#yes for whatever reason my vpn doesn't block ads on tumblr
Text
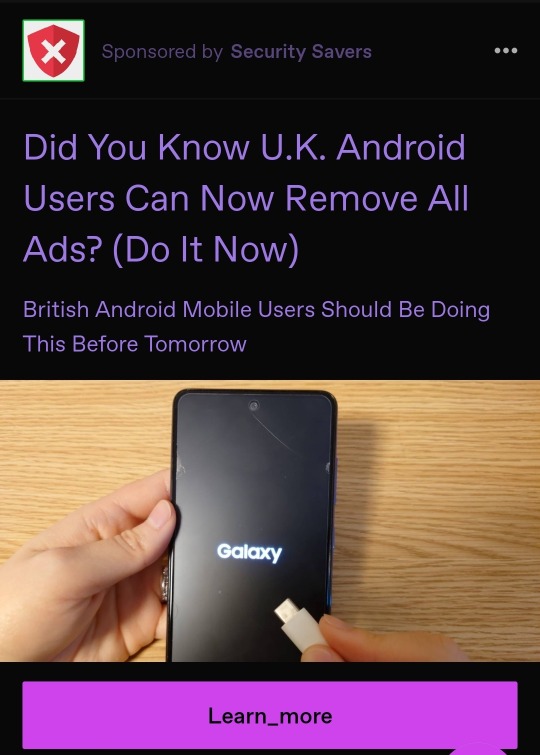
hmmn "(do it now)" and "before tomorrow" ??? randomer called "security savers" ?? clicking on them throws up a uBlock exception ????
definitely totally completely legit we promise this won't steal your data or try to defraud or scam you pinky prommy pls click our link pls pls pls pls
either this is tumblr attempting to coerce me into paying for ads to go away or it's a scam so uh heads up on both fronts friends !
#daemon.md#yes for whatever reason my vpn doesn't block ads on tumblr#but hey i'm switching out providers tomorrow anyway !
2 notes
·
View notes
Text

🔐 Why You (Probably) Don't Need A VPN
A rant by a software engineer sick of VPN ads from her favourite YouTubers
TL;DR:
Here are some legitimate reasons the average internet user might want to use a VPN:
To connect to their company's internal network
To bypass the Great Firewall of China (or other types of website blocks at country or organisation level)
To watch Netflix etc as if you were in another country
Here are absolutely rubbish reasons to use a VPN:
Privacy
And today, I'll tell you why.
Hang on, won't a VPN stop hackers from stealing my passwords?
I mean, it does encrypt the web traffic coming from your device.
You know what else encrypts web traffic coming from your device? Your browser.
Yes, in the year 2021, pretty much all websites on the internet are accessed over HTTPS. The "S" stands for "secure", as in "your request will be securely encrypted". If your browser is using HTTPS, nobody can capture the data you're sending over the internet. More detail in the "I like too much detail" section at the bottom of this post.
It's very easy to check if you are using HTTPS by looking at your URL bar. In most browsers, it will have a lock on it if secure:
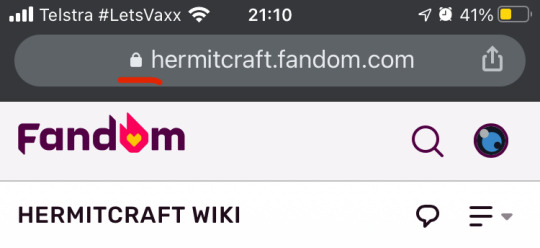
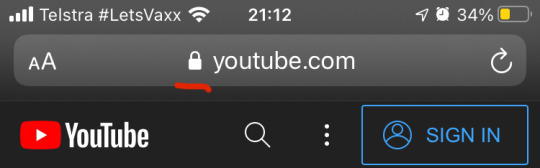




(From top left to bottom right: Chrome on iOS, Safari on iOS, Chrome on Windows, Edge on Windows, Firefox on Windows, and Safari on Mac. Screenshots reflect the UI at the time this post was written. Oh gosh this has taken over 4 hours to write.)
But isn't moar encryption better? What if somebody breaks HTTPS?
For starters, nobody's breaking your HTTPS, and there isn't any benefit from double encrypting. This is because of the maths behind encryption/decryption!
Encryption works kinda like a lock and key, except the lock is maths and the key is a special number only known to the person allowed to unlock the information.
The important thing is, without the key, all the locked data looks like complete and utter garbage. Completely unusable. Barely distinguishable from random noise. There's absolutely no way to tell what the original data was.
The other important thing is that the key is nearly unguessable. As in, with current technology, will generally take more than the lifetime of the universe to guess by chance. And when technology gets faster, we just make the numbers bigger again until they're once again secure.
For any major website you use, they will use a strong encryption algorithm (ie lock) with big numbers so your keys will be strong enough to withstand an attack. This means your data is safe as long as that lock icon is in your URL bar.
A VPN will not make the existing garble any more garbled. The extra $10/month or whatever you're paying for does not buy you any extra protection.
If you want to know more about how encryption and HTTPS in particular work, see the "I like too much detail" section at the end of this post.
