#active directory
Text
Exploring Kerberos and its related attacks
Introduction
In the world of cybersecurity, authentication is the linchpin upon which secure communications and data access rely. Kerberos, a network authentication protocol developed by MIT, has played a pivotal role in securing networks, particularly in Microsoft Windows environments. In this in-depth exploration of Kerberos, we'll delve into its technical intricacies, vulnerabilities, and the countermeasures that can help organizations safeguard their systems.
Understanding Kerberos: The Fundamentals
At its core, Kerberos is designed to provide secure authentication for users and services over a non-secure network, such as the internet. It operates on the principle of "need-to-know," ensuring that only authenticated users can access specific resources. To grasp its inner workings, let's break down Kerberos into its key components:
1. Authentication Server (AS)
The AS is the initial point of contact for authentication. When a user requests access to a service, the AS verifies their identity and issues a Ticket Granting Ticket (TGT) if authentication is successful.
2. Ticket Granting Server (TGS)
Once a user has a TGT, they can request access to various services without re-entering their credentials. The TGS validates the TGT and issues a service ticket for the requested resource.
3. Realm
A realm in Kerberos represents a security domain. It defines a specific set of users, services, and authentication servers that share a common Kerberos database.
4. Service Principal
A service principal represents a network service (e.g., a file server or email server) within the realm. Each service principal has a unique encryption key.
Vulnerabilities in Kerberos
While Kerberos is a robust authentication protocol, it is not immune to vulnerabilities and attacks. Understanding these vulnerabilities is crucial for securing a network environment that relies on Kerberos for authentication.
1. AS-REP Roasting
AS-REP Roasting is a common attack that exploits weak user account settings. When a user's pre-authentication is disabled, an attacker can request a TGT for that user without presenting a password. They can then brute-force the TGT offline to obtain the user's plaintext password.
2. Pass-the-Ticket Attacks
In a Pass-the-Ticket attack, an attacker steals a TGT or service ticket and uses it to impersonate a legitimate user or service. This attack can lead to unauthorized access and privilege escalation.
3. Golden Ticket Attacks
A Golden Ticket attack allows an attacker to forge TGTs, granting them unrestricted access to the domain. To execute this attack, the attacker needs to compromise the Key Distribution Center (KDC) long-term secret key.
4. Silver Ticket Attacks
Silver Ticket attacks target specific services or resources. Attackers create forged service tickets to access a particular resource without having the user's password.
Technical Aspects and Formulas
To gain a deeper understanding of Kerberos and its related attacks, let's delve into some of the technical aspects and cryptographic formulas that underpin the protocol:
1. Kerberos Authentication Flow
The Kerberos authentication process involves several steps, including ticket requests, encryption, and decryption. It relies on various cryptographic algorithms, such as DES, AES, and HMAC.
2. Ticket Granting Ticket (TGT) Structure
A TGT typically consists of a user's identity, the requested service, a timestamp, and other information encrypted with the TGS's secret key. The TGT structure can be expressed as:
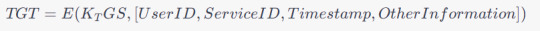
3. Encryption Keys
Kerberos relies on encryption keys generated during the authentication process. The user's password is typically used to derive these keys. The process involves key generation and hashing formulas.
Mitigating Kerberos Vulnerabilities
To protect against Kerberos-related vulnerabilities and attacks, organizations can implement several strategies and countermeasures:
1. Enforce Strong Password Policies
Strong password policies can mitigate attacks like AS-REP Roasting. Ensure that users create complex, difficult-to-guess passwords and consider enabling pre-authentication.
2. Implement Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide multiple forms of authentication. This can thwart various Kerberos attacks.
3. Regularly Rotate Encryption Keys
Frequent rotation of encryption keys can limit an attacker's ability to use stolen tickets. Implement a key rotation policy and ensure it aligns with best practices.
