#theres so much stuff PUBLICLY AVAILABLE TO YOU that you can research through and find new stuff
Note
how do you feel about the new tf2 leaks?
Oh it big sucks!
listen, this leak honestly makes me so mad im not even joking. not because of like, leaks like this cause so much trouble for the developers who own them (in how to combat it), or for the source licencees who are affected by the leak, but WHO it affects in this community.
say you've been working a beta recreation of 2Fort from Trailer 2 (since it's the version with the most footage), you've been working on it in your spare time for the past... 6 years lets say. you know the ins and outs of this map, you've watched footage and studied screenshots from around August 2006, and you've made an intense list of all the eras of 2Fort to ensure you have a timeline of eras so you know which to avoid and such.
so your beta 2Fort recreation is as accurate it can be from all the public media you could find from it. you've even gotten the sewers to be as low as they were in the beta combined with the higher water. there's some things left to your interpretation of the map, since the sewers have never been shown for example, and you push it out for people to play around on. this was basically your hobby for the past 6 years, and it meant so much to you to be able to create something with a love you can't put to words.
suddenly. the worst thing imaginable. a month after you post it? an entire developer repo leaks. and lets pretend it's got that version of 2Fort intact. that's a serious gut punch BUT, then you get comments from folks like "oh the actual 2fort leaked" "this is obsolete now" "oh well a recreation couldn't ever top a leak". it's demoralizing. it breaks their spirit for something they worked so hard on. the one thing you loved working on? well seemingly it doesn't matter now to the community you painstakingly made it for.
that's what hurts for me, is the people who've created content based off of things from TF2 (like the Spellcasters Witch), whom have made it from scratch, added their own personal touches like different outfits and hairstyles, to the ability to allow the user to recolour every part of that outfit. then a leak comes along and it seems everyone's ferally knashing their teeth at this leak. no leak can ever come close to the kind of love community members put into stuff.
that's why i hate this leak. and even with the 60 gigabytes of stuff that's leaked? people are still like "oh well this doesn't have everything 🙄". like sorry 60GB wasn't enough for you?
i hope we never see a TF2 leak again. this shit sucks and i hate the community around it.
#ask#catsmocha#i dont care whats in it. i dont care what maps are found. it fucking sucks#id have to imagine that any valve dev who had a slight want in working on TF2 again have quickly changed their mind from this#what do i know. im just some guy#but the whole ''cut content community'' for tf2 sucks#theyve been sitting on their hands waiting for the repo to leak. and theyre not even satisfied#now they want the SFM repo! which i bet doesnt exist. or wont exist now that this's happened#good job you idiots!#youll never see a TF2 leak after this point ill tell you that much. and good!!!! fuck 'em!!!#none of them deserve this stuff#sorry im just really mad at how people treat scrapped content for this game#theres so much stuff PUBLICLY AVAILABLE TO YOU that you can research through and find new stuff#but no 🙄💅 gotta get my hands on that repo!!! cant waste my time looking elsewhere#it makes me so mad#legit my heart goes out to the content creators who made models and maps before this leak#you put so much work into your craft. im sorry its being ignored for this shit#thank you for the ask honestly. i feel like if i didnt have an ask like this i wouldve explo💥💥💥💥💥
55 notes
·
View notes
Text
Week 7 Notes and Reflection
REFLECTION
Unfortunately I ran out of battery and lost the lectures notes for the second lecture. I had to reconstruct them using the class notes, Richard’s “slides” and what I remember. I’ll especially have to research more about Public Key Infrastructure later, it seems interesting!
Interesting lecture, I like how we found a mistake on the exam! I also liked the way Richard described Man in the middle attacks in Diffie-Hellman. There were lots of “homework” activities so I should do those!
I thought it was pretty insane you can write to memory using %n in printf! I wonder what the designers of printf were thinking?! They were like “o ye lets scan in some stuff using our printing function!!”
The extended lectures were cool - I found it weird that pressing that Command + S key on a Mac gives you root. There are so many interesting practical things with security... bug bounties, CTFs that you don’t really see in other areas of computing such as AI.
NOTES
Mid Term Exam
Question 5 Solution - Can’t brute force it by hand. The answer is F - type I /Type II error tradeoff.
