complete control! Chats, calls, and conferences are end-to-end encrypted in this office chat app.
Conclusion
Troop Messenger emerges as a versatile and indispensable tool for fostering collaboration and communication within teams across diverse industries. Office chat app With its robust features, user-friendly interface, and industry-specific solutions, Troop Messenger empowers organizations to streamline workflows, enhance productivity, and achieve their business objectives with ease. Whether you're a startup, a multinational corporation, or a non-profit organization, Troop Messenger is your ultimate instant messaging app for office chat, facilitating seamless collaboration and driving success in the digital age.
0 notes
Text
Smart Airports Market Soars: A USD 8.3 Billion Skyline by 2027
The Smart Airports Market is on a strategic trajectory, marked by a comprehensive forecast in the range of USD 7.0 Billion to USD 8.3 Billion by 2027, underlining a steady Compound Annual Growth Rate (CAGR) of 3.5% during 2022-2027. This trajectory is grounded in the increasing demand for sophisticated smart solutions, catering to the rising needs of air-passenger footfall on a global scale.
Download PDF Brochure: https://www.marketsandmarkets.com/pdfdownloadNew.asp?id=544
The Upgrades & Service segment is anticipated to take the lead in the smart airports market during the forecast period. This surge is attributed to ongoing efforts to upgrade existing systems and solutions with advanced technologies, focusing on improving both passenger experience and operational efficiency. The market is propelled by a collective desire for enhanced maintenance and services to ensure the seamless operation of airport systems.
In the system segment, the Endpoint Devices category is projected to dominate the market share during the forecast period. Airports worldwide are leveraging dependable endpoint devices, including biometrics, RFID, and beacons, to expedite the screening process. These advancements enhance customer experience and streamline airport operations, significantly raising security standards.
Within the application segment, the airside category is slated to dominate the market share during the forecast period. Smart operations at the airside, aimed at enhancing ground staff management and expediting aircraft turnaround, have witnessed substantial demand. This surge is evident in the adoption of advanced solutions such as sophisticated aircraft parking systems and cutting-edge maintenance and health monitoring.
The medium-sized airport segment is positioned to lead the smart airports market during the forecast period. This leadership role is attributed to the increasing demand for the installation of advanced technologies in airports and the rising need for system modifications on a global scale.
In the operation segment, non-aeronautical operations are poised to dominate market share during the forecast period. Airports are strategically focusing on targeted digital advertising and other initiatives like inventory management and intelligent transport services to meet consumer expectations and drive the growth of the non-aeronautical segment.
Asia Pacific is anticipated to account for the largest market share in 2022, with North America projected to witness the highest Compound Annual Growth Rate (CAGR) during the forecast period.
The rise in air travel demand, growth in international tourism, and the advent of low-cost flights to developing nations like India are key factors fueling the surge in passenger traffic in the Asia-Pacific region. The increasing demand for automated procedures, including baggage handling and self-check-in services, is expected to support the significant expansion of smart airports in the Asia-Pacific region.
Inquiry Before Buying: https://www.marketsandmarkets.com/Enquiry_Before_BuyingNew.asp?id=544
Major players operating in the smart airports market include SITA (Switzerland), THALES (France), Siemens AG (Germany), Amadeus IT Group SA (Spain), IBM Corporation (US), Cisco Systems Inc. (US), Indra Sistemas S.A. (Spain), Honeywell International Inc. (US), L3Harris Technologies Inc (US).are some of the market players.
0 notes
Text

Kuwait Managed Security Services (MSS) Market size at USD 672.14 million in 2023. During the forecast period between 2024 and 2030, BlueWeave expects the Kuwait Managed Security Services (MSS) Market size to expand at a CAGR of 6.11% reaching a value of USD 833.9 million by 2030. Stringent government rules to safeguard consumer data privacy and the growing frequency of cyberattacks are key growing factors for the Kuwait Managed Security Services (MSS) Market. Additionally, it is projected that the Kuwaiti Managed Security Services (MSS) Market will expand over the period in analysis due to rising internet and mobile device usage.