4. Monitor and Audit Kerberos Traffic
Continuous monitoring and auditing of Kerberos traffic can help detect and respond to suspicious activities. Utilize security information and event management (SIEM) tools for this purpose.
5. Segment and Isolate Critical Systems
Isolating sensitive systems from less-trusted parts of the network can reduce the risk of lateral movement by attackers who compromise one system.
6. Patch and Update
Regularly update and patch your Kerberos implementation to mitigate known vulnerabilities and stay ahead of emerging threats.
4. Kerberos Encryption Algorithms
Kerberos employs various encryption algorithms to protect data during authentication and ticket issuance. Common cryptographic algorithms include:
DES (Data Encryption Standard): Historically used, but now considered weak due to its susceptibility to brute-force attacks.
3DES (Triple DES): An improvement over DES, it applies the DES encryption algorithm three times to enhance security.
AES (Advanced Encryption Standard): A strong symmetric encryption algorithm, widely used in modern Kerberos implementations for better security.
HMAC (Hash-based Message Authentication Code): Used for message integrity, HMAC ensures that messages have not been tampered with during transmission.
5. Key Distribution Center (KDC)
The KDC is the heart of the Kerberos authentication system. It consists of two components: the Authentication Server (AS) and the Ticket Granting Server (TGS). The AS handles initial authentication requests and issues TGTs, while the TGS validates these TGTs and issues service tickets. This separation of functions enhances security by minimizing exposure to attack vectors.
6. Salting and Nonces
To thwart replay attacks, Kerberos employs salting and nonces (random numbers). Salting involves appending a random value to a user's password before hashing, making it more resistant to dictionary attacks. Nonces are unique values generated for each authentication request to prevent replay attacks.
Now, let's delve into further Kerberos vulnerabilities and their technical aspects:
7. Ticket-Granting Ticket (TGT) Expiry Time
By default, TGTs have a relatively long expiry time, which can be exploited by attackers if they can intercept and reuse them. Administrators should consider reducing TGT lifetimes to mitigate this risk.
8. Ticket Granting Ticket Renewal
Kerberos allows TGT renewal without re-entering the password. While convenient, this feature can be abused by attackers if they manage to capture a TGT. Limiting the number of renewals or implementing MFA for renewals can help mitigate this risk.
9. Service Principal Name (SPN) Abuse
Attackers may exploit misconfigured SPNs to impersonate legitimate services. Regularly review and audit SPNs to ensure they are correctly associated with the intended services.
10. Kerberoasting
Kerberoasting is an attack where attackers target service accounts to obtain service tickets and attempt offline brute-force attacks to recover plaintext passwords. Robust password policies and regular rotation of service account passwords can help mitigate this risk.
11. Silver Ticket and Golden Ticket Attacks
To defend against Silver and Golden Ticket attacks, it's essential to implement strong password policies, limit privileges of service accounts, and monitor for suspicious behavior, such as unusual access patterns.
12. Kerberos Constrained Delegation
Kerberos Constrained Delegation allows a service to impersonate a user to access other services. Misconfigurations can lead to security vulnerabilities, so careful planning and configuration are essential.
Mitigation strategies to counter these vulnerabilities include:
13. Shorter Ticket Lifetimes
Reducing the lifespan of TGTs and service tickets limits the window of opportunity for attackers to misuse captured tickets.
14. Regular Password Changes
Frequent password changes for service accounts and users can thwart offline attacks and reduce the impact of credential compromise.
15. Least Privilege Principle
Implement the principle of least privilege for service accounts, limiting their access only to the resources they need, and monitor for unusual access patterns.
16. Logging and Monitoring
Comprehensive logging and real-time monitoring of Kerberos traffic can help identify and respond to suspicious activities, including repeated failed authentication attempts.
Kerberos Delegation: A Technical Deep Dive
1. Understanding Delegation in Kerberos
Kerberos delegation allows a service to act on behalf of a user to access other services without requiring the user to reauthenticate for each service. This capability enhances the efficiency and usability of networked applications, particularly in complex environments where multiple services need to interact on behalf of a user.
