#Cloud Router
Text
Mastering Network Connectivity: Google Cloud Platform's Robust Networking Solutions
Unlock seamless connectivity with GCP's networking prowess! 🌐 Discover global load balancing, VPC security, and more. #GCP #CloudNetworking #HybridCloud
In today’s digital era, there’s nothing more crucial than seamless and reliable network connectivity for businesses thriving in the cloud. And when it comes to meeting these needs, Google Cloud Platform (GCP) truly stands out. With its comprehensive suite of networking solutions, GCP is tailor-made to address the diverse requirements of modern enterprises. In this captivating technical blog,…

View On WordPress
#aws#cloud#Cloud Computing#Cloud Interconnect#Cloud Networking#Cloud Router#Cloud VPN#gcp#GCP Networking Solutions#google cloud platform#Hybrid cloud#load balancing#Network Intelligence Center#Networking#technology#Virtual Private Cloud#VPC
2 notes
·
View notes
Text
InnoScale: Ihr Komplettanbieter für IT-Cloud-Lösungen im KMU-Bereich
Als Innoscale verstehen wir uns als Ihr starker Partner in allen Fragen der Digitalisierung. Wir sind ein Zusammenschluss von vier Unternehmen, die sich zum Ziel gesetzt haben, die gesamten digitalen Bedürfnisse Ihres KMU abzudecken.

Klingt zu schön um wahr zu sein? Dann überzeugen Sie sich selbst! Mit unseren maßgeschneiderten IT-Cloud-Lösungen unterstützen wir Sie dabei, Ihr Unternehmen effizienter zu gestalten, neue Wachstumsmöglichkeiten zu erschließen und sich im digitalen Wettbewerb zu behaupten.
Warum IT-Cloud-Lösungen für Ihr KMU?
In der heutigen Zeit ist Digitalisierung der Schlüssel zum Erfolg. Doch gerade für kleine und mittlere Unternehmen (KMU) stellen die damit verbundenen Investitionen und die Komplexität der Umsetzung oft eine Herausforderung dar.
Hier kommen IT-Cloud-Lösungen ins Spiel. Diese bieten Ihnen eine Reihe von Vorteilen, die Ihnen den Weg in die digitale Zukunft ebnen:
Skalierbarkeit: Mit Cloud-Lösungen können Sie Ihre IT-Infrastruktur flexibel an Ihre wachsenden Geschäftsanforderungen anpassen. Sie zahlen nur für die Ressourcen, die Sie tatsächlich nutzen.
Kosteneffizienz: Cloud-Dienste sind in der Regel kostengünstiger als der Aufbau und die Wartung einer eigenen IT-Infrastruktur. Sie sparen sich Investitionen in Hardware und Software sowie Personalkosten für die IT-Administration.
Sicherheit: Moderne Cloud-Anbieter bieten höchste Sicherheitsstandards und garantieren den Schutz Ihrer Unternehmensdaten.
Verfügbarkeit: Cloud-Dienste sind in der Regel hochverfügbar, sodass Sie jederzeit und von überall auf Ihre Daten und Anwendungen zugreifen können.
Mobilität: Cloud-basierte Anwendungen ermöglichen es Ihren Mitarbeitern, produktiv zu arbeiten, unabhängig davon, ob sie sich im Büro, zu Hause oder unterwegs befinden.
Automatisierung: Cloud-Dienste bieten häufig Funktionen zur Automatisierung von Geschäftsprozessen, was Ihnen Zeit und Ressourcen spart.
Welche IT-Cloud-Lösungen bietet InnoScale an?
Bei InnoScale bieten wir Ihnen ein umfassendes Portfolio an IT-Cloud-Lösungen, die speziell auf die Bedürfnisse von KMU zugeschnitten sind. Dazu gehören unter anderem:
Cloud-Speicher: Sichern Sie Ihre Unternehmensdaten sicher in der Cloud und greifen Sie von überall darauf zu.
Cloud-Backup: Schützen Sie sich vor Datenverlust durch regelmäßige Backups Ihrer Daten in die Cloud.
Cloud-Server: Nutzen Sie virtuelle Server in der Cloud, um Ihre Anwendungen und Dienste zu hosten.
Cloud-Desktop: Ermöglichen Sie Ihren Mitarbeitern den sicheren Zugriff auf ihre Desktops und Anwendungen von jedem Gerät aus.
Cloud-Collaboration: Arbeiten Sie effizient mit Kollegen und Partnern zusammen, indem Sie Dokumente und Dateien in der Cloud gemeinsam nutzen.
Cloud-Sicherheit: Schützen Sie Ihr Unternehmen vor Cyber-Bedrohungen mit modernen Cloud-Sicherheitslösungen.
Managed Cloud Services: Überlassen Sie die Verwaltung Ihrer Cloud-Infrastruktur unseren erfahrenen Experten.
Welche Vorteile haben Sie bei InnoScale?
Wir bei InnoScale gehen weit über die reine Bereitstellung von IT-Cloud-Lösungen hinaus. Wir bieten Ihnen einen umfassenden Service, der Sie auf Ihrem Weg in die Cloud begleitet:
Beratung: Unsere Experten beraten Sie bei der Auswahl der geeigneten IT-Cloud-Lösungen für Ihr Unternehmen.
Migration: Wir unterstützen Sie bei der sicheren und reibungslosen Migration Ihrer Daten und Anwendungen in die Cloud.
Schulung: Wir schulen Ihre Mitarbeiter im Umgang mit neuen Cloud-Anwendungen.
Support: Unser erfahrener Support steht Ihnen bei Fragen und Problemen jederzeit zur Verfügung.
Überzeugen Sie sich selbst!
Sind Sie bereit, Ihr Unternehmen in die digitale Zukunft zu führen? Vereinbaren Sie noch heute ein kostenloses Beratungsgespräch mit unseren Experten und lassen Sie sich von den Vorteilen unserer IT-Cloud-Lösungen überzeugen!
Zusätzliche Informationen:
Neben IT-Cloud-Lösungen bieten wir Ihnen auch eine Reihe weiterer Dienstleistungen an, um Ihr Unternehmen fit für die Digitalisierung zu machen. Dazu gehören unter anderem:
Webdesign und Entwicklung
E-Mail-Marketing
Suchmaschinenoptimierung (SEO)
Social Media Marketing
IT-Beratung
Besuchen Sie unsere Website https://innoscale.ch/ oder kontaktieren Sie uns direkt, um mehr über unser umfassendes Leistungsangebot zu erfahren!
#Netzwerk-Sicherheitslösungen#Virtuelle Private Netzwerke (VPN)#Firewall-Installation und Konfiguration#Router-Konfiguration und -Management#IT-Cloud-Lösungen#WLAN-Infrastruktur
0 notes
Text
Supersnel internet.....
De getallen van de internetproviders vliegen om je oren. De een heeft het over het Gigabit-netwerk wat ze kunnen aanbieden en daaroverheen komt er weer eentje met 2 Gigabit snelheid. Maar wat heb je nu aan dat supersnel internet?
Continue reading Untitled

View On WordPress
#bingewatchen#Cloud#fritzbox#GigaBite#glasvezel#internet#Router#snelheid#streamen#Switchbox#TP-Link#xs4all
1 note
·
View note
Text
BLIIoT R40 4G Industrial VPN Router used in Computer Room Base Stations Monitoring
1. Foreword
With the development and popularization of computer technology, the number of computer systems has increased day by day, and its supporting environmental equipment has also increased. Computer rooms have become an important part of major units. The equipment room equipment (power supply, UPS, air conditioning, fire protection, environment, security guards, etc.) must always provide a normal operating environment for the computer system. Once the environmental equipment of the computer room fails, it will affect the operation of the computer system. The reliability of data transmission, storage and system operation will pose a threat. If the accident is serious and cannot be dealt with in time, it may damage the hardware equipment and cause serious consequences. Therefore, it is necessary to monitor the water, smoke, access control, temperature and humidity, infrared, etc., and timely processing and solving problems, avoid damage to the hardware of the equipment, and cause serious consequences.
2. Monitoring content
Power distribution cabinets, intelligent power distribution equipment, air -on, UPS, battery, air conditioning, temperature and humidity, leakage, video, access control, etc.
