Text
Tiny Water Authority in Pennsylvania Hit by Iranian Cyberattack
It was struck by what federal authorities say are Iranian-backed hackers targeting a piece of equipment specifically because it was Israeli-made.
The tiny Aliquippa water authority in western Pennsylvania was perhaps the least-suspecting victim of an international cyberattack.
It had never had outside help in protecting its systems from a cyberattack, either at its existing plant that dates to the 1930s or the new $18.5 million one it is building.
Then it — along with several other water utilities — was struck by what federal authorities say are Iranian-backed hackers targeting a piece of equipment specifically because it was Israeli-made.
“If you told me to list 10 things that would go wrong with our water authority, this would not be on the list,” said Matthew Mottes, the chairman of the authority that handles water and wastewater for about 22,000 people in the woodsy exurbs around a one-time steel town outside Pittsburgh.
The hacking of the Municipal Water Authority of Aliquippa is prompting new warnings from U.S. security officials at a time when states and the federal government are wrestling with how to harden water utilities against cyberattacks.
The danger, officials say, is hackers gaining control of automated equipment to shut down pumps that supply drinking water or contaminate drinking water by reprogramming automated chemical treatments. Besides Iran, other potentially hostile geopolitical rivals, including China, are viewed by U.S. officials as a threat.
A number of states have sought to step up scrutiny, although water authority advocates say the money and the expertise are what is really lacking for a sector of more than 50,000 water utilities, most of which are local authorities that, like Aliquippa’s, serve corners of the country where residents are of modest means and cybersecurity professionals are scarce.
Besides, utilities say, it’s difficult to invest in cybersecurity when upkeep of pipes and other water infrastructure is already underfunded, and some cybersecurity measures have been pushed by private water companies, sparking pushback from public authorities that it is being used as a back door to privatization.
Efforts took on new urgency in 2021 when the federal government’s leading cybersecurity agency reported five attacks on water authorities over two years, four of them ransomware and a fifth by a former employee.
At the Aliquippa authority, Iranian hackers shut down a remotely controlled device that monitors and regulates water pressure at a pumping station. Customers weren’t affected because crews alerted by an alarm quickly switched to manual operation — but not every water authority has a built-in manual backup system.
With inaction in Congress, a handful of states passed legislation to step up scrutiny of cybersecurity, including New Jersey and Tennessee. Before 2021, Indiana and Missouri had passed similar laws. A 2021 California law commissioned state security agencies to develop outreach and funding plans to improve cybersecurity in the agriculture and water sectors.
Legislation died in several states, including Pennsylvania and Maryland, where public water authorities fought bills backed by private water companies.
Private water companies say the bills would force their public counterparts to abide by the stricter regulatory standards that private companies face from utility commissions and, as a result, boost public confidence in the safety of tap water.
“It’s protecting the nation’s tap water,” said Jennifer Kocher, a spokesperson for the National Association of Water Companies. “It is the most economical choice for most families, but it also has a lack of confidence from a lot of people who think they can drink it and every time there’s one of these issues it undercuts the confidence in water and it undercuts people’s willingness and trust in drinking it.”
Opponents said the legislation is designed to foist burdensome costs onto public authorities and encourage their boards and ratepayers to sell out to private companies that can persuade state utility commissions to raise rates to cover the costs.
“This is a privatization bill,” Justin Fiore of the Maryland Municipal League told Maryland lawmakers during a hearing last spring. “They’re seeking to take public water companies, privatize them by expanding the burden, cutting out public funding.”
For many authorities, the demands of cybersecurity tend to fade into the background of more pressing needs for residents wary of rate increases: aging pipes and increasing costs to comply with clean water regulations.
One critic, Pennsylvania state Sen. Katie Muth, a Democrat from suburban Philadelphia’s Montgomery County, criticized a GOP-penned bill for lacking funding.
“People are drinking water that is below standards, but selling out to corporations who are going to raise rates on families across our state who cannot afford it is not a solution,” Muth told colleagues during floor debate on a 2022 bill.
Pennsylvania state Rep. Rob Matzie, a Democrat whose district includes the Aliquippa water authority, is working on legislation to create a funding stream to help water and electric utilities pay for cybersecurity upgrades after he looked for an existing funding source and found none.
“The Aliquippa water and sewer authority? They don’t have the money,” Matzie said in an interview.
In March, the U.S. Environmental Protection Agency proposed a new rule to require states to audit the cybersecurity of water systems.
It was short-lived.
Three states — Arkansas, Missouri and Iowa — sued, accusing the agency of overstepping its authority and a federal appeals court promptly suspended the rule. The EPA withdrew the rule in October, although a deputy national security adviser, Anne Neuberger, told The Associated Press that it could have “identified vulnerabilities that were targeted in recent weeks.”
Two groups that represent public water authorities, the American Water Works Association and the National Rural Water Association, opposed the EPA rule and now are backing bills in Congress to address the issue in different ways.
One bill would roll out a tiered approach to regulation: more requirements for bigger or more complex water utilities. The other is an amendment to Farm Bill legislation to send federal employees called “circuit riders” into the field to help smaller and rural water systems detect cybersecurity weaknesses and address them.
If Congress does nothing, 6-year-old Safe Drinking Water Act standards will still be in place — a largely voluntary regime that both the EPA and cybersecurity analysts say has yielded minimal progress.
Meanwhile, states are in the midst of applying for grants from a $1 billion federal cybersecurity program, money from the 2021 federal infrastructure law.
But water utilities will have to compete for the money with other utilities, hospitals, police departments, courts, schools, local governments and others.
Robert M. Lee, CEO of Dragos Inc., which specializes in cybersecurity for industrial-control systems, said the Aliquippa water authority’s story — that it had no cybersecurity help — is common.
“That story is tens of thousands of utilities across the country,” Lee said.
Because of that, Dragos has begun offering free access to its online support and software that helps detect vulnerabilities and threats for water and electric utilities that draw under $100 million in revenue.
After Russia attacked Ukraine in 2022, Dragos tested the idea by rolling out software, hardware and installation at a cost of a couple million bucks for 30 utilities.
“It was amazing, the feedback,” Lee said. “You wonder, ‘Hey I think I can move the needle in this way’ … and those 30 were like, ‘Holy crap, no one’s ever paid attention to us. No one’s ever tried to get us help.'”
#cybersecurity#kairoscybersecurity#kairoscybersecurityconsultants#security#technology#cybercrime#cyberattack#kairoscybersecuritysolutions#critical infrastructure
0 notes
Text
Hacker hijacks Orange Spain RIPE account to cause BGP havoc

Orange Spain suffered an internet outage today after a hacker breached the company's RIPE account to misconfigure BGP routing and an RPKI configuration.
The routing of traffic on the internet is handled by Border Gateway Protocol (BGP), which allows organizations to associate their IP addresses with autonomous system (AS) numbers and advertise them to other routers they are connected to, known as their peers.
These BGP advertisements create a routing table that propagates to all other edge routers on the internet, allowing networks to know the best route to send traffic to a particular IP address.
However, when a rogue network announces IP ranges usually associated with another AS number, it is possible to hijack those IP ranges to redirect traffic to malicious websites or networks.
According to Cloudflare, this is possible because BGP is built on trust and the routing table will be updated based on which advertiser has the shortest and more specific route.
To prevent this, a new standard called Resource Public Key Infrastructure (RPKI) was created that acts as a cryptographic solution to BGP hijacking.
"Resource Public Key Infrastructure (RPKI) is a cryptographic method of signing records that associate a BGP route announcement with the correct originating AS number," explains a Cloudflare article on RPKI.
By enabling RPKI with a routing body such as ARIN or RIPE, a network can cryptographically certify that only routers under their control can advertise an AS number and their associated IP addresses.
Hacker breaches RIPE account to break BGP
Yesterday, a threat actor named 'Snow' breached the RIPE account of Orange Spain and tweeted to Orange Spain to contact them about getting new credentials.
Since then, the attacker modified the AS number associated with the company's IP addresses, and enabled an invalid RPKI configuration on them.
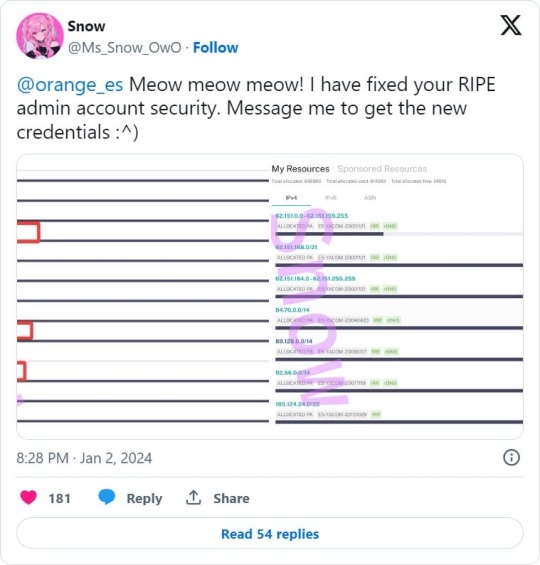
Announcing the IP addresses on someone else's AS number and then enabling RPKI effectively caused these IP addresses to no longer be announced properly on the internet.
"As we see, what they did was create some ROA /12 records, which basically indicate who is the AUTHORITY over a prefix (i.e., the AS that can announce it)," Felipe Cañizares, CTO from DMNTR Network Solutions, told BleepingComputer.
"These grouped together the /22 and /24 prefixes announced by Orange Spain, indicating that the AS that should announce that prefix was AS49581 (Ferdinand Zink trading as Tube-Hosting)."
"Once this was done, they activated RPKI on that /12... and goodbye..."
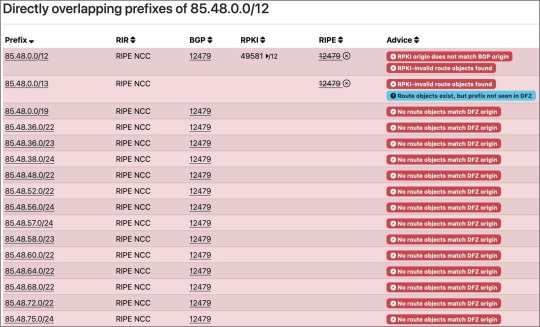
Invalid RPKI implementation on announced IP addresses
Source: Cañizares
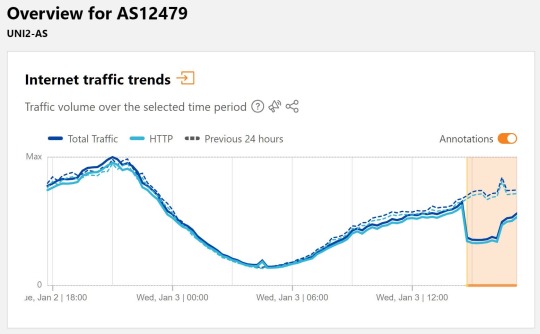
This led to a performance issue on Orange Spain's network between 14:45 and 16:15 UTC, which can be seen in the Cloudflare traffic graph below for AS12479.
Traffic graph for Orange Spain's AS12479
Source: Cloudflare
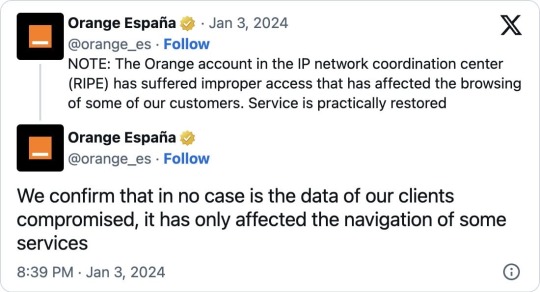
Orange Spain has since confirmed that their RIPE account was hacked and has begun to restore services.
"NOTE: The Orange account in the IP network coordination center (RIPE) has suffered improper access that has affected the browsing of some of our customers. Service is practically restored," Orange Spain tweeted.
"We confirm that in no case is the data of our clients compromised, it has only affected the navigation of some services."
It is unclear how the threat actor breached the RIPE account but Cañizares told BleepingComputer that he believes Orange Spain did not enable two-factor authentication on the account.
Cañizares has created a thread on X summarizing how this attack took place.
BleepingComputer contacted Orange Spain with questions about the attack but has not received a reply at this time.
Credentials likely stolen via malware
While Orange Spain has not disclosed how its RIPE account was breached, the threat actor provided a clue in a screenshot posted to Twitter that contained the hacked account's email address.
Alon Gal of cybersecurity intelligence service Hudson Rock told BleepingComputer that this email and an associated password for the RIPE account were found in a list of accounts stolen by information-stealing malware.
"The Orange employee had their computer infected by a Raccoon type Infostealer on September 4th 2023, and among the corporate credentials identified on the machine, the employee had specific credentials to "https://access.ripe.net" using the email address which was revealed by the threat actor ([email protected])," explains research from Hudson Rock.
According to Gal, the password for the account was 'ripeadmin,' which is a very easy password for a critical account.
The hacker, Snow, later confirmed Hudson Rock's findings, saying on Twitter that they found the account in public leaks of stolen data.
"For those wondering how i acquired access to the account in the first place, let me just say that the password security was very questionable," Snow posted on Twitter/X.
"I was just looking into public leaks of bot data and came across the ripe account with the password "ripeadmin" and no 2FA, No SE at all."
When asked why they hacked the account, the hacker says they did it for the "lulz," or in other words, for the laughs.
RIPE also conducted an investigation into the incident, saying they restored Orange's account and advised users to enable MFA.
"We encourage account holders to please update their passwords and enable multi-factor authentication for their accounts. If you suspect that your account might be impacted, please report it to [email protected]," RIPE posted to a page about the breach.
Information-stealing malware has become the bane of the enterprise, as threat actors use them to gather credentials for initial access to corporate networks.
Threat actors commonly purchase stolen credentials from cybercrime marketplaces, which are then used to breach networks to perform data theft, cyber espionage, and ransomware attacks.
For this reason, all accounts must have two-factor or multi-factor authentication enabled so that even if an account is stolen, attackers cannot log in to the account.
#BGP#kairoscybersecurity#kairoscybersecurityconsultants#cybersecurity#cyberattack#security#cybercrime#kairoscybersecuritysolutions#Border Gateway Protocol#information-stealing malware#IP Address#routing table#RIPE#RPKI#resource public key infrastructure
0 notes
Text
Museums Hit By Cyberattack Via Widely Used Gallery Systems Software
The Museum of Fine Arts Boston, the Rubin Museum of Art in New York, and the Crystal Bridges Museum of American Art in Arkansas have fallen victim and hit by a cyberattack leaving the institutions grappling with crippling system outages over several days this week.
Several well-known museums are currently facing challenges in showcasing their collections on the internet. This issue arose after a cyberattack targeted a major technology service provider that assists numerous cultural organisations in presenting their works digitally and handling internal documents.
Gallery Systems, the service provider, conveyed in a recent message to its clients, as reported by The New York Times, that it identified an issue on December 28. During this time, the computers running its software were encrypted, rendering them incapable of functioning.
“Certain computer systems that run our software became encrypted, which prevented them from operating,” it said.
The service provider stands as a prominent supplier of gallery and collection management software, boasting a portfolio that encompasses over 800 museums.
Among its esteemed clients are renowned institutions such as the Museum of Modern Art (MoMA) in New York, the Metropolitan Museum of Art (Met), the Chrysler Museum of Art, the Museum of Pop Culture (MoPOP) in Seattle, the Barnes Foundation, the Crystal Bridges Museum of American Art, and the San Francisco Museum of Modern Art (SFMOMA).
“We immediately took steps to isolate those systems and implemented measures to prevent additional systems from being affected, including taking systems offline as a precaution,” the company said in the message.
“We also launched an investigation and third-party cybersecurity experts were engaged to assist. In addition, we notified law enforcement.”
The impact of the disturbance became apparent as various museum websites displayed signs of dysfunction. eMuseum, a typically reliable tool that enables visitors to explore online collections, was inaccessible.
Behind the scenes, the disruption extended further. Some curators shared their experiences of returning from winter vacations only to discover that they were unable to access crucial information stored in another Gallery Systems program known as TMS.
The system holds valuable details such as donor names, loan agreements, provenance records, shipping information, and storage locations for priceless artworks.
“We noticed the outage starting Dec. 28,” Sandrine Milet, a spokeswoman for the Rubin Museum, said. “TMS was back and running yesterday while eMuseum is still down.”
T. Barton Thurber, the director of the Frances Lehman Loeb Art Center at Vassar College, said, “I can confirm that unfortunately our museum — along with many others — has been impacted by the attack.”
Paige Francis, the chief information officer at Crystal Bridges, said, “We are mostly concerned about the public’s inability to benefit from viewing our collection remotely during this disruption.”
Security experts report a rising frequency of cyberattacks targeting cultural organizations. In November, a ransomware group breached the British Library, stealing personal data and sharing images of internal human resources files.
Additionally, the Metropolitan Opera and the Philadelphia Orchestra encountered cyberattacks last winter, impeding their online ticket sales operations.
In numerous instances, these attacks have been orchestrated by ransomware groups, who seize control of the online service and demand payment from victims to restore access. The specific details regarding the attack on Gallery Systems remain unclear.
Several museums, such as the Metropolitan Museum of Art and the Whitney Museum of American Art, which depend on Gallery Systems, stated that they remained unaffected as they manage their own databases.
“The objects in museums are valuable, but the information about them is truly priceless,” says Erin Thompson, a professor of art crime at John Jay College of Criminal Justice in New York.
“Often, generations of curators will have worked to research and document an artifact. If this information is lost, the blow to our knowledge of the world would be immense.”
Meanwhile, the company has informed law enforcement and is presently examining the consequences of the incident. Gallery Systems has assured to furnish additional information as the investigation advances.
Threat actors responsible for the attack have yet to asserted accountability for the data breaches which is surprising as typically, a hacking collective would append its target to an undisclosed data leak platform, aiming to escalate pressure and compel negotiations for a ransom.
The extent of the cyberattack’s prevalence and its complete impact were not immediately evident, and Gallery Systems did not promptly respond to requests for comment via email and phone.
#data leaks#data breach#kairoscybersecuritysolutions#kairoscybersecurity#cybersecurity#kairoscybersecurityconsultants#cyberattack#security#cybercrime#technology
0 notes
Text
Data breach at healthcare tech firm impacts 4.5 million patients
HealthEC LLC, a provider of health management solutions, suffered a data breach that impacts close to 4.5 million individuals who received care through one of the company's customers.
HealthEC provides a population health management (PHM) platform that healthcare organizations can use for data integration, analytics, care coordination, patient engagement, compliance, and reporting.
On December 22, the firm disclosed that it suffered a data breach between July 14 and 23, 2023, which resulted in unauthorized access to some of its systems.
An investigation of the incident concluded on October 24, 2023, and revealed that the intruder had stolen files from the breached systems hosting the following data types:
Name
Address
Date of birth
Social Security number
Taxpayer Identification Number
Medical Record number
Medical information (diagnosis, diagnosis code, mental/physical condition, prescription information, and provider's name and location)
Health insurance information (beneficiary number, subscriber number, Medicaid/Medicare identification)
Billing and claims information (patient account number, patient identification number, and treatment cost information)
"In general, individuals should remain vigilant against incidents of identity theft and fraud by reviewing account statements, explanation of benefits statements, and monitoring free credit reports for suspicious activity and to detect errors," reads HealthEC's notification.
The company recommends that "suspicious activity should be promptly reported to relevant parties including an insurance company, health care provider, and/or financial institution."
At the time of the cyberattack, HealthEC didn't specify how many people were impacted by the intrusion, but a submission to Maine's Attorney General's office that concerned just one of the firm's clients, MD Valuecare, set the number of affected persons to 112,005.
A new listing that appeared earlier today on the breach portal of the U.S. Department of Health and Human Services shows the larger picture, informing that the total number of affected individuals is 4,452,782.
There are 17 healthcare service providers and state-level health systems that were impacted by the cyberattack on the HealthEC tech solutions provider.
Some major organizations listed in the notice include Corewell Health, HonorHealth, Beaumont ACO, State of Tennessee – Division of TennCare, the University Medical Center of Princeton Physicians' Organization, and the Alliance for Integrated Care of New York.
#kairoscybersecuritysolutions#kairoscybersecurity#cybersecurity#kairoscybersecurityconsultants#security#cyberattack#cybercrime#technology#healthcare#data leaks#data breach#health services
0 notes
Text
Iranian Hackers Lurked for 8 Months in Government Network

Iran-linked hacking group Crambus spent eight months inside a compromised network of a Middle Eastern government, Broadcom’s Symantec cybersecurity unit reports.
Symantec uses the Crambus name for clusters of activity that other cybersecurity firms are tracking as APT34 (also known as Cobalt Gypsy, OilRig, and Helix Kitten), and MuddyWater (aka Mango Sandstorm, Mercury, Seedworm, and Static Kitten).
Both APT34 and MuddyWater engage in espionage operations to support the objectives of the Iranian government, and MuddyWater was previously linked by US Cyber Command to Iranian intelligence.
As part of a recently identified attack, Crambus lurked between February and September 2023 in the compromised network of the government of a Middle Eastern country, stealing data and credentials, and deploying malware on multiple systems.
The attack started on February 1 with the execution of a PowerShell script on a single system. Malicious activity started on a second compromised system a few days later, and on a web server towards the end of February. In April, the attackers started executing commands on a domain controller.
While malicious activity was seen only on these systems until August, a second web server and additional systems were compromised toward the end of August and into September.
In a statement released by Symantec, malicious activity occurred on at least 12 computers and there is evidence that the attackers deployed backdoors and keyloggers on dozens more.
As part of the attack, Crambus installed a PowerShell backdoor dubbed PowerExchange, which can access Microsoft Exchange Servers using hardcoded credentials to monitor for emails sent by the attackers and execute PowerShell commands, write files, and steal files.
Additionally, the attackers used the network administration tool Plink to set port-forwarding rules and enable access via the Remote Desktop Protocol (RDP), and modified firewall rules to ensure remote access.
In addition to the PowerExchange backdoor, Crambus was seen deploying three new malware families, namely the Tokel backdoor (for PowerShell command execution and file download), the Dirps trojan (PowerShell command execution and file enumeration), and the Clipog infostealer (clipboard data theft, keylogging, and logging of processes where keystrokes are entered).
#cybersecurity#kairoscybersecurityconsultants#kairoscybersecurity#security#cyberattack#cybercrime#technology#coding#linux#ubuntu#power shell#apt34#hackers#kairoscybersecuritysolutions
0 notes
Text
Chinese hackers breach US critical infrastructure in stealthy attacks
According to Microsoft, a Chinese cyberespionage group known as Volt Typhoon has been actively targeting critical infrastructure organizations in the United States, including Guam, since at least mid-2021. The group's targets span various crucial sectors such as government, maritime, communications, manufacturing, information technology, utilities, transportation, construction, and education.
Microsoft's assessment suggests that the Volt Typhoon campaign aims to develop capabilities that could potentially disrupt vital communications infrastructure between the United States and the Asian region. The initial method of attack involves exploiting an unknown zero-day vulnerability to compromise Internet-exposed Fortinet FortiGuard devices.
Once the group gains access to the targeted networks, they employ "living-off-the-land" tactics, engaging in hands-on-keyboard activities and utilizing living-off-the-land binaries (LOLBins) like PowerShell, Certutil, Netsh, and the Windows Management Instrumentation Command-line (WMIC). Additionally, the group has been observed using open-source tools like Fast Reverse Proxy (frp), the Mimikatz credential-stealing tool, and the Impacket networking framework.
A joint advisory issued by the FBI, NSA, CISA, and cybersecurity agencies from Australia, New Zealand, the United Kingdom, and Canada revealed that Volt Typhoon also utilizes compromised small office and home office (SOHO) network equipment from brands like ASUS, Cisco, D-Link, Netgear, FatPipe, and Zyxel. This equipment, including routers, firewalls, and VPN appliances, helps the group blend their malicious activities with legitimate network traffic to evade detection.
By compromising Fortinet devices, the state-sponsored hackers gain privileged access, enabling them to extract credentials through the Local Security Authority Subsystem Service (LSASS). These stolen credentials then allow them to deploy Awen-based web shells, facilitating data exfiltration and establishing persistence on the compromised systems.
Mandiant Intelligence Chief Analyst John Hultquist noted that these intrusions into US critical infrastructure organizations likely serve as part of a larger effort by China to gain access in the event of a future conflict between the two countries. Hultquist emphasized that targeting critical infrastructure is often indicative of preparations for disruptive or destructive cyberattacks, as states engage in long-term intrusions to be adequately positioned ahead of potential conflicts.
Microsoft, as part of its response to nation-state actor activity, has proactively reached out to all targeted or compromised customers to provide them with the necessary information to enhance the security of their networks and defend against future hacking attempts.
#US-China Relations#Geopolitics#Cybersecurity#Cyberespionage#Critical Infrastructure#Volt Typhoon#Chinese Hacking Group#Microsoft#Zero-day Vulnerability#Living-off-the-land Attacks#Nation-state Actors#Data Exfiltration#Data Breach#Small Office Home Office (SOHO) Networks#Network Security#Fortinet FortiGuard#Mimikatz#Impacket#Awen-based Web Shells
0 notes
Text
[Media] HackRF One + Portapack H2 Mayhem
HackRF One + Portapack H2 Mayhem
The HackRF is an exceptionally capable software defined radio (SDR) transceiver, but naturally you need to connect it to a computer to actually do anything with it. So the PortaPack was developed to turn it into a stand-alone device with the addition of a touchscreen LCD, a few buttons, and a headphone jack. With all the hardware in place, it’s just a matter of installing a firmware capable enough to do some proper RF hacking on the go.
Enter MAYHEM, an evolved fork of the original PortaPack firmware that the developers claim is the most up-to-date and feature packed version available. Without ever plugging into a computer, this firmware allows you to receive, decode, and re-transmit a dizzying number of wireless protocols. From firing off the seating pagers at a local restaurant to creating a fleet of phantom aircraft with spoofed ADS-B transponders, MAYHEM certainly seems like it lives up to the name.
Detailed blog post about installing and using MAYHEM on the HackRF/PortaPack, complete with a number of real-world examples that show off just a handful of possible applications for the project. Jamming cell phones, sending fake pager messages, and cloning RF remotes is just scratching the surface of what’s possible.
Example of use: exploitation of a Honda vulnerability Honda’s Remote Keyless System (CVE-2022-27254)
Firmware to open any and all Tesla vehicle charging ports in range!
Buy online:
🛒 https://bit.ly/3AEBFHS
#radio #RF #SDR

10 notes
·
View notes
Text
New Russian-Linked Malware Poses "Immediate Threat" to Energy Grids
In an increasingly interconnected world, the security of critical infrastructure, such as energy grids, has become a matter of utmost importance. Unfortunately, the threat landscape continues to evolve, and a new form of malware with Russian links has recently emerged, posing an immediate danger to energy grids worldwide. This development has raised concerns among cybersecurity experts, government agencies, and energy providers, emphasizing the urgent need for enhanced defenses and collaborative efforts to safeguard these vital systems.
The Rising Threat:
Over the past decade, cyberattacks on critical infrastructure have grown more sophisticated and frequent. From disrupting power supply to stealing sensitive information, these attacks can have severe consequences for national security and public safety. The latest concern centers around a new strain of malware dubbed "Energetic Bear 2.0," believed to have Russian origins.
Energetic Bear 2.0: Unveiling the Threat:
Energetic Bear 2.0, an advanced persistent threat (APT) group, is known for targeting energy sectors across the globe. This new iteration of the group has gained notoriety for its ability to infiltrate and compromise energy grids, posing an immediate threat to the stability and reliability of these systems. While the exact method of infection remains unknown, it is likely that spear-phishing campaigns, social engineering tactics, and vulnerabilities in network infrastructure are being exploited.
Implications for Energy Grids:
The potential consequences of a successful attack on energy grids are significant and far-reaching. An adversary with control over a country's energy infrastructure can cause widespread blackouts, disrupt economic activities, and even compromise national security. The energy sector serves as the backbone of society, supporting essential services like healthcare, transportation, and communication. Any disruption or compromise in this sector can have cascading effects on the overall functioning of a nation.
Preventive Measures and Countermeasures:
Addressing the immediate threat posed by Energetic Bear 2.0 and similar malware requires a multi-faceted approach involving governments, energy companies, and cybersecurity professionals. Here are some crucial steps to enhance the security of energy grids:
Increased Vigilance: Energy companies should remain vigilant and actively monitor their networks for any signs of compromise. Early detection and swift response can help mitigate the damage caused by a cyberattack.
Employee Education: Cybersecurity awareness training is crucial for employees at all levels within energy organizations. By educating staff about phishing techniques, social engineering, and proper security practices, the risk of successful attacks can be reduced.
Regular Vulnerability Assessments: Conducting regular security assessments and penetration testing helps identify potential weaknesses in the network infrastructure. Prompt patching of vulnerabilities and keeping systems up to date can significantly enhance security.
Enhanced Collaboration: Governments, regulatory bodies, and energy companies must collaborate closely to share threat intelligence and best practices. This collaboration can help establish a proactive defense posture against emerging threats.
Advanced Security Solutions: Deploying state-of-the-art security solutions, such as intrusion detection systems, anomaly detection, and behavior analytics, can strengthen defenses against advanced malware like Energetic Bear 2.0.
Conclusion:
The emergence of Energetic Bear 2.0, a new strain of malware linked to Russian actors, highlights the urgent need to strengthen the security of energy grids. The potential consequences of a successful attack on these critical infrastructures are grave, necessitating concerted efforts from governments, energy providers, and cybersecurity experts. By implementing robust security measures, enhancing collaboration, and remaining vigilant, we can mitigate the immediate threat posed by this malware and safeguard the reliable operation of energy grids, ensuring the stability and resilience of our modern societies.
#Cybersecurity#Malware#Energy Grids#Critical Infrastructure#Energetic Bear#Russian Hackers#Threat Landscape#Cyber Attacks#APTs#infosec#Advanced Persistent Threats#Network Security#Spear-Phishing#Social Engineering#Collaborative Defense#Vulnerability Assessments#Patch Management#Threat Intelligence#Security Solutions#Government Cooperation#Resilience
0 notes
Text
Unmasking the Lazarus Group: A Wave of Espionage Attacks on Microsoft Web Servers
In the ever-evolving landscape of cyber threats, one persistent and formidable group has emerged as a significant concern for global cybersecurity: the Lazarus Group. Renowned for their sophisticated hacking techniques and state-sponsored activities, this elusive collective has once again made headlines with a series of highly targeted attacks aimed at exploiting vulnerabilities in Microsoft Web Servers. In this blog post, we delve into the recent activities of the Lazarus Group, their modus operandi, and the potential ramifications of their espionage malware campaigns.
Understanding the Lazarus Group:
The Lazarus Group, widely believed to be based in North Korea, has gained notoriety over the past decade for their involvement in various cyber operations, including high-profile attacks on financial institutions, cryptocurrency exchanges, and government agencies. These state-sponsored hackers possess advanced technical skills and resources, allowing them to carry out complex and long-term campaigns.
Recent Microsoft Web Server Exploits:
In recent months, the Lazarus Group has intensified its efforts to infiltrate organizations' networks by exploiting vulnerabilities in Microsoft Web Servers. These servers, which power numerous websites and web applications, have become a prime target for the group due to their wide-scale usage and potential for gaining access to valuable data.
Espionage Malware Deployment:
The Lazarus Group's objective with these attacks is to plant espionage malware within the compromised servers. Once successful, this malware allows the group to gain unauthorized access to sensitive information, conduct surveillance, and potentially exfiltrate data for their clandestine purposes. The targeted servers act as a gateway for the group to infiltrate other systems within the network, expanding the scope of their espionage operations.
Sophisticated Techniques:
The Lazarus Group's attacks demonstrate a high level of sophistication and strategic planning. They employ a combination of spear-phishing campaigns, social engineering tactics, and the exploitation of known vulnerabilities in the targeted Microsoft Web Servers. By leveraging a diverse range of techniques, the group increases their chances of successfully compromising their targets' networks, making detection and mitigation more challenging.
Implications for Organizations:
The Lazarus Group's attacks on Microsoft Web Servers pose significant risks to organizations of all sizes and industries. A successful breach can lead to severe consequences, including intellectual property theft, financial loss, reputational damage, and compromised customer data. Furthermore, the group's suspected state sponsorship implies that the stolen information could potentially be used for geopolitical purposes, further escalating the gravity of their actions.
Mitigating the Threat:
To defend against the Lazarus Group's attacks, organizations must adopt a multi-layered approach to cybersecurity. This includes regular patching and updating of software, implementing robust network security measures, conducting thorough employee training on phishing awareness, and deploying advanced threat detection and response solutions. Additionally, closely monitoring and analyzing network traffic and system logs can aid in early detection and swift response to potential breaches.
Collaborative Efforts:
Given the global nature of the Lazarus Group's activities, international collaboration between governments, law enforcement agencies, and cybersecurity organizations is vital. Sharing threat intelligence and coordinating response efforts can enhance the collective defense against these state-sponsored threat actors. By pooling resources and expertise, we can better equip ourselves to combat the Lazarus Group's ongoing campaigns.
In closing, The Lazarus Group's recent attacks targeting Microsoft Web Servers to launch espionage malware underscore the evolving and persistent nature of cyber threats faced by organizations worldwide. Heightened awareness, proactive security measures, and international collaboration are essential to counter these advanced threat actors. As we continue to witness the Lazarus Group's activities, it becomes increasingly crucial for organizations to remain vigilant and prioritize cybersecurity as an integral part of their operations.
#The Lazarus Group#Microsoft Web Servers#Cybersecurity#Microsoft#threat mitigation#infosec#purple team#Malware
0 notes
Text
Four Key GDPR Trends on the Law’s Fifth Anniversary
On the fifth anniversary of the General Data Protection Regulation (GDPR), four key trends have emerged that highlight the evolving landscape of data protection and privacy. These trends signify the impact and maturation of the GDPR since its implementation in May 2018:
Increased Regulatory Enforcement: Over the past five years, regulatory authorities across the European Union (EU) have significantly ramped up their enforcement actions. This trend reflects a growing commitment to holding organizations accountable for non-compliance with GDPR provisions. Regulators have imposed substantial fines on companies found in violation of data protection rules, emphasizing the importance of adhering to the regulation's requirements.
Heightened Awareness and Compliance Efforts: The GDPR has brought data protection and privacy to the forefront of public consciousness. Individuals are now more aware of their rights and are actively engaging with organizations to exercise those rights. Moreover, companies have invested heavily in compliance efforts, adopting stricter data protection practices, appointing data protection officers, and revising their privacy policies to align with GDPR principles. Compliance has become a priority due to the potential reputational damage and severe financial penalties associated with non-compliance.
Cross-Border Data Transfers Challenges: One of the primary objectives of the GDPR is to safeguard personal data when it is transferred outside the EU. However, achieving compliant cross-border data transfers has proven to be complex. The invalidation of the EU-US Privacy Shield framework by the Court of Justice of the European Union (CJEU) in 2020 highlighted the challenges associated with ensuring adequate data protection standards in countries outside the EU. This trend has prompted organizations to seek alternative mechanisms, such as Standard Contractual Clauses (SCCs), to legitimize international data transfers.
Evolving Technological Landscape: The GDPR was designed to be technology-neutral, but advancements in technology have posed new challenges. Emerging technologies like artificial intelligence (AI), machine learning, and big data analytics present privacy concerns that the GDPR did not anticipate fully. Organizations are now grappling with the need to strike a balance between utilizing innovative technologies while ensuring compliance with the GDPR's principles of transparency, purpose limitation, and data minimization.
Overall, these four key trends on the GDPR's fifth anniversary demonstrate the ongoing efforts to strengthen data protection practices, enforce compliance, and adapt to the evolving digital landscape. As the GDPR continues to shape the global privacy landscape, organizations must remain vigilant in their commitment to protecting individuals' personal data while embracing technological advancements responsibly.
0 notes
Text
Given the recent Department of Defense (DoD) I think it is important for my to cover the basic entry level security measure that could have prevented all of this leak and all potential fallout. It is the Principle of Least Privilege (POLP). Now I will provide my explanation of POLP but first NIST (National Institution of Standards and Technology) is a government agency that is trusted for all security professional to use. Why weren’t our top government, military, and intelligence officials. The pdf guides will be linked here too NIST SP 800-12 Rev. 1 , NIST SP 800-53 Rev. 5 , and NIST SP 800-171 Rev. 2 . Another reference is from the Committee on National Security Systems (CNSS) CNSSI 4009-2015 . It should also be noted that the DoD is the parent organization to CNSS. That’s right the DoD is responsible for CNSS.
Now here’s my take:

Principle of Least Privilege (POLP)
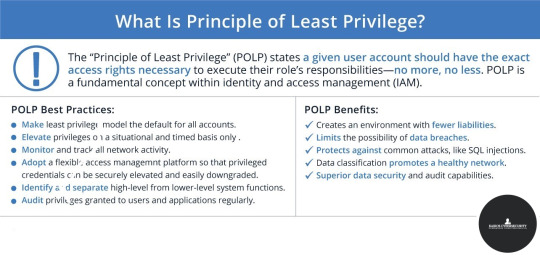
The Principle of Least Privilege (POLP) is a fundamental concept in information security concerned with limiting users' access rights, processes, and systems to only the resources necessary to carry out their intended functions. POLP aims to reduce the attack surface of a system by limiting the damage that an attacker can cause in case of a successful exploit. This principle is also known as the Principle of Minimum Privilege or Least Authority.
This paper will explore the principles of least privilege, their benefits to an organization, the challenges associated with their implementation, and the best practices to ensure its success.
Principle of Least Privilege Explained
The Principle of Least Privilege is based on privilege, which refers to the level of access a user, process, or system has to a particular resource or service. In information security, a privilege can be defined as a right or permission that allows a user, process, or system to perform a particular action or access a specific resource.
The principle of least privilege states that a user, process, or system should be granted only the minimum level of privilege necessary to perform its intended function. This means that a user, process, or system should not be given more access rights than required to carry out its duties. By limiting the access rights of users, processes, and systems, the attack surface of a system can be reduced, and the potential for unauthorized access, data breaches, and other security incidents can be minimized.
Benefits of POLP
The principle of least privilege offers several benefits to an organization. Firstly, it can help to reduce the risk of security incidents such as data breaches and unauthorized access. By limiting the access rights of users, processes, and systems, the potential for malicious actors to exploit vulnerabilities in the system is reduced, and the impact of any successful attacks is minimized.
Secondly, POLP can help improve an organization's overall security posture by enforcing the principle of separation of duties. Limiting the access rights of users, processes, and systems reduces the risk of insider threats and collusion. This means that even if one user's credentials are compromised, the attacker cannot access other parts of the system that require higher privileges.
Thirdly, POLP can help reduce a system’s complexity by limiting the number of permissions that need to be managed. This can make it easier for system administrators to manage access rights and reduce the potential for errors and misconfigurations.
Challenges of POLP Implementation
While the principle of least privilege offers many benefits to an organization, several challenges are associated with its implementation. One of the main challenges is the need to balance security requirements with business needs. In some cases, granting higher privileges may be necessary to enable specific business processes to function effectively. This can create tension between security and usability and may require careful consideration of the risks and benefits associated with each decision.
Another challenge associated with POLP implementation is ensuring the principle is enforced consistently across all systems and processes. This requires a clear understanding of the access requirements of each user, process, and system and a robust process for managing and monitoring access rights. Failure to implement the principle consistently can result in security gaps that attackers can exploit.
Best Practices for POLP Implementation

To ensure the successful implementation of the Principle of Least Privilege, there are several best practices that organizations can follow. These include
1. Conduct a Risk Assessment: Before implementing POLP, it is essential to conduct a risk assessment to identify the potential risks and threats to the system. This can help identify each user’s access requirements, process, and system and inform the implementation of access controls.
Indeed, a risk assessment is a critical step in implementing POLP, as it helps to identify the potential risks and threats to the system. A team of security experts familiar with the organization's systems and processes should conduct the risk assessment. The risk assessment should consider internal and external threats and the potential impact of a security incident on the organization.
Once the potential risks and threats have been identified, the next step is to identify the access requirements of each user, process, and system. This involves identifying the minimum level of access necessary for each user, process, and system to perform its intended function. This information can then be used to implement access controls that enforce the principle of least privilege.
2. Implement Role-Based Access Control (RBAC): Role-Based Access Control is a common access control model based on roles. This model assigns users specific roles based on their job functions and responsibilities. Each role is associated with a set of permissions defining the level of access that users in that role are granted. RBAC can help simplify access rights management and reduce the potential for errors and misconfigurations.
3. Use the Principle of Least Privilege as a Default: Organizations should adopt the principle of least privilege as a default, meaning that users, processes, and systems are granted the minimum level of access necessary to perform their intended function. This should be the starting point for any access control decisions, and higher access levels should only be granted when absolutely necessary.
4. Monitor Access Rights: It is essential to monitor access rights to ensure they are consistent with the principle of least privilege. Regular audits should be conducted to identify any unauthorized access or excessive privileges, and appropriate actions should be taken to address any identified issues.
5. Educate Users: Users should be educated on the importance of the least privilege and the potential risks associated with excessive privileges. This can help to ensure that users are aware of their responsibilities and can help to reduce the risk of insider threats.
6. Implement Multi-Factor Authentication (MFA): Multi-Factor Authentication can help to prevent unauthorized access by requiring users to provide additional authentication factors in addition to their password. This can make it more difficult for attackers to gain access to the system, even if they have obtained a user's credentials.
Conclusion
The Principle of Least Privilege is a fundamental concept in information security that can help to reduce the risk of security incidents and improve the overall security posture of an organization. By adopting the principle of least privilege as a default, educating users, and implementing Multi-Factor Authentication, organizations can reduce the attack surface of their systems and improve their organization’s overall security. While there are challenges associated with its implementation, following best practices such as conducting a risk assessment, implementing Role-Based Access Control, and monitoring access rights can help ensure the principle's successful implementation.
#top secret us intelligence docs revealing ukraine spring offensive against russia shared online sparking pentagon probe#top secret documents#nist#cybersecurity#kairoscybersecurity#kairoscybersecurityconsultants#security#cybercrime#polp#DoD#military secrets#NIST SP 800-12 Rev. 1#NIST SP 800-53 Rev. 5#NIST SP 800-171 Rev. 2#CNSSI 4009-2015#principle of least privilege#CryptoChris80#CryptoChris
0 notes
Text
Defense-In-Depth Strategy
Christopher Meyer
In cybersecurity, defense in depth is a cyber defense strategy in which multiple layers of security controls are put into place on an organization’s network. Multiple layers are used in case a hacker exploits a layer because of a vulnerability in a layer. System administrators need to understand how their networks and systems are protected. There is a daily battle in making sure you are safe from intruders. System administrators are at the front line of defense of an organization’s network and are the first responders in case of a security penetration.
As an analogy of medieval castle layers of defense illustrates the concept of defense in depth. First, the castle has the perimeter defense of the different levels of walls which is analogous to the local host and network firewall. The castle is also protected by the moat to give it another layer of protection. You have towers for guards to watch over the castle for intrusions like an intrusion detection system would over a network. You have a single-entry point of the inner and outer gates for physical protection such as how you would protect your data center of servers physically. The protection of the castle is done in a layered fashion to protect against intruders similar to the layers of controls system administrators put in place for an organization’s systems. Figure 1 shows the parts of the castle and its layers of protections.
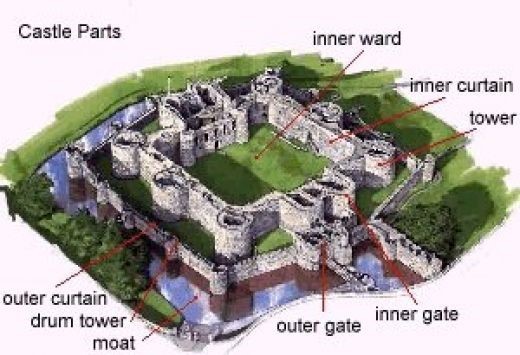
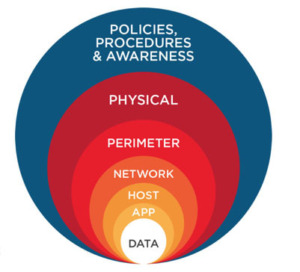
Figure 2 shows the layers of defense in an organization’s network. The highest level of protection are the policies and procedures in place to explain what you can and cannot do on the network and how you will handle a security breach. Awareness is critically important because the user is the weakest link. The user must continuously be educated and made aware of behaviors that put the organization at risk. Then, you have the physical protections in place for your systems. Then, you have the perimeter control which, a firewall that prevents unauthorized network traffic. The Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) scan the network for potential issues and notify the system administrator of potential issues with alerts. Also at the network level, you will have Access Control Lists (ACLs) on your routers to allow only certain traffic and deny others. At the host level, you need to harden the hosts and servers. Hardening is a process that system administrator uses to lower the risk of the system from hacking. Part of the hardening process is to install a local firewall to limit the exposure of the systems on the network. In this lab, you will be closing unnecessary ports, installing a firewall on a Windows server, and patching the server to remove vulnerabilities. You will also use antivirus software to protect your systems from malware and viruses. At the app level, you will set up a login process into the application to allow only authorized users. At the You will secure the data and any databases at the data level login processes and encryption.
#kairoscybersecurity#kairoscybersecurityconsultants#cybersecurity#defenseindepth#security#DiD securitylayers#levelsofsecurity
0 notes
Text
Apple, Android Phones Targeted by Italian Spyware: Google
An Italy-based firm's hacking tools were used to spy on Apple and Android smartphones in Italy and Kazakhstan, Google said Thursday, casting a light on a "flourishing" spyware industry.
Google's threat analysis team said spyware made by RCS Lab targeted the phones using a combination of tactics including unusual "drive-by downloads" that happen without victims being aware.
Concerns over spyware were fueled by media outlets reporting last year that Israeli firm NSO's Pegasus tools were used by governments to surveil opponents, activists and journalists.
"They claim to only sell to customers with legitimate use for surveillanceware, such as intelligence and law enforcement agencies," mobile cybersecurity specialist Lookout said of companies like NSO and RCS.
"In reality, such tools have often been abused under the guise of national security to spy on business executives, human rights activists, journalists, academics and government officials," Lookiout added.
Google's report said the RCS spyware it uncovered, and which was dubbed "Hermit", is the same one that Lookout reported on previously.
Lookout researchers said that in April they found Hermit being used by the government of Kazakhstan inside its borders to spy on smartphones, just months after anti-government protests in that country were suppressed.
"Like many spyware vendors, not much is known about RCS Lab and its clientele," Lookout said. "But based on the information we do have, it has a considerable international presence."
Growing spyware industry
Evidence suggests Hermit was used in a predominantly Kurdish region of Syria, the mobile security company said.
Analysis of Hermit showed that it can be employed to gain control of smartphones, recording audio, redirecting calls, and collecting data such as contacts, messages, photos and location, Lookout researchers said.
Google and Lookout noted the spyware spreads by getting people to click on links in messages sent to targets.
"In some cases, we believe the actors worked with the target's ISP (internet service provider) to disable the target's mobile data connectivity," Google said.
"Once disabled, the attacker would send a malicious link via SMS asking the target to install an application to recover their data connectivity."
When not masquerading as a mobile internet service provider, the cyber spies would send links pretending to be from phone makers or messaging applications to trick people into clicking, researchers said.
"Hermit tricks users by serving up the legitimate webpages of the brands it impersonates as it kickstarts malicious activities in the background," Lookout researchers said.
Google said it has warned Android users targeted by the spyware and ramped up software defenses. Apple told AFP it has taken steps to protect iPhone users.
Google's threat team is tracking more than 30 companies that sell surveillance capabilities to governments, according to the Alphabet-owned tech titan.
"The commercial spyware industry is thriving and growing at a significant rate," Google said.
#cybersecurity#kairoscybersecurity#kairoscybersecurityconsultants#security#cyberattack#technology#cybercrime#hacking#cisa#Crypto_Chris#kairoscybersecuritysolutions#ransomware#cyberwar#cyberwarfare#mobile security#Apple#google
0 notes
Text
Google Links Exploitation Frameworks to Spanish Spyware Vendor Variston
Google’s Threat Analysis Group (TAG) has linked three exploitation frameworks, as well as several vulnerabilities that were likely used as zero-days at some point, to a Spanish commercial spyware vendor named Variston.
Variston says it provides custom security solutions. The Barcelona-based company offers security products and custom patches for embedded systems, including industrial control systems (ICS) and IoT. It also offers data discovery services and training.
Google became aware of Variston’s products after receiving an anonymous submission in the Chrome bug bounty program. The reporter provided information on three vulnerabilities and the analysis of the reports led TAG researchers to Variston.
Google has identified three different exploitation frameworks designed for deploying exploits: Heliconia Noise, a web framework for deploying Chrome exploits; Heliconia Soft, a web framework that deploys a Windows Defender exploit via a PDF file; and Heliconia Files, which contains Firefox exploits for Windows and Linux.
Heliconia Noise is described in a manifest file as a “1-click full chain for Google Chrome without persistence reaching medium integrity”. Google says it can be used to deliver a Chrome renderer exploit, followed by a sandbox escape and agent installation in the post-exploitation stage. The victim needs to access a malicious webpage to trigger the first-stage exploit.
A vulnerability allowing the renderer exploit was patched in August 2021, but it was not assigned a CVE identifier as it was internally found by Google.
Heliconia Soft is designed to exploit CVE-2021-42298, a Microsoft Defender remote code execution vulnerability patched in November 2021. The framework is described as a “Windows Chrome & Chromium Edge 1-click chain without persistency reaching SYSTEM integrity”.
When the victim downloads a specially crafted PDF file, Windows Defender scans it, thus triggering the exploit.
As for Heliconia Files, it delivers a Firefox exploit chain for Windows and Linux. It leverages CVE-2022-26485 for remote code execution, which Mozilla patched with an emergency Firefox update in March 2022 after learning about its existence from Chinese cybersecurity firm Qihoo 360. A sandbox escape vulnerability affecting Firefox for Windows was addressed without a CVE in September 2019.
While the exploits delivered by the Heliconia frameworks are now patched, they were all likely used as zero-days before Google, Mozilla and Microsoft learned of their existence and released fixes. The Firefox remote code execution flaw, for instance, is believed to have been exploited by the Variston product since at least 2019.
“TAG's research has shown the proliferation of commercial surveillance and the extent to which commercial spyware vendors have developed capabilities that were previously only available to governments with deep pockets and technical expertise. The growth of the spyware industry puts users at risk and makes the Internet less safe, and while surveillance technology may be legal under national or international laws, they are often used in harmful ways to conduct digital espionage against a range of groups,” Google said.
This is not the first commercial spyware vendor whose activities and tools have been analyzed by Google. The company has also published reports on Israel-based NSO Group and Italy-based RCS Lab.
Google was also informed recently by Avast about a Chrome zero-day vulnerability exploited by Israel-based spyware vendor Candiru.
#cybersecurity#kairoscybersecurityconsultants#kairoscybersecurity#security#cyberattack#cyberwarfare#vulnerabilities#viruses#threats#Crypto_Chris#nso group#RCS Labs#hacking
0 notes
Text
Google Documents IE Browser Zero-Day Exploited by North Korean Hackers
Google’s Threat Analysis Group (TAG) has shared technical details on an Internet Explorer zero-day vulnerability exploited in attacks by North Korean hacking group APT37
Tracked as CVE-2022-41128 (CVSS score of 8.8), the vulnerability was identified in the browser’s ‘JScript9’ JavaScript engine and can be exploited by remote attackers to execute arbitrary code on a target system.
Google describes the security defect as an incorrect JIT optimization issue that leads to a type confusion. The bug is similar to CVE-2021-34480, a JScript9 flaw that was patched last year.
Microsoft patched CVE-2022-41128 one week after being alerted on it, as part of the November 2022 Patch Tuesday security updates, warning that the vulnerability was being exploited in attacks.
“This vulnerability requires that a user with an affected version of Windows accesses a malicious server. An attacker would have to host a specially crafted server share or website,” Microsoft warned at the time.
The tech giant noted that an attacker would need to entice the intended victim into visiting a specially crafted server share or website to trigger the exploit.
According to Google's public documentation, North Korea-linked APT37 used a malicious Microsoft Office document referencing the tragic incident in Seoul during Halloween celebrations on October 29, 2022 to target South Korean users with an exploit for CVE-2022-41128.
The malicious document was designed to fetch a rich text file (RTF) remote template, which in turn downloaded remote HTML content that Office would render using Internet Explorer.
Coming from an external source, the document would have the Mark-of-the-Web applied, and the user would have to disable the ‘Protected View’ in Office for the remote RTF template to be downloaded.
Google’s TAG researchers noticed that a cookie that is set when the RTF is delivered is sent again when the HTML content is requested, and that the JavaScript code would check for the cookie before launching the exploit.
Shellcode delivered during exploitation “erases all traces of exploitation by clearing the Internet Explorer cache and history before downloading the next stage” using the same cookie set when the remote RTF was delivered. Google says it could not retrieve the final payload.
The internet giant says that other identified documents that likely exploit the same Internet Explorer vulnerability and which appear to have similar targeting might be part of the same campaign.
APT37, which is known for using Internet Explorer zero-days in attacks, has historically focused on individuals in South Korea, while targeting North Korean defectors, human rights activists, journalists, and policy makers.
Also tracked as Group123, InkySquid, Reaper, and ScarCruft, and believed to be working on behalf of the North Korean government, APT37 was previously observed using backdoor like Bluelight, Dolphin, and Rokrat, which use legitimate cloud services for command-and-control (C&C).
#cybersecurity#kairoscybersecurity#kairoscybersecurityconsultants#security#cybercrime#cyberwarfare#cyberattack#hacking#cisa#phishing#identity theft#vulnerability#vulnerabilities#malware#viruses#virus#network
0 notes
Text
Apple Patches Zero-Day Vulnerability Exploited Against iPhones
Apple on Tuesday published 10 new advisories describing vulnerabilities affecting its products, including a zero-day that has been exploited against iPhone users.
Apple announced on November 30 that an advisory for iOS 16.1.2 would be released in the coming days. The advisory was published two weeks later, on Patch Tuesday, and it’s unclear why the tech giant waited for so long to make the information public.
According to the company, the flaw, tracked as CVE-2022-42856, is a type confusion affecting the WebKit browser engine. An attacker can exploit the vulnerability for arbitrary code execution by getting the targeted user to access a specially crafted website.
“Apple is aware of a report that this issue may have been actively exploited against versions of iOS released before iOS 15.1,” the company said in its advisory.
Clément Lecigne of Google's Threat Analysis Group has been credited for reporting the vulnerability to Apple. While no information has been released about the attacks leveraging CVE-2022-42856, Google typically tracks exploits used by sophisticated state-sponsored threat actors or commercial spyware vendors.
While it appears that CVE-2022-42856 has only been used against iPhone users, Apple has also patched the vulnerability with the release of macOS Ventura 13.1, tvOS 16.2, and Safari 16.2. iOS and iPadOS 15.7.2 also include fixes for the bug.
macOS Ventura 13.1 patches a total of 36 vulnerabilities that can lead to arbitrary code execution, sensitive information disclosure, security bypass, spoofing, or a denial-of-service (DoS) condition. macOS Big Sur 11.7.2 resolves 10 vulnerabilities, and macOS Monterey 12.6.2 fixes over a dozen issues.
A total of 35 flaws have been fixed with the release of iOS and iPadOS 16.2, and 17 security holes with the release of iOS and iPadOS 15.7.2
WatchOS 9.2 addresses 25 vulnerabilities, and tvOS 16.2 addresses 28 issues. Since these operating systems are based on iOS, most of these are flaws shared among all operating systems.
Safari 16.2 patches 10 flaws and iCloud for Windows 14.1 fixes three issues — all affecting WebKit.
Additional information is available on Apple's security updates pages
#ipados#macos update#cybersecurity#kairoscybersecurity#iOS#cve 2022 42855#kairoscybersecurityconsultants#security#cyberattack#hacking#cisa#zeroday
0 notes
Text
Uber suffers new data breach after attack on vendor, info leaked online
Update below: Uber shared further information with BleepingComputer on how its data was stolen in a breach on Teqtivity, which provides asset management and tracking services for the company.
Uber has suffered a new data breach after a threat actor leaked employee email addresses, corporate reports, and IT asset information stolen from a third-party vendor in a cybersecurity incident.
Early Saturday morning, a threat actor named 'UberLeaks' began leaking data they claimed was stolen from Uber and Uber Eats on a hacking forum known for publishing data breaches.
The leaked data includes numerous archives claiming to be source code associated with mobile device management platforms (MDM) used by Uber and Uber Eats and third-party vendor services.
The threat actor created four separate topics, allegedly for Uber MDM at uberhub.uberinternal.com and Uber Eats MDM, and the third-party Teqtivity MDM and TripActions MDM platforms.
Uber data leaked on a hacking forum
Source: BleepingComputer
Each post refers to a member of the Lapsus$ hacking group who is believed to be responsible for numerous high-profile attacks, including a September cyberattack on Uber where threat actors gained access to the internal network and the company's Slack server.
BleepingComputer has been told that the newly leaked data consists of source code, IT asset management reports, data destruction reports, Windows domain login names and email addresses, and other corporate information.
One of the documents seen by BleepingComputer includes email addresses and Windows Active Directory information for over 77,000 Uber employees.
While BleepingComputer initially thought this data was stolen during the September attack, Uber told BleepingComputer it believes it is related to a security breach on a third-party vendor.
“We believe these files are related to an incident at a third-party vendor and are unrelated to our security incident in September. Based on our initial review of the information available, the code is not owned by Uber; however, we are continuing to look into this matter.” - Uber.
Security researchers who have analyzed the leak told BleepingComputer that the leaked data is related to internal Uber corporate information and does not include any of its customers.
However, we are told that the leaked data contains enough detailed information to conduct targeted phishing attacks on Uber employees to acquire more sensitive information, such as login credentials.
Therefore, all Uber employees should be on the lookout for phishing emails impersonating Uber IT support and confirm all information directly with IT admins before responding to such emails.
BleepingComputer has reached out to Uber, TripActions, and Teqtivity with further questions regarding the incident but has not received a reply at this time.
Uber data was stolen in Teqtivity breach
Uber referred us to a Teqtivity data breach notification published this afternoon, which explains that a threat actor gained access to a Teqtivity AWS backup server that stores data for its customers.
This allowed the threat actor to access the following information for companies using their platform.
Device information: Serial Number, Make, Models, Technical Specs
User Information: First Name, Last Name, Work Email Address, Work Location details
Uber told BleepingComputer that the source code leaked on the hacking forum was created by Teqtivity to manage Uber's services, explaining the many references to the ride-sharing company.
Uber has also reiterated that the Lapsus$ group was not related to this breach, even though the forum posts reference one of the threat actors associated with the group.
Following the publishing of this story, Uber has shared that threat actors stole its data in a recent breach on Teqtivity, which it uses for asset management and tracking services.
While the forum posts state that they breached 'uberinternal.com,' Uber has said that they have not seen any malicious access to their systems.
"The third-party is still investigating but has confirmed that the data we've seen to date came from its systems, and to date we have not seen any malicious access to Uber Internal systems," Uber told BleepingComputer.
#cybersecurity#kairoscybersecurity#kairoscybersecurityconsultants#security#cyberattack#cybercrime#hacking#cyberattacks#data breach#lapsues#mobile device management#Uber
0 notes