2. Types of Kerberos Delegation
Kerberos delegation can be categorized into two main types:
Constrained Delegation: This type of delegation restricts the services a service can access on behalf of a user. It allows administrators to specify which services a given service can impersonate for the user.
Unconstrained Delegation: In contrast, unconstrained delegation grants the service full delegation rights, enabling it to access any service on behalf of the user without restrictions. Unconstrained delegation poses higher security risks and is generally discouraged.
3. How Delegation Works
Here's a step-by-step breakdown of how delegation occurs within the Kerberos authentication process:
Initial Authentication: The user logs in and obtains a Ticket Granting Ticket (TGT) from the Authentication Server (AS).
Request to Access a Delegated Service: The user requests access to a service that supports delegation.
Service Ticket Request: The user's client requests a service ticket from the Ticket Granting Server (TGS) to access the delegated service. The TGS issues a service ticket for the delegated service and includes the user's TGT encrypted with the service's secret key.
Service Access: The user presents the service ticket to the delegated service. The service decrypts the ticket using its secret key and obtains the user's TGT.
Secondary Authentication: The delegated service can then use the user's TGT to authenticate to other services on behalf of the user without the user's direct involvement. This secondary authentication occurs transparently to the user.
4. Delegation and Impersonation
Kerberos delegation can be seen as a form of impersonation. The delegated service effectively impersonates the user to access other services. This impersonation is secure because the delegated service needs to present both the user's TGT and the service ticket for the delegated service, proving it has the user's explicit permission.
5. Delegation in Multi-Tier Applications
Kerberos delegation is particularly useful in multi-tier applications, where multiple services are involved in processing a user's request. It allows a front-end service to securely delegate authentication to a back-end service on behalf of the user.
6. Protocol Extensions for Delegation
Kerberos extensions, such as Service-for-User (S4U) extensions, enable a service to request service tickets on behalf of a user without needing the user's TGT. These extensions are valuable for cases where the delegated service cannot obtain the user's TGT directly.
7. Benefits of Kerberos Delegation
Efficiency: Delegation eliminates the need for the user to repeatedly authenticate to access multiple services, improving the user experience.
Security: Delegation is secure because it relies on Kerberos authentication and requires proper configuration to work effectively.
Scalability: Delegation is well-suited for complex environments with multiple services and tiers, enhancing scalability.
In this comprehensive exploration of Kerberos, we've covered a wide array of topics, from the fundamentals of its authentication process to advanced concepts like delegation.
Kerberos, as a network authentication protocol, forms the backbone of secure communication within organizations. Its core principles include the use of tickets, encryption, and a trusted third-party Authentication Server (AS) to ensure secure client-service interactions.
Security is a paramount concern in Kerberos. The protocol employs encryption, timestamps, and mutual authentication to guarantee that only authorized users gain access to network resources. Understanding these security mechanisms is vital for maintaining robust network security.
Despite its robustness, Kerberos is not impervious to vulnerabilities. Attacks like AS-REP Roasting, Pass-the-Ticket, Golden Ticket, and Silver Ticket attacks can compromise security. Organizations must be aware of these vulnerabilities to take appropriate countermeasures.
Implementing best practices is essential for securing Kerberos-based authentication systems. These practices include enforcing strong password policies, regular key rotation, continuous monitoring, and employee training.
Delving into advanced Kerberos concepts, we explored delegation – both constrained and unconstrained. Delegation allows services to act on behalf of users, enhancing usability and efficiency in complex, multi-tiered applications. Understanding delegation and its security implications is crucial in such scenarios.
Advanced Kerberos concepts introduce additional security considerations. These include implementing fine-grained access controls, monitoring for unusual activities, and regularly analyzing logs to detect and respond to security incidents.