3. System composition
Smart Sensor + BLIIoT R40 4G Industrial VPN Router + Data Center
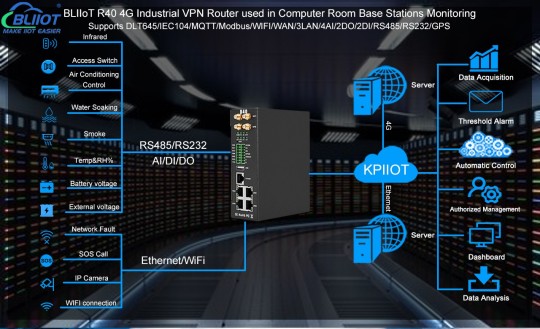
BLIIoT R40 4G Industrial VPN Router can be connected to various sensors, which can read the state of smoking and water -immersing switch in real time. Remote control of access control, air conditioning, and infrared switches, and real -time monitoring of the temperature and humidity index.BLIIoT Technology also provide access to the unmanned computer room monitoring cloud platform, which can remotely control the device and provide data collection, data storage, device maps, historical data analysis curves, timing tasks, alarm functions (SMS, WeChat, mail, APP), permissions Management (pyramid structure, perfect institution, role, user system), three -terminal interoperability (web webpage, APP, WeChat public account).
4. System advantage
24 hours full -time inspection, abnormal real -time alarm
The motion room monitoring system can achieve a 24 -hour full -time inspection. Once abnormal problems are found, the real -time alarm can be achieved through alarm to comprehensively ensure the safety of the computer room.
High integration and unity, convenient management and reduced cost
BLIIoT R40 4G Industrial VPN Router provide a variety of interfaces and support a variety of protocols. Only single terminals can access multiple devices for collection and linkage, which greatly reduces the cost of deployment and maintenance, and integrates unified management and control.
Remote environmental monitoring to reduce maintenance personnel
Real -time monitoring of the environmental data of the electrical room, the operating status of the equipment, and the uniform management of the electric equipment on the scene to avoid the tedious tasks of the staff to inspect the on -site inspection. The staff can fully grasp the entire information of the computer room in the monitoring room.
Automated monitoring system, improve management efficiency
The administrator can intuitively understand the overall operation status of the machine room, monitoring data, and alarm prompts through the background to improve management efficiency, reduce the workload of manual inspections, and reduce labor costs for enterprises; at the same time , Reduce the cost of accident handling.
5. Summarize
Monitoring system through the Internet of Things power room monitoring system allows the operation and maintenance management of power dispatching machine rooms and substation machine rooms to be more simple, concentrated, and efficient. No manual inspection and maintenance, at the same time, can achieve real -time monitoring and information notifications, multi -directional monitoring and alarm functions, and can realize intelligent linkage control, so that you can remotely control the equipment thousands of miles away, build a smart Internet of big data in the era of big data era. surveillance system.
More information of BLIIoT R40 4G Industrial VPN Router: https://www.iot-solution.com/industrial-iot-edge-gateway-p00307p1.html

#iot#iotsolutions#iotgateway#router#remotemonitoring#4glte#ethernet#wifi#edgecomputing#vpn#mqtt#modbus#datacollection#cloud#dlt BLIIoT BLIIOT Applications
0 notes
Link

Click and visit my website : https://www.hpshowroomhyderabad.in/cisco-servers.html
cisco servers dealers hyderabad, cisco servers price in hyderabad, cisco servers price in telangana, cisco servers pricelist hyderabad, cisco servers dealers in telangana, cisco servers dealers in nellore, vizag, vijayawada, tirupati, cisco servers review, cisco servers models telangana, cisco servers service in hyderabad, cisco servers price in india. For Contact-9551913312/9941534156(call/what's app)
Read More
#cisco server#cisco switch#cisco access point#cisco router#cloud server#cloud storage#chennai#hyderabad
0 notes
Text
Computation
part 7 of Complex Mathematics
(aka Dream vs Technology -- Technology: 1, Dream: 0)
------------
Wednesday, 3:54am
Hob. what is the wifi password?
3:56am: why are you texting me when I’m in the same house?
3:57am: I did not want to wake you up.
4:00am: ……….
4:01am: Ah.
4:03am: it’s 12345. which is terrible security by the way
4:04am: how do i know this and you don’t? we’re in YOUR flat
4:05am: Computers are your friends, not mine.
4:10am: It does not like the password.
4:12am: alright i’m getting up
Dream creeps back into the living room, holding a cup of tea, as Hob’s tinkering with the router. Turns out it needed to be completely reset before he could reconnect it to Dream’s laptop. Not that this is that hard, but for some reason Hob doesn’t understand, technology is simply out of Dream’s grasp. Head in the clouds, too smart for basic computer skills, etc etc.
“A peace offering,” Dream says, placing the tea on the coffee table. He perches on the couch beside where Hob’s leaning over the router on its spot on the bookshelf.
“I’m not mad at you,” Hob says. He pats the router as its indicator lights finally turn green again. “I will take tea, though.”
“I woke you,” Dream says softly.
“You’ve woken me before, you will again,” Hob says with equanimity. Their sleep schedules are out of alignment, it tends to happen.
It’s the wrong thing to say, though. Dream cringes, hands folding in his lap. “I should be able to handle such things.”
“It’s just the wifi.” Hob finally finishes reconnecting Dream’s laptop and turns properly towards him. Dream still looks guilty about it. Sometimes Hob misses the time before they were dating, when Dream would bristle at him instead of caving. Just because he doesn’t like seeing Dream feel bad.
He takes the cup of tea and places it in Dream’s hands instead, briefly wrapping their hands around each other. “It’s okay,” he repeats. Possibly they should have a longer conversation about it, but Hob’s not emotionally awake enough for it.
Instead, he gets up and heads for the kitchen to put on some coffee. He needs something with more caffeine in it than tea.
“What are you doing?” Dream asks.
“Might as well get something done while my brain is online,” Hob says. He goes to fetch his own laptop from Dream’s bedroom. Lord knows it’ll need to get reconnected to the glitchy wifi again, anyway.
~~
Friday, 2:05pm
Hob.
2:06pm: ?
2:07pm: The wifi is angry again.
2:09pm: did you antagonize it?
2:09pm: hang on did you just wake up now?
2:10pm: I cannot comment.
2:12pm: I assume you have been hard at work in the library since six.
2:14pm: more like hardly working in the library. i did make an app that gives you a gold star every time you do the laundry
2:16pm: Will that assist in your routines?
2:17pm: probably not but it’ll be fun for 5 minutes
2:17pm: wifi password’s still 12345
2:18pm: maybe I should make an app for that instead…
2:20pm: I do not think it would help.
2:30pm: …You are not trying to make said app, are you?
2:34pm: nope just realized I’m late for a class and had to scramble out of there. I’ll be back later can do couples counseling for you and wifi then?
2:35pm: Very well.
For a while after putting down his phone, Dream stares at the wifi router in vexation, as if that will possibly make the angry red lights turn green again. He doesn’t know what he’s done wrong. He knows even less what to do to fix it.
He needs the wifi operational to keep generating these fractals. He supposes he could go to the library and use university wifi, but that requires going out in public, which is preferably avoided, at least while he’s trying to work. So he will have to do something else until Hob gets back from class.
He recalls what Hob had said. That instead of working on his dissertation he had made an entire phone app about laundry. He had said it so casually, like it was a doodle to pass the time. Dream can use apps—barely—but he cannot begin to fathom how he would go about making one. Hob does not understand how even in his procrastination he is exceptional.
Well. This is something that Dream can do. Hob hates doing laundry—hence the app-based reward system—but Dream doesn’t mind. He finds it meditative. He will have to be more precise about fabric care instructions now, as while his own clothes rarely range beyond grey, black, and dark blue, Hob actually wears colors which might bleed into each other.
He puts on his headphones with some music, gathers up the laundry from the bedroom, and goes about his routine.
When Hob gets back, Dream has finished hanging the laundry to dry and returned to his contemplation of the router, this time still with his headphones playing. He’s lost in thought, and doesn’t notice Hob’s come in until his hand lands on Dream’s shoulder. Normally a sudden touch when he’s thinking would make him jump, but he’s become used to Hob.
“Trying to solve your marital problems through telepathy?” Hob asks.
