#Azimuth 257
Video
Ye mountains, that far off lift up your heads (Banff National Park) by Mark Stevens
Via Flickr:
Ye mountains, that far off lift up your heads While at Morant’s Curve and the overlook there to the Bow River and mountain peaks and ridges off in the distance. The view is looking to the west. This location is along the Bow Valley Parkway in Banff National Park. The caption used is from a poem. Green Mountains by James Russell Lowell
#Alberta Provincial Highway No. 1A#Alberta and Glacier National Park#Azimuth 257#Banff National Park#Banff-Lake Louise Core Area#Blue Skies#Bow Range#Bow River#Bow Valley Parkway#Canadian Pacific Railway Track#Canadian Rockies#Day 2#DxO PhotoLab 6 Edited#Evergreen Trees#Evergreens#Fairview Mountain#Forest#Forest Landscape#Hillside of Trees#Landscape#Landscape - Scenery#Looking West#Morant's Curve#Mount Aberdeen#Mount Lefroy#Mount Saint Piran#Mount Victoria#Mount Whyte#Mountain Peak#Mountains
3 notes
·
View notes
Text
0 notes
Text
Apple’s Lawsuit Against a Startup Shows How It Wants to Control the iPhone Hacking Market
Apple announced last week that it was willing to pay up to $1.5 million for iPhone bugs, and that it will give security researchers special devices so they can find more vulnerabilities in iOS.
These announcements, made to much fanfare at the Black Hat security conference in Las Vegas, were met with delight and enthusiasm by the jailbreaking and iOS hacking community, who saw this as a “historic moment” for the security of iPhones all over the world.
Just a few days later, Apple appears to have squandered that goodwill by suing a startup that provides virtual versions of iOS to developers and security researchers who look for flaws in iPhones to then sell them in the thriving market for software exploits. In its complaint, Apple argues that Corellium is infringing the company’s copyright by selling a service that allows customers to create virtual versions of iOS.
“Corellium’s business is based entirely on commercializing the illegal replication of the copyrighted operating system and applications that run on Apple’s iPhone, iPad, and other Apple devices,” Apple argued in the complaint. “Recreating with fastidious attention to detail not just the way the operating system and applications appear visually to bona fide purchasers, but also the underlying computer code. Corellium does so with no license or permission from Apple.”
Have a tip about Apple or a Apple-focused security company? You can contact Lorenzo Franceschi-Bicchierai securely on Signal at +1 917 257 1382, OTR chat at [email protected], or email [email protected]
Chris Wade, the founder of Corellium, did not respond to a request for comment. Earlier this year, Motherboard revealed that several security researchers, including Corellium, were buying stolen iPhones “prototypes,” which allowed them to more easily pull apart iOS and find flaws in it, an investigation that Apple references in its lawsuit.
Several security researchers who specialize in finding vulnerabilities and ways to exploit them lashed out at Apple on Twitter, saying that Apple’s crackdown on Corellium would be like Microsoft or other operating system developers going after virtual machines, which are copies of operating systems that can run within other operating systems and are widely used in security research and for other legitimate purposes.
“Hackintosh considered harmful today eh? Lame. Quick way to spend all the goodwill they just built in the community,” wrote Bas Alberts on Twitter, who works at government contractor Immunity.
Matt Suiche, a well-known researcher who developed virtualization software in the past, tweeted: “Imagine what today’s Cloud Computing landscape would look like if VMware had been sued by IBM or Microsoft back in 1998,” referring to the popular virtualization platform VMware. Daniel Cuthbert, a Black Hat review board and a veteran of the infosec community, called it a “poor move” by Apple. Luca Todesco, a well-known iPhone hacker, said this lawsuit is akin to Apple pulling “a Sony,” in reference to the Japanese giant suing security researcher George “Geohot” Hotz, in 2011 for jailbreaking the Playstation 3.
Apple did not respond to a request for comment, but the company defended its position in the complaint, arguing that Corellium encourages its customers to “to sell any discovered information on the open market to the highest bidder,” and that Corellium’s “sole function” is to “enable the creation of “virtual” iOS-operated devices, running unauthorized copies of iOS.”
