#Endpoint Protection Platforms Market
Text
Endpoint Protection Platforms Market Size Worth USD 6.91 Billion in 2030
The global Endpoint Protection Platforms (EPP) market size reached USD 3.33 Billion in 2021 and is expected to register a revenue CAGR of 8.4% during the forecast period, according to latest analysis by Emergen Research. Rise in trend of Bring Your Own Device (BYOD) and surge in incidence of cyberattacks are crucial factors driving market revenue growth.
0 notes
Text
#Endpoint Protection Platforms Software Market Size#Endpoint Protection Platforms Software Market Scope#Endpoint Protection Platforms Software Market Trend#Endpoint Protection Platforms Software Market Growth
0 notes
Text
How Does Walmart Product API Data Extraction Enhance Business Decision-Making
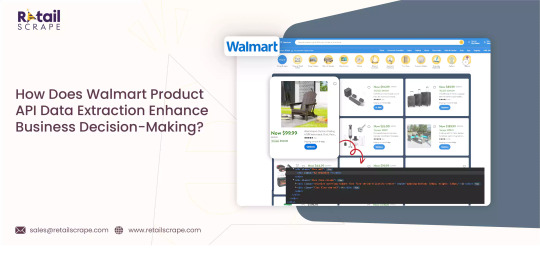
Have you heard about Walmart API data and its pivotal role in today's data-driven business landscape? In this digital age, where information is critical, accessing and analyzing data from retail giants like Walmart can provide invaluable insights for businesses. Walmart product API data extraction is a gateway to a treasure trove of information about products, prices, sales trends, and customer behavior.
Walmart data scraping involves collecting this valuable information from the Walmart website using automated tools and techniques. This process allows businesses to gather comprehensive data about Walmart's vast product catalog, pricing strategies, customer reviews, and more. By leveraging retail data scraping services, businesses can gain a competitive edge by monitoring market trends, analyzing competitor pricing, and optimizing their product offerings.
Furthermore, Walmart's scraping product API offers a more structured and efficient way to access data than traditional web scraping methods. Through the API, developers can programmatically retrieve specific data points in a standardized format, streamlining the data extraction process and enabling real-time updates.
Understanding how to scrape Walmart data and harness Walmart's API capabilities can empower businesses to make data-driven decisions, enhance their market intelligence, and stay ahead of the competition in the dynamic retail landscape. In this article, we will delve deeper into the intricacies of scraping Walmart data and explore the vast potential of Walmart's API for businesses.
Understanding API Data and Its Relevance to Business
API data, or Application Programming Interface data, refers to the information and functionalities that can be accessed and exchanged between different software applications through APIs. APIs serve as intermediaries that allow different systems to communicate and interact with each other seamlessly.
In the business context, Walmart product API data facilitates integration and interoperability between various software platforms and systems used within an organization. Allowing different applications to share data and functionality enables businesses to streamline operations, automate processes, and enhance efficiency.
Working Principles of API Data
The working principles of scraping API data involve leveraging the functionalities of APIs to extract relevant information from various sources in a structured and automated manner. This process typically follows these steps:
Authentication: Access to API data often requires authentication to ensure secure access to protected resources. It involves obtaining API keys or tokens and authenticating requests using standard authentication mechanisms such as OAuth.
Endpoint Discovery: Identify the API endpoints that contain the data you want to scrape. These endpoints represent specific resources or functionalities the API exposes and define the URLs or URIs to access the data.
Request Construction: Construct HTTP requests to access the desired data from the API endpoints. It specifies the HTTP method (e.g., GET, POST), required parameters or query strings, and headers such as authentication tokens.
Data Retrieval: Send the constructed requests to the API endpoints and retrieve the response data. The response typically contains the requested information in a structured data format such as JSON or XML.
Data Parsing: Parse the response data to extract the relevant information you want to scrape. It involves navigating the JSON or XML structure and extracting specific data fields or elements using parsing techniques such as XPath or JSONPath.
Data Storage: Store the scraped data in a structured format such as a database, CSV file, or spreadsheet for further analysis or processing. Ensure that the data storage mechanism aligns with your requirements for accessibility, scalability, and data integrity.
Error Handling: Implement error handling mechanisms to handle exceptions or errors that may occur during the scraping process. It includes gracefully handling HTTP status codes, connection errors, rate limiting, and other potential issues.
By following these principles, businesses can effectively scrape data from APIs, collect valuable insights, and leverage the information available through API endpoints for various purposes, such as market research, competitive analysis, and business intelligence.
For example, businesses can use APIs to integrate customer relationship management (CRM) systems with marketing automation platforms, enabling them to synchronize customer data, track interactions, and automate marketing campaigns. Similarly, APIs can connect e-commerce platforms with inventory management systems, enabling real-time product availability, pricing, and order updates.
Overall, e-commerce web scraping empowers businesses to effectively leverage the capabilities of different software applications and systems, enabling them to improve collaboration, enhance productivity, and deliver better customer service. It is vital in driving digital transformation and innovation across various industries, enabling businesses to stay competitive and adapt to evolving market trends and customer needs.
Role of Walmart Product API Data Extraction to Enhance Business Decision-Making
The role of Walmart data collection in enhancing business decision-making is pivotal. By tapping into the API's information, businesses can gain valuable insights into market dynamics, competitor strategies, and customer behavior. Analysis of this data empowers businesses to make informed decisions across multiple facets of operations. From market analysis and inventory management to competitive intelligence and marketing optimization, Walmart's Product data scraping services offer a treasure trove of data that can be leveraged to drive strategic initiatives. By utilizing this data effectively, businesses can stay ahead of trends, optimize resource allocation, and ultimately enhance their competitive position in the marketplace.
Gathering Walmart Data via Web Scraping
Utilizing web scraping for gathering data offers a more straightforward approach than utilizing specialized programs like the Walmart Data Extractor. The process begins with web scraping, where the company identifies a website with a layout resembling the target site, such as Walmart's product page. Ensuring a fast response time from the website is essential, and browsers supporting web scraping, like Google Chrome, are preferred.
Following this, software is developed for scraping, typically using languages like Python, Perl, Ruby, or PHP. Python is popular due to its cross-platform compatibility and readability. This software sends requests to the target website, retrieves desired data and saves it for further analysis or reporting. Remember that some web scraping technologies may necessitate additional software installation, such as Python, for optimal functionality.
Scraping Walmart Data Using Python
We are explaining the steps to scrape Walmart data using Python.
Obtain API Key: Sign up for Walmart's Developer Portal and obtain an API key to access their data.
Install Required Libraries: Install the necessary Python libraries for working with APIs, such as Requests.
pip install requests
Import Libraries: Import the required libraries into your Python script.
Handle Pagination (if needed): If the API response is paginated, handle pagination by iterating through multiple pages of results.
Extract Desired Information: Extract the relevant information from the API response, such as product names, prices, and ratings.
Conclusion
Walmart's Product scraping API offers businesses a powerful means of accessing and analyzing a wealth of product information on the platform. By harnessing this API, businesses can efficiently retrieve product names, prices, ratings, and more data, enabling them to gain valuable insights into market trends, competitor offerings, and consumer preferences. This data can inform strategic decision-making, enhance pricing strategies, optimize inventory management, and drive overall business growth. With proper implementation and utilization, Walmart Product API data extraction empowers businesses to stay competitive, make informed decisions, and capitalize on opportunities in the ever-evolving retail landscape.
UnlUnlock the potential of data-driven decisions through our Retail Scrape Company. Harness consumer behavior insights, refine pricing strategies, and outpace rivals with live retail data scraping. Elevate your enterprise with our full-range pricing optimization and strategic decision support. Connect today to transform your retail endeavors and amplify profits!
know more :
https://www.retailscrape.com/walmart-product-api-data-extraction-enhance-business.php
#WalmartProductAPIData#WalmartProductAPIDataExtraction#WalmartDataScraping#Walmart'sProductScrapingAPI#ScrapeWalmartData
0 notes
Text
Allot Ltd.: Unraveling Competitive Landscape
Allot Ltd. stands as a frontrunner in the realm of network intelligence and security solutions, dedicated to empowering service providers and enterprises with innovative technologies. With a keen eye on the competitive landscape, we offer insights into our competitors while highlighting our unique value proposition.
Delving into Allot Ltd.
Allot Ltd. is a renowned provider of network intelligence and security solutions, catering to the evolving needs of service providers and enterprises worldwide. Our comprehensive suite of products encompasses cutting-edge technologies designed to enhance network performance, optimize user experience, and mitigate security threats.
