#codebase
Text

Végre egy rendesen felszerelt iroda!
25 notes
·
View notes
Text

Cross mobile app development lets you create one codebase for multiple platforms. Save time and resources while delivering a seamless mobile experience with cross-platform development.
#cross mobile app development#mobile app development#platforms#app development#hybrid app builder#codebase#multiple platforms#mobile experience#development
2 notes
·
View notes
Text
Clearing the “Fog of More” in Cyber Security
New Post has been published on https://thedigitalinsider.com/clearing-the-fog-of-more-in-cyber-security/
Clearing the “Fog of More” in Cyber Security
At the RSA Conference in San Francisco this month, a dizzying array of dripping hot and new solutions were on display from the cybersecurity industry. Booth after booth claimed to be the tool that will save your organization from bad actors stealing your goodies or blackmailing you for millions of dollars.
After much consideration, I have come to the conclusion that our industry is lost. Lost in the soup of detect and respond with endless drivel claiming your problems will go away as long as you just add one more layer. Engulfed in a haze of technology investments, personnel, tools, and infrastructure layers, companies have now formed a labyrinth where they can no longer see the forest for the trees when it comes to identifying and preventing threat actors. These tools, meant to protect digital assets, are instead driving frustration for both security and development teams through increased workloads and incompatible tools. The “fog of more” is not working. But quite frankly, it never has.
Cyberattacks begin and end in code. It’s that simple. Either you have a security flaw or vulnerability in code, or the code was written without security in mind. Either way, every attack or headline you read, comes from code. And it’s the software developers that face the ultimate full brunt of the problem. But developers aren’t trained in security and, quite frankly, might never be. So they implement good old fashion code searching tools that simply grep the code for patterns. And be afraid for what you ask because as a result they get the alert tsunami, chasing down red herrings and phantoms for most of their day. In fact, developers are spending up to a third of their time chasing false positives and vulnerabilities. Only by focusing on prevention can enterprises really start fortifying their security programs and laying the foundation for a security-driven culture.
Finding and Fixing at the Code Level
It’s often said that prevention is better than cure, and this adage holds particularly true in cybersecurity. That’s why even amid tighter economic constraints, businesses are continually investing and plugging in more security tools, creating multiple barriers to entry to reduce the likelihood of successful cyberattacks. But despite adding more and more layers of security, the same types of attacks keep happening. It’s time for organizations to adopt a fresh perspective – one where we home in on the problem at the root level – by finding and fixing vulnerabilities in the code.
Applications often serve as the primary entry point for cybercriminals seeking to exploit weaknesses and gain unauthorized access to sensitive data. In late 2020, the SolarWinds compromise came to light and investigators found a compromised build process that allowed attackers to inject malicious code into the Orion network monitoring software. This attack underscored the need for securing every step of the software build process. By implementing robust application security, or AppSec, measures, organizations can mitigate the risk of these security breaches. To do this, enterprises need to look at a ‘shift left’ mentality, bringing preventive and predictive methods to the development stage.
While this is not an entirely new idea, it does come with drawbacks. One significant downside is increased development time and costs. Implementing comprehensive AppSec measures can require significant resources and expertise, leading to longer development cycles and higher expenses. Additionally, not all vulnerabilities pose a high risk to the organization. The potential for false positives from detection tools also leads to frustration among developers. This creates a gap between business, engineering and security teams, whose goals may not align. But generative AI may be the solution that closes that gap for good.
Entering the AI-Era
By leveraging the ubiquitous nature of generative AI within AppSec we will finally learn from the past to predict and prevent future attacks. For example, you can train a Large Language Model or LLM on all known code vulnerabilities, in all their variants, to learn the essential features of them all. These vulnerabilities could include common issues like buffer overflows, injection attacks, or improper input validation. The model will also learn the nuanced differences by language, framework, and library, as well as what code fixes are successful. The model can then use this knowledge to scan an organization’s code and find potential vulnerabilities that haven’t even been identified yet. By using the context around the code, scanning tools can better detect real threats. This means short scan times and less time chasing down and fixing false positives and increased productivity for development teams.
Generative AI tools can also offer suggested code fixes, automating the process of generating patches, significantly reducing the time and effort required to fix vulnerabilities in codebases. By training models on vast repositories of secure codebases and best practices, developers can leverage AI-generated code snippets that adhere to security standards and avoid common vulnerabilities. This proactive approach not only reduces the likelihood of introducing security flaws but also accelerates the development process by providing developers with pre-tested and validated code components.