In other words, Apple really doesn’t like the idea of having security researchers using Corellium to find exploits that may end up being sold to exploit brokers such as Zerodium, or directly to governments like Azimuth Security does.
“You really couldn’t ask for a lawsuit more than Corellium has.”
“Corellium makes no effort whatsoever to confine use of its product to good-faith research and testing of iOS. Nor does Corellium require its users to disclose any software bugs they find to Apple, so that Apple may correct them,” the company wrote. “Instead, Corellium is selling a product for profit, using unauthorized copies of Apple’s proprietary software, that it avowedly intends to be used for any purpose, without limitation, including for the sale of software exploits on the open market.”
In a way, offering special devices and suing Corellium may be part of the same strategy: attempting to control what security researchers do with iPhones. On the other hand, perhaps this was inevitable.
“You really couldn’t ask for a lawsuit more than Corellium has,” said an Apple employee, who spoke on condition of anonymity because he was not authorized to speak to the press.
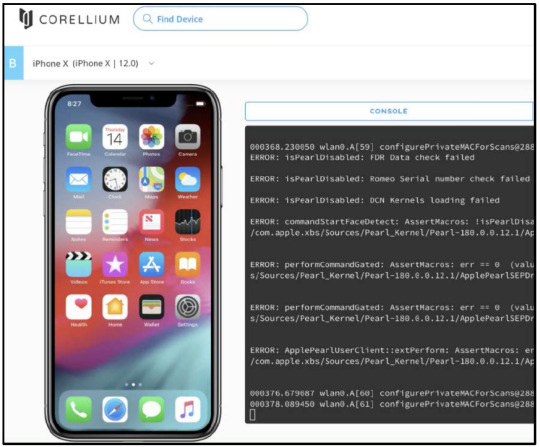
A screenshot of the Corellium interface.
The employee explained that the way Apple licenses its software, you can’t run a virtual version of MacOS on VMware or other virtualization platforms if it’s not running on a Mac computer. Corellium does something similar, but with iOS.
After Apple announced its new bug bounty payouts and the research devices, Corellium’s founder Wade criticized them on Twitter.
“Glad to see Apple opening the bounty to all. But how’s it a fair playing field if not everyone has the same tools? No track record of security research? Tough luck no soup for you,” Wade wrote on Twitter. “Apple has the potential to add serious cloud services revenue from developers but chooses instead to build custom devices for a select few.”
Subscribe to our new cybersecurity podcast, CYBER.
Apple’s Lawsuit Against a Startup Shows How It Wants to Control the iPhone Hacking Market syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes
Video
Seeing Amazing Sights in Grand Staircase-Escalante National Monument by Mark Stevens
Via Flickr:
A setting looking to the west while taking in views across eroded formations present at Devils Garden in Grand Staircase-Escalante National Monument. My thinking in composing this image was to capture a look across some of these nearby formations. I also wanted to balance the earth-tones in the lower portion of the image with the clouds and blues skies. I later worked with control points in DxO PhotoLab 5 and then made some adjustments to bring out the contrast, saturation and brightness I wanted for the final image.
#Azimuth 257#Canyonlands#Cloudy#Colorado Plateau#Day 3#Desert Landscape#Desert Mountain Landscape#Desert Plant Life#Devils Garden#DxO PhotoLab 5 Edited#Eroded Formations#Escalante-Staircase#Grand Staircase-Escalante National Monument#High Desert#Hoodoos#Intermountain West#Landscape#Landscape - Scenery#Layers of Rock#Looking West#Mostly Cloudy#Nature#Nikon D850#No People#Outside#Overcast#Portfolio#Project365#Rolling Hillsides#Sandstone
2 notes
·
View notes
Video
Under the New River Gorge Bridge (New River Gorge National Park & Preserve) by Mark Stevens
Via Flickr:
A view looking to the west across the New River Gorge while standing just out from underneath the namesake bridge. My thinking in composing this image was to have that view looking across and underneath the bridge itself with its intricate structures present. I went with a more leveled-on look across the setting as I felt the angle helped to maximize the arch and other structures of the bridge. While it would have been nice to have had sunny, blue skies that afternoon, the overcast skies did helps to mute the brightness present and allow me to focus more on the bridge. I later worked with control points in DxO PhotoLab 4 and then made some adjustments to bring out the contrast, saturation and brightness I wanted for the final image.