Opportunity: Rising adoption of cloud technologies
Based on security type, the Kuwait Managed Security Services (MSS) Market is segmented into network security, cloud security, endpoint security, and application security. The cloud security segment accounts for the highest market share in the market by security type. The rising adoption of cloud technologies, such as artificial intelligence (AI) and machine learning (ML), across businesses in Kuwait is boosting the need for advanced cloud security systems as a safety measure for data protection. These security measures include data privacy protection, data and resource access management, and user and device authentication.
Sample Request @ https://www.blueweaveconsulting.com/report/kuwait-managed-security-services-market/report-sample
0 notes
Text
Managed Security Services (MSS) Market To Deliver Prominent Growth & Striking Opportunities During 2033
Market Definition
Managed security services (MSS) are a type of security service that helps organizations manage and monitor their security systems and infrastructure. The services are typically provided by a third-party security service provider and can include things like security monitoring, incident response, and vulnerability management.
Market Outlook
In the managed security services (MSS) market, the service providers are constantly innovating and introducing new services and technologies to address the changing security needs of their clients. Some of the key trends in this market are:
The increasing adoption of cloud-based MSS: With the increasing adoption of cloud computing, more and more MSS providers are offering their services via the cloud. This enables organizations to benefit from the scalability, flexibility and cost-effectiveness of the cloud.
The growing popularity of managed detection and response (MDR) services: MDR services are becoming increasingly popular as they provide a more comprehensive and proactive approach to security. MSS providers are investing in MDR services to meet the growing demand from their clients.
The increasing focus on artificial intelligence (AI) and machine learning: AI and machine learning are being used by MSS providers to improve the accuracy of threat detection and response. These technologies are also being used to automate various tasks, such as security monitoring and incident response.
Lack of skilled workforce: There is a lack of skilled workforce in the field of cyber security, which is a key requirement for providing MSS. This is a major challenge for vendors in this market.
High cost of MSS: MSS can be quite costly, especially for small and medium businesses. This is a key restraint for the growth of this market.
Lack of awareness: There is a lack of awareness about MSS among small and medium businesses. This is a key challenge for vendors in this market.
Request Sample: https://www.globalinsightservices.com/request-sample/GIS20064/
Research Objectives
Estimates and forecast the overall market size for the total market, across product, service type, type, end-user, and region
Detailed information and key takeaways on qualitative and quantitative trends, dynamics, business framework, competitive landscape, and company profiling
Identify factors influencing market growth and challenges, opportunities, drivers and restraints
Identify factors that could limit company participation in identified international markets to help properly calibrate market share expectations and growth rates
Trace and evaluate key development strategies like acquisitions, product launches, mergers, collaborations, business expansions, agreements, partnerships, and R&D activities
Thoroughly analyze smaller market segments strategically, focusing on their potential, individual patterns of growth, and impact on the overall market
To thoroughly outline the competitive landscape within the market, including an assessment of business and corporate strategies, aimed at monitoring and dissecting competitive advancements.
Identify the primary market participants, based on their business objectives, regional footprint, product offerings, and strategic initiatives
Market Segmentation
The Managed Security Services (MSS) Market is segmented into deployment mode, enterprise size, application, vertical, and region. By deployment mode, the market is divided into On-premise and Cloud. Based on enterprise size, the market is bifurcated into large enterprises, small & medium-sized enterprises. By application, it is categorized as a Managed IPS and IDS, Distributed Denial of Services (DDoS), Unified Threat Management (UTM), Secured Information & Event Management (SIEM), Firewall Management, Endpoint Security, and Others. Whereas on the basis of the vertical, it is segmented into BFSI, Healthcare, Manufacturing, Retail, Telecom & IT, and Others. Region-Wise the market is segmented by North America, Europe, Asia-Pacific, and the rest of the world.
Request Customization@ https://www.globalinsightservices.com/request-customization/GIS20064/
Major Players
The Managed Security Services (MSS) Market report includes players such as AT&T (US), Broadcom (US), BT Group (UK), Check Point Software (Israel), Cisco System Inc. (US), DXC Technology (US), Fortinet Inc. (US), Hewlett Packard Enterprise (US), IBM Corporation (US), and SecureWorks Inc. (US), among others.