Our Product Portfolio
Our product portfolio encompasses a diverse range of solutions tailored to address the multifaceted challenges faced by modern networks:
Allot Secure: A holistic security platform that safeguards networks and endpoints against advanced cyber threats, including malware, ransomware, and phishing attacks.
Allot Smart: Leveraging advanced analytics and machine learning algorithms, Allot Smart enables service providers to optimize network performance, improve quality of service, and enhance subscriber experience.
Allot Protect: Designed to meet the unique needs of enterprise customers, Allot Protect delivers comprehensive security solutions to protect critical assets, safeguard sensitive data, and ensure regulatory compliance.
Allot Insight: Providing real-time visibility into network traffic and user behavior, Allot Insight empowers service providers and enterprises to make informed decisions, identify emerging trends, and optimize resource allocation.
Analyzing Allot Ltd.'s Competitors
Competitive Landscape
Allot Ltd competitive market landscape characterized by rapid technological advancements and evolving customer demands. Our key competitors include:
Cisco Systems: A global leader in networking and cybersecurity solutions, Cisco Systems offers a comprehensive portfolio of products and services catering to enterprises and service providers.
Palo Alto Networks: Known for its innovative approach to cybersecurity, Palo Alto Networks provides next-generation firewall solutions, advanced threat detection, and cloud security services.
Netskope: Specializing in cloud security, Netskope offers a range of solutions designed to secure cloud applications, data, and infrastructure against cyber threats.
0 notes
Text
Mobile Threat Defence Market Landscape: Trends, Drivers, and Forecast (2023-2032)
It is anticipated that between 2023 and 2030, the worldwide Mobile Threat Defence Market will expand at a compound annual growth rate (CAGR) of 26.50%. From USD 2154.8 million in 2022, the market is projected to be worth USD 14129.6 million by 2030.
Mobile Threat Defense (MTD) market refers to the industry and technologies focused on protecting mobile devices such as smartphones, tablets, and other endpoints from security threats and vulnerabilities. This market has grown significantly due to the increasing use of mobile devices in corporate environments and the rising sophistication of cyber threats targeting these devices. Mobile Threat Defense solutions typically include software that offers protection against a variety of threats, such as malware, phishing attacks, network exploits, and application vulnerabilities. These solutions may also provide features such as risk assessment, incident response, and compliance enforcement. The demand for MTD solutions is driven by the need for businesses to secure their mobile workforce, enforce security policies, and protect sensitive corporate data accessible from mobile devices. As mobile technology evolves and integrates more deeply into business operations, the MTD market continues to expand, adapting to new threats and compliance requirements.
These threats include malware, phishing attacks, network attacks, and malicious apps. MTD technologies often incorporate machine learning algorithms to analyze and predict threat patterns, provide real-time defense, and ensure secure access to corporate resources. Additionally, these solutions may offer features like vulnerability assessment, data protection, and compliance management. The growth of the MTD market is propelled by the widespread adoption of mobile technology, the increasing sophistication of cyber threats, and the need for robust regulatory compliance across various industries.
Mobile Threat Defence Market Trends-
Integration with Enterprise Mobility Management (EMM) and Unified Endpoint Management (UEM): There is a growing trend towards the integration of MTD solutions with broader enterprise mobility management and unified endpoint management platforms. This integration allows organizations to have a more comprehensive approach to endpoint security, encompassing not only mobile devices but also other endpoints within the network.
AI and Machine Learning: Artificial intelligence (AI) and machine learning (ML) are increasingly being used to enhance MTD solutions. These technologies help in the automation of threat detection and response processes, making them more efficient and effective at identifying and mitigating novel and sophisticated attacks.
Focus on Zero Trust Security Models: As the traditional network perimeter dissolves with the rise of remote work and cloud-based resources, there is a shift towards Zero Trust security models, which assume that no user or device is trusted by default. MTD solutions are evolving to support Zero Trust architectures by continuously validating every stage of digital interaction.
Regulatory Compliance: With stringent regulations like GDPR and CCPA, organizations are under pressure to ensure that their mobile security practices comply with legal standards. MTD solutions are increasingly including features that help organizations meet these regulatory requirements, particularly concerning data protection and privacy.
Rise of Phishing Attacks on Mobile: Mobile phishing attacks are becoming more common and sophisticated, prompting MTD solutions to focus more on detecting and preventing such threats, which often bypass traditional email filters and are delivered via messaging apps and social media platforms.
5G and IoT Security Concerns: The rollout of 5G networks and the expansion of the Internet of Things (IoT) create new security challenges, particularly in terms of larger attack surfaces and the potential for increased attack speeds. MTD providers are adapting their solutions to better protect devices connected to these faster, more complex networks.
User Education and Awareness: Alongside technological solutions, there is a trend towards enhancing user education and awareness about mobile threats. By educating users on best practices for mobile security, organizations can reduce the risk posed by human error and insider threats.
Key Players-
Cisco Systems
SAP SE
Broadcom, Inc.
VMware
Citrix Systems
Kaspersky Labs
Ivanti
Micro Focus
ZOHO
SolarWinds
Zimperium
Matrix42
Sophos
BlackberryEsper
More About Report- https://www.credenceresearch.com/report/mobile-threat-defence-market
Segmentation
By Security Threat Type:
Malware Protection
Phishing Protection
Data Loss Prevention (DLP)
Network Security
App Security
Device Security
By Deployment Model:
Cloud-based
On-Premises
Hybrid
Mobile Threat Defence Market Competitive Analysis-
Competitive Strategies
Integration and Ecosystem Expansion: Many MTD vendors are focusing on integrating their solutions with broader security and IT management ecosystems. This includes partnerships with UEM, cloud security, and identity management providers to offer a more holistic security approach.
Advanced Technology Utilization: Leading players are increasingly leveraging AI and machine learning to enhance their threat detection and response capabilities. This technology helps in predicting and mitigating threats more efficiently.
Focus on Regulatory Compliance: Vendors are tailoring their offerings to help enterprises meet specific regulatory requirements, which is a key selling point for industries such as finance and healthcare.
Customer and Industry Specific Solutions: Providers often develop specialized solutions tailored to the needs of specific industries or customer segments, offering customized security protocols and compliance assistance.
Market Dynamics
Rising Threat Levels: As the level of threats increases, particularly with sophisticated phishing and zero-day attacks, MTD solutions need to continuously evolve, driving competition based on technological innovation.
Adoption of Remote Work: The shift to remote work has expanded the use of mobile devices in business operations, necessitating robust MTD solutions and driving market growth.
5G Deployment: The deployment of 5G technology is anticipated to increase the attack surface for mobile devices due to higher connectivity and device density, pushing MTD providers to innovate further.
Consumer Awareness: As awareness of mobile threats grows, businesses are more inclined to invest in comprehensive solutions, influencing MTD vendors to differentiate their offerings through better user experience and enhanced security features.
Browse the full report – https://www.credenceresearch.com/report/mobile-threat-defence-market
Browse Our Blog : https://www.linkedin.com/pulse/mobile-threat-defence-market-key-industry-dynamics-analysis-singh-v1czf
Contact Us:
Phone: +91 6232 49 3207
Email: [email protected]
Website: https://www.credenceresearch.com

0 notes
Text
Social Media Security Market: Forthcoming Trends and Share Analysis by 2032
Social Media Security Market Size Was Valued at USD 1412 Million in 2023 and is Projected to Reach USD 5378.12 Million by 2032, Growing at a CAGR of 16.02 % From 2024-2032.
A crucial component of internet safety is social media security, which includes tactics and controls meant to shield people and institutions from the constantly changing threats connected to using social networking sites. Social media usage is increasing, which raises the possibility of a number of risks, such as phishing scams, identity theft, privacy violations, and cyberbullying.
The market for social media security has grown significantly in recent years due to growing worries about cyber attacks, data breaches, and online privacy on social media platforms. Social media security solutions are in more demand as more individuals and organizations realize how important it is to protect their digital presence from unwanted activity.
Get Full PDF Sample Copy of Report: (Including Full TOC, List of Tables & Figures, Chart) @
https://introspectivemarketresearch.com/request/3987
Updated Version 2024 is available our Sample Report May Includes the:
Scope For 2024
Brief Introduction to the research report.