#Allegheny Mountains#Appalachian Mountains#Appalachian Plateaus#Arch Bridge#Azimuth 257#Bridge#Bridge Structure#Cloudy#Day 2#DxO PhotoLab 4 Edited#Forest#Forest Landscape#Hillside of Trees#Landscape#Landscape - Scenery#Looking Up#Looking West#Looking up at Sky#Mostly Cloudy#Nature#New River Gorge#New River Gorge Bridge#New River Gorge National Park & Preserve#New River Gorge National Park and Preserve#New River Gorge and Indiana Dunes National Parks#Nikon D850#No People#Outside#Overcast#Portfolio
2 notes
·
View notes
Video
Seeing Amazing Sights in Grand Staircase-Escalante National Monument by Mark Stevens
Via Flickr:
A setting looking to the west while taking in views across eroded formations present at Devils Garden in Grand Staircase-Escalante National Monument. My thinking in composing this image was to capture a look across some of these nearby formations. I also wanted to balance the earth-tones in the lower portion of the image with the clouds and blues skies. I later worked with control points in DxO PhotoLab 5 and then made some adjustments to bring out the contrast, saturation and brightness I wanted for the final image.
#Azimuth 257#Canyonlands#Cloudy#Colorado Plateau#Day 3#Desert Landscape#Desert Mountain Landscape#Desert Plant Life#Devils Garden#DxO PhotoLab 5 Edited#Eroded Formations#Escalante-Staircase#Grand Staircase-Escalante National Monument#High Desert#Hoodoos#Intermountain West#Landscape#Landscape - Scenery#Layers of Rock#Looking West#Mostly Cloudy#Nature#Nikon D850#No People#Outside#Overcast#Portfolio#Project365#Rolling Hillsides#Sandstone
0 notes
Video
Under the New River Gorge Bridge (New River Gorge National Park & Preserve) by Mark Stevens
Via Flickr:
A view looking to the west across the New River Gorge while standing just out from underneath the namesake bridge. My thinking in composing this image was to have that view looking across and underneath the bridge itself with its intricate structures present. I went with a more leveled-on look across the setting as I felt the angle helped to maximize the arch and other structures of the bridge. While it would have been nice to have had sunny, blue skies that afternoon, the overcast skies did helps to mute the brightness present and allow me to focus more on the bridge. I later worked with control points in DxO PhotoLab 4 and then made some adjustments to bring out the contrast, saturation and brightness I wanted for the final image.
#Allegheny Mountains#Appalachian Mountains#Appalachian Plateaus#Arch Bridge#Azimuth 257#Bridge#Bridge Structure#Cloudy#Day 2#DxO PhotoLab 4 Edited#Forest#Forest Landscape#Hillside of Trees#Landscape#Landscape - Scenery#Looking Up#Looking West#Looking up at Sky#Mostly Cloudy#Nature#New River Gorge#New River Gorge Bridge#New River Gorge National Park & Preserve#New River Gorge National Park and Preserve#New River Gorge and Indiana Dunes National Parks#Nikon D850#No People#Outside#Overcast#Portfolio
1 note
·
View note
Video
The Gift of Going to Great Basin National Park with Wonder Found in Sunflowers by Mark Stevens
Via Flickr:
While walking the Baker Creek Loop with a view looking across a small field of sunflowers I came across. This view is looking to the west and is in Great Basin National Park. I lined up and composed this image using the LCD LiveView screen on my Nikon SLR camera. That allowed me to get the camera much lower to the ground and capture a look across rather than down at the wildflowers.