So to conclude, Kerberos stands as a foundational authentication protocol that plays a pivotal role in securing networked environments. It offers robust security mechanisms and advanced features like delegation to enhance usability. Staying informed about Kerberos' complexities, vulnerabilities, and best practices is essential to maintain a strong security posture in the ever-evolving landscape of cybersecurity.
12 notes
·
View notes
Text
Exploring the Depths: Active Directory Penetration Testing and the Enigma of Kerberos
Introduction
In the world of cybersecurity, staying one step ahead of potential threats is paramount. To safeguard an organization's sensitive information and network resources, it's crucial to regularly assess vulnerabilities and weaknesses. One potent approach is Active Directory (AD) penetration testing, which is an essential part of assessing and fortifying network security. This article delves into the intricacies of Active Directory penetration testing and the often elusive realm of Kerberos authentication.
Active Directory Penetration Testing: Unearthing Vulnerabilities
Active Directory, the cornerstone of identity management in Windows environments, serves as a centralized repository for user and system information, including authentication data. For cybercriminals, compromising AD can open the doors to a treasure trove of sensitive information. To counter this threat, organizations employ penetration testing to simulate real-world attacks and identify vulnerabilities.
Goals of Active Directory Penetration Testing
Identify Weak Passwords: One of the most common vulnerabilities is weak or easily guessable passwords. Penetration testers aim to uncover users with weak passwords and prompt them to strengthen their credentials.
Discover Misconfigured Permissions: Unauthorized access to resources can result from misconfigured permissions. Penetration testing assesses whether users have permissions that they shouldn't, potentially exposing sensitive data.
Locate Unpatched Systems: Outdated systems are susceptible to known vulnerabilities. Identifying and patching these systems is a critical goal of penetration testing.
Assess Kerberos Authentication: Active Directory relies heavily on Kerberos for secure authentication. Understanding Kerberos is essential for a thorough AD penetration test.
Kerberos: The Protector of Authentication
Kerberos, a network authentication protocol, plays a pivotal role in securing Active Directory environments. Named after the mythological three-headed dog guarding the gates of Hades, Kerberos acts as a guardian for network communication. Understanding how it works is vital for both defenders and attackers.
The Key Concepts of Kerberos
Authentication Tickets: In Kerberos, authentication occurs through tickets. A Ticket Granting Ticket (TGT) is obtained during initial authentication, and this TGT is used to request access to various resources without re-entering credentials.
Principle of Need to Know: Kerberos enforces the principle of "need to know." A user can access only the resources for which they have tickets, reducing the risk of unauthorized access.
Realms and Trust: In a multi-domain environment, Kerberos realms establish trust relationships between domains. Trust enables users from one domain to access resources in another.
Encryption: Kerberos relies on encryption to protect sensitive information, such as passwords and tickets. Encryption keys are generated dynamically during authentication.
Penetration Testing Kerberos: A Delicate Balancing Act
Penetration testing for Kerberos authentication involves a delicate balancing act between assessing security measures and not disrupting normal operations. Here are some critical aspects of Kerberos-focused penetration testing:
1. AS-REP Roasting
AS-REP Roasting is a common attack that exploits weak or vulnerable user accounts. Penetration testers attempt to retrieve Authentication Service (AS) tickets without the need for valid login credentials. This technique targets accounts with pre-authentication disabled, making them vulnerable to brute-force attacks.
2. Pass-the-Ticket Attacks
Pass-the-Ticket attacks involve stealing Ticket Granting Tickets (TGTs) from compromised systems. Attackers can then use these stolen TGTs to gain unauthorized access to other network resources. Penetration testing assesses the organization's ability to detect and defend against such attacks.
3. Golden Ticket Attacks
Golden Ticket attacks involve forging TGTs, effectively granting attackers unlimited access to the domain. Penetration testers may attempt to create Golden Tickets to evaluate the AD's resilience against this advanced attack.
4. Silver Ticket Attacks
Silver Tickets are used for unauthorized access to specific services or resources. A penetration test may focus on creating Silver Tickets to assess the AD's ability to detect and prevent such attacks.