Table of Contents (Scope covered as a part of the study)
Top players in the market
Research framework (structure of the report)
Research methodology adopted by Worldwide Market Reports
Leading players involved in the Social Media Security Market include:
Symantec (United States)
CA Technologies(United States)
ZeroFOX (United States)
RiskIQ (United States)
SolarWinds(United States)
Proofpoint (United States)
LookingGlass Cyber Solutions (United States)
KnowBe4 (United States)
Centrify (United States)
Social Hub (United States)
Brandle (United States)
Moreover, the report includes significant chapters such as Patent Analysis, Regulatory Framework, Technology Roadmap, BCG Matrix, Heat Map Analysis, Price Trend Analysis, and Investment Analysis which help to understand the market direction and movement in the current and upcoming years.
If You Have Any Query Social Media Security Market Report, Visit:
https://introspectivemarketresearch.com/inquiry/3987
Segmentation of Social Media Security Market:
By Solution
Monitoring
Threat Intelligence
Risk Management
By Security
Web Security
Application Security
Endpoint Security
Network Security
Cloud Security
By End Use Industry
BFSI
Healthcare and life sciences
Manufacturing
Telecom & IT
Media and entertainment
Others
An in-depth study of the Social Media Security industry for the years 2023–2030 is provided in the latest research. North America, Europe, Asia-Pacific, South America, the Middle East, and Africa are only some of the regions included in the report's segmented and regional analyses. The research also includes key insights including market trends and potential opportunities based on these major insights. All these quantitative data, such as market size and revenue forecasts, and qualitative data, such as customers' values, needs, and buying inclinations, are integral parts of any thorough market analysis.
Market Segment by Regions: -
North America (US, Canada, Mexico)
Eastern Europe (Bulgaria, The Czech Republic, Hungary, Poland, Romania, Rest of Eastern Europe)
Western Europe (Germany, UK, France, Netherlands, Italy, Russia, Spain, Rest of Western Europe)
Asia Pacific (China, India, Japan, South Korea, Malaysia, Thailand, Vietnam, The Philippines, Australia, New Zealand, Rest of APAC)
Middle East & Africa (Turkey, Bahrain, Kuwait, Saudi Arabia, Qatar, UAE, Israel, South Africa)
South America (Brazil, Argentina, Rest of SA)
Key Benefits of Social Media Security Market Research:
Research Report covers the Industry drivers, restraints, opportunities and challenges
Competitive landscape & strategies of leading key players
Potential & niche segments and regional analysis exhibiting promising growth covered in the study
Recent industry trends and market developments
Research provides historical, current, and projected market size & share, in terms of value
Market intelligence to enable effective decision making
Growth opportunities and trend analysis
Covid-19 Impact analysis and analysis to Social Media Security market
If you require any specific information that is not covered currently within the scope of the report, we will provide the same as a part of the customization.
Acquire This Reports: -
https://introspectivemarketresearch.com/checkout/?user=1&_sid=3987
About us:
Introspective Market Research (introspectivemarketresearch.com) is a visionary research consulting firm dedicated to assist our clients grow and have a successful impact on the market. Our team at IMR is ready to assist our clients flourish their business by offering strategies to gain success and monopoly in their respective fields. We are a global market research company, specialized in using big data and advanced analytics to show the bigger picture of the market trends. We help our clients to think differently and build better tomorrow for all of us. We are a technology-driven research company, we analyze extremely large sets of data to discover deeper insights and provide conclusive consulting. We not only provide intelligence solutions, but we help our clients in how they can achieve their goals.
Contact us:
Introspective Market Research
3001 S King Drive,
Chicago, Illinois
60616 USA
Ph no: +1 773 382 1049
Email: [email protected]
#Social Media Security#Social Media Security Market#Social Media Security Market Size#Social Media Security Market Share#Social Media Security Market Growth#Social Media Security Market Trend#Social Media Security Market segment#Social Media Security Market Opportunity#Social Media Security Market Analysis 2023
0 notes
Text
The Best Option for Secure Business Messaging Is Troop Messenger
Leave enough space for your business to grow. Provide it at any time and from any location. To guarantee flawless and totally secure business communication, check out Troop Messenger business Chat. Check out Troop Messenger, the best corporate instant messaging solution on the market with regard to data security, monitored and secured entrance protocol, ease of use, and intellectual property ownership, among many other features. We specifically designed this business chat software with you in mind. Take pleasure in using Troop Messenger, the professional chat application.
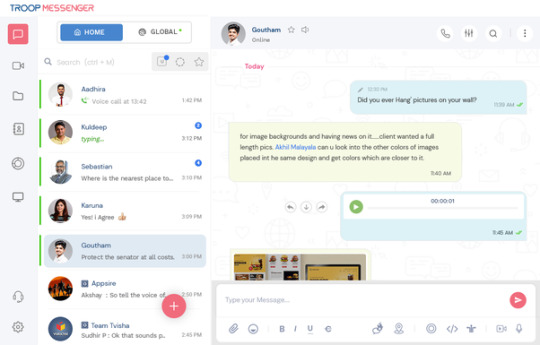
Success in the fast-paced corporate environment of today depends on teamwork and efficient communication. Presenting Troop Messenger, a cutting-edge instant messaging platform created to improve teamwork and communication in a variety of business contexts. Troop Messenger has emerged as the industry standard for workplace chat thanks to its wide range of features designed to facilitate smooth communication.
What is Troop Messenger?
Troop Messenger is a single, secure digital platform that facilitates communication between several departments or teams. In addition to many other time-saving productivity collaboration capabilities, it is a solution made to enable secure communications for Intelligence Agency Communication Solutions through messaging, phone, conference, and share screen.
On-premise Chat Server
Store your private and confidential call and conversation data inside your data centers using the highly secure and readily deployable on-premise service paradigm! We developed this self-hosted collaboration solution with chat server that is compatible with the intranet to facilitate seamless workplace communication.
Why Choose On-Premise/Troop-GRIT?
Troop-GRIT is the Troop Messenger team collaboration application's on-premise Chat Server edition. Having said that, in order to prevent third parties from accessing the application—whether over the public internet or another channel—you can install the self-managed Troop-GRIT on your local or on-premise servers.
Empowering Collaboration Across Industries
Troop Messenger caters to diverse industries, offering tailored solutions to meet specific collaboration needs. Here's how it benefits various sectors:
1. Defence: We understand the unique challenges you face to protect your critical data. Therefore we have leveraged a thought-out military messaging solution that comes with the best possible benefits. Bind and protect your communication untouched by any intruders with the defense collaboration software, Troop Messenger. Feel secure with this messaging app for defense, with the following privileges.
Troop Messenger for your C3 systems Command-Control-Communication
With the help of this Military Grade Messaging system, you can effortlessly carry out your complex C3 functions across all endpoints and monitor friendly, neutral, and enemy ships, planes, weapons, and soldiers. Utilize these resources to expedite your mission-critical operations with this ongoing defense application.
Bring your Ministry of Defense (MoD), departmental hierarchies, and military personnel to convey mission-critical controls.
focuses on the fundamental elements of military communication and coordination systems
Military-grade, self-hosted communication that keeps private talks in your data centers.
2. Government: A resourceful cum end-to-end encrypted messaging app for Government sectors, designed to sort all your complicated work in one place shrinking the latency issues. HD Audio/ Video calls & messaging in one on one or groups, video conferences, secure file sharing, and among others are some of the features of this secure chat application.
Makes Every System of Government Communicate Securely!
Federal, Devolved, Semi-Presidential, Presidential, Parliamentary Republics, and more! With its features, Troop Messenger, the government's messaging application, streamlines and organizes your dispersed communication and collaboration.
Through end-to-end encrypted chat, phone, and collaboration features, you can effectively communicate the formal aspects of your interpersonal, group, and mass communication with this dependable and safe government mobile messaging solution.
Increase the agility and delivery of your ministries and departments by digitizing your operations. With its end-to-end encrypted communication capabilities and self-managed service models, it enables you to operate in a secure and private manner.
Through chat, calls, audio-video conferencing, file sharing, and other features, Troop Messenger keeps you informed, involved, and connected for all sizes and types of government organizations—local, state, or federal.
3. Politics: Share party news, official announcements, latest activity updates of the party, all across one platform through customized political campaign software! Keep your party associates connected all the time through this Android and iOS voter management apps!
Provides secure collaboration for the political parties with:
Messaging, calling, audio-video conferencing, live-telecasting, voter participation on social media, and more! For Political Party Leaders, it's all in one safe political collaboration tool. Bring people, cadre, and party activists to this instant messaging app for political parties for optimal and well-organized party discussions. Spread your political campaign with the features and facilities of:
Secured Group Chats
Bulk Messaging
Audio-Video Conferencing
Live Feed across social media
Constituency-based chat facility
Posters/Gallery
Update party news and more
4. Ministry of Defence: Troop Messenger facilitates transparent MOD communication services to convey the policy framework of MOD to the armed forces to carry out their responsibilities. You can bring all entities onto this DOD mobile application to deliver the information securely.