#Azimuth 257#Baker Creek Loop#Day 7#DxO PhotoLab 5 Edited#Great Basin National Park#Landscape - Scenery#Looking West#Nikon D850#No People#Outside#Portfolio#Project365#Scenics - Nature#SnapBridge#Southern Utah and Great Basin National Parks#Sunflower#Sunflowers#Sunny#Travel#Wildflower#Wildflowers#Nevada#United States#flickr
1 note
·
View note
Video
A Place to Visit Along the Shores of Long Lake (Indiana Dunes National Park) by Mark Stevens
Via Flickr:
While walking the West Beach Trail in Indiana Dunes National Park with a view looking to the west. Here I decided to capture an image looking along the tall grasses of Long Lake. While overcast and even drizzling at times, I was able to work with control points in DxO PhotoLab 4 and then made some adjustments to bring out the contrast, saturation and brightness I wanted for the final image.
#Along Lakeshore#Azimuth 257#Cloudy#Day 5#DxO PhotoLab 4 Edited#Forest#Forest Landscape#Hillside of Trees#Indiana Dunes National Park#Lake#Lake Shoreline#Lakeshore#Landscape#Landscape - Scenery#Looking West#Lower Peninsula-Heartland#Michigan Lower Peninsula#Midwest-Great Lakes Area#Mostly Cloudy#Nature#New River Gorge and Indiana Dunes National Parks#Nikon D850#No People#North America Plains#Outside#Overcast#Project365#Rolling Hillsides#Scenics - Nature#Shore
0 notes
Video
Along the Scenic Drive and Under the New River Gorge Bridge (New River Gorge National Park & Preserve) by Mark Stevens
Via Flickr:
While on the Scenic Drive in the Canyon Rim portion of the national park with a view looking under and across the bridge and river valley. With this image, I used a landscape orientation so that I could capture both of the bridge with its arch and metal support structure as well as include hillside with trees and that more natural setting. There was no real reason in my mind to include more of the bridge going overhead as the overcast skies kind of added that blah feeling for the image.
#Allegheny Mountains#Appalachian Mountains#Appalachian Plateaus#Arch Bridge#Azimuth 257#Bridge#Bridge Structure#Cloudy#Day 2#DxO PhotoLab 4 Edited#Forest#Forest Landscape#Hillside of Trees#Landscape#Landscape - Scenery#Looking Up#Looking West#Looking up at Sky#Mostly Cloudy#Nature#New River Gorge#New River Gorge Bridge#New River Gorge National Park & Preserve#New River Gorge National Park and Preserve#New River Gorge and Indiana Dunes National Parks#Nikon D850#No People#Outside#Overcast#Portfolio
1 note
·
View note
Video
The Gift of Going to Great Basin National Park with Wonder Found in Sunflowers by Mark Stevens
Via Flickr:
While walking the Baker Creek Loop with a view looking across a small field of sunflowers I came across. This view is looking to the west and is in Great Basin National Park. I lined up and composed this image using the LCD LiveView screen on my Nikon SLR camera. That allowed me to get the camera much lower to the ground and capture a look across rather than down at the wildflowers.
#Azimuth 257#Baker Creek Loop#Day 7#DxO PhotoLab 5 Edited#Great Basin National Park#Landscape - Scenery#Looking West#Nikon D850#No People#Outside#Portfolio#Project365#Scenics - Nature#SnapBridge#Southern Utah and Great Basin National Parks#Sunflower#Sunflowers#Sunny#Travel#Wildflower#Wildflowers#Nevada#United States#flickr
0 notes
Video
A Place to Visit Along the Shores of Long Lake (Indiana Dunes National Park) by Mark Stevens
Via Flickr:
While walking the West Beach Trail in Indiana Dunes National Park with a view looking to the west. Here I decided to capture an image looking along the tall grasses of Long Lake. While overcast and even drizzling at times, I was able to work with control points in DxO PhotoLab 4 and then made some adjustments to bring out the contrast, saturation and brightness I wanted for the final image.