10 notes
·
View notes
Text
Securing Active Directory Accounts
Photo by Andrea Piacquadio on Pexels.com
Active Directory is a directory service that manages user accounts and other resources on a network. It is important to secure Active Directory user accounts to prevent unauthorized access, data breaches, and identity theft. In this blog post, we will describe the step-by-step process to secure Active Directory user accounts using best practices and…

View On WordPress
#active directory#Azure Active Directory#Group Policy#Least privilege#Microsoft#Multi-Factor Authentication
2 notes
·
View notes
Text
For all the time I've spent working with active directory, which self admittedly isn't so long...about a year or two- I've come to realize- I hate Active Directory xD
Just this week I was doing WDS deployments like a noob does, and changing the computer names manually cuz of a small lil woops I did when making the image (causing me to need to change all names manually) and it turns out I now have to:
Leave the domain.
Reset.
Join the domain and rename the PC at the same time.
Reset
Boot and log into the user's profile.
Shutdown.
Deploy the PC to the work area.
Fun in IT.
2 notes
·
View notes
Text
Always On VPN DPC with Intune
Always On VPN DPC with Intune
In the past, I’ve written about PowerON Platforms’ Always On VPN Dynamic Profile Configurator (DPC), a software solution administrators can use to provision and manage Always On VPN client configuration settings using Active Directory and group policy. In addition to streamlining the deployment and management of Always On VPN client settings, DPC has many advanced features and capabilities to…

View On WordPress
#Active Directory#Always On VPN#AOVPN#ConfigMgr#configuration#DPC#Dynamic Profile Configurator#endpoint#endpoint management#endpoint manager#enterprise mobility#GPMC#group policy#Group Policy Management Console#InTune#MEM#MEMCM#Microsoft#Microsoft Endpoint Manager#Mobility#optimizations#otpimization#performance#policy#PowerON Platforms#Proactive Remediation#SCCM#security#systems management#Windows
2 notes
·
View notes
Text
How to create the custom attribute in active directory.
Extend the Active Directory Schema by Adding Custom Attributes... read more

3 notes
·
View notes
Text
(2024-04-23) Breaking The Glass Of Your "Get-Out-Of-Jail-For-Free" AD Account - Introduction (Part 1)
When installing Active Directory (AD), in the first AD domain, the so-called Forest Root AD Domain, an administrator account is created as part of the creation of the AD domain. This also happens in the respective AD domains when adding additional child or tree root AD domains. The (default) administrator account (RID 500) in any AD domain is always a member of the “administrators” group and the…

View On WordPress
0 notes
Text
Windows Server 2025 Active Directory New Features
Windows Server 2025 Active Directory New Features @vexpert #windowsserver2025 #activedirectory #vmwarecommunities #addomain #domaincontroller #homelab #homeserver #windowsserver #windowsserversummit #windowsforest #windowsdomain
Windows Server 2025 contains many great new improvements from previous versions of Windows Server. One of the areas where we are seeing many new features and capabilities introduced is Active Directory, including a new domain functional level and forest functional level. In this post, we will take a deep dive into Windows Server 2025 new Active Directory features in the latest release.
Table of…

View On WordPress
0 notes
Text
Akira ransomware prevention and defense 2024
New Post has been published on https://thedigitalinsider.com/akira-ransomware-prevention-and-defense-2024/
Akira ransomware prevention and defense 2024


EXECUTIVE SUMMARY:
In March of 2023, the first Akira ransomware strain was observed in the wild. Since then, the group has compromised over 100 different organizations, targeting those in the financial, manufacturing, real-estate, healthcare and medical sectors.
Akira operates on a Ransomware-as-a-Service (RaaS) model and typically deploys a double-extortion scheme. This involves exfiltrating sensitive data prior to device encryption and insisting on a ransom in exchange for withholding the data from the group’s TOR leak site.