Question 10 - The answer is D - easy to factorise a 64 bit number. Even 512 bit modulus is crackable. However even RSA is wrong for some reason.... All wrong!!
Proof of liveness - Like a replay attack, challenge response. Proof that there is someone there.
Richard expects you to go to all the lectures. Should have known Sun Tzu!
Diffie-Hellman - How do you set that shared secret up?
5^3^7 is the same as 5^7^3. Power raising is associative.
R -> 78125 -> S
S-> 125 -> R
We don’t know R or S private key. Only the number they raised (5). Very difficult to solve the discrete log problem, to go backward to the private key.
When both sides receive their key, they both raise the value by their private key. Both becomes the same.
Forward Secrecy - protects the future messages.
Syria Castle - Defence in depth. The castle fell when the sieiging people forged a letter telling the castle people to surrender. Didn’t fall due to the defence of the castle.
CYBER LITERACY - VULNERABILITIES
A vulnerability is a weakness, and an exploit something that takes advantage of that.
Bug - software mistake. Sometimes bugs become vulnerability.
Types
Memory corruption - somehow the bad guy can change something in memory to allow the program to be under the control of the bad guy.
Buffer overflow
Stack and heap - FIFO temporary info about the functions are on the stack. Heap for allocated memory - dynamic memory allocation.
How functions are called in C - when control switches to another function, the function is frozen. Temporary info such as registers stored on stack. COMP1521 stuff.
Integer overflow - If you keep adding, it will go negative. This can cause it to maybe pass some tests.
Format String - Like Bird flu - Everyone has written buffer overflow bad code in the old days! Then people started patching it. Apparently they are coming back. C has crazy way of printing stuff using printf(). In the old days when you wanted to print hello world had to use printf(”%s\n”, “Hello World”). However no ever did that. Everyone just writes printf(”Hello World\n”). However someone might write name <- get user name. Then you want to print the name you write printf(name). E.g. my name is “%s Richard Buckland”. It will try and look lower down in the stack and print that out as the argument. %s will print out the contents of the stack until a null character. You can use %x to print out the next byte and print out hexadecimal versions of the stack. Printf(”%x %x %x %x”). Shows entire contents of stack. Could have passwords, return addresses. %n WRITES TO MEMORY. You can do arbitrary writes to memory.
Swiss Cheese - holes might line up! Holes overlapping and poke finger through. These sort of bugs are like that! Get lucky.
Stack Canary? Research that.
Shell Code - if you attacking a system, how nice it would be to get a private shell to come up and do whatever you want? Write some machine code that calls OS functions that makes shell pop up. This code is shell code. Put shell code into a buffer and run it.
Nop sleds - You can use buffer overflows to jump back to your buffer to run programs. However sometimes don’t know where in memory where the code is placed. Nice to have a bit of wiggle room. Just put lots of NOP operations - it will be like a slide into your code. Looking for NOP sleds - malware scanners. However whole lots of way to write NOP sleds without NOP.
If you find vulnerabilities, into will go into the National Vulnerability Database and CVN (Common Vulnerabilities and Exposures) and CNA (CVE Naming Authority).
Responsible disclosure - If you find a vulnerability, tell the vendor then CERT(eg CERT Australia). or you can sell it to the bad guys!
OWASP Top 10 list should know for top 10 vulnerabilities. Essentially the same every year!
BUG PUZZLES - Check slides
Example 1 - Integer overflow for the length. Get_user_length is UNSIGNED, but length is signed. Lots of implicit conversions between sign and unsigned. Then read will read the overflowed length value since read() takes in an unsigned length value, which might be bigger than 1024.
Example 2- Optimistic indenting
ASSETS
Security is to protect your assets. Sometimes we protect the wrong assets. Cold war - I wonder if the world will be here tomorrow? The most important asset is to protect mankind.
Door bell on the car - If you placed that in the car it went ding dong in his house. $5 car alarm first step into brilliance. What are you going to do when the ding dong happens? Might run down there and get killed!! The real asset is the window of the car, not the money! Leave the window open! Got wallet stolen, but got AIDS. Easy to protect the wrong thing.