#Along Lakeshore#Azimuth 257#Cloudy#Day 5#DxO PhotoLab 4 Edited#Forest#Forest Landscape#Hillside of Trees#Indiana Dunes National Park#Lake#Lake Shoreline#Lakeshore#Landscape#Landscape - Scenery#Looking West#Lower Peninsula-Heartland#Michigan Lower Peninsula#Midwest-Great Lakes Area#Mostly Cloudy#Nature#New River Gorge and Indiana Dunes National Parks#Nikon D850#No People#North America Plains#Outside#Overcast#Project365#Rolling Hillsides#Scenics - Nature#Shore
2 notes
·
View notes
Video
Along the Scenic Drive and Under the New River Gorge Bridge (New River Gorge National Park & Preserve) by Mark Stevens
Via Flickr:
While on the Scenic Drive in the Canyon Rim portion of the national park with a view looking under and across the bridge and river valley. With this image, I used a landscape orientation so that I could capture both of the bridge with its arch and metal support structure as well as include hillside with trees and that more natural setting. There was no real reason in my mind to include more of the bridge going overhead as the overcast skies kind of added that blah feeling for the image.
#Allegheny Mountains#Appalachian Mountains#Appalachian Plateaus#Arch Bridge#Azimuth 257#Bridge#Bridge Structure#Cloudy#Day 2#DxO PhotoLab 4 Edited#Forest#Forest Landscape#Hillside of Trees#Landscape#Landscape - Scenery#Looking Up#Looking West#Looking up at Sky#Mostly Cloudy#Nature#New River Gorge#New River Gorge Bridge#New River Gorge National Park & Preserve#New River Gorge National Park and Preserve#New River Gorge and Indiana Dunes National Parks#Nikon D850#No People#Outside#Overcast#Portfolio
0 notes
Text
iPhone Research Tool Sued by Apple Says It’s Just Like a PlayStation Emulator
A cybersecurity startup embroiled in a copyright lawsuit with Apple over a product that lets customers analyze the iPhone's operating system has fired back, saying its system is just like a video game emulator. It has called the suit a "blatant power grab."
On Monday, Corellium, a Florida-based startup that sells a system that allows customers to tinker with and analyze virtual versions of Apple’s mobile operating system iOS (but not devices themselves), as well as Google’s Android, filed a motion for summary judgment. In the filing, Corellium argues that its software does not infringe on Apple’s copyright as it does not contain any copyrighted code, nor was it made using any copyrighted material. Moreover, its lawyers argued, Corellium’s products are protected by fair use.
Corellium also accused Apple of inappropriately using copyright law to control what independent security researchers can do with their research on iPhones. When Apple sued Corellium in August of last year, Motherboard reported that the real reason behind the lawsuit was precisely that: an attempt to control the flourishing market for iOS vulnerabilities and exploits.
Besides security professionals, Motherboard viewed leaked marketing materials that show Corellium was courting customers with government security clearances, and the company’s filing says its customers work to protect U.S. citizens.
“Apple would love to be the fox guarding the hen house," Corellium wrote in its filing. "But, by operation of law, we are entitled to dig into and learn from the devices in our stores and the software programs that are made available online. By this lawsuit, Apple has asserted that within its bundle of rights is the right to keep security researchers out of its publicly available code."
“This is a blatant power grab and a purposeful attempt to secure a monopoly to prevent independent researchers from being able to hold Apple accountable and injure its reputation," the filing continues.
“Apple would love to be the fox guarding the hen house”
Corellium made the argument that its product is just like the infamous PlayStation emulator Virtual Game Station, made by Connectix, which allowed people to run PlayStation games on their PCs. Sony sued the company and lost the suit. Corellium also said the case of Google Books winning a lawsuit against authors that claimed the product was infringing their copyrights should be considered a favorable precedent. In both cases, according to Corellium, judges found that these products were a transformative use of the original works, and thus did not infringe on copyright.
“Like Connectix, Corellium has created an entirely new product through which iOS can be studied and tested in an entirely new environment,” the company argued. “Corellium has not created a clone of an Apple device; it has transformed the field of security research for mobile operating systems entirely.”
A Corellium lawyer declined to comment. The company’s founder, Chris Wade, did not respond to a request for comment.