“We were never married,” Dream says. “Indeed we are enemies.”
Hob laughs. He kisses Dream on the cheek, then kneels in front of the router. “You have to stop tormenting my boyfriend,” he tells it. It only blinks back at him innocently.
Hob can be very silly at times. “I do not think arguing with the inanimate object will help,” Dream says.
“You never know.” Hob takes the router down and sets about unplugging all the cables. Dream still doesn’t know what any of them precisely do, nor how wifi works. It may as well be magic.
Hob has it fixed within minutes, of course. Far more effective than Dream’s intense staring. He gets Dream’s laptop reconnected, and Dream is finally able to start generating his fractal. “Thank you,” he says.
“Anything for my love,” says Hob, getting to his feet again. “Guessing you want some time to yourself now to work on this?”
“Yes,” says Dream, with some guilt. Hob has come home to help him only for him to immediately bury himself in his work again. But yes, he does want to make progress on this at last.
“Well, good,” says Hob, and Dream turns to him in surprise. “Because I’m due for a nap.”
Dream still hasn’t formulated a response to this by the time Hob’s disappeared into his bedroom. Strange, that their routines can be so opposite and still meld together so well.
Hob pokes his head back out into the hall. “Did you do the laundry?”
“Yes,” says Dream.
“I could kiss you,” Hob declares, then blows one to him before disappearing back into the bedroom.
Dream presses his hand to his cheek, as if to touch a kiss that had really landed there. Smiles to himself. Then goes back to his fractal.
~~
Monday, 5:02pm
Hob.
5:03pm: Wifi?
5:04pm: …Yes.
Thursday, 9:50pm
…..Hob.
9:50pm: I’m sitting right next to you.
9:51pm: ….
9:51pm: I’m just gonna get you a new router. This thing’s got problems.
9:52pm: I think it is I who has the problems.
9:52pm: That too.
Saturday, 6:00pm
Hob.
6:00pm: Is it broken AGAIN??
6:01pm: No. I got dinner.
6:02pm: Oh!
6:02pm: Fuck I’m starving.
6:03pm: Coming back from class now.
6:03pm: Don’t touch the router it’s in a fragile mental state.
6:04pm: Aren’t we all.
~~
Thursday, 3:50pm
This time, it is the wifi in Hob’s flat that is stymieing Dream. He does not think it is broken. Hob has merely changed the password, as he’s much more diligent about internet security than Dream, and then forgotten to tell Dream what it is. Or, more likely, correctly assumed Dream would have to ask him again anyway.
He briefly contemplates trying to deduce the password, but it is likely an incomprehensible string of characters that Hob would claim is ideal security precisely because of the impossibility of deducing it.
He refuses to text Hob about it again. Hob has a class to teach soon—Dream has his schedule memorized—Dream does not want to distract him. Though speaking of…
3:50pm: You have a class in ten minutes.
3:51pm: FUCK
3:51pm: I got distracted
3:53pm: Now… running
3:54pm: You are not near the building, are you.
3:55pm: NOPE
Dream smiles to himself, thinking of Hob sprinting across campus. It happens often. Hob is good at many things, but time management is not one of them. This is why Dream knows his schedule.
He does feel… a bit silly, though. He should be better at this, should he not? Less bothersome to Hob over small things that he should be able to handle.
Normally he would go back to his work to distract himself from these thoughts, but he still can’t work on his fractals without being able to connect remotely to the university computers, which are more powerful than his own. This is something Hob had also set up for him, because Dream had not been able to make any sense of the instructions he had been given for remote login, and the like.
Sighing, he instead takes his sketchbook out of his bag. It’s been a while since he’s made any time for drawing. But he had started looking at fractals in the first place to better understand patterns in art, to understand resonances between what occurred in nature and what was projected by mathematics. And drawing used to soothe him.
So he starts drawing, sketching the fractal he has been generating—to the extant that he can with the imprecise instrument of his pen. Even in infinite impossible digital form, the branching spirals eventually become too small for him to see, though he knows they continue on in perfect replication forever, smaller and smaller until they disappear into atoms. He cannot recreate that level of detail by hand. But he tries.
By the time he gets another text back from Hob, an hour later, he’s moved to the floor to have more space. He’s found a bigger piece of scrap paper and is drawing the fractal again, in more detail this time, color-coding the different shapes, free-handing where he should probably use a ruler for more precision. He has achieved several more levels of replication than before, but it is still not right. He can’t get it right. If he could only use the stupid computer system he could get it right.
Finally he looks at his phone, several minutes after the text alert pinged.
Thanks love 😘
Unexpectedly, it makes him tear up. Always this happens to him. He does not realize how frustrated he has become with himself until it is too late.
Of course, to only make matters worse, he is still sitting hunched on the floor, pen clasped tight in his hand, teeth clenched so hard it’s hurting his jaw, when Hob comes through the door. He must have texted not far from home.
“Hey, love,” Hob’s already saying as he comes through the door, “meant to stop and grab dinner but I totally forgot— I’m sure I have something here, though— Dream?”
Dream hasn’t moved from the floor, or responded. Hob puts down his bag and comes over to him. He looks down at the fractal, which is still incomplete. “Did you draw that?”
“Obviously,” Dream bites. The pen is still in his hand. He drops it, scraping a hand through his hair. Great. Now he’s snapping at Hob, too.
Hob sits down on the floor beside him. He studies the fractal. Then points to one of the shapes that Dream’s colored in red. “That’s supposed to be purple.”
Dream stares at the fractal. Hob is right, it is meant to be purple. According to the way Dream had color-coded it digitally. He looks at Hob. “How do you know that?”
“I’ve watched you fiddling with it enough. We set it up on your laptop, remember?”
Yes. Dream remembers. He remembers how Hob had helped him.
“Wifi giving you troubles again?” Hob asks, looking from the drawing, to Dream’s laptop, which is sleeping on the couch.
Dream nods, then saws quietly, “Are you not… frustrated with me? Annoyed?”
Hob doesn’t need to ask what he means. “Sometimes,” he says, and Dream can’t help his flinch. “So?”
“So?”
Hob shrugs. “I would have missed that class if you didn’t text me.”
Dream does not understand the relevance.
Hob looks up at him, raising an eyebrow in challenge. “Aren’t you annoyed with me?”
Perhaps he is, at times. Recently, Dream has been too absorbed in his project to feel much about it at all.
“I don’t know,” he says. “It is just how you are.”
Hob seems to think that Dream still doesn’t understand the point he’s making, and perhaps Dream doesn’t. Hob takes his hand. “Look. I’ve no idea why someone as smart as you are is constantly defeated by basic technology, but it doesn’t matter. Always having to be the one to fix the router is a small price to pay for having you in my life.”
Dream’s mouth opens, but no words come out. He… he does not know if anyone has ever put up with him with so little complaint. For truly, it is not only computer troubles. It is all the small things that stack upon each other to make him feel different and difficult.
“I find I do not like…” Dream admits tentatively, “when you must do these things. That I should be able to do.”
“You did the laundry the other day,” Hob says.
Why must he jump topics in this manner? “I do not understand.”
“Well, we don’t actually live together, you know. You have your own laundry. You don’t have to do mine, too.”
“I thought it would help you,” Dream says.
Hob just waits expectantly.
Dream looks down at his lap. “Ah. I… see.” Hob finds him frustrating at times, he had said so, but still wants to help him. He finds Hob’s admittance that Dream is frustrating to be a relief, in its way. He would only feel more on edge if Hob pretended otherwise, surely to snap later when Dream was least expecting it, as so many have done.
“Give me your arm,” Hob says then.
When Dream does, Hob pushes up his sleeve, takes one of the markers from the floor and writes on Dream’s forearm, the wifi password is I love you.
“There,” he says. “Now you won’t forget.”
Dream touches the words with a light fingertip. “This is not good internet security.”
“Oh, so you do listen my ramblings,” Hob says, laughing. Always, Dream thinks. “What, you’re going to throw out my valentine because I cut the heart out a little wonky?”
He makes as if to rub the marker off, and Dream pulls his arm protectively to his chest. Hob’s smile softens. He carefully pulls Dream forward into a hug, Dream’s arm pressed between them. Dream tucks his face into the crook of Hob’s neck. It’s one of his favorite places to hide.