Request Discounted Pricing@ https://www.globalinsightservices.com/request-special-pricing/GIS20064/
Research Scope
Scope – Highlights, Trends, Insights. Attractiveness, Forecast
Market Sizing – Product Type, End User, Offering Type, Technology, Region, Country, Others
Market Dynamics – Market Segmentation, Demand and Supply, Bargaining Power of Buyers and Sellers, Drivers, Restraints, Opportunities, Threat Analysis, Impact Analysis, Porters 5 Forces, Ansoff Analysis, Supply Chain
Business Framework – Case Studies, Regulatory Landscape, Pricing, Policies and Regulations, New Product Launches. M&As, Recent Developments
Competitive Landscape – Market Share Analysis, Market Leaders, Emerging Players, Vendor Benchmarking, Developmental Strategy Benchmarking, PESTLE Analysis, Value Chain Analysis
Company Profiles – Overview, Business Segments, Business Performance, Product Offering, Key Developmental Strategies, SWOT Analysis
Buy your copy here: https://www.globalinsightservices.com/checkout/single_user/GIS20064/
With Global Insight Services, you receive:
10-year forecast to help you make strategic decisions
In-depth segmentation which can be customized as per your requirements
Free consultation with lead analyst of the report
Infographic excel data pack, easy to analyze big data
Robust and transparent research methodology
Unmatched data quality and after sales service
Contact Us:
Global Insight Services LLC
16192, Coastal Highway, Lewes DE 19958
E-mail: [email protected]
Phone: +1-833-761-1700
Website: https://www.globalinsightservices.com/
0 notes
Text
Rapid Surge in Botnet Detection Market: Projected Revenue of US$ 15.4 Billion by 2033
The need for sophisticated security measures has increased in response to the ever-widening danger landscape, driving the Botnet Detection Market to unprecedented heights. Recent market research indicates that the Botnet Detection Market is expected to generate a significant amount of revenue in 2023—US$ 839.4 million. With an astounding valuation of US$ 15,358.7 million by 2033 and an excellent CAGR of 33.7% over the forecast period, the market is expected to rise exponentially in the future.
The increasing digitization of sectors is making them more vulnerable to botnet assaults. The integrity of digital ecosystems is seriously threatened by these attacks, which are coordinated by networks of hacked devices. The worldwide corporate environment is adopting cutting-edge botnet detection systems to combat this threat.
Ready to Gain Knowledge? Grab Your Insights Sample! : https://www.futuremarketinsights.com/reports/sample/rep-gb-14555
Key Takeaways: Botnet Detection Market
By component, the solution segment is anticipated to account for the leading share in the global demand for botnet detection during the forecast period. However, the services segment is estimated to grow at a robust CAGR of 34.7% through 2032.
By deployment, the cloud-based segment is anticipated to grow at a CAGR of 35% between 2022 & 2032.
Among the enterprise size, large enterprises segment is anticipated to hold the largest share of the global market and is estimated to increase at a CAGR of 33% between 2022 & 2032.
By industry, the media and entertainment segment is anticipated to grow at a CAGR of 35.9% between 2022 & 2032.
North America is dominating botnet detection market followed by Europe region in 2022. South Asia & Pacific is estimated to grow at the fastest rate over the forecast period.
The market in U.S. is expected to progress at a CAGR of around 33.9% through 2032.
In India, the botnet detection market is expected to grow at a CAGR of 39.2% during the forecast period.
Botnet detection market in China is estimated to witness the absolute opportunity of US$ 955.2 Mn in the forecast period.
Competition Analysis – Regional Trends
The Botnet Detection Market is characterized by intense competition, driven by the growing importance of cybersecurity in today’s interconnected world. A noteworthy trend is the dominance of the top 5 vendors, accounting for around 45% of the market share. As cyber threats continue to evolve, these vendors are at the forefront of delivering cutting-edge solutions to counteract sophisticated botnet attacks.