Something something viruses
How's a VPN going to stop viruses? It controls the path your internet traffic takes, not the content that gets sent down that path. I guess it could block some known virus-giving hosts? But if it's known to the VPN provider, it's probably also known to the built-in antivirus on your computer who can block it for you.
(Oh yeah, 3rd party antivirus is another thing that's not worth paying for these days. Microsoft's built-in Windows Defender is as good as the third party options, and something something Macs don't get viruses easily because of how they're architected.)
Honestly though, keep your software up to date, don't click on anything suspicious, don't open files from sources you don't trust, and you'll be right most of the time.
And keep your software up to date. Then update your software. Hey, did I mention keeping your stuff updated? Update! Now! It only takes a few minutes. Please update to the latest version of your software I'm begging you. It's the number 1 way to protect yourself from viruses and other malware. Most major software attacks could have been prevented if people just updated their damn software!
But my ISP is spying on me!
Ok, it is true that there are TWO bits of data that HTTPS can't and won't hide. Those are:
The source of a request (your IP)
What website that request is going to (the website's IP)
These are the bits of information that routers use to know where to send your data, so of course they can't be hidden as the data is moving across the internet. And people can see that information very easily if they want to.
Note: this will show which website you're going to, but not which page you're looking at, and not the content of that page. So it will show that you were on Tumblr, but will not show anyone that you're still reading SuperWhoLock content in 2021.
It's this source/destination information that VPNs hide, which is why they can be used to bypass website blocks and region locks.
By using a VPN, those sniffing traffic on your side of the VPN will just show you connecting to the VPN, not the actual website you want. That means you can read AO3 at work/school without your boss/teachers knowing (unless they look over your shoulder of course).
As for those sniffing on the websites end, including the website itself, they will see the VPN as the source of the connection, not you. So if you're in the US and using a VPN node in the UK, Netflix will see you as being in the UK and show you their British library rather than the American one.
If this is what you're using a VPN for and you think the price is fair, then by all means keep doing it! This is 100% what VPNs are good for.
HOWEVER, and this is a big "however", if it's your ISP you're trying to hide your internet traffic from, then you will want to think twice before using a VPN.
Let me put it this way. Without a VPN, your ISP knows every website you connect to and when. With a VPN, do you know who has that exact same information? The VPN provider. Sure, many claim to not keep logs, but do you really trust the people asking for you to send them all your data for a fee to not just turn around and sell your data on for a profit, or worse?
In effect, you're trading one snooper for another. One snooper is heavily regulated, in many jurisdictions must obey net neutrality, and is already getting a big fee from you regardless of where you browse. The other isn't. Again, it's all a matter of who you trust more.
For me personally, I trust my ISP more than a random VPN provider, if for no other reason than my ISP is an old enough company with enough inertia and incompetence that I don't think they could organise to sell my data even if they wanted to. And with the amount of money I'm paying them per month, they've only got everything to lose if they broke consumer trust by on-selling that data. So yeah, I trust my ISP more with my privacy than the random VPN company.
But my VPN comes with a password manager!
Password managers are great. I 100% recommend you use a password manager. If there's one thing you could do right now to improve your security (other than updating your software, speaking of, have you updated yet?), it's getting and using a password manager.
Password managers also come for free.
I'm currently using LastPass free, but am planning to switch after they did a bad capitalism and only let their free accounts access either laptop or mobile but not both now. I personally am planning to move to Bitwarden on friends' recommendation since it's not only free but open source and available across devices. I also have friends who use passbolt and enjoy it, which is also free and open source, but it's also a bit DIY to set up. Great if you like tinkering though! And there are probably many other options out there if you do a bit of googling.
So, yeah, please use a password manager, but don't pay for it unless you actually have use for the extra features.
No I really need to hide my internet activity from everybody for reasons
In this case, you're probably looking for TOR. TOR is basically untraceable. It's also a terrible user experience for the most part because of this, so I'd only recommend it if you need it, such as if you're trying to escape the Great Firewall. But please don't use it for Bad Crimes. I am not to be held liable for any crime committed using information learned from this post.
Further reading viewing
If you want to know more about why you don't need a VPN, see Tom Scott's amazing video on the subject. It's honestly a great intro for beginners.
I like too much detail
Ahhh, so you're the type of person who doesn't get turned off by long explanations I see. Well, here's a little more info on the stuff I oversimplified in the main post about encryption. Uhh, words get bigger and more jargony in this section.
So first oversimplification: the assumption that all web traffic is either HTTP or HTTPS. This isn't exactly true. There are many other application layer internet standards out there, such as ssh, ftp, websockets, and all the proprietary standards certain companies use for stuff such as streaming and video conferencing. Some of these are secure, using TLS or some other security algorithm under the hood, and some of them aren't.
But most of the web requests you care about are HTTP/HTTPS calls. As for the rest, if they come from a company of a decent size that hasn't been hacked off the face of the planet already, they're probably also secure. In other words, you don't need to worry about it.
Next, we've already said that encryption works as a lock and a key, where the lock is a maths formula and the key is a number. But how do we get that key to lock and unlock the data?