Troop Messenger - Messaging Platform for Ministry of Defence
Highlights of the DOD messaging services:
Highly secured, Instant messaging and Internal Team collaboration application.
Built for Defence, Government, Law Enforcement Agencies, Aviation, BFSI, Large enterprises etc.
Organizes Virtual Meetings with audio/video calls, share & access remote screens.
A comprehensive File & Folder Management platform.
Multi-device & platform compatibility for enhanced user reach. Integrate with your existing in-house applications or third-Party Platforms.
Manages your day-to-day work communication and their updates with organized groups.
Shares ideas, work deliverables, and project updates through images, videos & files.
100+ features which can transform & enhance workplace productivity.
5. Army: Initiate Chat, Calls, remote screen access, conferencing, and more within this army chat app! Secure your sensitive army information with the world’s best security protocols and practices that combines the Double Ratchet algorithm, Pre-keys, and a triple Elliptic-curve Diffie–Hellman (3-DH) handshake, Curve25519, AES-256, HMAC-SHA256 as primitives.
Purpose-Built for Army’s land-based strategic and tactical communications
Our army-grade messaging application is a sophisticated digital system made to fit the entire structure of army within it.
Synchronizes with your independent and robust communication networks.
Collaborative and user-friendly unified and secure mobile application for army
Brings your command control systems and hierarchies to a single communication interface
Self-hosted chat application for army that helps retain confidential conversations in your data centers.
6. Navy: High-trust and uniquely determined collaboration features for the seaborne branch! Integrate our end-to-end encrypted navy messaging system, the Troop Messenger, into your communication ecosystem; to securely chat, call, collaborate and meet.
Deploy the self-hosted, have secured navy communications.
Run Troop Messenger, the self-hosted messenger, internally on your local datacenters and over your air-gapped networks to secure the conversations of your operational commands. This navy chat solution makes your army personnel to:
Manage and maintain the application
Have full control over user data and files
Route messages and calls through your servers and databases
scale the application to the needs.
7. Air Force: Reach the skies with secured Command-Control Instructions from the Base! We have incorporated highly secured collaborative tools for Airforce, such as chat, calling, audio-video conferencing, screen sharing, and others. Use it while conversating daily interactions, during natural disasters and internal disturbances, and for your other critical missions.
Defend the nation by safeguarding your air communication with Troop Messenger.
How can Troop Messenger help you?
Integrate this Air Force Instant Messenger in your military networks to provide reliable communications to your Airmen and Airwomen.
Works as an instant messaging app for Air Force.
Use it in your deployed locations for efficient information sharing.
Integrate into your C3 Systems to track all end-points of the mission.
Burnout chat erases Air Force message when the set duration on it expires
It’s a platform to conduct your operational discussions.
8. Defence Manufacturing: Our advanced Defence Manufacturing messaging system, Troop Messenger, help you exchange secure and classified conversations while you develop a comprehensive production infrastructure to produce weapons, systems, platforms, and military equipment required for defence across your Defence manufacturing industries.
Who can use this Military-Grade Messaging System?
Use it across State-Run, New State, Private Defence Manufacturing Companies, and others to secure in-office work conversations. Commission this chat application for Arms industry within your Department of Defence Production:
services headquarters,
regulatory authorities,
inter-services organisations,
technical directorates,
production establishments,
R&D centres and others.
9. Courts And Justice: Troop Messenger is a video conferencing and instant messaging platform made for the courts of India, in India. A single, integrated, and independent judiciary needs a unified communication system to bring seamless collaboration to its judges, lawyers, court staff, etc. Livestream court proceedings, upload case files to a secure file repository, transmit court orders through encrypted lines, and do much more with this court management software.
Virtual Communication Support for Virtual Courts
Courts need secure video solutions for virtual courts, such as Troop Messenger. Start conversating with the wide range of features and facilities available within this secure communication for court and justice department that helps have seamless virtual court proceedings, such as,
Hearing arguments.
Proceedings of remand cases.
Digital storage of electronic evidence management
Separate links for open and private court hearings.
10. Law Enforcement Agencies: Hinge on this law enforcement app to bring the hierarchies of your police system onto the unified communication platform to pass on the orders of law enforcement to the police on duty to maintain public safety and social order and prevent crime across your jurisdiction.
Secure Messaging Web and Mobile App for Police
A compliant messaging system for Police, Troop Messenger, is the best platform designed to solve the complexity of the communication process. With the help of advanced, safe, and secure features and intense collaboration facilities, it shall not allow classified data to fall into the hands of unauthorized persons.
Accessibility and Security:
The software application supports various deployments models such as SaaS, On-Premise, and other unique deployments required by agencies on their premises.
The software can be configured and customized at all locations.
Troop Messenger is a well-equipped encrypted chat app that secures your information end-to-end.
Operate and maintain by self.
This cross-platform can be installed in various systems in PCs, Mobile phones, and browsers.
The files such as images, videos, and other data can be accessed anytime, anywhere.
11. Intelligence Agencies: Use this modern, agile, and sophisticated instant messenger for intelligence in your country’s internal and external intelligence agencies to encrypt and safeguard the flow of critical conversations while protecting your nation against domestic and foreign threats.
Chat App for Intelligence Agencies
Highly secured, Instant messaging and Internal Team collaboration application.
Built for Defence, Government, Law Enforcement Agencies, Aviation, BFSI, Large enterprises etc.
Organizes Virtual Meetings with audio/video calls, share & access remote screens.
A comprehensive File & Folder Management platform.
Multi-device & platform compatibility for enhanced user reach. Integrate with your existing in-house applications or third-Party Platforms.
Manages your day-to-day work communication and their updates with organized groups.
Shares ideas, work deliverables, and project updates through images, videos & files.
100+ features which can transform & enhance workplace productivity.
12. IT and Software Development: In the fast-paced world of IT and software development, effective collaboration is paramount for project success. Troop Messenger facilitates real-time communication among developers, testers, and project managers, enabling agile development practices and accelerating time-to-market.
13. Healthcare: In the healthcare sector, timely communication can be a matter of life and death. Troop Messenger provides secure messaging channels compliant with HIPAA regulations, enabling healthcare professionals to exchange sensitive patient information securely while collaborating on patient care.
14. Education: In the realm of education, seamless communication between educators, administrators, and students is essential for academic success. Troop Messenger serves as a virtual classroom, enabling educators to conduct lectures, share resources, and engage with students in real time, regardless of physical distance.
15. Finance and Banking: Security and compliance are paramount in the finance and banking industry. Troop Messenger offers end-to-end encryption and compliance features, ensuring secure communication among financial professionals while facilitating collaboration on transactions, compliance tasks, and risk management.
Features that Propel Team Collaboration
Troop Messenger offers a plethora of features geared towards facilitating smooth communication and collaboration among team members. Here's a closer look at some of its standout features:
Instant Messaging: With Troop Messenger, exchanging messages in real-time has never been easier. Whether you're seeking quick updates or engaging in brainstorming sessions, the app enables instant communication, fostering agility and responsiveness within teams.
File Sharing: Gone are the days of cumbersome email exchanges. Troop Messenger allows users to effortlessly share files of various formats, including documents, images, videos, and more. This feature ensures that crucial information is readily accessible to team members, promoting efficiency and productivity.
Group Chats: Collaboration often involves multiple stakeholders. Troop Messenger simplifies group communication by offering robust group chat functionality. Users can create dedicated chat groups for projects, departments, or specific topics, enabling seamless collaboration and knowledge sharing.
Voice and Video Calls: Sometimes, a face-to-face conversation is necessary to convey complex ideas or resolve issues effectively. Troop Messenger supports voice and video calls, allowing team members to connect instantly and engage in productive discussions irrespective of their physical location.
Integration Capabilities: Troop Messenger seamlessly integrates with a variety of third-party applications commonly used in the workplace, such as Google Drive, Dropbox, Trello, and more. This integration enhances workflow efficiency by centralizing communication and eliminating the need to switch between multiple platforms.
Remote Screen Share: Reach out to your remotest office teams with Troop Messenger’s productive and ultra-new screen share feature.
End-to-End Encryption: Your work conversations are under your complete control! Chats, calls, and conferences are end-to-end encrypted in this office chat app.