Region-wise Insights
Across various regions, the demand for robust botnet detection solutions is on the rise. North America leads the charge, being an early adopter of advanced cybersecurity measures. Europe follows suit, with a keen focus on data protection regulations. Asia Pacific showcases significant potential for growth due to the rapid digitization of industries. Meanwhile, emerging economies in Latin America and the Middle East are also ramping up their cybersecurity efforts to safeguard critical digital infrastructure.
Request for Methodology:
https://www.futuremarketinsights.com/request-report-methodology/rep-gb-14555
Category-wise Insights
In the landscape of botnet detection, diverse categories of industries are seeking tailored solutions. From banking and finance to healthcare and manufacturing, every sector is recognizing the need for proactive threat mitigation. As Internet of Things (IoT) devices proliferate, securing these interconnected endpoints becomes paramount, spurring demand for botnet detection across consumer electronics, industrial automation, and smart cities.
Botnet Detection Market Outlook By Category
By Component:
Botnet Detection Solution
Services
Professional Services
Managed Services
By Deployment:
Cloud
On-premises
By Enterprise Size:
Small and Medium-sized Enterprises (SMEs)
Large Enterprises
By Industry:
BFSI
Healthcare
IT and Telecom
Retail
Media and Entertainment
Travel and Hospitality
Government
Others
0 notes
Text
0 notes
Text
CISA’s Zero Trust Maturity Model 2.0: Cybersecurity Roadmap

Zero trust maturity model version 2
Zero trust maturity model 2.0
With the help of CISA’s Zero Trust Maturity Model v2.0, the Federal IT environment is rapidly changing in favor of increased cybersecurity. To improve their cyber posture, federal agencies might use this model as a guide. The correct tools must be chosen in order for government entities to successfully manage this transition. Designed to fulfill the strict compliance requirements of federal organizations, Google Workspace brings strong security features to the table.
Google Workspace’s Role in Cisa zero trust maturity model 2.0
Cisa zero trust maturity model
Thin-layer security, continuous validation, and device-independent protection are highlighted in the CISA Zero Trust Maturity Model. A set of principles and ideas known as “zero trust” is intended to reduce ambiguity when it comes to enforcing precise, least privilege per-request access choices in information systems and services while dealing with networks that are seen as weak. Maintaining as much granularity in access control enforcement while preventing unwanted access to data and services is the aim.
For the following reasons, zero trust puts fine-grained security restrictions across individuals, systems, data, and assets that vary over time in a more data-centric manner rather than a location-centric one.To educate agencies on how to apply Zero Trust (ZT) concepts to mobile security technologies that are already on the market and probably included in a Federal Enterprise’s mobility program, CISA prepared the Applying Zero Trust concepts to Enterprise Mobility document.
On March 7, 2022, and ending on April 20, 2022, CISA made the document available for public comment. A revised version of the paper will be produced when CISA has taken into consideration the feedback provided by all responders. The formulation, execution, enforcement, and evolution of security rules are supported by the visibility that this gives. At a deeper level, zero trust can need altering the cybersecurity culture and mindset of a business.The following elements of Google Workspace support the idea of “never trust, always verify”:
Boost Access Control and Identity:
Context-Aware The correct individuals only get access to the right data thanks to strong authentication mechanisms and access.
Zero trust maturity model version 2
These measures safeguard private data at all points of access with sophisticated device controls and endpoint management.
Collaborating while preserving data is made possible by granular sharing settings and data loss prevention (DLP) features.Uncovered Information from the Google Workspace Zero Trust Security Workshop.
Recent Google Workspace Zero Trust Security Workshop provided an insightful overview of how Google Workspace may help federal agencies on their Zero Trust journeys. Using Zero Trust concepts in the federal context was discussed at the session by CISA specialists. A practical application of Zero Trust architecture driven by Google Workspace and Gemini AI was shown in the ManTech case study, which proved beneficial to the attendees.