These tools can also adapt to different programming languages and coding styles, making them versatile tools for code security across various environments. They can improve over time as they continue to train on new data and feedback, leading to more effective and reliable patch generation.
The Human Element
It’s essential to note that while code fixes can be automated, human oversight and validation are still crucial to ensure the quality and correctness of generated patches. While advanced tools and algorithms play a significant role in identifying and mitigating security vulnerabilities, human expertise, creativity, and intuition remain indispensable in effectively securing applications.
Developers are ultimately responsible for writing secure code. Their understanding of security best practices, coding standards, and potential vulnerabilities is paramount in ensuring that applications are built with security in mind from the outset. By integrating security training and awareness programs into the development process, organizations can empower developers to proactively identify and address security issues, reducing the likelihood of introducing vulnerabilities into the codebase.
Additionally, effective communication and collaboration between different stakeholders within an organization are essential for AppSec success. While AI solutions can help to “close the gap” between development and security operations, it takes a culture of collaboration and shared responsibility to build more resilient and secure applications.
In a world where the threat landscape is constantly evolving, it’s easy to become overwhelmed by the sheer volume of tools and technologies available in the cybersecurity space. However, by focusing on prevention and finding vulnerabilities in code, organizations can trim the ‘fat’ of their existing security stack, saving an exponential amount of time and money in the process. At root-level, such solutions will be able to not only find known vulnerabilities and fix zero-day vulnerabilities but also pre-zero-day vulnerabilities before they occur. We may finally keep pace, if not get ahead, of evolving threat actors.
#ai#ai tools#Algorithms#Application Security#applications#approach#AppSec#assets#attackers#awareness#Business#code#codebase#coding#Collaboration#communication#Companies#comprehensive#compromise#conference#creativity#cyber#cyber security#Cyberattacks#cybercriminals#cybersecurity#data#detection#developers#development
0 notes
Text
A Complete Guide to Create and Publish React Components using Bit Harmony

Overview
Bit stands at the intersection between product and engineering. Bit allows you to identify a section of your code as a component and treat it independently from the rest of your project. It will enable you to create components and compose them with each other. They can be of different kinds like apps, pages, UI components, backend services, and even content.
Goals
Avoid unnecessary amounts of duplicated code, and create reusable code.
Simplify the sharing process since you don’t have to set up a separate repo and rework the way you import those files into your project.
Features:
Component source-control = Essentially, git but for components
Isolated component development = Includes isolated rendering, tests and builds,
Component dependency graphs = Includes two types of dependencies, node packages and other components
Create workspace
The first step in the Bit journey is to initiate a new Bit workspace. It is a development workspace for distributed, component-driven software. Log in to your bit.cloud account. Create a scope or organization.

Installation
First, you need to install the bvm in your global environment. Next, install bit with the using bvm install command and make sure to install the latest version.
If you get a warning or the bvm command is not available you will need to run the code below.
echo 'export PATH=$HOME/bin:$PATH' >> ~/.bashrc && source ~/.bashrc
Creating bit components from an existing project
If you are creating bit components from an existing project then First, initialize bit harmony workspace. Bit creates the following files when initializing a new workspace:
workspace.jsonc – The workspace configuration file that sets rules and policies for the workspace and all its components.You need configure the file to apply the React development environment on all components to your workspace, and to change the default scope to your remote scope. You can refer this section
.bitmap – An auto-generated mapping between tracked components in the workspace and their physical location on the file system. The file structure of your workspace is entirely up to you.
.git/bit (hidden directory) – Your local scope. Where your workspace’s component release versions are stored.
Start configuring the workspace.jsonc file. Create the components you need to share across multiple projects. I’ve created the components/hooks and components/ui.
The bit commands are pretty much the same as git. You need to stage the components and then add a meaningful commit to create a snapshot of the staged changes. The Bit harmony doesn’t allow adding of individual files instead it uses directories. So if you try to add single files.
You can avoid this from happening by creating a main file and using all the other files there, Or you can create an individual directory for each component with its required files and use bit add with path to stage them. After that you need to compile the code. You can use the bit status command and bit install command which serve the same purpose as they do in git.