Conclusion
Troop Messenger emerges as a versatile and indispensable tool for fostering collaboration and communication within teams across diverse industries. Office chat app With its robust features, user-friendly interface, and industry-specific solutions, Troop Messenger empowers organizations to streamline workflows, enhance productivity, and achieve their business objectives with ease. Whether you're a startup, a multinational corporation, or a non-profit organization, Troop Messenger is your ultimate instant messaging app for office chat, facilitating seamless collaboration and driving success in the digital age.
0 notes
Text
Endpoint Protection Platforms Market Size Worth USD 6.91 Billion in 2030
The global Endpoint Protection Platforms (EPP) market size reached USD 3.33 Billion in 2021 and is expected to register a revenue CAGR of 8.4% during the forecast period, according to latest analysis by Emergen Research. Rise in trend of Bring Your Own Device (BYOD) and surge in incidence of cyberattacks are crucial factors driving market revenue growth.
0 notes
Text
Boomi API Management

Title: Mastering API Management with Boomi
Introduction
In today’s interconnected digital landscape, APIs (Application Programming Interfaces) form the backbone of communication and data exchange across applications, systems, and organizations. Managing these APIs effectively is crucial for streamlining operations, driving innovation, and unlocking new revenue streams. This is where Boomi API Management comes into play.
What is Boomi API Management?
Boomi API Management is a robust platform within the Boomi AtomSphere suite that empowers you to create, publish, govern, and analyze your APIs. It offers a comprehensive toolkit to manage the entire API lifecycle, ensuring seamless integration and unlocking the full potential of your digital ecosystem.
Key Features of Boomi API Management
Intuitive API Design: Boomi’s user-friendly interface makes it easy to build well-structured APIs defining endpoints (REST, SOAP, OData, or a combination).
API Gateways: Secure and control access to your APIs with API gateways. These gateways regulate traffic flow, authenticate incoming requests, and enforce usage policies.
Flexible Deployment: You can deploy your APIs in the cloud, on-premises, or hybrid environment, providing the adaptability you need for diverse scenarios.
API Developer Portal: A customizable developer portal enables self-service discovery and consumption of APIs. It also provides clear documentation and interactive testing tools to streamline API adoption.
Robust Security: Protect your APIs with advanced security mechanisms like API keys, OAuth, Open ID, and SAML authentication.
Analytics and Monitoring: Gain real-time insights into API usage patterns, performance metrics, and potential errors. Use this data to optimize your APIs and make informed decisions.
Why Use Boomi API Management?
Accelerated API Development: Streamline API creation with Boomi’s low-code, visual approach, reducing development cycles and enabling rapid time-to-market.
Centralized API Governance: Establish and enforce consistent policies across your APIs to ensure security, compliance, and maintainability.
Simplified API Discovery and Consumption: Empower developers to easily find and integrate the APIs they need through a well-organized and intuitive developer portal.
API Monetization: Explore new revenue streams by offering APIs as products or services, enabling partners and third-party developers to build on top of your data and functionality.
Enhanced Agility and Scalability: Boomi’s multi-cloud architecture allows you to scale your API infrastructure dynamically to meet changing demands.
Getting Started with Boomi API Management
You can easily access API Management features within your AtomSphere platform if you’re a Boomi user. Boomi offers comprehensive documentation, training, and community support to guide you through the API management journey.
Conclusion
Boomi API Management provides a powerful and versatile platform for managing the entire API lifecycle. By embracing it, you can accelerate digital transformation, foster innovation, and establish a robust API ecosystem that drives business agility and success.
youtube
You can find more information about Dell Boomi in this Dell Boomi Link
Conclusion:
Unogeeks is the No.1 IT Training Institute for Dell Boomi Training. Anyone Disagree? Please drop in a comment
You can check out our other latest blogs on Dell Boomi here – Dell Boomi Blogs
You can check out our Best In Class Dell Boomi Details here – Dell Boomi Training
Follow & Connect with us:
———————————-
For Training inquiries:
Call/Whatsapp: +91 73960 33555
Mail us at: [email protected]
Our Website ➜ https://unogeeks.com
Follow us:
Instagram: https://www.instagram.com/unogeeks
Facebook: https://www.facebook.com/UnogeeksSoftwareTrainingInstitute
Twitter: https://twitter.com/unogeek
0 notes
Text
Unlocking Business Success: The Importance of REST API in Your Project

In today's digital landscape, where connectivity and interoperability reign supreme, integrating a REST API (Representational State Transfer Application Programming Interface) into your business project is no longer just an option—it's a necessity. Whether you're developing a web application, mobile app, or any other software solution, leveraging RESTful APIs can unlock a multitude of benefits that are critical for achieving success in the competitive market.
Here are some compelling reasons why your business project needs a REST API:
Seamless Integration:
REST APIs provide a standardized way for different software systems to communicate with each other over the internet. By adhering to the principles of REST, such as stateless communication and resource-based URLs, RESTful APIs enable seamless integration between disparate systems, regardless of the technologies they are built with. This interoperability allows you to leverage existing services, data sources, and functionalities, saving time and resources while enriching your project's capabilities.
Enhanced Scalability:
One of the key advantages of REST APIs is their scalability. As your business grows and evolves, the demands placed on your application may increase exponentially. RESTful APIs are designed to handle these scalability challenges effortlessly, thanks to their stateless nature and lightweight architecture. By decoupling the client and server components and relying on HTTP protocols, REST APIs can efficiently scale to accommodate a growing user base, increased traffic, and evolving business requirements without sacrificing performance or reliability.
Improved Flexibility and Modularity:
RESTful APIs promote a modular approach to software development, allowing you to break down complex systems into smaller, more manageable components. Each resource exposed by the API represents a discrete unit of functionality, making it easier to update, extend, or replace individual features without impacting the rest of the system. This flexibility enables agile development practices, facilitates collaboration among development teams, and empowers you to adapt quickly to changing market conditions and customer feedback.
Cross-Platform Compatibility:
In today's multi-device world, delivering a seamless user experience across different platforms and devices is paramount. REST APIs enable you to achieve cross-platform compatibility by providing a uniform interface that can be accessed from any device with internet connectivity. Whether your users are accessing your application from a web browser, mobile app, or IoT device, they can interact with your services and data through a consistent set of API endpoints, ensuring a cohesive experience across all touchpoints.
Security and Control:
Security is a top priority for any business project, especially when dealing with sensitive data and transactions. REST APIs offer robust security mechanisms, including HTTPS encryption, authentication, and authorization, to safeguard your resources and protect against unauthorized access and malicious attacks. By centralizing access control and enforcing granular permissions at the API level, you can maintain strict security policies while granting controlled access to your application's functionalities.
Partnering with a specialized REST API development company is essential for maximizing the benefits of integrating a RESTful API into your business project. A reputable firm with expertise in API design, development, and integration can provide invaluable guidance, best practices, and tailored solutions to meet your specific requirements. Whether you're building a new application from scratch, enhancing an existing system, or migrating to a microservices architecture, collaborating with experienced professionals can ensure seamless integration, optimal performance, and future scalability.
In conclusion, incorporating a REST API into your business project is not just a technical decision—it's a strategic imperative. From enabling seamless integration and enhancing scalability to promoting flexibility and ensuring security, RESTful APIs play a crucial role in driving innovation, efficiency, and growth. By partnering with a leading REST API development company, you can harness the full potential of REST APIs and propel your project towards success in today's interconnected world.
0 notes
Text
does cisco offer free vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does cisco offer free vpn
Cisco free VPN services
Title: Exploring Cisco's Free VPN Services: A Comprehensive Guide
In today's digitally connected world, ensuring the security and privacy of online activities is paramount. Virtual Private Networks (VPNs) have emerged as a popular solution, offering users a secure and encrypted connection over the internet. While there are numerous VPN providers in the market, Cisco, a leading networking technology company, offers its own suite of VPN services, including some that are free of charge.
Cisco's free VPN services cater to both individual users and businesses, providing them with a range of features to enhance online security and privacy. One of the key offerings is the Cisco AnyConnect Secure Mobility Client, which enables users to connect to their organization's network securely from any location. This client supports various platforms, including Windows, macOS, Linux, iOS, and Android, ensuring compatibility across devices.
Additionally, Cisco offers a free version of its Umbrella DNS security service, which helps protect users from accessing malicious websites and phishing attacks. By leveraging Cisco's global network infrastructure, Umbrella provides fast and reliable DNS resolution while blocking access to harmful sites in real-time.
For businesses, Cisco's free VPN services can be particularly valuable, allowing remote employees to securely access corporate resources without compromising sensitive data. The Cisco VPN Client also supports advanced features such as multi-factor authentication and endpoint security, further bolstering security measures.