The platform’s ability to achieve CMMC compliance is shown by ManTech’s shared experience, which provides other agencies with a useful model. IT decision-makers had practical experience with Google Workspace’s security controls via interactive demonstrations that were included in the training.
Zero trust maturity model
The Google Workspace Zero trust best practices guide for U.S. public sector organizations is a great tool for anybody who was unable to attend the event and wants to achieve CISA-compliant Zero trust maturity.
Special Sessions at Google Cloud Next ’24 on Google Workspace and Federal Cybersecurity.
Google Cloud Next ’24 is the next stop in the discussion, with talks on:
Achieve strict compliance across many frameworks (CJIS, FedRAMP, ITAR, DoD ILs) with Assured Workloads for Public Sector Compliance.
Using Gemini in Google Workspace, Keep Your Data Private and Compliant Come learn about the privacy and security features that come standard with Gemini for Google Workspace and how Sovereign Controls may help your company attain digital sovereignty.
AI-Powered Cooperation to Break Down Silos: Discover how creativity, productivity, and safe collaboration are facilitated with Google Workspace.
Through Google Workspace, Gemini: Privacy Guaranteed: Learn about the ways that Gemini protects data sovereignty while offering strong capabilities.
Ready for the government: The way that Google Workspace makes safe collaboration possible: Learn how federal, state, and local government organizations may simplify operations while upholding the highest standards of data security (with ManTech) using Google Workspace.
Google is dedicated to providing creative solutions that will assist agencies in the dynamic field of federal cybersecurity. Zero Trust principles are the foundation of Google Workspace, which gives users the flexibility and toughness they need to meet new challenges. Agency tasks are accomplished and sensitive data is safeguarded with more efficacy when paired with the wider capabilities of Google Cloud.
Federal agencies will always have access to state-of-the-art resources necessary to keep ahead of emerging cyber threats because to Google’s commitment to ongoing innovation.
Read more on Govindhtech.com
0 notes
Text
Smart Airports Market Soars: A USD 8.3 Billion Skyline by 2027
The Smart Airports Market is on a strategic trajectory, marked by a comprehensive forecast in the range of USD 7.0 Billion to USD 8.3 Billion by 2027, underlining a steady Compound Annual Growth Rate (CAGR) of 3.5% during 2022-2027. This trajectory is grounded in the increasing demand for sophisticated smart solutions, catering to the rising needs of air-passenger footfall on a global scale.
Download PDF Brochure: https://www.marketsandmarkets.com/pdfdownloadNew.asp?id=544
The Upgrades & Service segment is anticipated to take the lead in the smart airports market during the forecast period. This surge is attributed to ongoing efforts to upgrade existing systems and solutions with advanced technologies, focusing on improving both passenger experience and operational efficiency. The market is propelled by a collective desire for enhanced maintenance and services to ensure the seamless operation of airport systems.
In the system segment, the Endpoint Devices category is projected to dominate the market share during the forecast period. Airports worldwide are leveraging dependable endpoint devices, including biometrics, RFID, and beacons, to expedite the screening process. These advancements enhance customer experience and streamline airport operations, significantly raising security standards.
Within the application segment, the airside category is slated to dominate the market share during the forecast period. Smart operations at the airside, aimed at enhancing ground staff management and expediting aircraft turnaround, have witnessed substantial demand. This surge is evident in the adoption of advanced solutions such as sophisticated aircraft parking systems and cutting-edge maintenance and health monitoring.
The medium-sized airport segment is positioned to lead the smart airports market during the forecast period. This leadership role is attributed to the increasing demand for the installation of advanced technologies in airports and the rising need for system modifications on a global scale.
In the operation segment, non-aeronautical operations are poised to dominate market share during the forecast period. Airports are strategically focusing on targeted digital advertising and other initiatives like inventory management and intelligent transport services to meet consumer expectations and drive the growth of the non-aeronautical segment.
Asia Pacific is anticipated to account for the largest market share in 2022, with North America projected to witness the highest Compound Annual Growth Rate (CAGR) during the forecast period.