Well, to answer that, we first need to talk about the two different types of encryption: symmetric and asymmetric. Symmetric encryption such as AES uses the same key to both encrypt and decrypt data, whereas asymmetric encryption such as RSA uses a different key to encode and decode.
For the sake of my writing, we're going to call the person encrypting Alice, the person decrypting Bob, and the eavesdropper trying to break our communications Eve from now on. These are standard names in crypto FYI. Also, crypto is short for cryptography not cryptocurrencies. Get your Bitcoin and Etherium outta here!
Sorry if things start getting incoherent. I'm tired. It's after 1am now.
So first, how do we get the key from symmetric crypto? This is probably the easier place to start. Well, you need a number, any number of sufficient size, that both Alice and Bob know. There are many ways you could share this number. They could decide it when they meet in person. They could send it to each other using carrier pigeons. Or they could radio it via morse code. But those aren't convenient, and somebody could intercept the number and use it to read all their messages.
So what we use instead is a super clever algorithm called Diffie-Hellman, which uses maths and, in particular, the fact it's really hard to factor large numbers (probably NP Hard to be specific, but there's no actual proof of that). The Wikipedia page for this is surprisingly easy to read, so I'll just direct you there to read all about it because I've been writing for too long. This algorithm allows Alice and Bob to agree on a secret number, despite Eve being able to read everything they send each other.
Now Alice and Bob have this secret number key, they can talk in private. Alice puts her message and the key into the encryption algorithm and out pops what looks like a load of garbage. She can then send this garbage to Bob without worrying about Eve being able to read it. Bob can then put the garbage and the key into the decryption algorithm to undo the scrambling and get the original message out telling him where the good donuts are. Voila, they're done!
But how does Alice know that she's sending her message to Bob and not Eve? Eve could pretend to be Bob so that Alice does the Diffie-Hellman dance with her instead and sends her the secret location of the good donuts instead.
This is where asymmetric crypto comes in! This is the one with private and public keys, and the one that uses prime numbers.
I'm not 100% across the maths on this one TBH, but it has something to do with group theory. Anyway, just like Diffie-Hellman, it relies on the fact that prime factorisation is hard, and so it does some magic with semi-primes, ie numbers with only 2 prime factors other than 1. Google it if you want to know more. I kinda zoned out of this bit in my security courses. Maths hard
But the effect of that maths is easier to explain: things that are encoded with one of the keys can only be decoded with the other key. This means that one of those keys can be well-known to the public and the other is known only to the person it belongs to.
If Alice wants to send a message to Bob and just Bob, no Eve allowed, she can first look up Bob's public key and encrypt a beginning message with that. Once Bob receives the message, he can decrypt it with his private key and read the contents. Eve can't read the contents though because, even though she has Bob's public key, she doesn't know his private key.
This public key information is what the lock in your browser is all about BTW. It's saying that the website is legit based on the public key they provide.
So why do we need symmetric crypto when we have asymmetric crypto? Seems a lot less hassle to exchange keys with asymmetric crypto.
Well, it's because asymmetric crypto is slooooow. So, in TLS, the security algorithm that puts the "S" in "HTTPS", asymmetric RSA is used to establish the initial connection and figure out what symmetric key to use, and then the rest of the session uses AES symmetric encryption using the agreed secret key.
And there you have it! Crypto in slightly-less-short-but-still-high-enough-level-that-I-hope-you-understand.
Just realised how long this section is. Well, I did call it "too much detail" for a reason.
Now, next question is what exactly is and isn't encrypted using HTTPS.
Well, as I said earlier, it's basically just the source IP:port and the destination IP:port. In fact, this information is actually communicated on the logical layer below the application layer HTTPS is on, known as the transport layer. Again, as I said before, you can't really encrypt this unless you don't want your data to reach the place you want at all.
Also, DNS is unencrypted. A DNS request is a request that turns a domain name, such as tumblr.com, into an IP address, by asking a special server called a Domain Name Server where to find the website you're looking for. A DNS request is made before an HTTP(S) request. Anyone who can read your internet traffic can therefore tell you wanted to go to Tumblr.
But importantly, this only shows the domain name, not the full URL. The rest of the URL, the part after the third slash (the first two slashes being part of http://), is stuff that's interpreted by the server itself and so isn't needed during transport. Therefore, it encrypted and completely unreadable, just like all the content on your page.
I was going to show a Wireshark scan of a web request using HTTP and HTTPS to show you the difference, but this has taken long enough to write as it is, so sorry!
I could probably write more, but it's 1:30am and I'm sleepy. I hope you found some of this interesting and think twice before purchasing a VPN subscription. Again, there are legit good uses for a VPN, but they're not the ones primarily being advertised in VPN ads. It's the fact that VPN ads rely so heavily on false advertising that really grinds my gears and made me want to do this rant. It's especially bad when it comes from somebody I'd think of as technologically competent (naming no names here, but if you've worked in tech and still promote VPNs as a way to keep data safe... no). Feel free to ask questions if you want and hopefully I'll get around to answering any that I feel I know enough to answer.
Nighty night Tumblr. Please update your software. And use a (free) password manager. And enable two factor authentication on all your accounts. But mostly just update your software.
577 notes
·
View notes