It's important to note that while Cisco offers free VPN services, there are also paid options available with additional features and support. Organizations with more complex networking requirements may opt for these paid solutions to meet their specific needs.
In conclusion, Cisco's free VPN services provide individuals and businesses with a reliable and secure way to protect their online activities. Whether it's accessing corporate resources remotely or browsing the web securely, Cisco's offerings ensure peace of mind in an increasingly interconnected world.
Cisco VPN cost comparison
Title: Cisco VPN Cost Comparison: Finding the Best Value for Your Business
When it comes to securing your business's network, Cisco VPN solutions are often a top choice due to their reputation for reliability and robust security features. However, navigating the various pricing options can be daunting. This article aims to provide a comprehensive comparison of Cisco VPN costs to help you make an informed decision for your business.
Cisco offers several VPN solutions tailored to different business needs, ranging from small businesses to large enterprises. The cost of these solutions depends on factors such as the number of users, features, and support options.
For small businesses, Cisco offers the Cisco Small Business RV Series Routers, which include VPN functionality. These routers typically range in price from $100 to $500, depending on the model and features.
For medium to large enterprises, Cisco's Adaptive Security Appliance (ASA) with VPN capabilities is a popular choice. Pricing for ASA devices varies widely based on factors such as throughput capacity and licensing options. Entry-level ASA models start at around $500, with higher-end models costing several thousand dollars or more.
In addition to hardware costs, businesses must also consider software licensing fees and ongoing support costs. Cisco typically offers subscription-based licensing for VPN features, with prices ranging from a few hundred to several thousand dollars per year, depending on the number of users and features required.
Furthermore, businesses may opt for additional support services, such as Cisco's Smart Net Total Care, which provides technical support, software updates, and hardware replacement services for an additional fee.
While Cisco VPN solutions may come with a higher upfront cost compared to some alternatives, many businesses find the investment worthwhile due to the reliability, performance, and security features offered by Cisco's products. However, it's essential to carefully evaluate your business's specific needs and budget constraints to determine the best value proposition.
Cisco VPN pricing models
Cisco offers a variety of VPN solutions with different pricing models to cater to the diverse needs of businesses. The pricing of Cisco VPN solutions varies based on factors such as the type of VPN service, number of users, and level of features required.
One common pricing model offered by Cisco is the subscription-based model. With this model, businesses pay a recurring fee, usually on a monthly or yearly basis, to access the VPN service. This model is popular among businesses as it allows for better budget predictability and scalability. Businesses can choose from different subscription tiers based on the number of users and the level of security and features needed.
Another pricing model offered by Cisco is the perpetual license model. With this model, businesses make a one-time payment to purchase the VPN software license outright. This model is ideal for businesses that prefer a one-time investment rather than recurring payments. Businesses can also opt for additional support and maintenance services for an extra fee.
Cisco also offers a pay-as-you-go pricing model for businesses that require more flexibility. With this model, businesses pay for the VPN service based on their usage, such as the amount of data transferred or the number of concurrent connections. This model allows businesses to scale their VPN usage up or down based on their needs, making it a cost-effective option for businesses with fluctuating VPN usage.
Overall, Cisco offers a range of pricing models for its VPN solutions to accommodate different business requirements and budgets. Whether businesses prefer a subscription-based model for predictability, a perpetual license for a one-time investment, or a pay-as-you-go model for flexibility, Cisco has options to suit various needs.
Free vs paid Cisco VPN options
When it comes to securing your internet connection, Cisco VPN is a robust solution that offers both free and paid options. Understanding the differences between free and paid Cisco VPN options can help you make an informed decision based on your needs.
Free Cisco VPN options typically come with limitations in terms of features, server locations, and speed. While they can be a good starting point for basic security needs, free versions may not offer the same level of protection and performance as their paid counterparts. Additionally, free VPNs may be more prone to logging user data, which can raise privacy concerns.
On the other hand, paid Cisco VPN options often provide advanced features such as unlimited bandwidth, a larger selection of server locations, and faster connection speeds. Paid VPNs also typically offer better customer support and improved security features to safeguard your online activities effectively.
Choosing between free and paid Cisco VPN options ultimately depends on your specific requirements. If you only need basic protection for casual browsing, a free VPN may suffice. However, if you rely on a VPN for secure access to sensitive information or faster speeds for streaming and downloading, investing in a paid Cisco VPN could be worth it in the long run.
In conclusion, while free Cisco VPN options can provide a certain level of security, paid options offer enhanced features and performance that cater to more demanding users. Evaluate your needs and priorities to determine which option aligns best with your online security and browsing requirements.
Cisco VPN affordability analysis
Title: Analyzing the Affordability of Cisco VPN Solutions
Virtual Private Networks (VPNs) have become indispensable tools for businesses seeking secure and reliable remote connectivity. Among the plethora of VPN providers, Cisco stands out as a renowned leader offering a range of solutions tailored to various enterprise needs. However, assessing the affordability of Cisco VPN solutions requires a comprehensive analysis considering several factors.
Firstly, Cisco offers diverse VPN options, including hardware-based solutions like Cisco ASA (Adaptive Security Appliance) and software-based solutions like Cisco AnyConnect. The cost of hardware appliances typically includes upfront expenses for purchasing the device and ongoing maintenance fees. In contrast, software solutions often involve subscription-based pricing models, which may be more flexible for budget planning.
Secondly, the scale of deployment influences the overall affordability. For small to medium-sized businesses with limited resources, Cisco Meraki MX series routers provide cost-effective VPN functionality with simple setup and management. Conversely, large enterprises may opt for Cisco ASA with FirePOWER Services for robust security features and scalability, albeit at a higher initial investment.
Additionally, the total cost of ownership (TCO) should be considered, encompassing not only upfront costs but also factors like maintenance, support, and potential scalability. Cisco's reputation for reliability and extensive support infrastructure can mitigate operational expenses over time, enhancing the long-term affordability of its VPN solutions.
Furthermore, businesses should evaluate the return on investment (ROI) enabled by Cisco VPNs, considering factors such as improved productivity, reduced risk of data breaches, and compliance with regulatory requirements. While the initial investment in Cisco VPN solutions may seem significant, the long-term benefits often outweigh the costs, making them a financially prudent choice for businesses prioritizing security and connectivity.
In conclusion, assessing the affordability of Cisco VPN solutions requires a nuanced examination of factors such as deployment scale, TCO, and ROI. While the upfront costs may vary depending on the chosen solution and business requirements, Cisco's reputation for reliability and comprehensive support services positions its VPN offerings as competitive options for businesses seeking secure and scalable remote connectivity.
0 notes
Text
CISA’s Zero Trust Maturity Model 2.0: Cybersecurity Roadmap

Zero trust maturity model version 2
Zero trust maturity model 2.0
With the help of CISA’s Zero Trust Maturity Model v2.0, the Federal IT environment is rapidly changing in favor of increased cybersecurity. To improve their cyber posture, federal agencies might use this model as a guide. The correct tools must be chosen in order for government entities to successfully manage this transition. Designed to fulfill the strict compliance requirements of federal organizations, Google Workspace brings strong security features to the table.
Google Workspace’s Role in Cisa zero trust maturity model 2.0
Cisa zero trust maturity model
Thin-layer security, continuous validation, and device-independent protection are highlighted in the CISA Zero Trust Maturity Model. A set of principles and ideas known as “zero trust” is intended to reduce ambiguity when it comes to enforcing precise, least privilege per-request access choices in information systems and services while dealing with networks that are seen as weak. Maintaining as much granularity in access control enforcement while preventing unwanted access to data and services is the aim.
For the following reasons, zero trust puts fine-grained security restrictions across individuals, systems, data, and assets that vary over time in a more data-centric manner rather than a location-centric one.To educate agencies on how to apply Zero Trust (ZT) concepts to mobile security technologies that are already on the market and probably included in a Federal Enterprise’s mobility program, CISA prepared the Applying Zero Trust concepts to Enterprise Mobility document.
On March 7, 2022, and ending on April 20, 2022, CISA made the document available for public comment. A revised version of the paper will be produced when CISA has taken into consideration the feedback provided by all responders. The formulation, execution, enforcement, and evolution of security rules are supported by the visibility that this gives. At a deeper level, zero trust can need altering the cybersecurity culture and mindset of a business.The following elements of Google Workspace support the idea of “never trust, always verify”:
Boost Access Control and Identity:
Context-Aware The correct individuals only get access to the right data thanks to strong authentication mechanisms and access.