The rise in air travel demand, growth in international tourism, and the advent of low-cost flights to developing nations like India are key factors fueling the surge in passenger traffic in the Asia-Pacific region. The increasing demand for automated procedures, including baggage handling and self-check-in services, is expected to support the significant expansion of smart airports in the Asia-Pacific region.
Inquiry Before Buying: https://www.marketsandmarkets.com/Enquiry_Before_BuyingNew.asp?id=544
Major players operating in the smart airports market include SITA (Switzerland), THALES (France), Siemens AG (Germany), Amadeus IT Group SA (Spain), IBM Corporation (US), Cisco Systems Inc. (US), Indra Sistemas S.A. (Spain), Honeywell International Inc. (US), L3Harris Technologies Inc (US).are some of the market players.
0 notes
Text
Exploring the Rise of Druva Share Price
Introduction
Nowadays, Druva Share Price has been witnessing a remarkable surge, Druva is a leading provider of cloud data protection and management solutions,. This article delves into the factors driving the upward trajectory of Druva Share Price and the implications for investors. Druva Data Solutions Ltd ("Druva") is a software-as-a-service platform developed to protect and manage enterprise data across edge, on-premises and cloud workloads. Their platform offers innovative cloud-native solutions to address data protection, governance, and compliance needs. Built on scalability and security, Druva enables efficient data protection and management across diverse environments.
Druva's strategy centres on delivering comprehensive data resilience solutions, covering backup, disaster recovery, and archival functions. Using AI and machine learning, Druva helps automate data protection, optimize storage, and preemptively address risks, boosting operational efficiency and resilience while cutting costs.
In 2011, smartphone support was added to the inSync app. The next year, the company relocated to Silicon Valley, refocusing on cloud-based data management. In 2014, Druva launched its Phoenix server backup product. By 2018, Druva had acquired CloudRanger, based in Letterkenny, specializing in backup and disaster recovery. In 2019, CloudLances was acquired to bolster on-premises to cloud performance. The subsequent year, sfApex, a Texas-based company focused on Salesforce data backup and migration, was acquired.
Druva Data Solutions is a Foreign Subsidiary of Druva Inc. and was incorporated on 11 February 2013, with its registered office at Plot No- 403/1, CTS No- 985, 8th Floor The Pavilion, Senapati Barat Road, Shivaji Nagar Pune MH 411016 IN.
Innovative Cloud Data Solutions
One of the primary drivers behind the rise in Druva's share price is its innovative cloud data protection and management solutions. Druva's platform offers organizations a comprehensive suite of services to safeguard and manage their data across various endpoints, on-premises infrastructure, and cloud environments. As businesses increasingly adopt cloud-based solutions for data protection, Druva's cutting-edge offerings have positioned it as a market leader, driving investor confidence and share price appreciation.
Strong Financial Performance
Druva's strong financial performance has also contributed to the surge in its share price. The company has consistently delivered impressive revenue growth and profitability, reflecting the increasing demand for its solutions. Investors are optimistic about Druva's ability to capitalize on the growing market for cloud data protection, driving speculation and investment in its shares.
Expansion into New Markets
Druva's strategic expansion into new markets has further fueled the rise in its share price. The company has been expanding its presence globally, tapping into emerging markets and forging partnerships with key players in the industry. By diversifying its geographic footprint and customer base, Druva has enhanced its growth prospects and attracted investor attention, leading to a surge in its share price.
Recognition and Industry Accolades
Druva's industry recognition and accolades have also played a role in boosting investor confidence and share price. The company has received numerous awards and accolades for its innovative solutions and customer-centric approach. Such recognition not only validates Druva's leadership position in the market but also enhances its reputation among investors, driving increased interest in its shares.
Strategic Partnerships and Collaborations
Druva's strategic partnerships and collaborations with leading technology companies have contributed to its share price rally. By aligning with industry giants, Druva has expanded its reach and access to new customers, while also leveraging complementary technologies to enhance its product offerings. Investors view these strategic alliances as a positive indicator of Druva's growth potential, driving enthusiasm for its shares.