At the uni’s security review was all machines. Uni assets are students, reputation, user data, staff. The trick is, what you should do is the assets - what are you trying to protect? Ask people - junior, senior people. Review the list of assets every year/month. Real weakness is something you don’t see - blind spot. Try and find the things you haven’t seen.
Strategies for Identifying the Assets
Regularly surveying the values of people of the involved in what you are protecting. Multiple pairs of eyes is a good asset.
Develop a sensible plan - well designed to tease this information out of them. Humans are generally poor at regurgitating everything they know, however they are generally very good critics.
Periodically revise current list of assets. Don't set and forget. Values and assets of an organisation can drift.
Examples
Team America
Richard's wallet vs Richard with AIDS
Car doorbell
Leave windows open?
Share registry - no more paper trails, everything is recorded electronically. Land title database was privatised. What are the risks?
Coke formula
Parliament - a collection of people that hold particular importance together.
Valuing the Assets - Defining what is important
Categorising types of assets
Tangible Assets: Those that are easily given a value
A gold chain valued at some relatively static amount
The jewellery in a jewellery store.
Intangible Assets: These cannot be easily and objectively be valued
Company secrets
Availability of services
Employee Morale & Security
Customer information
* Monetary + psychological/emotional costs
* Difficult <> Don't do
Examples:
Company secret - what is at stake?
QOS Guarantees
Strategies for assigning values to assets
Survey what many people think
no single person or group should be solely evaluating the assets;
Examples of the information that should be gathered are as follows:
"How much money would you lose where this data center to go down for 24 hours?".
"How much will you lose if your company is disconnected to the internet for 3 hours?".
Examples
In assessing the value of a park
Picasso
Diffie-Hellman - Only provides confidentiality and integrity? Does not provide authentication.
Web of Trust (PgP) - Research this
Public Key Infrastructure (PKI)
SSL/TLS
Read Bruce Schneier's paper https://www.schneier.com/academic/paperfiles/paper-pki.pdf
passports (links photo with name, certified by office)
x509 certificates (links public key with domain (and maybe some other info))
padlock in your browser
look at some certs
CAs, root certificates, RAs, pay money to browser manufacturer??!! (check out your web browser)
conflicts of interest
most google search pages on SSL written by vendors
it was the blockchain of the 2000s
self signed, domain verification, organisational verification, extended verification. (ha!)
what if anything are the risks of self-signed?
safety vs identity
the green bar
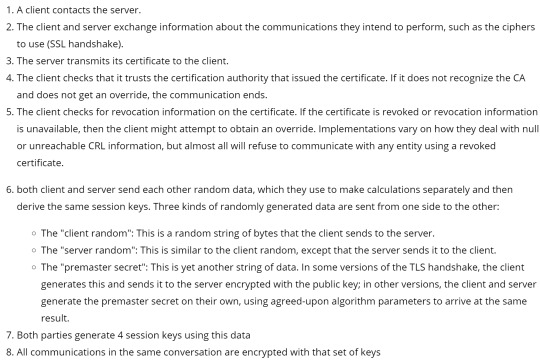
session keys - the TLS handshake (4 keys)
why use session keys rather than using RSA for all?
wildcards
3 main certificate authorities: Symantec, Comodo, GoDaddy
homework : find examples of (serious) fraudulant certificates being issued
Certificates don’t protect against gooooogle.com
TLS handshake example
BUG BOUNTIES (From notes, I lost mine)
Crowd-Sourced Bug Bounty Websites
Public: Hackerone, bugcrowd
Private: Synack
Often have criteria of whats in/out of scope, as well as what kind of bugs they won’t accept. For example websites that they don’t want you touch
Tips
Learn web apps
Usea a wide scope → bigger net = more bugs
Look for software updates, or assets that have recently changed
Look for publicly disclosed reports → Can see prior bugs that have been found/exposed. If a bug has occurred once, theres a chance it will occur again
Pentesting (From notes, I lost mine)
Fuzzing
Automate process - a program that continually adds input
Some fuzzers are aware of input structure, and some even are away of program structure
Fuzzers aren't precise, but can test a large amount of inputs
Fuzzing software - afl (the way to go apparently)
Mutation strategies - bit flips, byte flips, arithmetic, havoc (combination
Use fuzzing to test your own software
Homework: Do the fuzzing tutorial
0 notes