Most recently, Akira interrupted a U.S. emergency dispatch system, causing a nine-day operational outage. During the outage, dispatchers relied on backup systems. As of the present writing, full system restoration is still a work-in-progress.
About Akira
The group is believed to have taken its name from the 1988 cult anime film of the same name, which depicts biker gangs in a dystopian Tokyo. The Akira ransomware gang is known for use of a retro aesthetic on victims’ sites, reminiscent of the 1980’s green screen consoles.
Cyber security researchers have uncovered evidence linking the Akira group to the notorious Conti ransomware operation. In at least three separate cryptocurrency transactions, Akira criminals appear to have sent the full amount of the ransom payment to Conti-affiliated addresses.
The overlap of cryptocurrency wallets indicates that the individual controlling the address or wallet has either splintered off from the original group, or is working with two different groups simultaneously.
How Akira operates
Akira commonly breaches systems by obtaining unauthorized access to the target organization’s VPNs, as through a compromised username/password combination.
After sneaking in through an endpoint, Akira typically uses any of several methods to acquire permissions that enable lateral network movement.
These methods include orchestrating a mini-dump of the LSASS (Local Security Authority Subsystem Service) process memory, obtaining credentials stored in the Active Directory database and exploiting known vulnerabilities in backup software.
Advanced persistence mechanisms
Akira ordinarily deploys tools and techniques like Remote Desktop Protocol (RDP), Server Message Block (SMB), impacket module wmiexec, and a service manager tool known as nssm.exe, in order to gain persistence within systems.
As is the case among many cyber criminal groups, Akira also attempts to uninstall or disable security defenses, including anti-malware and network monitoring tools.
Beyond that, the group tends to use the runas command (a Windows command-line tool that allows for the execution of scripts, apps…etc., with different user permissions from the currently logged-in user) in order to execute commands.
This, in turn, makes tracking hacker activities more difficult for defenders.
Akira and C2 mechanisms
Most ransomware attackers weaponize a command and control (C2) mechanism to execute activities. The C2 system establishes communication with and exerts control over a compromised machine or network.
The C2 server can potentially be used to manage the ransomware deployment and to initiate the encryption of data on targeted systems. For the purpose of establishing persistent remote access to multiple systems within the network, Akira seems to prefer AnyDesk.
Akira and data exfiltration
Akira uses a number of different tools when it comes to data exfiltration. These include WinRAR, WinSCP, rclone, and MEGA.
After data exfiltration, Akira demands a ransom from victims. In the event that the ransom goes unpaid, the group will leak stolen data on its TOR site, as previously mentioned.
Akira’s encryption tactic
To encrypt a given target’s data, Akira relies on a combination of AES and RSA algorithms. The group will also purge Windows Shadow Volume Copies from devices by running a PowerShell command. For victims, this massively complicates the process of independently restoring systems and recovering encrypted data.
Recommended means of preventing and defending against Akira’s ransomware
1. Address identity and access management.
Enhance access controls. Implement multi-factor authentication (MFA). Akira can gain initial access via unauthorized logins to VPNs through accounts that lack MFA. This seemingly simplistic safeguard can significantly limit the risk of unauthorized access.
2. Store credentials securely.
As noted earlier, Akira deploys a variety of tactics to obtain credentials. These tactics include execution of a mini-dump of the LSASS process memory, retrieving credentials stored in the Active Directory database and leveraging vulnerabilities in backup services.
To that effect, organizations need to take care when it comes to credential management. Credentials should be stored securely, and regularly updated. Backup services must also be appropriately secured.
3. Elevate your patch management protocol.
Akira commonly exploits vulnerabilities in VPN software. Thus, regular patching and updating of software can proactively prevent Akira attacks.
4. Monitor your network like a ninja.
Akira relies on built-in commands and tools to identify an environment’s systems and to learn about the status of target devices. Detect duplicitous behavior by monitoring for unusual network activity.