Future Outlook
As Druva continues to innovate and expand its market presence, the future looks promising for the company and its investors. With a solid foundation built on cutting-edge technology, strong financial performance, and strategic partnerships, Druva is well-positioned to capitalize on the growing demand for cloud data protection and management solutions. Investors can expect the upward trajectory of Druva's share price to persist as the company continues to deliver value and drive innovation in the market.
Conclusion
The rise of Druva's share price reflects investor confidence in the company's innovative solutions, strong financial performance, and strategic initiatives. As Druva continues to expand its market presence and capitalize on emerging opportunities, investors stand to benefit from the company's continued growth and success. With a focus on driving value for customers and shareholders alike, Druva is poised to maintain its position as a leader in the cloud data protection and management industry.

0 notes
Text
How Does Walmart Product API Data Extraction Enhance Business Decision-Making
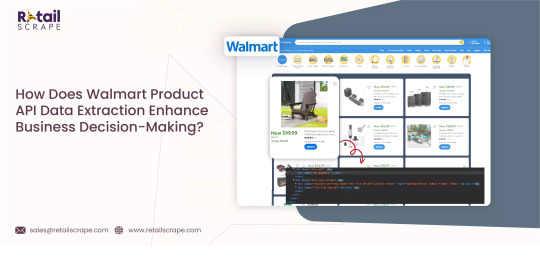
Have you heard about Walmart API data and its pivotal role in today's data-driven business landscape? In this digital age, where information is critical, accessing and analyzing data from retail giants like Walmart can provide invaluable insights for businesses. Walmart product API data extraction is a gateway to a treasure trove of information about products, prices, sales trends, and customer behavior.
Walmart data scraping involves collecting this valuable information from the Walmart website using automated tools and techniques. This process allows businesses to gather comprehensive data about Walmart's vast product catalog, pricing strategies, customer reviews, and more. By leveraging retail data scraping services, businesses can gain a competitive edge by monitoring market trends, analyzing competitor pricing, and optimizing their product offerings.
Furthermore, Walmart's scraping product API offers a more structured and efficient way to access data than traditional web scraping methods. Through the API, developers can programmatically retrieve specific data points in a standardized format, streamlining the data extraction process and enabling real-time updates.
Understanding how to scrape Walmart data and harness Walmart's API capabilities can empower businesses to make data-driven decisions, enhance their market intelligence, and stay ahead of the competition in the dynamic retail landscape. In this article, we will delve deeper into the intricacies of scraping Walmart data and explore the vast potential of Walmart's API for businesses.
Understanding API Data and Its Relevance to Business
API data, or Application Programming Interface data, refers to the information and functionalities that can be accessed and exchanged between different software applications through APIs. APIs serve as intermediaries that allow different systems to communicate and interact with each other seamlessly.
In the business context, Walmart product API data facilitates integration and interoperability between various software platforms and systems used within an organization. Allowing different applications to share data and functionality enables businesses to streamline operations, automate processes, and enhance efficiency.
Working Principles of API Data
The working principles of scraping API data involve leveraging the functionalities of APIs to extract relevant information from various sources in a structured and automated manner. This process typically follows these steps:
Authentication: Access to API data often requires authentication to ensure secure access to protected resources. It involves obtaining API keys or tokens and authenticating requests using standard authentication mechanisms such as OAuth.
Endpoint Discovery: Identify the API endpoints that contain the data you want to scrape. These endpoints represent specific resources or functionalities the API exposes and define the URLs or URIs to access the data.
Request Construction: Construct HTTP requests to access the desired data from the API endpoints. It specifies the HTTP method (e.g., GET, POST), required parameters or query strings, and headers such as authentication tokens.
Data Retrieval: Send the constructed requests to the API endpoints and retrieve the response data. The response typically contains the requested information in a structured data format such as JSON or XML.
Data Parsing: Parse the response data to extract the relevant information you want to scrape. It involves navigating the JSON or XML structure and extracting specific data fields or elements using parsing techniques such as XPath or JSONPath.
Data Storage: Store the scraped data in a structured format such as a database, CSV file, or spreadsheet for further analysis or processing. Ensure that the data storage mechanism aligns with your requirements for accessibility, scalability, and data integrity.