Apple did not immediately respond to a request for comment.
Do you work or used to work at Corellium? Or have you used Corellium for your work? Or otherwise, do you know anything about Corellium that you think we should know? We’d love to hear from you. You can contact Lorenzo Franceschi-Bicchierai securely on Signal at +1 917 257 1382, OTR chat at [email protected], or email [email protected]
Two copyright lawyers who reviewed the filing agreed that it makes strong arguments in favor of Corellium, but that it may not be enough to convince the judge at this stage of the lawsuit.
“Corellium does raise good points—its iOS emulator is highly transformative if the usage for security purposes is considered, and its product is unlikely to supplant the market for Apple’s own products,” Tom Dietrich, a senior attorney at the McArthur law firm in Los Angeles who specializes in intellectual property, told Motherboard.
According to Stan Adams, the deputy general counsel at the Center for Democracy and Technology, the relevant question in this case is whether Corellium used copyrighted material to develop its product, but the company “seems to deflect this question and instead focuses on the use of its product by researchers.”
Leaked marketing materials obtained by Motherboard show that the company was also courting customers with security clearance, and the lawsuit hints at government customers.
According to a partially redacted passage in the suit, some of its customers “use Corellium for highly socially-beneficial research that protects not only end users of mobile operating systems and applications but also the citizens of the United States.”
“Premium support is encouraged for any customers requiring security clearance,” the brochure explains, likely referring to security researchers, like Corellium’s customer Azimuth Security, who sell zero-day vulnerabilities and hacking tools to governments.
Corellium’s version of its product where the company ships special servers to customers (it also has a cloud offering) has two tiers: for a 24-core server the cost is $50,000, and $100,000 for a 60-core server, according to the brochure.
Any additional server costs $25,000 and $50,000 respectively. If customers want the module to analyze the Security Enclave Processor, or SEP, which is a key iPhone component that handles data encryption, that costs another $50,000 or $100,000 depending on the type of server they chose. For the iBoot module, the part of iOS responsible for ensuring a trusted boot of the operating system, there’s another extra $50,000 or $100,000. Premium support cost $50,000 in both cases.
In perhaps the most unexpected passage in the filing, Corellium cites a classic line from Spider-Man’s Uncle Ben:
“‘[W]ith great power there must also come—great responsibility!’ Apple has hundreds of millions of portable supercomputers in the pockets and homes of Americans,” the company wrote. “Many households have several of these devices, which, in addition to storing and sharing our personal data, have sensitive microphones and high definition cameras. We must ensure that our devices are secure.”
This story was updated to include information about Apple's own motion for summary judgment.
Subscribe to our new cybersecurity podcast, CYBER.
iPhone Research Tool Sued by Apple Says It’s Just Like a PlayStation Emulator syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes
Text
Apple’s Copyright Lawsuit Has Created a ‘Chilling Effect’ on Security Research
Last year, Apple accused a cybersecurity startup based in Florida of infringing its copyright by developing and selling software that allows customers to create virtual iPhone replicas. Critics have called the Apple's lawsuit against the company, called Corellium, “dangerous” as it may shape how security researchers and software makers can tinker with Apple’s products and code.
The lawsuit, however, has already produced a tangible outcome: very few people, especially current and former customers and users, want to talk about Corellium, which sells the eponymous software that virtualizes iPhones and Android devices. During the lawsuit's proceedings, Apple has sought information from companies that have used the tool, which emulates iOS on a computer, allowing researchers to probe potential iPhone vulnerabilities in a forgiving and easy-to-use environment.
“Apple has created a chilling effect,” a security researcher familiar with Corellium's product, who asked to remain anonymous because he wasn’t allowed to talk to the press, told Motherboard.
“Apple has created a chilling effect.”
“I don’t know if they intended it but when they name individuals at companies that have spoken in favor [of Corellium], I definitely believe retribution is possible,” the researcher added, referring to Apple’s subpoena to the spanish finance giant Santander Bank, which named an employee who had Tweeted about Corellium.
Several other cybersecurity researchers expressed fear of retribution from Apple for using Corellium.