Your organization should also monitor for data exfiltration. Look for substantial data transfers and unusual network patterns.
5. Secure C2 channels.
Akira uses widely recognized dual-use agents, such as AnyDesk, to establish persistent remote access. Remain vigilant in regards to abnormal remote access activities and fortify Command and Control (C2) channels. This can be of tremendous assistance when it comes to thwarting potential attacks.
6. Secure remote desktop protocol.
Akira frequently employes Remote Desktop Protocol (RDP), using legitimate local administrator user accounts to facilitate lateral movement. Enhancing the security of RDP and staying vigilant for atypical RDP activity can be effective in preventing lateral movement.
7. Implement endpoint protection.
Akira usually attempts to uninstall endpoint protections as a means of evading detection. Deploying robust endpoint protection measures and consistently monitoring for efforts to disable or uninstall such safeguards can also assist with attack prevention and detection.
Related resources
The 10 most dangerous ransomware groups right now – Read article
Secure your data. Explore endpoint security solutions – Learn more
Identity and access management solution free trial – Click here
#2023#2024#access management#Accounts#active directory#Akira#Akira ransomware#Algorithms#anti-malware#apps#Article#attackers#authentication#backup#Behavior#C2#CISO#command#communication#Conti#Conti ransomware#credential#credentials#cryptocurrency#cyber#cyber security#data#data exfiltration#Database#defenders
0 notes
Text
Force a sync from Local AD to Azure AD (or Entra, as it would prefer to be known)
This is a nice, quick and easy one.
If you need to force a sync from Local AD to Azure/Entra outside of the schedule, simply:
On the server with the Azure AD/Entra sync tools, open a Powershell prompt with Admin rights
Enter the command:
Start-ADSyncSyncCycle -PolicyType delta
That should be it, and Local AD will be force-sunc up to Azure/Entra
0 notes
Text
What are YOU looking at?
youtube
View On WordPress
0 notes
Text
Microsoft Intune Cloud PKI and Certificate Templates
Microsoft recently announced the general availability of its new PKI-as-a-Service platform called Microsoft Intune Cloud PKI. With Intune Cloud PKI, administrators create certification authorities (CAs) to issue and manage user and device authentication certificates for Intune-managed endpoints. Cloud PKI also provides hosted Authority Information Access (AIA) and Certificate Revocation List…

View On WordPress
#Active Directory#Active Directory Certificate Services#AD#AD CS#ADCS#AIA#authentication#CDP#certificate#certificate authority#certificate template#certificates#Certification Authority#Cloud PKI#CRL#encryption#endpoint manager#InTune#Intune Cloud PKI#MEM#Microsoft#Microsoft Endpoint Manager#Microsoft Intune Cloud PKI#NDES#Network Device Enrollment Service#PKI#public key infrastructure#SCEP#security#Simple Certificate Enrollment Protocol
0 notes
Text
She dom on my ain til I admin
0 notes
Text
Active Directoryサーバの再構築
ジャンクかき集めのCF-T4を使って、今稼働中のActive Directoryサーバを再構築するログ。
OSはDebian bookwormで、最小構成のセットアップからスタート。
インストールパッケージの選択は、一旦すべてのチェックを外して実行。
OSセットアップ完了後に最低限のパッケージをインストール。
apt update && apt upgrade && apt install -y sudo vim openssh-server
SSHを鍵認証でセットアップしたけど、公開鍵のファイル名変更を忘れて、ちょっとハマった。
mv ~/.ssh/id_rsa.pub ~/.ssh/authorized_keys
Dockerでコンテナ環境を整える予定だったけど、Dockerの必須要件が64bitだったので断念。
クライアントのDockerでコンテナを作ったあと、chroot環境に展開して行く方針に変更。
と思って、試しにdebianの公式リポジトリから、aptで叩いてみたら、普通にインストールできた・・・
apt install -y docker.io docker-compose
0 notes