Error Handling: Implement error handling mechanisms to handle exceptions or errors that may occur during the scraping process. It includes gracefully handling HTTP status codes, connection errors, rate limiting, and other potential issues.
By following these principles, businesses can effectively scrape data from APIs, collect valuable insights, and leverage the information available through API endpoints for various purposes, such as market research, competitive analysis, and business intelligence.
For example, businesses can use APIs to integrate customer relationship management (CRM) systems with marketing automation platforms, enabling them to synchronize customer data, track interactions, and automate marketing campaigns. Similarly, APIs can connect e-commerce platforms with inventory management systems, enabling real-time product availability, pricing, and order updates.
Overall, e-commerce web scraping empowers businesses to effectively leverage the capabilities of different software applications and systems, enabling them to improve collaboration, enhance productivity, and deliver better customer service. It is vital in driving digital transformation and innovation across various industries, enabling businesses to stay competitive and adapt to evolving market trends and customer needs.
Role of Walmart Product API Data Extraction to Enhance Business Decision-Making
The role of Walmart data collection in enhancing business decision-making is pivotal. By tapping into the API's information, businesses can gain valuable insights into market dynamics, competitor strategies, and customer behavior. Analysis of this data empowers businesses to make informed decisions across multiple facets of operations. From market analysis and inventory management to competitive intelligence and marketing optimization, Walmart's Product data scraping services offer a treasure trove of data that can be leveraged to drive strategic initiatives. By utilizing this data effectively, businesses can stay ahead of trends, optimize resource allocation, and ultimately enhance their competitive position in the marketplace.
Gathering Walmart Data via Web Scraping
Utilizing web scraping for gathering data offers a more straightforward approach than utilizing specialized programs like the Walmart Data Extractor. The process begins with web scraping, where the company identifies a website with a layout resembling the target site, such as Walmart's product page. Ensuring a fast response time from the website is essential, and browsers supporting web scraping, like Google Chrome, are preferred.
Following this, software is developed for scraping, typically using languages like Python, Perl, Ruby, or PHP. Python is popular due to its cross-platform compatibility and readability. This software sends requests to the target website, retrieves desired data and saves it for further analysis or reporting. Remember that some web scraping technologies may necessitate additional software installation, such as Python, for optimal functionality.
Scraping Walmart Data Using Python
We are explaining the steps to scrape Walmart data using Python.
Obtain API Key: Sign up for Walmart's Developer Portal and obtain an API key to access their data.
Install Required Libraries: Install the necessary Python libraries for working with APIs, such as Requests.
pip install requests
Import Libraries: Import the required libraries into your Python script.
Handle Pagination (if needed): If the API response is paginated, handle pagination by iterating through multiple pages of results.
Extract Desired Information: Extract the relevant information from the API response, such as product names, prices, and ratings.
Conclusion
Walmart's Product scraping API offers businesses a powerful means of accessing and analyzing a wealth of product information on the platform. By harnessing this API, businesses can efficiently retrieve product names, prices, ratings, and more data, enabling them to gain valuable insights into market trends, competitor offerings, and consumer preferences. This data can inform strategic decision-making, enhance pricing strategies, optimize inventory management, and drive overall business growth. With proper implementation and utilization, Walmart Product API data extraction empowers businesses to stay competitive, make informed decisions, and capitalize on opportunities in the ever-evolving retail landscape.
UnlUnlock the potential of data-driven decisions through our Retail Scrape Company. Harness consumer behavior insights, refine pricing strategies, and outpace rivals with live retail data scraping. Elevate your enterprise with our full-range pricing optimization and strategic decision support. Connect today to transform your retail endeavors and amplify profits!
know more :
https://www.retailscrape.com/walmart-product-api-data-extraction-enhance-business.php
#WalmartProductAPIData#WalmartProductAPIDataExtraction#WalmartDataScraping#Walmart'sProductScrapingAPI#ScrapeWalmartData#WalmartDataCollection
0 notes