Zero trust maturity model version 2
These measures safeguard private data at all points of access with sophisticated device controls and endpoint management.
Collaborating while preserving data is made possible by granular sharing settings and data loss prevention (DLP) features.Uncovered Information from the Google Workspace Zero Trust Security Workshop.
Recent Google Workspace Zero Trust Security Workshop provided an insightful overview of how Google Workspace may help federal agencies on their Zero Trust journeys. Using Zero Trust concepts in the federal context was discussed at the session by CISA specialists. A practical application of Zero Trust architecture driven by Google Workspace and Gemini AI was shown in the ManTech case study, which proved beneficial to the attendees.
The platform’s ability to achieve CMMC compliance is shown by ManTech’s shared experience, which provides other agencies with a useful model. IT decision-makers had practical experience with Google Workspace’s security controls via interactive demonstrations that were included in the training.
Zero trust maturity model
The Google Workspace Zero trust best practices guide for U.S. public sector organizations is a great tool for anybody who was unable to attend the event and wants to achieve CISA-compliant Zero trust maturity.
Special Sessions at Google Cloud Next ’24 on Google Workspace and Federal Cybersecurity.
Google Cloud Next ’24 is the next stop in the discussion, with talks on:
Achieve strict compliance across many frameworks (CJIS, FedRAMP, ITAR, DoD ILs) with Assured Workloads for Public Sector Compliance.
Using Gemini in Google Workspace, Keep Your Data Private and Compliant Come learn about the privacy and security features that come standard with Gemini for Google Workspace and how Sovereign Controls may help your company attain digital sovereignty.
AI-Powered Cooperation to Break Down Silos: Discover how creativity, productivity, and safe collaboration are facilitated with Google Workspace.
Through Google Workspace, Gemini: Privacy Guaranteed: Learn about the ways that Gemini protects data sovereignty while offering strong capabilities.
Ready for the government: The way that Google Workspace makes safe collaboration possible: Learn how federal, state, and local government organizations may simplify operations while upholding the highest standards of data security (with ManTech) using Google Workspace.
Google is dedicated to providing creative solutions that will assist agencies in the dynamic field of federal cybersecurity. Zero Trust principles are the foundation of Google Workspace, which gives users the flexibility and toughness they need to meet new challenges. Agency tasks are accomplished and sensitive data is safeguarded with more efficacy when paired with the wider capabilities of Google Cloud.
Federal agencies will always have access to state-of-the-art resources necessary to keep ahead of emerging cyber threats because to Google’s commitment to ongoing innovation.
Read more on Govindhtech.com
0 notes
Text
Exploring the Rise of Druva Share Price
Introduction
Nowadays, Druva Share Price has been witnessing a remarkable surge, Druva is a leading provider of cloud data protection and management solutions,. This article delves into the factors driving the upward trajectory of Druva Share Price and the implications for investors. Druva Data Solutions Ltd ("Druva") is a software-as-a-service platform developed to protect and manage enterprise data across edge, on-premises and cloud workloads. Their platform offers innovative cloud-native solutions to address data protection, governance, and compliance needs. Built on scalability and security, Druva enables efficient data protection and management across diverse environments.
Druva's strategy centres on delivering comprehensive data resilience solutions, covering backup, disaster recovery, and archival functions. Using AI and machine learning, Druva helps automate data protection, optimize storage, and preemptively address risks, boosting operational efficiency and resilience while cutting costs.
In 2011, smartphone support was added to the inSync app. The next year, the company relocated to Silicon Valley, refocusing on cloud-based data management. In 2014, Druva launched its Phoenix server backup product. By 2018, Druva had acquired CloudRanger, based in Letterkenny, specializing in backup and disaster recovery. In 2019, CloudLances was acquired to bolster on-premises to cloud performance. The subsequent year, sfApex, a Texas-based company focused on Salesforce data backup and migration, was acquired.
Druva Data Solutions is a Foreign Subsidiary of Druva Inc. and was incorporated on 11 February 2013, with its registered office at Plot No- 403/1, CTS No- 985, 8th Floor The Pavilion, Senapati Barat Road, Shivaji Nagar Pune MH 411016 IN.
Innovative Cloud Data Solutions
One of the primary drivers behind the rise in Druva's share price is its innovative cloud data protection and management solutions. Druva's platform offers organizations a comprehensive suite of services to safeguard and manage their data across various endpoints, on-premises infrastructure, and cloud environments. As businesses increasingly adopt cloud-based solutions for data protection, Druva's cutting-edge offerings have positioned it as a market leader, driving investor confidence and share price appreciation.
Strong Financial Performance
Druva's strong financial performance has also contributed to the surge in its share price. The company has consistently delivered impressive revenue growth and profitability, reflecting the increasing demand for its solutions. Investors are optimistic about Druva's ability to capitalize on the growing market for cloud data protection, driving speculation and investment in its shares.
Expansion into New Markets
Druva's strategic expansion into new markets has further fueled the rise in its share price. The company has been expanding its presence globally, tapping into emerging markets and forging partnerships with key players in the industry. By diversifying its geographic footprint and customer base, Druva has enhanced its growth prospects and attracted investor attention, leading to a surge in its share price.
Recognition and Industry Accolades
Druva's industry recognition and accolades have also played a role in boosting investor confidence and share price. The company has received numerous awards and accolades for its innovative solutions and customer-centric approach. Such recognition not only validates Druva's leadership position in the market but also enhances its reputation among investors, driving increased interest in its shares.
Strategic Partnerships and Collaborations
Druva's strategic partnerships and collaborations with leading technology companies have contributed to its share price rally. By aligning with industry giants, Druva has expanded its reach and access to new customers, while also leveraging complementary technologies to enhance its product offerings. Investors view these strategic alliances as a positive indicator of Druva's growth potential, driving enthusiasm for its shares.
Future Outlook
As Druva continues to innovate and expand its market presence, the future looks promising for the company and its investors. With a solid foundation built on cutting-edge technology, strong financial performance, and strategic partnerships, Druva is well-positioned to capitalize on the growing demand for cloud data protection and management solutions. Investors can expect the upward trajectory of Druva's share price to persist as the company continues to deliver value and drive innovation in the market.
Conclusion
The rise of Druva's share price reflects investor confidence in the company's innovative solutions, strong financial performance, and strategic initiatives. As Druva continues to expand its market presence and capitalize on emerging opportunities, investors stand to benefit from the company's continued growth and success. With a focus on driving value for customers and shareholders alike, Druva is poised to maintain its position as a leader in the cloud data protection and management industry.

0 notes
Text
How Does Walmart Product API Data Extraction Enhance Business Decision-Making
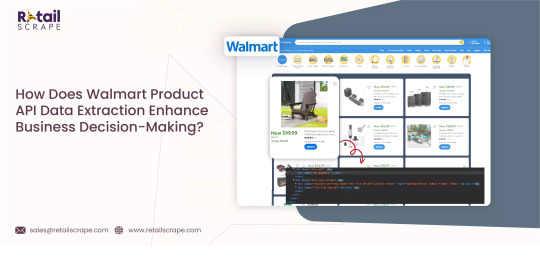
Have you heard about Walmart API data and its pivotal role in today's data-driven business landscape? In this digital age, where information is critical, accessing and analyzing data from retail giants like Walmart can provide invaluable insights for businesses. Walmart product API data extraction is a gateway to a treasure trove of information about products, prices, sales trends, and customer behavior.
Walmart data scraping involves collecting this valuable information from the Walmart website using automated tools and techniques. This process allows businesses to gather comprehensive data about Walmart's vast product catalog, pricing strategies, customer reviews, and more. By leveraging retail data scraping services, businesses can gain a competitive edge by monitoring market trends, analyzing competitor pricing, and optimizing their product offerings.
Furthermore, Walmart's scraping product API offers a more structured and efficient way to access data than traditional web scraping methods. Through the API, developers can programmatically retrieve specific data points in a standardized format, streamlining the data extraction process and enabling real-time updates.
Understanding how to scrape Walmart data and harness Walmart's API capabilities can empower businesses to make data-driven decisions, enhance their market intelligence, and stay ahead of the competition in the dynamic retail landscape. In this article, we will delve deeper into the intricacies of scraping Walmart data and explore the vast potential of Walmart's API for businesses.
Understanding API Data and Its Relevance to Business
API data, or Application Programming Interface data, refers to the information and functionalities that can be accessed and exchanged between different software applications through APIs. APIs serve as intermediaries that allow different systems to communicate and interact with each other seamlessly.
In the business context, Walmart product API data facilitates integration and interoperability between various software platforms and systems used within an organization. Allowing different applications to share data and functionality enables businesses to streamline operations, automate processes, and enhance efficiency.
Working Principles of API Data
The working principles of scraping API data involve leveraging the functionalities of APIs to extract relevant information from various sources in a structured and automated manner. This process typically follows these steps:
Authentication: Access to API data often requires authentication to ensure secure access to protected resources. It involves obtaining API keys or tokens and authenticating requests using standard authentication mechanisms such as OAuth.
Endpoint Discovery: Identify the API endpoints that contain the data you want to scrape. These endpoints represent specific resources or functionalities the API exposes and define the URLs or URIs to access the data.
Request Construction: Construct HTTP requests to access the desired data from the API endpoints. It specifies the HTTP method (e.g., GET, POST), required parameters or query strings, and headers such as authentication tokens.
Data Retrieval: Send the constructed requests to the API endpoints and retrieve the response data. The response typically contains the requested information in a structured data format such as JSON or XML.
Data Parsing: Parse the response data to extract the relevant information you want to scrape. It involves navigating the JSON or XML structure and extracting specific data fields or elements using parsing techniques such as XPath or JSONPath.
Data Storage: Store the scraped data in a structured format such as a database, CSV file, or spreadsheet for further analysis or processing. Ensure that the data storage mechanism aligns with your requirements for accessibility, scalability, and data integrity.
Error Handling: Implement error handling mechanisms to handle exceptions or errors that may occur during the scraping process. It includes gracefully handling HTTP status codes, connection errors, rate limiting, and other potential issues.
By following these principles, businesses can effectively scrape data from APIs, collect valuable insights, and leverage the information available through API endpoints for various purposes, such as market research, competitive analysis, and business intelligence.
For example, businesses can use APIs to integrate customer relationship management (CRM) systems with marketing automation platforms, enabling them to synchronize customer data, track interactions, and automate marketing campaigns. Similarly, APIs can connect e-commerce platforms with inventory management systems, enabling real-time product availability, pricing, and order updates.
Overall, e-commerce web scraping empowers businesses to effectively leverage the capabilities of different software applications and systems, enabling them to improve collaboration, enhance productivity, and deliver better customer service. It is vital in driving digital transformation and innovation across various industries, enabling businesses to stay competitive and adapt to evolving market trends and customer needs.
Role of Walmart Product API Data Extraction to Enhance Business Decision-Making
The role of Walmart data collection in enhancing business decision-making is pivotal. By tapping into the API's information, businesses can gain valuable insights into market dynamics, competitor strategies, and customer behavior. Analysis of this data empowers businesses to make informed decisions across multiple facets of operations. From market analysis and inventory management to competitive intelligence and marketing optimization, Walmart's Product data scraping services offer a treasure trove of data that can be leveraged to drive strategic initiatives. By utilizing this data effectively, businesses can stay ahead of trends, optimize resource allocation, and ultimately enhance their competitive position in the marketplace.
Gathering Walmart Data via Web Scraping
Utilizing web scraping for gathering data offers a more straightforward approach than utilizing specialized programs like the Walmart Data Extractor. The process begins with web scraping, where the company identifies a website with a layout resembling the target site, such as Walmart's product page. Ensuring a fast response time from the website is essential, and browsers supporting web scraping, like Google Chrome, are preferred.
Following this, software is developed for scraping, typically using languages like Python, Perl, Ruby, or PHP. Python is popular due to its cross-platform compatibility and readability. This software sends requests to the target website, retrieves desired data and saves it for further analysis or reporting. Remember that some web scraping technologies may necessitate additional software installation, such as Python, for optimal functionality.
Scraping Walmart Data Using Python
We are explaining the steps to scrape Walmart data using Python.
Obtain API Key: Sign up for Walmart's Developer Portal and obtain an API key to access their data.
Install Required Libraries: Install the necessary Python libraries for working with APIs, such as Requests.
pip install requests
Import Libraries: Import the required libraries into your Python script.
Handle Pagination (if needed): If the API response is paginated, handle pagination by iterating through multiple pages of results.
Extract Desired Information: Extract the relevant information from the API response, such as product names, prices, and ratings.
Conclusion
Walmart's Product scraping API offers businesses a powerful means of accessing and analyzing a wealth of product information on the platform. By harnessing this API, businesses can efficiently retrieve product names, prices, ratings, and more data, enabling them to gain valuable insights into market trends, competitor offerings, and consumer preferences. This data can inform strategic decision-making, enhance pricing strategies, optimize inventory management, and drive overall business growth. With proper implementation and utilization, Walmart Product API data extraction empowers businesses to stay competitive, make informed decisions, and capitalize on opportunities in the ever-evolving retail landscape.
UnlUnlock the potential of data-driven decisions through our Retail Scrape Company. Harness consumer behavior insights, refine pricing strategies, and outpace rivals with live retail data scraping. Elevate your enterprise with our full-range pricing optimization and strategic decision support. Connect today to transform your retail endeavors and amplify profits!
know more :
https://www.retailscrape.com/walmart-product-api-data-extraction-enhance-business.php
#WalmartProductAPIData#WalmartProductAPIDataExtraction#WalmartDataScraping#Walmart'sProductScrapingAPI#ScrapeWalmartData#WalmartDataCollection
0 notes
Text
Keeper Security Joins the AWS Partner Network

Keeper Security, a leading provider of cloud-based zero-trust and zero-knowledge cybersecurity software protecting passwords, passkeys, secrets, connections and privileged access, announces today it has joined the Amazon Web Services (AWS) Partner Network (APN). The APN is a global community of AWS Partners that leverage programs, expertise and resources to build, market and sell customer offerings. As an APN member, Keeper joins a global network of 130,000 partners from more than 200 countries working with AWS to provide innovative solutions, solve technical challenges, win deals and deliver value to customers. Keeper joined the APN to address the growing demand for robust account security and enhance the digital protections available to businesses around the world faced with the growing threat of cyberattacks.
"AWS has long been recognized as the leading cloud services provider and we're proud to meet their rigid standards and bring their technical advantages to public and private-sector business and enterprise customers," said Darren Guccione, CEO and Co-founder, Keeper Security. "This relationship marks a significant achievement for Keeper, as it furthers our steadfast commitment to deliver cutting-edge cybersecurity solutions."
Keeper provides a full suite of award-winning consumer and business offerings in password, secrets and privileged connection management, as well as differentiators that set Keeper apart from its competitors including dark web monitoring, secure file storage, encrypted messaging, seamless Single-Sign On (SSO) integration, compliance reporting and comprehensive event logging. Keeper's solutions scale to organizations of all sizes, from small home offices to multinational enterprises and the largest public sector organizations. Keeper also offers a solution for managed service providers, KeeperMSP.
Keeper's Enterprise Password Manager is designed to provide organizations with complete visibility into employee password practices, allowing IT administrators to enforce company password policies, monitor employee compliance and generate audit trails and reports. Keeper securely manages the lifecycle of privileged account credentials with Role-Based Access Controls (RBAC) and controlled credential sharing. Keeper supports the storage and use of passkeys in the vault and enables organizations to embrace a fully passwordless experience by integrating with SSO, enabling users to access their vaults without the use of a master password.
Keeper's latest offering, KeeperPAM™, provides a next-generation Privileged Access Management (PAM) solution that is disrupting the traditional PAM market. KeeperPAM delivers enterprise-grade password, secrets and privileged connection management within a unified SaaS platform that is cost-effective, easy-to-use and simple-to-deploy. The patented cybersecurity solution enables organizations to achieve complete visibility, security, control and reporting across every privileged user on every device within an organization.
Customers prefer Keeper for:
- Enterprise Security - Keeper mitigates the risk of breaches by providing real-time protection and access to applications, systems, secrets and IT resources.
- Robust Compliance and Reporting - Keeper simplifies and strengthens auditing and compliance including support for RBAC, 2FA, FIPS 140-2 encryption, HIPAA, FINRA, SOC, ITAR and more.
- Powerful Security Insights - Keeper provides analytics into credential security and hygiene across all endpoints and systems with native SIEM integration.
Through its relationship with AWS, Keeper extends its market reach and enhances its ability to serve customers across various industries all over the world, in addition to offering Consulting Partner Private Offers (CPPO) to Keeper's Reseller Community of over 2,000 partners, allowing them to facilitate customer purchases in AWS Marketplace. For more information, please visit APN.
Read the full article
0 notes