“I’ll help you fix your program after we find some dinner,” Hob tells him, rubbing his back.
“I think I should give up on using computers,” Dream mumbles.
Hob chuckles. “See how you feel about it after I make you some brownies for dessert.”
Dream hums in pleasure at the thought, and Hob kisses the side of his head. And Dream touches, again, the words Hob’s written on his arm, where it’s pressed between them. And allows himself to smile.
Wednesday, 6:03pm
Dream is attempting to cook dinner. Hob doesn’t think it’s going so well. At least not if the blaring fire alarm, which Hob’s just silenced by waving a dish towel at it until the smoke dissipated, is any indication. But it does mean he’s been treated to the sight of Dream with his sleeves rolled up, delicate hands at work—and wearing an actual apron.
Having soothed the alarm, he leans against the counter so he can shamelessly ogle instead of helping.
“What are you even trying to make?” he asks, eyeing the still-smoking oven.
Dream pouts. “Only bread. It should not be so hard.”
“You didn’t wait for me to get home to watch?” He imagines the sight of Dream aggressively kneading the bread dough. It shouldn’t be a turn on, but it kind of is.
“You would make a spectacle of my misery?” Dream says, but there’s a smile tugging at the corner of his lips, like he knows exactly what Hob is thinking about.
“Definitely,” Hob says, and Dream sighs, but turns to take the attempt at bread out of the oven. It’s… pretty blackened, to be honest. “Butter’ll save it, I’m sure!” Hob says cheerfully.
“Nothing will save it,” says Dream, morosely. He pulls off his oven mitt in apparent disgrace, and— Hob catches his arm.
“How has this not faded yet?”
For Hob’s writing saying the wifi password is I love you is still on his forearm.
Dream looks sheepish. “I got it tattooed.”
Hob tilts his head at him, confused. “So you could remember the wifi password?”
“So that I could remember this.” He traces his finger over, I love you.
Hob feels a blush creep across his cheeks. But it’s a pleasant feeling. “This is not even my best handwriting.”
“I know,” says Dream. He does not seem unhappy about it.
Hob takes his arm, touches the words, too. “You could have just gotten this part done.”
“I think,” Dream says slowly, touching the part that says, the wifi password is, “that this is another form of the same.”
And Hob… finds himself tearing up a little. Because it’s true. It’s so silly that Dream, certifiable maths genius, struggles so much with basic computer skills. But Hob will do any silly thing for him, because he loves him.
“Yeah,” he says, taking a shaky breath. “It is.”
“Unfortunately, you can never change the wifi password now,” says Dream, and Hob laughs wetly.
“I really can’t, can I? Terrible security. The things I’ll do for you, darling.”
“Would that include making proper bread?” Dream asks, and Hob nods, patting his arm.
“We’ll fix it, don’t worry.”
Now he’s wondering how he didn’t notice Dream getting a tattoo. Though to be fair, they haven’t seen each other as much in the past two weeks as they usually would, thanks to very inconvenient scheduling. Apparently Dream’s taken advantage of that time to do this.
“Can’t let you out of my sight for a second,” he says, as he fetches a new bread pan from the cupboard. “God knows what you’ll come back with next.”
“Be careful or I will consider that a challenge,” Dream says, and Hob pauses as way too many images flash through his mind. He shakes them off. He’ll never be able to focus on anything like that.
And Dream, the bastard, is smirking.
“Watch that look on your face or you might find that flour you’re holding dumped over your head,” Hob warns, but Dream only looks victorious, and utterly uncaring of the bag of flour he's precariously picked up.
“How will you ogle me kneading the dough that way?”
Hob swipes a dish towel from the counter and throws it at him. Dream yelps and spills the flour, which poofs up in a cloud of white landing all over his black t-shirt.
“Hob,” he complains.
“Serves you right, you dickhead,” Hob says. It only returns the smirk to Dream’s face.
“If you feel that way perhaps I’ll decide I don’t need your supervision,” he says archly.
Hob tears a piece off of Dream’s first attempt at a loaf. Or rather, breaks off a piece, which is hard as stone. He shows it to him as evidence.
Dream snatches it and shoves it into his mouth. Bites down with a crunch so horrifying Hob’s afraid he’s broken a tooth. But Dream persists, chewing it painstakingly and then swallowing, as if by force.
“Taste good?” Hob asks.
“Yes—” Dream starts to insist—then dissolves into a fit of coughing that swiftly turns into giggles. Hob loves it so much when he laughs like that. It’s so rare.
Hob laughs with him. Then frees the crumpled bag of flour from Dream’s grasp and sets it aside, brushes the flour and crumbs from his shirt. Then he takes Dream’s arm and runs his fingertip over the words again, still in awe.
He again finds himself having to clear his throat to avoid tearing up. But he manages, and says, “Let’s get you some proper, not burnt bread, yeah?”
“Please,” says Dream, a tad sheepish. “I am… very hungry.”
Hob kisses his cheek, then goes about solving that problem, too.
#this is so... silly. so sappy#complex mathematics#dreamling#dream of the endless#hob gadling#my writing#proofread this many times so here's hoping it's fine now XD
233 notes
·
View notes
Text

"Absolutely not."
Clark pauses instinctually at the specific tone of Bruce's voice. It's the one Clark has labeled Bruce's "annoyed but can't process why" tone, typically reserved for when Hal or Oliver are *existing* too close to him.
"Everything ok in there?" Clark asks, even though "in there" is the living room just ahead of the kitchenette bar in Clark's apartment. The open floor plan allows front row seats to Bruce's slow glare development.
The left brow is a little lower than the right which means they've reached category 2 in Bruce's annoyance scale.
Uhoh
Currently the not-masked crusader is sitting on the couch, worn but clean cushions half swallowing the spine-straight posture like a cloud. Donning his typical all-black fashion which only ever makes his skin look like bleach bone peeking out from the darkness.
"Wifi." Bruce states, watching Clark with disapproval that probably has activated Dick Grayson to shudder somewhere.
"Ah." Clark replies, knowing exactly what the issue is.
He tries to will his ears to stop burning, convinced if he acts casual enough, pouring coffee out evenly between two mugs before him, that his body will obey. "In my defense ---" He tries, but there's really no defense for his password to be "Bruce Wayne is Batman" Still, he scrambles for anything. "You're really the only person who'd guess it."
Bruce's face reads *I better be* while taking the mug offered as Clark comes around the couch. Trying to remain cool and calm and kicking himself for not thinking about this before Bruce spent time in his home.
Part of him just assumed Batman has a hotspot hidden in his shoe sole at all times or something equally convoluted - the idea that Bruce would need his wifi felt too domestic for the man. Then again that Bruce Wayne is in his apartment at all while the sun is up - and not just skulking in the shadows of his fire escape as Batman, judging him for the growing collection of houseplants - felt surreal enough.
"Where's your router?" Bruce demands when Clark comes around, handing him the mug and settling in beside him on the couch. Allowing the broken-in cushions to support his body with a soft embrace.
The sudden shift of weight causes Bruce's stiff frame to overcompensate on soft cushions to keep coffee from spilling. Leaving him no choice but to fall against Clark's side.
"You're not changing it."
Too-blue of eyes glare over at him, affronted at being told what he can and cannot do.
"Your digital security is abysmal." There's the smallest gesture of surrender in the way Bruce allows this nearness, the shock of cold ever clinging to the man's body melding with Clark's warmth. It's a victory that leaves Clark's skin humming and Bruce avoiding his gaze as he wrestles with the urge to meddle everything around him.
"If you think that's bad, don't look at my work login." Clark pushes his luck to tease and, despite being the alien in the room, when Bruce goes tense with calculation it feels out of this world.
"I swear to God if it's: I'm Superman...."
Clark drinks his coffee very quickly in an attempt to hide the guilty flinch from Bruce.
It doesn't work...
"CLARK."
#superbat#clark kent#superman#batman#bruce wayne#oz drabbles#fic generator inspo for the morning cause im the worst employee ever
260 notes
·
View notes
Note
hello friend Bee! I am still doing vault hunters though I haven’t gotten very far at all. I have however specced entirely into ‘Go Fast’ and ‘hit hard’ so I’m like level 28 with three levels of speed and like, maxed strength. I’m running out of keyboard buttons close to my hands so I haven’t got any ranged attacks. My favorite vaults are elixir! I may also have a hoarding problem, I have so much stuff I rarely use. How are you doing?
my most recent run is on a server with my friends we started a few months ago! I’m about level 80 now and have recently switched from my old physical scatter javelins build to a poison nova build, with a side spec into lucky hit for when my cooldowns are up and I have to actually hit things with my sword. switching from shields to wands has made me MUCH squishier, but at high levels the toxic reaction/poison nova build is just so damn fun I don’t care. (plus, hilarious side effect of “I carry a wand with a legendary CDR modifier in the overworld so I can dash as much as possible, and by chance it has poison cloud, and since my killing routers in my farm use my stats it clears out the farm SO FAST whenever the cloud procs and toxic reaction goes brrrrrr.)
getting high speed is FUN, and strength is actually REALLY GOOD earlygame especially; +12 attack damage at max strength increase is a LOT of attack damage at a point in the game where that just about doubles your damage outright. plus, if you get some armor with % attack damage modifiers you can do some real hurt! javelins for range sound like they’d be good for your build, if you have the free space.
glad you’re having fun LOVE vault hunters here,
28 notes
·
View notes
Text
Delegating trust is really, really, really hard (infosec edition)

CORRECTION: A previous version of this thread reported that Trustcor has the same officers as Packet Forensics; they do not; they have the same officers as Measurement Systems. I regret the error.
I’ve got trust issues. We all do. Some infosec pros go so far as to say “trust no one,” a philosophy more formally known as “Zero Trust,” that holds that certain elements of your security should never be delegated to any third party.
The problem is, it’s trust all the way down. Say you maintain your own cryptographic keys on your own device. How do you know the software you use to store those keys is trustworthy? Well, maybe you audit the source-code and compile it yourself.
But how do you know your compiler is trustworthy? When Unix/C co-creator Ken Thompson received the Turing Prize, he either admitted or joked that he had hidden back doors in the compiler he’d written, which was used to compile all of the other compilers:
https://pluralistic.net/2022/10/11/rene-descartes-was-a-drunken-fart/#trusting-trust
OK, say you whittle your own compiler out of a whole log that you felled yourself in an old growth forest that no human had set foot in for a thousand years. How about your hardware? Back in 2018, Bloomberg published a blockbuster story claiming that the server infrastructure of the biggest cloud companies had been compromised with tiny hardware interception devices:
https://www.bloomberg.com/news/features/2018-10-04/the-big-hack-how-china-used-a-tiny-chip-to-infiltrate-america-s-top-companies
The authors claimed to have verified their story in every conceivable way. The companies whose servers were said to have been compromised rejected the entire story. Four years later, we still don’t know who was right.
How do we trust the Bloomberg reporters? How do we trust Apple? If we ask a regulator to investigate their claims, how do we trust the regulator? Hell, how do we trust our senses? And even if we trust our senses, how do we trust our reason? I had a lurid, bizarre nightmare last night where the most surreal events seemed perfectly reasonable (tldr: I was mugged by invisible monsters while trying to order a paloma at the DNA Lounge, who stole my phone and then a bicycle I had rented from the bartender).
If you can’t trust your senses, your reason, the authorities, your hardware, your software, your compiler, or third-party service-providers, well, shit, that’s pretty frightening, isn’t it (paging R. Descartes to a white courtesy phone)?
There’s a joke about physicists, that all of their reasoning begins with something they know isn’t true: “Assume a perfectly spherical cow of uniform density on a frictionless surface…” The world of information security has a lot of these assumptions, and they get us into trouble.
Take internet data privacy and integrity — that is, ensuring that when you send some data to someone else, the data arrives unchanged and no one except that person can read that data. In the earliest days of the internet, we operated on the assumption that the major threat here was technical: our routers and wires might corrupt or lose the data on the way.
The solution was the ingenious system of packet-switching error-correction, a complex system that allowed the sender to verify that the recipient had gotten all the parts of their transmission and resend the parts that disappeared en route.
This took care of integrity, but not privacy. We mostly just pretended that sysadmins, sysops, network engineers, and other people who could peek at our data “on the wire” wouldn’t, even though we knew that, at least some of the time, this was going on. The fact that the people who provided communications infrastructure had a sense of duty and mission didn’t mean they wouldn’t spy on us — sometimes, that was why they peeked, just to be sure that we weren’t planning to mess up “their” network.
The internet always carried “sensitive” information — love letters, private discussions of health issues, political plans — but it wasn’t until investors set their sights on commerce that the issue of data privacy came to the fore. The rise of online financial transactions goosed the fringe world of cryptography into the mainstream of internet development.
This gave rise to an epic, three-sided battle, between civil libertarians, spies, and business-people. For years, the civil liberties people had battled the spy agencies over “strong encryption” (more properly called “working encryption” or just “encryption”).
The spy agencies insisted that civilization would collapse if they couldn’t wiretap any and every message traversing the internet, and maintained that they would neither abuse this facility, nor would they screw up and let someone else do so (“trust us,” they said).
The business world wanted to be able to secure their customers’ data, at least to the extent that an insurer would bail them out if they leaked it; and they wanted to actually secure their own data from rivals and insider threats.
Businesses lacked the technological sophistication to evaluate the spy agencies’ claims that there was such a thing as encryption that would keep their data secure from “bad guys” but would fail completely whenever a “good guy” wanted to peek at it.
In a bid to educate them on this score, EFF co-founder John Gilmore built a $250,000 computer that could break the (already broken) cryptography the NSA and other spy agencies claimed businesses could rely on, in just a couple hours. The message of this DES Cracker was that anyone with $250,000 will be able to break into the communications of any American business:
https://cryptome.org/jya/des-cracker.htm
Fun fact: John got tired of the bar-fridge-sized DES Cracker cluttering up his garage and he sent it to my house for safekeeping; it’s in my office next to my desk in LA. If I ever move to the UK, I’ll have to leave it behind because it’s (probably) still illegal to export.
The deadlock might have never been broken but for a key lawsuit: Cindy Cohn (now EFF’s executive director) won the Bernstein case, which established that publishing cryptographic source-code was protected by the First Amendment:
https://www.eff.org/cases/bernstein-v-us-dept-justice
With cryptography legalized, browser vendors set about securing the data-layer in earnest, expanding and formalizing the “public key infrastructure” (PKI) in browsers. Here’s how that works: your browser ships with a list of cryptographic keys from trusted “certificate authorities.” These are entities that are trusted to issue “certificates” to web-hosts, which are used to wrap up their messages to you.
When you open a connection to “https://foo.com," Foo sends you a stream of data that is encrypted with a key identified as belonging to “foo.com” (this key is Foo’s “certificate” — it certifies that the user of this key is Foo, Inc). That certificate is, in turn, signed by a “Certificate Authority.”
Any Certificate Authority can sign any certificate — your browser ships with a long list of these CAs, and if any one of them certifies that the bearer is “Foo.com,” that server can send your browser “secure” traffic and it will dutifully display the data with all assurances that it arrived from one of Foo, Inc’s servers.
This means that you are trusting all of the Certificate Authorities that come with your browser, and you’re also trusting the company that made your browser to choose good Certificate Authorities. This is a lot of trust. If any of those CAs betrays your trust and issues a bad cert, it can be used to reveal, copy, and alter the data you send and receive from a server that presents that certificate.
You’d hope that certificate authorities would be very prudent, cautious and transparent — and that browser vendors would go to great lengths to verify that they were. There are PKI models for this: for example, the “DNS root keys” that control the internet’s domain-name service are updated via a formal, livestreamed ceremony:
https://www.cloudflare.com/dns/dnssec/root-signing-ceremony/
There are 14 people entrusted to perform this ceremony, and at least three must be present at each performance. The keys are stored at two facilities, and the attendees need to show government ID to enter them (is the government that issued the ID trustworthy? Do you trust the guards to verify it? Ugh, my head hurts).
Further access to the facility is controlled by biometric locks (do you trust the lock maker? How about the person who registers the permitted handprints?). Everyone puts a wet signature in a logbook. A staffer has their retina scanned and presents a smartcard.
Then the staffer opens a safe that has a “tamper proof” (read: “tamper resistant”) hardware module whose manufacturer is trusted (why?) not to have made mistakes or inserted a back-door. A special laptop (also trusted) is needed to activate the safe’s hardware module. The laptop “has no battery, hard disk, or even a clock backup battery, and thus can’t store state once it’s unplugged.” Or, at least, the people in charge of it claim that it doesn’t and can’t.
The ceremony continues: the safe yields a USB stick and a DVD. Each of the trusted officials hands over a smart card that they trust and keep in a safe deposit box in a tamper-evident bag. The special laptop is booted from the trusted DVD and mounts the trusted USB stick. The trusted cards are used to sign three months worth of keys, and these are the basis for the next quarter’s worth of secure DNS queries.
All of this is published, videoed, livestreamed, etc. It’s a real “defense in depth” situation where you’d need a very big conspiracy to subvert all the parts of the system that need to work in order to steal underlying secrets. Yes, bottom line, you’re still trusting people, but in part you’re trusting them not to be able to all keep a secret from the rest of us.
The process for determining which CAs are trusted by your browser is a lot less transparent and, judging from experience, a lot less thorough. Many of these CAs have proven to be manifestly untrustworthy over the years. There was Diginotar, a Dutch CA whose bad security practices left it vulnerable to a hack-attack:
https://en.wikipedia.org/wiki/DigiNotar
Some people say it was Iranian government hackers, who used its signing keys to forge certificates and spy on Iranian dissidents, who are liable to arrest, torture and execution. Other people say it was the NSA pretending to be Iranian government hackers:
https://www.schneier.com/blog/archives/2013/09/new_nsa_leak_sh.html
In 2015, the China Internet Network Information Center was used to issue fake Google certificates, which gave hackers the power to intercept and take over Google accounts and devices linked to them (e.g. Android devices):
https://thenextweb.com/news/google-to-drop-chinas-cnnic-root-certificate-authority-after-trust-breach
In 2019, the UAE cyber-arms dealer Darkmatter — an aggressive recruiter of American ex-spies — applied to become a trusted Certificate Authority, but was denied:
https://www.reuters.com/investigates/special-report/usa-spying-raven/
Browser PKI is very brittle. By design, any of the trusted CAs can compromise every site on the internet. An early attempt to address this was “certificate pinning,” whereby browsers shipped with a database of which CAs were authorized to issue certificates for major internet companies. That meant that even though your browser trusted Crazy Joe’s Discount House of Certification to issue certs for any site online, it also knew that Google didn’t use Crazy Joe, and any google.com certs that Crazy Joe issued would be rejected.
But pinning has a scale problem: there are billions of websites and many of them change CAs from time to time, which means that every browser now needs a massive database of CA-site pin-pairs, and a means to trust the updates that site owners submit to browsers with new information about which CAs can issue their certificates.
Pinning was a stopgap. It was succeeded by a radically different approach: surveillance, not prevention. That surveillance tool is Certificate Transparency (CT), a system designed to quickly and publicly catch untrustworthy CAs that issue bad certificates:
https://www.nature.com/articles/491325a
Here’s how Certificate Transparency works: every time your browser receives a certificate, it makes and signs a tiny fingerprint of that certificate, recording the date, time, and issuing CA, as well as proof that the CA signed the certificate with its private key. Every few minutes, your browser packages up all these little fingerprints and fires them off to one or more of about a dozen public logs:
https://certificate.transparency.dev/logs/
These logs use a cool cryptographic technology called Merkle trees that make them tamper-evident: that means that if some alters the log (say, to remove or forge evidence of a bad cert), everyone who’s got a copy of any of the log’s previous entries can tell that the alteration took place.
Merkle Trees are super efficient. A modest server can easily host the eight billion or so CT records that exist to date. Anyone can monitor any of these public logs, checking to see whether a CA they don’t recognize has issued a certificate for their own domain, and then prove that the CA has betrayed its mission.
CT works. It’s how we learned that Symantec engaged in incredibly reckless behavior: as part of their test-suite for verifying a new certificate-issuing server, they would issue fake Google certificates. These were supposed to be destroyed after creation, but at least one leaked and showed up in the CT log:
https://arstechnica.com/information-technology/2017/03/google-takes-symantec-to-the-woodshed-for-mis-issuing-30000-https-certs/
It wasn’t just Google — Symantec had issued tens of thousands of bad certs. Worse: Symantec was responsible for more than a third of the web’s certificates. We had operated on the blithe assumption that Symantec was a trustworthy entity — a perfectly spherical cow of uniform density — but on inspection it was proved to be a sloppy, reckless mess.
After the Symantec scandal, browser vendors cleaned house — they ditched Symantec from browsers’ roots of trust. A lot of us assumed that this scandal would also trigger a re-evaluation of how CAs demonstrated that they were worth of inclusion in a browser’s default list of trusted entities.
If that happened, it wasn’t enough.
Yesterday, the Washington Post’s Joseph Menn published an in-depth investigation into Trustcor, a certificate authority that is trusted by default by Safari, Chrome and Firefox:
https://www.washingtonpost.com/technology/2022/11/08/trustcor-internet-addresses-government-connections/
Menn’s report is alarming. Working from reports from University of Calgary privacy researcher Joel Reardon and UC Berkeley security researcher Serge Egelman, Menn presented a laundry list of profoundly disturbing problems with Trustcor:
https://groups.google.com/a/mozilla.org/g/dev-security-policy/c/oxX69KFvsm4/m/etbBho-VBQAJ
First, there’s an apparent connection to Packet Forensics, a high-tech arms dealer that sells surveillance equipment to the US government. One of Trustcor’s partners is a holding company managed by Packet Forensics spokesman Raymond Saulino.
If Trustcor is working with (or part of) Packet Forensics, it could issue fake certificates for any internet site that Packet Forensics could use to capture, read and modify traffic between that site and any browser. One of Menn’s sources claimed that Packet Forensics “used TrustCor’s certificate process and its email service, MsgSafe, to intercept communications and help the U.S. government.”
Trustcor denies this, as did the general counsel for Packet Forensics.
Should we trust either of them? It’s hard to understand why we would. Take Trustcor: as mentioned, it has a “private” email service called “Msgsafe,” that claims to offer end-to-end encrypted email. But it is not encrypted end-to-end — it sends copies of its users’ private keys to Trustcor, allowing the company (or anyone who hacks the company) to intercept its email.
It’s hard to avoid the conclusion that Trustcor is making an intentionally deceptive statement about how its security products work, or it lacks the basic technical capacity to understand how those products should work. You’d hope that either of those would disqualify Trustcor from being trusted by default by billions of browsers.
It’s worse than that, though: there are so many red flags about Trustcor beyond the defects in Msgsafe. Menn found that that company’s website identified two named personnel, both supposed founders. One of those men was dead. The other one’s Linkedin profile has him departing the company in 2019.
The company lists two phone numbers. One is out of service. The other goes to unmonitored voicemail. The company’s address is a UPS Store in Toronto. Trustcor’s security audits are performed by the “Princeton Audit Group” whose address is a private residence in Princeton, NJ.
A company spokesperson named Rachel McPherson publicly responded to Menn’s article and Reardon and Egelman’s report with a bizarre, rambling message:
https://groups.google.com/a/mozilla.org/g/dev-security-policy/c/oxX69KFvsm4/m/X_6OFLGfBQAJ
In it, McPherson insinuates that Reardon and Egelman are just trying to drum up business for a small security research business they run called Appsecure. She says that Msgsafe’s defects aren’t germane to Trustcor’s Certificate Authority business, instead exhorting the researchers to make “positive suggestions for improving that product suite.”
As to the company’s registration, she makes a difficult-to-follow claim that the irregularities are due to using the same Panamanian law-firm as Packet Forensics, says that she needs to investigate some missing paperwork, and makes vague claims about “insurance impersonation” and “potential for foul play.”
Certificate Authorities have one job: to be very, very, very careful. The parts of Menn’s story and Reardon and Egelman’s report that aren’t disputed are, to my mind, enough to disqualify them from inclusion in browsers’ root of trust.
But the disputed parts — which I personally believe, based on my trust in Menn, which comes from his decades of careful and excellent reporting — are even worse.
For example, Menn makes an excellent case that Packet Forensics is not credible. In 2007, a company called Vostrom Holdings applied for permission for Packet Forensics to do business in Virginia as “Measurement Systems.” Measurement Systems, in turn, tricked app vendors into bundling spyware into their apps, which gathered location data that Measurement Systems sold to private and government customers. Measurement Systems’ data included the identities of 10,000,000 users of Muslim prayer apps.
Packet Forensics denies that it owns Measurement Systems, which doesn’t explain why Vostrom Holdings asked the state of Virginia to let it do business as Measurement Systems. Vostrom also owns the domain “Trustcor.co,” which directed to Trustcor’s main site. Trustcor’s “president, agents and holding-company partners” are identical to those of Measurement Systems.
One of the holding companies listed in both Trustcor and Measurement Systems’ ownership structures is Frigate Bay Holdings. This March, Raymond Saulino — the one-time Packet Forensics spokesman — filed papers in Wyoming identifying himself as manager of Frigate Bay Holdings.
Neither Menn nor Reardon and Egelman claim that Packet Forensics has obtained fake certificates from Trustcor to help its customers spy on their targets, something that McPherson stresses in her reply. However, Menn’s source claims that this is happening.
These companies are so opaque and obscure that it might be impossible to ever find out what’s really going on, and that’s the point. For the web to have privacy, the Certificate Authorities that hold the (literal) keys to that privacy must be totally transparent. We can’t assume that they are perfectly spherical cows of uniform density.
In a reply to Reardon and Egelman’s report, Mozilla’s Kathleen Wilson asked a series of excellent, probing followup questions for Trustcor, with the promise that if Trustcor failed to respond quickly and satisfactorily, it would be purged from Firefox’s root of trust:
https://groups.google.com/a/mozilla.org/g/dev-security-policy/c/oxX69KFvsm4/m/WJXUELicBQAJ
Which is exactly what you’d hope a browser vendor would do when one of its default Certificate Authorities was credibly called into question. But that still leaves an important question: how did Trustcor, who marketed a defective security product, whose corporate ownership is irregular and opaque with a seeming connection to a cyber-arms-dealer, end up in our browsers’ root of trust to begin with?
Formally, the process for inclusion in the root of trust is quite good. It’s a two-year vetting process that includes an external audit:
https://wiki.mozilla.org/CA/Application_Process
But Daniel Schwalbe, CISO of Domain Tools, told Menn that this process was not closely watched, claiming “With enough money, you or I could become a trusted root certificate authority.” Menn’s unnamed Packet Forensics source claimed that most of the vetting process was self-certified — that is, would-be CAs merely had to promise they were doing the right thing.
Remember, Trustcor isn’t just in Firefox’s root of trust — it’s in the roots of trust for Chrome (Google) and Safari (Apple). All the major browser vendors were supposed to investigate this company and none of them disqualified it, despite all the vivid red flags.
Worse, Reardon and Egelman say they notified all three companies about the problems with Trustcor seven months ago, but didn’t hear back until they published their findings publicly on Tuesday.
There are 169 root certificate authorities in Firefox, and comparable numbers in the other major browsers. It’s inconceivable that you could personally investigate each of these and determine whether you want to trust it. We rely on the big browser vendors to do that work for us. We start with: “Assume the browser vendors are careful and diligent when it comes to trusting companies on our behalf.” We assume that these messy, irregular companies are perfectly spherical cows of uniform density on a frictionless surface.
The problem of trust is everywhere. Vaccine deniers say they don’t trust the pharma companies not to kill them for money, and don’t trust the FDA to hold them to account. Unless you have a PhD in virology, cell biology and epidemiology, you can’t verify the claims of vaccine safety. Even if you have those qualifications, you’re trusting that the study data in journals isn’t forged.
I trust vaccines — I’ve been jabbed five times now — but I don’t think it’s unreasonable to doubt either Big Pharma or its regulators. A decade ago, my chronic pain specialist told me I should take regular doses of powerful opioids, and pooh-poohed my safety and addiction concerns. He told me that pharma companies like Purdue and regulators like the FDA had re-evaluated the safety of opioids and now deemed them far safer.
I “did my own research” and concluded that this was wrong. I concluded that the FDA had been captured by a monopolistic and rapacious pharma sector that was complicit in waves of mass-death that produced billions in profits for the Sackler family and other opioid crime-bosses.
I was an “opioid denier.” I was right. The failure of the pharma companies to act in good faith, and the failure of the regulator to hold them to account is a disaster that has consequences beyond the mountain of overdose deaths. There’s a direct line from that failure to vaccine denial, and another to the subsequent cruel denial of pain meds to people who desperately need them.
Today, learning that the CA-vetting process I’d blithely assumed was careful and sober-sided is so slapdash that a company without a working phone or a valid physical address could be trusted by billions of browsers, I feel like I did when I decided not to fill my opioid prescription.
I feel like I’m on the precipice of a great, epistemological void. I can’t “do my own research” for everything. I have to delegate my trust. But when the companies and institutions I rely on to be prudent (not infallible, mind, just prudent) fail this way, it makes me want to delete all the certificates in my browser.
Which would, of course, make the web wildly insecure.
Unless it’s already that insecure.
Ugh.
Image:
Curt Smith (modified)
https://commons.wikimedia.org/wiki/File:Sand_castle,_Cannon_Beach.jpg
CC BY 2.0:
https://creativecommons.org/licenses/by/2.0/deed.en
[Image ID: An animated gif of a sand-castle that is melting into the rising tide; through the course of the animation, the castle gradually fills up with a Matrix-style 'code waterfall' effect.]
350 notes
·
View notes
Text
the year is 2048. a smiling young farmer in a power wheelchair sells me the biggest bag of muesli I've ever seen out of a market stall built from repurposed drone parts. he sees the toys in my reusable bag and insists on throwing in some homemade cat treats “on the house”. I get an email from the wind farm: they've deposited another $20 in my account for using up excess electricity outside peak hours, so I decide to splurge on some flavoured honey and boba tea. I tell the barista I feel like a billionaire today and she smiles politely and asks me what a “billionaire” is. I run into an old friend handing out free insulin packets and we spend some time catching up. I've got a new gig at the organ printing depot and she's on rotating job assignments with the Workers' Cooperative: this month is insulin distribution, last month was reprogramming robot dogs as automated planters for the pollinator farm, next month she'll be on a work crew converting the old football stadium into a greenhouse. She's been sleeping in the park (by choice, of course, the local housing co-op has tons of suites open) but the climate bureau is cloud seeding this weekend and we're expecting a lot of rain. I invite her to crash at my place. She smiles and says she would like that. Our trolley ride home is briefly halted by an impromptu pride parade and the sun is setting as we pass the ivy-covered sign advertising the golf course that once existed where my neighbourhood now stands. A friendly technician explains she's just finished replacing the faulty router on our block so we can use the public WiFi again. I start a fire in the fireplace and sort through some mail: a postcard from one of my exes in Hawaii installing carbon dioxide scrubbers that double as frog habitats, a flyer for a music recital at the rehab clinic, and a letter from International Blood Services declining my donation because they are fully stocked. I ask my Global Music Archive uplink to select a random decade, country and genre and it starts a playlist while the two of us snuggle together on the couch under a hand-knitted blanket and my cat makes biscuits on top. On TV, a newscaster says global temperatures are at their lowest point in the last 40 years. I flip channels to some standup comedian saying kids these days don't know how to conceal when they're high because there's no cops anymore. We laugh until the rain softly falling on the roof lulls us to sleep.
#microfiction#hope for the future#a post by me™#this deserved its own post i hope it brightens someone's day
44 notes
·
View notes
Text
“The threats of data colonialism are real,” says Tahu Kukutai, a professor at New Zealand’s University of Waikato and a founding member of Te Mana Raraunga, the Māori Data Sovereignty Network. “They’re a continuation of old processes of extraction and exploitation of our land—the same is being done to our information.”
To shore up their defenses, some Indigenous groups are developing new privacy-first storage systems that give users control and agency over all aspects of this information: what is collected and by whom, where it’s stored, how it’s used and, crucially, who has access to it.
Storing data in a user’s device—rather than in the cloud or in centralized servers controlled by a tech company—is an essential privacy feature of these technologies. Rudo Kemper is founder of Terrastories, a free and open-source app co-created with Indigenous communities to map their land and share stories about it. He recalls a community in Guyana that was emphatic about having an offline, on-premise installation of the Terrastories app. To members of this group, the issue was more than just the lack of Internet access in the remote region where they live. “To them, the idea of data existing in the cloud is almost like the knowledge is leaving the territory because it’s not physically present,” Kemper says.
Likewise, creators of Our Data Indigenous, a digital survey app designed by academic researchers in collaboration with First Nations communities across Canada, chose to store their database in local servers in the country rather than in the cloud. (Canada has strict regulations on disclosing personal information without prior consent.) In order to access this information on the go, the app’s developers also created a portable backpack kit that acts as a local area network without connections to the broader Internet. The kit includes a laptop, battery pack and router, with data stored on the laptop. This allows users to fill out surveys in remote locations and back up the data immediately without relying on cloud storage.
50 notes
·
View notes
Text
Character Voice Tag
Rules: rewrite the line in the voices of your OCs, then come up with a new line for the next person
I got two, so thanks @illarian-rambling and @willtheweaver for the tags! My lines are, “Oh damn, the wifi stopped working,” and, “Quiet down, I’m trying to sleep.”
Line 1: “Oh damn, the wifi stopped working.”
Belladonna: “The wifi is down. I’ll contact a technician.”
Cassie: “Fucking wifi, what the fuck is wrong with you?” *rests her hand in the router* “All right, what’s your fucking problem?”
Nellie: “I think the internet stopped working.”
Narcissus: “My wifi is down? My wifi is down??? What happened? Has someone been tampering with it? How dare they? Who would want to sabotage me? Well, everyone, I suppose - they’re all jealous - but who would dare???”
Ricinus: “Our wifi’s down again? I’m going to fire that useless technician.”
Goldenrod: “Can you believe it? The wifi’s gone out again. With all we pay that technician, I can’t believe they can’t keep up.”
Cassiopeia: “Why is the wifi out again? Get it fixed.”
Stellaris: “Wait. Why isn’t my internet working? I was going to study my Old World history and now my schedule is all mixed up!” *starts stressed-stimming aggressively, trying not to cry*
Rhys: “Is the internet not working? I didn’t notice.”
Line 2: “Quiet down, I’m trying to sleep.”
Belladonna: “Can you snore a bit more quietly? I’m trying to get a bit of sleep.”
Cassie: “Shut the fuck up, I want to sleep.”
Nellie: “Would you be able to be a bit quieter? I have trouble sleeping.”
Narcissus: “Be quiet! This instant! I’m getting my beauty sleep, don’t you dare deprive me of that.”
Ricinus: “Be quiet, I’m sleeping.”
Goldenrod: “Darling, you keep waking me up, and I’m just so tired. Can’t you be quieter and let me sleep?”
Cassiopeia: “Quiet down and let me sleep or I’ll have you flogged.”
Stellaris: “Can you stop making that sound? It makes my ears hurt. You’re not making a sound? But I can hear it. Please stop. Oh. No? Okay.”
Rhys: *considers asking but just plugs his ears instead*
These were very fun! Thank you two again for the tags! I’m going to offer this one to @kaylinalexanderbooks @modernwritercraft and @marigold-clouds - your line is, “It’ll be fun, come on!”
17 notes
·
View notes
Text
Router-Konfiguration und -Management - Innoscale macht's einfach!
In der heutigen digitalen Welt ist ein zuverlässiges Netzwerk für jedes Unternehmen unerlässlich. Ein Router ist dabei ein wichtiges Gerät, das für die Verbindung Ihrer Geräte mit dem Internet sorgt. Die Konfiguration und Verwaltung eines Routers kann jedoch für einige Benutzer eine Herausforderung darstellen.

In diesem Beitrag wollen wir Ihnen zeigen, wie einfach die Router-Konfiguration und -Verwaltung mit Innoscale sein kann. Innoscale ist ein Anbieter digitaler Dienstleistungen, der sich zum Ziel gesetzt hat, alle digitalen Bedürfnisse Ihres KMU zu erfüllen. Dazu gehört auch die Unterstützung bei der Einrichtung und Verwaltung Ihres Netzwerks.
Was ist Router-Konfiguration und -Verwaltung?
Die Router-Konfiguration ist der Prozess der Einrichtung Ihres Routers, so dass er ordnungsgemäß funktioniert. Dazu gehört unter anderem die Einrichtung Ihrer Wi-Fi-Verbindung, die Festlegung von Sicherheitseinstellungen und die Priorisierung von Geräten.
Die Router-Verwaltung bezieht sich auf die laufende Wartung Ihres Routers. Dazu gehört die Überwachung der Netzwerkverbindung, die Fehlerbehebung bei Problemen und die Aktualisierung der Router-Firmware.
Warum ist die Router-Konfiguration und -Verwaltung wichtig?
Eine ordnungsgemäße Router-Konfiguration und -Verwaltung ist aus mehreren Gründen wichtig:
Sicherheit: Ein falsch konfigurierter Router kann Ihr Netzwerk anfällig für Sicherheitsbedrohungen machen. Durch die Einrichtung starker Sicherheitseinstellungen können Sie Ihr Netzwerk vor unbefugtem Zugriff schützen.
Leistung: Eine optimale Routerkonfiguration kann die Leistung Ihres Netzwerks verbessern. Dazu gehört die Optimierung der Wi-Fi-Einstellungen und die Priorisierung von Geräten, die eine höhere Bandbreite benötigen.
Zuverlässigkeit: Durch die regelmäßige Überwachung Ihres Routers und die Aktualisierung der Firmware können Sie Netzwerkprobleme verhindern und die Zuverlässigkeit Ihres Netzwerks verbessern.
Wie kann Innoscale Ihnen helfen?
Innoscale bietet eine Reihe von Dienstleistungen an, die Ihnen bei der Router-Konfiguration und -Verwaltung helfen können:
Beratung: Unsere IT-Experten beraten Sie bei der Auswahl des richtigen Routers für Ihr Unternehmen und helfen Ihnen bei der Einrichtung.
Konfiguration: Wir können Ihren Router für Sie konfigurieren und die optimalen Einstellungen vornehmen.
Verwaltung: Wir bieten laufende Überwachungs- und Wartungsdienste an, um sicherzustellen, dass Ihr Netzwerk reibungslos funktioniert.
Mit Innoscale können Sie sich darauf konzentrieren, Ihr Unternehmen zu führen, während wir uns um die technischen Details kümmern.
Zusätzliche Informationen:
In diesem Beitrag haben wir Ihnen einen kurzen Überblick über die Router-Konfiguration und -Verwaltung gegeben und erklärt, warum sie für Ihr Unternehmen wichtig ist. Wir haben Ihnen auch erklärt, wie Innoscale Ihnen helfen kann.
Wenn Sie mehr über unsere Router-Konfigurations- und - Verwaltungsdienste erfahren möchten, besuchen Sie bitte unsere Website oder kontaktieren Sie uns noch heute.
#Netzwerk-Sicherheitslösungen#Virtuelle Private Netzwerke (VPN)#Firewall-Installation und Konfiguration#Router-Konfiguration und -Management#IT-Cloud-Lösungen#WLAN-Infrastruktur#Innoscale Holding
0 notes
Text
one good thing about cloud managed switches and routers is I can configure them from my phone while I'm out lol
9 notes
·
View notes
Text
New Cuttlefish Malware Hijacks Router Connections, Sniffs for Cloud Credentials
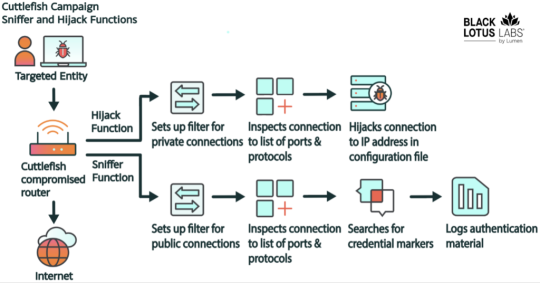
Source: https://thehackernews.com/2024/05/new-cuttlefish-malware-hijacks-router.html
More info: https://blog.lumen.com/eight-arms-to-hold-you-the-cuttlefish-malware/
4 notes
·
View notes
Text
my router shat itself and I won't have time to exchange it until friday, probably
and THIS is why I still keep physical media around!!!!! Fuck everything being on streaming or the cloud or whatever
3 notes
·
View notes