Export the components in the below mentioned format:
bit export company.scope OR bit export //if you have default scope configured
You can see your exported components after you start the bit server with bit start command. You’ll be prompted with a window of bit cloud as shown here:
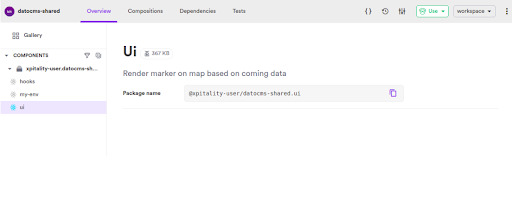
Installing bit components with npm
To start installing and using bit components you need to configure your npm registry to bit. To do that, set the username for npm to the scoped registry. You can find that by clicking on the use option as shown below:
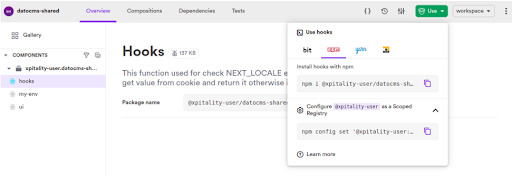
This will set your remote scope registry in your .npmrc file. And now you can install the component by copy-pasting the command from the prompt and use them just as any npm package.
Apply the environment to component
You can apply the environment to all your components or a set of components via the command:
bit env set <pattern or component_id> <compnay.scope/my-env>
You can find the command for your env component in the bit cloud tab.
Alternatively, under the variant section of your workspace.json file choose which components you want to have the custom environment set. Validate that the environment is set for the component by running the show command for the component.
Conclusion:
We demonstrated how to create and share the reusable React components using bit harmony. First, we created the workspace, installed the Bit CLI tool globally, set the npm registry and pulled in the components we added to the workspace. We have also added the configuration to support Tailwind CSS.
You can use bit.dev to implement the shared react components in your team’s code too, so different developers can share and sync it across your different projects and applications.
Originally published by: https://www.inexture.com/react-components-using-bit-harmony/
0 notes
Text
Malicious Plugins Found on 25,000 WordPress Websites: Study
Malicious Plugins Found on 25,000 WordPress Websites: Study
Home › Virus & Threats
Malicious Plugins Found on 25,000 WordPress Websites: Study
By Ionut Arghire on August 29, 2022
Tweet
Researchers at Georgia Institute of Technology have identified malicious plugins on tens of thousands of WordPress websites.
An analysis of nightly backups of more than 400,000 unique web servers has revealed the existence of more than 47,000 malicious plugins installed on…
View On WordPress
0 notes
Text
Join Creative Bridge Cohort Nine - The Creative Industries Accelerator
Applications are now open for cohort nine of Creative Bridge, the accelerator for creatives with early stage ideas.
Creative Bridge Cohort Nine is an accelerator for creatives with early stage ideas, or who are just at the beginning of their ideation process. It has been designed specifically for creatives who want to learn about startup thinking, innovation and digital product development.
Run by CodeBase and funded via Creative Informatics, Creative Bridge is free for successful applicants. It takes place…

View On WordPress
0 notes
Text
idk maybe it's because i care about understanding what my code is doing, or efficiency, or something. but i can't imagine using python in a serious context. i think probably everything that runs on python should be regarded as a fad
147 notes
·
View notes
Note
Fabric is supposedly more optimized than forge. Both of them still have mods being developed for them but imo fabric has more interesting ones and they tend to run a little better
i think i figured it all out! thank you everyone for your help

hehehe square aurora borealis
#dibi#minecraft#by far the most annoying part of the whole affair#is how EVERY MOD WANTS FIVE HUNDRED MORE SUPPORTING MODS#it's like installing skyrim animation mods#i love the paraglider in skyrim that mod is legit a game changer#but installing it is like. okay download seven framework mods. two of those require mods to rewrite the entire codebase#oh one of those mods is gone. find a dodgy mirror reupload#oh the game updated. figure out which version to downgrade your game to so it still works#then reinstall everything#i've more or less given up on modding skyrim bc of it suddenly updating again#but minecraft was easy in the end by comparison#i just needed a LOT of supporting / framework mods huh#i couldn't get bobby to work#i might need to try distant horizons instead#or something...#there seemed to be a few options for the same thing
60 notes
·
View notes
Text
I swear to god if I see anyone doing the "look what modders can do!" bullshit around the mob vote this year I'm gonna fucking lose it
#modders are not required to balance version parity between two entirely different codebases!#modders are not required to go through multiple rounds of design and implementation!!!#modders are not required to make something WORK!!!!!#every minecraft modder I know (myself included) is so fucking tired of this shit#we are not REMOTELY under the same constraints that mojang employees are#and most mojang employees are FORMER MODDERS!!!!!!!!!!#they hate the limitations as much as you do!#they're real people with lives and bills!#stop demanding they overwork themselves for your amusement!