A security researcher, who specializes in offensive security and asked to remain anonymous, said that he would definitely “have legal look into it beforehand if I needed [Corellium’s] stuff,” arguing that he’d be wary of Apple getting involved.
Three other researchers who specialize in hacking Apple software declined to comment citing the risk of some sort of retaliation from Apple.
Ivan Rodriguez, a security researcher who tried Corellium for free in the past, said that he “would have to get some legal advice before” purchasing it.
Do you work at Corellium? Or have you used Corellium for your work? We’d love to hear from you. You can contact Lorenzo Franceschi-Bicchierai securely on Signal at +1 917 257 1382, OTR chat at [email protected], or email [email protected]
In January, Apple subpoenaed the defense contractor L3Harris and Santander Bank, requesting information on how they use Corellium, all communications they've had with the startup, internal communications about their products, and any contracts they've signed with the company, among other information.
Mark Dowd, the founder of Azimuth Security, a cybersecurity startup that specializes in developing hacking tools for governments that’s now part of L3Harris, said last year that he couldn’t comment about Corellium “because [Apple] mention[ed] us in the original filing.” (Dowd did not respond to a request for comment this week.)
Apple declined to comment and referred to its court filings against Corellium. In one of them, Apple wrote that “the purpose of this lawsuit is not to encumber good-faith security research, but to bring an end to Corellium’s unlawful commercialization of Apple’s valuable copyrighted works.”
Corellium obviously disagrees.
“This litigation presents an existential threat to an open and healthy security research community not only for Apple products but for consumer devices in general,” the company said in a statement sent by its lawyer. “Apple is using its lawsuit against Corellium to force a dangerous expansion of its dominance, including its ability to pick and choose who performs research and how.”
Some researchers, however, are not afraid of Apple. Elias Naur uses Corellium to test code written in the Go language for mobile operating systems. Before Corellium, Naur said he had to test code on two busted old phones plugged in under his couch. Naur said he’s “not worried Apple will come after Corellium’s customers” and is still using the software.
“Apple v Corellium isn't about jailbreaking, it's about Apple wanting control over Apple research and the bugs that come with it.”
According to cybersecurity experts, Apple legal battle against Corellium is not really about copyright, but trying to control and restrain researchers and companies that develop hacking tools to break into Apple devices, which make up a profitable and ballooning market.
“Apple v Corellium isn't about jailbreaking, it's about Apple wanting control over Apple research and the bugs that come with it,” Marcus Hutchins, a security researcher best known as MalwareTech, said on Twitter. “Their intention is probably to prevent researchers selling bugs to brokers, but you'd be insane to think they'd sanction jailbreaking either.”
In its legal defense, Corellium has argued that its products help researchers find vulnerabilities and ultimately help Apple make safer devices.
On April 20, Apple revealed in a filing that it asked Chris Wade, Corellium’s founder, for all documents and communications relating to him obtaining dev-fused iPhones. As Motherboard reported last year, dev-fused or prototype iPhones are special Apple devices in early stages of development that allow researchers to more easily hack and analyze iOS, as they have some security features disabled. These are “highly confidential” iPhones that “are intended for Apple’s internal testing and development purposes only,” Apple lawyers wrote in the filing.
According to multiple sources who spoke to Motherboard last year, Wade was among several researchers that acquired dev-fused iPhones. Wade has denied this claim.
In this David v. Goliath battle, as Forbes called it, many people are choosing to stay away from David even before seeing who wins.
Subscribe to our new cybersecurity podcast, CYBER.
Apple’s Copyright Lawsuit Has Created a ‘Chilling Effect’ on Security Research syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes
Text
iPhone Emulation Company Sued by Apple Says It’s Making iPhones Safer
A startup that makes replicas of the iPhone that help hackers find vulnerabilities is accusing Apple of suing it in an attempt to shut it down. Corellium also fired back at Apple and claimed the company owes it $300,000.