23 notes
·
View notes
Text

How it feels to be a stickler for best practices when the rest of your team is passive-aggressively side eyeing you to rush and just hard-code things
#no!!!! that’s gonna cause PROBLEMS later and then you’ll blame me!!!#there’s already stupid inconsistent stuff in this codebase and I will NOT contribute to this problem
7 notes
·
View notes
Text
Gil Pekelman, Atera: How businesses can harness the power of AI - AI News
New Post has been published on https://thedigitalinsider.com/gil-pekelman-atera-how-businesses-can-harness-the-power-of-ai-ai-news/
Gil Pekelman, Atera: How businesses can harness the power of AI - AI News
.pp-multiple-authors-boxes-wrapper display:none;
img width:100%;
TechForge recently caught up with Gil Pekelman, CEO of all-in-one IT management platform, Atera, to discuss how AI is becoming the IT professionals’ number one companion.
Can you tell us a little bit about Atera and what it does?
We launched the Atera all-in-one platform for IT management in 2016, so quite a few years ago. And it’s very broad. It’s everything from technical things like patching and security to ongoing support, alerts, automations, ticket management, reports, and analytics, etc.
Atera is a single platform that manages all your IT in a single pane of glass. The power of it – and we’re the only company that does this – is it’s a single codebase and single database for all of that. The alternative, for many years now, has been to buy four or five different products, and have them all somehow connected, which is usually very difficult.
Here, the fact is it’s a single codebase and a single database. Everything is connected and streamlined and very intuitive. So, in essence, you sign up or start a trial and within five minutes, you’re already running with it and onboarding. It’s that intuitive.
We have 12,000+ customers in 120 countries around the world. The UK is our second-largest country in terms of business, currently. The US is the first, but the UK is right behind them.
What are the latest trends you’re seeing develop in AI this year?
From the start, we’ve been dedicated to integrating AI into our company’s DNA. Our goal has always been to use data to identify problems and alert humans so they can fix or avoid issues. Initially, we focused on leveraging data to provide solutions.
Over the past nine years, we’ve aimed to let AI handle mundane IT tasks, freeing up professionals for more engaging work. With early access to Chat GPT and Open AI tools a year and a half ago, we’ve been pioneering a new trend we call Action AI.
Unlike generic Generative AI, which creates content like songs or emails, Action AI operates in the real world, interacting with hardware and software to perform tasks autonomously. Our AI can understand IT problems and resolve them on its own, moving beyond mere dialogue to real-world action.
Atera offers Copilot and Autopilot. Could you explain what these are?
Autopilot is autonomous. It understands a problem you might have on your computer. It’s a widget on your computer, and it will communicate with you and fix the problem autonomously. However, it has boundaries on what it’s allowed to fix and what it’s not allowed to fix. And everything it’s allowed to deal with has to be bulletproof. 100% secure or private. No opportunity to do any damage or anything like that.
So if a ticket is opened up, or a complaint is raised, if it’s outside of these boundaries, it will then activate the Copilot. The Copilot augments the IT professional.
They’re both companions. The Autopilot is a companion that takes away password resets, printer issues, installs software, etc. – mundane and repetitive issues – and the Copilot is a companion that will help the IT professional deal with the issues they deal with on a day-to-day basis. And it has all kinds of different tools.
The Copilot is very elaborate. If you have a problem, you can ask it and it will not only give you an answer like ChatGPT, but it will research and run all kinds of tests on the network, the computer, and the printer, and it will come to a conclusion, and create the action that is required to solve it. But it won’t solve it. It will still leave that to the IT professional to think about the different information and decide what they want to do.
Copilot can save IT professionals nearly half of their workday. While it’s been tested in the field for some time, we’re excited to officially launch it now. Meanwhile, Autopilot is still in the beta phase.
What advice would you give to any companies that are thinking about integrating AI technologies into their business operations?
I strongly recommend that companies begin integrating AI technologies immediately, but it is crucial to research and select the right and secure generative AI tools. Incorporating AI offers numerous advantages: it automates routine tasks, enhances efficiency and productivity, improves accuracy by reducing human error, and speeds up problem resolution. That being said, it’s important to pick the right generative AI tool to help you reap the benefits without compromising on security. For example, with our collaboration with Microsoft, our customers’ data is secure—it stays within the system, and the AI doesn’t use it for training or expanding its database. This ensures safety while delivering substantial benefits.
Our incorporation of AI into our product focuses on two key aspects. First, your IT team no longer has to deal with mundane, frustrating tasks. Second, for end users, issues like non-working printers, forgotten passwords, or slow internet are resolved in seconds or minutes instead of hours. This provides a measurable and significant improvement in efficiency.
There are all kinds of AIs out there. Some of them are more beneficial, some are less. Some are just Chat GPT in disguise, and it’s a very thin layer. What we do literally changes the whole interaction with IT. And we know, when IT has a problem things stop working, and you stop working. Our solution ensures everything keeps running smoothly.
What can we expect from AI over the next few years?
AI is set to become significantly more intelligent and aware. One remarkable development is its growing ability to reason, predict, and understand data. This capability enables AI to foresee issues and autonomously resolve them, showcasing an astonishing level of reasoning.
We anticipate a dual advancement: a rapid acceleration in AI’s intelligence and a substantial enhancement in its empathetic interactions, as demonstrated in the latest OpenAI release. This evolution will transform how humans engage with AI.
Our work exemplifies this shift. When non-technical users interact with our software to solve problems, AI responds with a highly empathetic, human-like approach. Users feel as though they are speaking to a real IT professional, ensuring a seamless and comforting experience.
As AI continues to evolve, it will become increasingly powerful and capable. Recent breakthroughs in understanding AI’s mechanisms will not only enhance its functionality but also ensure its security and ethical use, reinforcing its role as a force for good.
What plans does Atera have for the next year?
We are excited to announce the upcoming launch of Autopilot, scheduled for release in a few months. While Copilot, our comprehensive suite of advanced tools designed specifically for IT professionals, has already been instrumental in enhancing efficiency and effectiveness, Autopilot represents the next significant advancement.
Currently in beta so whoever wants to try it already can, Autopilot directly interacts with end users, automating and resolving common IT issues that typically burden IT staff, such as password resets and printer malfunctions. By addressing these routine tasks, Autopilot allows IT professionals to focus on more strategic and rewarding activities, ultimately improving overall productivity and job satisfaction.
For more information, visit atera.com
Atera is a sponsor of TechEx North America 2024 on June 5-6 in Santa Clara, US. Visit the Atera team at booth 237 for a personalised demo, or to test your IT skills with the company’s first-of-kind AIT game, APOLLO IT, for a chance to win a prize.
Want to learn more about AI and big data from industry leaders? Check out AI & Big Data Expo taking place in Amsterdam, California, and London. The comprehensive event is co-located with other leading events including Intelligent Automation Conference, BlockX, Digital Transformation Week, and Cyber Security & Cloud Expo.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.
Tags: Atera, automation, cybersecurity, IT support
#000#2024#Advice#ai#ai & big data expo#ai news#ai tools#alerts#America#amp#Analytics#applications#approach#Artificial Intelligence#atera#automation#autopilot#Big Data#Business#career#CEO#Chat GPT#chatGPT#Cloud#codebase#Collaboration#Companies#comprehensive#computer#conference
0 notes
Text
There's probably a viable pathway into career software development by starting as a QA tester - especially if you demonstrate basic proficiency w like python or javascript (node)
#qa rly just means 'professional software user'#so if yr good on the computer but not necessarily at coding you can probably do it fine#excel experience would prob help too#particularly a lot of like e2e/full integration tests are pretty disconnected from the details of the codebase#like in web stuff its rly abt understanding html structure & ids/class names more than anything to do w js
24 notes
·
View notes
Text
chose a weird time to start learning rust because I can hear all the ongoing C/++ drama in the next room
#computer stuff#i pay attention to it but my codebases are all antiques so the impact C23 has on me is limited
47 notes
·
View notes
Text

#using chatgpt for entire codebases is gonna bite so many companies in the ass#trans#r196#fuck staff#dune
4 notes
·
View notes
Text
what i really want is for tumblr to federate so i can keep following y'all here but see the #emacs tag there. I'd move my main onto another instance to avoid the random terminations.
a girl can dream
#they teased it years ago#i understand that it's hard to adapt an existing live codebase to interoperate with another existing network#but you gotta try#if i had any faith in tumblr inc i would give them a large chunk of my inheritance to make it happen
4 notes
·
View notes
Text
I just noticed an interesting bug for the first time. Apparently, if a link includes "tag" as part of the URL? At least on mobile, Tumblr can ignore the domain to interpret that as an internal link, and take you to whatever comes after that as if it is a Tumblr tag. 🤔
The example that brought this to my attention, when I was double checking that the links were actually working on one reblog:
https://www.makeuseof.com/tag/install-linux-windows-vmware-virtual-machine/
Yeah, getting taken to some fake tag within Tumblr was really not helpful. Very strange behavior that I would not have expected.
(That link is already replaced with one to another tutorial, and I have not yet tried it out with other URLs fitting that pattern or on desktop.)
2 notes
·
View notes