On Monday, Corellium, the startup that was sued by Apple for alleged copyright infringement in August, filed its response to the lawsuit. Apple alleged that Corellium’s product is illegal, and helps researchers sell hacking tools based on software bugs found in iOS to government agencies that then use them to hack targets. The cybersecurity world was shocked by Apple’s lawsuit, which was seen as an attempt to use copyright as an excuse to control the thriving, and largely legal, market for software vulnerabilities. The lawsuit was filed just a few days after Apple announced it would give researchers special “pre-hacked” devices to allow them to find and report more bugs to the company.
“Through its invitation-only research device program and this lawsuit, Apple is trying to control who is permitted to identify vulnerabilities, if and how Apple will address identified vulnerabilities, and if Apple will disclose identified vulnerabilities to the public at all,” Corellium argues in its response, echoing arguments made by the security research community.
In its response, Corellium essentially argues that using Apple’s code in Corellium is fair use and its product makes the world a better place by helping security researchers inspect the iPhone’s operating system, find flaws in it, and help Apple fix them. With Corellium, researchers can more easily find bugs by creating virtual instances of iOS and test them more quickly, as opposed to having to use actual physical devices. Corellium attempts to illustrate this by including "before" and "after" images in its response that demonstrate what it was like to try to hack the iPhone before it released its software.
A screenshot of a portion of Corellium’s response to Apple.
As Motherboard reported earlier this year, Corellium employees acquired special iPhones from the grey market that are sometimes called “dev-fused” or “prototype” iPhones. These are iPhones loaded with special software that Apple employees and factory workers use for testing, and have fewer security restrictions in place, allowing researchers better access to parts of the phone’s operating system and code. (At the time, Wade denied ever acquiring these devices, but six sources told us that the company did have them.)
Last week, Apple made eBay remove a listing that offered a prototype iPhone for sale for $10,000.
Corellium’s key argument lies on the assumption that Corellium’s customers are looking for bugs with the intention of alerting Apple of their existence.
Do you work or have at Apple or Corellium? We'd love to hear what you think about this lawsuit. You can contact this reporter securely on Signal at +1 917 257 1382, OTR chat at [email protected], or email [email protected]
For now, however, that is only an assumption.
The only customer Corellium names in its response is Azimuth Security, which was acquired by defense contractor L3 last year. As Motherboard reported last year, Azimuth is one of the best companies in the world at finding bugs in iOS, and developing exploits that take advantage of those bugs. Azimuth does not report those bugs to Apple. Instead, it sells hacking tools based on those bugs to law enforcement and intelligence agencies in the United States, UK, Canada, and other countries. Many security researchers who specialize in finding flaws in iOS don’t report bugs to Apple because they prefer to keep the bugs for themselves, or sell them to third parties.
When Motherboard asked today whether they ever reported a bug in iOS found using Corellium, Mark Dowd, the founder of Azimuth, said: “no.”
Another key part of Corellium’s defense is that Apple has known about the company for years and has always been friendly to one of its founders, Chris Wade. Corellium alleges that Apple invited Wade to join its bug bounty program, which rewards researchers who report security vulnerabilities to Apple, in 2017, and even offered him a job years before he founded Corellium. Since then, according to Corellium, Wade reported as many as seven bugs, worth $300,000, for which he has not been paid.
When asked for comment, an Apple spokesperson directed Motherboard to the company's original filing.
Wade was not immediately available to respond to questions.
Researchers had been reluctant to report bugs to Apple after the bug bounty was launched in 2016, and some complained it was hard to get paid. But some researchers have been paid in the last couple of years, as Motherboard reported last year.
Corellium hinted that it knows the real reason why Apple allegedly did not pay Wade for the bugs he found, but the reason is redacted in the response.
The startup asked for permission to file its response under seal to avoid “the possibility of expanding this litigation,” but said in a motion that it believes the response should be published in full.
In an article published on Tuesday, Forbes revealed that Apple was in talks to acquire Wade’s previous startup, which offered a similar product as Corellium. Multiple sources told Motherboard that Apple was in talks to acquire Corellium as well, but those talks did not go anywhere.
iPhone Emulation Company Sued by Apple Says It’s Making iPhones Safer syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes



